Oracle has built-in network encryption methods in its Oracle Advanced Security pack. The main advantage of using OAS encryption instead of other encryption methods is its ability to integrate and work with other Oracle security products such as Oracle Database Firewall and third-party products provided by other vendors such as IBM (InfoSphere Guardium), Imperva, and others. As a disadvantage, being a separate pack, it is expensive and requires licensing.
In case that you use unencrypted network communication, all the data flow from server to client will be sent in clear text. The only exception is the password which is sent in encrypted form during authentication. Packet interception becomes a trivial task if the attacker is located at the right place on the network and the data is transmitted unencrypted. In this recipe we will sniff and analyze the data in flight between nodeorcl5 and nodeorcl1 using Winshark. We will capture the network packets using unencrypted communication at the beginning of recipe and we will repeat the operation after we set up OAS network encryption to emphasize the role of encryption as a solid defence against different types of network attacks involving data interception and authentication.
- As a preliminary task download and set up Wireshark on
nodeorcl5. - On
nodeorcl5as root, launch Wireshark from the command line. Navigate to the Capture menu and click on Interfaces, and then check the interface on which packet capture will be performed and click on the Start button: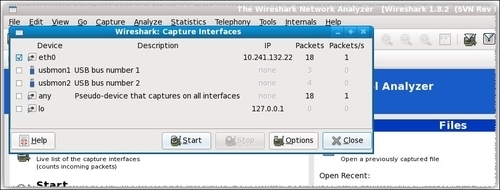
- Open a second terminal as the
oraclientuser and connect to theHACKDBdatabase as the userHR, then issue aSELECTstatement against theemployeestable as follows:[oraclient@nodeorcl5 ~]$ sqlplus HR@HACKDB SQL*Plus: Release 11.2.0.3.0 Production on Sun Sep 2 15:56:21 2012 Copyright (c) 1982, 2011, Oracle. All rights reserved. Enter password: Connected to: Oracle Database 11g Enterprise Edition Release 11.2.0.3.0 - 64bit Production With the Partitioning, OLAP, Data Mining and Real Application Testing options SQL> select first_name,last_name,salary,commission_pct from employees where commission_pct is not null; FIRST_NAME LAST_NAME SALARY COMMISSION_PCT ----- ------------------------- ---------- -------------- John Russell 14000 .4 Karen Partners 13500 .3 ............................................................................... SQL>
- Next, stop the packet capture by pressing Ctrl + E, or navigate to the Capture menu and click on Stop Capture. The traffic on port 1521 was automatically recognized by Wireshark as TNS transport. Click on any TNS packet captured, navigate to the Analyze menu, and click on Follow TCP Stream. If you scroll down in the Follow TCP Stream window you will identify the
SELECTstatement issued against theemployeestable and the result returned to the client. Close Wireshark without saving anything.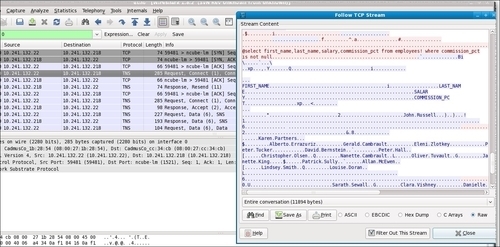
- In the following steps we will enable network encryption. Open the
$ORACLE_HOME/network/admin/sqlnet.oraconfiguration file onnodeorcl1. The first parameter that should be added tosqlnet.oraisSQLNET.ENCRYPTION_SERVER. This parameter sets the desired encryption behavior:SQLNET.ENCRYPTION_SERVER = required - The following parameter,
SQLNET.CRYPTO_SEED, which should be added, defines the encryption seed used at key exchange. It is recommended to choose a totally random value as follows:SQLNET.CRYPTO_SEED = 'uolPTYz(!)713@' - The following parameter defines
SQLNET.ENCRYPTION_TYPES_SERVER, the encryption algorithms to be used on the server side for encrypting the network packets. AddAES192and3DES168as follows:SQLNET.ENCRYPTION_TYPES_SERVER= (AES192, 3DES168) - The same configuration can be set by using Network Manager. Launch Network Manager (
