Linux is a UNIX-like open source operating system gifted to the world by Linus Torvalds. Here the word open source sticks out as it refers to the licensing nature of Linux. Being open source means that Linux is free and not owned by anyone. The source code is available to download and use for the public. Linux stays free as it is distributed under a GNU General Public License (GPL). This makes Linux a popular choice for computer enthusiasts and developers. Linux is a fast and secure alternative to other operating systems.
In 1991, Torvalds was a college student in Helsinki, Finland where he was working on creating his own operating system. What he developed was the Linux kernel, which is the core of Linux. He uploaded his work on to the internet, and coding enthusiasts all over the world kept adding their inputs to it; this sparked the community-driven Linux operating system.
Linux is a crucial part of the IT industry; it powers most of the supercomputers around the world, which are used in meteorology, statistics, and advanced computing.
Linux comes in numerous different versions called distributions: for example, Ubuntu, Debian, Fedora, SUSE, etc. Developers use the Linux kernel to create object-specific distributions. There are Linux distributions, which are designed to carry out specific tasks as they are configured for them. For example, Debian is ideal for servers; Santoku is ideal for Mobile forensics whereas Ubuntu, which is a derivative of Debian, is also a popular choice for servers, cloud computing, and mobile devices running on Ubuntu Linux; and Kali Linux, DEFT, Parrot, etc., are also ideal choices for penetration testing and digital forensic analysis.
Linux systems were earlier associated with black screens, command-line working, and dull desktops. This is a big misconception; Linux systems are modern with state-of-the-art GUI and customizable desktops. Linux still has the Terminal at its core, which most users use to input and execute commands, but modern systems have an equally capable GUI and other tools, which allow users to operate a Linux system with total ease.
Popular Linux Distributions
Linux has come a long way from being a command-line interface to having a Graphical user interface and a user-friendly desktop environment. Linux systems come with lots of open source and free tools to enhance the user experience. Here is a list of a few popular Linux Distributions that are commonly used.
Red Hat Linux
Red Hat Linux is the commercial version of the Linux distribution used extensively by large corporations, banks, and offices. Red Hat is associated with powering most of the Fortune 500 companies in their daily operations.
Ubuntu
Developed and maintained by Canonical, Ubuntu is one of the most popular Linux distributions among home users and professionals. Ubuntu has been revolutionary in promoting Linux among non-Linux users with its attractive features and strong performance. Many other Linux distributions are based on Ubuntu.
Fedora
Fedora is a Linux distribution sponsored by Red Hat and developed by the community-supported Fedora Project. It contains various free and open source software and aims to be on the leading edge of such technologies.
Debian
Debian is a Unix-like operating system, started by Ian Murdock on August 16, 1993. It is one of the earliest operating systems based on Linux Kernel and officially contains only free software. Any non-free software can be downloaded and installed from the Debian repositories. Debian is the largest collection of software in the world, having access to online repositories, which contain over 51,000 packages.
SUSE
SUSE is a Unix-based operating system built on top of the free and open source Linux kernel. SUSE Linux an acronym of “Software and System-Entwicklung” (software and systems development). It is of German origin, and it was mainly developed in Europe. The first version appeared in early 1994, making it one of the oldest Linux distributions.
Mint
Mint is a Debian- and Ubuntu-based Linux distribution, which aims to provide its users with a modern, elegant, and comfortable operating system.
Arch Linux
Arch is an independently developed Linux distribution, which is aimed at providing users a simple and minimalist environment for computing.
Linux Lite
Linux Lite is a free operating system based on Debian and Ubuntu, and it uses Xfce, which is a lightweight desktop environment. Xfce is similar to the Windows interface, and therefore Linux Lite it is a preferred choice for users who want to switch from Windows to Linux. It comes with lots of preinstalled applications like Dropbox, VLC, LibreOffice, etc.
File System
Linux supports many file system formats, but the default file system for modern Linux system is EXT4. The EXT4 is the successor of the EXT2 and EXT3 file systems, and it offers improved performance, reliability, and capacity. Improvements include Metadata and Journal checksums, which improved reliability.
Another upgrade in EXT4 is the introduction of extents. Extents allow a more efficient way to map blocks of data together. It groups contiguous blocks together by performing multiblock allocation at the time of file creation. This reserves a group of inodes together. Whenever a file is created or saved, it gets indexed by a number or inode. These inodes have multiple attributes attached to it, which is the metadata. EXT4 file system and inode structure. It is shown in Figures 3-1 and 3-2.

Inode structure in EXT4 file system
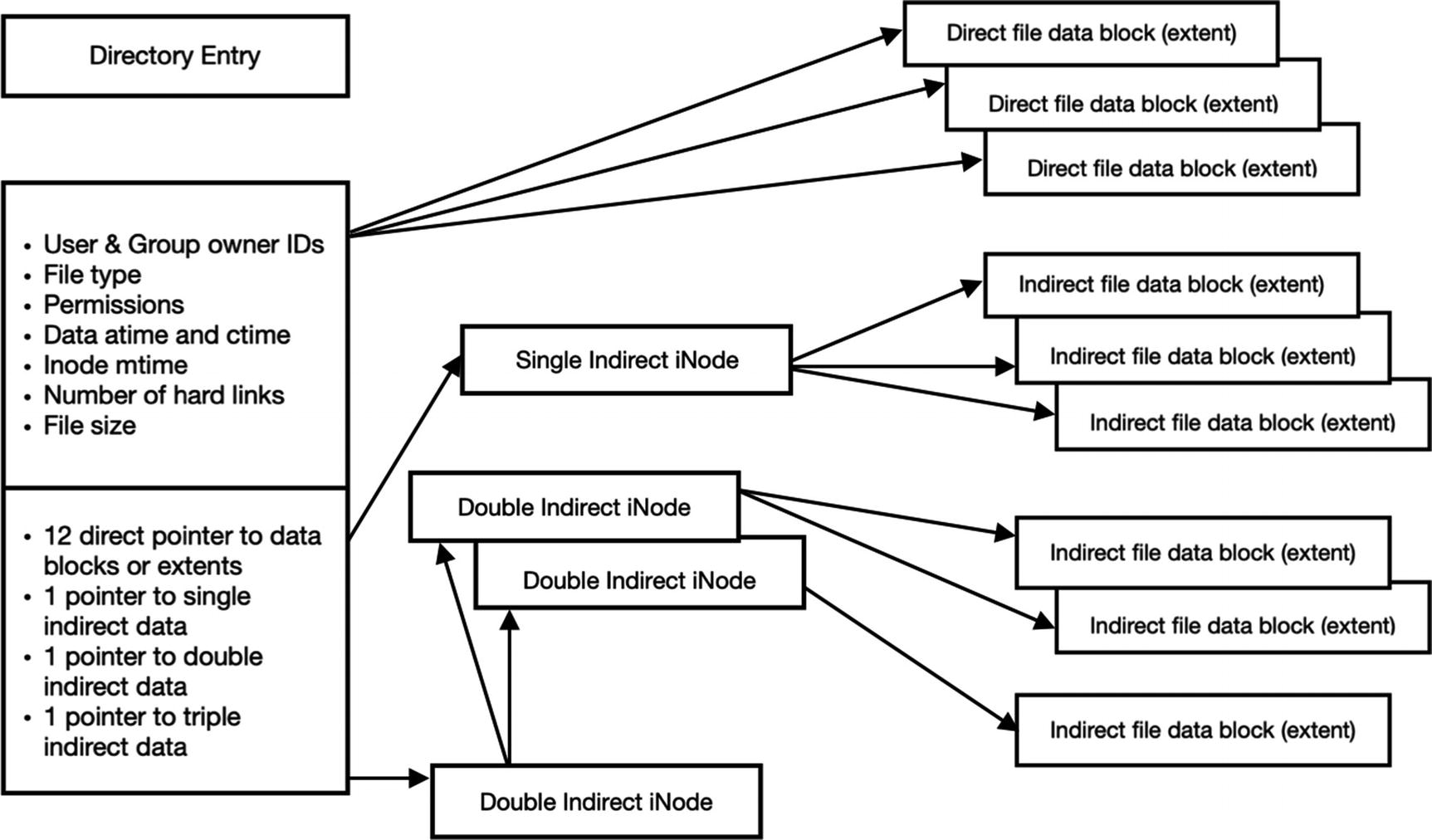
The inode stores information about each file and enables the EXT file system to locate all of the data belonging to it
Forensic Process for Linux Systems
A forensic investigator will follow the same protocol for the forensic examination of a Linux system as for Windows. Linux and Windows both have Volatile and nonvolatile evidence, and when it comes to open source tools, most of them are multiplatform. The approach is slightly changed as the artifacts are located at different places, and different tools will be required to obtain them.
Forensic Artifacts
Directory | Description |
|---|---|
/bin | The essential command binaries |
/boot | Files required for the system bootloader |
/dev | Device files |
/etc | System configuration files |
/home | Home directories |
/lib | Shared libraries and kernel modules |
/media | Mount points for removable media |
/opt | Add-on application packages |
/root | Root user home directory |
/sbin | System binaries |
/tmp | Temporary files |
/var/logs | Centralized repository of log files |
These locations have important files related to the system and user. Cyber forensics experts are needed to examine these locations and the data it houses.
