DMZ, Extranet, and Intranet VPN Solutions
A demilitarized zone (DMZ) is a physical or logical subnetwork that contains and exposes an organization’s external services to a larger untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization’s LAN. An external attacker can gain access to equipment in the DMZ, but not parts of the network behind the firewall.
For example, public-facing servers that need accessibility from the Internet are placed in the DMZ. This could include web servers, email servers, File Transfer Protocol (FTP) servers, and more. Organizations often place VPN servers for remote access in the DMZ.
In a network, the hosts most vulnerable to attack are those that provide services such as email, web, and FTP servers to users outside of the local area network. Because of the increased potential of compromise, these hosts are placed into a subnetwork to protect the rest of the network if an intruder were to succeed.
Hosts in the DMZ have limited connectivity to specific hosts in the internal network, but connectivity to the external network is allowed. For example, a web server in the DMZ may be able to connect to a database server in the internal network, but not to any other hosts in the internal network. This allows hosts in the DMZ to provide services to both the internal and external network, while an intervening firewall controls the traffic between the DMZ servers and the internal network clients.
Intranet VPNs
An intranet is an internal network. Although users within the intranet can access the Internet using different resources such as a proxy server, access to the internal network is severely restricted. Because traffic in the intranet is primarily from internal clients, the intranet is a trusted zone and needs fewer security measures.
An intranet VPN is a VPN that connects two or more internal networks. Earlier in this chapter, you learned about the concept of gateway-to-gateway VPNs. A gateway-to-gateway VPN provides connectivity between two locations, such as a main office and a branch office. This is also known as an intranet VPN.
It is important to realize that even though the VPN may be called an intranet VPN, it will still traverse a wide area network (WAN) link. Most organizations will rent access to this WAN link; it is very rare that a company has exclusive access to it. In other words, the WAN link will be accessible to users outside the organization. The same level of security measures used in a DMZ VPN should also secure an intranet VPN.
Extranet VPNs
Extranet VPNs link customers, suppliers, partners, or communities of interest to a corporate intranet over a shared infrastructure. For example, an organization may hire a consulting company to evaluate different processes within the organization and provide recommendations for improvement. The organization could create an extranet VPN to allow the consultants access to some internal resources.
Extranets are commonly configured to connect via the Internet, but can use leased lines or even dedicated connections. Extranets differ from intranets in that remote users outside of the enterprise are allowed access to the resources inside the network.
FIGURE 12-2 illustrates an extranet VPN topology. Using digital certificates, clients establish a secure tunnel over the Internet to the enterprise. A certification authority (CA) issues a digital certificate to each client for device authentication. The CA server checks the identity of remote users and then authorizes remote users to access information relevant to their functions.
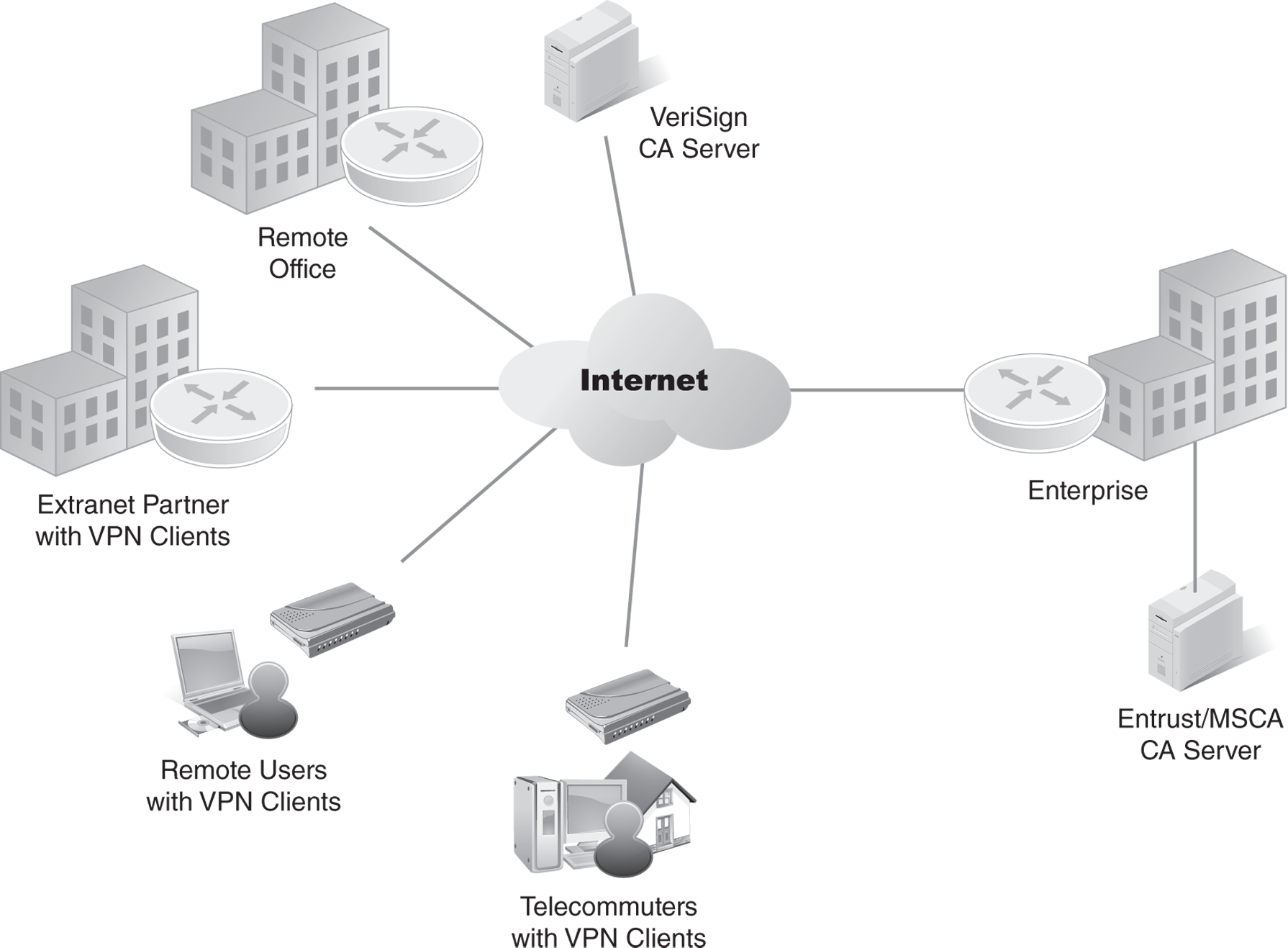
FIGURE 12-2 An extranet VPN topology.