netmgr), navigate to Profile, and choose Oracle Advanced Security in the list box located in the left-hand side panel. Choose the Encryption tab and choose SERVER for encryption side, for Encryption type select requested, Encryption seed, 'uolPTYz(!)713@', and as selected encryption methods choose AES192 and 3DES168. Navigate to File and Save the network configuration.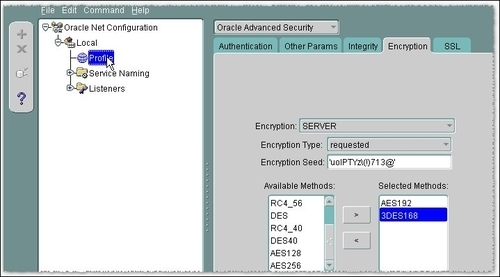
- Open the
$ORACLE_HOME/network/admin/sqlnet.oraconfiguration file onnodeorcl5. Here we have the same parameters but suffixed withCLIENT. Add the desired encryption behavior parameterSQLNET.ENCRYPTION_CLIENTusing the same value used on the server side as follows:SQLNET.ENCRYPTION_CLIENT = required - For the encryption seed choose a different random value:
SQLNET.CRYPTO_SEED = '!2)Zf^"l(!)713' - For the encryption algorithms add the same values:
SQLNET.ENCRYPTION_TYPES_CLIENT=(AES192, 3DES168) - Similarly for the client, if we use Network Manager Launch Network Manager (netmgr), choose Oracle Advanced Security in the list box located in the left-hand panel. Choose the Encryption tab and choose CLIENT for encryption side, for Encryption type select accepted, choose a different Encryption seed such as '!2)Zf^"l(!)713'. As selected encryption methods choose AES192 and 3DES168. Navigate to File and Save the Network configuration:
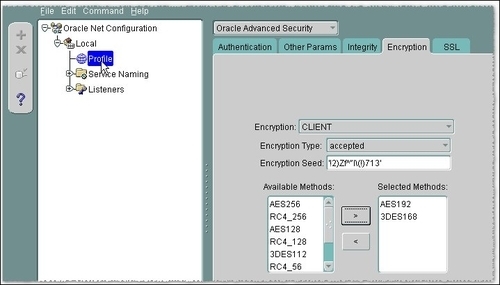
- Next we will proceed to sniff the connection again. Launch Wireshark, choose the interface, and press Ctrl + E to start the capture.
- Connect again as the
HRuser and reissue the previousSELECTstatement against theemployeestable. - In Wireshark stop the capture by pressing Ctrl + E, click on the TNS type captured packets, navigate to the Analyze menu, and open the Follow TCP Stream window. You should observe this time that the content is ineligible.
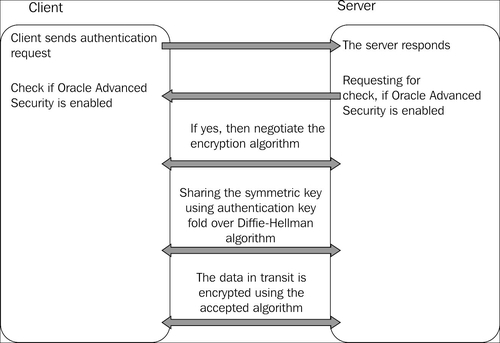
The stages of establishing an encrypted connection between a server and a client can be summarized in the following schema:
To list the supported encryption algorithms, crypto-checksums, and authentication methods provided by OAS, execute the adapters command:
[oracle@nodeorcl1 ~]$adapters ................................................................................ Installed Oracle Advanced Security options are: RC4 40-bit encryption RC4 56-bit encryption RC4 128-bit encryption RC4 256-bit encryption DES40 40-bit encryption DES 56-bit encryption 3DES 112-bit encryption 3DES 168-bit encryption AES 128-bit encryption AES 192-bit encryption AES 256-bit encryption MD5 crypto-checksumming SHA-1 crypto-checksumming Kerberos v5 authentication RADIUS authentication [oracle@nodeorcl1 ~]$
From this listing, RC4, AES, and DES families are symmetric key algorithms, and also named ciphers. A symmetric key cipher will use the same key for both encryption and decryption. RC4 ciphers are stream-based ciphers, AES and DES are block-based ciphers.
Stream ciphers encrypt every bit individually by adding a key stream bit to a plain text bit. Depending on implementation there could be synchronous stream ciphers (the key stream depends only on the key) and asynchronous stream ciphers (the key stream also depends on the ciphertext). These types of ciphers have the advantage to be very fast compared to block ciphers but are more vulnerable to attacks. RC4 has a demonstrated weakness related to key setup hence you should use the high key length variant (RC4 256) whenever possible. The stream ciphers provided by Oracle OAS are RC4 40, RC4 56, RC4 128, and RC4 256 bits, where 40, 56, 128, and 256 represent the key length.
