Examples of Network Infrastructures and Related Security Concerns
As you design a network, you need to evaluate every aspect in light of its security consequences. With limited budgets, personnel, and time, you must also minimize risk and maximize protection. Consider how each of the following network security aspects affects security for large corporations, small companies, and even home-based businesses.
Workgroups
A workgroup is a form of networking in which each computer is a peer or equal. Peers are equal in how much power or controlling authority any one system has over the other members of the same workgroup. All workgroup members are able to manage their own local resources and assets, but not those of any other workgroup member.
Workgroups are an excellent network design for very small environments, such as home family networks or very small companies. In most cases, a workgroup comprises fewer than 10 computers and rarely contains more than 20 computers. No single rule dictates the size of a workgroup. Instead, the administrative overhead of larger workgroups encourages network managers to move to a client/server configuration.
Workgroups do not have a central authority that controls or restricts network activity or resource access. Instead, each individual workgroup member makes the rules and restrictions over resources and assets. The security defined for one member does not apply to or affect any other computer in the workgroup.
FIGURE 3-18 shows a typical workgroup configuration. In this example, a switch interconnects the four desktop workgroup members, as well as an Internet connection device and a wireless access point (WAP). Additional clients can connect wirelessly via the access point or wired via a cable connecting to the switch.
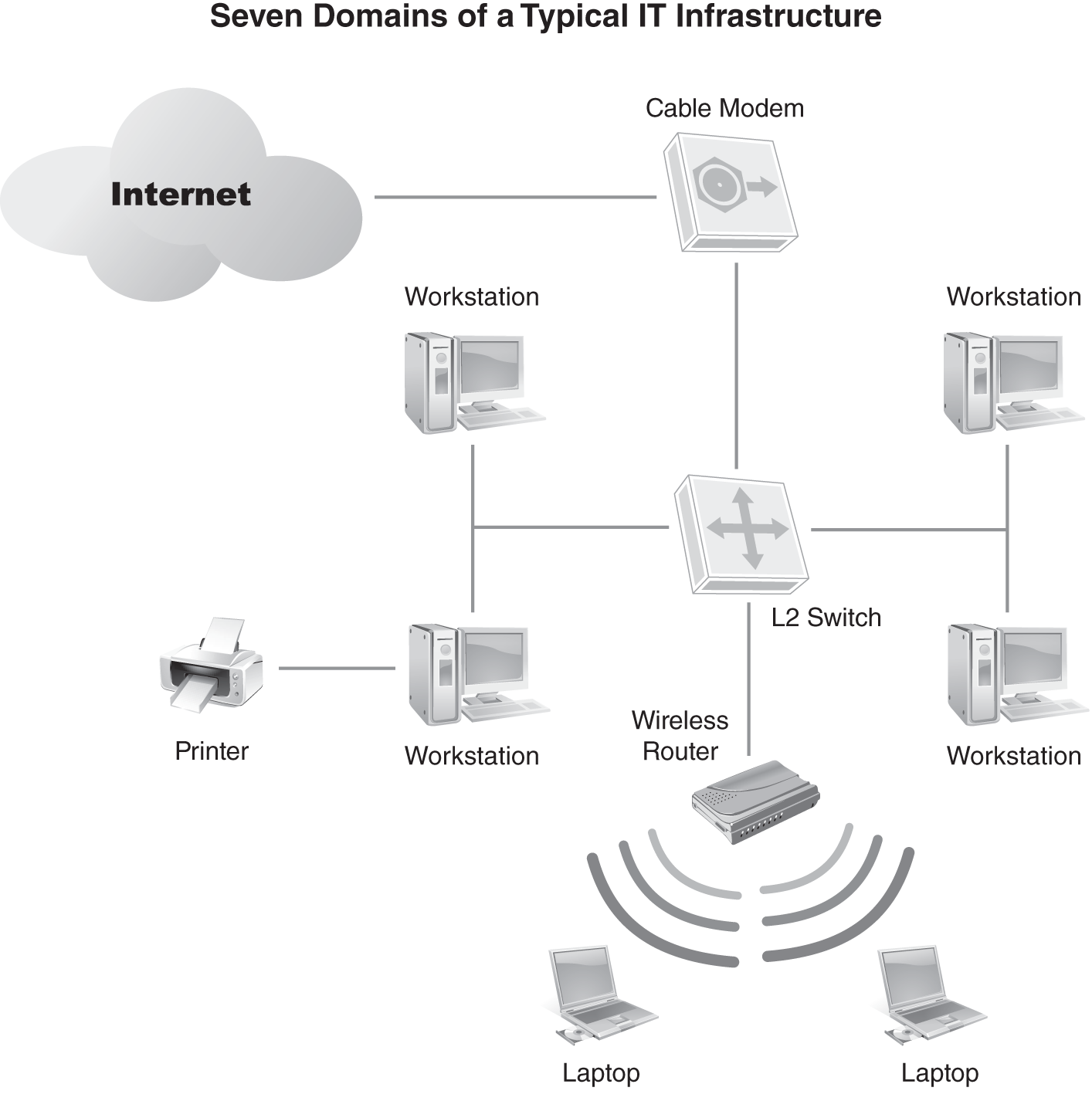
FIGURE 3-18 An example of a typical workgroup.
Due to system-by-system–based security, a worker or a workgroup member needs to have a user account defined for each of the other workgroup members to access resources on those systems. Each of these accounts is technically a unique user account, even if it is created by using the same characters for the username and password.
This results in either several unique user accounts with different names and different passwords or several unique user accounts with the same name and same password. In either case, security is poor. In the former case, the user must remember several sets of credentials. This often results in the user writing down the credentials. In the latter case, an intruder need compromise only one set of credentials.
