I don’t need a hard disk in my computer if I can get to the server faster.… Carrying around these non-connected computers is byzantine by comparison.
—Steve Jobs
The CLOUD services companies of all sizes.… The cloud is for everyone. THE CLOUD IS A DEMOCRACY.
—Marc Benioff, CEO – Salesforce
One of the fast-growing trends in the IT industry today is the widespread use of cloud computing. Developers are using cloud computing platform to develop tools, services, and products for a variety of fields.
Cloud computing is the on-demand delivery of computing services such as servers, storage, databases, software, networking analytics, and other IT resources over the internet.
This type of computing relies on shared resources in place of having local servers or other devices to run operations.
Cost – The expense of buying hardware and software gets eliminated, saving the customer a ton of money.
Speed – Cloud computing services are customized as per needs of the client; this saves planning and testing of systems and boosts the speed of operations.
Security – Cloud providers have strong security policies and protect the data and programs of their customers.
Performance – Cloud providers use high-end systems with premium hardware, the latest software, and qualified engineers to provide their customers with a productive platform.
Cloud Computing models
Cloud Forensics
Server-Side Forensics
Client-Side Forensics
Forensics as a Service (FaaS)
Cloud Computing Models
Software as a Service (SaaS) – This model of cloud computing provides the users the facility of utilizing a cloud service provider’s software application running on cloud infrastructure. The cloud service provider owns all the layers, and the customer only has indirect control over the underlying operating infrastructure. This model is very cost effective for the customer as the maintenance cost is reduced. Popular examples include Google Docs, Microsoft 365, Citrix, etc. From a forensic perspective, SaaS model is a forensic goldmine. SaaS programs such as Google Docs have a nature of recording every event and maintaining an extensive log. From user logs to timestamps, all the details are of high value in a forensics investigation.
Platform as a Service (PaaS) – This model allows the user to deploy their own application with the help of the software components built into the middleware. PaaS offers quick and cost-effective solution for development and testing of customer-deployed applications. Full control is given to the customers on the application layer. Google App Engine, Heroku, and Apprenda are examples of the PaaS model. In the context of forensics, customers can perform extensive logging, which can help the investigators.
Infrastructure as a Service (IaaS) – As the name suggests, this model provides the entire infrastructure for cloud computing. This includes networking components, physical/virtual machines, firewalls, etc. Basically, a user will be outsourcing an entire IT ecosystem, which will be provided as a service over the internet. The cloud service provider manages the entire setup in direct response to customer requests. Microsoft Azure, Amazon Web Service (AWS), and Google Computer Engine are some popular examples of the IaaS model. This model provides the capabilities of taking snapshots of the physical memory and disk of virtual machines when forensic investigation is required.
Defining Cloud Forensics
Cloud Forensics is a subdiscipline of Digital forensics, which revolves around cloud computing. It is also recognized as a subset of network forensics as investigators deal with public and private networks, and cloud computing is based on broad network access.
For forensics investigators, Cloud forensics is a daunting task due to the various challenges, something like a Nightmare On Forensics Street.
Technical – It encompasses the tools and procedures required to perform forensic investigation in the cloud. Data collection, evidence management, and live forensics are performed here.
Organizational – It covers the organizational aspects of forensics and includes entities such as cloud service providers, legal advisors, customers’ incident handlers, and objects such as binding service-level agreements (SLAs), policies, etc.
Legal – It covers the development of agreements and regulations to ensure forensic activities do not breach laws and regulations in the jurisdiction where the forensics services are deployed.
Differences Between Traditional Cyber Forensics and Cloud Forensics
Stage | Process | Traditional Forensics | Cloud Forensics |
|---|---|---|---|
Identification | Identification of event | Multiple tools available | Few tools available |
Preservation | Securing and documentation of crime scene | Yes | No |
Evidence collection | Physical | Virtual | |
Acquisition | Acquisition Time | Slow | Fast |
Hash | Slow | Fast | |
RAM acquisition | Yes | Situational | |
TimeStamp | Precise | Complex | |
Analysis | Data recovery | High Possibility | Low possibility |
Availability of Forensic software | Yes but are expensive | Yes and are relatively cheaper | |
Presentation | Documentation of evidence | Acquired evidence | Data from multiple sources |
Declaration | Common | Difficult to put forward to a judge |
Server-Side Forensics
Server logs
Application logs
Database logs
User Authentication logs
Access information
A major problem with server-side forensics is the physical inaccessibility and unknown location of data. In case of a highly decentralized cloud environment, data might be spread across the multiple data centers and also located at different geographic locations.
Live forensics is a tough task to perform on the server side due to time synchronization. In cases of an audit, timestamps must be recorded carefully with reference to the time synchronization settings of the server.
Role of Cloud Service Provider
Most CSPs will only keep a limited number of backups because of the sheer volume of data and users within the cloud environment.
In case of an incident, the cloud provider will focus on restoring the service rather than preserving the evidence.
Due to potential damages upon their reputation, some CSPs may not report the incident or cooperate in an investigation.
The location uncertainty of the data makes the response time to a digital evidence request extremely challenging.
Client-Side Forensics
Statistics show that cybercrime mostly occur on the client side, and therefore evidence identification and collection are a vital part of cloud forensics. Most of the forensic techniques are developed for client forensics. Moreover, client systems are easier to access and, in some cases, the only option when forensic investigation is to be performed.
Traces found in registry
Log files
Database files
User accounts
Synchronization logs
The use of cloud storage platforms such as Dropbox, Google Drive, Microsoft OneDrive, Evernote, etc., is popular and an important aspect of client-side forensics. These applications contain the most private and important data that a user wishes to keep safe such as photos, documents, even cryptocurrency wallets. These programs leave important artifacts on the system that are important to forensic investigators. The logs of these programs can be used to create a Timeline and can be used for Event reconstruction.
Challenges in Cloud Forensics
Collection of evidence by the forensics investigator as there is a strong possibility the virtual instance the victim was using stands deleted or in use by a totally new user at that point in time.
Was the CSP providing the services using their self-owned infrastructure, or was it outsourced from another CSP? In that case, what were the SLAs signed by the two parties in the context of security and forensics attributes.
What policies define the retentions and backups of any forensics attributed data at the time of a cyber incident by the CSP.
Retrieving erased data in the Cloud.
Synchronization of date/timestamps.
Real-time traffic analysis.
Data backup and mirroring.
Reconstructing the crime scene – includes evaluating the context of a crime scene and the physical evidence found there and trying to identify what occurred and in what order it occurred.
Artifacts in Cloud Forensics
There are some important areas and artifacts to examine in cloud forensics.
Log Files of Browsers
Cloud storage is basically a web-based service; therefore, it is important to collect and analyze the internet history. Browser log files are stored in the Profile directory consisting of cache, cookies, history, and downloaded files. The cache includes HTML files, XML files, text files, download times, download files, and data sizes. Cookies possess information about hosts, paths, cookie modification and expiration times, names, and values. A downloads list consists of local paths of downloaded files, downloaded URLs, file sizes, and unsuccessful downloads.
Physical Memory
Physical memory of a device contains information such as user IDs and passwords that were used to log in to a particular service. In a live system, it is important to collect the physical memory dump before imaging the device.
Registry
The Windows Registry remains one of the favorite places for cyber forensic experts to obtain valuable information. Many cloud apps create an entry in the Windows Registry.
For Mobile Devices
iOS – Both Amazon S3 and Dropbox create a SQLite database file. While Amazon S3 leaves a bucket file with the timestamps, Dropbox leaves a ‘Dropbox.sqlite’ file with all its details.
Android – In Android OS, a similar system is employed by these apps. The downloaded files from the cloud app are stored on the device with details about login and full path in which the app is installed. In Android devices, users mostly store data on their external SD card, and imaging and analysis of the device help the investigators to obtain these files.
