So it's 2 A.M. on a Tuesday, you're the SCEP administrator on call, and you've just been woken up for an alert for a malware outbreak. What do you do? This recipe will show you where to go in the SCCM console to review the alert, as well as provide some guidance on what actions to take.
For the example outlined in this recipe, we will be responding to a situation where malware has been detected on a few PCs in the All Systems collection, which has an alert for malware detection assigned to it, and the number of PCs with the malware in question was great enough to trigger the malware outbreak alert as well.
For this recipe, you will need to utilize an account that has at least the SCEP administrator role assignment attached to it.
Follow these steps:
- Log into your SCCM CAS server and launch your SCCM 2012 management console.
- Navigate to
Monitoring|Overview|Alerts. - Any alerts that have been recently triggered will be marked with the red X icon and have an alert state of Active.
- Locate and select the alert labeled Malware detection for collection: All Systems. At the bottom of the UI, click on the Machines tab to see list of PCs that generated this alert, as shown in the following screenshot:
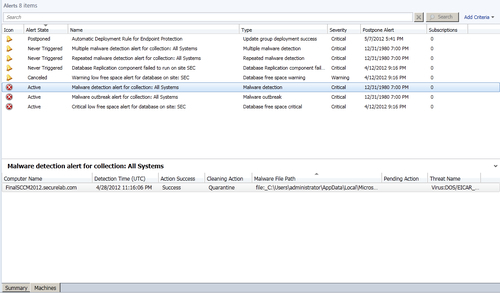
- Pay special attention to the columns labeled Action Success and Pending Action. This information will inform you of whether or not SCEP was successful in zapping the malware or if there are any additional steps, such as reboot, left outstanding for the malware to be fully removed.
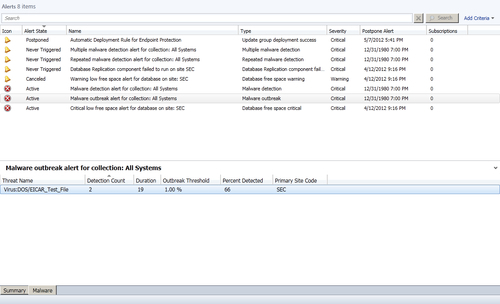
- Next, find the alert labeled Malware outbreak alert for a collection: All Systems and click on the Malware tab to see a list of the malware threats that have been detected on multiple computers, as shown in the following screenshot:
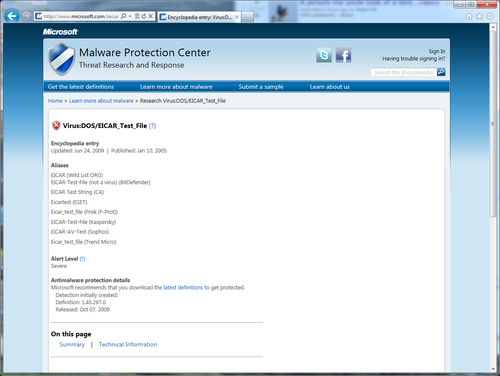
- It's a best practice to search for this malware by name against the Microsoft Malware Encyclopedia: http://www.microsoft.com/security/portal/. Look for the Antimalware protection details section at the bottom of the page. Here, you will find the first version of the SCEP definition file that protects against this threat. This is vitally important. If this is a very recently discovered piece of malware and some SCEP clients are behind in their definitions, then you may be in a situation where either there are more infected clients on your network than you know because it's going undetected, or clients with old definitions may soon contract this malware. In either case, your goal should be to get all your PCs up-to-date with a definition that covers this malware as fast as possible. Refer to the following screenshot:
- The actions you can take on the Alerts page are somewhat limited. You can add comments to an alert, which could be used to inform other SCEP administrators that you are looking into the situation. You can also postpone the alert; this could be useful if you're fighting off an outbreak and simply wish to stop the deluge of e-mail alerts. It's important to note, that postponing an alert will still allow the malware event to be added to your reporting data, it simply stops an e-mail subscription rule from executing.
SCEP alerts are a vital tool for SCEP administrators to respond quickly to malware events. In SCCM 2012, Microsoft created something called the High Speed Data Channel to facilitate a five minute or less SLA for malware detections. This means that within five minutes or less after a piece of malware is first detected by a SCEP client, the event data for this detection is available within the SCCM console. If the computer in question is a member of a collection that has a SCEP alert assigned to it and an alert subscription has been created, an e-mail will be generated and delivered to your inbox.
As a best practice, it makes sense to have malware alerts assigned to the All Systems collection, as you probably want to know about malware that is detected anywhere on your network. However, if you work for a very large organization with global operations, you may want to break your alerts up into regions. This can be done by assigning alerts to specific collections made up of a given region's PCs, rather than All Systems. Either approach is valid, but it's not recommended to do both as this will create redundant alerts for the same event, which can be very confusing at 2 A.M.
