Firewall Rules
Firewalls filter traffic using rules or filters. All firewalls, of whatever type—static packet filtering, stateful inspection, application proxy, circuit proxy, or content filtering—use rules to filter traffic. Rules are instructions that evaluate and take action on traffic traversing the network.
Firewall rules are used to control what traffic enters or leaves a secured network area. Depending on where the firewall is positioned, this mechanism can protect the private network from the public Internet or filter traffic between internal subnets or departments. The security administrator or the dedicated firewall administrator configures firewall rules in accordance with the organization’s security policy.
Generally, two main philosophies or security stances govern the use of rules: default deny or default allow. Default deny is also known as deny by default or deny all. Default allow is also known as allow by default or allow all. These two rules define the foundation for rules governing traffic crossing the firewall.
A default-deny stance assumes that all traffic is potentially malicious—or at least unwanted or unauthorized. Thus, everything is prohibited by default. Then, as benign, desired, and authorized traffic is identified, an exception rule grants it access to the network. This is known as deny by default/allow by exception. This method of rule creation allows security administrators to focus on what is wanted or needed, rather than watching out for all possible forms of unwanted or malicious activity. This is the whitelist-like action in a firewall whereby only those exceptions you define are allowed through.
A default-allow stance assumes that most traffic is benign. Thus, everything is allowed by default. Then, as malicious, unwanted, or unauthorized traffic is identified, an exception rule blocks it. This is known as allow by default/deny by exception. This method of rule creation forces the security administrator to be on constant watch for new and different forms of unwanted, unauthorized, and malicious activity. This is the blacklist-like action in a firewall, whereby everything is permitted with a few noted exceptions.
Most security experts agree that deny by default/allow by exception is the more secure stance to adopt. This stance automatically prevents most malicious communications by default, while the opposite allow-by-default stance allows most malicious communications by default. In most situations, fewer exceptions are required for a default-deny solution than for a default-allow system.
Most firewalls, both hardware and software varieties, usually come preconfigured with rules above and beyond the default rule. Firewalls are normally factory-configured in a deny-by-default stance with some common exception rules thrown in for end user/customer convenience (FIGURE 8-1). Often, these rules allow the most common forms of communication to occur across a new firewall without requiring you to configure the firewall fully upon initial installation. Some of the more common factory default rules allow for web, email, instant messaging, and file transfer through common Internet services on default ports.
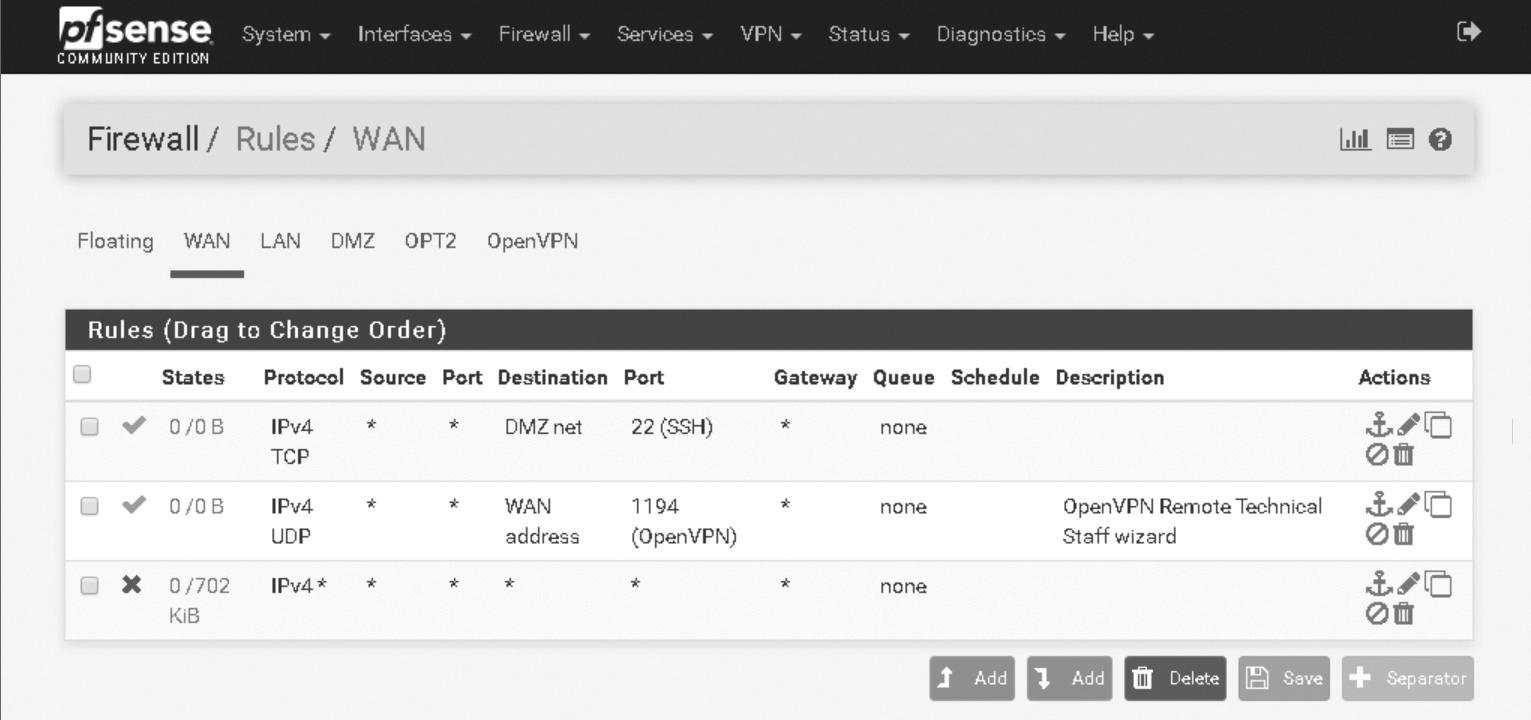
FIGURE 8-1 pfSense’s default rule configuration interface, showing a default deny as the last rule.
