Appendix
The Bottom Line
Chapter 1: Abstracting Network and Security
- SDDC Virtualization Software Defined Data Centers are possible due to decoupling physical hardware from software. VMware changed the game by first virtualizing compute resources. VMware virtual machines are operating systems that have been separated from the physical server by a hypervisor abstraction layer, called ESXi.
- Master It VMware extended the same concepts to the other major infrastructure services including storage, networking, and security. What is the name of the hypervisor abstraction layer that VMware developed for networking and security?
- Solution NSX
- NSX Prerequisites NSX re-creates traditional physical network components such as routers, switches, ports, and firewalls in software. You manage the vSphere team for your organization and are considering NSX. Which additional physical components are required before NSX can be deployed? (Choose all that apply.)
- Master It
- Firewall virtual appliance
- Distributed Resource Scheduler (DRS)
- SDDC-compatible servers
- None
- Solution 4. NSX is a software overlay that runs over the existing physical network created by adding components to the ESXi hypervisor. No additional physical devices are needed.
- Master It
- NSX Kernel-Embedded Firewall By moving firewall services to the kernel, which of the following is not true?
- Master It
- An embedded firewall only increases resource utilization by a negligible amount.
- Bandwidth is conserved due to the elimination of hairpinning.
- Firewall rules are distributed and are the same on every ESXi host.
- VM-to-VM traffic is easier to secure.
- Solution 1. By embedding the firewall in the kernel, it decreases resource utilization, avoiding the need to send every packet to an external firewall.
- Master It
Chapter 2: NSX Architecture and Requirements
- Planes of Operation Traditional network devices operate autonomously, having the management, control, and data planes all contained within each. NSX moves the management plane to NSX Manager and the control plane to NSX Controllers.
- Master It What NSX component provides the data plane?
- NSX Data Appliance
- NSX Virtual Switch
- ESXi Host
- NSX Edge
- Solution 2. NSX Virtual Switch
- Master It What NSX component provides the data plane?
- NSX Controllers Instead of an active/backup design, each NSX Controller in a cluster is always active. This is so that they can slice and share the workloads.
- Master It When deploying NSX Controllers in production, how many should a cluster contain?
- Solution Three
- Software-Defined Data Center Terminology It's commonly thought that most data center traffic is between the data center and outside networks, when in reality, it is from one VM to another within the data center. Both types of traffic have specific SDDC terms to describe each.
- Master It East-West traffic refers to:
- Traffic within the data center
- Traffic between the data center and outside networks
- Traffic between the virtual and physical networks
- Solution 1. Traffic within the data center. This includes traffic from VM to VM within the same ESXi host and traffic between VMs located on different hosts.
- Master It East-West traffic refers to:
Chapter 3: Preparing NSX
- Deploying NSX Manager When deploying the NSX Manager, rather than cloning an existing instance, it is recommended to deploy it from an OVA file.
- Master It The primary reason for deploying from an OVA file is so that NSX Manager gets its own what?
- Solution UUID (Universally Unique Identifier)
- Deploying an NSX Controller A secure password must be configured when deploying an NSX Controller.
- Master It Which of the following is not a listed requirement for the NSX Controller password to be accepted?
- At least one uppercase letter
- At least one lowercase letter
- At least one special character
- At least eight characters
- At least 12 characters
- Solution 4. At least eight characters. The minimum password size for the NSX Controller is 12.
- Master It Which of the following is not a listed requirement for the NSX Controller password to be accepted?
- Connectivity between Multiple vCenter Domains Cross-vCenter can allow multiple data centers to be managed from a central point.
- Master It Your Cross-vCenter design will include one primary NSX Manager and four secondary NSX Managers. How many vCenter Servers are required to support this configuration?
- Solution Five. There is a one-to-one relationship between an NSX Manager and a vCenter Server. This holds true even when the design includes a primary NSX Manager and several secondaries.
Chapter 4: Distributed Logical Switch
- Address Resolution Protocol Address Resolution Protocol (ARP) is used to discover the MAC address of the next hop along the path.
