Email was invented way back in the 1960s but was used to a limited capacity and in a restricted manner; it only became popular by 1993. Email communication sparked the business revolution as it connected the world. Although many modern forms of communications have been invented, email still remains the most popular in the corporate world. As email communication flourished, it became an important part of our personal and professional lives. Email is an important part of e-discovery and forensic investigation, especially with the rise of cybercrime.
In this chapter, we will look into different email crimes and how their investigation takes place, by looking at different case studies. Email played a major role in the investigation of the Enron scandal, which we shall see later on.
Email Anatomy
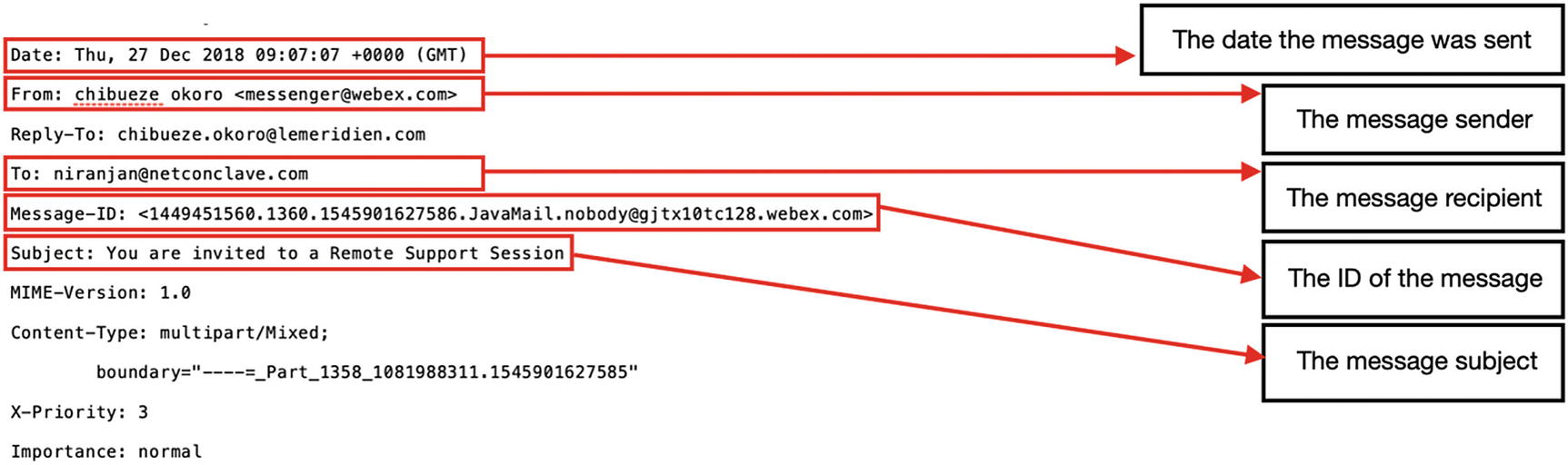
The email consists of two components: Header and the Body. Every email has a header, which is a section that contains information about the source of the email and the path it traveled to reach the destination. The body of the email is what we read in the email; it contains the message and/or any attachments, which the sender has sent.
Working of Email System
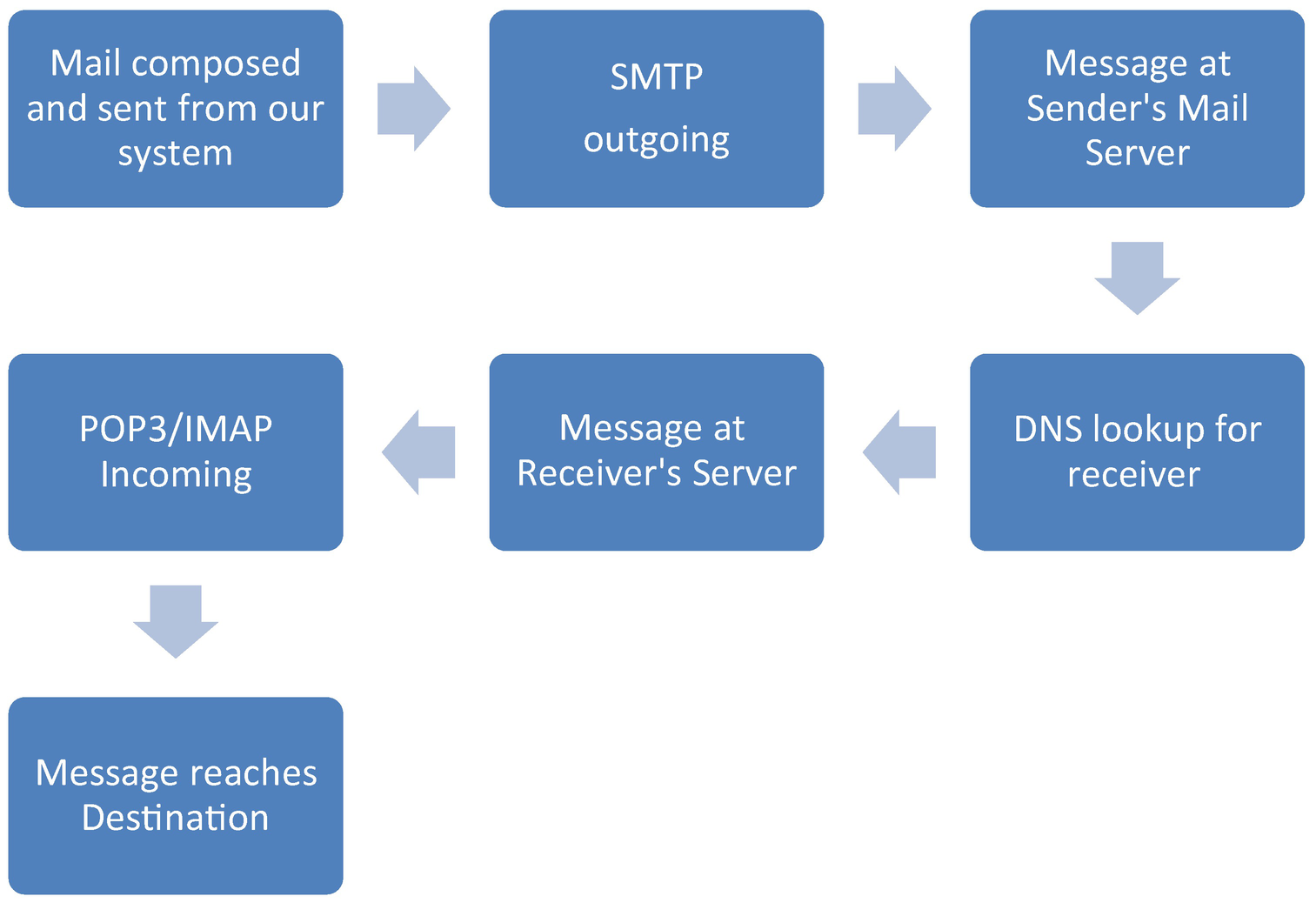
Working of Email System
The email client is known as a Message User Agent (MUA), which is a program that is used to send and read email. It translates the message to email format and forwards it to the Message Submission Agent (MSA).
The MSA is responsible for determining the destination in the Simple Mail Transfer Protocol (SMTP) and resolves the domain name to determine the fully qualified domain name of the mail server.
The Domain Name System (DNS) server responds to the request by checking for the domain with the mail exchange servers listing.
The mail is then forwarded to the Mail Transfer Agent (MTA), and finally the message arrives at the Mail Delivery Agent (MDA), which delivers it to the mailbox.
The Receiver’s MUA uses either Post Office Protocol (POP3) or Internet Message Access Protocol (IMAP) to get the message.
Protocols Used in Email Communication
Emails in today’s digital world play a very significant and crucial role in electronic communication. In order to make this electronic communication happen and transmit information between two or more entities, we have a set of protocols.
