In this chapter we’ll introduce mobile forensics by using different programs and tools to acquire from iOS (iPhone8) and Android (Samsung Galaxy S7) devices. We’ll then use the forensic tools to make several backup copies of the iPhone 8, and analyze results from those files. The goal is to see if it is possible to recover and extract the deleted files. The forensic tools will be put to use in later chapters as well.
The Importance of Mobile Forensic Analysis
Understanding Mobile Forensics
Digital Investigation Process
Rules of Evidence
Tools Used for Mobile Forensics
The Mobile Phone Evidence Extraction Process
Mobile Forensic Challenges on iOS and Android
The Importance of Mobile Forensic Analysis
While mobile devices have become a necessity for everyone, smartphones are the most used devices in our daily lives. There are many operating systems used by smartphones and one of these systems is the iOS. These phones are widely used in many fields such as making calls, email, communication through social media, and payment and purchase through the Internet (Kuittinen, 2013). Mobile forensics is a branch of science that is concerned with retrieving digital evidence from mobile devices using reliable and appropriate forensic tools (Riadi, Umar, & Firdonsyah, 2017). Because of the increasing demand for smartphone-based services and the increasing number of its users, mobile forensic science has become a necessity because of the proliferation of services, facilities for users, and the spread of the Internet of things technology that requires a device connection; there is also a popular tendency for people to use mobile phone transactions during their daily dealings (Al-Dhaqm, Razak, Ikuesan, Kebande, & Siddique, 2020).
Mobile forensics is the science of obtaining evidence from portable devices under forensically sound conditions utilizing acknowledged strategies, while mobile device forensics is a branch of digital forensics that entails gathering evidence from mobile devices under forensically sound conditions. Preservation, acquisition, examination, analysis, and reporting are the five phases of mobile forensics. Seizing and safeguarding suspect mobile devices without affecting the contents of stored data is preservation. The term “acquisition” refers to the process of recovering data from a computer. The term “cloud computing” refers to “the application of digital forensic science in cloud computing environments.”
Recent years have revealed the generation of behavior and exploitation of modern crimes through the Internet that was not known before, which led to these crimes threatening the security and safety of individuals and institutions; with the increasing use of the Internet in ecommerce operations, the types of these attacks and threats will increase, which prompted us to acknowledge the existence of this type of crime and be alerted to its seriousness and the need to take a strict stance to fight it and find appropriate solutions to it.
During this case study, we will focus mainly on iOS, which is one of the worldwide operating systems; we will use an iPhone 8 (A1905) device as a sample for one of the types of devices that use the Apple file system, and we will do an acquisition for this device. The acquisition passes through several promising stages. Through this research, we will learn about the most important challenges that we face while extracting and restoring files for Apple devices in general and for iPhone 8 devices in particular.
Understanding Mobile Forensics
Mobile forensics is defined as the science of obtaining and handling digital evidence from portable devices by use of techniques similar to digital forensic investigations. Mobile device models, depending on where the storage is located so that it can be stored on the internal or external memory card, and the phone memory may be volatile or nonvolatile.
Digital forensics can be defined as an applied and practical use of reliable and proven methods for digital devices, and this action has been done in several ways, the most important of which are verification, identification, analysis, and interpretation; then, the digital evidence that has been derived from digital data is presented. It is the reconstruction of the events that show the crime or that help in the anticipation of unauthorized procedures. With the ever-increasing popularity of smartphones and people’s reliance on instant messages in their everyday lives, quick updates of instant messages increase the features of the application and entice users to continue using their product. On the other hand, the majority of these characteristics will provide a significant challenge to digital forensic practitioners and specialists. Many studies have been done to acquire data from older versions of the WhatsApp apps. Many security measures arose with the introduction of new versions of WhatsApp, making it difficult for mobile forensic practitioners to gather information and evidence that live in internal storage.
Digital Investigation Process
Obtaining digital forensics data from mobile devices must include the use of the two main technologies, mainly logical acquisition and physical acquisition, and each of these features has its advantages (Anwar & Riadi, 2017); taking a logical copy of the device may not need to root the device, and it can give us the virtual files of the stored data on the memory, while the physical version (bit by bit) needs to root the device and may cause problems on mobile devices.
To pursue and achieve the goal in this practical case, we will conduct a forensic investigation into the iPhone, and we will also assume a scenario to simulate the case and apply all the mobile forensic stages. In terms of seizing, acquisition, extracting, analyzing, we will finally write the report on this phone.
We’ll assume a scenario in which there is a drug dealer, where this person takes pictures of narcotic substances and sends the drug pictures to his friends, along with audio recordings to tell them the prices through social networking sites, and then deletes these pictures and recordings from his phone and social media sites.
The digital forensic officer must take all safety measures for the seized phone to preserve the data and follow the official and legal procedures to check the phone without destroying the data and to present their final report to the court.
- 1.
Collection - Identify, acquire, and protect the data collected at the crime scene.
- 2.
