Appendix A. Technical Terms and References
This Appendix provides a glossary of technical terms used in the book, along with the occasional technical references that didn’t fit into the flow of the respective chapter. The latter introduce a number of computer and Internet terms that aren’t necessarily defined in place or could benefit from some expansion.
- 24/7,
-
shorthand for “constantly online” (24 hours, seven days a week). In common usage it less strictly means fixed-line connectivity as opposed to dial-up. When speaking of server uptime, for instance, 24/7 and 24/7/365 is taken in the literal sense, implying 99+ percent availability.
- Actor,
-
entity that can initiate activities—an actor can be a user, device, or software.
- Analog telephone,
-
or POTS (“plain ordinary telephone system”) line. Digital data connectivity is by way of dial-up modem to an ISP modem pool and limited to a maximum 56Kbps, although substandard line quality causes a fallback to significantly less. Modem use blocks the line from accepting voice calls.
- Architecture,
-
a design map or model of a particular system, showing significant conceptual features.
- Authentication,
-
a procedure to determine that a user is entitled to use a particular identity, commonly login and password but might be tied much tighter to location, digital signatures or pass-code devices, or hard-to-spoof personal properties using various analytic methods.
- Bandwidth,
-
a measure of the capacity a given connection has to transmit data, typically in some power of bits per second or bytes per second.
- Broker,
-
a component (with business logic) that can negotiate procurement and sales of network resources. Discussed in Chapter 8, with Mojo Nation.
- CD,
-
Compact Disc, a Philips/Sony defined standard originally created for digital audio recordings (of one hour), but adopted as a storage medium for any data (about 600MB). DVD (Digital Video Disc, later renamed Digital Versatile Disc) uses the same physical form factor, but it has in its current version seven times the capacity of a CD, suitable for digital (usually compressed) cinema.
- Checksum,
-
a mathematical method for error or change detection.
- Client-Server,
-
the traditional division between simpler user applications and central functionality or content providers, sometimes written server-client—a seen variant is “cC-S” for centralized client-server, though cS-C would strictly speaking have been more logical to avoid thinking the clients are centralized.
- Clone,
-
a functionally similar and format-compatible piece of software. When the original code is proprietary, a clone can be reverse-engineered from analyzed traffic (output from original) and deduced protocols.
- Convenience feature,
-
an automated or default setting intended to make life “easier” for the casual user, but which often gets underfoot and makes it difficult to fathom how the application works.
- CPRM/CPPM (Content Protection for Recordable Media and Prerecorded Media),
-
a renewable cryptographic method for protecting entertainment content when recorded on physical media.
- DAV (or WebDAV),
-
Distributed Authoring and Versioning, a proposed new Internet protocol that includes built-in functionality to facilitate remote collaboration and content management. Current, similar functionality is provided only by add-on server or client applications.
- Delta,
-
math-jargon term for value or variable that conveys state change information, strictly speaking rate of change.
- DHCP,
-
Dynamic Host Configuration Protocol, is a method of automatically assigning IP numbers to machines that join a server-administrated network.
- Directory or Index services,
-
translate between naming and actual location. DNS is such a service for translating Internet domain names to actual IP addresses.
- DoS,
-
denial-of-service, a condition when a particular server or service is unable to respond to new requests, usually caused by bandwidth flooding or server overload. DoS is usually but not always due to malicious attacks. DDoS, Distributed DoS, is a malicious attack where many network nodes are remotely orchestrated to simultaneously flood designated targets with spurious requests, causing a massive DoS.
- DSL,
-
Digital Subscriber Line, usually known in its asynchronous form ADSL, a form of broadband access that works by aggressive multiplexing of many carrier frequencies on the last transport segment (or mile) of twisted-pair phone line to the user. Upstream of this last leg, connectivity relies on fiber-optic cable. DSL is always-on broadband, concurrent with any voice phone calls but sensitive to audible interference if line and connector quality is poor.
- Dumb-terminal mainframe system,
-
many clients with little or no logic communicating with a central server where all processing occurs.
- End user,
-
the person who actually uses an implementation.
- Encryption,
-
opaquely encoding information so that only someone with a secret key can decrypt and read or use it.
- Exponential backoff algorithm,
-
a way of ensuring that clients avoid repeated collisions of packets on a common line or channel. Each delays retransmit by a random time, and on failure, by a random time in a doubled delay interval.
- Exposure (specifically client exposure),
-
the degree that the user application enables remote endpoints to access information (possibly covertly) other than that which is freely and deliberately shared. Most clients pass along more information than users are aware of, although some of it is “needed” for client-server functionality. Some clients become downright invasive. Firewall and proxy filters can reduce the exposure.
- Fat or thin client,
-
reflects relative amount of resources built into or installed on a networked client (as hardware or software). Thin clients rely heavily on server or network services for functionality.