Use of Cloud Forensics
Cloud forensics is three dimensional (as discussed in the cloud forensics section of this chapter).
Investigation – Used to investigate cloud-related incidents.
Troubleshooting – Using forensic techniques to resolve issues such as locating data files, hosts, etc.
Data Recovery – In case of data recovery, forensics has plenty of tools to assist users.
Log monitoring – collection and monitoring of logs.
Forensics as a Service (FaaS)
This model of cloud computing focuses on providing forensic services over the cloud. FaaS is a newly developed subset under cloud forensics, which is becoming an accepted step forward. The rise of IT and cloud computing has also led to increased requirements of forensic services. Cloud antivirus programs have become successful and popular as its developers showcased its advantages. Cyber forensic experts believe that even cloud-based forensic services have lots of advantages and will be widely accepted. Terremark is one such entity that provides FaaS.
Virtual Machine Introspection (VMI) is a technique that is helpful for debugging or forensic analysis. It is used for monitoring the runtime state of a system-level Virtual Machine. Terremark uses VMI for monitoring, management, and security of their vSphere cloud computing offering.
FaaS should be considered with IaaS, PaaS and SaaS. Cloud forensics gives a new direction and scope to digital forensic investigation, and it is not just confined to cloud crime; it can be useful in other digital forensic investigations as well.
The emerging delivery models include services delivered through the Cloud, and start-up information security companies play as pure CSPs. It includes providing security only as a cloud service and not as traditional client/server security products for networks, hosts, and/or applications. Forensics as a Service make use of massive computing power to facilitate cybercrime investigations on all levels.
Instance Gathering Process (IGP) – will have built-in modules to address timestamps, hashing tools, tools for aggregating Access Control, and Centralized log monitoring records.
Instance Sample verification – Each instance sample is then taken for verification against an agreed-upon standard. This standard is dynamic in nature due to the nature of the cloud. Upon completion of verification, a hash value is taken and logged.
Dedicated CSP Forensic Storage – These instances are stored in an encrypted state in dedicated storage.
Case Study: Google Drive Investigation
Google drive is a cloud storage service developed by Google. It allows its users to store their files, synchronize their files across devices, and share files. It also provides 15 GB of free storage.
Forensic artifacts in Google Drive investigation
Google Drive client is installed inside | C:Program FilesGoogleDrive |
The default folder used for syncing files | C:Users<username>Google Drive |
Different keys and values created inside the registry | SOFTWAREMicrosoftWindowsCurrentVersionInstallerFolders SOFTWAREGoogleDrive NTUSERSoftwareMicrosoftWindowsCurrentVersionRunGoogleDriveSync NTUSERSoftwareClasses From the registry we can obtain: • Installed version • User folder |
Sync_config.db | The Sync_config.db is a SQLITE3 DB which contain profile configuration like: • Client version installed • Local Sync Root Path • User Email |
Snapshot.db | The Snapshot.db is a SQLITE3 DB that contains information about local and cloud entries • Cloud_entry table • File name • Created (UNIX Timestamp) • Modified (UNIX Timestamp) • URL • Checksum (MD5 hash) • Size • Shared • Local_entry • File name • Modified (UNIX Timestamp) • Checksum (MD5 hash) • Size |
- 1.
- 2.
Download Google Drive on your System. You can download it from:
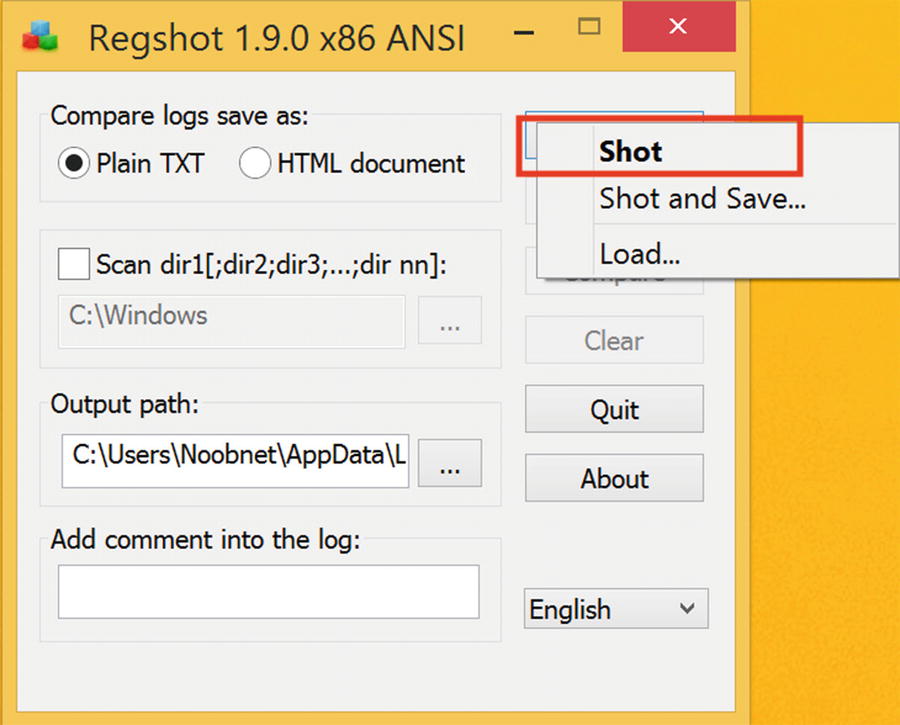
- 3.Take the second snapshot of registry (Figure 8-2).
 Figure 8-2
Figure 8-2The second snapshot
- 4.
Click on Compare.
- 5.We can see added entries in ~res file (Figure 8-3). We can conclude that Google Drive is installed on the system.
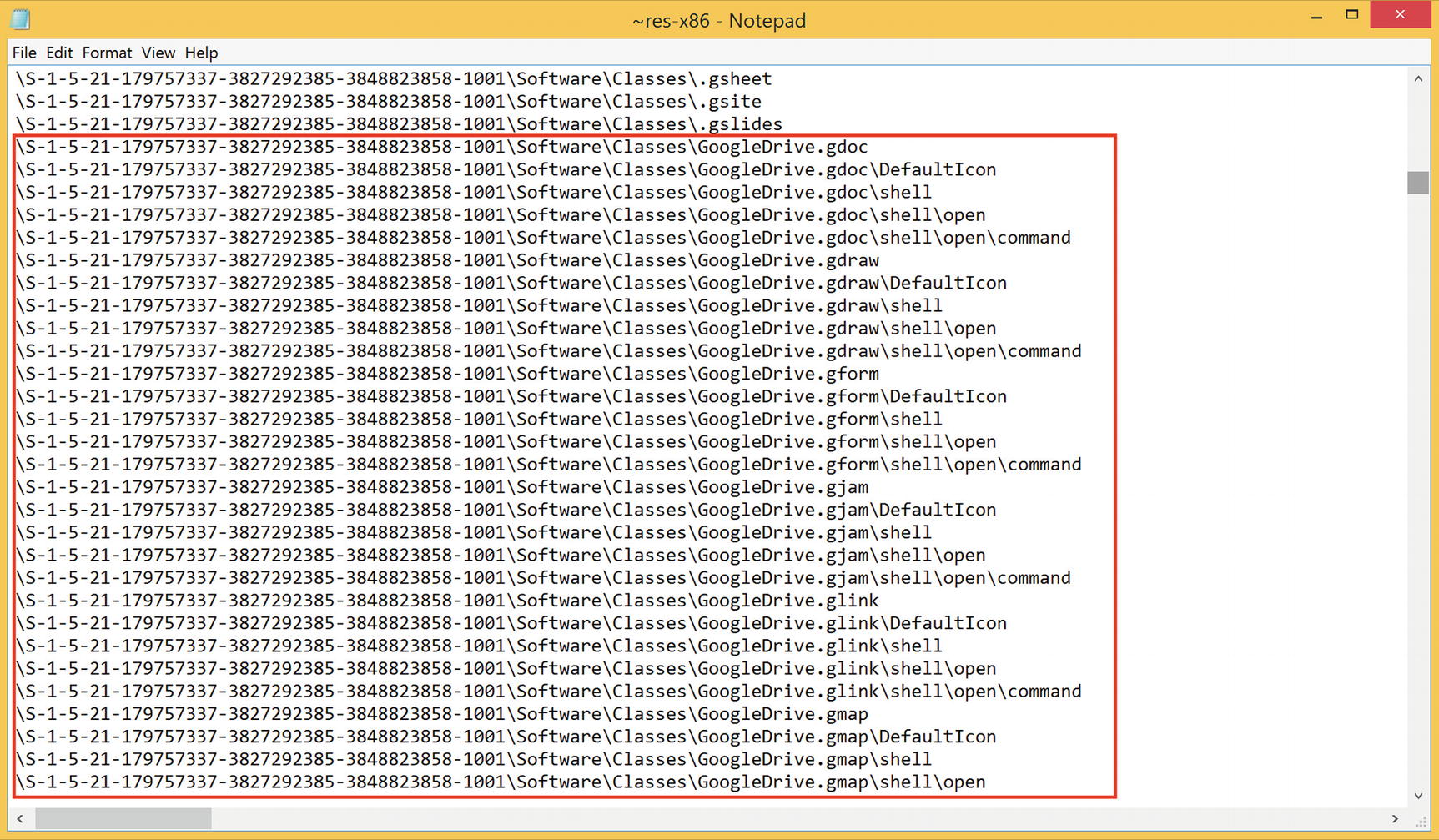 Figure 8-3.
Figure 8-3.Evidence that Google Drive is installed
- 6.
When you download Google Drive on your personal system, it will allow you to sync your Google Drive cloud storage with your computer. You can either sync the entire Drive or just specific files and folders. These are treated as local files on the computer. The default folder for the sync folder on Google Drive can be found at:
C:UsersusernameGoogle Drive - 7.
Let’s check the Registry to see if the sync process has started automatically with the user’s login (Figure 8-4). The entry to view is:
ComputerHKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun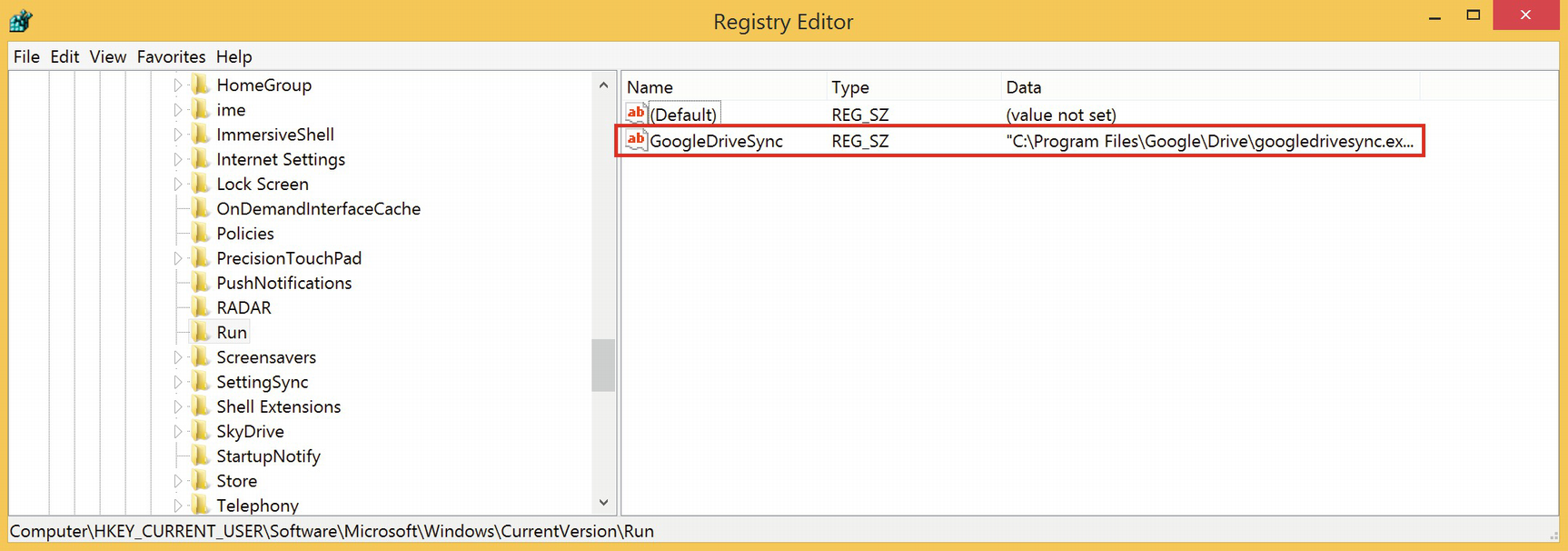 Figure 8-4.
Figure 8-4.Checking the sync process
- 8.
Location of Google Drive in Window’s Registry is as follows. We can see that Google Drive is installed on the system, and its version and the path of Installation are also shown here (Figure 8-5).
ComputerHKEY_CURRENT_USERSoftwareGoogleDrive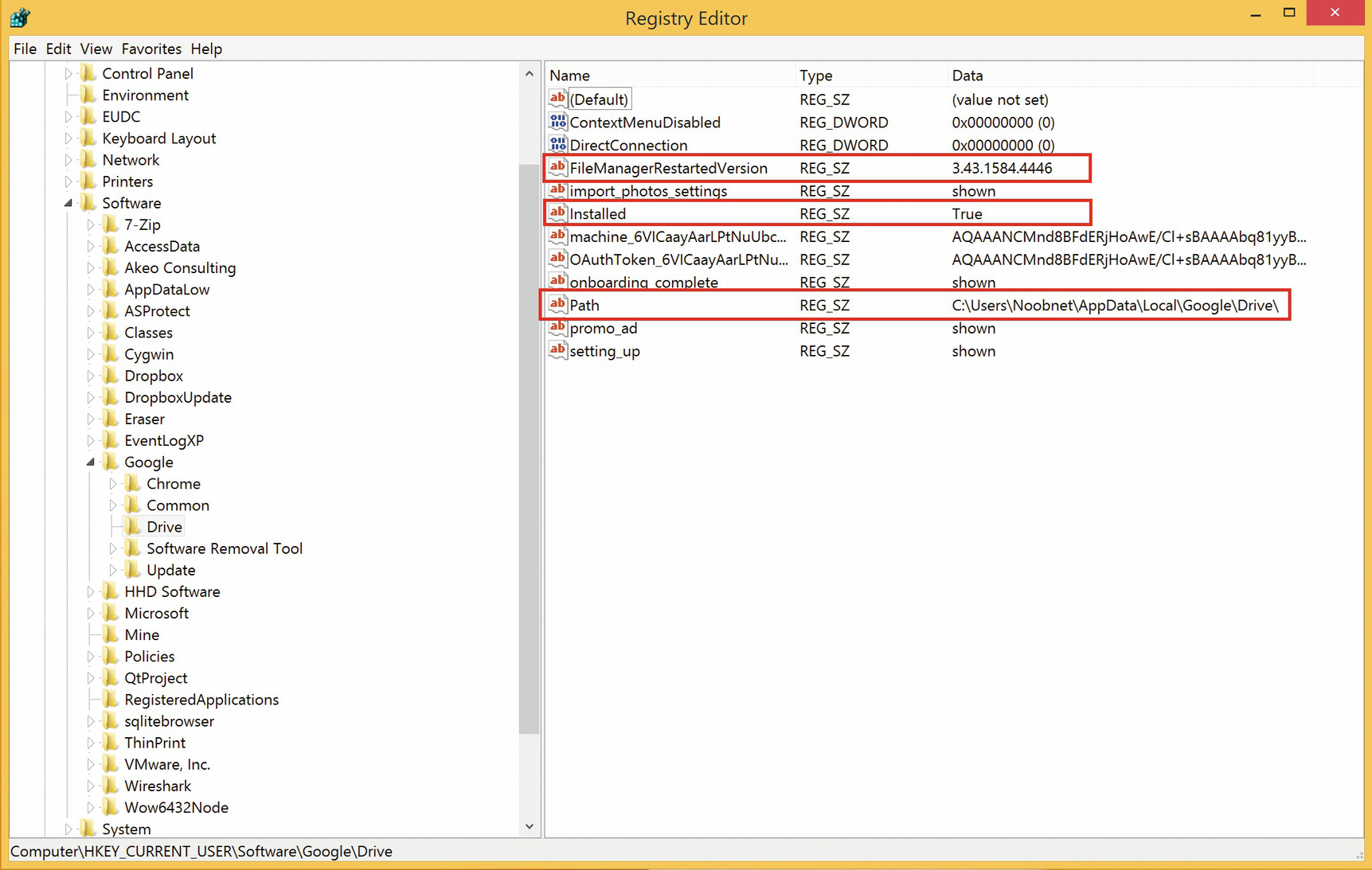 Figure 8-5.