Special Artifacts
Artifacts | Location |
|---|---|
User profile | /home/$USER |
System and Application logs | /etc |
Operating system information | /etc/os-release |
Operating system install | /root/install.log |
Host/ Computer name | /etc/hostname |
IP address, DNS | /var/log |
Time Zone Information | /etc/timezone |
User login History | /var/log/auth.log |
Recently Accessed files | /home/username/local/share/recently-used.xbel |
Command History | $HOME/.bash_history |
- 1.
Flaws in protocol designs or lacking security checks within the source code.
- 2.
Programming defects and misconfigurations resulting in security vulnerability.
- 3.
Lack of patch management.
- 4.
Outdated third-party applications such as Apache, MySQL, OpenSSL, etc.
- 5.
Most of the software packages come with default configurations; and while most of the settings are functions, some of them might negatively impact security measures.
Linux Distributions Used for Forensic Analysis
Linux systems can be used for forensic analysis and penetration testing as well. They come with lots of free open source tools built in to them for forensic analysis of digital evidence. Here are a few Linux distributions that can be used as forensic workstations by a Forensic Investigator.
Kali
Tools in Kali | |
|---|---|
Forensics | • Autopsy • Binwalk • Capstone • chntpw • dc3dd • ddrescue • DFF • diStorm3 • Dumpzilla • Extundelete • Foremost • Galleta • Guymager • iPhone backup analyzer • p0f • pdf-parser • pdgmail • REgRipper • Volatility • Xplico |
Password tools | • Acccheck • BruteSpray • CeWL • cisco-auditing-tool, findmyhash |
Apart from these tools , Kali has numerous other tools, which are useful in Information Security, as well as many more tools to boost up Kali’s arsenal of them.
DEFT
Digital Evidence and Forensics Toolkit or DEFT is an Italian-made Linux distribution. DEFT comes loaded with some of the industry’s best free and open source tools.
The goal of DEFT is to provide a well-designed and equipped environment for law enforcement agencies, cyber forensic experts, and military and government agencies for forensic investigations.
Tools in DEFT Linux | |
|---|---|
Artifact extraction | • Extractmsg, • Readpst, • Msgconvert • Rifiuiti2 • Reglookup, • pl • Evtxtract |
Data recovery | • Catfish • Testdisk • Scalpel • Bulk_extractor |
Imaging | • Affcat • Affcopy • Affcrypto • Affsign • Cyclone • Guymager |
Hashing | • Ssdeep • Md5deep • sha256sum • sha512sum |
Live Forensics | • Evolve • Evtxtract • Rekall • Volatility |
Malware Analysis | • Analyzepdf • Balbuzard • Damm • Mastiff • Chkrootkit • Brxor • Clamscan • Yara • Rkhunter • Unxor.py • Cuckoo • Muliscanner |
Mobile Forensics | • ADB • Fastboot • Bitpim • Apktool • Ipddump • idevicebackup2 • iphonebackupanalyzer2 |
Mount | • Bdemount • Dislocker • vmdkmnt |
Network Forensics | • ccze • Lnav • Multitail • CapAnalysis • Driftnet • Ettercup • Nmap • Tshark • Wireshark • Xplico • Kismet • Aircrack-ng |
Picture forensics | • Exifprobe • Vinetto • Outguess • Mat • Stagedetect |
Password recovery | • Cmospwd • Cup • Hashcat • John the ripper • Pdfcrack • xhydra |
Misc | • Maltego community • Tinfoleak |
Timeline | • Hfind • blkcalc • blkcat • fls • ifind • jcat • mmcat • mactime • sorter • srch_strings • fiwalk • log2timeline.py • jpeg_extract • psort.py |
Parrot
Parrot OS is a Linux distribution focused on cybersecurity and forensics. It was developed by Frozenbox Network and is based on Debian. Parrot OS is a modern, lightweight Linux distribution with a very detailed and elegant GUI. It was one of the first distributions to introduce anti-forensic tools to the world.
Santoku Linux
Santoku Linux is a specialized mobile forensic Linux platform sponsored by NowSecure. Santoku has a wide array of tools built to carry out general, mobile forensic investigations. It is based on the Ubuntu platform. It is capable of imaging NAND, media cards, and RAM; and it also performs mobile malware analysis.
Blackbuntu
Blackbuntu is a Linux operating system distribution that is mainly used for penetration testing and digital forensics. Blackbuntu is designed for computer security, penetration testing, information security, and internet security.
Paladin Linux
Developed by Sumuri, Paladin is a versatile Linux distribution, which is based on Ubuntu. It is one of the most beautifully crafted forensic suites available in the market. With over 100 tools spanning across 33 categories, Paladin is fully equipped to take on any forensic challenge.
CAINE
CAINE is an acronym for Computer Aided Investigation Environment. It is a Linux distribution built for Digital Forensic Investigation. It offers a complete forensic environment and user-friendly GUI. This project is completely open source.
Challenges
The fundamental approach to a forensic examination of a Linux system remains the same as for any other operating system. However, it is important to note that there are few changes in the design of the Linux system, which the cyber forensic experts need to make note of.
First, Linux does not have a central Registry like Windows. The data is scattered across the OS, which has to be collected from multiple sources. Second, metadata for files is zeroed when it is deleted. This becomes a huge problem at the time for data recovery.
Over a period of time, Linux systems have gained significant popularity and have seen a growth in its user base; however, compared to Microsoft Windows, it is still used in very few home systems in comparison. Due to such low numbers of systems, there not been a lot of buzz to create specialized forensic tools for Linux systems.
Linux is mostly used for advanced computing needs like server systems or corporate computing, whereas in home systems it serves as a desktop/notebook operating system. We mentioned that there are numerous Linux distributions that are designed for specific tasks or have unique USPs. This is the challenge that a cyber forensic examiner faces when a Linux machine is encountered. Although these Linux distributions have “the Linux kernel” at the core distribution, the developers put unique code above it to create vivid and special operating systems.
Cyber forensic experts will need to study the operating system to obtain the forensically important artifacts and use compatible tools and techniques. Although the EXT4 is a strong and stable file system, it is still a new feature in modern Linux systems, so there is an issue of tool compatibility with it.
Linux tools are mostly command line and therefore not the easiest to use. This is due to less demand and less availability of Linux forensic tool developers. But with changing times, this is sure to change in the due course of time; and more tools are expected to be seen in the future.
Differences Between Windows and Linux from a Forensics Perspective
Windows | Linux |
|---|---|
Windows has a central Registry that is used for collecting and storing the configuration settings of Windows components, installed hardware & software applications, etc. | Linux does not have a central Registry like Windows. The data is scattered across the OS, which has to be collected from multiple sources. |
Windows supports FAT (with its variations) or NTFS file systems. | Linux supports EXT (with its variations) file system. |
Most of the tools are GUI based and easy to understand or use. | Most of the Linux tools are command line and not GUI based, and hence they are not the easiest ones to use. |
In Windows, you can have many user accounts with administrative privileges. | Linux has only one administrative account called root. Root account has complete control of the system. |
In Windows, you can find file permissions in the Security tab of Properties section of My Computer, and they are kept in Registry. | In Linux, by running the ls l command on a directory or on a particular file, you can view these file permissions. |
Windows has a Recycle Bin folder to store deleted files, and these deleted files can be recovered from it. | Linux distributions have Trash functions that contain deleted files of the particular user. |
In Windows, a Computer Forensics 'write blocker' device (it allows gathering the data without writing anything on the drive) is used during the examination of the suspect's hard drive. | In Linux, the examiner has to manually select to mount the file system as read-only. |
In Windows, default location of Event Viewer log files is in the folder:%SystemRoot%System32Config | In Linux, configuration files and system logs are stored at: /etc/passwd, /etc/shadow, /etc/hosts, /etc/sysconfig, /etc/syslog.conf |
Case Study: Listing Partitions
- 1.Type fdisk -h for a quick overview of arguments that can be passed with it. See Figure 3-3.
