Malware is a term coined by merging two words – malicious and software, which is used to define a broad range of software that disrupt computer services, steal data, or compromise user safety. It is used to define a range of intrusive and hostile software applications. Malware are software designed for malicious purposes and deliberately cause harm to its target.
Initially malware was designed and shared as pranks or experiments by cyber experts in order to boast their scripting skills. It was all done in good faith, and no evil intentions were in play. But malware scripting evolved to become a multibillion-dollar business as malware authors started to create stronger malware. Such malware was hard to detect, caused harm to affected systems, and even compromised sensitive user data.
Hackers and malware authors have numerous targets, from banks to MNCs, and customized malware are created to exploit these big corporations.
Types of Malware
Let’s look at the different types of malware.
Viruses
These are possibly the most common malware type that every user is acquainted with. Virus is a piece of software, which upon being triggered, infects the system and spreads to other computers. Viruses are usually destructive and cause harm to computer processes. These are covert and are hard to detect; advanced viruses modify themselves when they replicate in order to avoid string detection.
Boot Infectors – Target the boot sector of the system.
File Infectors – Target specific files on a system.
Macro Viruses – These run under different programs and remain hidden.
Viruses are becoming stronger and more advanced as hackers keep improving their scripts.
Worms
Worms are self-replicating software that spread across the network and eat up large amounts of bandwidth. Worms don’t need container files and are stand-alones. Worms might even have payloads that are designed to diddle data on computer system. Worms are commonly spread through mass emails with infected attachments.
Trojan
Remote Access Trojans – install backdoors on target system for hacker to operate it remotely.
Data destruction Trojans – designed to destroy data on a system.
Software disabler Trojans – once installed on target system, it stops or kills a program or service.
There has been a new ‘stealthy’ Linux backdoor Trojan that has been discovered that bypasses the intrusion the detection system (IDS) and web application firewalls (WAF).
It implants a Backdoor that evades all security vendors. The new Trojan, named ‘SpeakUp’, exploits known vulnerabilities in six different Linux distributions. The attack is mainly targeting servers on AWS-hosted machines. The SpeakUp Trojan propagates internally within the infected machines, exploiting remote code execution vulnerabilities. It also infects Mac devices with the undetected backdoor.
Rootkits
Rootkit is a collection of malware software that is designed to remotely access and completely take over a computer. They work in stealth by remaining hidden from the monitoring processes of software. Rootkits are extremely dangerous as security products are often ineffective to detect their presence. Meticulous manual detection is the only method to search for Rootkits.
Spyware
Spyware are a type of malware that is designed to spy on users and record their activities. This malware collects user information such as internet browsing history, download history, keystrokes, etc.
Adware
Adware is the most annoying malware, as it auto-delivers advertisements. A common example is pop-up ads. Adware is one the most revenue-generating malware, which is now being used commercially by giant companies. In many cases, Adware has been used as a vector to spread spyware and other malware.
Exploits
Every software has security loopholes that are called vulnerabilities, and hackers use these vulnerabilities to develop Exploits. With these Exploits, a hacker can access the system and cause havoc. Exploits allow hackers to gain control of running processes on a system via privacy escalation. Software companies spend millions of dollars in order to create security patches for vulnerabilities. New vulnerabilities are known as ‘Zero-day exploits’, which hackers create and sell on the dark web.
Ransomware
Ransomware is an advanced malware that encrypts and blocks access to a system and threatens to wipe the data only in exchange of ransom, hence the name. Once a user pays the ransom, the hacker sends the decryption key to the user. However, there is no guarantee that the hacker will send the decryption key. Hackers ask for ransoms in cryptocurrency in order to avoid being traced.
Bot
Bot is short for robot, so when a malware infects a system and allows the hacker to control all its operations remotely, it becomes a bot. This Bot is then used by a hacker to launch attacks as individual missions or with multiple other bots. This is Botnet. Hackers use bots to carry out a range of operations such as illegal cryptocurrency mining, masquerading, DoS/DDoS attacks, etc.
Malware Analysis
Any malicious program or script is a malware. Malware analysis is the process to determine what the acquired malware sample does. It is a process to get to the internals of the malware code to identify malware type, action, author, etc., and to mitigate future infections. Below are the key processes for Malware Analysis.
Static Analysis
File type determination
Strings encoded in binary file
Obfuscation check
Hash comparison
Checking against database
Hashing
Hashing involves converting character strings into a shorter value. This shorter value helps in searching a database. Also, it is an indicator of the integrity of the data. A hash value of the program is generated from the original source and compared with the clone that is being inspected. A matching hash ensures integrity of data on the source and copy of the file/hard disk.
Hashing is standard practice for all forensic investigations. All malware suspected must be hashed prior to analysis.
Antivirus Check
Before forensic investigators start examining the malware files, it is a smart strategy to check the files with a malware database. This can be achieved via antivirus tools, or the files can be uploaded online to a web service that examines it for malware. Antivirus software compares the file signature with its database of malware file signatures and presents results.
String Analysis
A sequence of characters within a program is a string. If a program prints a message, copies a file, or connects to a URL, it contains strings. String analysis helps the cyber forensic experts to find evidence connected with the malware as it contains a lot of technical information. Usually, strings contain things like FTP or HTTP commands that download web pages and files, hostnames, IPs, and also where the malware connects. Via string analysis Investigators can find information about the compiler used, programming language, embedded scripts, etc. Cyber forensic experts may even get clues from the language used to write the malware script and find its country of origin.
Detection of Obfuscation and Packed Archives
Initial analysis may not prove to be sufficient in finding any evidence; therefore, cyber forensic experts then disassemble the malware binary. With disassembly, malware’s binary code is translated into valid x86 assembly language. Malware binaries are initially written in high-level languages like C and C++ by malware authors. Later they use a compiler to compile the source code into X86 binary code. By disassembling the malware, it becomes easy to understand how the script was designed. If malware binary is packed, then special tools will be required to first unpack it and then to analyze it. These scripts are in Windows Portable execution format (PE), which describes the structure of Windows program files such as .dll, .exe, and .sys. PE formats instruct Windows how to load a program to memory. The contents of the PE file are studied for details about the malware.
If this provides no conclusive results, then experts proceed toward performing dynamic analysis.
Dynamic Analysis
System processes
Registry analysis
Network analysis
Sandboxing
As mentioned earlier, cyber forensic experts perform dynamic analysis in a controlled environment; this is possible due to a technology called Sandbox – software that creates a safe and isolated environment where applications are tested without harming the computer. Dynamic analysis can never be performed without sandboxing. Sandboxing allows investigators to carry malware analysis a step further and execute it to study it without the harm of damaging the forensic workstation.
Behavioral Analysis
This method is referring to how the cyber forensic experts observe the malware’s behavior upon triggering it. All the details such as how the system files are modified, resource consumption, and other parameters are observed.
Memory Forensics
Memory Forensics is a crucial aspect in today’s digital forensics investigations.
RAM is a very useful part of the system, which gives us an insight of all the data that is used by software that are being operational at the point of time the system was live and running. It is of utmost importance since it depicts us with the series of events that were incurred when the attack took place.
A listing of running/terminated processes.
Open files of a process.
Cache-related data like all data regarding the web, SAM database, and much more related stuff.
DLL’s loaded.
Usernames and Passwords.
Old/Previous & New/present network connections.
Tools for Analysis
Cuckoo Sandbox – Cuckoo is a very popular sandboxing software that is used in malware analysis. Cuckoo allows cyber forensic experts to analyze files under Windows, Linux, Mac OS X, and Android virtualized environments. It also performs memory analysis and network traffic analysis.
Yara Rules/Analyzer – A powerful tool that malware researchers use to identify and classify malware samples.
REMnux – REMnux is a free Linux toolkit that is used in malware analysis and reverse engineering malicious software. REMnux provides a clean and feature-rich environment to analyze malware files with ease.
Virus total database – an online utility that allows users to upload suspicious files to detect types of malware.
Google Rapid Response framework – Google Rapid Response or GRR is an incident response framework that focuses on remote live forensics. In a GRR system and file analysis, capabilities are provided by Sleuthkit and pytask, while memory analysis and acquisition are provided by a rekall project.
Radare – A feature-rich disassembly framework. It performs debugging with local debuggers and has powerful analysis capabilities to speed up reversing.
Challenges
Performing malware analysis is a tedious task for cyber forensic experts. When we compare this discipline of cyber forensics with other disciplines, the risk involved with the digital evidence and forensic system is significantly high. Analyzing malicious scripts requires proper preparation, and cyber forensic experts need to follow and take many precautions. One wrong move, and they risk of damaging their forensic workstation.
In static analysis, if cyber forensic experts encounter advanced malware that use encryption or are polymorphic in nature, then the efforts might be futile. Static malware analysis becomes a time-consuming exercise when a disassembly is performed in search of evidence. As more and more malware scripts are studied, it has been observed that malware authors are using stronger obfuscation for their scripts. This increases the time to examine such scripts and, in some cases, even leads to a dead end in static analysis.
We mentioned hackers getting stronger and sharper with their malware scripts. Recently many malware scripts were studied that showcased ‘sandbox evasion’. Such malware could detect the presence of a sandbox environment.
Cyber forensic experts become only as skilled as the hacker’s last attack. Cyber forensic experts study hackers’ attack patterns and reverse engineer them.
Malware as a Service
The rise of malware threats has surged to new heights with global attacks having increased significantly. As hackers find new platforms to make money, one such very significant one that came under cyber forensic experts’ radar was Atom – a platform that provides Ransomware as a Service (RaaS). Unlike its counterparts, Atom ran on public websites and servers and even came with a downloadable program that allowed users to create and upload their payload. This event was taken as a wake-up call by authorities as they realized what threats they are facing. With such services being provided on the internet to script kiddies and noobs, it can be assumed that it will only increase the work of cyber forensic experts. It will increase the work of cyber forensic experts to track and isolate the malware, and also the security companies will need to add it to their database to implement better scan probabilities.