Figure 8-5.Google Drive Registry entries
- 9.
Under C:UserusernameAppDataLocalGoogleDriveuser_default you will find a bunch of SQLite databases. For example, sync_config.db, device.db, uploader.db and snapshot.db.
- 10.Open sync_config.db. We can see highest app version, sync root path, user email id, and lots of other information (Figure 8-6).
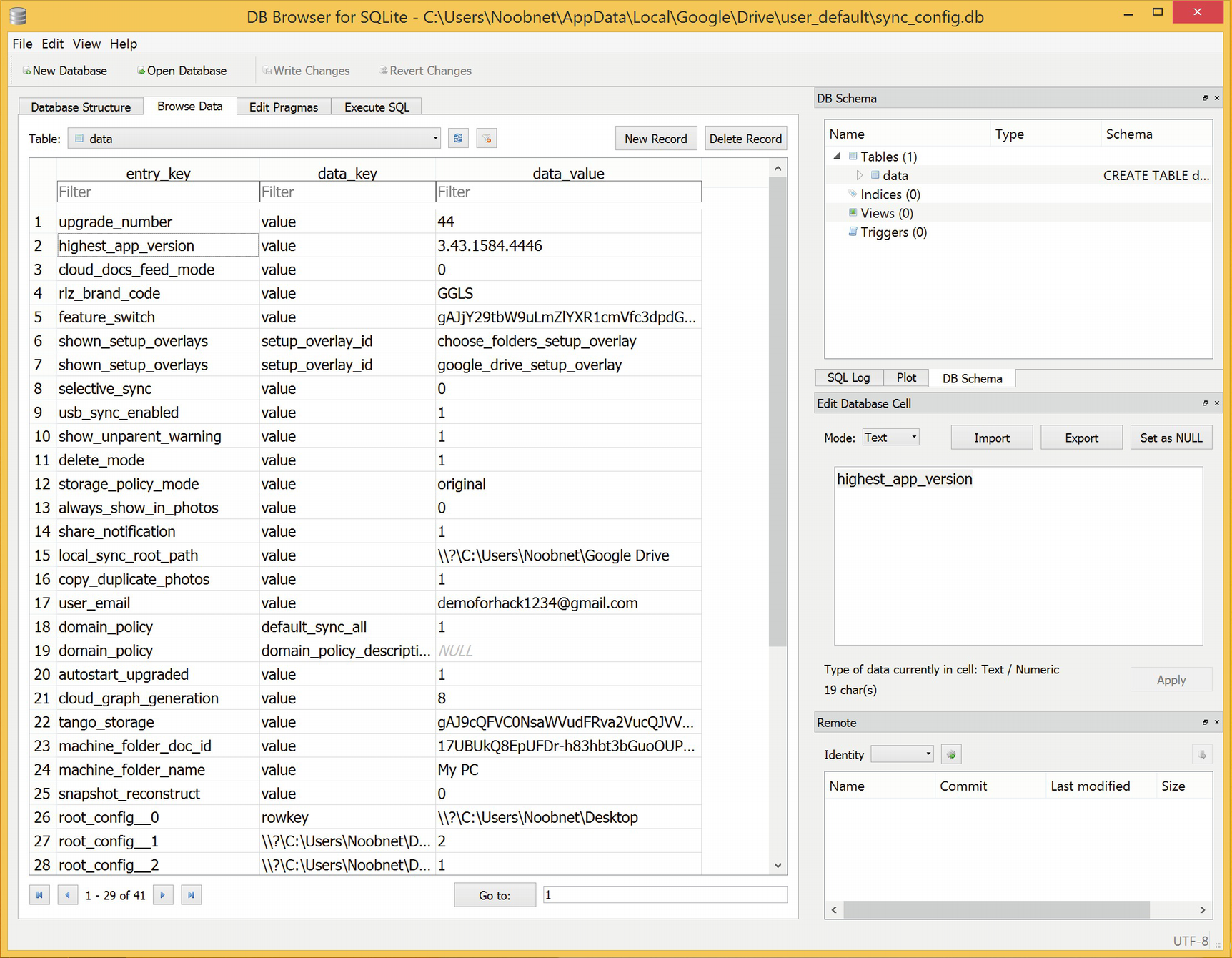 Figure 8-6.
Figure 8-6.sync_config.db details
- 11.Similarly, we can open snapshot.db and its local_entry table. Here we can see filename, their size, modified timestamp, etc., of all the files present on our Google Drive and its sync folder (Figure 8-7).
 Figure 8-7.
Figure 8-7.snapshot.db details
- 1.
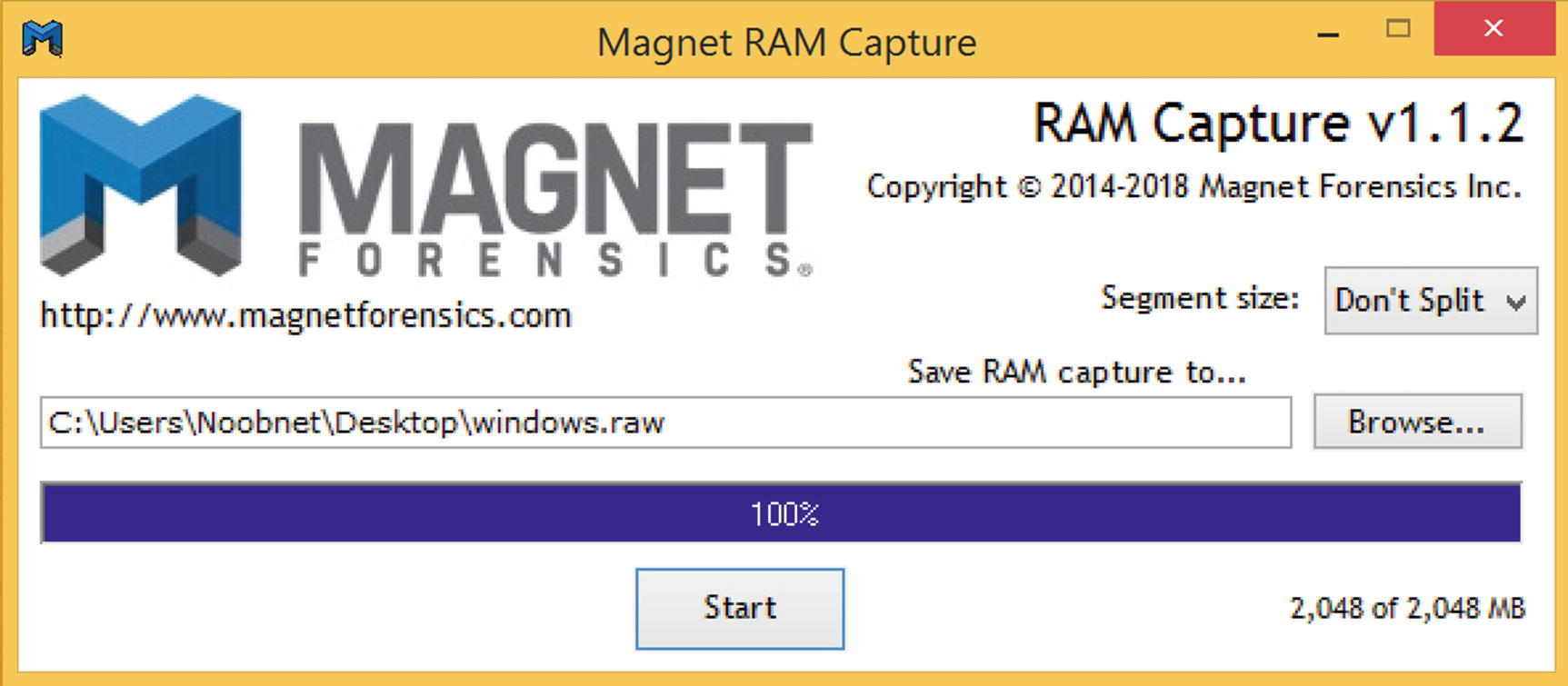
RAM Capturer tool is used to extract the entire contents of a computer’s volatile memory and it creates a .mem file. Let’s create a .mem file of the entire system that can be used in the next step for analysis. Make sure the Google Drive client is running processes in RAM and run the tool.