- Master It You are troubleshooting a connectivity issue (see Figure 4.28). In one of your tests, you ping the server on the right from the PC on the left. Using a packet sniffer, you examine the packet received on the server. If everything is working as it should, what source MAC address do you expect to see in the Layer 2 header?
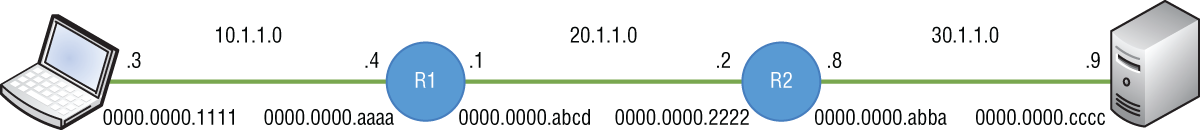
FIGURE 4.28 Troubleshooting connectivity
- Solution 0000.0000.abba
Source and destination MAC addresses are used to cross each local link. Once received, the Layer 2 header is discarded and a new Layer 2 source and destination are filled in for the next link. The server would have seen the source MAC to be that of R2 (0000.0000.abba), not the PC's MAC address (0000.0000.1111), and it would have seen the destination MAC to be its own (0000.0000.cccc). The Layer 3 header is different. It doesn't change from end to end. The server would still see the L3 source as 10.1.1.3 and the L3 destination as itself, 30.1.1.9.
- Master It You are troubleshooting a connectivity issue (see Figure 4.28). In one of your tests, you ping the server on the right from the PC on the left. Using a packet sniffer, you examine the packet received on the server. If everything is working as it should, what source MAC address do you expect to see in the Layer 2 header?
- VTEP Table The Virtual Tunnel Endpoint can be thought of as a door or subway stop on the ESXi host to the VMs behind it. The VTEPs store the information for every VNI and VM that is local to the host. This information is then sent to the Controllers, which are responsible for distributing the information to all of the other ESXi hosts.
- Master It You are troubleshooting an issue and need to verify that the mappings are correct. You issue the following command:
show logical-switch controller master vni 5001 vtepWhat do you expect to see?
- VNI 5001, the VTEP IP, and the VTEP MAC
- VNI 5001, the VTEP IP, and the VM MAC
- VNI 5001, the VM IP, and the VM MAC
- VNI 5001, the VTEP IP, and the VM IP
- Solution 1. VNI 5001, the VTEP IP, and the VTEP MAC.
The MAC table tells you where the VM lives; which door to go through. It maps the VM's MAC address (what you're trying to find) to the VTEP's IP address (the door).
The ARP table tells you the MAC address of the VM.
It maps the VM's IP address to its MAC address.
The VTEP table, which is what this question was asking about, tells you the MAC address of the VTEP.
It maps the VTEP's IP address to the VTEP's MAC address.
- Master It You are troubleshooting an issue and need to verify that the mappings are correct. You issue the following command:
- VXLAN Encapsulation NSX is a virtual overlay that exists on top of your physical network, the underlay. Once implemented, it's possible to greatly simplify your data center L2 design and quickly deploy a VM to attach to any segment regardless of its location within the data center. This is possible due to VXLAN encapsulation, which allows the traffic from the NSX virtual environment to be tunneled through the physical environment. Doing so adds an additional 50 bytes to your Ethernet headers.
- Master It In order to accommodate VXLAN encapsulation, what might you need to change in your physical environment?
- Enable trunking on the physical switches
- Install hardware VTEPs
- Change the MTU size
- Suppress ARP broadcasts
- Solution 3. Change the MTU size
By default, Ethernet has a Maximum Transmission Unit size of 1500 bytes. This means that any traffic larger than the set maximum will either be fragmented, or depending on the configuration, dropped. VMware recommends that the MTU size be changed to at least 1600 bytes. If your network is using jumbo frames (9000+ bytes), it will depend on what is running in your physical network.
The maximum MTU for Arista is 9214 bytes. The maximum for Cisco is 9216, and the maximum for Juniper is 9192.
- Master It In order to accommodate VXLAN encapsulation, what might you need to change in your physical environment?