This lack of a central authentication authority is both a strength and weakness of workgroups. This characteristic is a strength in that each user of each computer can make choices about sharing resources with others. However, this is also a weakness because of the inconsistent levels of access.
Workgroups are easy to create. Often, the default network configuration of operating systems is to be a member of a workgroup. A new workgroup is created by defining a unique name on a computer. Once one computer names the workgroup, it now exists. Other computers become members of the new workgroup just by using the same workgroup name. Because workgroups lack a central authority, anyone can join or leave a workgroup at any time. This includes unauthorized systems owned by rogue employees or external parties.
Most workgroups use only basic resource-share protections, fail to use encrypted protocols, and are lax on monitoring for intrusions or intrusion attempts. Although it is possible to impose some security on workgroups, usually each workgroup member is configured individually. Fortunately, because workgroups are small, this does not represent a significant amount of effort.
SOHO Networks
SOHO (small office/home office) is a popular term that describes smaller networks commonly found in small businesses, often deployed in someone’s home, garage, portable building, or leased office space. A SOHO environment can be a workgroup or a client/server network. Usually a SOHO network implies purposeful design with business and security in mind.
SOHO networks generally are more secure than a typical workgroup, usually because a manager or owner enforces network security. Security settings defined for each workgroup member are more likely to be consistent when the workgroup has a security administrator. Additionally, SOHO networks are more likely to employ security tools, such as antivirus software, firewalls, and auditing.
Client/Server Networks
A client/server network is a form of network where you designate some computers as servers and others as clients. Servers host resources shared with the network. Clients access resources and perform tasks. Users work from a client computer to interact with resources hosted by servers. In a client/server network, access is managed centrally from the servers. Thus, consistent security is easily imposed across all network members.
FIGURE 3-19 shows a possible basic layout of a client/server network. In this example, three servers host the resources, such as printers, Internet connectivity, and file storage shared with the network. Both wired and wireless clients are possible. Switches interconnect all nodes. Client/server networks are more likely to use hardware or appliance firewalls.
