CHAPTER 1: INTRODUCTION TO PENETRATION TESTING
Penetration testing captures the imagination and sparks the interests of many people. It is part mystery, part challenge, part creativity and part risk. It has the glamour and mystique of doing something on the wild side of life by simulating a criminal act, but without the penalties. Therefore, it is no surprise that many people are drawn to penetration testing and want to know more about what it is, how to do it and, moreover, how they can use it to help protect their systems and defend their networks.
Protecting the systems and networks of today requires a broad understanding and in-depth knowledge of the tactics, tools and motivations of the adversary. The person given the responsibility to protect a system should know the nature and techniques of the enemy, and be able to prevent successful attacks by discovering and securing any vulnerabilities in their systems or networks before the adversary can find them.
Penetration testing is the simulation of an attack on a system, network, piece of equipment or other facility, with the objective of proving how vulnerable that system or “target” would be to a real attack.
Penetration testing is based on knowledge. The more knowledge the tester has, the more effective their attack will likely be. But what knowledge do they need? They need knowledge about the target, the operating environment, the users, the culture, the business itself, the physical security and, most of all, knowledge of how to use the tools (and their imagination) effectively.
Many people have a narrow and limited perception of penetration testing; they see it as an attack using a few common tools against a list of commonly known vulnerabilities. This type of testing provides some benefit to the organization, but is far too superficial and restrained to be really effective and meaningful. A pen test is innovative, probing, testing, evaluative, persistent and thorough.
In this booklet, we will examine various types of penetration tests, the tools commonly used, and the ways to leverage a pen test to provide the greatest possible benefit to the organization. The resulting penetration tests will deliver assurance and confidence to clients and business owners that their systems, networks and facilities are secure, that the level of risk to the organization of an attack is within acceptable levels, and that their information systems are being managed properly.
Case study
The General responsible for overseeing the security and operations of a military network requested a penetration test. The General was convinced that his network was secure, well-hidden and impenetrable. He had diligently instructed his staff to ensure that the network was well managed, unnecessary services were disabled, and that no extraneous information about the network was available anywhere outside of the network itself. He hired a top-quality pen testing team and challenged them to enter his network, but, at the same time, was convinced they would not even find it, let alone gain enough knowledge to launch a proper attack.
A couple of weeks into the test schedule, the pen testing team requested a meeting with the General. As he entered the meeting, the General asked if they had “given up already.” The team then laid in front of the General the information they had managed to access, and stated that they were required to cease the test once they had obtained such information under the rules of the engagement. (Note: these rules must be set out at the beginning of the test, since there may be serious implications and potential damage to the organization once the testing team has gained access – especially when succeeding in penetrating a military network.)
Upon reviewing the documents obtained by the pen testing team, the General exploded in rage, demanding to know how they had managed to obtain so much sensitive, classified material. He threatened to demote his entire technical team and launch a legal investigation into his department. It was at this point that the pen testing team advised the General that the General’s network was quite secure, and that the way they broke into the network was not through a sophisticated technical attack. They were able to access all of the information by simply sending a DVD that contained a Trojan horse to the General himself. When inserted into the General’s machine, the Trojan promptly copied the entire contents of the hard drive on the General’s machine to a secure server that the pen testing team had set up.
They delivered the DVD to the General using a journalist that had an interview with him to discuss a news article being written about technology in today’s military. The DVD contained video clips and articles as a sample of the work that the journalist had already done to prepare the article.
Such an attack should not have been successful – no foreign media should have been installed onto a classified machine, and both policies and technical controls should have prevented this. But what happens in reality? Many people, including Generals, senior managers and even technical staff, could fall for such an easy trick.
As can be seen in this case, there are many challenges involved in carrying out a successful pen test. The first is to gain approval to conduct the test, the second is to determine the rules of engagement, the third is to know the reporting structure and who to deliver the results to, the fourth is to ensure the pen test is not limited to a strictly technical attack and, finally, the fifth is to ensure that the test provides meaningful results and recommendations for the organization.
