What Are You Trying to Protect?
In terms of security, the things you want to protect are known as assets. An asset is anything used to conduct business. Any object, computer, program, piece of data, or other logical or physical component that employees need to accomplish a task is an asset.
Assets do not have to be expensive, complicated, or large. In fact, many assets are relatively inexpensive, commonplace, and variable in size. But no matter the characteristics, an asset needs protection. When assets are unavailable for whatever reason, employees cannot complete their work.
For most organizations, whether small or large, the assets of highest concern include business and personal data. If this information is lost, damaged, or stolen, serious complications result. Businesses can fail. Individuals can lose money. Identities can be stolen. Lives can be ruined.
What causes these problems? What violates network security? The answer includes accidents, ignorance, and hackers. Accidents happen, including hardware failures and natural disasters. Poor training equals ignorance. Workers with the best of intentions can damage systems if they do not know proper procedures or if they lack necessary skills. Overworked and rushed personnel overlook issues that can result in asset compromise or loss. Malicious hackers can launch attacks and exploits against the network, seeking to gain access or simply to cause damage.
Seven Domains of a Typical IT Infrastructure
No aspect of an IT infrastructure is without risk, nor is it immune to the scrutiny of a hacker. Risk is the likelihood that a threat will take advantage of a vulnerability. When designing and implementing network security, you need to analyze every one of the seven domains of a typical IT infrastructure (FIGURE 1-2) for potential vulnerabilities and weaknesses. Security measures must be detailed, focused, and exhaustive. You must consider every possible avenue of attack; assess risk; and if the risk is sufficient, apply a countermeasure. Failing to do so will leave an open pathway for a hacker. A hacker needs only one crack in your defenses to begin chipping away at the security of the entire network.
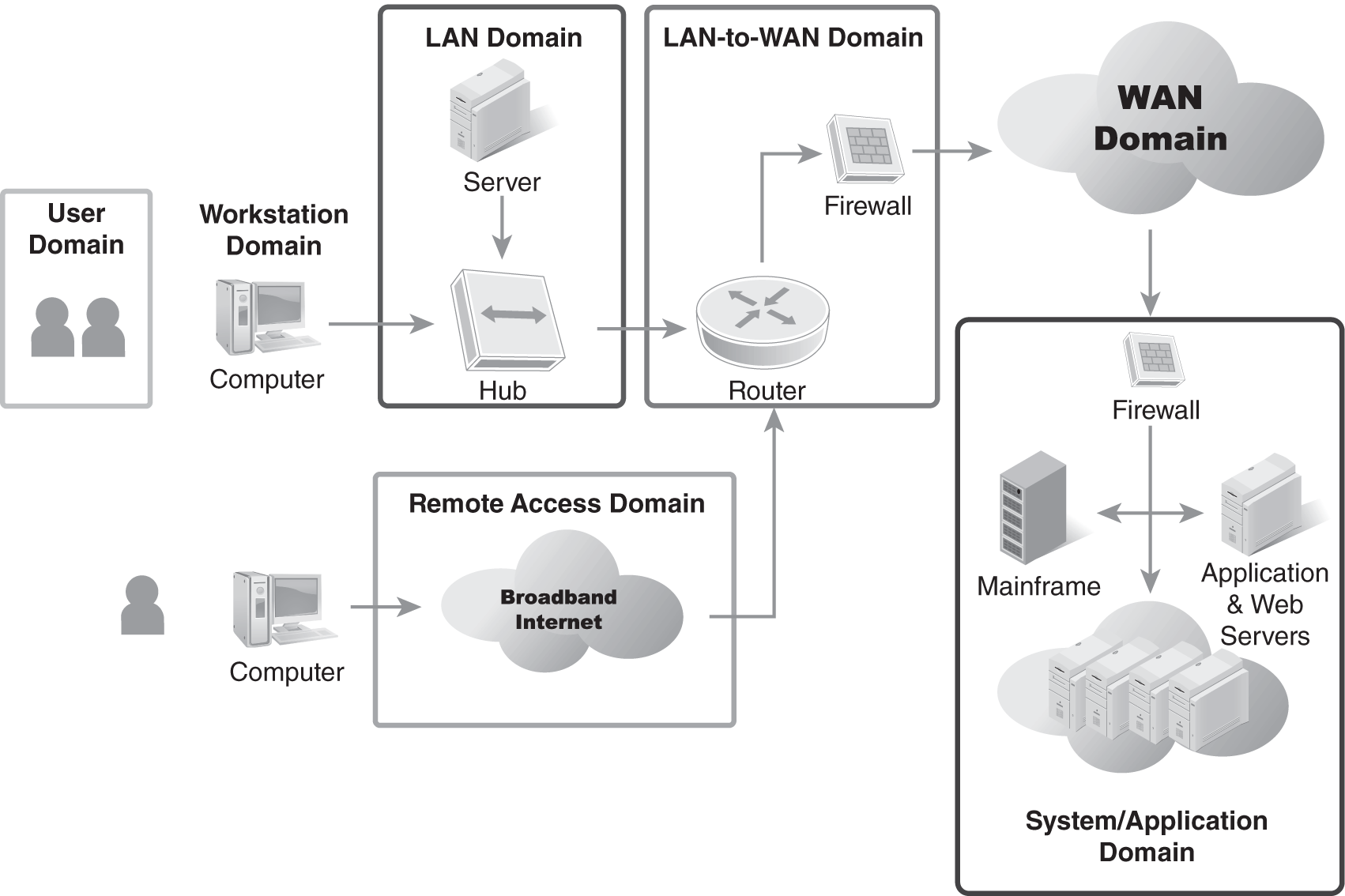
FIGURE 1-2 The seven domains of a typical IT infrastructure.