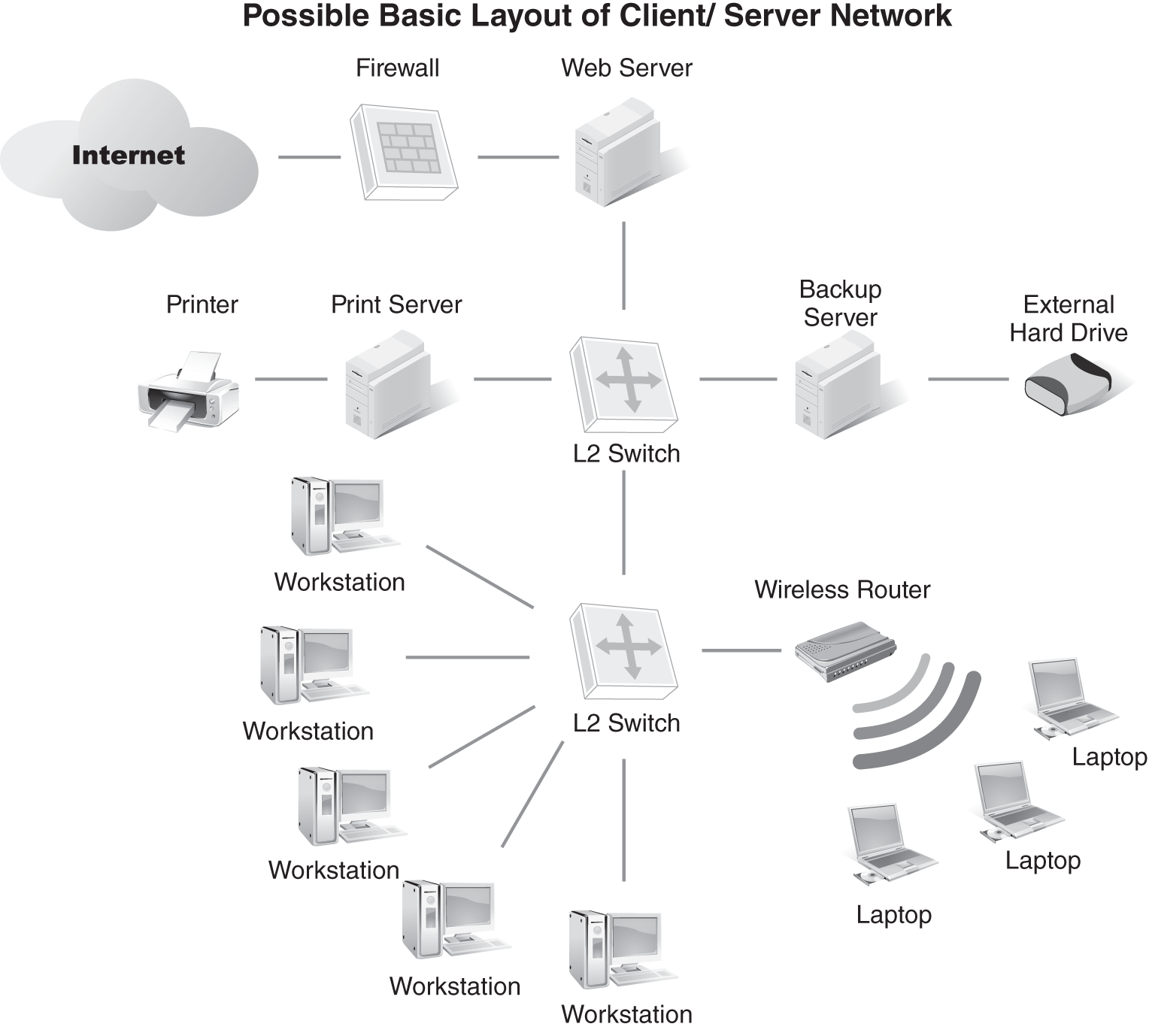
FIGURE 3-19 An example of a typical client/server network.
Client/server networks also employ single sign-on (SSO). SSO allows for a single but stronger set of credentials per user. With SSO, each user must perform authentication to gain access to the client and the network. Once the user has logged on, access control manages resource use. In other words, client/server authentication with SSO is often more complex than workgroup authentication—but it’s more secure. Users need to log on only once, not every time they contact a resource host server.
