The Hacking Process
As much as cybersecurity professionals dislike the practice, hacking can be a fascinating process. Hackers’ activities often appear chaotic and random, at least when observed from the mainstream IT industry. Hackers do not have to follow any fixed procedures or recognize any established boundaries. Instead, they seek vulnerabilities on a selected target, using any and all means at their disposal. For them, chaos is both a methodology and a defense mechanism.
Generally, hacking falls into five main subgroups of events or activities referred to as phases. This categorization can represent hacking, but it does not actually control or prevent it. The five categories are reconnaissance, scanning, enumeration, attacking, and post-attack activities. (See FIGURE 2-2.) This order of phases occurs if an attack is successful. If an attack is not successful, the hacker can instead attempt a fallback position.
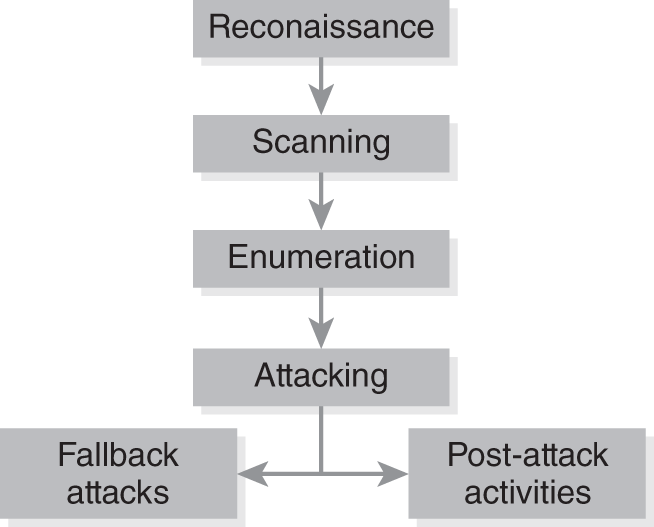
FIGURE 2-2 Five phases of hacking.
Fallback Attacks
Fallback attacks are the other options for mayhem a hacker can deploy after unsuccessful breach attempts against a target. Common alternatives to intrusion include DoS, eavesdropping, breaking and entering, social engineering, malicious code, session hijacking, man-in-the-middle attacks, wireless hacking, SQL injection, website attacks, and more.
Reconnaissance
Reconnaissance is the initiation of the process of hacking. Reconnaissance means the act of inspecting or exploring and can also be called footprinting, discovery, research, and information gathering. This phase is the first of three pre-attack phases in which hackers learn as much as possible about a target before attempting the first actual attacks. Reconnaissance consists of collecting data about the target from all possible sources online and offline. The hacker is careful to avoid alerting the target that it has probed the network for information.
Reconnaissance can include:
- Researching old versions of a target organization’s website at archive.org
- Examining search engine contents
- Reviewing the organization’s website
- Investigating the background of personnel
- Performing location mapping
- Reading job postings
- Checking insider information leak sites
- Looking at newspaper and magazine articles for mentions of the organization
- Perusing press releases
- Searching newsgroups, chat archives, blogs, and forums
- Auditing financial records or reviewing public filings
- Reviewing court cases and other public records
- Querying whois, domain registrations, and public IP assignments
- Eavesdropping on email and other conversations
- Visiting a physical location for the organization
These are just some of the possible reconnaissance activities a hacker can perform. Information gathering is limited only by the time, resources, and imagination of the hacker. Once the hacker has built and organized a reasonable portfolio of information about the target, the next step is scanning.
Scanning
Scanning is the activity of using various tools to confirm information learned during reconnaissance and to discover new details. Scanning is aimed at discovering live and active systems. Scanning can include wardialing, wardriving, ping sweeps, and port scanning.
Wardialing is an older tactic that uses the telephone system to locate any active and answering modems. Using a modem and often a dialing program, a hacker’s computer automatically dials target phone numbers. The hacker obtains phone numbers during reconnaissance or by dialing all the numbers in an area code or prefix.
Wardriving, a term derived from wardialing, is the technique of using a wireless detector (sniffer) to locate wireless networks. Hackers used to drive through cities or neighborhoods with laptop computers to discover wireless networks. Today, driving is not necessary and smartphones detect wireless networks automatically.
Ping sweeps are used to discover systems over network connections that will respond to Internet Control Messaging Protocol (ICMP) echo requests. Hackers commonly use ICMP for network health and testing. The ping command typed from the command line of a computer or network mapping utility sends ICMP echo requests to all possible recipients within an Internet Protocol (IP) address range or subnet. ICMP echo responses from systems indicate their IP addresses and that they are up and running.