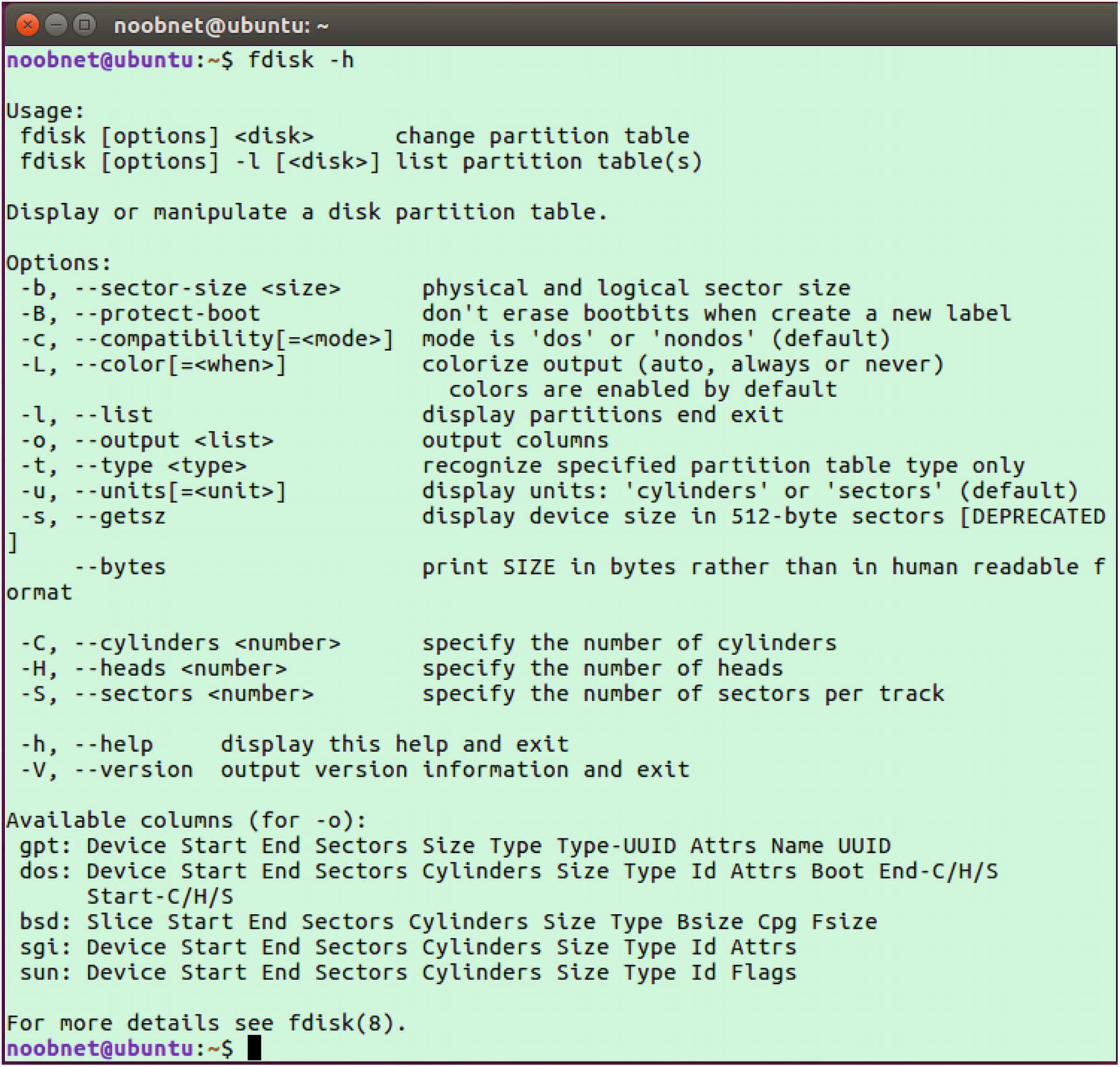 Figure 3-3
Figure 3-3Fdisk help command
- 2.Type fdisk -l to get a listing of all available drives and the partition information. This is shown in Figure 3-4.
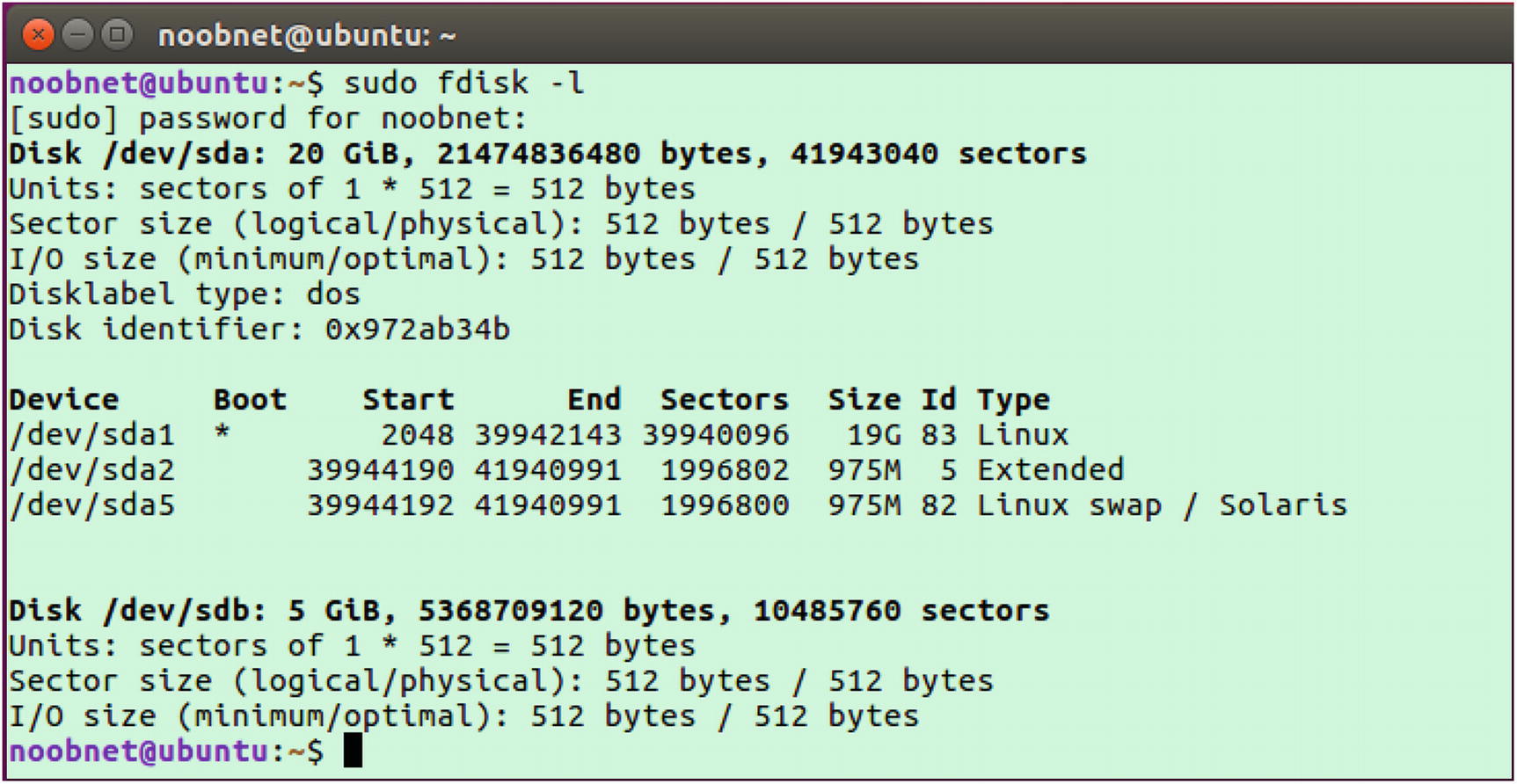 Figure 3-4
Figure 3-4fdisk list command
- 3.
Here in Figure 3-4, we can see that there are two hard drives on the system: /dev/sda and /dev/sdb. Linux stores disk names in alphabetical order. Here /dev/sda is our first hard drive of size 20GB and contains three partitions, namely /dev/sda1, /dev/sda2, and /dev/sda5. /dev/sdb is our second hard drive of size 5GB, which we are going to use for imaging in the next step.
After we get the list of hard disks on the system, we can create a dd image of the disk or a hard drive or flash drive. dd is a command-line utility for Unix operating systems, and its main functionality is copying and converting files. Here we are going to use this utility to create an image of the partition on Linux system.
Here 'if=/dev/sdb' means read from partition /dev/sdb.
'of=image.001' means write the contents of partition /dev/sdb to image.001 file.
'bs=2M' means read and write 2048 i.e. 2MB of file at a time.
'status=progress' to show the status of number of bytes copied to the file.

dd command on Linux
Case Study: Memory Acquisition of Linux System
- 1.
We will clone the LiME source code from the git repository https://github.com/504ensicsLabs/LiME/ .
- 2.The command to clone the source code is git clone https://github.com/504ensicsLabs/LiME/ shown in Figure 3-6.
 Figure 3-6
Figure 3-6Downloading LiME tool
- 3.Now we will build the source code so that we can get the kernel object. Change the directory to LiME and then go to the src directory. Type the command make to create the kernel object. The whole procedure is shown in Figure 3-7.
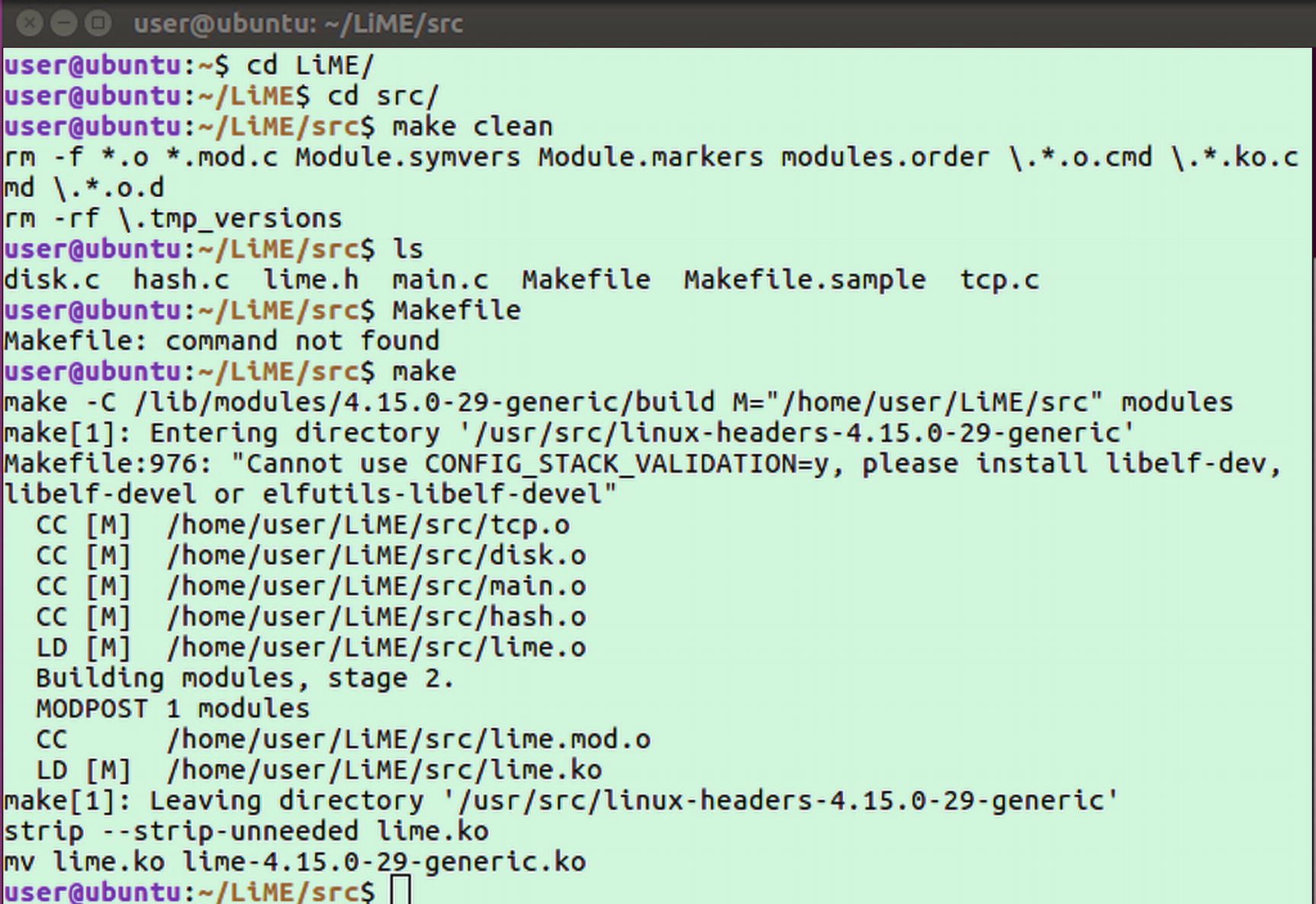 Figure 3-7
Figure 3-7Creating kernel object
- 4.To capture RAM contents, type the following command as shown in Figure 3-8. You can use any path to save the memory file, including the external drive, but make sure that the external drive has been mounted.sudo insmod ./lime-4.15.0-29-generic.ko "path=../Linux_Memory.mem format=raw"
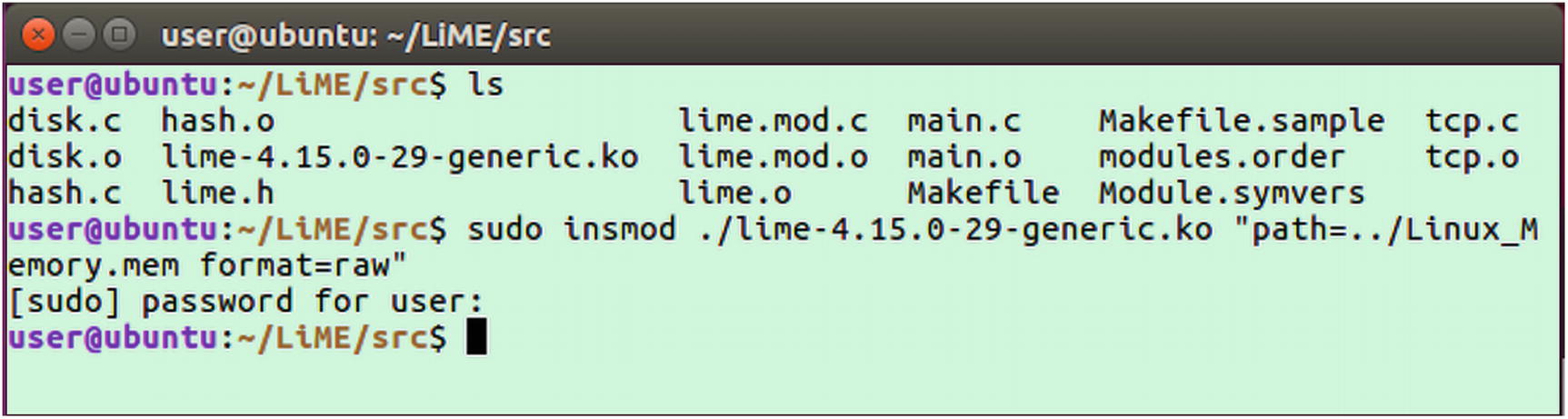 Figure 3-8
Figure 3-8Creating memory image
- 5.
We have successfully created a memory dump image of our Linux system using LiME tool. You can use either volatility or rekall, or any other memory analysis tools, to analyze the RAM dump files.
Rekall is a free and open source advanced forensic and incident response framework, which implements the most advanced analysis techniques in the field, while still being developed in the open. It provides an end-to-end solution to forensic investigators.
Case Study: SysScout Tool
We can carry out a live acquisition from a Linux machine using SysScout tool.
SysScout is an open source framework available on https://github.com/joshbrunty/SysScout . This tool helps us find the vital information from a Linux operating system such as timing information, network and DNS information, last online user, logged-in users, and so on.
- 1.Download and run SysScout tool using command git clone https://github.com/joshbrunty/SysScout . This is shown in Figure 3-10.
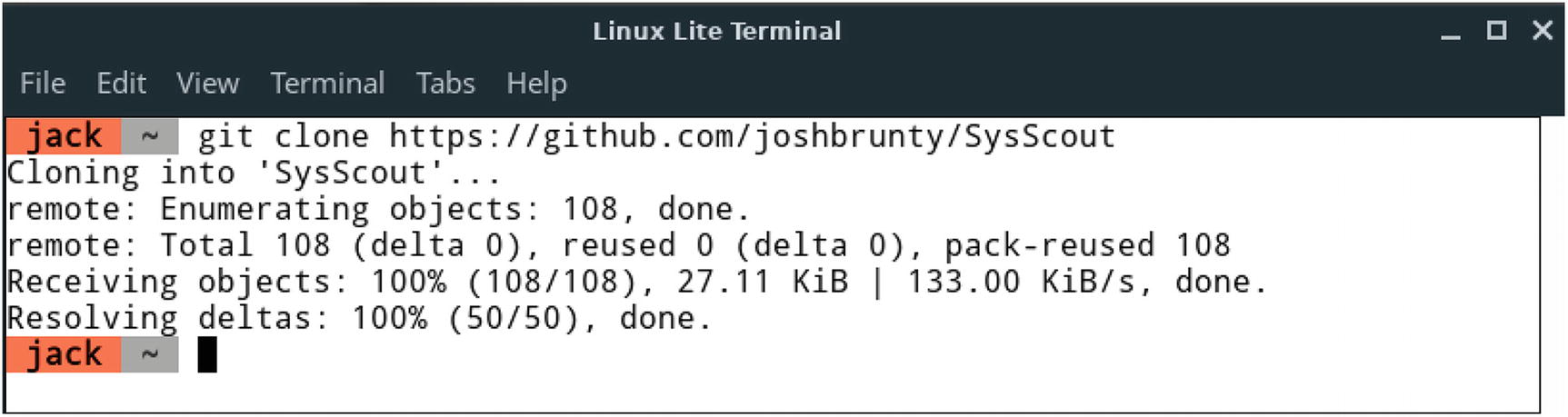 Figure 3-10
Figure 3-10Installing SysScout on Linux system
- 2.Go to the SysScout folder using the command cd SysScout as shown in Figure 3-11.
 Figure 3-11
Figure 3-11SysScout directory
- 3.To run this tool, type command bash SysScout.sh. This tool will provide you with various options for live forensics as shown in Figure 3-12.
