The usage of the valid node checking security feature is very similar to the TCP wrappers presented in Chapter 1, Operating System Security. Using this capability, you can deny or the allow connecting clients based on IP address or hostname.
- Open
$ORACLE_HOME/network/admin/sqlnet.oraand enable valid node checking by settingTCP.VALIDNODE_CKECINKas follows:TCP.VALIDNODE_CHECKING=ON - Next, you can establish the hosts that will be allowed to connect by setting the
TCP.INVITED_NODESparameter as follows:TCP.INVITED_NODES= {nodeorcl5} - After you add the invited nodes you must reload the listener configuration.
lsnrctl reload - If we want to establish a connection from a node that is not included in the invited node list, the
ORA-12537: TNS:connection closederror will be thrown as follows:oraclient@nodeorcl2:~> sqlplus hr/hr@HCKDB SQL*Plus: Release 11.2.0.3.0 Production on Sun Feb 26 22:09:25 2012 Copyright (c) 1982, 2011, Oracle. All rights reserved. ERROR: ORA-12537: TNS:connection closed
The configuration of node checking can be implemented by using two parameters: TCP.INVITED_NODES or TCP.EXCLUDED_NODES. The latter can be used for defining explicitly which nodes will be denied to connect. TCP.INVITED_NODES has precedence over TCP.EXCLUDED_NODES, and they are mutually exclusive. Usually you should use one of them to form a list. You can use only complete IP addresses or hostnames; subnets or wildcards are not permitted.
This feature usually must be correlated with firewall rules related to allowed and denied hosts or networks. Valid node checking protection can be bypassed by an attacker by using IP spoofing—hence it is a good idea to enable IP spoofing protection at kernel level, as we presented in Chapter 1, Operating System Security.
In a very large network with thousands of databases and a very large client base, you should consider using Oracle Connection Manager to define connection rules in a centralized manner. For more about Oracle Connection Manager check the Oracle documentation (http://docs.oracle.com/cd/E11882_01/network.112/e10836/cman.htm#i491788) or check this comprehensive article, http://arup.blogspot.ro/2011/08/setting-up-oracle-connection-manager.html, written by Arup Nanda.
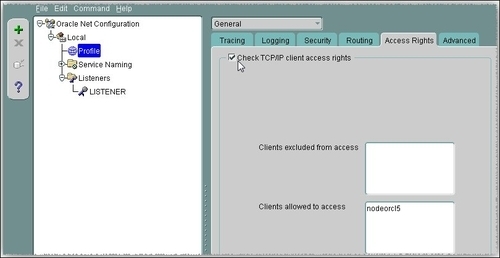
To enable tcp.validnode_checking by using Net Manager (netmgr), perform the following steps:
- Navigate to Profile.
- In the left-hand side pane, scroll the upper listbox to select General, and click on the Access Rights tab.
- Check the Check TCP/IP client access right checkbox and in the Clients allowed to access listbox type
nodeorcl5. - Next, go to File and then Save Network Configuration.