Examination - Process the collected data/evidence and extract relevant information.
- 3.
Analysis - Analyze the extracted information to connect the dots and be able to build a robust and admissible case.
- 4.
Reporting - Present the findings of the analysis stage into an admissible and understandable format.

Digital forensics process steps
Evidence and Scene Security
Evidence preservation failure may make it inadmissible by a court or even less-formal parties; the preservation stage involves locating the evidence and identifying it including any related digital equipment. Additionally, it deals with securing, evaluating, and documenting the evidence and the scene; securing the evidence involves its isolation and packaging. Procedures should be followed also during evidence transportation and archiving.
During the seizure process, not handling the device properly may cause data loss or damage the evidence. Far away from digital forensics, some cases may require biological forensics involvement to extract DNA or fingerprints from the device. This is to relate the evidence to its owner or user. Evidence contamination can destroy the relationship of the evidence to the owner and lose evidence. Accordingly, it is necessary to wear gloves all the time while working on the device.
The scene should be searched carefully not to miss any evidence-related equipment; this includes cables, power adapters, memory cards, and other accessories related to the mobile device. Computers at the scene may provide valuable help if the mobile was synced with them; in a few cases during the seizure process, the evidence may be found at the scene in a seemingly unusable condition, such as having sunk in liquid or having broken parts. If the liquid is water or another harmless liquid, the battery can be removed, and the device should be put in a container with the same liquid until moved to the laboratory. If the liquid is blood or a dangerous explosive liquid, an expert should be consulted before taking action. Damaged devices can provide evidence in some cases. External damage does not necessarily prevent data extraction. Accordingly, broken devices should be seized too.
Scene Documentation
The entire crime scene should be photographed as well as each digital device with its accessories; a record of all digital devices found should be made including identification and state description for each one. Related nondigital documents, notes, and manuals should be collected; they may contain information about unlocking the device, its storage size, related capabilities, and any other information that may help during the examination. Running devices on the scene should be photographed while they are running; this is to record contents appearing on them including time. Also, any changes or actions made on the device should be recorded, including connecting the device to power adaptors or other devices; these records and photographs provide information if the court asks about the evidence environment.
Evidence Isolation
Mobile device isolation is very important to avoid data loss or change; factory reset commands can be sent remotely to the device and wipe all data; evidence can also be changed if the mobile receives an SMS or a call; and isolation is also required to prevent sending data from the device such as its geolocation. Isolation can be performed in different ways: the first method is disabling the communication through putting the device in Airplane mode. Enabling Airplane mode involves using the device, and thus is not preferred; but if it is used, it should be recorded and pictured. Another concern with using Airplane mode is that it does not prevent all services on the device such as geolocation. The second isolation method is by turning the device off. The availability of the unlock code should be considered in this case. The unlock code will be required when turning the device on for examination. Some services can still run even when the device is off such as alarms in some models. The third method that can be used involves isolation containers such as Faraday containers. In this case, the device will be kept on. This will increase the network signal and drain the battery quickly. Faraday containers should be sealed very well. There is a risk of communication success if it is not completely locked. Power-saving mode can be activated before putting the device in the Faraday container.
Prepare for Acquisition
The acquisition is imaging the mobile device or else getting evidential information from it or its related media; examination starts with identifying the seized mobile device. Learning the device model and hardware characteristics helps determine the method of acquisition and forensic toolkit choices. This will be discussed in the next subsections for Android and iOS devices.
Mobile forensics is a wide field that aims to extract digital evidence from mobile devices running different operating systems. All the previous stages are within the digital investigation process, as the nature of the seized material determines what the digital investigator focuses on, establishes hypotheses about what happened, and verifies any information that proves or clarifies the case. As digital investigators, we always assume that any digital device may contain the required digital evidence, so it is important to adhere to these stages to protect and save all seizures.

Mobile forensic investigation processes for different mobile devices
In the next section, we extracted data from the Apple iPhone using various tools, where we jailbreak an iPhone 8 and display the images including the results obtained through the use of different tools.
The Identification Phase
Agency: Digital Forensics Lab, Cyber Crime Department, Palestinian Civil Police – PCP.
Case identifier: Investigative Case Number: 75/2021 – Ramallah Prosecution (fake case Number) Police Case Number: 127.
Based on: Article (22,39) of Law No. (10) of 2018 regarding cybercrime, a Permission warrant was issued for the aforementioned case.
Investigator: Eng. Ammar Dawabsheh – Digital Forensics Expert. Specializing in cybercrime and digital evidence in a joint program between Khadouri University and the Arab American University, and he works at the Cyber Crime Department in the Digital Evidence Laboratory of the Palestinian Civil Police (PCP) from 2015 until now (2021).
Submitter identity: The seized phone was sent by the Public Prosecution - Ramallah, where the phone belongs to the suspect, M***** H***** (assumed name).