Simple Mail Transfer Protocol (SMTP)
The SMTP is a text-based and application-level protocol.
The port numbers used for SMTP are port 25 or 2525 or 587. Secure SMTP (SSL / TLS) uses port 465 or 25 or 587, or 2526.
Post Office Protocol (POP3)
POP3 server handles all incoming emails.
Only a single mailbox is allowed per server.
POP supports offline access to messages, which cuts down on internet usage time.
POP3 protocol commonly works on two ports: the first port 110, which is used as the default POP3 non-encrypted port; and the second is port 995 when you need to connect securely using POP3.
Internet Mail Access Protocol (IMAP)
Email is held and maintained by the remote server.
It enables users to download and delete an email without reading it.
Multiple mailboxes are supported.
Suitable for attachments.
IMAP protocol works on port 143 and uses port 993 for SSL/TLS-encrypted IMAP.
Email Crimes
The rise of crimes related to email escalated as the population of digital citizens grew to millions. However, new users are not given any guides or pointers of how to be safe on the web. Eventually many such users become easy targets of hackers and scammers who exploit information and, in many cases, demand money from them. Phishing mails, Fraud mails, Harassment mails, etc., are just some examples of email crimes. Email has mostly been a vector for white-collar crimes but now is being used to spread terrorism and is also being used by stalkers to send threats.
Phishing
Phishing scams are primarily emails that lead to gathering crucial and sensitive information such as bank account details, credit card numbers, and social security numbers, and often for misusing or selling it illegally. The attack is most commonly delivered as an email communication that is spoofed but looks legitimate as a well-known bank, shopping portal, hotel, etc., but it can also appear to come from a person in charge of an authoritative position or of some known or personal acquaintance. This occurs when a cybercriminal, pretending and being assumed as a trusted entity, dupes a victim into opening an email. The recipient is then lured to click on a malicious link or document, which can lead to the installation of a malware (a malicious program), and thus all sensitive information on that system is compromised.
Phishing is often used to gain access to corporate or governmental networks by luring and targeting innocent employees as a part of a larger attack, such as an advanced persistent threat (APT) event. In this latter part, many employees are compromised in order to bypass security perimeters like Firewalls, Endpoint Security, and email Security, spreading malware inside a closed environment, or gaining privileged access to all of the secured data and information.
An organization falling prey to such an attack typically faces severe financial losses and reputational losses. Depending on the scope, a phishing attempt might escalate into a security incident that would become a daunting task to recover and gain back its market share.
Types of Phishing:
Spear phishing , as the title signifies, usually targets a specific person or organization. Since these types of attacks are so accurate, phishers scout the internet for all available information about their target so that they craft a believable and legitimate-looking email to extract information (if not money) from their targeted victims. An example is described in the sidebar.
Bangladesh Bank Heist 2016
In February 2016, the fraudsters hacked their way into the Bangladesh Central Bank. The attack into the Bangladesh bank took place by sending spear-phishing emails sent to the innocent employees of the bank as victims, thus gaining access to the bank’s network.
The hackers who broke into and hacked the bank's systems and caused the illegal payment instructions to be delivered to the New York Fed used a malicious computer malware to access the necessary and relevant servers; retrieve files and extract data; create files; change file names; steal credentials and login information, including to the SWIFT system; erase key files and histories; and digitally cover their tracks. The hackers used Fedwire of The New York Fed’s system, which is designed to instantaneously transfer huge-dollar amounts, and it allegedly played a key role in the attackers' scheme.
Usage of the Fedwire system in New York was a key component in this attack, as it allowed the cybercriminals to instantly transfer the funds to the intermediary banks. From there, the intermediary banks, through Rizal Commercial Banking Corporation (RCBC) correspondent accounts, swiftly transferred the stolen funds out of New York City and the United States to fictitious U.S. dollar accounts in the Philippines, which RCBC created nearly a year earlier to receive the stolen funds from New York.
The instructions to steal money from the Bangladesh bank were issued via the SWIFT (Society for Worldwide Interbank Financial Telecommunication) network.
SWIFT is a Belgium-based cooperative that maintains a messaging platform that banks use to circulate money internationally. Using this SWIFT transaction system, the hackers stole $101 million from the Bangladesh bank’s account by sending fake orders.
The malware used against the Bangladesh bank shows the same characteristics as software used in the 2014 Sony breach. The hackers used a custom-made malware for hiding evidence and going undetected by erasing records of illegal transfers.
Whaling is a form of spear phishing targeted toward executives or other high-profile targets within a business group; government; or other private entities, such as a COO, CEO, or somebody else who has access to the financial data or assets. CFO fraud is a common example of whaling. It generally attacks toward the high profiles in order to steal critical and sensitive information from a company. Generally, these are the persons who hold complete access to sensitive data.
Smishing , a means for SMS phishing, is done via SMS text messaging on mobile devices. A similar technique, Vishing, meaning voice phishing is conducted via the phone.
Deceptive Phishing : Here the sender masks (makes it look legitimate) email ids as an official and original company’s email address, luring and encouraging users to click on the fake links provided in the email. Cybercriminals usually target their victims via bulk email processes.
Pharming , also known as DNS-based phishing, involves the modification or tampering of a system’s host files or domain name system to redirect requests for URLs to a fake site. So, users have no clue that the website they are entering their personal details into is actually fake.
Content-injection phishing is where scamsters/phishers insert malicious code or misleading content into legitimate websites that asks users to enter their credentials or personal information. This phishing attack goes on as part of content spoofing.
Search engine phishing begins when scamsters or phishers create malicious websites with irresistible jaw-dropping offers, and search engines index them. As the saying goes, “Too Good to Be True,” innocent victims then get lured toward such sites doing their own online searches and think these sites are legitimate, unknowingly sharing all their personal information.
The bitter truth is there are, indeed, a lot of phish in the sea!
The majority of data breach attempts begin with a phishing attack. Unfortunately, no matter how secure and how many various precautions that companies implement, some phishing emails will always crawl and find their way into the inbox of a victim. And those messages are extremely effective – the majority of people around the globe cannot identify a sophisticated phishing email. That’s where user awareness and employee education plays a major role and is of the utmost importance.
Case Study: Bypassing Two-Factor Authentication
Hackers successfully bypassed Google’s two-factor authentication (2FA) and broke into Gmail accounts. In this sophisticated campaign, hackers gained access to hundreds of Google and Yahoo accounts in order to bypass two-factor authentication.
- 1.
Hacker sets up a fake Gmail login website.
- 2.
Hacker sends phishing Gmail security alert to the victim (Your Gmail account has been blocked for security reasons. You will need to login to reactivate the account blah, …).
- 3.
The victim clicks the phishing link and is redirected to a fake Gmail authentication page.
- 4.
The victim logs on using a username/password.
- 5.
Hacker accepts the login and then is presented with a ‘Please enter 2-Factor Authentication code:’ screen to the victim.
- 6.
Hackers at remote location open legit Gmail page and logs in using the captured username/password from the victim.
- 7.
Legitimate Gmail accepts the login and sends two-factor authentication SMS message to the victim’s phone.
- 8.
Victim’s submits the 2FA code from the SMS into the phishing site.
- 9.
The hacker captures the 2FA code and submits the code to legit Gmail.
- 10.
Hacker has gained access to victim’s Gmail account.
Source: motherboard.vice.com/en_us/article/bje3kw/how-hackers-bypass-gmail-two-factor.
Phishing Emails
- 1.
Cybercriminals send an email stating that, for example, there has been an error in calculating your tax and a refund has to be issued. Once you click on the link, it will redirect you to a banking login page, and once you log in to it by entering your account details, your bank account could be hacked.
- 2.
In this case, if you check for the sender’s address, it would appear as [email protected] & not [email protected], which is the legitimate email address of the income tax department. Note the in this case, the letter *e* is missing from the word *efiling* and *filing* is misspelled as *filling*.