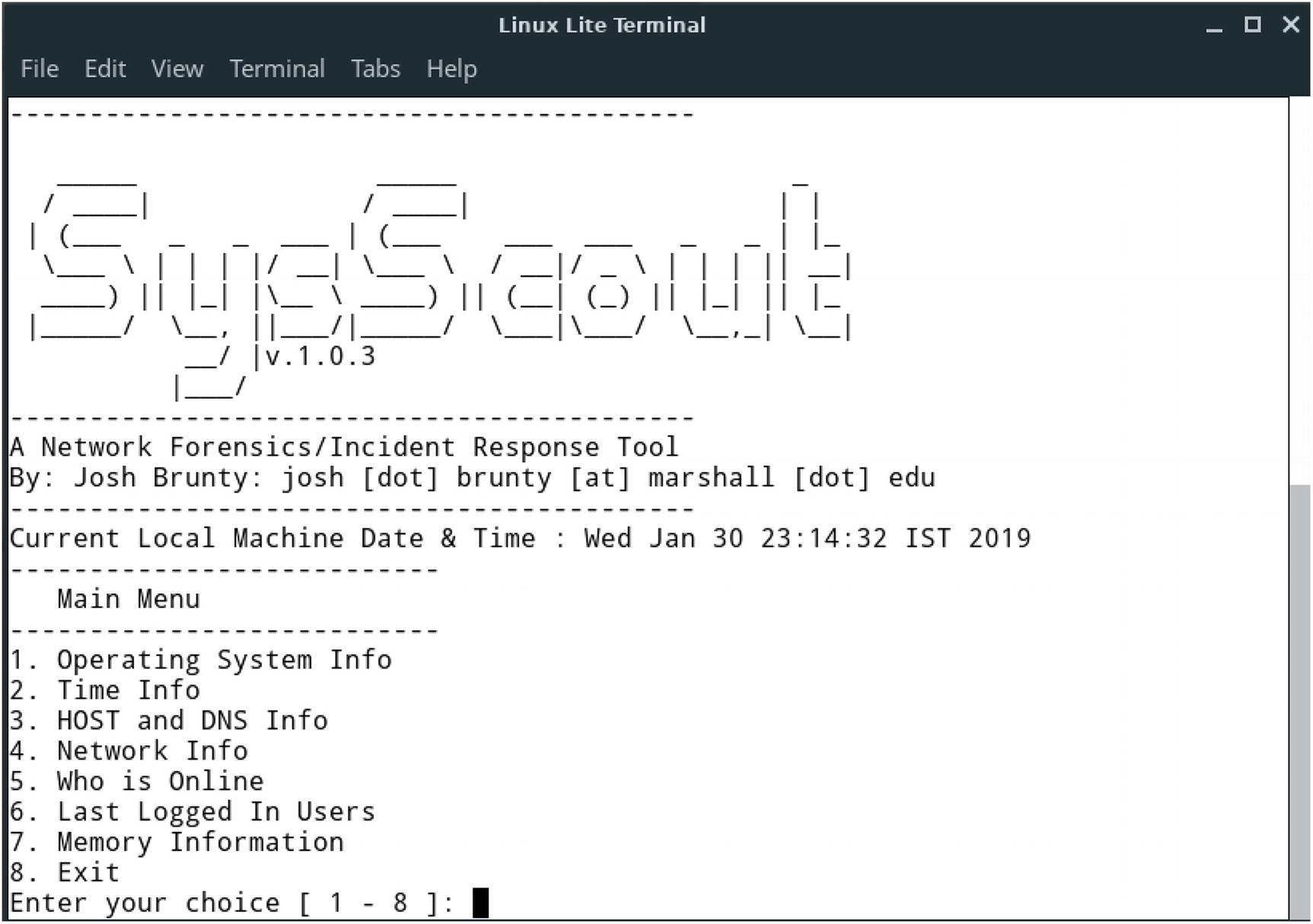 Figure 3-12
Figure 3-12Starting SysScout
- Option 1: To get the Operating system information, select option 1 from the Main Menu. As shown in Figure 3-13, we can see it's a Linux Operating System.
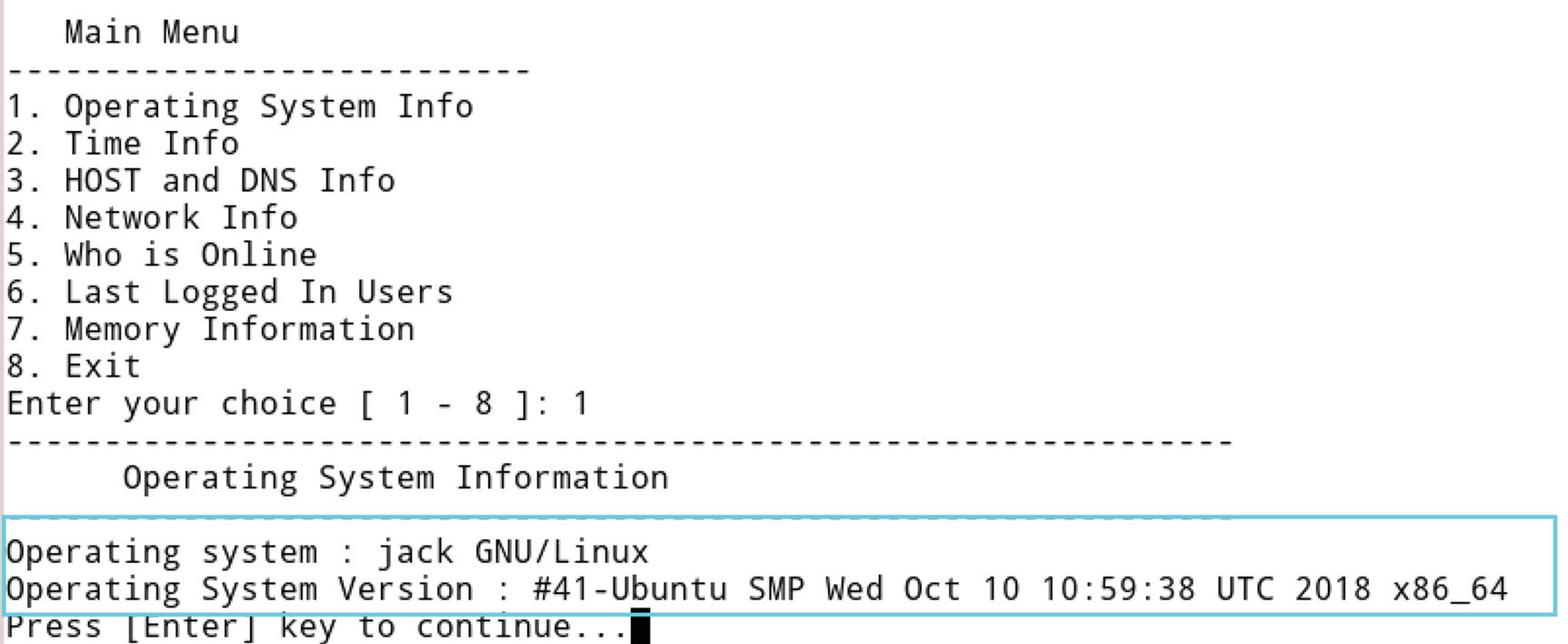 Figure 3-13
Figure 3-13Results of option 1
- Option 2: To find the current time information, select option 2 in the main menu. This option gives the time zone, machine time, and date information as shown in Figure 3-14, which helps to match the timelines of the crime.
 Figure 3-14
Figure 3-14Results of option 2
- Option 3: To find the hostname and DNS IP address, select option 3 from the main menu. Here our host name is jack, Network IP is 127.0.1.1 and DNS IP is 127.0.0.53 as shown in Figure 3-15.