Block-based ciphers encrypt an entire block of bits at a time using the same key. This means that every bit from a block depends on every bit on the same block.
AES is the abbreviation for Advanced Encryption Standard , and should be favored based on its solidity and good performance. It is a derivation of the Rijndael cipher where the block size is restricted to 128 bits. It was designed to replace the DES algorithm.
DES is the abbreviation for Data Encryption Standard. The original DES, based on the 56 bit key, is rarely used nowadays and is considered insecure. 3DES112 is a variant of 3DES, also called Triple DES, with two keys derived from the fact that it is using two keys each being 56 bits in size or two phases of encryption.
3DES168 is a variant of 3DES using three 56 bits key or phases for encryption. It is strong but slow in software-based implementations.
Based on the fact that symmetric encryption is used, there must be a mechanism that allows exchanging the encryption keys between the parties involved in communication. The key exchange phase uses the Diffie-Hellman key exchange algorithm. In the Diffie-Hellman key exchange the two parties have to agree on a random generated number known only to them. Based on this random number, after a series of transformations an encryption key is generated (for RSA Laboratories - 3.6.1 What is Diffie-Hellman? go to http://www.rsa.com/rsalabs/node.asp?id=2248) and used for data encryption. The encryption seed is used and strongly correlated with the generation of the random numbers. OAS network encryption uses CBC as the cipher mode of operation. For more about cipher mode of operation see Chapter 3, Using DBMS_CRYPTO for column encryption.
For the desired encryption behavior you can specify four parameters both on the server and on client side: REJECTED, ACCEPTED, REQUESTED, and REQUIRED.
The following table summarizes the combinations of parameters for desired behavior on client and server:
|
Desired behavior – Client |
Desired behavior – Server |
Encryption |
|---|---|---|
|
ACCEPTED |
REJECTED |
OFF |
|
REQUESTED |
REJECTED |
OFF |
|
REQUIRED |
REJECTED |
Connection fails |
|
REJECTED |
ACCEPTED |
OFF |
|
ACCEPTED |
ACCEPTED |
OFF |
|
REQUESTED |
ACCEPTED |
ON |
|
REQUIRED |
ACCEPTED |
ON |
|
REJECTED |
REQUESTED |
OFF |
|
ACCEPTED |
REQUESTED |
ON |
|
REQUESTED |
REQUESTED |
ON |
|
REQUIRED |
REQUESTED |
ON |
|
REJECTED |
REQUIRED |
Connection fails |
|
ACCEPTED |
REQUIRED |
ON |
|
REQUESTED |
REQUIRED |
ON |
|
REQUIRED |
REQUIRED |
ON |
To discover the utility of network encryption against MITM attacks, replay the Hijacking Scenario covered in the previous recipe with encryption configured.
The flow of encrypted data packets captured by ettercap during ARP poisoning stage of Oracle Hijacking scenario:
[root@mitmattack ~]# ettercap -T -M arp /10.241.132.22/ /10.241.132.218/ ettercap 0.7.4.1 copyright 2001-2011 ALoR & NaGA Listening on eth0... (Ethernet) Ettercap ……………………………………………………………………………………………………………………………………..Sat May 12 19:21:36 2012 TCPy□□ 10.241.132.22:33592 --> 10.241.132.218:1521 | AP ..........h.G...b...e.0.........q..:...6..-....... 7..."a~.-........../...3.^...(...?N.....dH...'.Gf.'..X.w......Y5... A[Df..{w...r.....5...G.P....l.%%..."o..Y...L..S.E...5:........)..Udc~ *R..9...I.{?. ........kL]..'..J..4.y.F.J.....yA.b..T....._b..1Y::kq..;v....P......p.C....e...c..%....l..'2."....:.0P..K...W.b....}.i .}.t.q.6...X;.C..B...G..K..*.Y....dym......R.hz./....N.+V..}..FS$K.....u..1.;....A R5.N&....".A....T.%33q..~H5P.i.y.....KE"A^..B...;.M1.2...d........L..
And the hijacking proxy will be blocked and unable to perform the session hijacking:
[root@mitmattack pythonproxy_0.1]# python pytnsproxy.py 10.241.132.22 connected:
