Hijack and Replay Attacks
A hijack attack occurs when a hacker uses a network sniffer to watch a communications session to learn its parameters. The hacker then disconnects one of the session’s hosts, impersonates the offline system, and begins to inject crafted packets into the communication stream. If successful, the hacker takes over the session of the offline host, while the other host is unaware of the switch.
Replay attacks are also known as playback attacks. A replay attack occurs when a hacker uses a network sniffer to capture network traffic, and then retransmits that traffic back on to the network at a later time. The goal of a replay attack is to gain interactive or session access to a system.
The traffic captured and retransmitted for a replay attack is authentication packets (FIGURE 2-7). In this type of attack, the hacker captures traffic between a client and server, and then later retransmits it against the same server as the original communication. Replay attacks often focus on authentication traffic in the hope that retransmitting the same packets that allowed the real user to log onto a system will grant the hacker the same access.
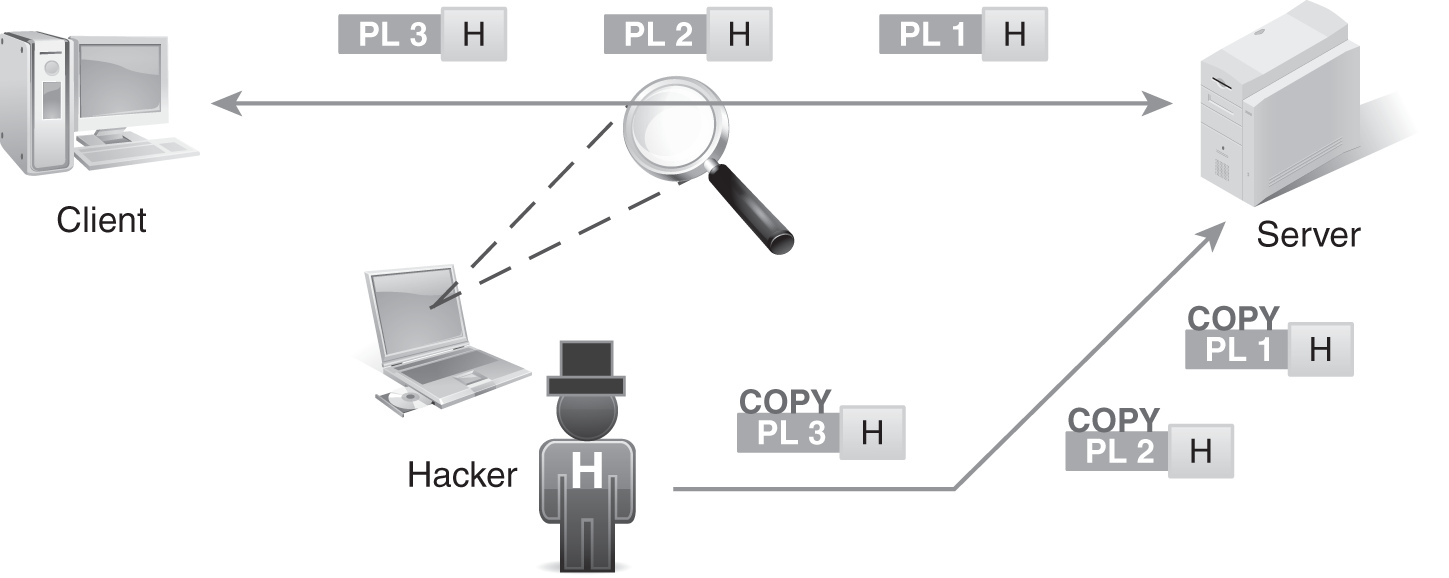
FIGURE 2-7 Replay attacks collect authentication packets, and then retransmit the packets at a later time.
Fortunately, you can thwart most replay attacks by using one of several common communication improvements. Many authentication transactions include a random challenge-response dialogue that cannot be replayed. This dialogue consists of one endpoint generating a random seed value sent to the other endpoint. The second endpoint uses a mutual secret known by both endpoints to compute a response using a one-way computation. The response returns to the original endpoint, where the response was predicted. If the received and predicted responses match, the user is authenticated.
Time stamps are another defense against replay attacks. Some authentication exchanges have encoded time details that are difficult to reproduce or modify without detection. Additionally, the use of one-time pad or session-based encryption can make replay attacks impossible.