- FEC, Forward Error Correction,
-
a number of related encoding methods that allow reconstruction of a complete file despite packet losses. See Chapter 8.
- Firewall,
-
a packet-filtering form of gateway or proxy that allows connections only over approved protocols, on approved ports, to or from approved applications.
- Freeware,
-
software that is distributed free, but the author retains formal copyright unless the material is explicitly declared “in the public domain” or under some other IPR “free license”.
- FTP (File Transfer Protocol),
-
is a common method to transfer files between server and client. It’s considered more reliable than transfers using HTTP.
- Gateway or proxy,
-
network device (often a computer) that routes or bridges between LAN and WAN, or different network types, and frequently also provides NAT and firewall functionality.
- Hash,
-
a mathematical method for creating a numeric signature based on content; these days, often unique and based on public key encryption technology.
- HTTP (HyperText Transfer Protocol),
-
is the common protocol for communication between Web server and browser client. The current implementation is v1.1.
- HTTPS (HTTP over SSL),
-
a secure Web protocol that is based on transaction-generated public keys exchanged between client and server and used to encrypt the messages. The method is commonly used in e-commerce (credit card information) and whenever Web pages require identity and password login.
- Implementation,
-
a practical construction that realizes a particular design.
- IP numbers,
-
the Internet Protocol addressing scheme, written as four dot-separated numbers A.B.C.D, each originally representing a block range for subnets of varying size. A block that remains local to a LAN is reserved in each range.
- ISDN,
-
Integrated Services Digital Network, is a fully digital telephone line that supports voice and dual A-B data channels of 64 kbps each over standard twisted-pair phone lines. ISDN is more common in Europe where it was long marketed simply as “duo-com”, two subscriber numbers for the cost of one line. The terminator adapter device supports both digital equipment and analog phones—data connectivity is by way of another adapter.
- ISP,
-
Internet Service Provider, a business entity that provides Internet access and hosting services. IPP, Internet Presence Provider, is an entity that provides Internet services, but only for customers who already have Internet access.
- Journalizing,
-
recording change information for delayed updates, rollbacks, or recovery purposes.
- Kbps and kbps,
-
measures of digital transfer rate. The abbreviations are used in the book in the international sense, as defined by ISO. Thus, 1Kbps = 1,024 bits/s (power of 2) and 1 kbps = 1,000 bits/s (power of 10). It’s unfortunately common in U.S. writing to have Kbps also mean the latter.
- Keyspace,
-
a namespace for numeric keys, which are hashed from human-readable names.
- LAN,
-
local area network where the computer owner generally also is in full control of the physical network. LAN is distinct from WAN , wide area network, where at least some connectivity is through an external (or public) infrastructure.
- Mailbox services,
-
commonly implemented with POP3 (Post Office Protocol v3) or IMAP4 (Internet Message Access Protocol v4). The latter allows continued storage and manipulation of e-mail on the mailbox server after reading.
- Market meme,
-
a trendy term for “buzz” concept. An idea that is popular or widespread in current use—in the “meme market”—by virtue of being repeated the most. This is measured based on how often the idea pops up in the media, writings, or human conversations.
- MB (megabyte),
-
a measure of storage size. As used in the book, it’s interpreted as true power-of-2 million—that is, 1,024 x 1024 or 1,048,576 bytes. (1KB is 1024 bytes.) In common usage elsewhere, however, MB might arbitrarily mean 1,024 x 1,024, 1,000 x 1,024, or 1,000 x 1,000.
- Message,
-
a higher logical unit of data, comprising one or more network packets, and defined by the implementation protocol.
- Middleware,
-
a third-party layer between applications and infrastructure.
- Modem,
-
modulator-demodulator, device to convert between digital data and audio-encoded data suitable for telephone lines. Also used more generally and less accurately for adapter devices to digitally encoded transports such as ISDN, DSL (ADSL or SDSL), and cable broadband.
- NAT,
-
network address translation, implemented by device or computer as a way of connecting a LAN, with local machine addresses, to a WAN, using typically a single external address.
- NIC,
-
network interface card, a device that physically connects computer to network, lowest level of the OSI model.
- Node,
-
a connection endpoint in a network, often a computer or the network client-server application, depending on one’s perspective—physical or virtual.
- Open protocol,
-
the specifications are published and can be used by anyone.
- Open source,
-
opposite of proprietary “closed” source. Open means that the source code to applications and the related documentation is public and freely available. Often, runnable software itself is readily available for free.
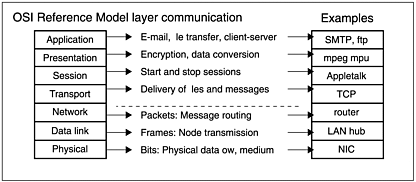
- OSI reference model (Open Systems Interconnect protocol layers),
-
see Figure A.1, with reference to the OSI diagrams in Chapter 1 and 2, and to the native implementation examples. (.NET usually runs at the Application layer).