Hackers perform port scanning by sending various constructions of Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) packets to ports (FIGURE 2-3). If the hacker does not know the computer system exists, then a port scan can determine the existence of a system at a specific IP address, as well as whether a port is open, closed, or filtered. A TCP port is known to be open if a full TCP three-way handshake can establish a virtual circuit. A UDP port cannot be confirmed as open because the default response from an open port is always silence.
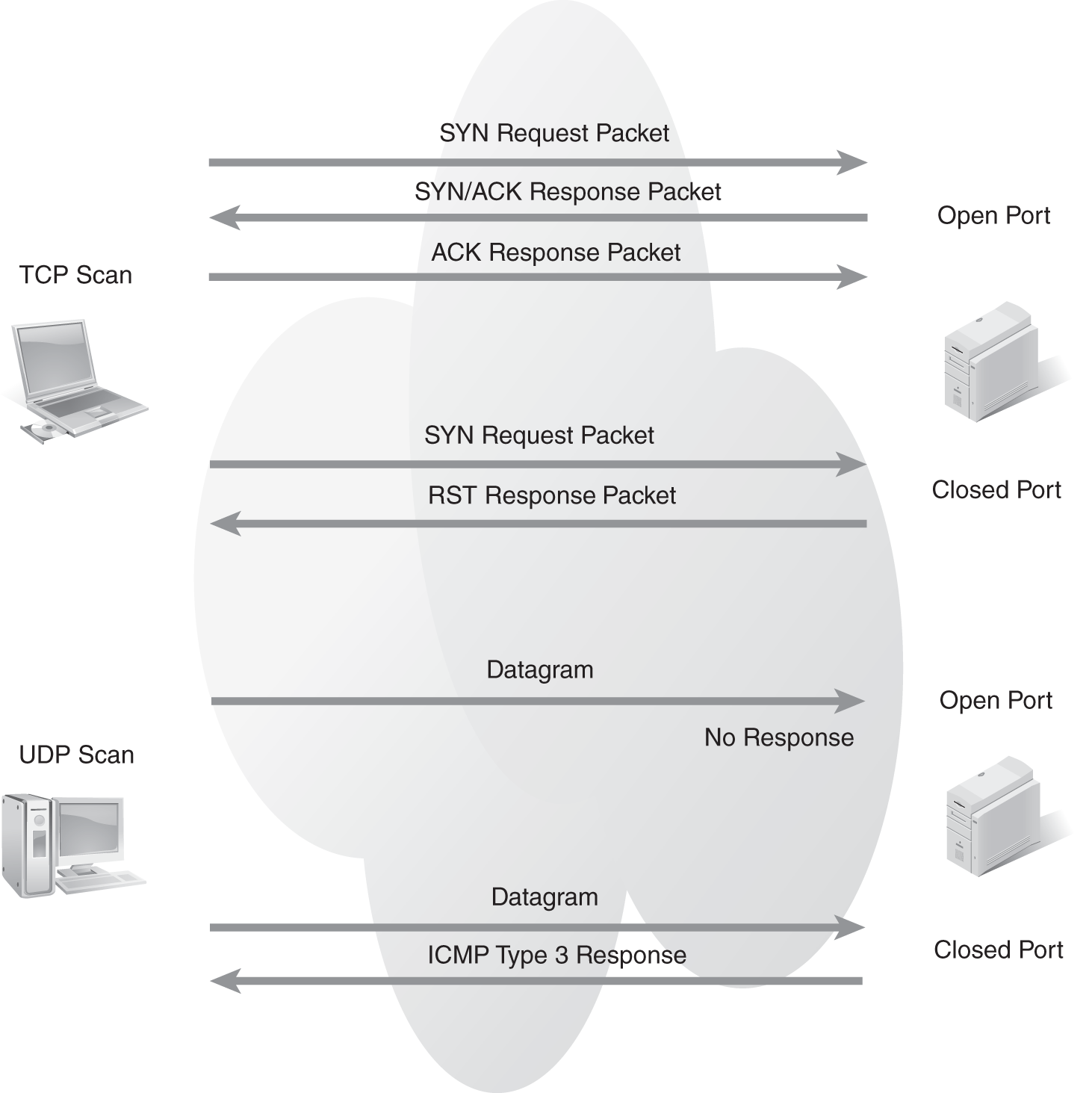
FIGURE 2-3 Basic TCP and UDP port scanning.
Technical TIP
Ports exist at the Transport Layer (Layer 4) of the Open Systems Interconnection (OSI) Reference Model. TCP and UDP use ports to support multiple simultaneous communications, connections, or sessions over a single Layer 3 (Network Layer) IP address. There are 65,535 ports, but most systems can only support a few hundred concurrent transactions.
A port is open if an active service is ready to process data through the specific port. A port is closed if no service is associated with that specific port.