Because of their complexity, client/server networks are invariably more secure than SOHO and workgroup networks. But complexity alone is not security. Instead, because they are more complex, client/server networks require more thorough design and planning. Security is an important aspect of infrastructure planning and thus becomes integrated into the network’s design.
Client/server networks are not necessarily secure, because you can deploy a client/server network without any thought toward security. But most organizations understand that if they overlook network security, they are ensuring their ultimate technological downfall. Security is rarely excluded from the deployment process. And some networks are by nature more secure than others.
LAN Versus WAN
LAN stands for local area network. A LAN is a network within a limited geographic area. This means that a LAN network is located in a single physical location rather than spread across multiple locations. Some LANs are quite large, while others are very small. A more distinguishing characteristic of a LAN is that all of the segments or links of a LAN are owned and controlled by one organization. A LAN does not contain or use any leased or externally owned connections.
WAN stands for wide area network. A WAN is a network not limited by any geographic boundaries. This means that a WAN network can span a few city blocks, reach across the globe, and even extend into outer space. A distinguishing characteristic of a WAN is that it often uses leased or external connections and links. Most organizations rely on telecommunication service providers (often referred to as telcos) for WAN circuits and links to physical buildings and facilities, including the last-mile connection to the physical demarcation point. Both LAN and WAN networks can be secure or insecure. With a LAN, the owner of the network has the sole responsibility of ensuring that security is enforced. With a WAN, the leasing entity must select a telco that has a secure WAN infrastructure and incorporate service level agreements (SLAs) that define the level of service and performance that is to be provided on a monthly basis for the customer. In most cases, WAN data is secure only if the data sent across leased lines is encrypted before transmission. This service is the responsibility of the data owner, not the telecommunications service provider, unless this option is offered as a value-added service.
Thin Clients and Terminal Services
Thin client computing, also known as terminal services, is an old computing idea that has made a comeback in the modern era. In the early days of computers, the main computing core, commonly called a mainframe, was controlled through an interface called a terminal. The terminal was nothing more than a video screen (usually monochrome) and a keyboard. The terminal had no local processing or storage capabilities. All activities took place on the mainframe, and the results appeared on the screen of the terminal.
With the advent of personal computers (PCs), a computer at a worker’s desk offered local processing and storage capabilities. These PCs became the clients of client/server computers. Modern networking environments can offer a wide range of options for end users. Fully capable PCs used as workstations or client systems are the most common. PCs can run thin-client software, which emulates the terminal system of the past. That means they perform all tasks on the server or mainframe system and use the PC only as a display screen with a keyboard and mouse. Even modern thin-client terminals can connect into a server or mainframe without using a full PC.
Remote Control, Remote Access, and VPN
Remote control is the ability to use a local computer system to remotely take over control of another computer over a network connection. In a way, this is the application of the thin-client concept on a modern fully capable workstation to simulate working against a mainframe or to virtualize your physical presence.
With remote control connection, the local keyboard and mouse control a remote system. This looks and feels as if you are physically present at the keyboard of the remote system, which could be located in another city or even on the other side of the world. Every action you perform locally takes place at that remote computer via the remote control connection. The only limitations are the speed of the intermediary network link and the inability to physically insert or remove media, such as a flash drive, and use peripherals, such as a printer.
You might consider remote control as a form of software-based thin client or terminal client. In fact, many thin client and terminal client products are sold as remote control solutions.
Many modern operating systems include remote control features, such as the Remote Desktop feature found in most versions of Windows. Once enabled, a Remote Desktop connection remotely controls another Windows system from across the network.
Remote access is different from remote control. A remote access link enables access to network resources using a WAN link to connect to the geographically distant network. In effect, remote access creates a local network link for a system not physically local to the network. Over a remote access connection, a client system can technically perform all the same tasks as a locally connected client, with the only difference being the speed of the connection. Network administrators can impose restrictions on which resources and services a remote access client can use.
Remote access originally took place over dial-up telephone links using modems. Today, remote access encompasses a variety of connection types, including ISDN (Integrated Services Digital Network), DSL, cable modem, satellite, mobile broadband, and more.
In most cases, a remote access connection links from a remote client back to a primary network. A remote access server (RAS) accepts the inbound connection from the remote client. Once the connection goes through, the remote client now interacts with the network as if it were locally connected.
Another variant of remote connections is the virtual private network (VPN). A VPN is a form of network connection created over other network connections. In most cases, a VPN link connects a remote system and a LAN, but only after a normal network connection links to an intermediary network.
In FIGURE 3-20, a LAN has a normal network connection to the Internet, and a remote client has established a normal network connection to the Internet. These two connections work independently of each other. The LAN’s connection is usually a permanent or dedicated connection supporting both inbound and outbound activities with the Internet. The remote client’s connection to the Internet can be dedicated or nondedicated. In the latter case, the connection precedes the VPN creation. Once both endpoints of the future VPN link have a connection to the intermediary network (in this example, the Internet), then the VPN exists.
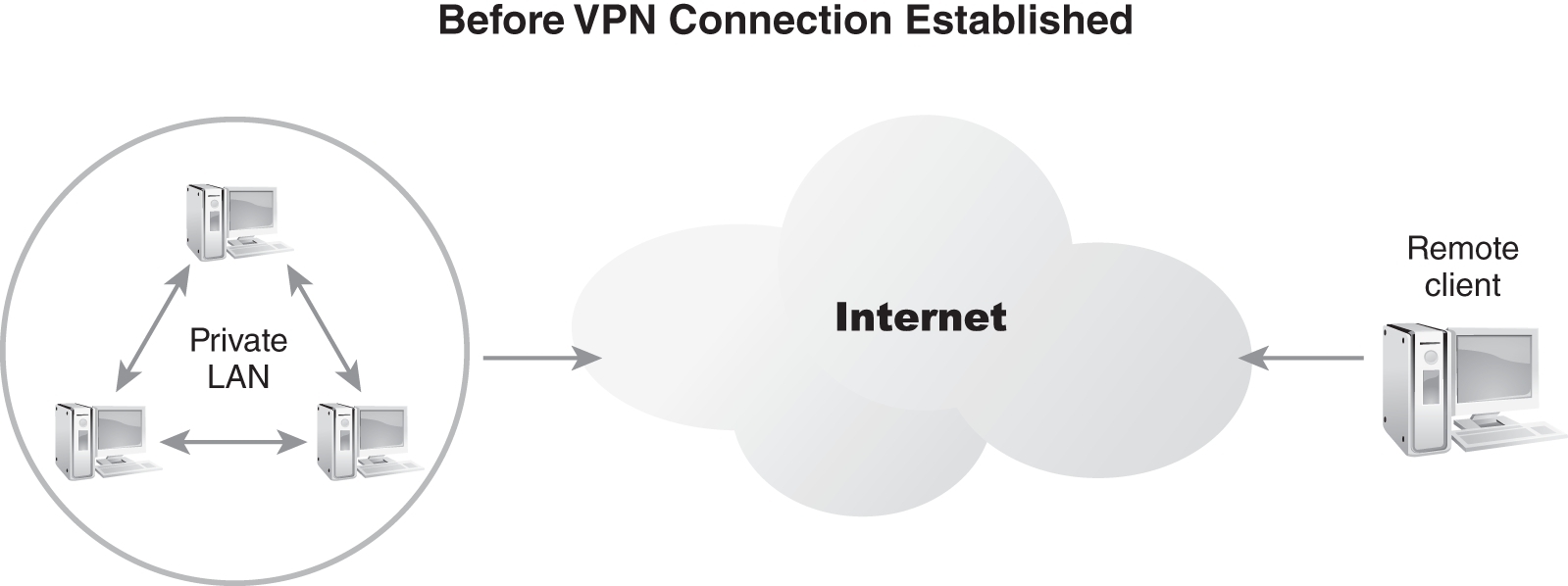
FIGURE 3-20 Common resource access connections.
