When the audit is performed, it is important to be able to identify the originating host, username, and logon and logoff time for sessions. In this recipe we will enable an audit on sessions created by users HR, DRAPHEAL, and SMAVRIS.
- Connect as user
SYSTEM, and start to audit sessions for userHR,DRAPHEAL, andSMAVRISas follows:SQL> conn system Enter password: Connected. SQL> audit session by HR, DRAPHEAL, SMAVRIS; Audit succeeded. SQL>
- Next connect as user
HRand wait for 10 seconds, then disconnect. - Connect also as user
DRAPHEALandSMAVRISand wait for 10 seconds or more, then disconnect. - One source of information for audit trails related to the session can be found by querying the
DBA_AUDIT_SESSIONdictionary view. Check the generated audit records byOS_USERNAME,USERNAME,USERHOST,TERMINAL,TIMESTAMP,ACTION_NAME, andLOGOFF_TIMEas follows: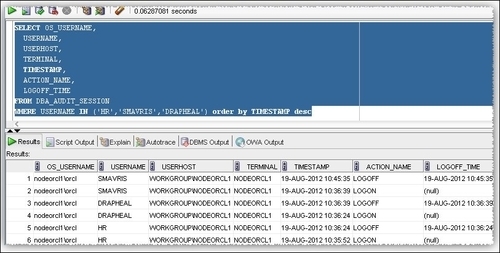
The information about the session audit can be found in DBA_AUDIT_SESSION, DBA_COMMON_TRAIL, and USER_AUDIT_SESSION dictionary views.
If you want to audit all sessions then use the following statement:
audit session by access;
To disable audits on all sessions use the noaudit command as follows:
noaudit session;
To disable audits only for specific users execute the following:
noaudit session by HR, DRAPHEAL, SMAVRIS;
It is highly recommended to couple session audit with a real time alarming mechanism that fires when a user logs on.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