Chapter 5: Marrying VLANs and VXLANs
- Creating a Layer 2 Bridge Getting VM 172.16.1.5 on ESXi Host1 to communicate with VM 172.16.1.7 on ESXi Host9 can be easily accomplished in NSX using a VXLAN. The X is for eXtensible. You can use it extend your Layer 2 domain across any of your hosts, regardless of where they are located in your data center. NSX provides the virtual overlay network, and it's easy to have virtual talk to virtual. But we often want to be able to just as easily have virtual talk to physical: VXLAN to VLAN.
- Master It You are configuring a Layer 2 Bridge to connect the VMs on VXLAN 5005 to the physical servers on VLAN 20. You're logged in to vSphere and you go to Menu ➢ Networking & Security (see Figure 5.31).

FIGURE 5.31 Network And Security (NSX) menu options
To create a Layer 2 Bridge, what do you click next?
- Dashboard
- Installation and Upgrade
- Logical Switches
- NSX Edges
- Solution 4. NSX Edges
The first step is to create a Distributed Logical Router. DLRs and ESGs are two flavors of NSX Edges.We need to use the DLR as a Control VM to create a Layer 2 Bridge.
To do this, you will need to go to:
NSX Edges ➢ Add ➢ Distributed Logical Router
- Master It You are configuring a Layer 2 Bridge to connect the VMs on VXLAN 5005 to the physical servers on VLAN 20. You're logged in to vSphere and you go to Menu ➢ Networking & Security (see Figure 5.31).
- Hardware VTEP NSX provides several ways to bridge a VXLAN with a VLAN sharing the same IP subnet. You could create a Layer 2 Bridge (software bridge), use a hardware VTEP, or configure a Layer 2 VPN.
- Master It You have been tasked with choosing a solution to bridge a workload on VXLAN 5005 with VLAN 15 on the physical network. Which of the following reasons might you give for implementing a hardware VTEP?
- Least cost
- Lowest latency
- Single vendor solution
- Services embedded in the VMkernel have a negligible impact
- Solution 2. Lowest latency
Hardware VTEPs provide the lowest latency of the three choices. The higher cost of a physical switch supporting a hardware VTEP is a factor, and if troubleshooting support is needed, it may involve both VMware and the physical switch vendor. Also note that the hardware VTEP is not a service embedded in the VMkernel.
- Master It You have been tasked with choosing a solution to bridge a workload on VXLAN 5005 with VLAN 15 on the physical network. Which of the following reasons might you give for implementing a hardware VTEP?
- To Bridge or Not to Bridge Virtualization involves abstraction, and abstraction is all about hiding the underlying complexities. Moving workloads into the virtual environment provides options for simplification, including the ability to have single subnets that span the data center vs. lots of smaller individual domains to manage.
Some situations don't allow you to move workloads from the physical network to the virtual overlay in their entirety. When faced with this issue, knowing how to bridge the two can help to solve the problem with minimal effort.
- Master It In which of the following situations would bridging not be considered?
- Servers attached to a VLAN need to communicate at Layer 2 with VMs attached to a Logical Switch.
- You are unable to virtualize an application due to licensing costs.
- A VLAN port group on vDS-1 needs to communicate at Layer 2 with a VXLAN Logical Switch on vDS-2 in the same data center.
- A legacy server can't be virtualized.
- Solution 3. A VLAN port group on vDS-1 needs to communicate at Layer 2 with a VXLAN Logical Switch on vDS-2 in the same data center.
The VLAN port group and VXLAN Logical Switch must be connected to the same vDS in order to bridge them.
- Master It In which of the following situations would bridging not be considered?
Chapter 6: Distributed Logical Router
- Forwarding Address vs. Protocol Address The control and data planes are separate in NSX. The separation allows for higher availability since it's possible for the control plane to fail, while the data plane continues to route traffic.
- Master It Because of the dichotomy of routing functions, there is a protocol address and a forwarding address assigned to learn routes and to route traffic. Which component would be assigned the forwarding address?
- DLR
- ESG
- LR Control VM
- UWA
- Solution 1. DLR
The LR Control VM doesn't route any traffic, but it requires an IP address to be able to peer with the ESG to exchange routing information. That address is the protocol (routing protocol) address. The forwarding address is used by the DLR, not to exchange routing information, but to route the traffic to the ESG.
- Master It Because of the dichotomy of routing functions, there is a protocol address and a forwarding address assigned to learn routes and to route traffic. Which component would be assigned the forwarding address?
- North-South East-West NSX handles VM-to-VM (East-West) traffic as well as NSX-to-physical (North-South) traffic. By a large margin, most traffic flows in a data center are made up of East-West traffic.
- Master It What component specializes and is optimized for East-West traffic?
- ESG
- DLR
- Layer 2 Bridge
- Internal LIF
- Solution 2. DLR
Because the DLR is a distributed router across all ESXi hosts in a transport zone, routing decisions do not have to be looked up on a routing device outside the host, causing the conversation to hairpin. Instead, the routing information is distributed to the host itself, in the kernel.
- Master It What component specializes and is optimized for East-West traffic?
- OSPF Design Rules OSPF is one option to use as a dynamic routing protocol for NSX. OSPF implementations require adhering to rules designed for scalability and stability. OSPF can operate in a single area, but convergence can be optimized by subdividing OSPF into multiple areas.
- Master It If your OSPF design has multiple areas, which of the following is true?
- All LSAs are Type 7 NSSA.
- One area must be numbered 0.
- No areas can be numbered 0.
- Adding areas reduces scalability.
- Solution 2. One area must be numbered 0.
Area 0 is the backbone area. If you only have one area, you are free to choose any number, but as soon as a second area is added, one must be Area 0. All other areas, by OSPF design, should directly connect to Area 0.
- Master It If your OSPF design has multiple areas, which of the following is true?
- DLR Minus a LR Control VM When installing a DLR, a Logical Router Control VM is also deployed, by default. However, it's possible to deploy the DLR without the Control VM.
- Master It Which could be a valid reason for purposefully choosing not to deploy the LR Control VM with the DLR?
- You are only using the DLR to route North-South traffic.
- You don't need the Control VM with OSPF.
- You don't need the Control VM with static routes.
- The LR Control VM is only necessary if the DLR is supporting multiple routing protocols simultaneously.
- Solution 3. You don't need the Control VM with static routes.
The LR Control VM is used to peer with the ESG to exchange routes dynamically using a routing protocol. If you are only using static routes, it isn't necessary; however, you may want to add it anyway in case you change your mind later and want to enable a dynamic routing protocol. Also, the LR Control VM can only run a single routing protocol at a time.
- Master It Which could be a valid reason for purposefully choosing not to deploy the LR Control VM with the DLR?
Chapter 7: NFV: Routing with NSX Edges
- Virtualization Terminology NSX is VMware's Software-Defined Network solution for network virtualization and security. Network Function Virtualization (NVF) is often mentioned when discussing SDN, but they aren't synonymous terms.
- Master It NFV and SDN go hand-in-hand, but they have different objectives.
Which of the following is an objective of NFV?
- Abstracting network functions from physical to virtual
- Abstracting the control plane from the data plane
- Abstracting routing functions from the kernel
- Abstracting routing protocols
- Solution 1. Abstracting network functions from physical to virtual
Network Function Virtualization focuses on taking network functions that have traditionally been supplied by physical devices, such as a physical firewall, and virtualizing the function. SDN's focus is on abstracting the control plane from the data plane to provide centralized control.
- Master It NFV and SDN go hand-in-hand, but they have different objectives.
- DLR Routing Restrictions Physical routers can easily run multiple routing protocols simultaneously and often support proprietary routing protocols like Cisco's EIGRP as well. They take a “ships in the night” approach with each protocol keeping track of its own information independently. With an NSX DLR, the supported routing options are different.
- Master It Which of the following can a DLR support?
- Only one routing method: BGP, OSPF, or static routes
- BGP and OSPF simultaneously
- BGP and static routes simultaneously
- BGP, OSPF, IS-IS, and static routes
- Solution 3. BGP and static routes simultaneously
A DLR can run a single dynamic routing protocol (BGP or OSPF) and static routes at the same time. BGP and OSPF cannot be run simultaneously and IS-IS is not supported by the DLR at all.
- Master It Which of the following can a DLR support?
- Configuring BGP on a DLR or ESG BGP comes in two flavors: internal BGP (iBGP) and external BGP (eBGP). Both are supported by the DLR and the ESG.
- Master It The ESG is using BGP to exchange routes with the DLR. Examining the configuration, you find that the DLR uses AS number 65000 and the ESG is configured with AS 65001. Which statement is true?
- iBGP is configured.
- eBGP is configured.
- 65000 is not a valid AS number.
- The AS number must match to exchange routes.
- Solution 2. eBGP is configured.
External BGP implies that your BGP neighbor does not share the same AS number. With Internal BGP, the AS numbers match. Either iBGP or eBGP could be used between the DLR and ESG. BGP AS numbers have a private range from 64512 to 65535. Therefore, 65000 is a valid AS number.
- Master It The ESG is using BGP to exchange routes with the DLR. Examining the configuration, you find that the DLR uses AS number 65000 and the ESG is configured with AS 65001. Which statement is true?
- Justifications for Enabling ECMP Equal Cost Multi-Path (ECMP) routing is a mechanism for routing packets over parallel links all having the same cost. Because they are both parallel and equivalent in terms of routing characteristics, the protocol allows the links to act as if they were bundled together.
- Master It Which of the following would not be a valid reason for enabling ECMP for connections between NSX and the external network?
- To increase scalability
- To increase availability
- BGP does not load balance by default
- OSPF does not load balance by default
- Solution Virtually every dynamic routing protocol load balances across equal cost paths by default (OSPFv2, IS-IS, RIP, RIPv2, EIGRP as well as their IPv6 cousins OSPFv3, IS-IS for IPv6, RIPng, and EIGRP for IPv6). BGP is the exception in its attempt to be overly cautious about preventing routing loops. ECMP provides a way to allow multiple BGP equal cost routes to coexist in the routing table. The benefits outweigh the risks here, since you are trading what might be considered an excessive precaution for the benefits of increased bandwidth, fault tolerance, load balancing, and the ability to reduce failover time to zero in the case of a single path failing.
- Master It Which of the following would not be a valid reason for enabling ECMP for connections between NSX and the external network?
Chapter 8: More NVF: NSX Edge Services Gateway
- Matching VPN Solution to Use Case The NSX Edge Services Gateway supports several types of VPNs to support different use cases. When choosing a VPN solution, factors to consider include temporary vs. permanent and mobile vs. fixed locations.
- Master It Your organization has contractors based in different countries who travel to customer sites. To access resources within the corporate data center in New York, which type of VPN would you configure for these workers?
- Site-to-site VPN
- Layer 2 VPN
- Layer 3 VPN
- SSL VPN
- Solution 4. SSL VPN
The SSL VPN is a user VPN allowing the user to initiate a connection and form a secure tunnel to the destination.
- Master It Your organization has contractors based in different countries who travel to customer sites. To access resources within the corporate data center in New York, which type of VPN would you configure for these workers?
- Benefits in Balancing Availability and scalability are always a concern in any network. Load balancing provides both. For example, if you are load balancing traffic across four servers, availability is not affected if one server needs to be taken down for maintenance. The other three continue working and the service remains available. Or say you are load balancing across four web servers. You can scale up and add more servers to improve performance when needed or scale down by removing servers when overall utilization decreases.
- Master It Which of the following is not a valid load balancer configuration choice when specifying how the ESG will split the incoming traffic to connected servers?
- Weighted round-robin
- IP hash
- Least used connection
- Most used connection
- Solution 4. Most used connection
There is no option for most used connection. The least used connection algorithm takes into consideration the server load. It checks to see which server has the least number of active sessions and sends the traffic to that server.
- Master It Which of the following is not a valid load balancer configuration choice when specifying how the ESG will split the incoming traffic to connected servers?
- Choosing the Right Interface to Relay An Amazon delivery driver places a package on your porch and rings the doorbell. The bell rings throughout the house but no one is home to hear it. This is analogous to a DHCP Discover message. It's a broadcast intended for the local segment, which is fine if you have a DHCP server on that segment (or for the analogy, that someone is home). DHCP Relay is like having a smart doorbell connected to the cloud. When the doorbell button is pressed, it sends live video to your phone allowing you to communicate with the delivery driver. Similarly, DHCP Relay forwards the message to the ESG, which responds with an offer.
- Master It In Figure 8.50, the admin configured a DHCP Relay Agent so that VM-B could successfully receive an IP address from the ESG. On which interface did the admin configure DHCP Relay to get this to work?
- 192.168.1.1
- 192.168.1.2
- 10.30.8.1
- 10.10.1.1
- Solution 3. 10.30.8.1
The question was specifically referring to VM-B. VM-B is on the 10.30.8.X segment. If the DLR's internal interface, 10.30.8.1, is configured as a DHCP Relay Agent, the interface will actively listen for and intercept DHCP messages on that connected segment and will forward them to the DHCP server, which in this example is the ESG, 192.168.1.1. To make it easier to remember where to configure the agent, DHCP Relay is almost always configured on the interface used as the default gateway for the VMs.
- Master It In Figure 8.50, the admin configured a DHCP Relay Agent so that VM-B could successfully receive an IP address from the ESG. On which interface did the admin configure DHCP Relay to get this to work?
Chapter 9: NSX Security, the Money Maker
- IOChain Gang NSX uses a set of IOChain slots to handle how packets are processed at the kernel level. The first four are reserved for NSX and some slots are available to integrate third-party solutions into the process, giving NSX greater functionality.
- Master It Instead of having antivirus software installed internally on a VM, you want to insert a third-party antivirus solution into the IOChain. Which would be a valid slot number within the IOChain to accomplish this?
- Slot 1
- Slot 2
- Slot 4
- Slot 16
- Solution 3. Slot 4
Slots 4–12 are available to add Guest Introspection services from third-party vendors that have partnered with VMware to use their proprietary solutions to extend NSX functionality. The first slot is slot 0, the last slot is slot 15.
- Master It Instead of having antivirus software installed internally on a VM, you want to insert a third-party antivirus solution into the IOChain. Which would be a valid slot number within the IOChain to accomplish this?
- Matching on Access Lists NSX firewall rules can match on things like partial VM names, operating systems, security tags, data center, and so forth, making rules easy to understand and implement.
- Master It In addition to the ability of firewall rules matching on various object types and labels, NSX also supports the traditional IP 5-tuple categories. Which of the following is not a 5-tuple variable?
- Source IP address
- Source port
- Protocol
- Subnet mask
- Solution 4. Subnet mask
The 5-tuple values are source IP address, destination IP address, source port, destination port, and protocol.
- Master It In addition to the ability of firewall rules matching on various object types and labels, NSX also supports the traditional IP 5-tuple categories. Which of the following is not a 5-tuple variable?
- IP Discovery If you specify a vCenter object in your DFW rule, like a VM name, NSX needs a way to discover the IP address of that VM before the rule can be enforced, or the mapping must be done statically.
- Master It Which of the following is not a valid option for NSX to discover the IP address of a VM based on the name referenced in a DFW rule?
- DHCP snooping
- ARP snooping
- Gratuitous snooping
- SpoofGuard
- Solution 3. Gratuitous snooping
Gratuitous snooping is a method employed by parents of teenagers acting suspiciously, but there's no such thing in NSX.
- Master It Which of the following is not a valid option for NSX to discover the IP address of a VM based on the name referenced in a DFW rule?
Chapter 10: Service Composer and Third-Party Appliances
- Dynamic Inclusion Service Composer allows you to provision and assign security services within the virtual environment using security groups and to apply security policies. Group membership can be accomplished statically or dynamically.
- Master It When creating a new security group, you will see these listed as steps:
Step 1. Name and description
Step 2. Define dynamic membership
Step 3. Select objects to include
Step 4. Select objects to exclude
Step 5. Ready to complete
What parameter is not valid criteria to match on when dynamically assigning a member to a security group?
- Computer OS name
- VM name
- vNIC
- Computer name
- Security tag
- Solution 3. vNIC
It is possible to add a specific vNIC to a security group, but it wouldn't be done dynamically. It would be configured under the step to select objects to include.
- Master It When creating a new security group, you will see these listed as steps:
- Inbound vs. Outbound You create a firewall rule within a Service Composer security policy. The source is Any. The destination is Policy's Security Groups. VM-6 is a member of a security group with this policy applied.