Case Study: Android Malware Analysis
This section covers the techniques to analyze Android malware by using a custom malware sample. The malware, when running on an Android device, will get multiple access permissions to different services and also connect to a C&C (command and control Server).
Custom Malware Sample
- 1.
Just open your browser, find the APK file you want to download, and tap it – you should then be able to see it downloading on the top bar of your device.
- 2.
Once the .apk file is downloaded, open Downloads on your Android device, tap on the APK file, and tap yes when prompted. The app will begin installing on your Android device.
For this case study, we will use a few tools like QUIXXI, QARK, and MOBsf. Some other tools that can be used for Malware Analysis are ADB, Wireshark, dex2jar, JD GUI, and high-tech bridge APK analyzer.
Let’s do some static analysis.
Tool 1: QUIXXI
QUIXXI is an award-winning, leading platform, which provides enterprises and mobile application developers end-to-end solutions for security, analytics, and blockchains. Basically, this tool is all about providing security to your Android application. QUIXXI Shield provides protection to your device against hackers or cybercriminals who are looking to clone, tamper, inject malicious code, or in general exploit your mobile application. This tool generates an automated Vulnerability Assessment and provides quick static evaluation of your app to outline critical security weaknesses and suggestions on how to fix them. This tool also secures your mobile applications by making it difficult for hackers to reverse engineer the source code and uses advanced technology to detect the genuineness of the app run by the final user.
Here, an application is chosen: for example, Tik-Tok. It is an application used for creating and sharing small videos. The objective of this example is to analyze the vulnerabilities existing in this application.
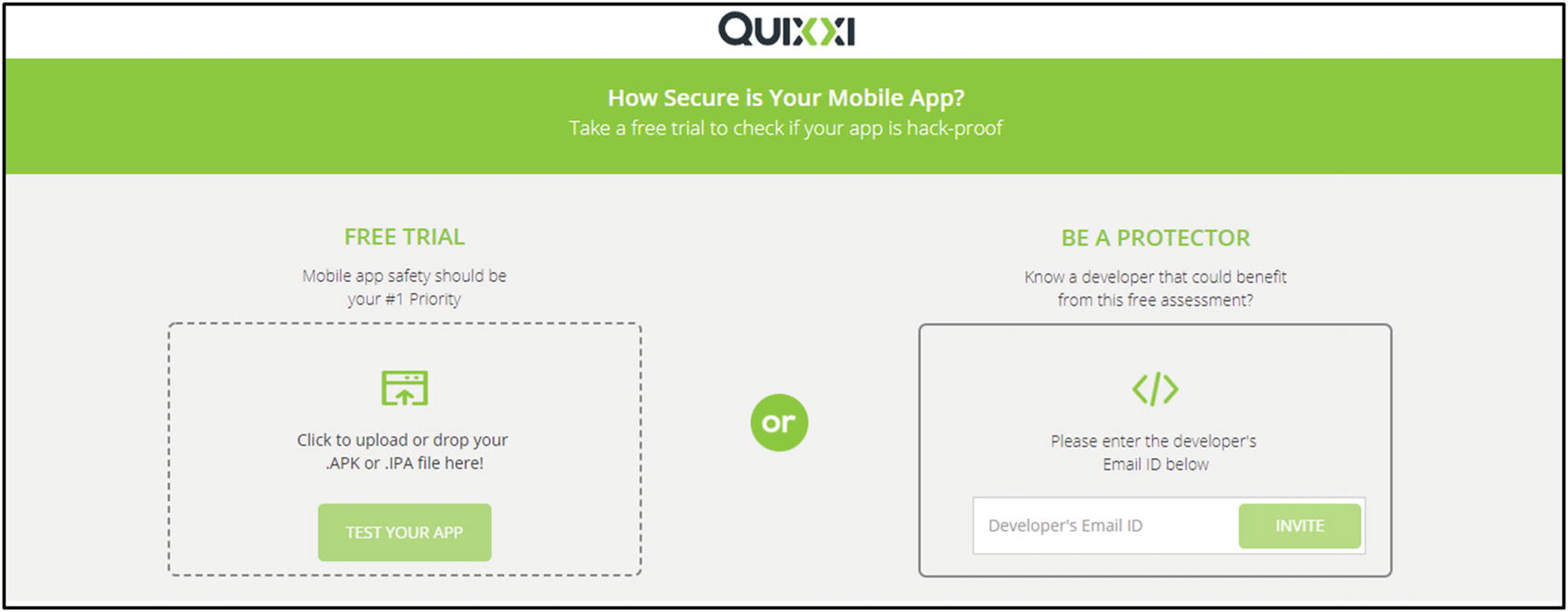
Quixxi upload form. APK is uploaded for analysis.
You’ll then see the results of the analysis.
After scanning your application, it generates a vulnerability assessment report, which includes all the vulnerabilities in your application.
Vulnerabilities are generally classified into three severity levels: High, Medium, and Low. A High severity vulnerability requires immediate attention and remediation. It also indicates the effort for compromising the vulnerability. A High severity vulnerability is much easier to compromise. A Medium severity poses a risk, but not at the levels of a High severity. A Low severity vulnerability also needs to be addressed but does not possess the levels of threat that High and Medium vulnerabilities pose to the system. Also, the probability of compromise of a Low vulnerability is the least, whereas it is the highest for High and Medium ones.
We have considered the High vulnerabilities category here to indicate the possible levels of compromise and damage caused due to a misconfigured application. These vulnerabilities can lead to a complete takeover of the device/system/data. These vulnerabilities can be exploited by a malicious application to piggyback on its rights and run/install/delete applications. Many times, malware activity may be detected which uses such applications for their use.
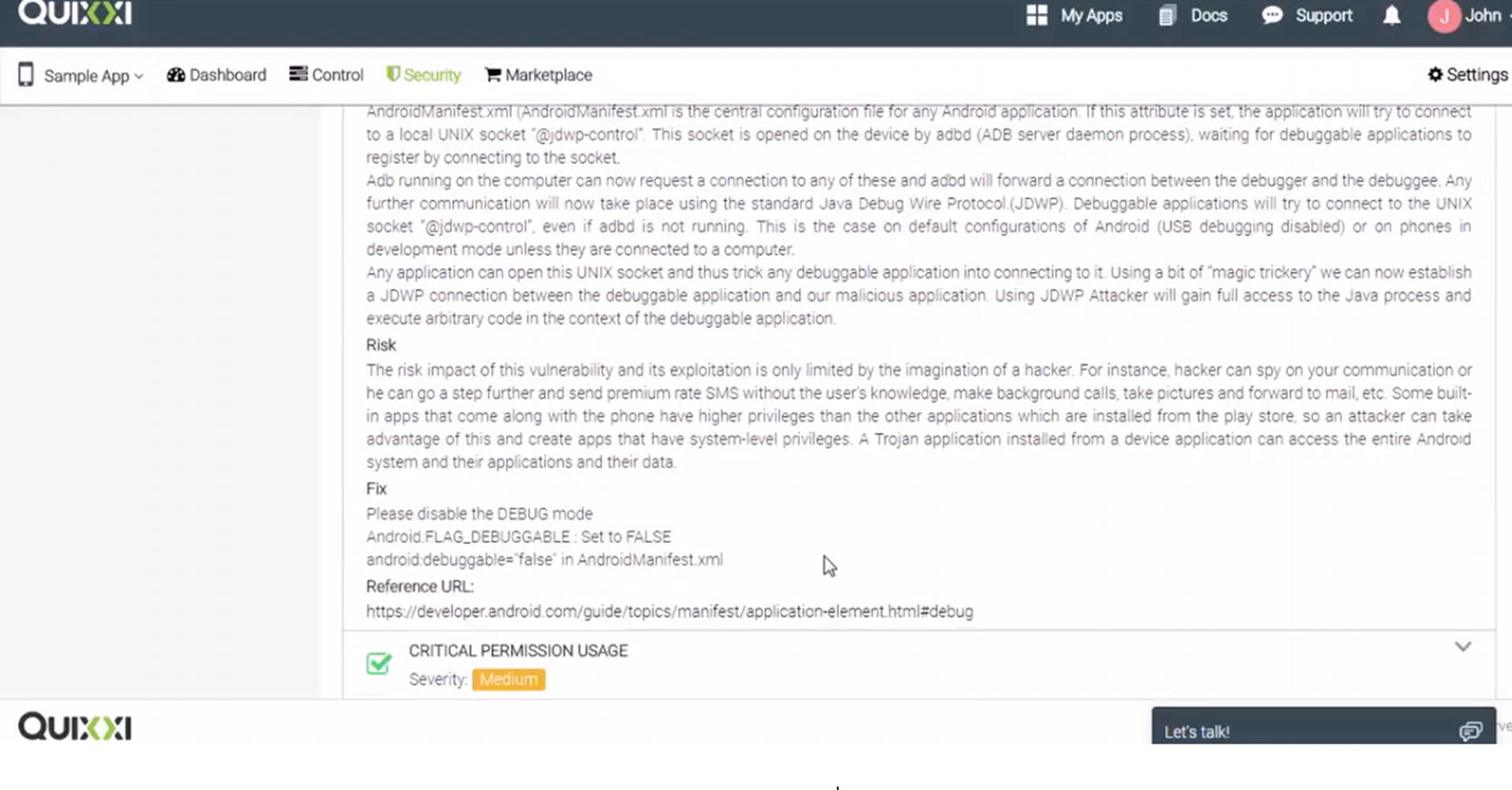
An identified threat
Some seemingly innocent applications may display these vulnerabilities. Now let’s see how App Shield works.
App Shield
Here’s the process:
- 1.
Let’s use the unsigned unprotected APK.
- 2.Then click on APK decompiler, and choose the same file to upload and decompile (Figure 9-3).
 Figure 9-3.
Figure 9-3.Decompiling
- 3.Click to com + example + quixxi + android test file (Figure 9-4). From there, click to MainActivity.java.
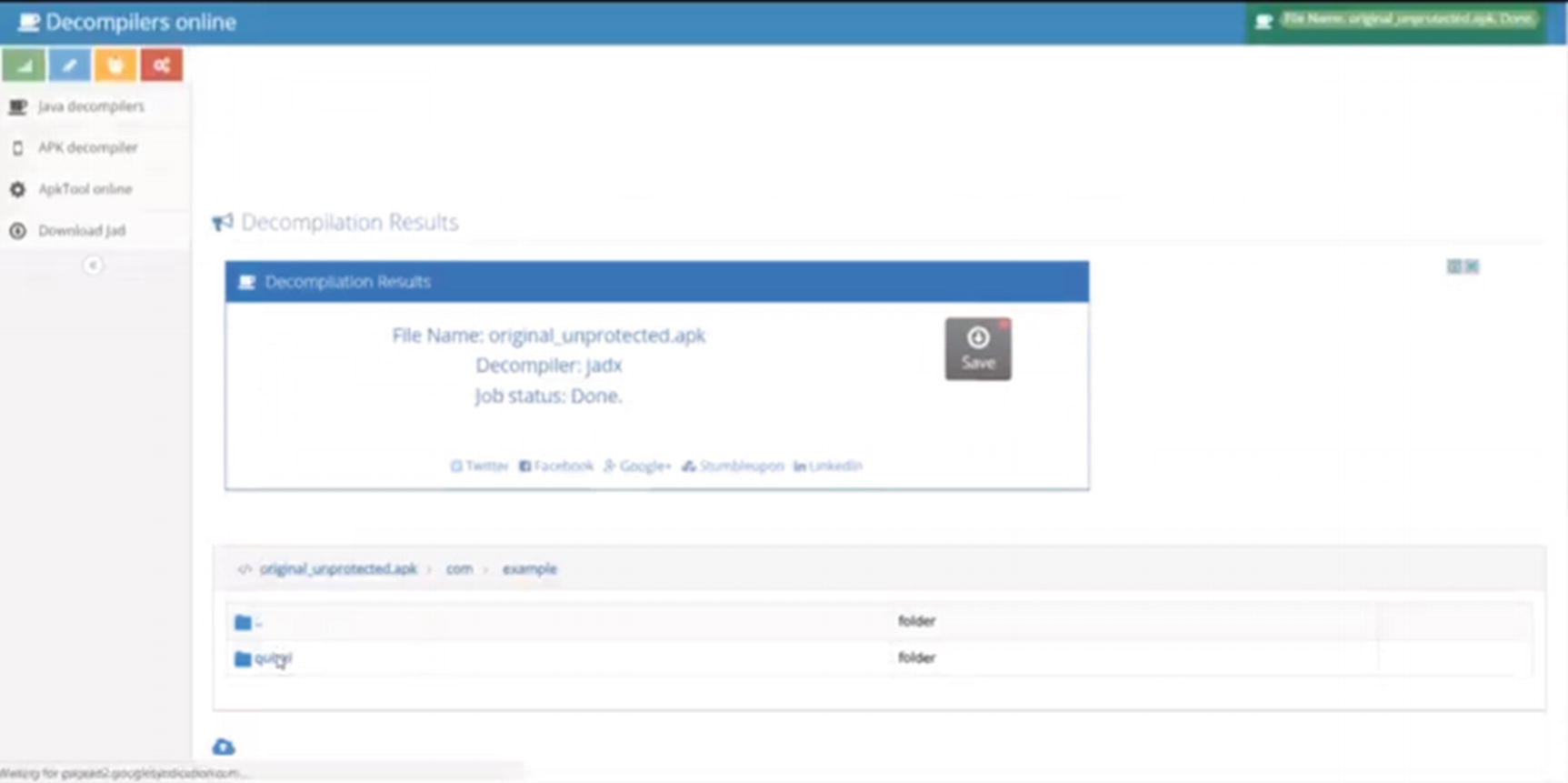 Figure 9-4.
Figure 9-4.Click to go down the package hierarchy
- 4.Here, you can see the code is easily readable, which will help attackers to introduce malicious code (Figure 9-5).
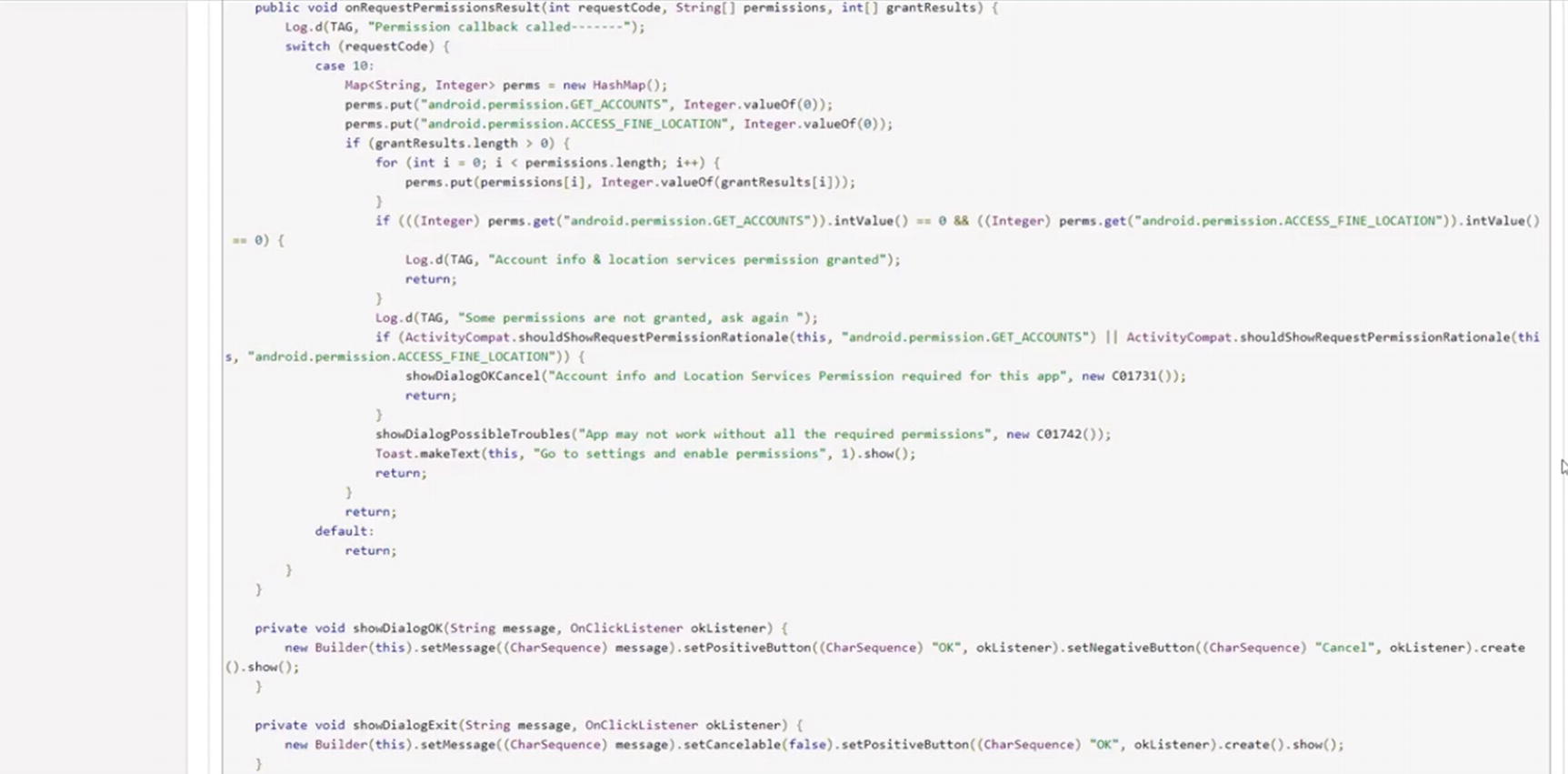 Figure 9-5.
Figure 9-5.The decompiled code
Protect Your App
- 1.
As usual, drag and drop the APK into the box. Configure the security solutions required by the particular app. Once done, the QUIXXI app shield will be applied on your .apk file, and the unsigned unprotected app will be transformed into a signed protected app.
- 2.
Now, the protected application will be available in your Report section. Go to Report section to download the protected app.
- 3.
Let’s decompile it to see how we’ve protected it. Choose the file and then upload it
- 4.
Next, click on Upload and Decompile option.
- 5.The APK is uploaded and decompiled successfully as shown in Figure 9-6.
 Figure 9-6.
Figure 9-6.Decompiling the protected APK
- 6.Now click to com + example + quixxi + android test file. From there, click to MainActivity.java (Figure 9-7).
 Figure 9-7.
Figure 9-7.Choosing MainActivity.java again
- 7.In the main activity, we will observe that the security of the code is increased, which was not the case before (Figure 9-8). We can see that in the protected signed app’s main activity, the hard-coded strings and methods are replaced by garbage values that will make it difficult to understand the order of the code, thereby securing your app from being tampered with, reused, or injections.
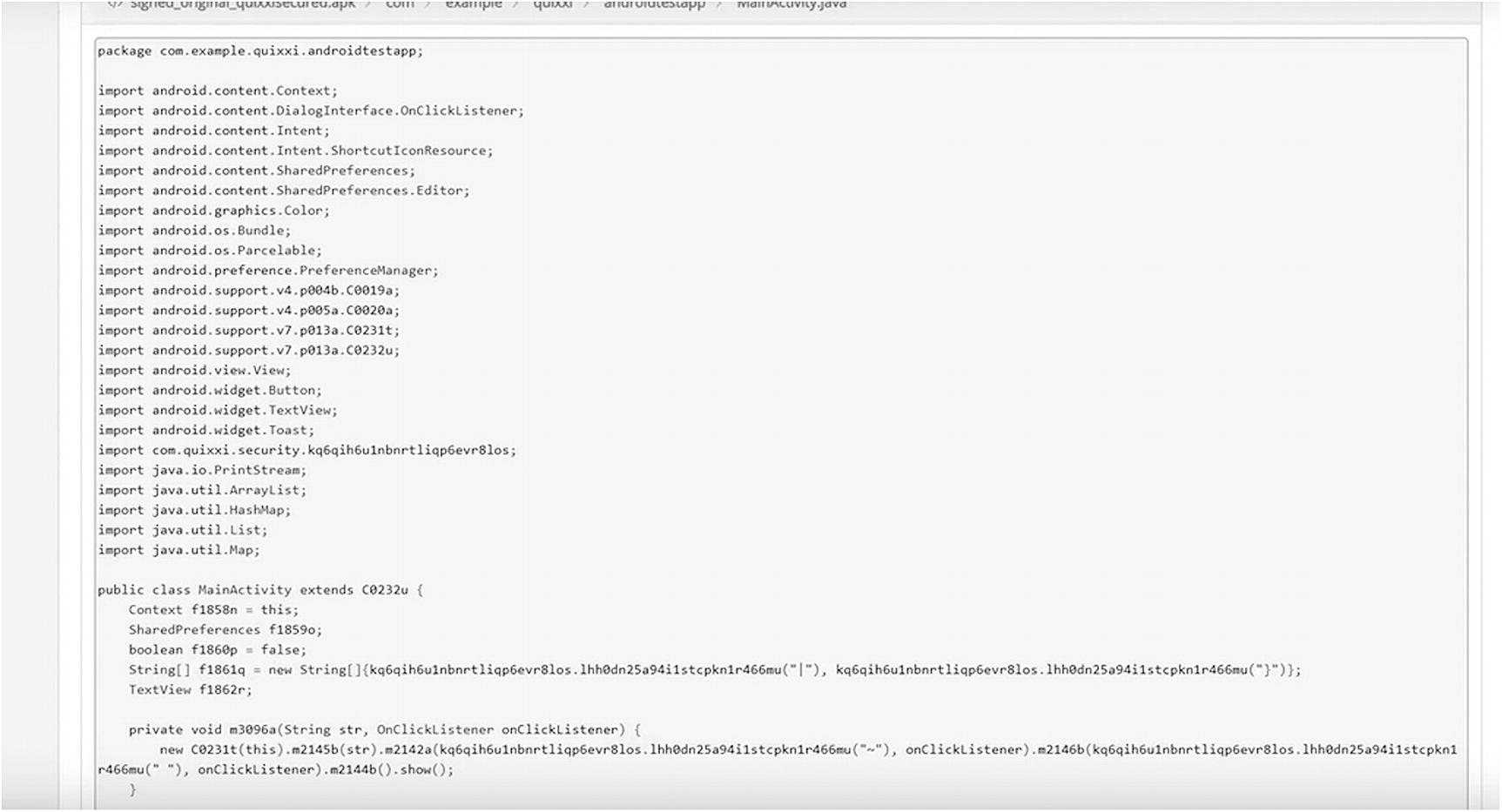 Figure 9-8.
Figure 9-8.Obfuscated code
Tool 2: QARK
QARK is an acronym for Quick Android Review Kit. It is community based, free, and open source aimed at improving Android application security. It is a static code analysis tool, designed to acknowledge potential security vulnerabilities and points of concern for Java-based Android applications by educating Android developers and information security personnel about potential risks associated with Android application security. It does so by providing clear descriptions of issues and links to authoritative reference sources. This tool also attempts to provide dynamically generated ADB (Android Debug Bridge) commands to aid in the validation of potential vulnerabilities that it detects. It will even dynamically produce a custom-built testing app, which is a ready-to-use APK and designed specifically to demonstrate the potential problems it discovers, whenever attainable.
The only thing required for this tool is the actual location of the SDK, so if you are an Android developer, you already have the Android SDK on your system, so you can just point the location of the Android SDK to the tool, and you are ready to go! But in case you don’t have the Android SDK on your system, it gives you an option to download the SDK for you and save this configuration so that you don’t have to repeat the process every time when you are using the tool.
When the QARK starts, you will notice that it gives an option to either click the APK or start scanning the source code. It gives two opportunities because if you are an auditor or penetration tester of your company, you would prefer to choose APK; and if you are a developer for your company and you want to update the code, then you would choose the source code to be analyzed.

The QARK prompt
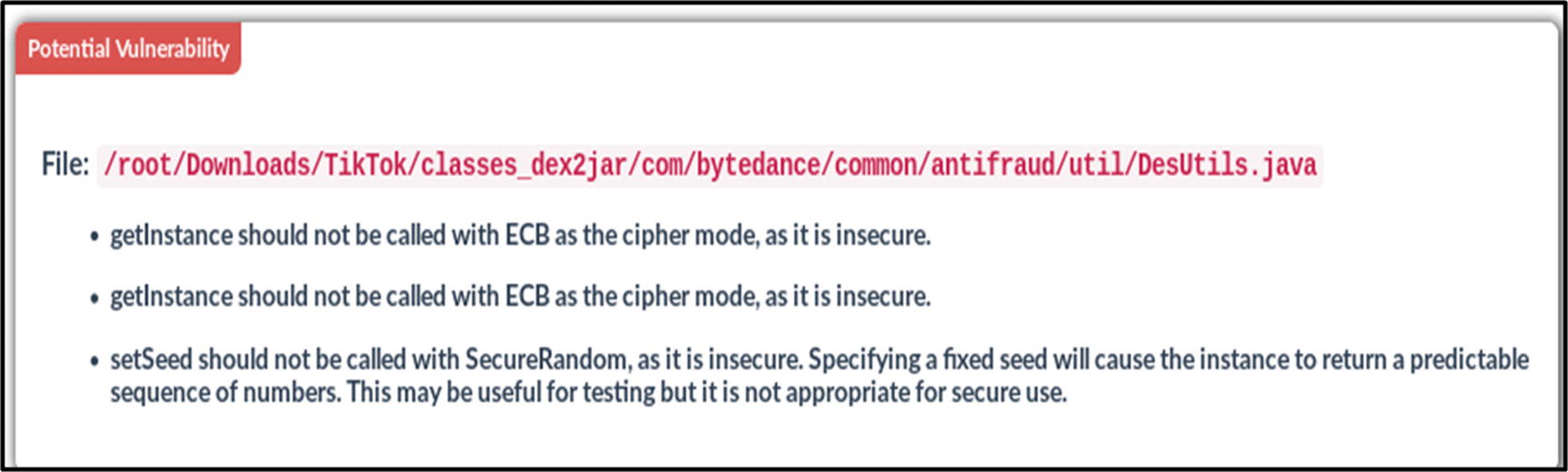
A vulnerability
Tool 3: MOBsf
- 1.
Make sure you have Python on your system.
- 2.
After installing python, we need to install an rsa module. To do so, type the following at a command prompt:
python – m pip install rsa - 3.
Download setup.py from https://github.com/MobSF/Mobile-Security-Framework-MobSF/tree/master/install/windows .
- 4.
Then run a command in the directory where you saved setup.py:
python setup.py - 5.
Install Binscope by clicking Next when prompted.
Note
Binscope is preinstalled in a licensed version of Microsoft Windows.
- 6.Copy your IP address to MobSF/settings.py file (search for WINDOWS_VM_IP, as shown in Figure 9-11).
 Figure 9-11.
Figure 9-11.Adding your IP addresss
- 7.
After adding your IP address, you can run MobSF.
- 8.
- 9.For checking its operational working , you can directly go to your browser and paste your localhost IP address there: for example, 127.0.0.1:8000 as your local machine’s loopback address (Figure 9-13). As per the screenshot, you can then upload your file to get tested.
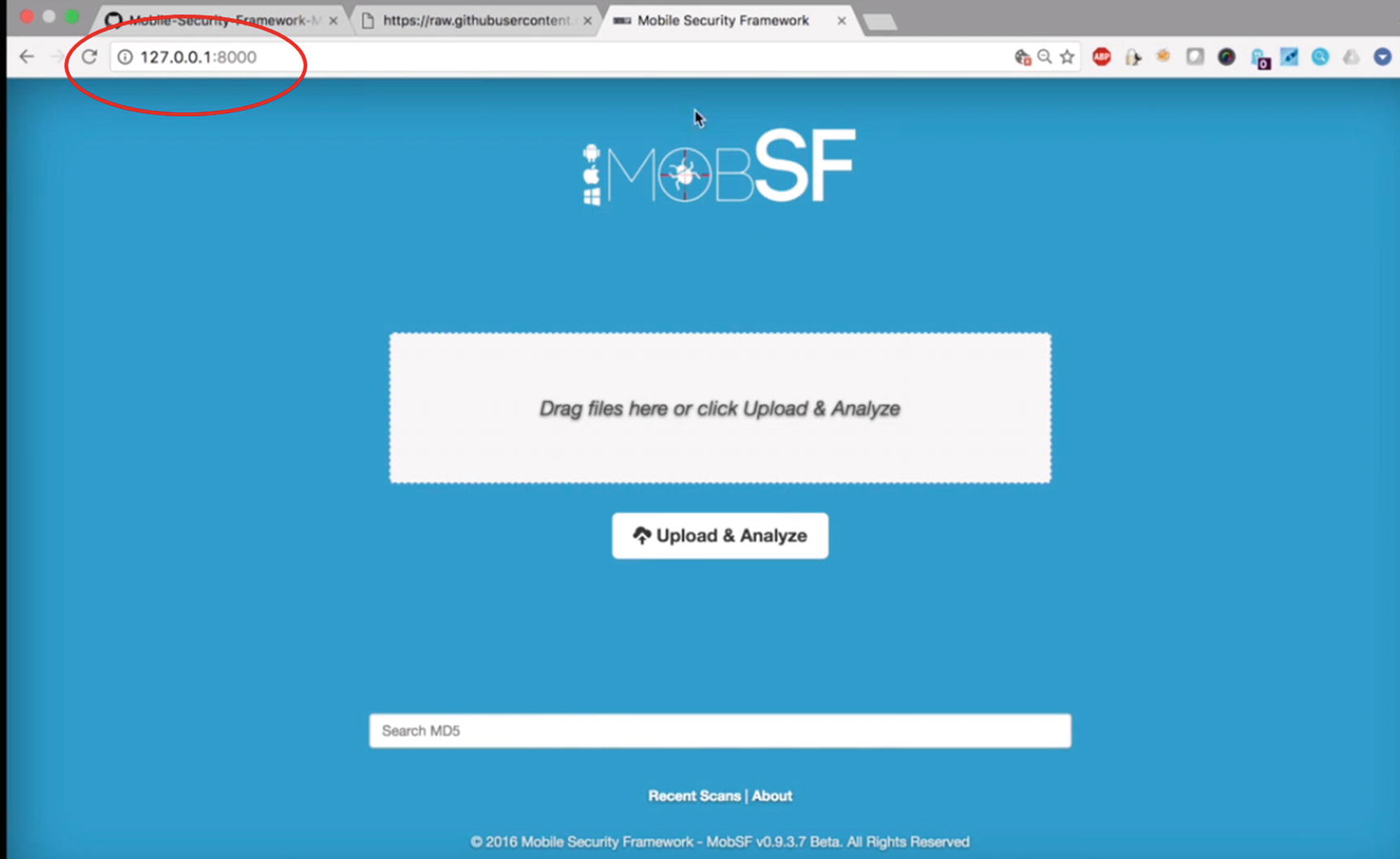 Figure 9-13.
Figure 9-13.Confirming MobSF is running
- 10.After uploading your file, it will display all the code as shown in Figure 9-14 to check whether it is secure or not.
 Figure 9-14.
Figure 9-14.Results of the scan
Case Study: Windows Malware Analysis of Data Stealing Malware
We will be seeing a detailed analysis of a data stealing malware that includes static, dynamic, and behavior analysis.
FTK Imager: Forensic Toolkit, or FTK, is a forensics software made by AccessData. It comprises FTK Imager , which is a simple and concise tool. It operates by saving an image of a hard disk drive (HDD) into one file or in segments that can be later reconstructed. It also calculates MD5/SHA1 hash values that confirm the integrity of the data before closing the files.
Regshot: Utility for registry comparisons that we first used in Chapter 2.
Volatility is an open-source memory forensics framework generally used for a malware analysis incident response. It has been written in the Python language and supports nearly all platforms like Microsoft Windows, Mac OS X, and Linux (as of version 2.5).
Process Hacker is an open source process viewer and free. It has multiple functions like assisting in debugging, malware detection, and system monitoring. It has a powerful process termination, memory viewing/editing, and other unique and specialized features.
PE Studio: PE Studio is a free tool used in performing a static investigation for any Windows executable binary.
Virus Total: It is an online portal (www.virustotal.com) used to analyze, detect, and inform you about malware (virus, trojans, worms) on your phone or system, which allows you to upload any unknown applications to it. In simpler words, Virus Total for Android will get your applications scanned with more than 50 antivirus engines, alerting and flagging any undesired or malicious content.
Also note that Virus Total for Android cannot provide real-time protection; hence, it cannot be a substitute for any antivirus product, just as a second opinion or option available for your apps.
Static Analysis
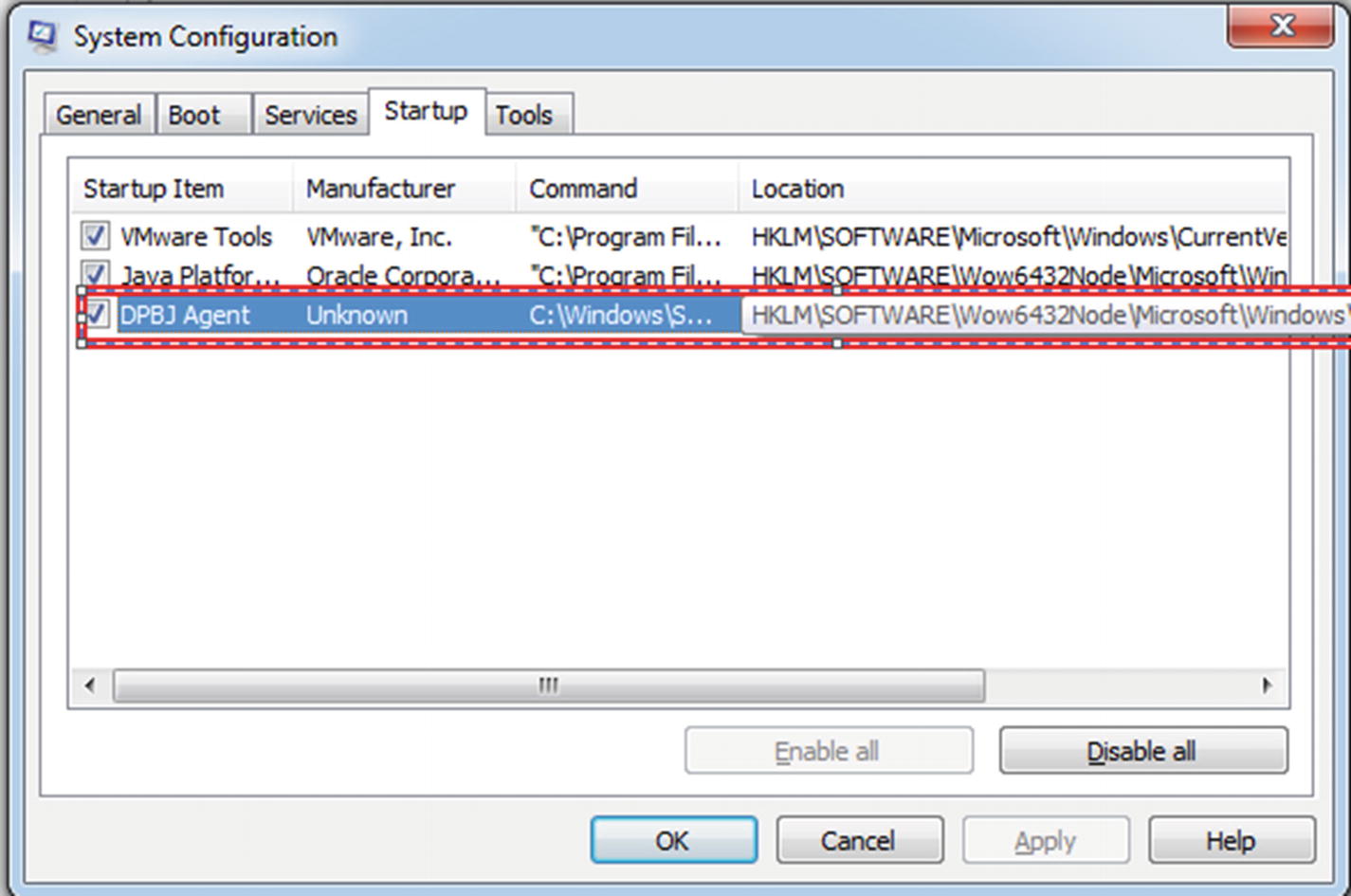
An unknown executable has been found in the system. It is not part of the standard file list.

Same process is visible in Task Manager
- 1.We’ll start by taking the RAM dump of the live system using FTK Imager (Figure 9-17).
 Figure 9-17.
Figure 9-17.Process to take RAM dump of the system
- 2.
Analyze the memory dump(.mem) we just took from the previous step using Volatility. Type command to identify the operating system, hardware architecture, and service pack used.
volatility-2.4.standalone.exe -f memdump.mem imageinfo - 3.Here we can see the memory dump has a Windows 7 operating system (Figure 9-18).
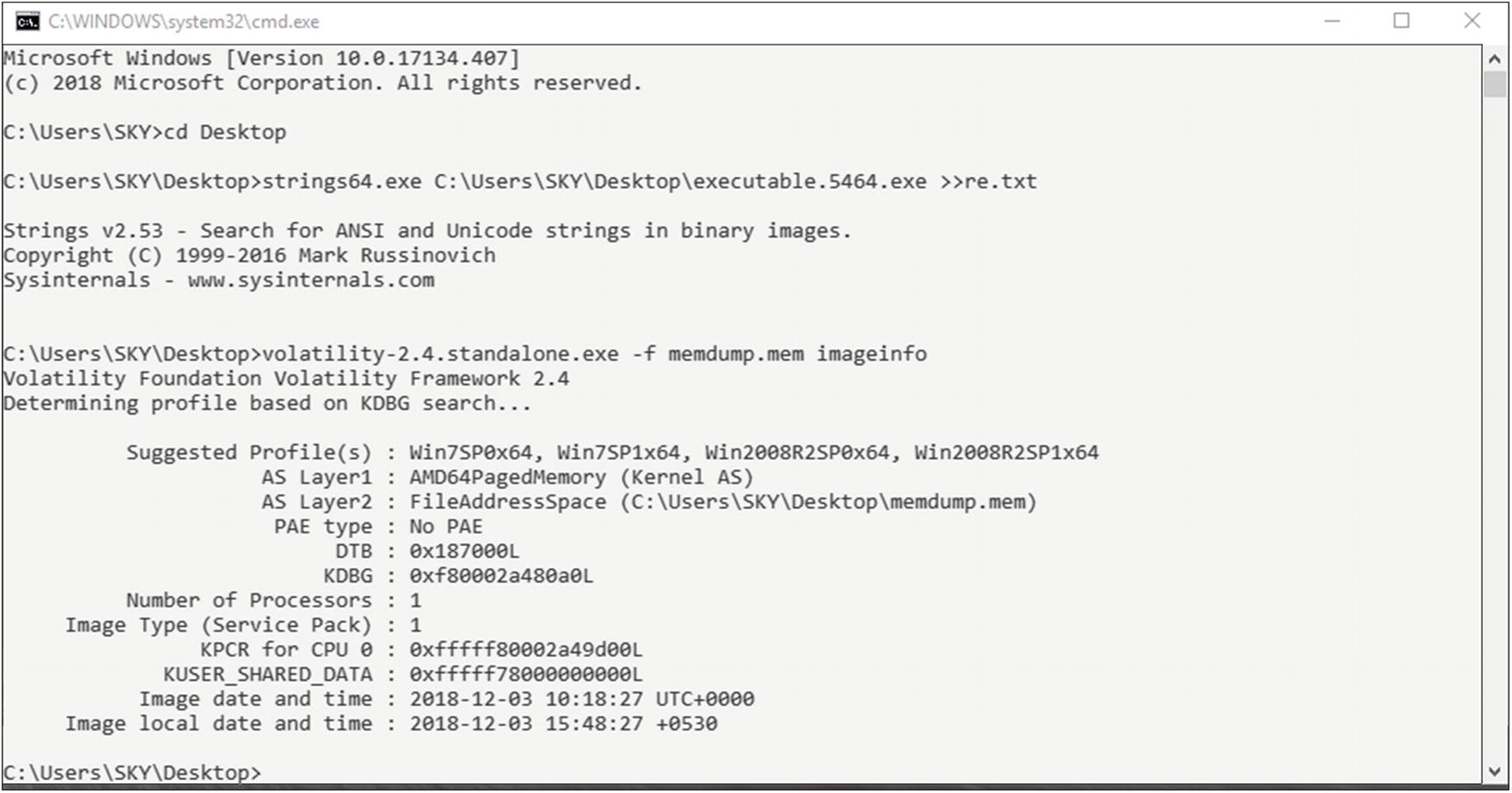 Figure 9-18.
Figure 9-18.Running volatility, which is a tool for memory forensics analysis
- 4.The pslist lists all the processes running on that system when we acquired the RAM dump on the memory dump file memdump.mem. Type the following command to list all the processes running on that system when the RAM dump was acquired:volatility-2.4.standalone.exe -f memdump.mem --profile=Win7SP1x64 pslist
- 5.In Figure 9-19, we can see DPBJ.exe (a suspicious process) running.
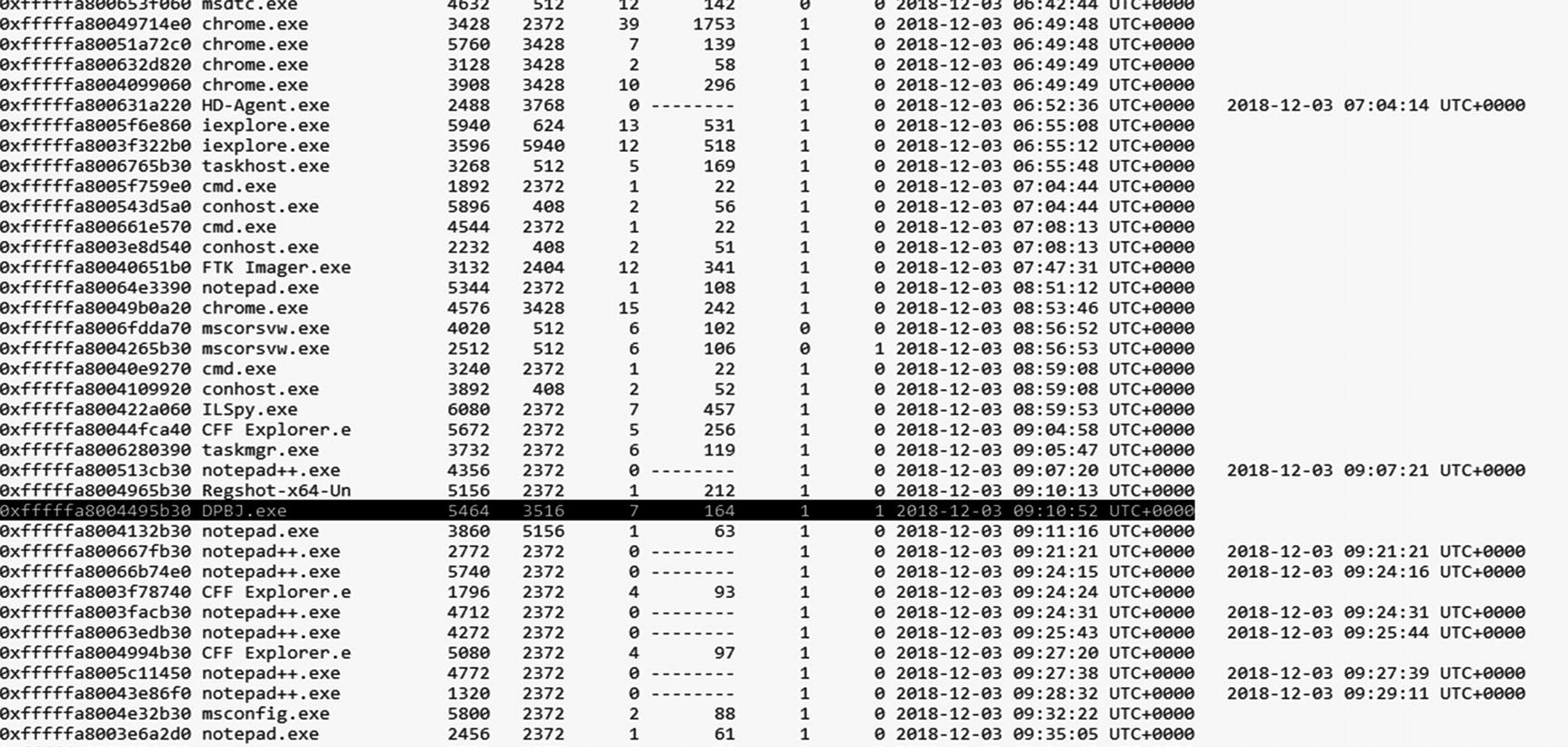 Figure 9-19.
Figure 9-19.We see a suspicious process running
- 6.Type command as shown in Figure 9-20 below to list all the processes on that system (running or previously terminated). We can see DPBJ.exe (the suspicious process) was still running on the system when the RAM dump was taken.volatility-2.4.standalone.exe -f memdump.mem --profile=Win7SP1x64 psscan
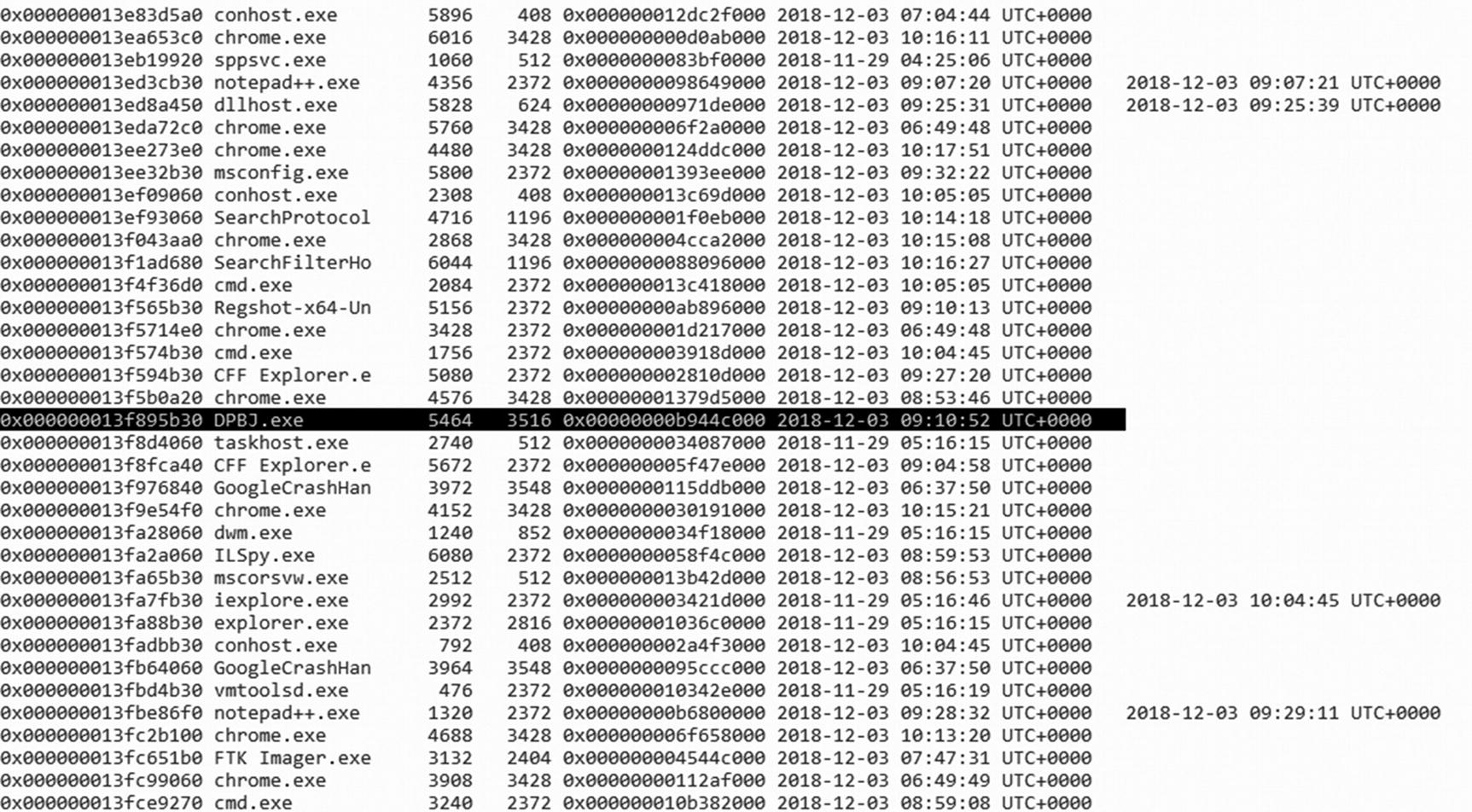 Figure 9-20.
Figure 9-20.List of all running processes on the system
- 7.
Type the command as shown below to enumerate processes. This command can find terminated processes as well as hidden processes.
volatility-2.4.standalone.exe -f memdump.mem --profile=Win7SP1x64 modscan

Memory map of the system
Properties of the Malicious Executable

Properties of the malicious executable file
Right-click on the file and select properties; it will display all the relevant information about the selected file. The detail shows that the exe has an unknown publisher with no copyrights. Most malware are distributed by hiding them within executable programs or applications. That is why computing devices only allow applications or programs with trusted publishers to be installed on the system. The computer blocks installation of any application with an unknown publisher by default. So, analyzing the properties of any exe file is also an important and crucial part of the malware analysis process.
Header Information
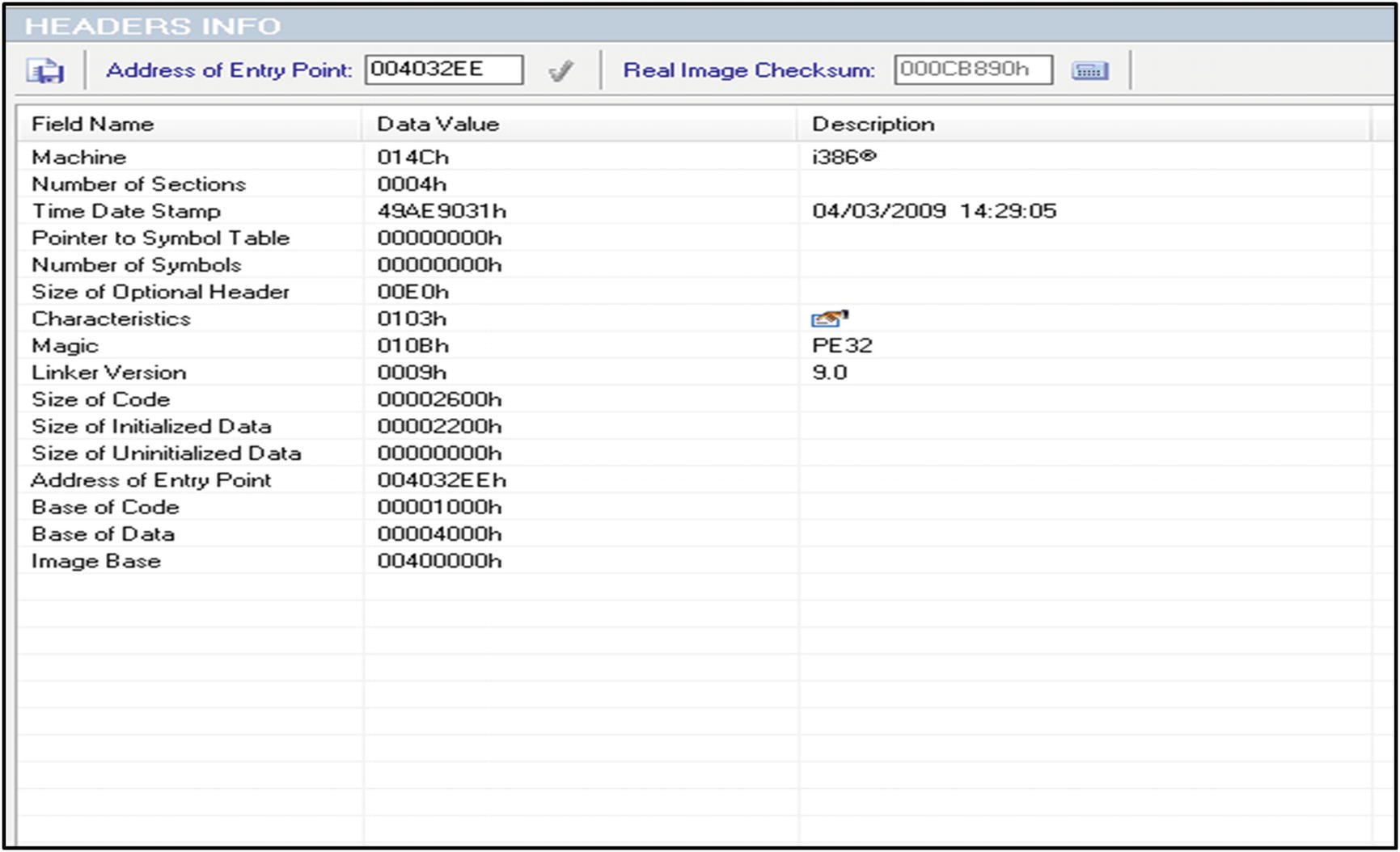
File properties
The next step is to check for the file header, which shows whether a particular file is an exe or not. This is done by checking the existence and validity of the PE headers. Additionally, checking the leading 2 bytes ("MZ" for PE files) will return true for DLLs as well.
Header Information
DLL Information

Dynamic Link Library(DLL) information
Indicators
PE studio is the tool used here to gather more information. You can download this tool from https://www.winitor.com/get.html . To analyze a file, we can simply drag and drop the file on PE studio tool or we can select File ➤ Open file and select the suspicious file that we want to analyze.

Indicators
A VirusTotal result is shown as per the behavior analysis of the executables. In Figure 9-26, in the indicators section, we can see that the file contains another file within it, and it imports blacklisted functions.
VirusTotal Result
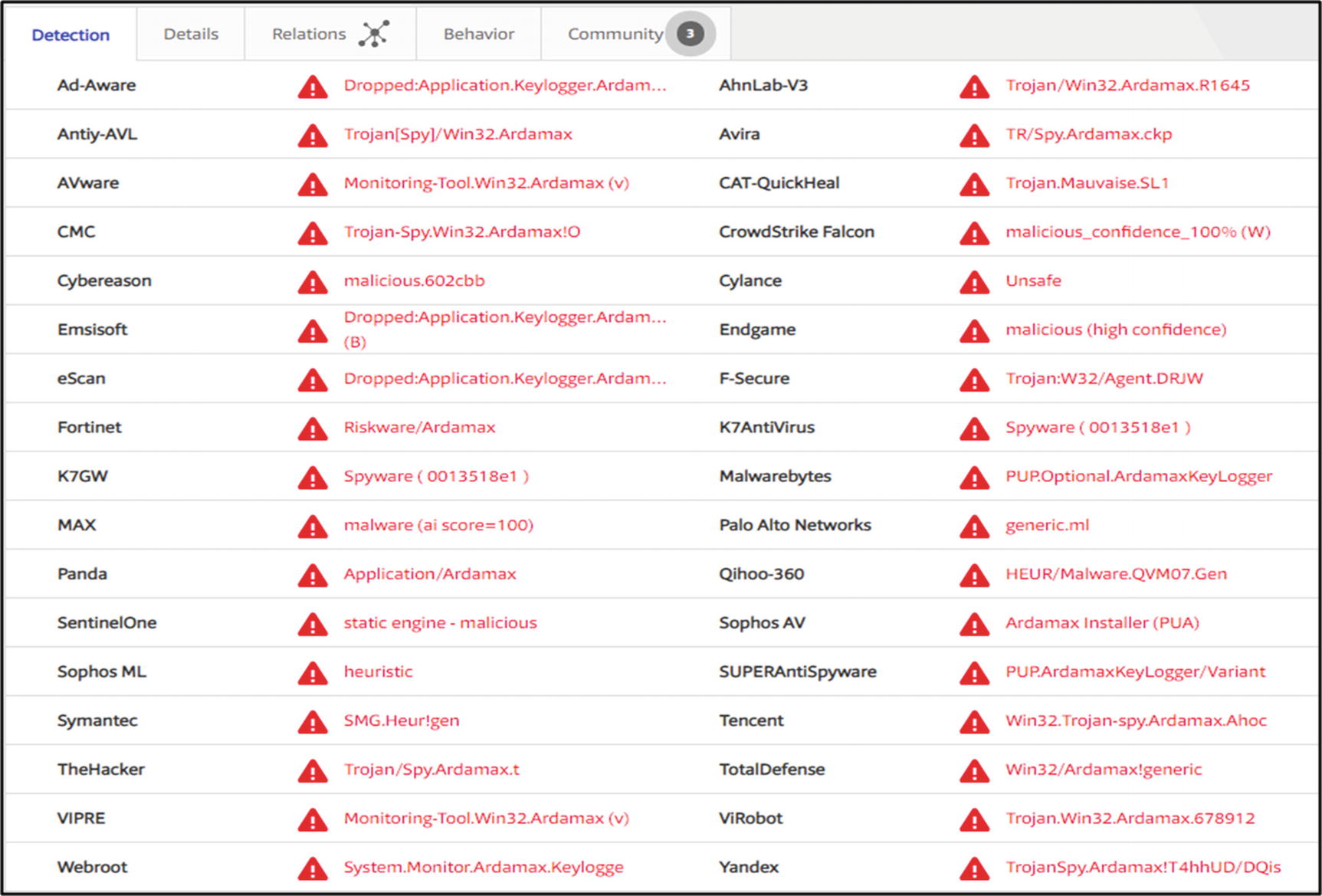
VirusTotal
As shown in Figure 9-27, there are various companies providing antivirus software that are listing our file as a malware file (trojan).
Dynamic Analysis
- 1.
Execute the malicious executable.
- 2.
Take registry shot by Regshot before and after the execution of the executable.
- 3.
Compare the two-registry shots by the same tool.