A new trend is to create a malicious phishing email and deliver the payload to network users without setting off dynamic malware detection systems because you can use the Mozilla’s FFSend service. send.firefox.com is a trusted domain on most organizational controls, and you don’t need to set up a fake website.
FFSend is a file transfer tool designed by Mozilla and it will generate a safe, private, and encrypted link that will automatically expire to ensure your file does not remain online forever. This makes FFSend a useful way to send private files between two users in a secure manner. It also helps scamsters to send malicious phishing emails and help them go undetected.
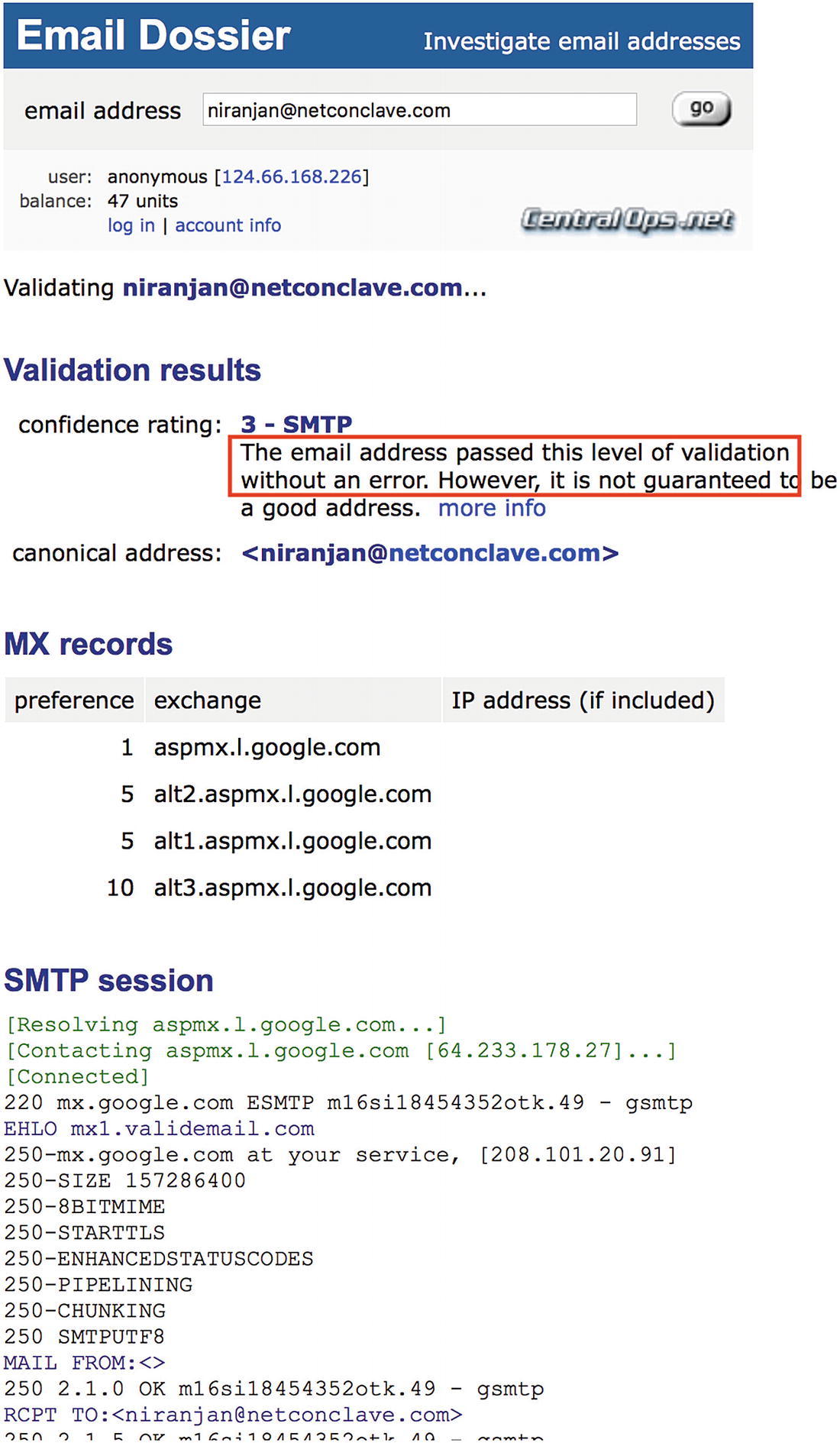
An example of a spoofed email address
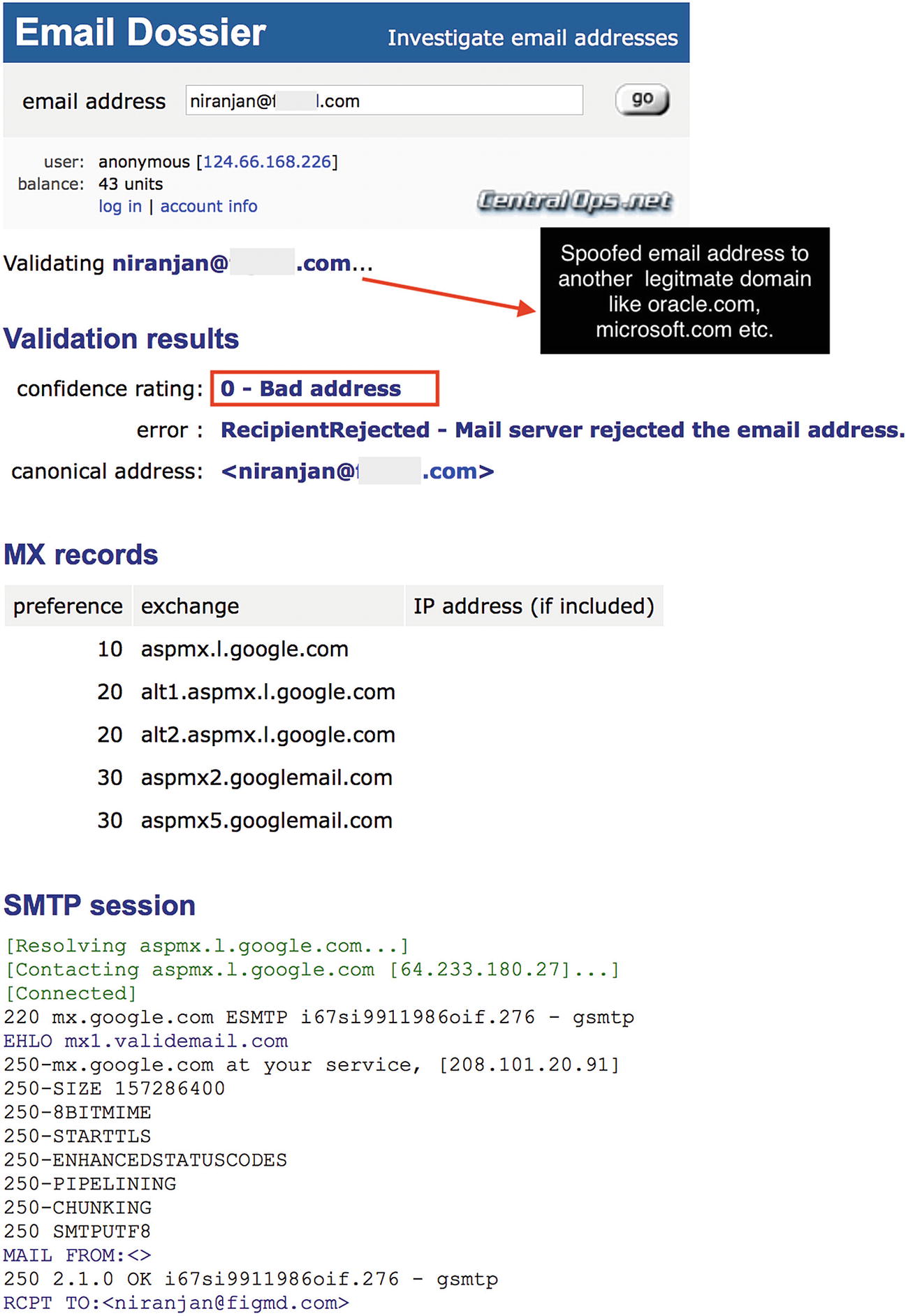
Email Dossier showing a fake email address
If an email contains any suspicious URL, check if that URL is malicious or not, redirecting to any other websites, or installing/downloading any malware.