- 2.Open your .mem file (here 20181217.mem) captured using the RAM Capturer tool from the previous step in your HxD hex editor for analysis (Figure 8-8).
 Figure 8-8.
Figure 8-8.The RAM dump
- 3.Find the user’s email id search user_emailvalue string in a hex editor (Figure 8-9). Here the email account is [email protected].
 Figure 8-9.
Figure 8-9.The user’s email
- 4.To check the version of Google Drive client, search the highest_app_versionvalue string (Figure 8-10). Here it is 3.43.1584.4446
 Figure 8-10
Figure 8-10The client version
Case Study: Dropbox Investigation
Dropbox provides 2.5 GB of free cloud storage, and we can access Dropbox from anywhere across the world as long as we have an internet connection on the device we are trying to access. Dropbox is used in two ways: either we download the Dropbox client on to our machine, or else we use it through a web portal where you can log on to the Dropbox account. One should know about the Dropbox policies before starting to investigate. But again, it depends from case to case. Once an investigator goes through the Standard Operating Procedure (SOP) then it won’t create any issues during the litigation of a particular case where Dropbox was used during the crime.
All the disputes that arise from the contract are under the Jurisdictions of the Courts of the service providers’ country. Dropbox provides facilities for the recovery of your deleted data so that you can recover deleted data, but data should not be older than 30 days in the free version. But in a commercial paid version, all data can be recovered.
Forensic artifacts in Dropbox investigation
Dropbox client is installed inside. | C:Users<username>AppDataRoamingDropbox |
The default folder used for syncing files. | C:Users<username>Dropbox |
Filecache.dbx | C:Users <username> Application DataDropboxinstance1 Filecache.dbx is an encrypted database and the decrypted filecache.db contains: • Server path • Local file name • Local creation time • Local modified time • Local size |
Different keys and values created inside the registry. | HKLMSOFTWAREMicrosoftWindowsCurrentVersionExplorerShellconOverlayIdentifiersDropboxExt(n) HKLMSOFTWAREMicrosoftWindowsCurrentVersionUninstallDropbox HKLMSOFTWAREDropboxInstallPath HKLMSOFTWAREDropBoxClientVersion From the registry we can obtain: • Installed Location • Installed version |
- 1.
Install Access Data FTK imager and open it. Then Click on File ➤ Add Evidence Item.
- 2.
- 3.Go to Program files ➤ Dropbox ➤ Update ➤ Install. We can see here the date and time of Dropbox installation on this Virtual Machine (Figure 8-12).
 Figure 8-12
Figure 8-12Dropbox installation details
- 4.We can see here the prefetch files containing information about the Dropbox executable files, Dropbox sample files, and Enron test data file names (Figure 8-13).
 Figure 8-13
Figure 8-13Dropbox details
We’ll use Magnet Forensics RAM Capture tool to capture memory of the system. This tool is a free imaging tool designed to capture the physical memory of a suspect’s computer. Here we will create a .raw file for analysis. You can download this tool from https://www.magnetforensics.com/free-tool-magnet-ram-capture/ .
- 1.
- 2.Here we will use the HxD tool to view windows.raw image. Now we search the userdisplayname string to find the logged-in username. Here we can also see the email address of the user (Figure 8-15).
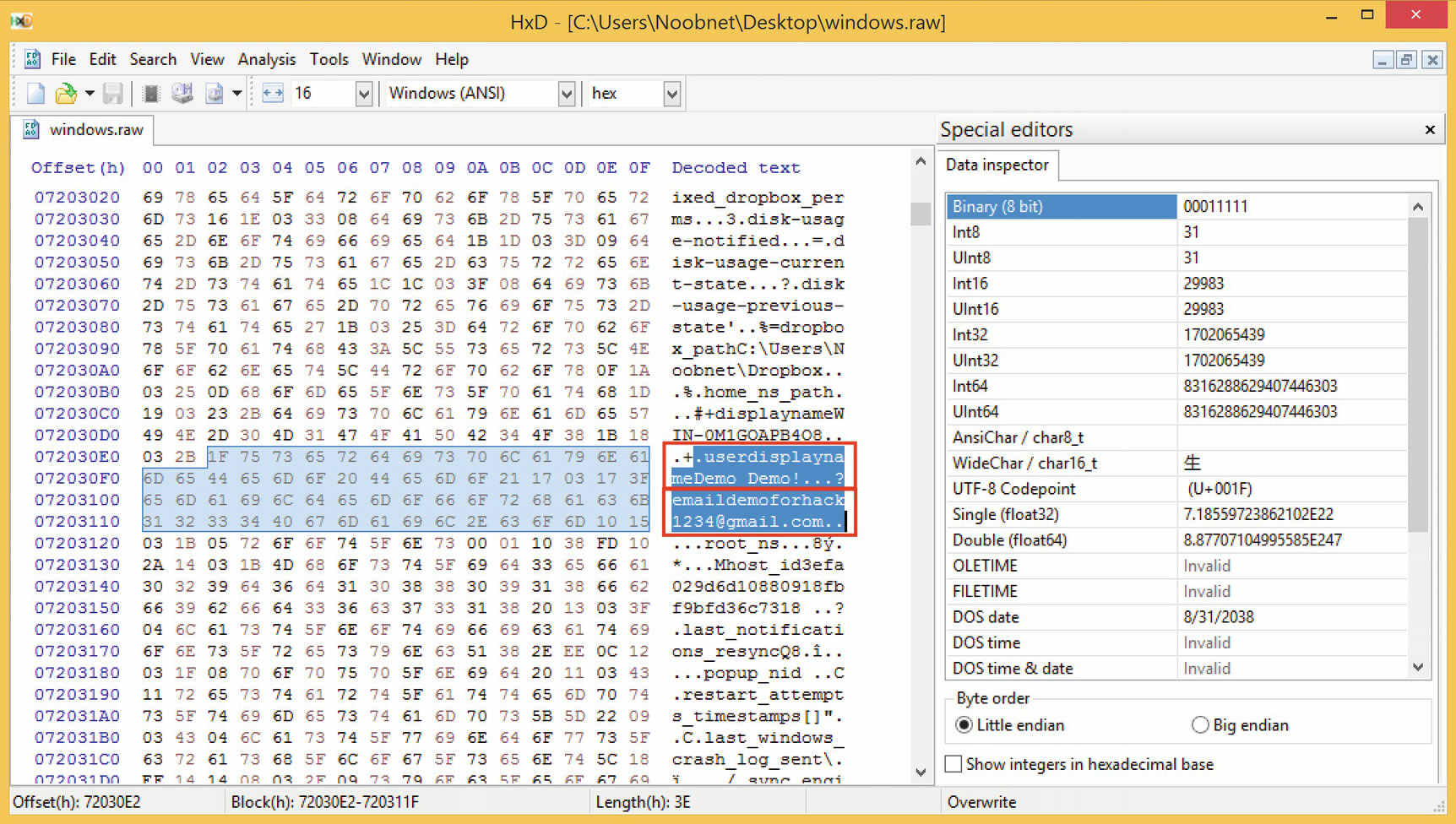 Figure 8-15.
Figure 8-15.The user’s email address
The investigator also captured Network traffic using Wireshark and saved it in db.pcap file. Now we will open this db.pcap file in Network Miner for analysis (see Chapter 6 for more on Network Miner). Here we can see that the suspected Device tried to access the Dropbox site under host section.
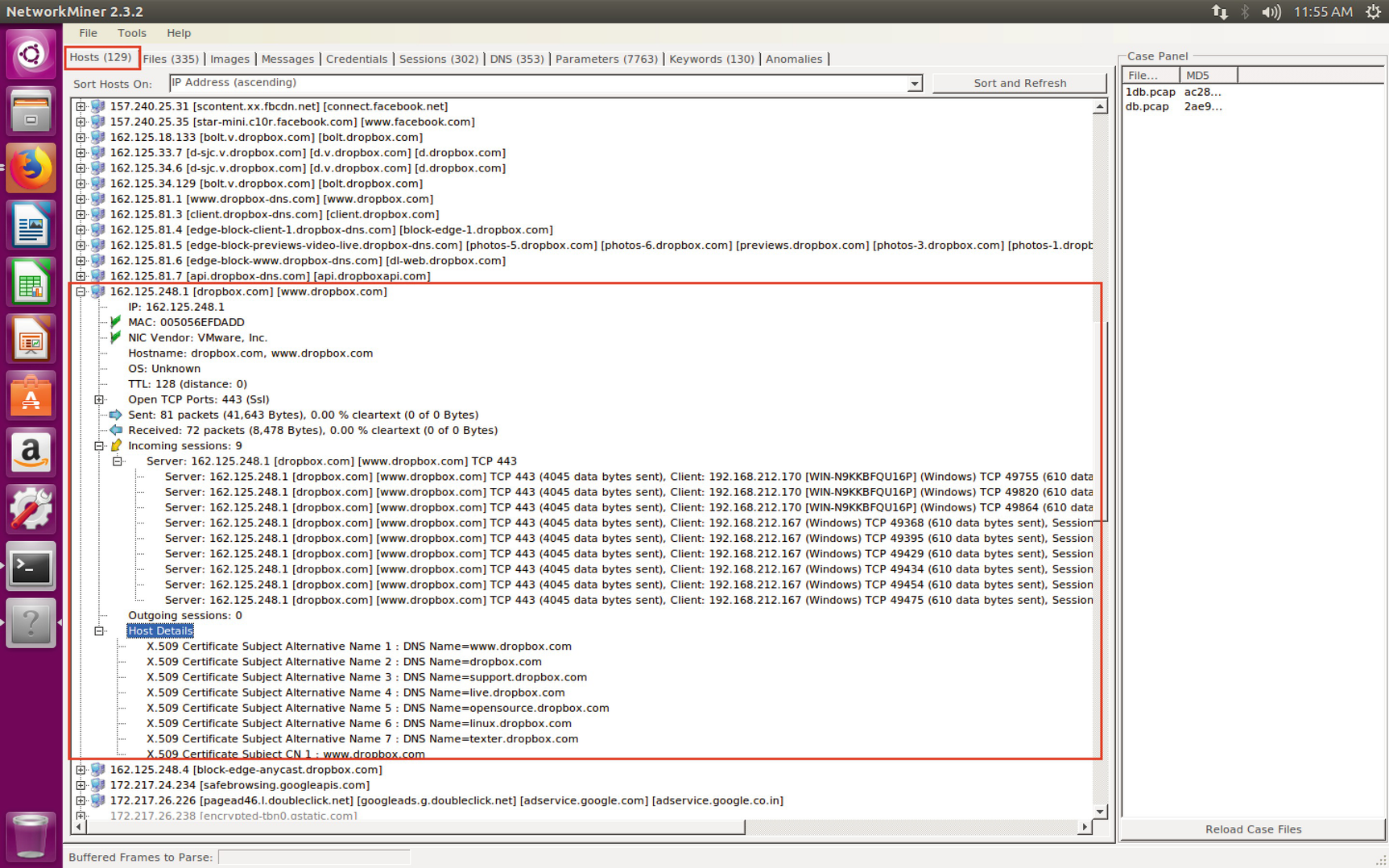
Network traffic for Dropbox
WhatsApp Forensics
In today’s tech savvy generation, many companies are allowing their employees to use their own smartphones both for work and their personal use. There are possibilities that proprietary or confidential information may be being unknowingly leaked as users take to using their smartphone cameras to take photos of documents and written contents – potentially risking disclosure of such information to the public. Smartphones have replaced computers for scanning data, thus reducing the need for organizations to have Whiteboard printouts (thus saving money). With this, a huge risk prevails where a user might not intentionally leak information. WhatsApp does provide for exchange of information during in-party calls, potentially allowing confidential data to be circulated.
WhatsApp is one of the most popular messaging platforms that is available across all platforms today. It is a very versatile app that does not only allow users to chat but also to share pictures, videos, contacts, documents, and voice messages. WhatsApp also allows users to have VoIP calls and Video Calls with their contacts.
Globally there are millions of users on the WhatsApp platform. We can say that it is used by nearly everybody due to free availability, along with its ease of use and convenience. Previously WhatsApp messages were sent in clear text between two clients, and all these messages were stored on their server until the messages were read by the recipient. WhatsApp’s implementation of end-to-end encryption follows Apple’s debate with the FBI over unlocking a terrorist’s iPhone. During this dispute, the WhatsApp co-founder Jan Koum said that he strongly supported Apple’s stand in its efforts to protect users’ data. In 2016, WhatsApp rolled out its end-to-end encryption feature to keep the chats of users safe and secure. WhatsApp uses XMPP protocol during the transfer of messages from one client to the other.
WhatsApp also allows users to back up their chats on their cloud storage. When forensic investigators obtain data from the cloud, chat backups are an important evidence to procure and proceed with investigations. Chat backups will help the forensic investigators to study about the owner of the device and also create timelines.
- 1.WhatsApp message databases contain chats, contacts, photos, document files, etc. Messages are stored in a systematic manner with contact details, timestamps, and media linked to the chats.
WhatsApp stores messages in an encrypted database on the device. The main file for chats is msgstore.db. It uses ‘crpyt’ format for its encrypted databases. This ‘crypt’ format gets updated from time to time; currently WhatsApp uses ‘crypt12’. However, the decryption key is present in the same folder as the chats that are used to decrypt the databases.
Case Study: WhatsApp Database Extraction
Here we will decrypt the WhatsApp database for a forensics investigation using open source tools. Titanium Backup is the most powerful tool for backup on an Android device. You can back up and restore your apps, data, and Market links, including all protected apps and system apps, and external data on your SD card. It needs rooted Android 1.5-8.0+ (ARM, x86, MIPS).
- 1.
Install WhatsApp on the Android device.
- 2.