In FIGURE 3-21, a new network connection connects the remote client to the LAN across the intermediary network. This new network connection is the VPN.
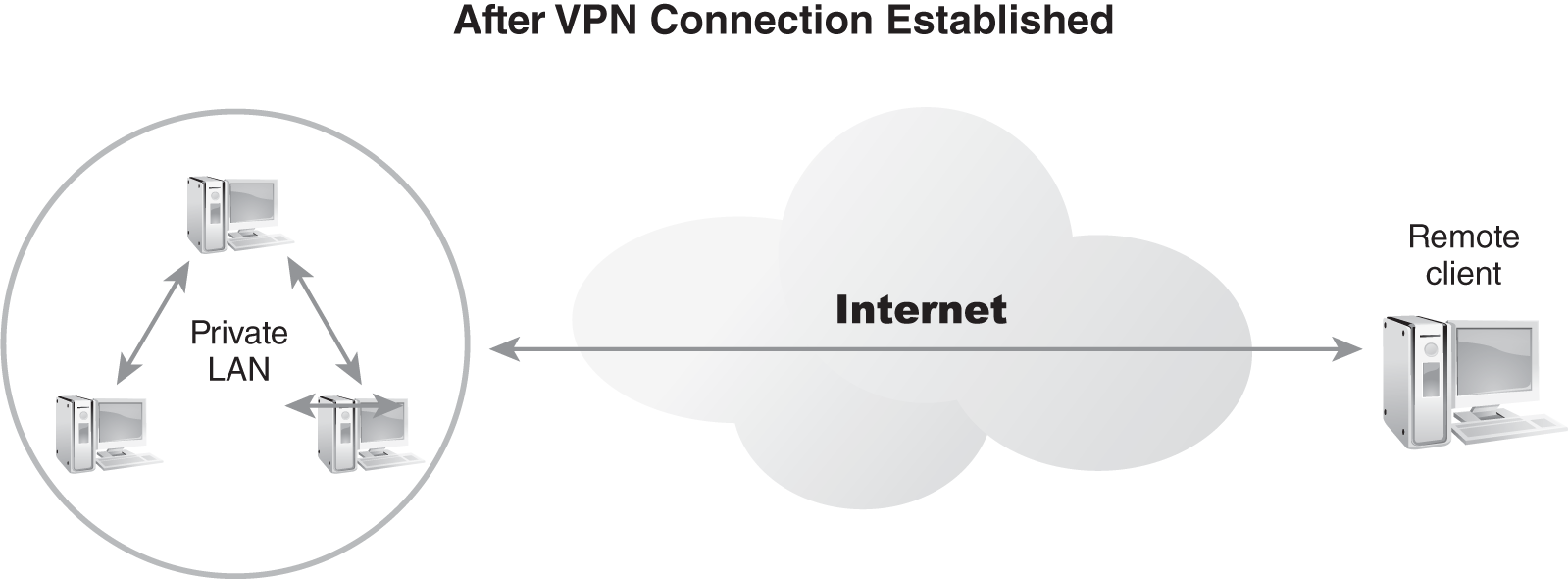
FIGURE 3-21 A VPN established between a remote client and a LAN over the Internet.
A VPN is a mechanism to establish a remote access connection across an intermediary network, often the Internet. VPNs allow for cheap long-distance connections over the Internet, as both endpoints only need a local Internet link. The Internet itself serves as a “free” long-distance carrier.
A VPN uses tunneling or encapsulation protocols. Tunneling protocols encase the original network protocol so that it can traverse the intermediary network. In many cases, the tunneling protocol employs encryption so that the original data securely traverses the intermediary network.
Boundary Networks
A boundary network is a subnetwork, or subnet, positioned on the edge of a LAN. A boundary network isolates certain activities, such as programming or research and development, from the internal environment (private LANs), which does not need to be externally accessible. External users can also access resources hosted in a boundary network. Such a subnet is known as a demilitarized zone (DMZ).