We scanned a suspicious URL using VirusTotal. The results are shown in Figure 11-5.

VirusTotal result
Case Study: Apple Receipts
The award for the best phishing scam of the year 2018 goes to this scam: Apple App Store Purchase Receipts. This widespread scam is extremely well designed and flawlessly executed, leaving you completely fooled. I personally tried it and was blown away.
It starts with an email and claims to be a purchase confirmation from Apple, with a PDF attached, posing as a receipt. There’s no malware in the PDF itself, but the 100% beautifully designed (Mojave themed, which is Apple’s new OS) PDF contains a link with a shortened URL. Clicking on it sends you to a fake Apple Account login page, prompting you to enter your username and password.
After logging in to the fake site, a prompt tells you that your account has been locked for security reasons and offers an Unlock Account button. Click it and you will be prompted to input your name, address, social security number, payment info, answers to common security questions, and even your driver’s license and passport number.

The legitimate Apple page
Case Study: Social Fish
Social Fish is an open source phishing tool, which allows an attacker to create dummy pages that mask themselves as legitimate websites. This tool is used for educational purposes, to show how to create fake websites easily, which looks legitimate to users.
- 1.
Download Social Fish from: https://github.com/UndeadSec/SocialFish and install it on your Linux-based system.
- 2.
Once installed, type the following to start the tool.
python3 SocialFish.py - 3.
Once Social Fish starts, it will ask, ‘Do you agree to use this tool for educational purposes only?’ type ‘y’ to continue. If you type ‘N’ the tool will close automatically as shown in Figure 11-7.
You can choose if you want to receive the credentials by email or on the terminal itself.
- 4.After that, there are two options: Social Media and Others, as shown in Figure 11-7.
 Figure 11-7.
Figure 11-7.Options for phishing
- 5.Type ‘o’ to choose others. You can now create phishing web pages of the following websites shown in Figure 11-8.
 Figure 11-8.
Figure 11-8.Other phishing options
- 6.Type ‘s’ to choose social media. By doing this, you can create phishing web pages of the following websites shown in Figure 11-9.
 Figure 11-9.
Figure 11-9.Social Media phishing options
- 7.
Here, we choose ‘s’ (social media), and we will create a phishing page for GitHub.
- 8.Here our Ngrok URL for the phishing page is: https://8bda2276.ngrok.io , as shown in Figure 11-10.
 Figure 11-10.
Figure 11-10.Phishing URL
- 9.Now our phishing page is ready. The fraudster sends it to the target and waits for the credentials to be entered. Our GitHub phishing page is as shown in Figure 11-11.
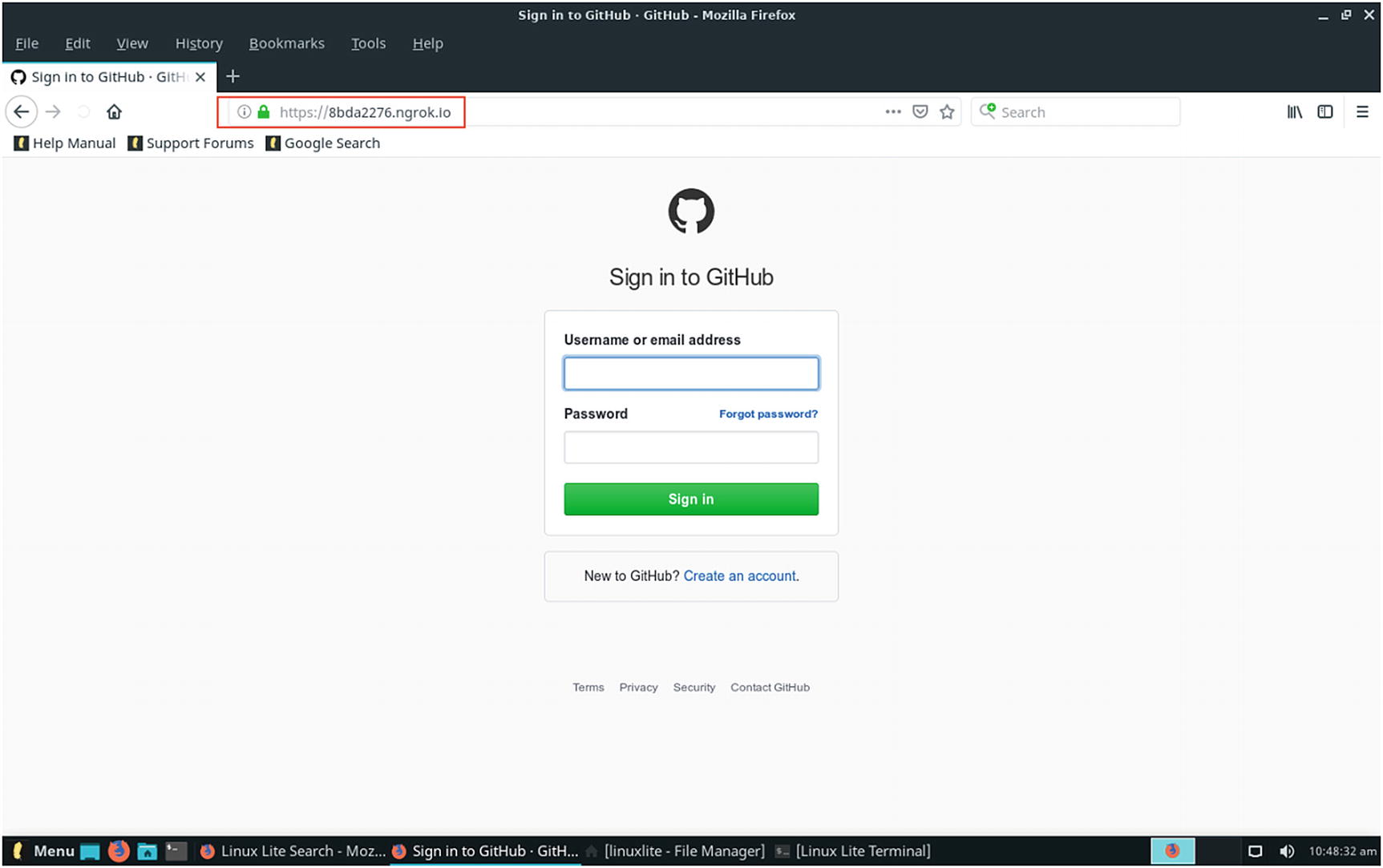 Figure 11-11.
Figure 11-11.Github phishing page
- 10.
As the victim enters the credentials, the fraudster receives it. Captured credentials are shown in Figure 11-12.

Captured user credentials
Spam
Spam is unsolicited and unwanted email that we receive in our Inbox. Spammers flood inboxes of thousands of recipients with ‘Junk Mail’. Generally, spam emails started out as advertisement carriers but have become a threat and are a nuisance. Not all unsolicited email is spam, however. Spam doesn’t usually contain malicious or virus-infected files but often leads to malicious pages. Spam is of two types, based on its content – Unsolicited Bulk email (UBE) and Unsolicited Commercial email (UCE). Spam is sent via spoofed id or by commercial mass-mailing software.
Note
A spammer is a person or entity that sends spam emails.