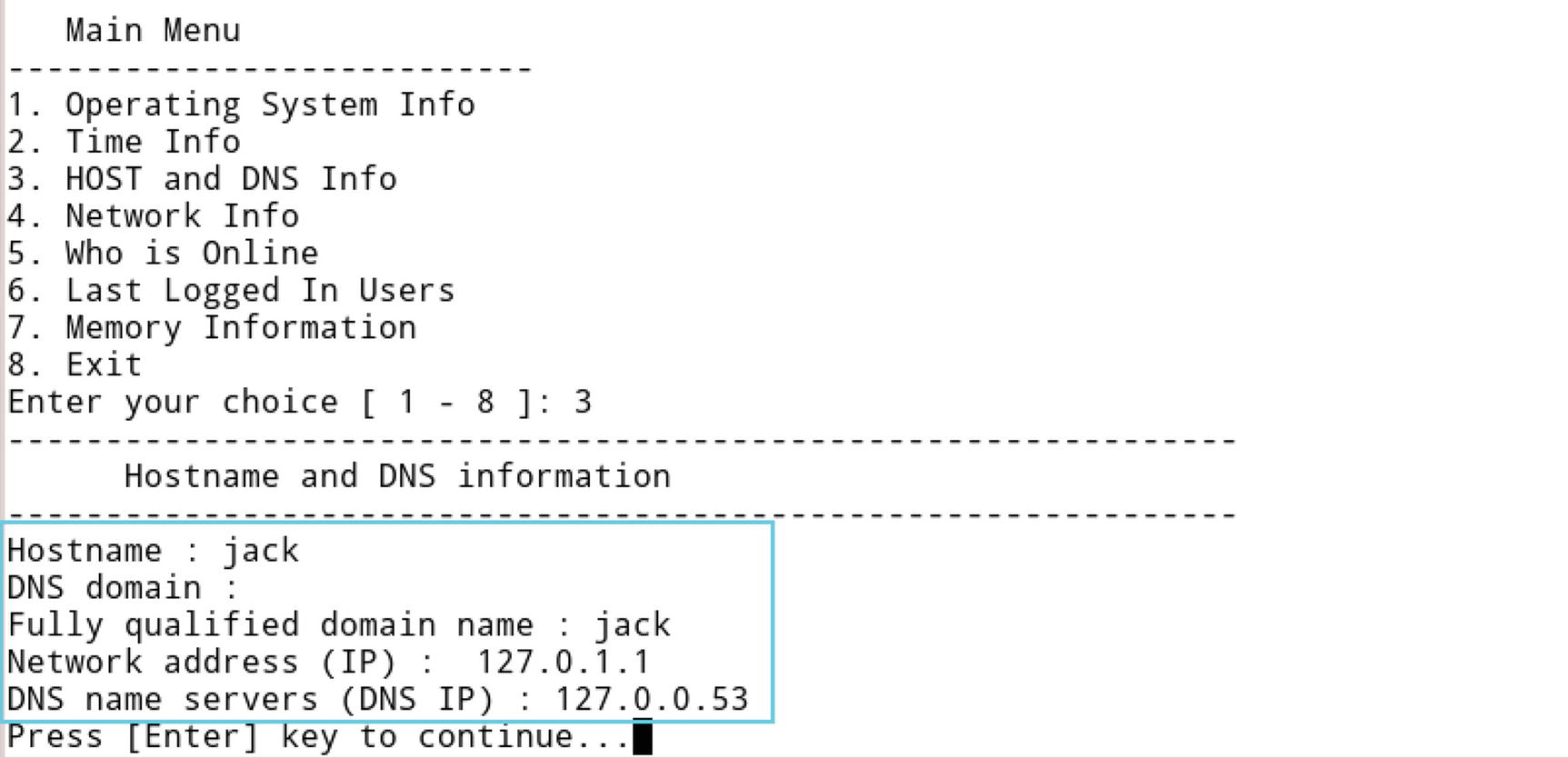 Figure 3-15
Figure 3-15Results of option
- Option 4: To get the information about the IP address, a routing table, and mac address, select option 4 from the main menu. This information helps the examiner to find any suspicious connections or traffic to the victim system. Results are shown in Figure 3-16.
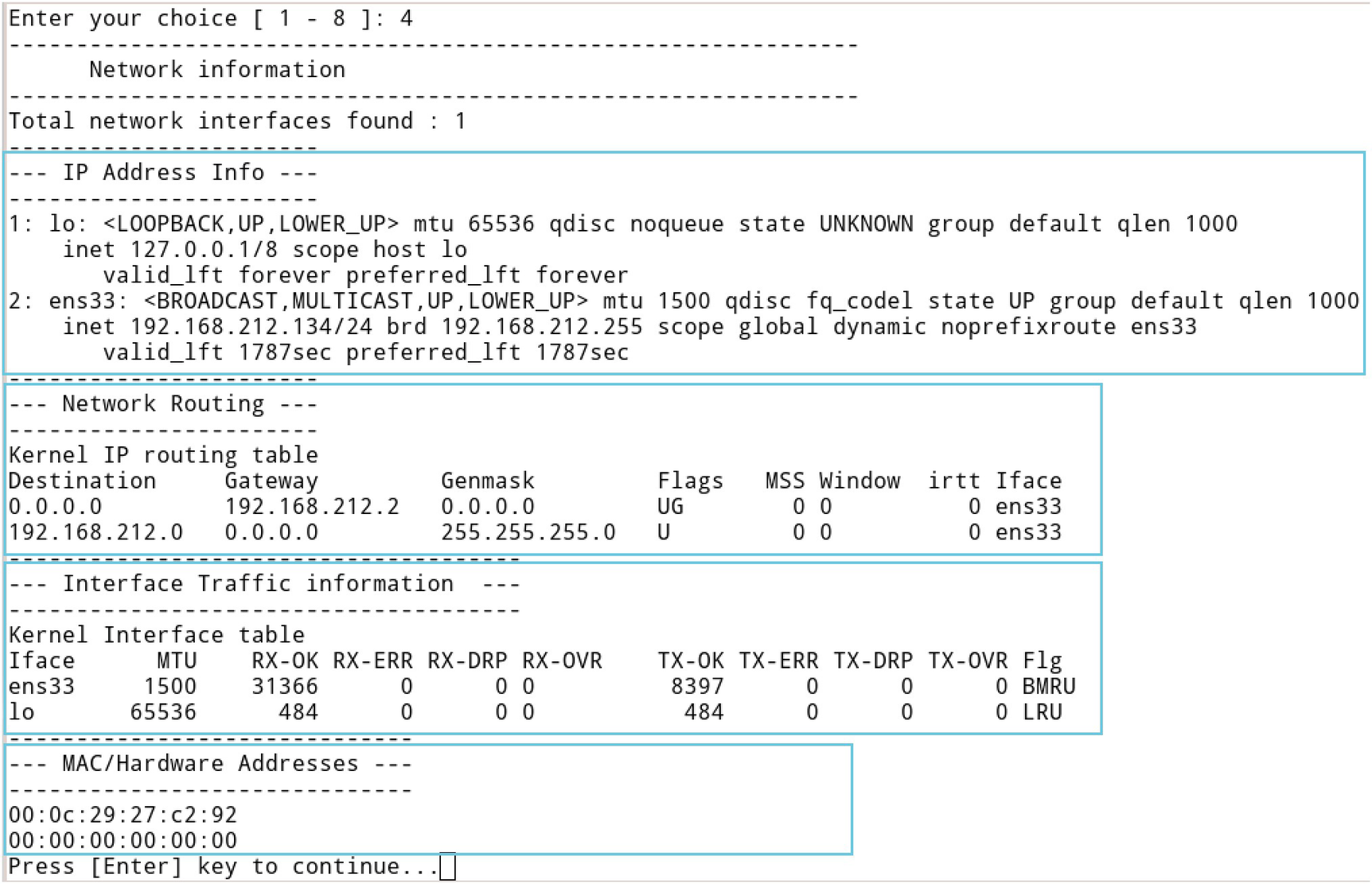 Figure 3-16
Figure 3-16Results of option 4
- Option 5: To get information about how many users are logged in, select option 5 from the main menu. Here we can see in Figure 3-17 that only one user ‘jack’ is logged in. This information will be useful to check if the intruder created any new user accounts.
 Figure 3-17
Figure 3-17Results of option 5
- Option 6: This option lists the last logged-in users on that system. As we can see in Figure 3-18, the user ‘jack’ logged in twice and currently this user ‘jack’ is still logged in. This is very useful in a forensic examination to check which users were logged in during the time of the crime.