Each of the seven domains of a typical IT infrastructure has unique aspects that need security improvements. The following sections describe important foundational network security issues related to the seven domains.
User Domain
This domain refers to actual users, whether they are employees, consultants, contractors, or other third-party users. Any user who accesses and uses the organization’s IT infrastructure must review and sign an acceptable use policy (AUP) prior to being granted access to the organization’s IT resources and infrastructure. This domain should also focus on training, strong authentication, granular authorization, and detailed accounting. Additionally, many of the protections added to other domains provide additional protections for and against the User Domain.
Social engineering is a hacker attack against people. This type of attack attempts to fool people through clever wording, lying, misdirection, relationship manipulation, fear, psychological tricks, and confidence games. The results of social engineering attacks can include users giving away private information or performing actions on a computer that cause a reduction in network security.
Workstation Domain
This domain refers to the end user’s desktop devices, such as a desktop computer, laptop, Voice over Internet Protocol (VoIP) telephone, or other endpoint device. Workstation devices typically require security countermeasures such as antivirus, anti-spyware, and vulnerability software patch management to maintain the integrity of the device.
The workstation, client, or standalone home system can be a target. These types of hosts are often less secure than local area network servers. This is not on purpose, because most security focuses on core components of the infrastructure, rather than those seemingly on the periphery. Many times, the security measures on a workstation are old, out-of-date, or improperly installed and configured. System hardening, communication protection, and positioning of work stations are critical to security.
LAN Domain
This domain refers to the physical and logical local area network (LAN) technologies (i.e., the wired or wireless topology built from devices and communication protocols) used to support workstation connectivity to the organization’s network infrastructure. Protocols, addressing, topology, and communication encryption provide security for this domain.
The private LAN, from home offices to large corporations, is a common target for attack. A LAN often consists of dozens to thousands of hosts, which can make securing every host difficult. Once a hacker gains access to one system on the network, the rest of the LAN is vulnerable to attack. The compromise of a single host can lead to the compromise of the entire infrastructure.
LAN-to-WAN Domain
This domain refers to the organization’s internetworking and interconnectivity point between the LAN and the WAN network infrastructures. Routers, firewalls, switches, proxies, demilitarized zones (DMZs), intrusion detection systems (IDSs), intrusion prevention systems (IPSs), and communication encryption are commonly used as security monitoring devices in this domain.
The wide area network (WAN) connections between LAN locations, especially those controlled by third-party entities, are targets. Transition interfaces between a private LAN and a WAN connection can be potential weak points. If a compromise is successful against a WAN connection, the malicious traffic inbound across the WAN/LAN interface is unlikely to be filtered.
Remote Access Domain
This domain refers to the authorized and authenticated remote access procedures for users to remotely access the organization’s IT infrastructure, systems, and data. Remote access is always a popular target of hackers, as it removes the need for the hacker to be physically present to access and attack the LAN. Hackers anywhere in the world with an Internet or telephone connection can still reach out to attack any seemingly isolated target. Remote access is an invitation to hackers to try to breach your defenses.
Remote access solutions typically involve encrypted remote browser access or encrypted virtual private network (VPN) tunnels for secure remote communications.
WAN Domain
Organizations with remote locations require a WAN for interconnection. Organizations typically outsource WAN connectivity from service providers for end-to-end connectivity and bandwidth.
The WAN Domain includes networks, such as those using Asynchronous Transfer Mode (ATM) or Frame Relay, owned by a telco or a carrier network company that leases access to corporations. Often, the privacy of these WAN connections is electronic isolation rather than encryption. Hackers focusing on a specific target may attempt to breach the electronic isolation of the carrier network, rather than focusing on the endpoint LANs. This domain typically includes routers, circuits, switches, firewalls, and equivalent gear at remote locations, sometimes under a managed service offering by the service provider. Protocol selection, addressing schemes, and communication encryption are elements of securing this domain.
System/Application Domain
This domain refers to the hardware, operating system software, database software, client/server applications, and data that are typically housed in the organization’s data center and/or computer rooms. Collections of servers hosting applications, virtualized systems, or databases are valuable targets. Sometimes the data hosted is the target. Sometimes the computing power of the servers is the resource the hacker wishes to seize. Network design, authentication, authorization, accounting, and node security are important security concerns for this domain.
Network administrators need to recognize that the potential for compromised security exists throughout an organization, which leads to the need for adequate network security. Starting from the knowledge that risk exists and threats loom, network security administrators can design and implement appropriate countermeasures and safeguards. The first step is to recognize that the potential for compromised security exists throughout an organization. The next step is to comprehend the goals of network security.