We all know that most organizations would fall for such an attack. There is no technical control that is sufficient to totally prevent user mistakes! The 2011 attacks against RSA (the security division of the EMC) are an example of how easy it can be to penetrate even the most security-conscious organization. In the case of RSA, the exploit was enabled through a simple spear phishing e-mail sent to an employee. The employee opened the attachment that was linked to the e-mail (which promised them a list of open employment positions) and thereby launched the hacking tool that provided a backdoor into the company for the attacker to use1.
The purpose of a pen test is to find any problems on the system and network, and in the user training, business procedures and operational controls related to the system being tested. A successful pen test is one that discovers the vulnerabilities and determines the level of risk they pose to the organization. An unsuccessful pen test is one where the team fails to find existing serious vulnerabilities and provides management with a false assurance of security, or one that provides the organization with a flood of meaningless data that is not sorted according to priorities or levels of risk.
The many breaches that Sony experienced in 2011 were mostly the result of simple attacks. The vulnerabilities that allowed the attacks to do the damage and compromise those systems affected should have been found by competent pen testers and thereby corrected. The Verizon-USSS data breach report of 2010 indicated that 96% of all data breaches were avoidable through simple or intermediate controls2. This is where many pen tests are failing. The pen tester bears the responsibility to perform their duties in a professional and competent manner, and thereby provide the information required by their clients to strengthen and secure their systems and networks.
Security basics
Penetration testing is a process of testing and validating the security posture and maturity of an organization. In order to test the security program, it is necessary for the pen tester to know what to look for and what the security priorities are.
The first problem is that the term “security” is an abstract term and can mean many different things to different people.
Definition
One resource3 defines security in the following ways:
1. Freedom from danger, risk, etc.; safety
2. Freedom from care, anxiety, or doubt; well-founded confidence
3. Something that secures or makes safe; protection; defense
4. Freedom from financial cares or from want
5. Precautions taken to guard against crime, attack, sabotage, espionage, etc.
We can see many positive aspects of security – freedom from worry and danger, for example – but we also see that security is very much an emotional term, conveying a sense of safety and protection. The last definition is most relevant for us: “precautions taken to guard.”
A pen tester is not testing emotion or a feeling of safety; the tester is testing the precautions, the defenses and the levels of risk or danger.
The information security triad
For many years, the information security industry has defined the term “security” as comprising three core elements: confidentiality, integrity and availability. There are good reasons for this. Using these three elements to define security gives a more complete picture, and provides a way to move the term away from an abstract, emotion-based meaning to one denoting something solid and measureable.

Confidentiality
Confidentiality is based on confidence – trust and assurance that the organization is protecting sensitive information and systems from unauthorized access and disclosure. This requires the organization to know what information it has that requires protection. It starts with the classification of systems and data according to the level of damage that would occur if the security of that system or data was compromised.
The objective of an attacker is not just to prove that they can get access. They want something. They want the organization’s sensitive data, and they want continued access; they want to “own” the systems and networks of the organization for their own benefit. The pen tester must, therefore, see the objectives of the test as evaluating the ability of the organization to resist compromise, detecting an intrusion, and mitigating any damage that results from an intrusion.
The pen tester is testing the security of the system and ensuring that the core assets of the organization are protected from compromise.
Testing for confidentiality, therefore, is testing whether an unauthorized person can gain access to the organization’s systems and data, and whether an authorized person may be able to commit unauthorized acts.
Integrity
“Integrity” refers to the accuracy and precision of data and systems processing. When an organization relies on the accuracy of data – or the reliability of a process – it must be confident of the integrity of that data and process and prevent improper modification or alteration of that data or process, whether through error, malicious activity or equipment malfunction.
A pen test is always a test conducted at a point in time, but the pen tester must still ensure that the data is not only accurate at the time of the test, but that the controls are adequate to protect it from improper modification in the future, as well. This would mean testing for the ability to make a change or alter a process in a way, or by a person, that should not have been permitted.
Availability
In today’s world of rapid business operations, where decisions must be made both quickly and accurately, the availability of systems and data must also be assured. Where users and customers rely on systems providing data and service in a real-time mode, an outage may have catastrophic consequences. For many organizations, it is simply not good enough to tell customers that their systems are down or that the data they require is currently not available.
The main point is that not all systems and data have the same importance – some systems are critical, while others are simply “nice to have.” Air traffic control systems are extremely critical (as long as the airport is operational), but an automated teller machine (ATM) or automated banking machine (ABM) is not nearly as important. The failure of an ATM is an inconvenience; the failure of air traffic control – for even a few moments – may result in extreme loss of life. Therefore, there is no security solution that is suitable for every need. Each business must tailor its security solution according to factors including the law, customer expectations, financial impact and reputation. When testing the security of an organization and its susceptibility to failure or compromise, the pen tester must relate the tests and the test results to the operational and security environment the organization works in.
The yardstick
By using confidentiality, integrity and availability as yardsticks, an organization can measure how well they are doing (their current level of security) against their desired position (where they need/want to be). Availability, for example, is an excellent yardstick. The organization will need to ask: what is the standard/level of availability the organization requires? How are they currently doing in comparison to that metric or standard? Are the systems and data of the organization meeting the required standard? Are they exceeding the desired standard? Or, are the current levels of availability substandard and inadequate? These questions are critically important, since they allow the organization to put a solid definition on what security means for them. A secure system is a system that provides the levels of confidentiality, availability and integrity required by the organization. Once the organization knows what those levels of security are, and whether or not it is meeting them, it can put in place the steps to address any security deficiencies and allocate the time, budget and resources required to implement its security program. This is why a pen test is so very important – it identifies the current security level of the organization, helps put together the plan to fix any vulnerabilities before an attacker finds those same vulnerabilities and makes the organization a victim of an attack.
The pen tester should not work strictly according to a template or checklist. A checklist is generic, and may be insensitive to the unique characteristics of the organization. Instead, the checklist should be used as a framework and then adjusted accordingly. The pen tester must understand the operational and security environment of the organization, and must measure the security against best practices, standards and the security position the organization is attempting to reach. Some organizations are more cautious than others; others have a larger risk appetite. The pen test must deliver an assessment that is sensitive to that operational environment.
Non-repudiation
Another area sometimes included in the CIA security triad is non-repudiation. Non-repudiation is a very important term in e-commerce and networked operations. Nonrepudiation makes it possible to link an activity to its originator. It ensures that the person that initiated an activity would be unable to later deny that they were the person that committed that act. This would remove their option hide their identity and mask their activity. The pen tester will test the non-repudiation controls to determine whether an attacker would be able to erase log files, masquerade as another user, or set up false user accounts on the system to hide their activity.
Information classification
Not all information, and not all systems, require the same level of protection. Therefore, many organizations will set up a security classification scheme that will identify and label data according to the level of protection it needs. Information that requires higher levels of protection must be labeled and handled appropriately – according to how the data is stored, handled, transmitted, disposed of and displayed. The security controls must be adequate to protect sensitive information from unauthorized changes, disclosure and destruction, and the tests performed should ensure that the data protection controls are working correctly and cannot be easily circumvented by an attacker.
When is security enough?
The inevitable question is, “When is enough security enough?” There is no easy answer to this question. If an organization has had a breach, then there was not enough security – no matter how much they spent on it. If they have not had a breach, then there is always the suspicion that they are spending too much! Pen testers have a responsibility (and some may say a liability) to provide accurate and complete results to the client organization. They must ensure that they completed their work with due diligence and competence and have not provided false or misleading information to the client. There is no one answer to the “enough security” question, and all of the benchmarks and best practices represent only an attempt to define “adequate security.” The pen tester must be able to defend the testing program they have set up. This is why the pen tester may want to base their tests on standards, such as the Payment Card Industry Data Security Standard (PCI DSS), ISO/IEC 27002 or COBIT,® or other such benchmarks.
Risk management
Risk management is the process that allows IT managers to balance the operational and economic costs of protective measures and achieve gains in mission capability by protecting the IT systems and data that support their organizations’ missions.
Risk is a function of the likelihood of a given threat-source’s exercising a particular potential vulnerability, and the resulting impact of that adverse event on the organization.
NIST SP 800-304
We cannot avoid risk – but we must manage it. We operate in a world full of it, but risk is both danger and opportunity. Taking risks may lead to rewards; taking too much risk may lead to loss. In performing a pen test, the tester must understand the risk appetite of the organization: whether the organization tends to minimize risk or embrace it. IT risk is only a subset of business risk5. The danger for a technical pen tester is that they will forget that that risk must be measured, ultimately, from the perspective of the business, and not just in terms of IT-related risk.
As written in the ISO31000, organizations should develop, implement and continuously improve a framework whose purpose is to integrate the process for managing risk into the organization’s overall governance, strategy and planning, management, reporting processes, policies, values and culture6.
Risk justifies controls and controls should be traceable back to risk7. When planning and conducting a pen test, the tester must know the balance between security, risk, business and assurance.
Definitions8
• Threat: the potential for a threat source to exercise (accidentally trigger or intentionally exploit) a specific vulnerability.
• Threat source: either
1. An intent and method targeted at the intentional exploitation of a vulnerability, or
2. A situation and method that may accidentally trigger a vulnerability.
• Threat analysis: the examination of threat sources against system vulnerabilities to determine the threats for a particular system in a particular operational environment.
• Vulnerability: a flaw or weakness in system security procedures, design, implementation, or internal controls that could be exercised (accidentally triggered or intentionally exploited) and result in a security breach or a violation of the system’s security policy.
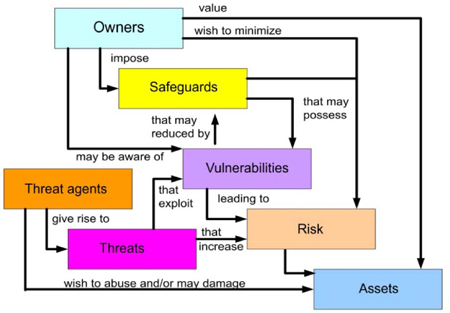
The above graphic is from the Common Criteria9 and is an excellent way to depict the process of risk management.
An asset is anything of value to its owner – including things both tangible (money, property, etc.) and intangible (reputation, confidence, etc.) While the owner wants to protect his assets, an attacker may pose the risk of abusing, damaging or destroying those assets. In order for the threat source to pose a legitimate threat, there must be a way for the threat source to cause the damage – the threat itself (a virus, physical access, equipment failure, etc.) Despite the presence of a threat (a virus, for example), an asset is still not at risk unless there is some way for the threat to damage or gain access to the asset – a vulnerability. Therefore, we can see that a risk is a combination of three main elements: an asset, a threat and a vulnerability. Once the threats and vulnerabilities have been identified, the organization can deploy safeguards and countermeasures to reduce the risk. In nearly every case, it is impossible to eliminate or even reduce a threat – those are often beyond the control of the owner – but it is possible to mitigate the risk by reducing the vulnerability. For example, a virus is a threat written by a threat agent/source to exploit a vulnerability in an application. The owner deploys a patch that closes the vulnerability. This reduces the risk of that virus affecting that asset. It does not remove the threat or affect the threat agent, but it makes the owner’s asset (the application) impervious to the threat. When conducting a pen test, the tester must understand how to identify assets that need protecting, what the threats to those assets are, and what vulnerabilities may exist in the management, technical or operational environment that may allow a threat agent to damage the asset and thereby pose a risk to it.
The threat environment
The environment that the systems and networks of each business operate in changes at an almost daily pace. New technologies are emerging; new methods of business are developing; and the methods of attack used by adversaries are improving – as is the skill and motivation of the attackers.
As every organization undergoes changes to its operations and infrastructure, new risks or opportunities emerge for the attacker. The technologies that enable improved business operations may also present new attack surfaces, introduce new vulnerabilities, and present the attacker with an opportunity to launch a pre-emptive strike before the target organization is ready. The attacker can launch new forms of attack against these technologies before the organization has managed to implement new controls, policies or operational procedures to deal with the new technology. The introduction of wireless internet, smartphones and SCADA® controls can create such a risk. Many organizations were exposed to the risks associated with the implementations of these tools long before they had determined the policies, procedures, standards and baseline configurations that should have been followed in bringing such technologies into the workplace. The same is happening today with web applications. Most organizations are just beginning to realize the risks and security requirements that are associated with developing and deploying web applications – especially those that handle sensitive data or support critical business functions. Insecure web applications are the attackers’ treasure chest.
It is only by conducting regular pen tests and vulnerability assessments that the organization can ensure that their systems, applications and networks remain protected, and that the security controls and countermeasures that are in place are operating effectively.
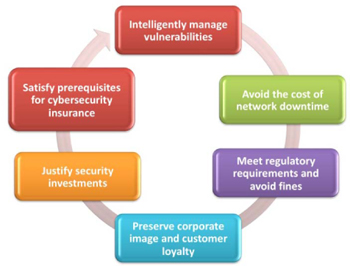
Figure 3: Reasons to conduct a pen test
The ability of an attack to succeed is dependent on several factors: the vulnerabilities, skill and motivation of the attacker, and the presence of a legitimate threat capability (a tool that can be used in the attack). The more skilled and motivated the attacker is, the more likely they are to succeed. This is a threat in today’s world especially, since many attackers are highly skilled and employed by organized criminal groups or foreign governments. This situation requires the pen tester to be all the more diligent in executing a thorough and skilled test and providing accurate, meaningful reports and recommendations to their clients.
Overview of the steps to penetration testing
A penetration test is not a disjointed series of random actions, but rather a targeted and carefully planned series of activities, which build on each other to create a successful attack. As stated earlier, the secret to penetration testing is knowledge: knowing the enemy, knowing the victim, knowing the tools and techniques, and knowing how to use those in an effective manner.
The steps to a penetration test can be defined as follows:
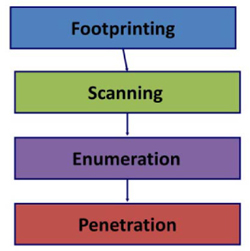
Figure 4: Steps to penetration testing
We can use the analogy of an attack against a medieval castle to make the steps to penetration testing simple and easy to understand.
Footprinting
The first step in attacking a castle is to learn about the castle. Describe it: what are its strengths, weaknesses, its behaviors and its level of alertness?
Footprinting is all about gathering as much information as possible about the target system. This would include determining the attack surfaces of the target system and documenting all the information available from public sources and from surreptitious tests.
Scanning
The second phase of attacking a castle will involve sending in spies and conducting more active searches of the target.
The attacker will now move on to the process of more active probing or scanning. This will highlight some of the characteristics of the system, including ports or services that are open.
Enumeration
The third step is to begin developing the strategy for the attack – this based on knowledge of potential weaknesses or known vulnerabilities. The attacker may select tools to be used in the attack – siege engines, battering rams, catapults and personnel, for example.
Enumeration is the documenting of the system characteristics, which include operating system patch levels, applications running on the system, configurations, user accounts, and any other information that may be strategically important as the attack is planned.
Penetration
The final phase of the attack on the city is the attack itself. During this phase, the attacker will try to exploit the vulnerabilities that were identified and use the tools available to gain access to the city.
Using a variety of tools and techniques, the pen tester will attempt to gain access to the organization’s systems. The attack may be based on a tool, social engineering, or physical security attacks. The pen tester must be creative, methodical, flexible and persistent in order to complete a worthwhile test.
Figure 5: The many facets of pen testing
Once the pen tester has successfully managed to gain access to the system, they will often stop the attack. There is a significant danger that a penetration test will cause system outages and interrupt business operations, so the pen tester must always be careful, be watchful of the ongoing status of the tests, and be ready to work with system administrators to recover the systems if a failure does occur.
Penetration testing versus hacking
The discipline of penetration testing is not to be confused with unethical hacking. A penetration test is an authorized, carefully managed and structured analysis of the security of a system or network, and is done to support the organization that requests it. An unethical hack is an attack against a government, military, corporation or individual that is not authorized by the victim, and may be done with malicious intent. Many individuals and groups (including protestors, criminal organizations, script kiddies, and unethical computer specialists) participate in hacking for various reasons, ranging from financial gain, competitive advantage and military strategy, to revenge, ideology and ego.