Greylisting – allows temporary denial to receive a mail from an unknown IP. Email from greylisted IPs get rejected via a ‘try again later’ error message. As this spam message is not sent via an RFC-compliant MTA (Mail Transfer Agent), the software doesn’t resend the message again.
Content Filtering – Commercial content filtration tools are available that filter out spam mails based on the metadata of the message. Content filters scan all parts of the email for any malicious detail.
Blacklisting – DNS-based Blackhole Lists or DNSBL remains one the oldest methods to combat spam. It effectively blocks all mail traffic coming from the IP servers on a specified list. Also, it blacklists sites on the internet that are known to be as spam originators.
Antivirus software – Usage of an antivirus software is used to reject any email that contains known viruses.
Email Harvesting
The disreputable and majorly illegal practice uses an automated program to scan web pages and collect these email addresses for use by spammers to send spam mails.
Email Bombing
In this attack, the attacker floods the victim’s mailbox with a surge of emails in a short duration. The aim of the attacker is to crash the mailbox with heavy traffic. Even if the victim gets lucky and the mailbox doesn’t crash, they are left with a large number of emails in the mailbox, due to which any legitimate incoming mail to that mailbox will bounce back since it is filled with the clutter of spam mails and thus exceeds its mail quota of space.
Email Forensics
Email forensics is the branch of cyber forensics that involves the use of tools and techniques to analyze and examine the contents and components of emails. As hackers evolved, so did their methods. Cybercriminals use different tactics to keep their identities hidden to save themselves from being traced back. The use of proxy servers and other IP spoofing techniques make tracing the source of email a nightmare for investigators.
As we are already aware, just doing data extraction and reporting is not forensics. Digital forensics is all about forensic science focusing on the recovery and investigation of raw data residing in any digital or electronic media. The aim here is to extract and recover any information from a digital device without altering the data present on the device.
With the introduction of various technologies such as Ajax (Asynchronous JavaScript and XML), recovery of webmail artifacts has become much more challenging and difficult for a forensic examiner. Many webmail artifacts such as the content of a message are no longer stored in areas of the disk where examiners may be used to finding them. Instead, forensic examiners should rely on items such as the paging file and hibernation file for recovery of webmail artifacts. A system’s RAM is also a potential source of webmail-related information. However, this may not be an available option because many forensic examiners do not become involved until after the machine in question has been powered down.
Recovering Emails
An email consists of many components that collaboratively help in its forensics, namely the email header, body and its fields, attachments, and its related properties – which help in its analysis. The various levels in email forensics is comprised of collecting data in a readable format, which means Data Recovery at the initial stage; when the data to be investigated is converted into a readable format, it simplifies and eases out the remaining part of its forensics.
Data Recovery is a wide area that has today become a requirement for investigators as it provides help in restoring and filtering emails without any damage to its integrity. The various tools available for email forensics incorporate algorithms for recovery in order to see that all stages of e-discovery are carried out successfully.
Some Techniques
Messages sent out after standard business hours.
Messages sent from corporate accounts to personal addresses, the media, or competitor or rival companies.
Messages that contain encrypted .zip or rar files as attachments.
Utilizing IP address geopositioning, mobile phone call records, and GPS data embedded in photos to plot locations on a map.
Rebuild email conversations, text messages, and various online chats from various sources so that it can help an investigator to read them in the order sent between individuals.
By identifying duplicate and very similar documents, investigators can act on them more systematically and intelligently, either setting them aside or utilizing them for deeper analysis.
Merge near-duplicate documents and word-context analysis (i.e. analyzing the impact of a word or a phrase) for quick identification of evidence, and discard large quantities of irrelevant data.

Steps of email forensic investigation
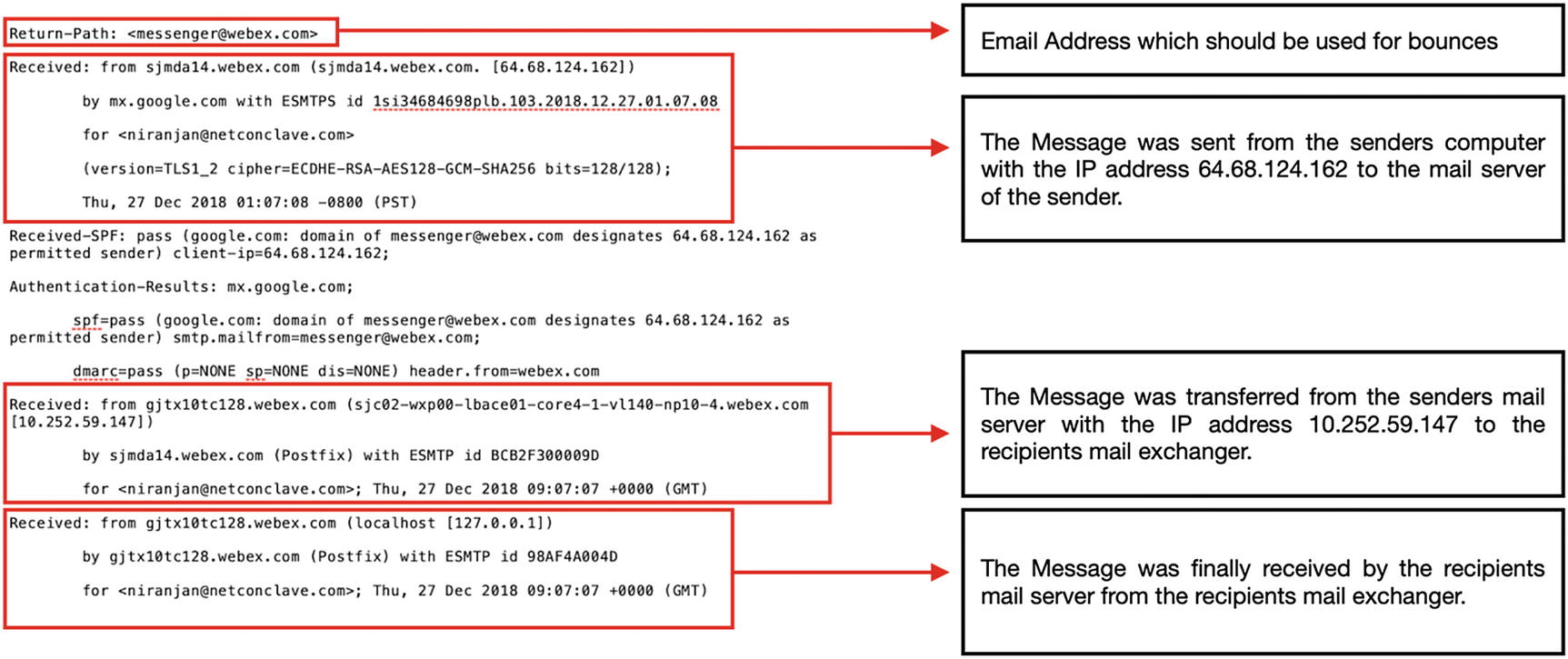
Email Header Analysis
Email headers are a source of information, which contain the metadata enclosed to each email and assists the forensic investigator in analyzing and examining the email artifacts.
Sender email
SMTP servers the mail passed
Network path of the mail
IP address of the sender
Timestamp
Client info
Encoding info
The header is of utmost importance when the sender needs to be traced. To determine the source of the email, the investigators need to examine the header from the bottom where the ‘Received’ section is listed and work their way up. All the details must be studied well and written down; HTTP and SMTP servers are archived frequently. If details such as time, multiple server info, etc., are found out of place, chances are that the header is altered and the email is a fake one. If the attacker has used proxies or has spoofed the IP, it might lead to some complex header analysis.
Retrieve Email Headers
- 1.
Log on to the victim mail id.
- 2.
Open the suspected email.
- 3.
Obtain the header of different email service providers as shown in Table 11-1.