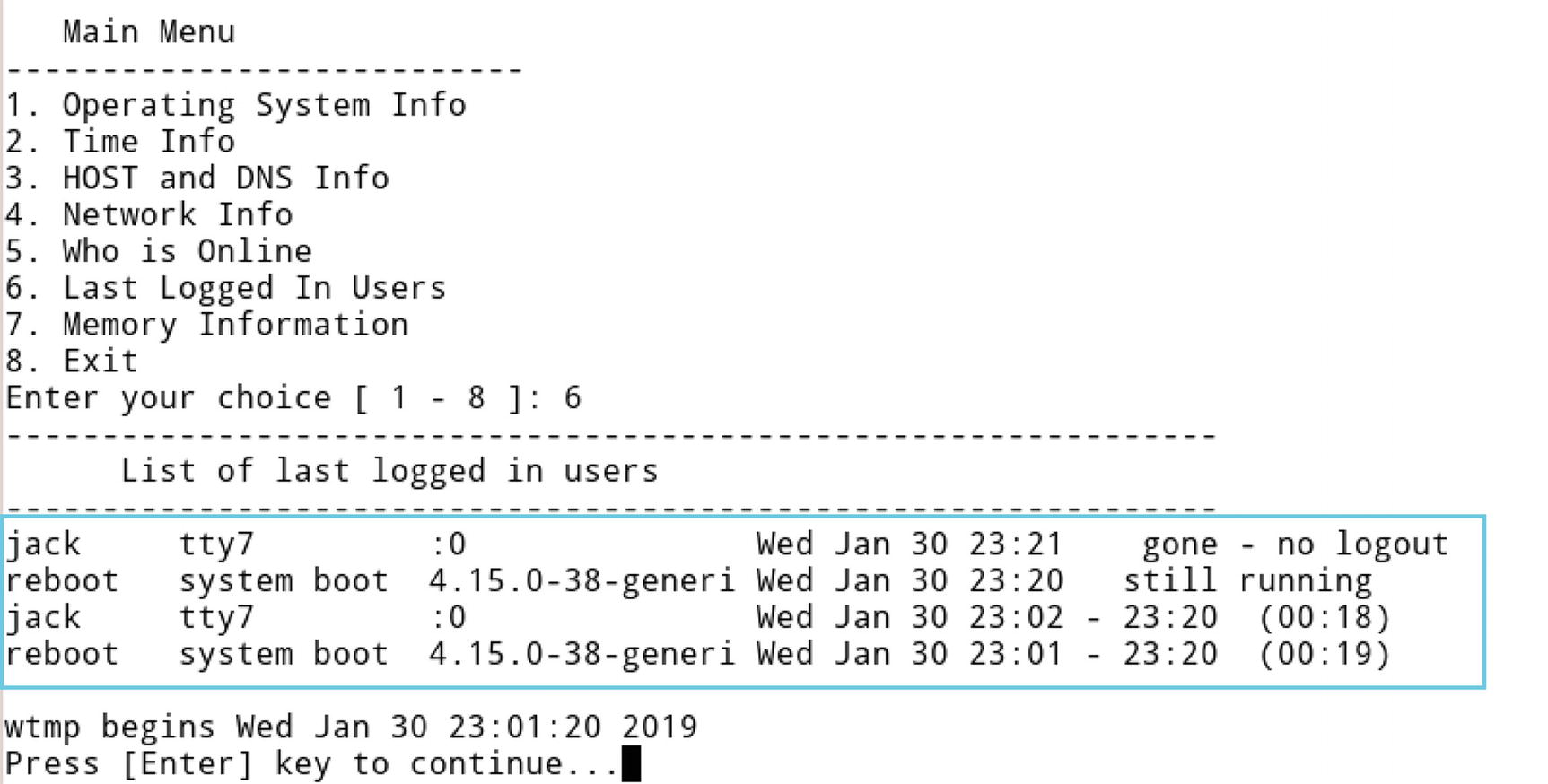 Figure 3-18
Figure 3-18Results of option 6
- Option 7: This option provides current (RAM) memory information and the top five memory utilizing process information like free and used memory, along with virtual memory statistics as shown in Figure 3-19.
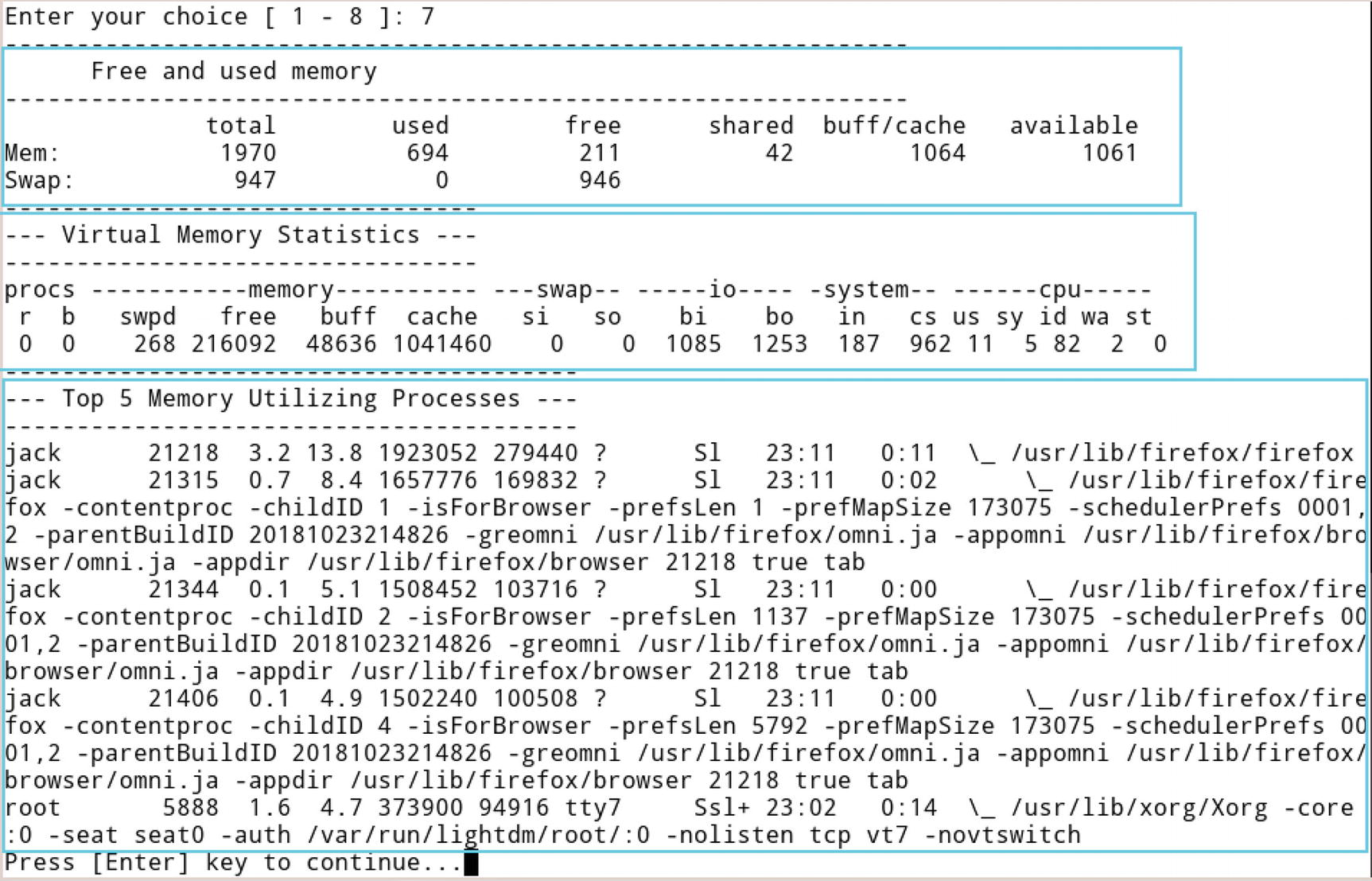 Figure 3-19
Figure 3-19Results of option 7
Option 8: To Exit
We successfully have found information about the operating system, timings, network and DNS details, last online user, current logged-in users, and memory information from the Linux Lite operating system using the SysScout tool.
Case Study: Raw Image Analysis
- 1.To check if the image belonged to a disk or a partition type, use the command mmls image.001 as shown in Figure 3-20. Our image is of a hard disk and not the partition in the hard disk; therefore, the output is ‘cannot display partition type’.
 Figure 3-20
Figure 3-20mmls command
- 2.fsstat (name of our image file) command is used to determine the partition type as shown in Figure 3-21 . It displays the details associated with the file system. Here we can see the file system is EXT4.
 Figure 3-21
Figure 3-21fsstat command
- 3.Use ils –a image.001 to list inode information and to find the list of MFT entries. MFT entries contain information details like file creation, Modification, accessed, etc., of the file stored in the disk image image.001. Results are as shown in Figure 3-22.
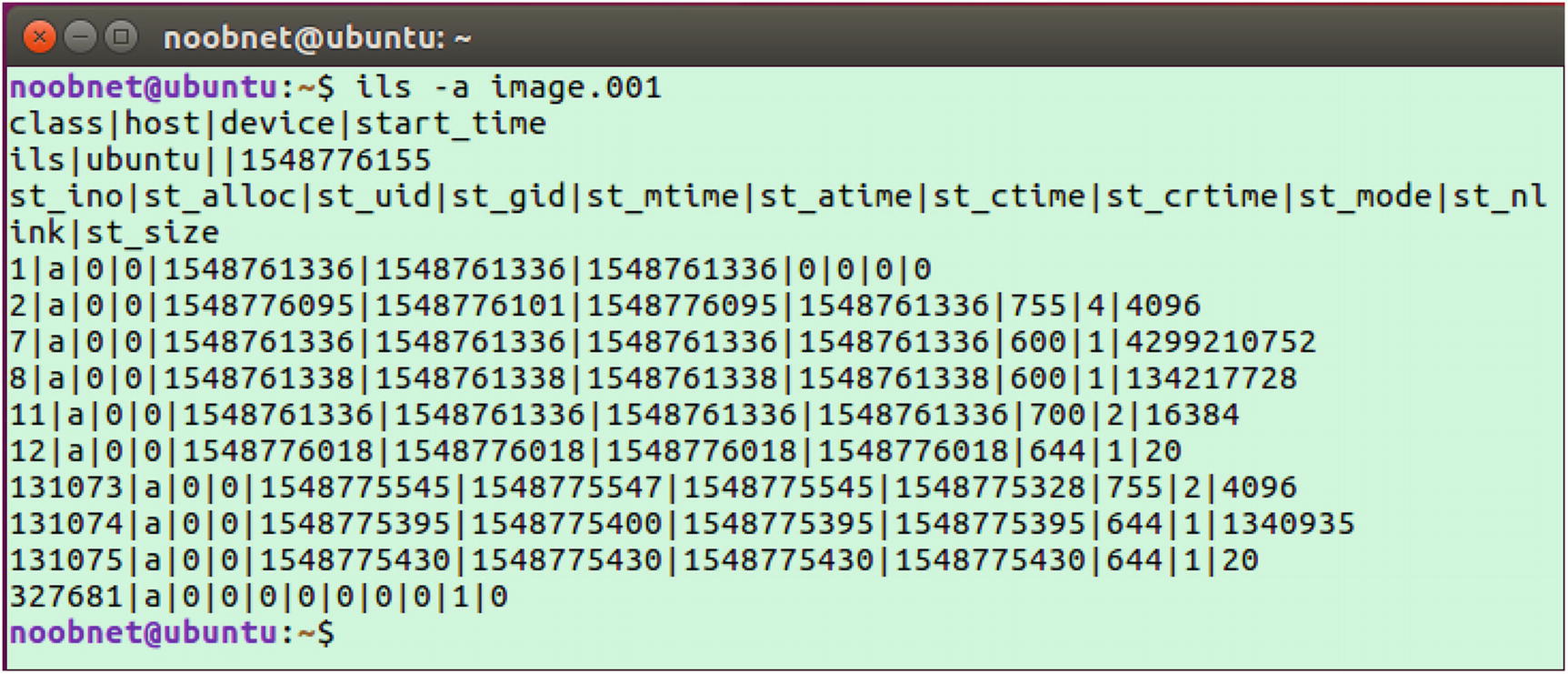 Figure 3-22
Figure 3-22ils command
- 4.To list files and directory names on the disk image, use the fls image.001 command as shown in Figure 3-23.