Open WhatsApp and go to Settings ➤ Chats ➤ Chat Backup to back up your WhatsApp.
- 3.
Once you back up, you can see that msgstore.db.crypt12 file is created in File Manager ➤ sdcard ➤ WhatsApp ➤ Databases.
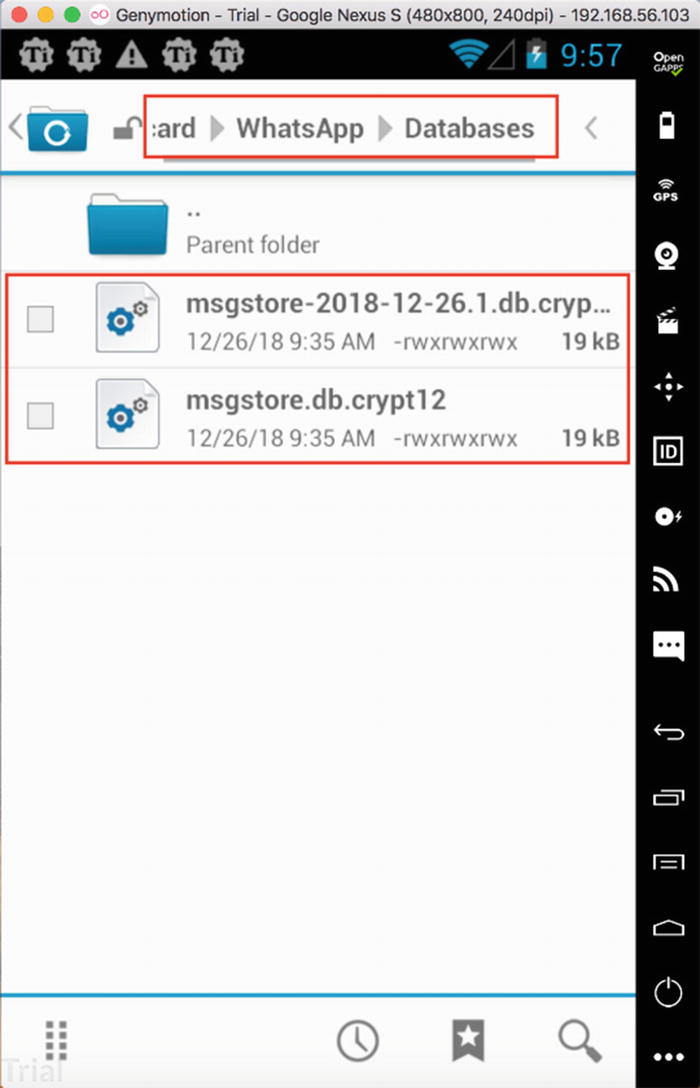
The encrypted database
- 4.
Open Titanium Backup, and click on Backup/Restore.
- 5.
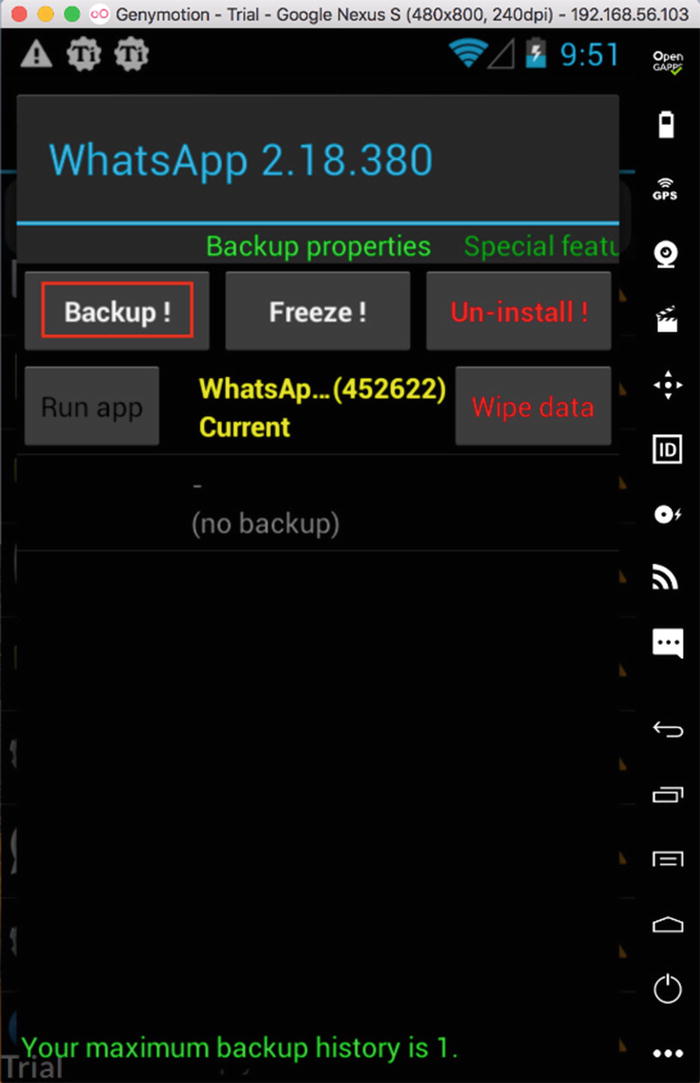
- 6.Here you can see that WhatsApp (containing files, databases, images, etc.) is backed up successfully (Figure 8-19).
 Figure 8-19.
Figure 8-19.The successful backup
- 7.
You can see these backed-up files in the File Manager ➤ sdcard ➤ TitaniumBackup folder.
- 8.Export these files to your Windows OS for further analysis. This backup is stored in a .tar.gz file format (Figure 8-20).
 Figure 8-20.
Figure 8-20.The files to export
- 9.
Then we use the site https://www.whatcrypt.com/ to decrypt the WhatsApp Database.
- 10.Select ‘Upload Your Crypt 6-12 Key’ and click on ‘Choose File’ Option (Figure 8-21). The WhatsApp database is encrypted and thus needs a key to decrypt it. We can find this key in our Titanium backup .tar.gz file.
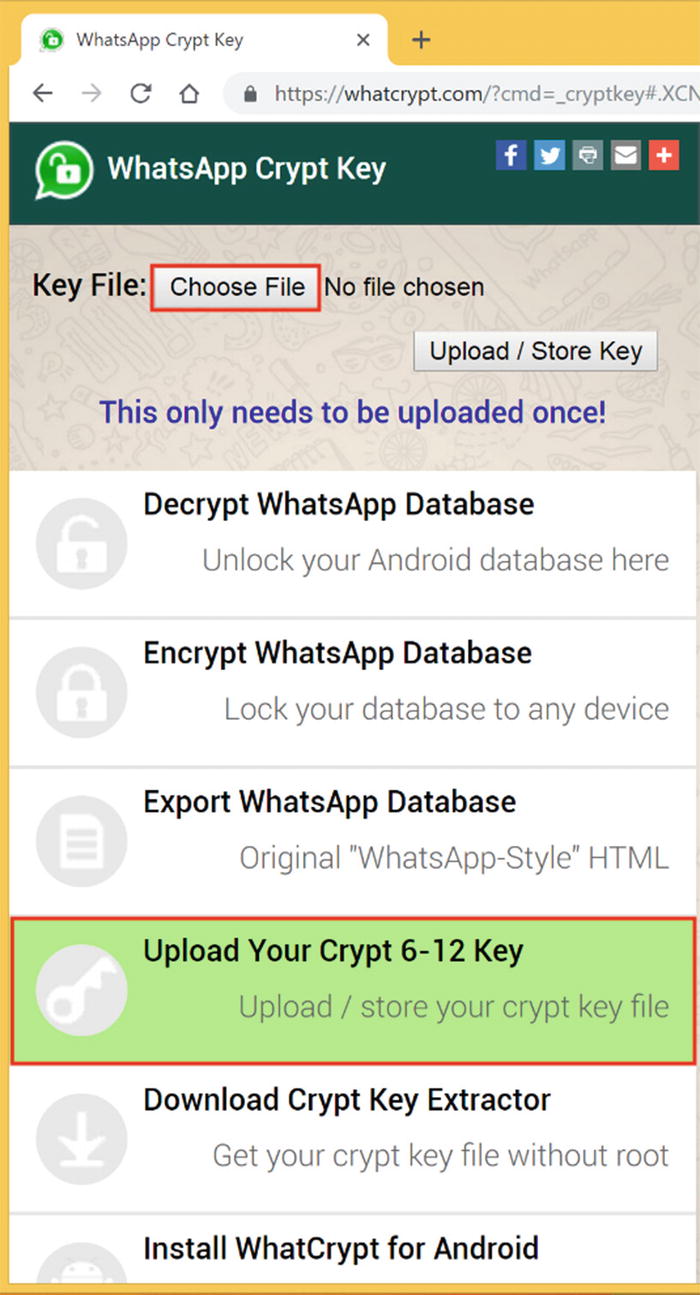 Figure 8-21.