Retrieving email headers from different mail providers
Gmail | Open the e-mail message for which you want to view the header. At the top there is a link titled “Show original.” |
|
Yahoo Mail | Open the e-mail message for which you want to view the header. At the top click on … and then select ‘View raw message’. |
|
Outlook Express | Open the e-mail message for which you want to view the header. At the top right click on … and then select ‘View message source’. |
|
iCloud | Double-click on the email message, for which you want to view the header, to open it. Click on ‘View’ in the menu tab on your Apple Mac OS. Select Message ➤ All Header. |
|
Analysis of an Email Header
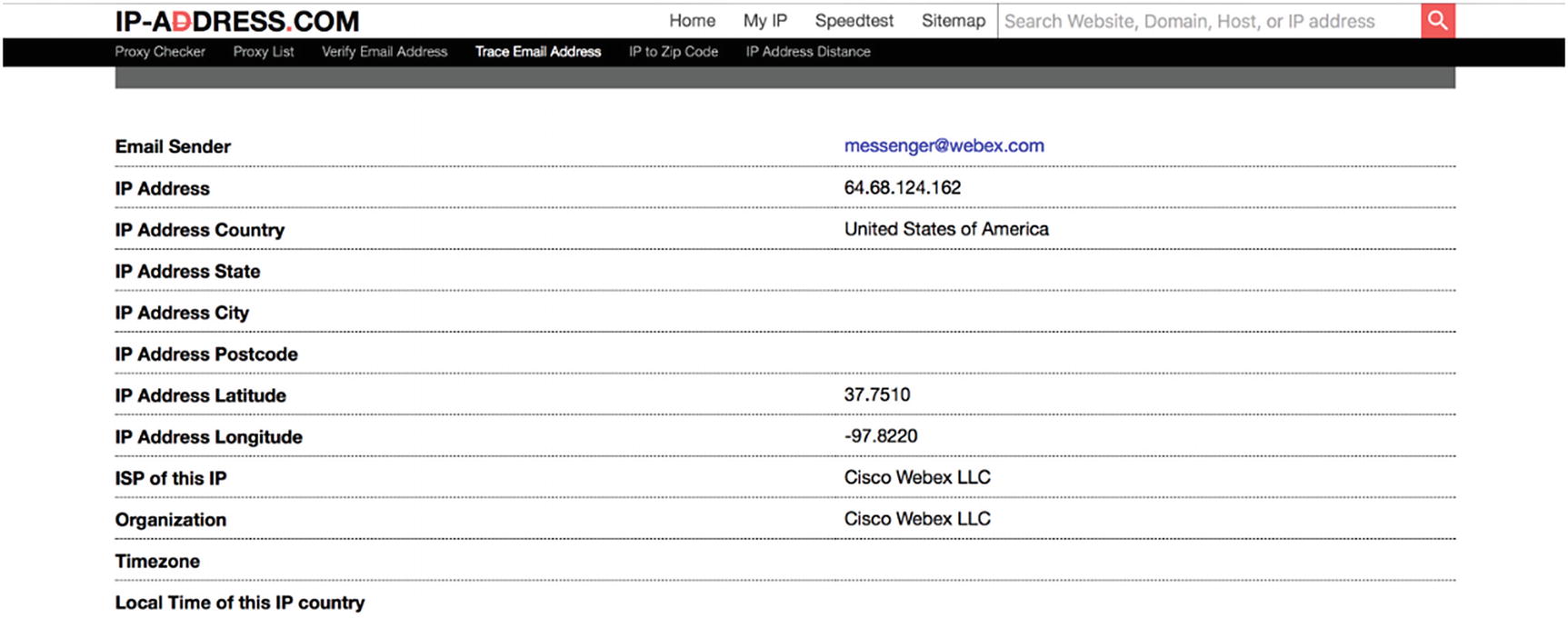
Email header analysis gives us information about the attacker, like SMTP server detail, IP address of attacker and victim, timestamp when email was sent, and attachment file information. We have many commercial as well as online tools for analysis like www.ip-adress.com, emailtracker pro, MailXmainer, MX Toolbox, etc. We will use the ip-adress tool to analyze an email header and understand the different fields designated in the header.
Once the IP is confirmed to be genuine, all the details are collected, and the associated Internet Service Provider (ISP) is contacted by authorities and the customer details for the IP are requested. ISP then forwards the customer details to the investigators who, with the help of local law enforcement agencies, track the culprit.
Case Study: Email Hoax
A reputable hotel had to contend with quite a scare when a 40-year-old depressed man sent a hoax email to the hotel, keeping the staff on their toes for almost a week.
On June 1, an email with ‘Bombs in Hotel’ in the subject line came to the inbox of the hotel’s email ID, from the attacker using yahoo.com email. The contents of the email (unedited) are shown below:
Hi,
3 suitcases filled with 20 Kg of RDX has been placed in your hotel. Over the last 3 days, we have successfully bypassed all your security systems. The detonator for all 3 explosives will be controlled by a mobile phone. When I call the numbers, the explosives will go off and destroy your hotel.
You have 24 hours to deliver Rs 5 Crores else witness the destruction of your hotel.
You will send 2 Bank DD’s each of Rs 2.5 Crores to the following address:
(his wife’s Bangalore, India address mentioned here)
Do not waste time, the explosives will be set off at exactly 2 pm on Wednesday, June 2, 2010. This email is not a hoax. You are advised to take it very seriously to avoid millions of dollars of damage and loss of life.
The terror alert is real, this is my last warning!
However, the hoax mail sender was nabbed in Bangalore after the assistant security manager of the hotel approached the Cyber Crime cell officials.
Hotel authorities provided us with the emails and other details. As the accounts were that of Yahoo, we contacted Yahoo and gathered details of the account that was created in the name of like [email protected]. Yahoo provided us with the details of the IP address.
We did header analysis using ip-adress.com and the IP address belonged to a cyber cafe in Bangalore. It was an Airtel service internet connection, and with further assistance from Airtel, we tracked down the physical location of the cyber cafe from where the mails were sent. We then sent a team of experts for further investigations.
The culprit had sent two hoax emails to the hotel. Investigations revealed his wife had left him, leaving him homeless. This prompted him to send an email by creating an email id in her name. He also demanded that 7,000,000 USD (the Rs. 5 crores from the email) be delivered to her local residential address.
After reaching Bangalore, we first visited the cyber cafe. We then went through the register where customer details were recorded. Our observation was that the account user usually used his mail between 10 and 11 a.m. We then did a forensic analysis of the computer from which the mails were sent. With the help of the cyber cafe owner, we laid a trap. The next morning, when the attacker visited the cafe and opened the Yahoo ID, we caught him red-handed and he confessed to his crime.
Bait Method
If the evidence email is confirmed as spam mail, the experts set bait to catch the culprit. The experts create a message and use a <img src> tag, and the source of the picture is placed on a trusted HTTP server, then this email is sent to the spammer. When the attacker opens the mail, a log entry is created in the server’s log with the attacker’s IP. This technique fails if the mail client disables auto download and the hacker does not open the mail.
Java Applet Method – Investigators send mail with “embedded” Java applet that obtains IP address on the destination and mails it back to them.
Active X Control method – The investigators create an HTML page with Active X controls that extracts the IP of receiver’s system and mails to the attacker. The investigators obtain IP and other details of the attacker when the mail reaches the destination.
Case Study: e-Discovery from Enron Corpus
Enron was an energy, commodities, and services-based company headquartered in Houston, Texas. At their peak, they had a staff of over 20,000 employees and had revenues of over 100 billion USD. But Enron is remembered in history for the 2001 Enron scandal.