A DMZ is a boundary network that hosts resource servers for the public Internet. An extranet is a boundary network that hosts resource servers for a limited and controlled group of external users, such as business partners, suppliers, distributors, contractors, and others.
A DMZ subnet is a common network design component used to host public information services, such as websites. A DMZ allows for anyone on the public Internet to access resources. But at the same time, the DMZ provides some filtering of obvious malicious traffic and prevents Internet users from accessing the private LAN.
An extranet subnet provides companies that need to exchange data with external partners a safe place for that activity. An extranet is secured so only the intended external users can access it. Often, accessing an extranet requires VPN connections. An extranet configuration keeps public users from the Internet out and keeps the external partners out of the private LAN. An extranet example you may be familiar with is tracking the progress of a package by accessing a delivery company’s website and entering in your package’s unique tracking number.
You deploy DMZs and extranet subnets in different ways. Two of the most common designs are a screened subnet using a three-homed firewall (FIGURE 3-22) and N-tier deployment (FIGURE 3-23). A screened subnet using a three-homed firewall creates a network segment for the private LAN and a network segment for the DMZ or extranet. The three-homed firewall serves as a filtering device, as well as a router, to control traffic entering these two segments.
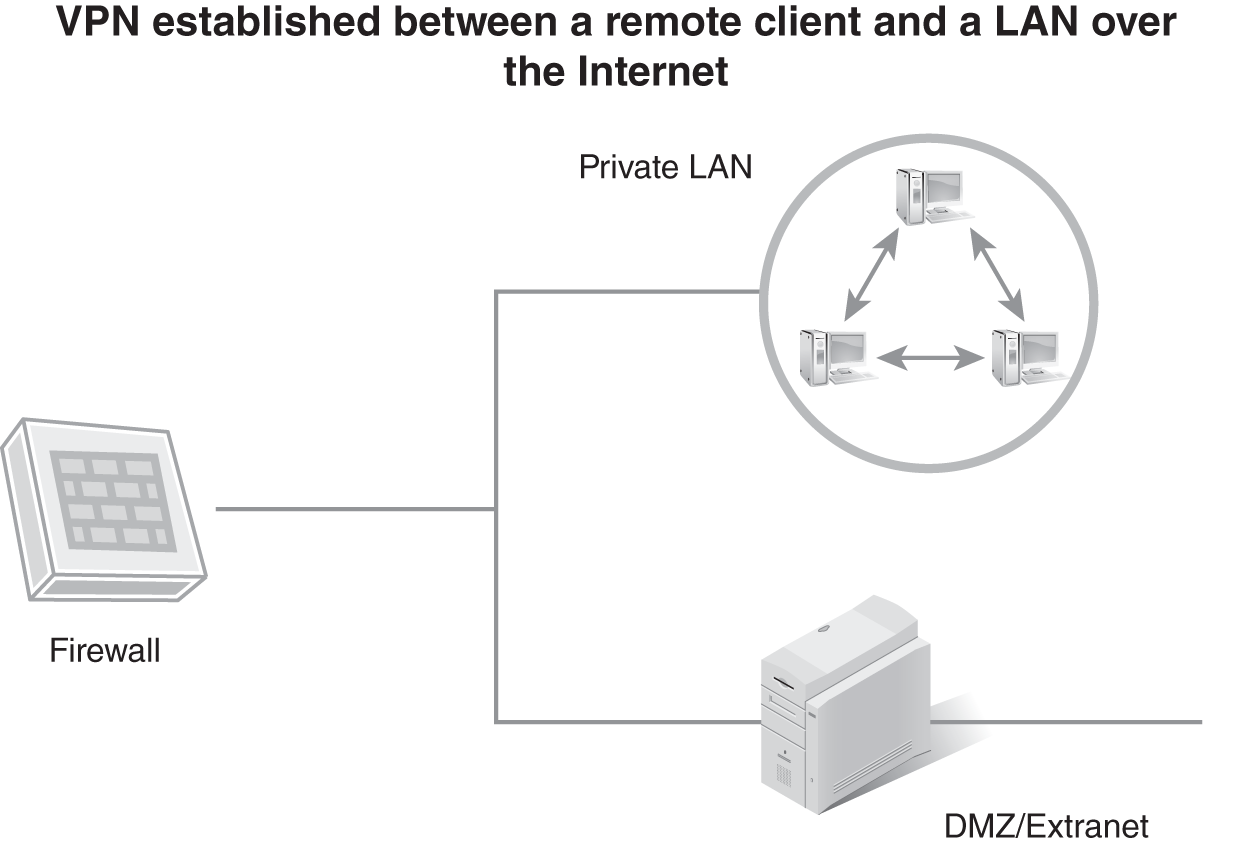
FIGURE 3-22 A DMZ or extranet deployed as a screened subnet with a threehomed firewall.