Registry Changes
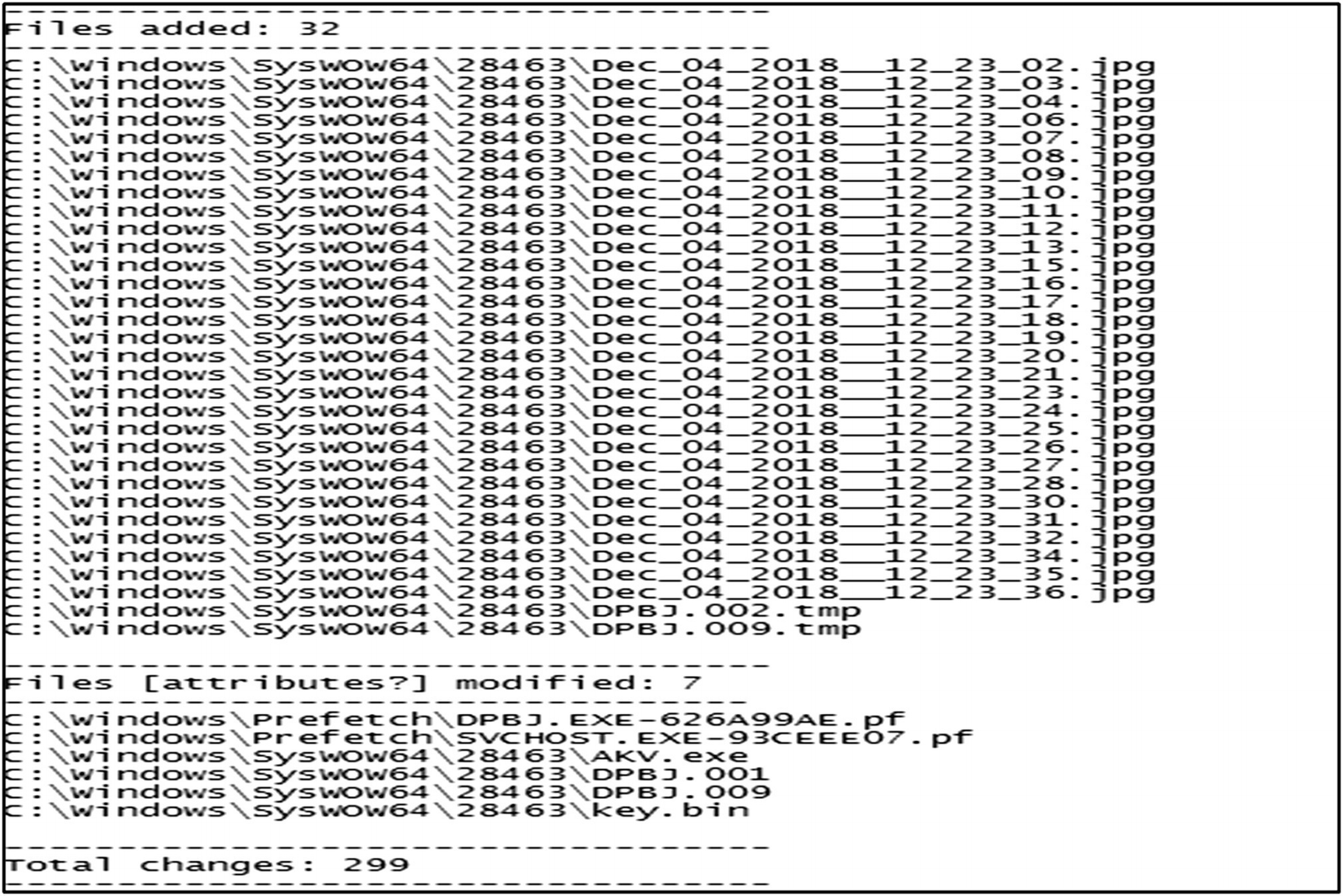
Path of the suspect file
Current Process on Explorer

Suspicious process is running on the system
Files Deleted and Created After Execution
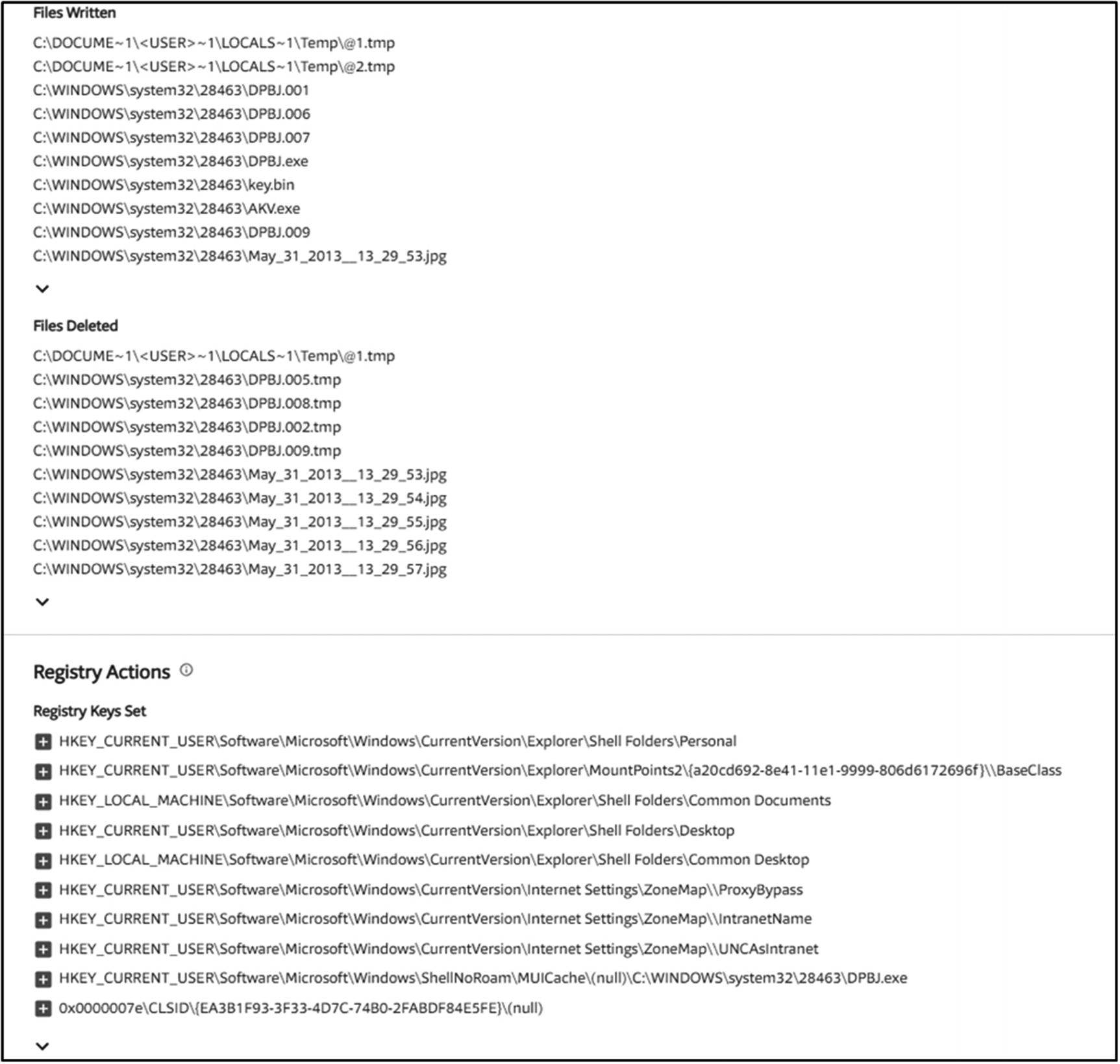
Written and Deleted Files in the registry
Network Outbound Connection
Go to the Relations section on the VirusTotal website, and you will find graphical representation of all the outbound connections.
File System Actions

File System Actions
Case Study: Ransomware
Ransomware attacks have been topping in the 2018 headlines for malware-based attacks. Time to move over Ransomwares, so this year, 2019, Cryptojacking is going to be the hacker’s attack choice for generating revenue.
Cyrptojacking involves victimization of someone else’s computing power to generate bitcoins or tokens. This involves compromising the victim’s system and loading a little cryptojacking script/program onto the victim’s system. These programs get triggered once the CPU/memory usage is of a smaller amount in order to avoid detection. They get triggered throughout the idle time. This results in the attacker using the victim’s IT resources as well as the internet bandwidth for generating bitcoins not getting detected easily.
Though the target for such attackers are servers of large corporations, they have also been known to infect even individual user’s systems.
In this case the risk of being found and identified is much less than in the case of ransomwares. This cryptomining code can go undiscovered for a very long time.
Summary
Malware is a term coined by merging two words: malicious and software, which is used to define a broad range of software that disrupt computer services, steal data, or compromise user safety.
Malware are software designed for malicious purposes and deliberately cause harm to its target.
We can classify malware as trojans, bots, exploits, viruses, worms, spyware, ransomwares, rootkits, and adware.
Malware analysis is the process of understanding how the malware functions, determining the purpose of a given malware sample, how to identify any malware on a system, and how to eliminate that malware.
Static analysis involves analyzing the malware without executing it.
Dynamic analysis involves running the malware and studying its behavior.
Behavioral Analysis is the method of observing the malware’s behavior upon triggering it. All the details such as how the system files are modified, resource consumption, and other parameters are observed by a forensic investigator.
RAM is a very useful part of the system that gives us an insight of all the data that is used by software that are being operational at the point of time the system was live and running. Memory Forensics, used by imaging the RAM of the system, can be used for malware forensics.
Various tools available for malware analysis are Cuckoo Sandbox, Yara Rules/Analyzer, REmnux, VirusTotal, Google Rapid Response, Radare, etc.
Analyzing malicious scripts requires proper preparation and analysis; so cyber forensic experts need to follow the standard procedures.
References
https://usa.kaspersky.com/resource-center/threats/malware-classifications
https://www.forensicswiki.org/wiki/Malware_analysis
https://www.first.org/global/sigs/malware/resources/