© pfSense
Although this can be a convenience, it is never in your best interest to rely upon a third party’s assumptions about your environment or guesses as to what types of traffic you do or do not want to cross your firewalled boundaries. Always take the time to review any factory-installed rules before deploying the firewall in the production environment. Delete or disable any rule that you do not need or want. With regard to any rules that you do want or need, you should double-check to make sure the rules are in line with your security policy. If you need rules that are not present by default, add each carefully and double-check your work as you go.
Your organization will need to decide which firewall rules to define; this is an essential part of its security policy. If the appropriate sections of the organization’s security policy related to firewalls do not predefine which rules to implement on a new firewall, perform the following procedure:
- Inventory all essential business processes and communications that will cross the firewall/checkpoint.
- Determine the protocols, ports, and Internet Protocol (IP) addresses of valid traffic for both internal and external hosts.
- Write out the rules or use a firewall rule designer/simulator.
- Test the rules in a safe, nonproduction environment.
- Obtain written approval for the rule sets from a change approval board or administration.
- Document the rules into a security policy procedure amendment and submit the amendment to the security policy management team or administrator for inclusion in the official document.
Ultimately, this is the basic process for creating any new element of security. The goal is to have a written security policy for every security component. If there is no current policy or procedure defining the steps to take for the deployment of a new security element, then you must write, test, and get approval for a new policy or procedure. Once a procedure exists, use it to judge successful deployment.
The exact rules to add to a new firewall depend upon the business processes that are unique to every organization. However, some common types of rules are found on most firewalls. These include:
- Access to insecure Internet websites (HTTP)
- Access to secure Internet websites (HTTP over SSL or TLS)
- Access to other Internet website protocols (SQL, Java, and so on)
- Inbound Internet email
- Outbound Internet email
If other Internet services are essential to a business task, rules allowing or enabling such communications would be needed. Try to keep the number of rules to a minimum. Grant access only to traffic that is essential. Each rule added to a firewall increases its attack surface—and therefore its security vulnerability.
Inbound and Outbound Communications
Keep in mind that most network communications are two-way transactions, exchanges, or sessions. Often, an internal client makes an initiation request to an external server. The server responds and sets up a communication channel, often called a virtual circuit (at the Transport Layer based on TCP) or, more generically, a session. Traffic can traverse the session in either direction. Thus, most rules should allow inbound responses to initial outbound requests.
Depending upon the firewall, a single rule can sometimes define both the outbound and inbound communication parameters. Other firewalls need two separate rules: one rule for the initial outbound request and a second rule to handle the resultant inbound response. In either case, each desired session-based communication service must be supported or allowed through proper two-way rule construction.
In addition to rules that allow traffic based on internal user initiation, consider rules that manage inbound communications for externally initiated communications. When a firewall is to allow an external host to request access to internal resources, you need to create an inbound rule or ingress filter. Define rules that allow inbound initiations only if external entities need to access services and resources hosted internally.
Otherwise, allow the firewall to serve its primary purpose and prevent outsiders from gaining easy access to internal systems. Most firewalls deny by default all access to internal resources from external entities. This is done either by ignoring all requests received on a specific interface (such as on dual-homed or triple-homed firewalls) or by having a specific rule (or a set of rules) that filter out all traffic originating from noninternal IP addresses.
Access Control Lists
A firewall rule can also be called a filter or an access control list (ACL). These terms are often used interchangeably in documentation, in books, and in the firewall’s configuration or management interfaces. Don’t be confused by this. A rule is a written expression of an item of concern (protocol, port, service, application, user, IP address) and one or more actions to take when the item of concern appears in traffic. A filter is the same thing as a rule, but the point or purpose of using a filter is to emphasize the intention to block or deny unwanted items of concern. Thus, the use of the term ACL emphasizes the intention to grant or deny traffic on an access control/authentication basis. An ACL focuses on controlling a specific user or client’s access to a protocol or port.
Rules allow traffic to pass unhindered or block or deny traffic to prevent it from reaching its intended destination. A rule can also include a logging element, so the traffic is logged whether allowed or denied.
Technical TIP
Use your firewall to ensure that only properly originated communications are authorized. Unless you are running internal services (such as a web server), external entities should never be able to initiate a connection.
Technical TIP
Most session-based communications will use a well-known default port for the destination port where the service or resource resides. These often use a randomly selected higher order port (any port above 1023) for the client source port. Most firewalls, especially those capable of stateful inspection, will automatically handle and adjust for the random source port when establishing a session. If this is not the case with a specific firewall, you may need to create a custom rule or consider replacing the firewall with a better product.