In 2001, after many articles questioned Enron’s overpriced stock prices, many meetings and audits were held within the company, and over the year many irregularities were found in the financial statements. With tension and chaos growing rapidly among Enron employees and its investors, Enron’s share price started falling at an alarming pace. In November 2001, Enron filed for bankruptcy when its shares plummeted to $0.60 per share price. Jeffrey Skilling, who was the former Chief Executive Officer (CEO) and Chief Operating Officer (COO); and Kenneth Lay, who was the former chairman and CEO, were eventually sentenced to prison for 25 years and 45 years terms, respectively. And the curtains came to close on Enron. Enron will always be remembered as the biggest audit failure in American history.
Enron Corpus is the 600,000 emails database of the Enron employees acquired by the Federal Energy Regulatory Commission during the course of their investigation. The emails were processed and hosted on iConnect for the investigation teams. After the investigation concluded, the email archives were made publicly available. Since then, this mail corpus has been used by many institutes and companies for research purposes. Many of the research work performed on this database has been applied to areas such as social networking, statistics, and even e-discovery.
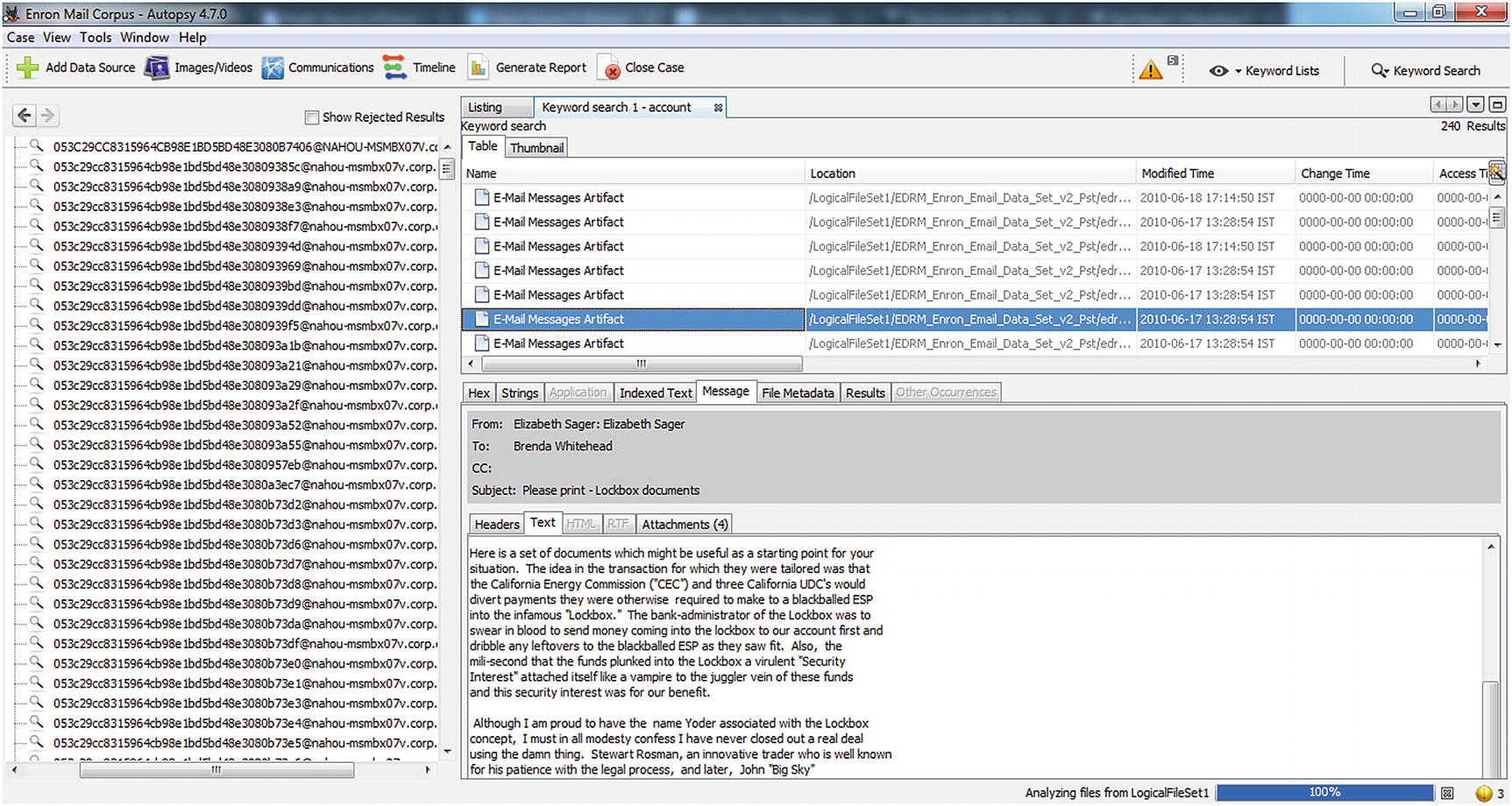
We have obtained a part of the Enron mail corpus and analyzed it in Autopsy, which is an open source tool used to investigate a computer breach. We have performed keyword searches and examined some Exif files as well, as shown in Figure 11-8.
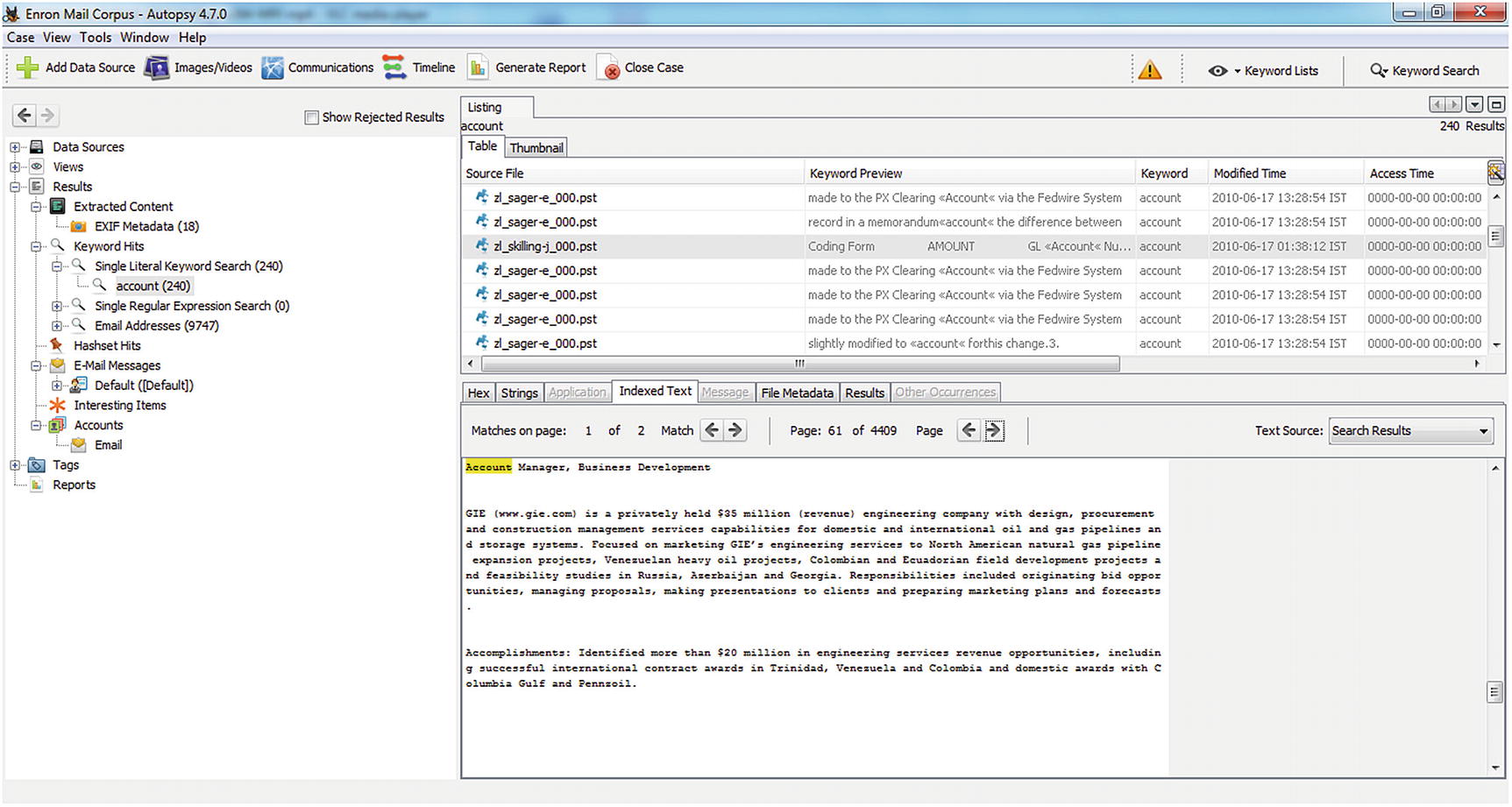
Enron case autopsy results 2
We can see there are over 4,000 pages of emails, which consist of the word “account.”