When communications elicit error messages or abnormal responses from a port, a firewall can filter out these responses. This will result in a port being visible for valid and normal communications. A firewall can block any attempt to elicit errors or abnormal responses.
During scanning, often referred to as probing, a hacker sends packets to elicit responses. When a hacker performs scanning, it is detectable. Reconnaissance is generally silent, secretive, and unobtrusive. You are also unlikely to detect scanning to verify individual data items, such as a single open or closed port. But when hackers scan to discover all possible IP addresses in use and all possible open and closed ports, it is noticeable to network administrators and usually captured in system logs. Reconnaissance activity might or might not draw attention, but scanning—if not conducted carefully and on single ports, as opposed to all ports at once in a port sweep or blast—will be hard to ignore.
Hackers perform scanning until they discover one or more targets. Because scanning uncovers only a system and the open ports, hackers learn very little about the targets. Hackers stop scanning and move to the enumeration phase, the next step toward attacking, whenever they have enough information or their scans fail to reveal new information, based on the purpose of their attacks. Keep in mind that an attacker needs only a single vulnerability to gain access to a system or network. Once hackers can access a machine, moving on toward attacking it quickly is the most common escalation.
Enumeration
Enumeration is the discovery and listing of potential attack targets. Enumeration is the hackers’ process of discovering sufficient details about a potential target to learn whether a vulnerability exists that they can successfully attack. Enumeration often starts with operating system (OS) identification, followed by application identification, then extraction of information from discovered services.
Hackers perform OS identification by probing an open and closed port of a target. The responses from these ports identify the OS. This identification is possible because of the idiosyncrasies of different programmers writing interoperable code. Each OS uses a different group of programmers to write the network protocol stack. Even though the resultant protocol stack may be in compliance with IEEE standards, the defaults and reactions of the stack often differ from one OS to the next. These differences are known and maintained in a small database, which is coded into most network scanning and probing tools, such as nmap.
Each open port has a service running behind it. Banner grabbing is the activity of probing those services to obtain information (FIGURE 2-4). Once a connection has begun, a service may send an announcement of connection or communication confirmation. This announcement is called the banner. The banner may contain additional details, such as the product name and version number of the service.
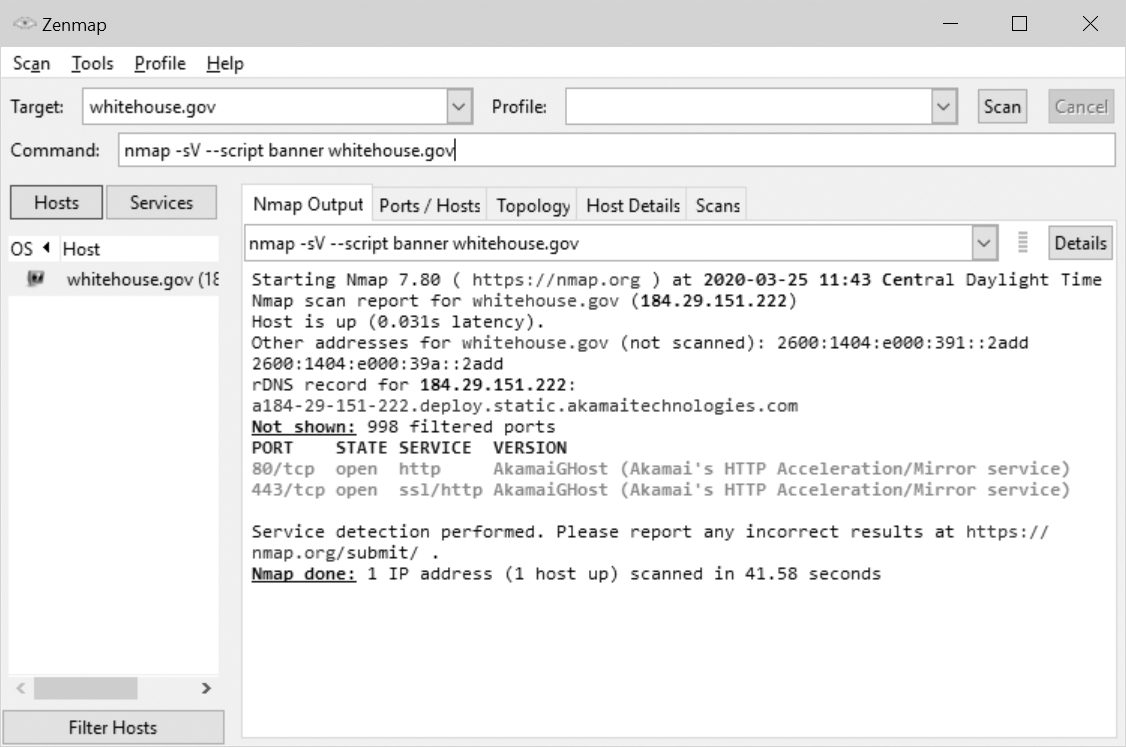
FIGURE 2-4 A banner grabbed from a web server.