Figure 8-21.Uploading your key
- 11.
- 12.We can see the key is successfully stored, and hence we can decrypt the database now (Figure 8-23).
 Figure 8-23.
Figure 8-23.The key is stored
- 13.Now Select ‘Decrypt WhatsApp Database’ and upload your msgstore.db.crypt12 file (as shown in Step 1). Then click on ‘Process/Download Zip’ to download the decrypted database (Figure 8-24).
 Figure 8-24.
Figure 8-24.You can download the zip now
- 14.Now open WhatsApp Viewer (a tool to display chats from the Android msgstore.db database available at https://andreas-mausch.de/whatsapp-viewer/ ) and click on File ➤ Open and select the decrypted msgstore.db file (Figure 8-25).
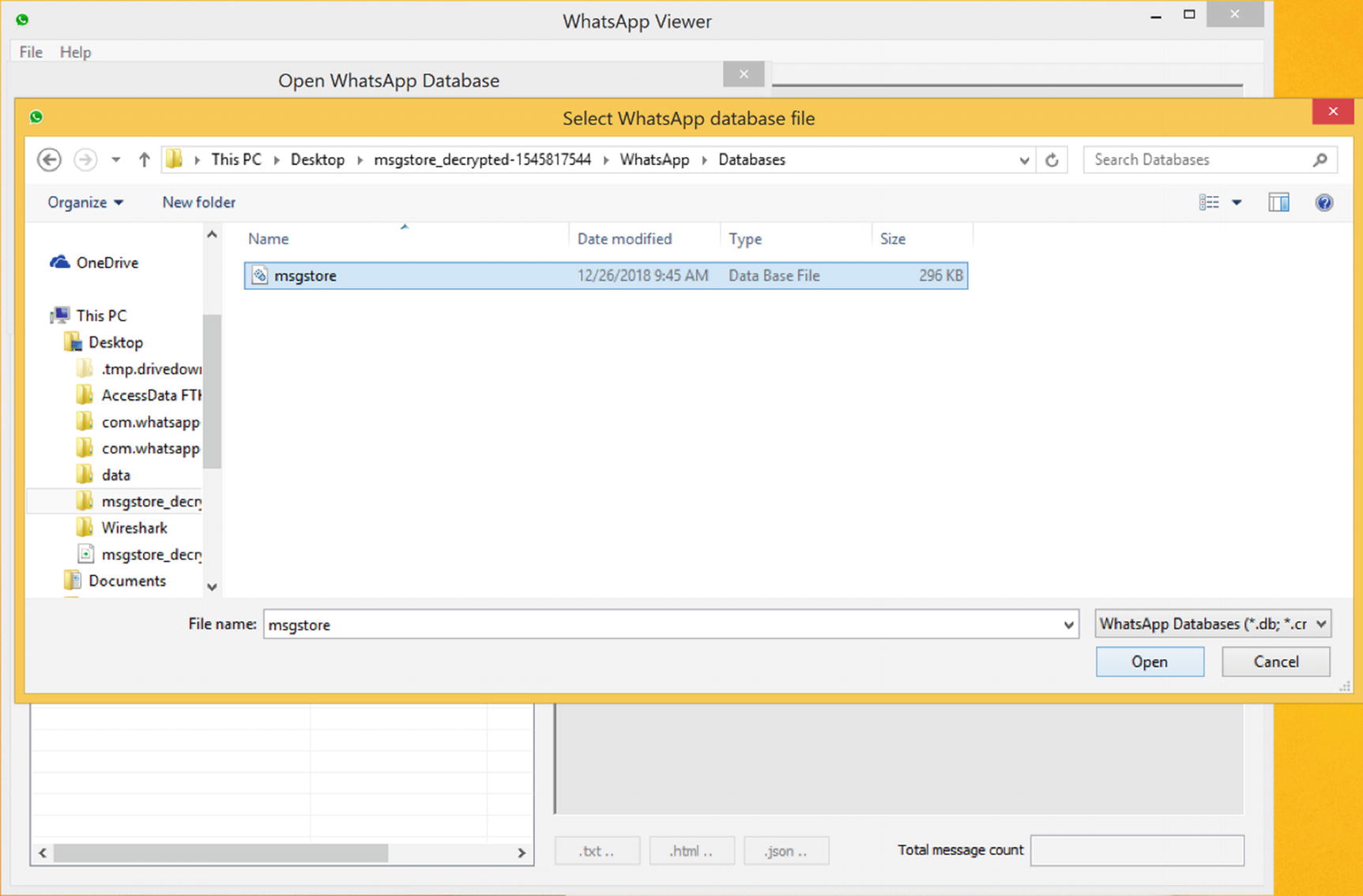 Figure 8-25.
Figure 8-25.Selecting the database file
- 15.Now we can see all the decrypted chats with images; here we have found two documents sent via WhatsApp as shown in Figure 8-26.
 Figure 8-26.
Figure 8-26.The results
Summary
One of the fast-growing trends in the IT industry today is the widespread use of cloud computing.
Different cloud computing models are Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
Cloud Forensics is also recognized as a subset of network forensics as investigators deal with public and private networks, and cloud computing is based on broad network access.
Cloud forensics consists of three dimensions, namely Technical, Organizational, and Legal.
There are server-side forensics and client-side forensics. Server-side forensics refers to the forensic procedures performed on the server to obtain evidence.
Similarly, client-side forensics refers to the forensic procedure performed on the client to obtain evidence.
Statistics show that cybercrime mostly occurs on the client side, and therefore evidence identification and collection are a vital part of cloud forensics.
Due to the lack of control of the system and as data is distributed among many hosts in multiple data centers, knowing where the data is physically located is difficult. This is one of the greatest challenges faced by a forensic investigator while performing memory acquisition of the disk.
Therefore, both customers and investigators are heavily dependent upon the CSP in order to collect the digital evidence from the cloud computing environment and this dependence introduces some serious issues of the Cloud Service Provider’s trust and evidence integrity.
Some Artifacts in Cloud Forensics are Log files of browsers, Physical memory, Registry.
FaaS (Forensics as a Service) is a newly developed subset under cloud forensics, and this model of cloud computing focuses on providing forensic services over the cloud.
FaaS should be considered with IaaS, PaaS, and SaaS. Some of the features of FaaS include Instance Gathering Process (IGP), Instance Sample verification, and Dedicated CSP Forensic Storage.
References
https://www.computer.org/csdl/proceedings/hpcc/2016/4297/00/07828448.pdf
https://www.tandfonline.com/doi/full/10.1080/00450618.2016.1153714
https://ieeexplore.ieee.org/document/7904287/
https://dpmforensics.com/2017/03/12/cloud-forensics-box/
https://www.sciencepubco.com/index.php/ijet/article/view/12230/4865