Figure A.1. An indication of what kind of communication occurs at particular levels in the OSI model, and some examples of relevant technologies that function at the respective levels. The top four are “message based”.
- Out-of-band (OoB),
-
a communications (or distribution) channel external to and independent of the considered or normal network.
- Packet,
-
a smallest logical unit of data transported by a network, which includes extra header information that identifies its place in a larger stream managed by a higher protocol level.
- Persistency,
-
the property of stored data remaining available and accessible indefinitely or at least a very long time, in some contexts despite active efforts to remove it
- Platform,
-
shorthand for a specific mix of hardware, software and possibly environment that determines which software can run. In this sense, even the Internet as a whole is a “platform” for the (possibly distributed) applications and services that run there.
- Protocol,
-
specifies how various components in a system interact in a standardized way. Each implementation is defined by both model (as a static design) and protocol (as a specified dynamic behavior).
- Proxy (also see gateway),
-
an entity acting on behalf of another, often a server acting as a local gateway from a LAN to the Internet.
- Push,
-
a Web (or any) technology that effectively broadcasts or streams content, as distinct from “pull” that responds only to discrete, specific user requests.
- Redundancy,
-
more information than is strictly required to retrieve or reconstruct the original data. Discussed at length in the section on FEC in Chapter 8.
- Reliable and unreliable packet transport
-
methods are distinguished by the fact that reliable transport requires that each and every message/packet is acknowledged when received, or it will be resent either until it is, or a time-out value or termination condition is reached.
- Representational,
-
when some abstraction is used for indirect reference instead of the actual thing—a name, for example.
- RPC,
-
remote procedure call, a protocol extension that enables remote software to directly invoke a host’s local API (application program interface) functionality.
- SDMI (Secure Digital Music Initiative),
-
an encoding method that is intended to make it impossible to copy the protected CD music tracks or MP3 files.
- Security
-
is fundamentally in conflict with availability (I know that it’s there) and especially accessibility (I can get it). Perfect security would deny both bits of information from the casual user. Encryption adds the further dimension that even if I can find it and get it, I won’t necessarily be able to read it. Good security is finding the optimal balance for the situation and retaining a reasonable measure of convenience for the legitimate user.
- Sendmail services,
-
commonly implemented by the old but still prevalent SMTP (Simple Mail Transport Protocol) to transport e-mail across the Internet from sending server to mailbox server.
- Shared workspace,
-
when actions and data are shared over a p2p network.
- Spyware,
-
an application that includes software components that covertly collect information about a user and convey it to some collection endpoint.
- Swarm distribution,
-
when peers adaptively source downloaded content to other peers requesting the same material. Random offsets ensure quick fulfillment. Swarm services in general are network services implemented by cooperating nodes, often self-organizing in adaptive ways.
- Swarm storage,
-
when content is fragmented and distributed (with redundancy) to many different nodes. On retrieval, swarms adaptively cooperate to source.
- TCP/IP,
-
Transmission Control Protocol with Internet Protocol, the currently most common “reliable” network protocol—the protocol that defines the Internet.
- Token server,
-
a virtual bank that can issue digitally signed virtual currency in a secure manner. The server can allow withdrawal and deposit of tokens.
- UDP,
-
User Datagram Protocol, as UDP/IP is the Internet “unreliable” protocol that corresponds to reliable TCP/IP. UDP is transaction oriented with a minimum of protocol mechanism, and is defined in RFC 768.
- Uniform protocol,
-
all compliant clients can handle messages in the protocol; hence all these clients are interoperable and can freely pass messages to each other.
- URI,
-
Uniform Resource Identifier, is a complete and unique scheme for identifying arbitrary entities, defined in RFC 2396 (www.ietf.org/rfc/rfc2396.txt).
- URL,
-
Uniform Resource Locator, is a standard way to specify the location of a resource available electronically, as a representation of its primary access mechanism—the addressing notation we are used to from Web and other Internet clients (including e-mail). URLs are a subset of the URI model and are defined in RFC 1738. Another subset of URI, the URN (Uniform Resource Name), instead refers to specifiers that are required to remain globally unique and persistent even when the resource ceases to exist or becomes unavailable. It is thus a representation based on resource name.
- Usenet,
-
the peer-server network hosting newsgroups, defined by the protocols for posting, transferring and reading. A decent history is available from www.vrx.net/usenet/history/.
- Web (World Wide Web, WWW),
-
that part of the Internet accessed using HTTP-compliant clients—that is, the familiar Web browser.
- Webmail service,
-
a way to let users access server-based mailbox and sendmail services using an ordinary Web browser, and manage mail on the server rather than on a local machine’s e-mail client. Webmail is useful for users who access e-mail from several machines or when travelling.