Courtesy of Zenmap.
The information in the banner can be used by a hacker for reconnaissance purposes—to gain the intelligence needed to form the basis of an attack. One low-cost method of protection is to change the banner to mislead hackers into using the wrong exploits against the server, but still allow the service on the given port to perform its duties. In some cases, banners are not actually used, so these may be greatly shortened; in other cases, advanced features that are not used may be abandoned in a trade-off that results in better security.
Once hackers have identified the service, they can request additional information. The information request may be ignored and is secure, as no response is sent. But if insecure, the service may return volumes of data to the hacker. Depending upon the service and the queries the hacker performs, the extracted information could include system name, network name, user names, group names, share names, security settings, resources available, access control settings, and more.
Enumeration provides the hacker with identified, potential attack points. After reviewing vulnerability databases, such as MITRE (http://cve.mitre.org) or National Institute of Standards and Technology (NIST) (https://nvd.nist.gov), hackers evaluate the potential vulnerabilities. Once the hacker selects an attack target, they collect exploit tools and wage the attack.
One aspect that characterizes modern attacks is the amount of time that passes between the reconnaissance phase and the attack phase. In the past, a matter of minutes may have separated the two, but the more modern attack might take weeks, months, or longer to gather information before the attack is unleashed. Such an attack, the highly targeted advanced persistent threat (APT), will be discussed in more depth later in this chapter.
Attacking
Attacking is the fourth phase of hacking. Although this seems to be the phase that attracts most of the hype about hackers, in fact, it is the briefest phase of the overall hacking process. A successful attack, based on solid research and preparation, can take just seconds.
If an initial attack fails, hackers can modify their exploits, tune their payloads, adjust their shell code, reset their vectors, and relaunch the attack. Once hackers figure out that an assumed vulnerability does not exist or has been secured, they return to their enumeration results to select a new point of assault. Again, think of termites: If they can’t get into the house structure through a doorjamb, they will just as eagerly try to enter through a windowsill. Both pests are relentless.
Repeated attacks will lead either to an eventual successful breach or to the frustration of a hacker due to successful defense by the target. If successful, the attacker moves on to post-attack activities. If unsuccessful, the attacker can elect to move to alternative fallback attacks.
Post-Attack Activities
In a successful attack, the hacker usually has breached the target’s security to gain some level of logical access. This could be the credentials of a standard user account or access to a command shell accessed through a buffer overflow exploit. In any case, some common post-attack activities usually take place. These include privilege escalation, depositing additional hacker tools, pilfering data, creating a re-entry point (backdoor) and removing evidence of the hack.
Privilege escalation is attempting to gain higher levels of access or privilege from the target. This can occur using a keystroke logger, known OS exploits to steal administrator or system access, manipulation of scheduled tasks, social engineering, Trojan horses, remote control programs, and other mechanisms. The result is that the hacker gains access to a user account or a command shell that operates as an administrator, root, or the system itself. With privileged access, the remaining post-attack activities are much easier.
Depositing additional hacker tools gives the hacker more power over the compromised system. Tools may enable additional abilities unavailable through the current connection method. Tools may assist in pilfering data, removing evidence of the hack, or maintaining or regaining access in the future. To regain access, hackers often create new accounts on the system. Scanning for new accounts is an easy way to identify this technique.
Pilfering data is just that: scouring storage devices looking for files of interest. Hackers look for anything they can turn into cash quickly. They also look for things that would be fun, interesting, or damaging to disclose to the public. They look for items they can use to blackmail or coerce users. And, of course, they are on the lookout for potentially valuable information for bartering or trading with other hackers or criminals. Dumping the user account database and password hashes is often a priority as well. Cracking the passwords of other users will help in accessing the system in the future.
Removing evidence of the compromise and subsequent activities is an important step for the hackers. Failing to cover their tracks could lead to apprehension and prosecution. Allowing the IT and security staff to discover the intrusion will lead only to heightened levels of security. Discovery makes future returns more difficult, if not impossible, depending on the hacker’s skill set.
Once the hacker performs evidence cleanup, the attacker can claim to have owned (or pwned, in leetspeak, hackers’ code language) a system. The hacker has demonstrated skills through the discovery, tracking, and penetration of a target. This is often the goal of a hacker: to successfully penetrate a target. However, such successes are not always easy, or common. If the attacks fail, the hacker may have fallback attack options.