Here r/r denotes a file and d/d denotes a directory, as shown in Figure 3-23. v/v denotes a virtual file or directory (not shown in the image ).
The first value in the second field denotes the MFT entry. For example, the MTF entry for noobnet directory is 131073, as shown in Figure 3-23.
- Some files have the * symbol: for example, my_document file. This means that the file was deleted at some point, as shown in Figure 3-23.
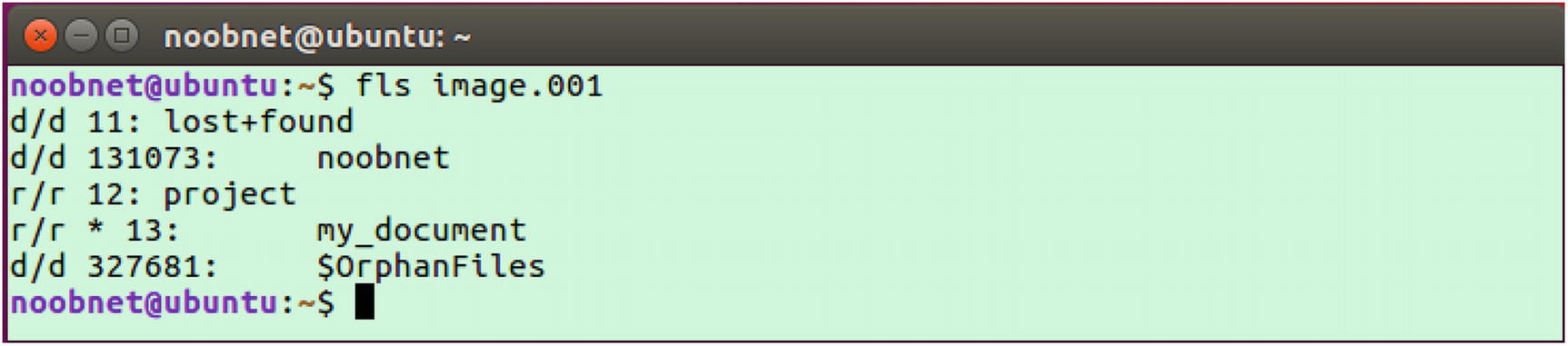 Figure 3-23
Figure 3-23fls command
- 5.The command istat image.001 displays the timestamps of when the file was created, accessed, and modified, as shown in Figure 3-24.
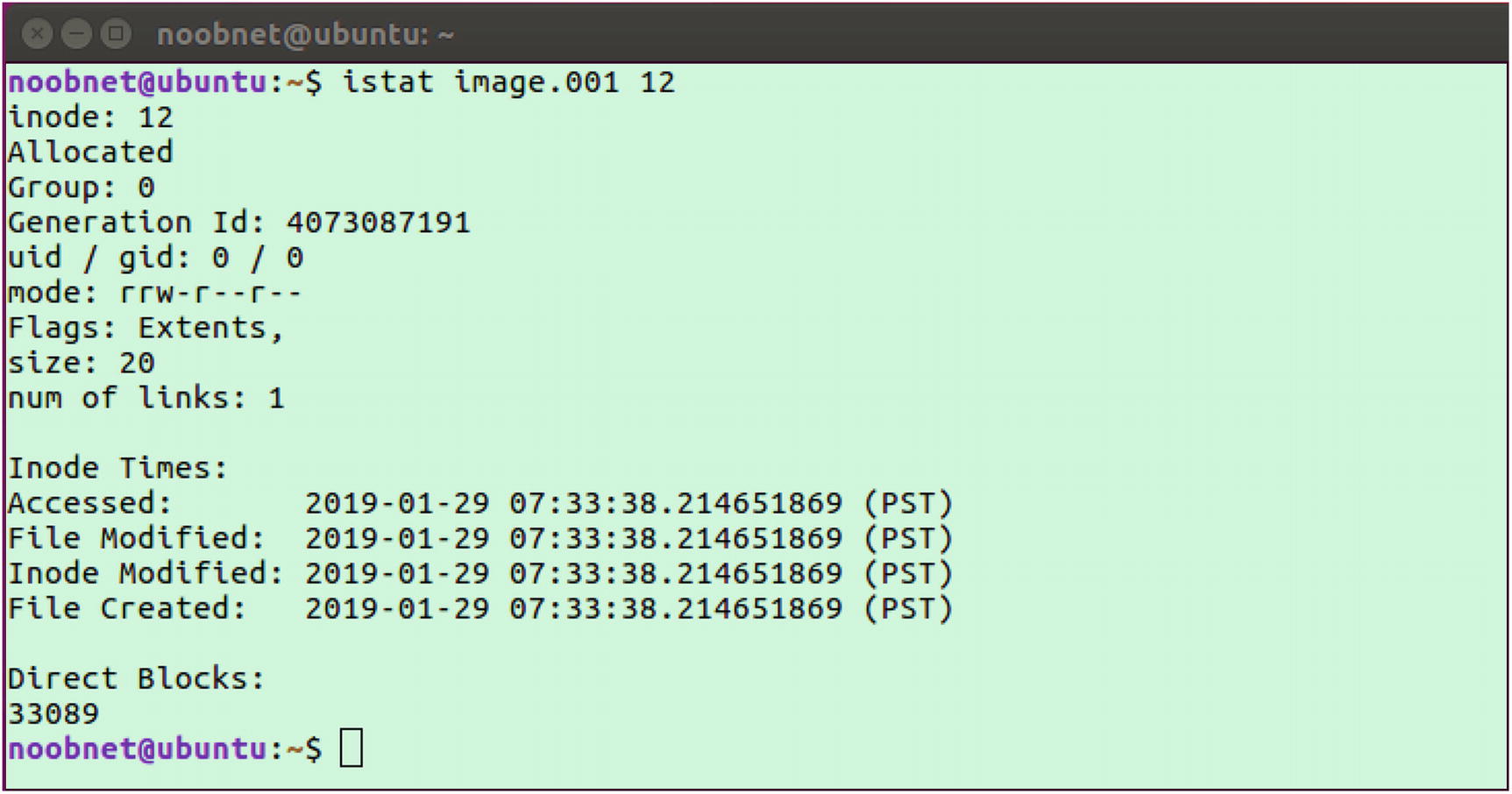 Figure 3-24
Figure 3-24istat command
- 6.Type fls –d image.001 command as shown in Figure 3-25 to see only deleted entries.
 Figure 3-25
Figure 3-25fls -d command
- 7.We can use istat image.001 command to display timestamps of the deleted entries as shown in Figure 3-26.
 Figure 3-26
Figure 3-26istat command for a deleted file
Overall, we have analyzed the dd raw image and retrieved the timestamps of files currently present and deleted as well using the tool sleuth kit. This is an important analysis that helps investigators during investigation of a case.
Summary
Linux is an UNIX-like open source operating system. Being open source meant that Linux was free and not owned by anyone.
Linux comes in numerous different versions called as distributions like Ubuntu, Fedora, SUSE, Debian, Arch Linux, etc.
Linux supports many file system formats, but the default file system for modern Linux system is EXT4. The EXT4 is the successor of the EXT2 and EXT3 file system, and it offers improved performance, reliability, and capacity.
A forensic investigator will follow the same protocol for forensic examination of a Linux system as for Windows.
Kali, DEFT, Parrot, BlackBuntu, Santaku, and CAINE are some Linux distributions used as forensic workstations.
References
https://ieeexplore.ieee.org/document/6643000
https://www.sciencedirect.com/science/article/pii/S174228761400019X
https://www.sciencedirect.com/science/article/pii/S1742287612000357