- Master It When Policy's Security Groups is set as the destination in a Service Composer firewall rule, which traffic will be examined based on the security policy?
- Incoming traffic
- Outgoing traffic
- Solution 1. Incoming traffic
An easy way to approach this is to look at the rule from the perspective of the members within the security group. VM-6 belongs to the group listed as the destination. Traffic forwarded to this destination would therefore be incoming from VM-6's perspective. If this example had Policy's Security Groups specified as the source, VM-6 is sourcing traffic that would be examined as it travels outbound to the destination.
- Master It When Policy's Security Groups is set as the destination in a Service Composer firewall rule, which traffic will be examined based on the security policy?
- Default Policy Priority Service Composer can create a single policy that includes firewall rules, guest introspection services, and network introspection services. When multiple security policies are listed, priority is based on a weight value.
- Master It After creating a new security policy, it is added to the existing list of policies. By default, how will the order of the policies be affected?
- The new policy will have top priority
- The new policy will have the lowest priority
- The new policy is not published until a weight is entered
- Solution 1. The new policy will have top priority.
The higher the weight, the higher the priority. By default, the new policy will have top priority with a weight value that is automatically set by NSX at a value 1000 greater than any other existing policy. This default behavior places the policy at the top of the list. The weight value can be manually changed to customize the order.
- Master It After creating a new security policy, it is added to the existing list of policies. By default, how will the order of the policies be affected?
Chapter 11: vRealize Automation and REST APIs
- vRA Network Profile Network profiles contain specific network settings to use when provisioning VMs with vRealize Automation. The profiles contain IP address ranges, the gateway to use, the subnet mask to apply, and the ability to deploy NSX Edges if required.
- Master It You want to create a vRA catalog item that allows the user to provision a VM that will be placed on an existing network segment. Which network profile type should you use?
- External network profile
- Internal network profile
- NAT network profile
- Routed network profile
- Solution 1. External network profile
The external network profile is used when you want to add VMs to an existing segment.
- Master It You want to create a vRA catalog item that allows the user to provision a VM that will be placed on an existing network segment. Which network profile type should you use?
- Routed Network Profiles A routed network profile can create multiple subnet segments with connectivity through a Distributed Logical Router. The ranges (blocks) of the subnets are based on the subnet mask specified in the profile.
- Master It A routed network profile is configured with the following information:
Base IP: 172.16.1.0
Subnet mask: 255.255.0.0
Range subnet mask: 255.255.255.224
The first subnet assigned would be 172.16.1.0 255.255.255.224. What would be the address and mask of the second subnet?
- 172.16.2.0 255.255.255.224
- 172.16.2.0 255.255.255.255
- 172.16.1.32 255.255.255.224
- 172.16.1.8 255.255.255.224
- Solution 3. 172.16.1.32 255.255.255.224
The base IP 172.16.1.0 and subnet mask 255.255.255.0 determine the entire range of addresses that can be used for the deployment. You read this as, “All subnets created from this profile will start with 172.16.1.x”
The range subnet mask indicates how to subdivide this 172.16.1.x range. Since the last octet of the mask is 224, we can use a shortcut to avoid binary hell and take 256 minus 224, resulting in blocks of 32 in the last octet. All of the created networks would have the mask of 255.255.255.224 and the first four blocks would look like this:
172.16.1.0
172.16.1.32
172.16.1.64
172.16.1.96
- Master It A routed network profile is configured with the following information:
- REST APIs REST APIs are used to allow different applications to easily communicate with one another by presenting a software interface that other applications can essentially plug into. This obviates the need for companies to have to realign code on both sides to provide inter-application communication. It also means that the tasks we complete using a GUI can be turned into code or automated as a script.
- Master It The NSX API requires that a client connecting to it must be authenticated and the messages secured through encryption. What port is required to accomplish this?
- 80
- 8080
- 443
- 224
- Solution 3. 443
Specifically, it uses TCP port 443, the standard for SSL connections.
- Master It The NSX API requires that a client connecting to it must be authenticated and the messages secured through encryption. What port is required to accomplish this?