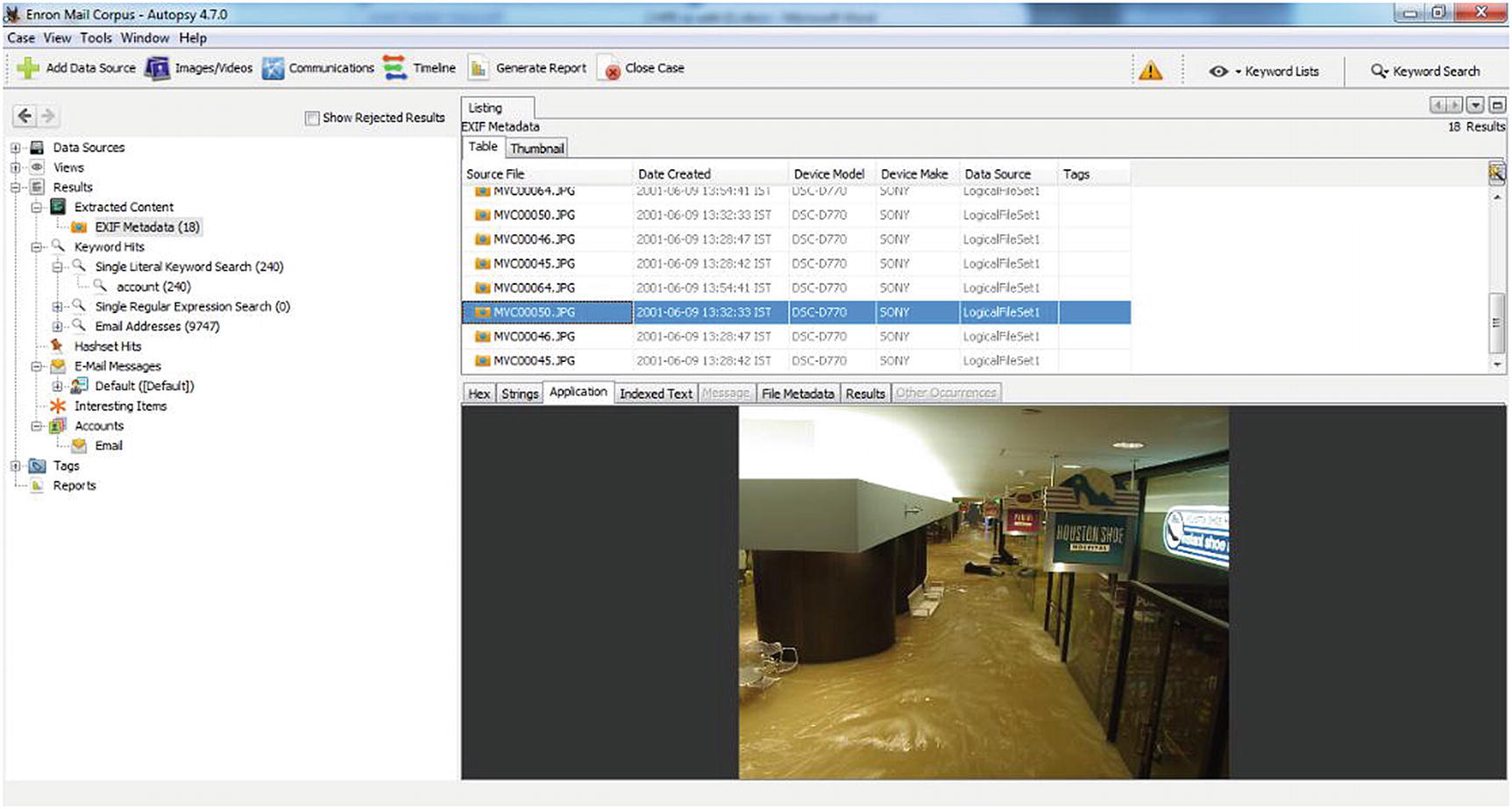
Enron case autopsy results 3
From a forensic perspective, the Enron email corpus is a data goldmine. From simple communication like lunch plans – to elaborate secret meetings – this was discussed in these emails. Forensic study of the corpus reveals many details about the company, its employees, and the environmental surroundings.
Email databases such as the Enron mail corpus is a rich source of Electronically Stored Information (ESI). This case revolutionized e-discovery practices all over. Due to this major incident and scandal, the e-discovery (a legal proceeding) industry boomed, seemingly overnight, in order to provide support to law firms and their clients in the burgeoning field of e-discovery. New companies came up and existing companies also added this as a part of their services. They drew on an array of sources services like photocopying, investigations, and analytic services; litigation support and case management services; and others. All these services were present before e-discovery became a big business. The volume (and profitability) of e-discovery services brought out many new firms, and it literally gave rise to an industry that today does billions of dollars of business annually.
New protocols were set in place for future investigators to conduct investigations with proper authority and create a strong case. The Enron mail corpus remains the biggest resource of e-discovery to be made public due to its nature.
Case Study: Microsoft Internal Spam
Microsoft employees found themselves trapped in a massive reply-all email thread due to a mistake made by an employee by making a change to Microsoft’s GitHub account. This caused the system to send automatic messages to a huge base of around 11,543 Microsoft employees registered with this account.
This did not take much time before it turned to complete chaos. Some people replied to everyone in the e-mail thread asking to be removed; others cracked jokes to their captive audience; some begged their colleagues to stop replying or tried to offer useful advice to those stuck in the thread; even employees who managed to unsubscribe kept getting resubscribed.
Summary
Phishing scams are primarily an email that leads to gather crucial and sensitive information such as credit card numbers, social security numbers, and bank account numbers, often used for misusing or selling the information illegally.
Spam is unsolicited and unwanted email that we receive in our inbox. Spammers flood inboxes of thousands of recipients with ‘Junk Mail’.
Some Anti-Spam measures are Greylisting, Content Filtering, and Blacklisting DNS.
Email bombing is a method in which the attacker floods the victim’s mailbox with a surge of emails in a short duration. The aim of the attacker is to crash the mailbox with heavy traffic.
Email forensics is the branch of cyber forensics that involves the use of tools and techniques to analyze and examine the contents and components of emails.
Email headers are a critical source of information, which contain the metadata enclosed to each email and assists the forensics investigator in analyzing and examining the email artifacts.
Email header analysis gives us information about the attacker, such as SMTP server detail, IP address of attacker and victim, timestamp when email was sent, and attachment file information.
If the evidence email is confirmed as spam mail, the experts set bait to catch the culprit. This method is known as the bait method.
References
https://pdfs.semanticscholar.org/8625/a3b17d199e5cabbb796bad0df56a7979c77c.pdf
http://jpsra.am.gdynia.pl/upload/SSARS2016PDF/Vol1/SSARS2016-Charalambous.pdf
https://cyberforensicator.com/wp-content/uploads/2017/01/SSARS2016-Charalambous.pdf