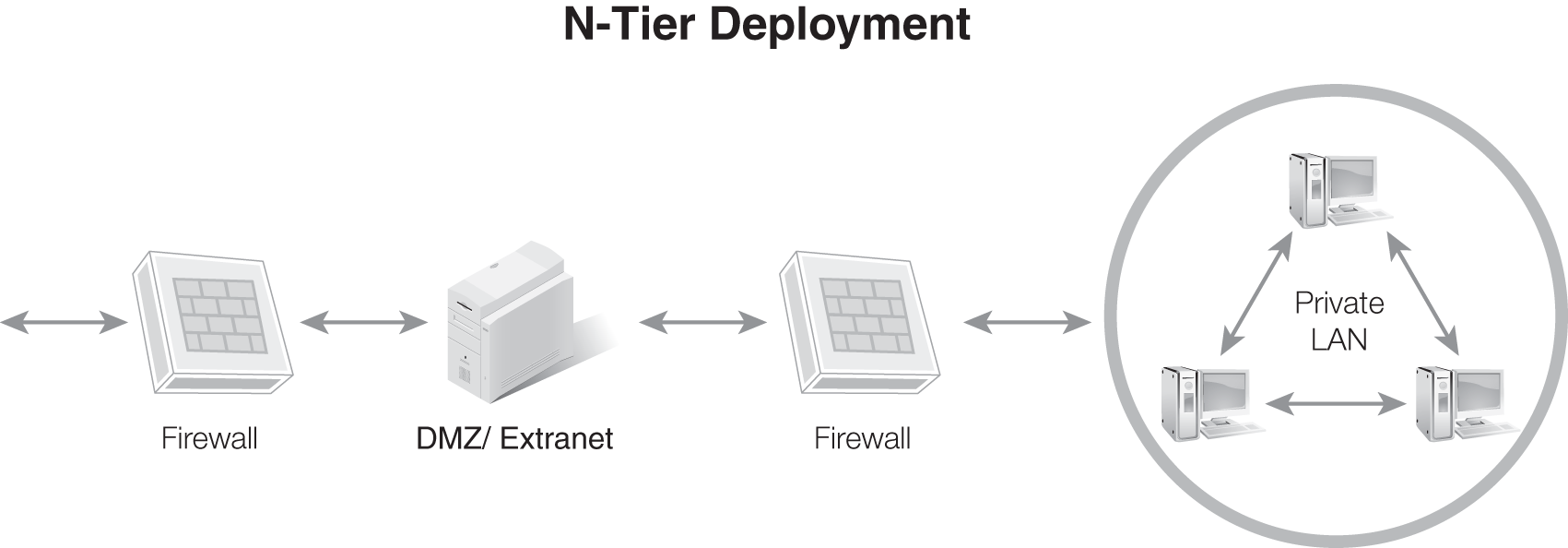
FIGURE 3-23 A DMZ or extranet deployed in an N-tier configuration.
The N-tier deployment creates a series of subnets separated by firewalls. The DMZ or extranet subnet serves as a buffer network between the Internet and the private LAN. The “N” in N-tier is a variable to be replaced with whatever number of tiers you actually build in your network.