The purpose of a penetration test is to simulate the type of attack that an unethical hacker would conduct in order to determine if the client is vulnerable to a hacking attack. The pen tester, therefore, will use many of the same tools and techniques used by an unauthorized attacker. The pen tester must, however, be careful to act within the authorized bounds of the test and respect the privacy and integrity of the client.
Many hackers are brilliant and determined to be successful; they may be very well educated, and supported with the latest tools and equipment. Therefore, the pen tester must realize the seriousness of their work. The pen tester must be thorough and always keep up with an ever-changing threat environment.
Benefits of penetration testing
Conducting a penetration test may provide many benefits for an organization. These may be immediate financial savings in insurance or liability costs, or long term benefits – such as avoiding costly downtime or damage to the reputation of the organization.
In the past few years, major breaches of organizations, such as TJX and the US Department of Veterans Affairs, have cost those organizations in the hundreds of millions of dollars – money that could have been saved and put to much better use if the organizations had been aware of the vulnerabilities that they had. In both the above cases, the attacks would have been easily avoided by way of a few simple changes.
Some of the key benefits of penetration testing include:
• Preservation of customer loyalty
• Better vulnerability management
• A robust security program
• Avoidance of downtime costs
• Meeting of regulatory compliance requirements
• Protection of corporate image and reputation
• Justification of security measures
• Fulfilment of audit requirements.
Summary
Throughout this book, we will look at risk management, threat and vulnerability identification, and detail the steps to take to conduct a penetration test. We will examine the use of some of the most popular and effective tools available today and examine how to conduct an attack against various types of systems, applications and networks. This effort will build towards a successful penetration test and deliver a beneficial result for the client.
Key learning points
The key learning points from this chapter are:
• A penetration test is a business-oriented activity: it must never be conducted without first obtaining the approval of the organization, determining the scope, clarifying the reporting requirements, and selecting the penetration testing techniques, schedule, and plan.
• A penetration test is not simply the use of tools and is more than a technical operation.
• A penetration test must be thorough and executed with skill and discipline.
• A penetration test is conducted through a series of steps that help ensure a successful result.
Questions
1. What is the purpose of a penetration test?
a) To exploit network vulnerabilities
b) To provide a report to management on the effectiveness of their security program
c) To test the effectiveness of a security control
d) To measure the level of risk to an organization.
Answer: B
Answers A, C, and D are some of the results of the tests, but the main purpose of a test is to support the governance and better management of information systems.
2. Who should conduct a penetration test?
a) Skilled, authorized professionals
b) Information technology staff
c) Outsiders with a love for hacking
d) Internal staff with an interest in security.
Answer: A
The other answers are not correct, since a penetration test conducted by unskilled, unethical or unauthorized persons can result in serious damage to the organization.
3. What is the first step in a penetration test?
a) Probing any potential vulnerabilities
b) Exploiting system flaws or misconfigurations
c) Gathering data about the client
d) Reporting on potential vulnerabilities to management.
Answer: C
This is the first step. The other steps will come later in the testing sequence.
4. A penetration testing report should be presented to:
a) The management team of the organization
b) IT staff and management only
c) Authorized personnel only
d) All staff.
Answer: C
A penetration test is a confidential report that may list serious potential vulnerabilities; it should only be given to authorized personnel.
5. A penetration test is the examination of:
a) Technical controls
b) Vulnerabilities in software
c) Gaps in user training
d) All controls related to information systems.
Answer: D
The penetration test is the examination of all types of controls within the authorized scope of the test.
1 www.f-secure.com/weblog/archives/00002226.html.
2 http://securityblog.verizonbusiness.com.
3 http://dictionary.reference.com.
4 NIST SP 800-30: Risk Management Guide for Information Technology Systems (2002), www.csrc.nist.gov/publications/drafts/800-30-rev1/SP800-30-Rev1-ipd.pdf.
5 The Risk IT Framework, www.isaca.org.
6 ISO/IEC 31000:2009 – Risk management – Principles and guidelines.
7 SABSA – Sherwood Applied Business Security Architecture, www.sabsa.org.
8 NIST SP800-30: Risk Management Guide for Information Technology Systems (2002).