The Collection Phase
The collection phase includes a description of the device details that we use in our practical case; Table 1-1 shows that we use a set of tools such as iTunes, iBackup, and iExplorer as described in the next section, but the main tool we use is XRY FINALMobile.
XRY is a powerful, intuitive, and efficient software application that runs on the Windows operating system. It lets you securely extract more high-quality data in less time than ever before, while at all times fully maintaining the integrity of the evidence.
Specification for Seized iOS Phone
Brand | iPhone | Model No. | Apple iPhone 8 TD-LTE (A1905) |
IMEI1 | 123123123123 | Color | White |
Jailbroken | Yes. | SIM | Jawwal |
Storage | 64 GB | Phone lock | Yes (password:000000) |
iOS Version | 13.5.1 | Battery Percentage | 82% |
Other Notes: - available storage 42.5 GB. - there is a break in the protection screen. - the device was powered on. - the suspect provided us the password with the search warrant, which is 000000. | |||
Mobile photos: attached with the report | |||
Tools Used for Mobile Forensics in Examination Phase
iPhone Acquisition Using XRY

XRY main menu
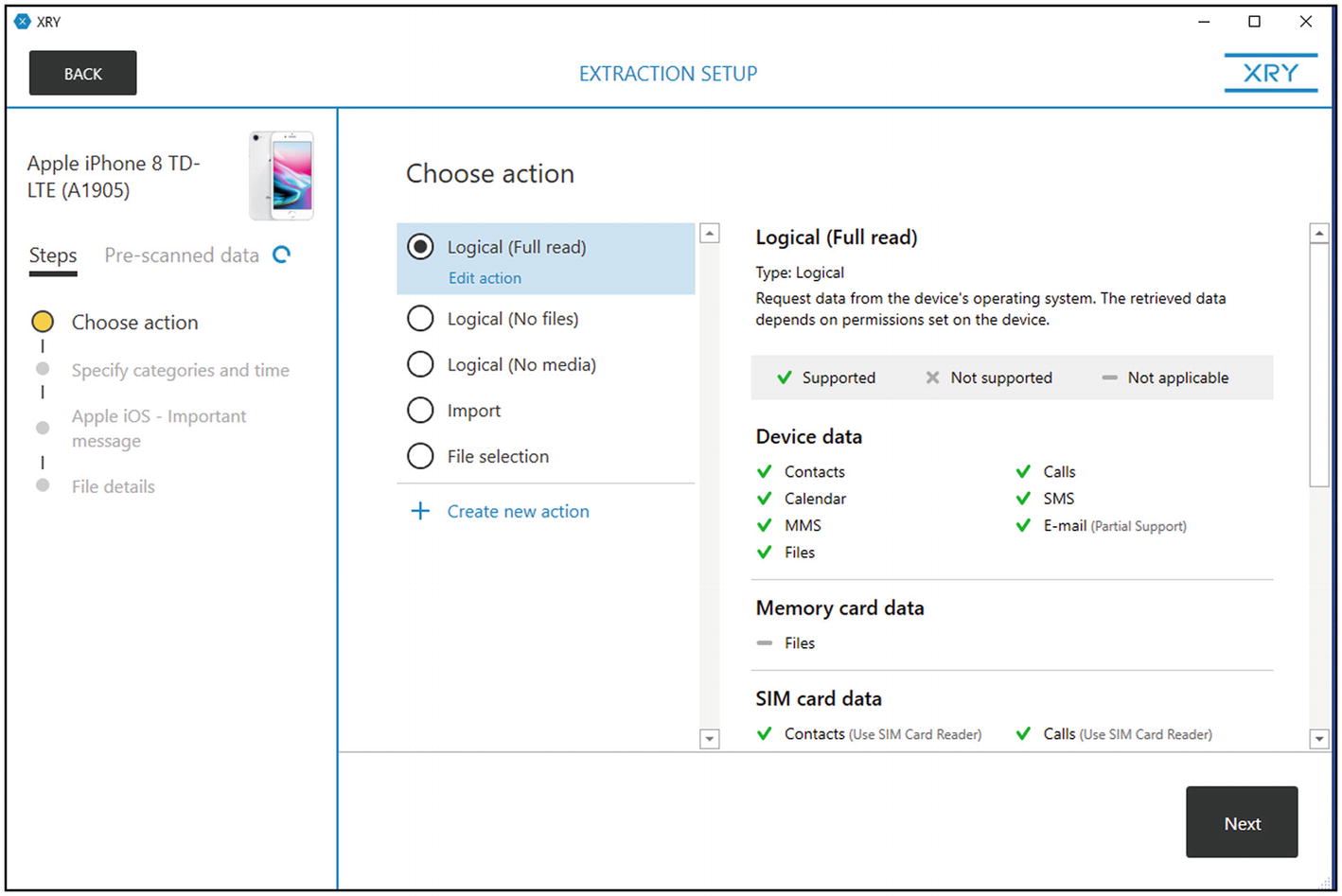
Logical (full read acquisition)
Extraction setup menu
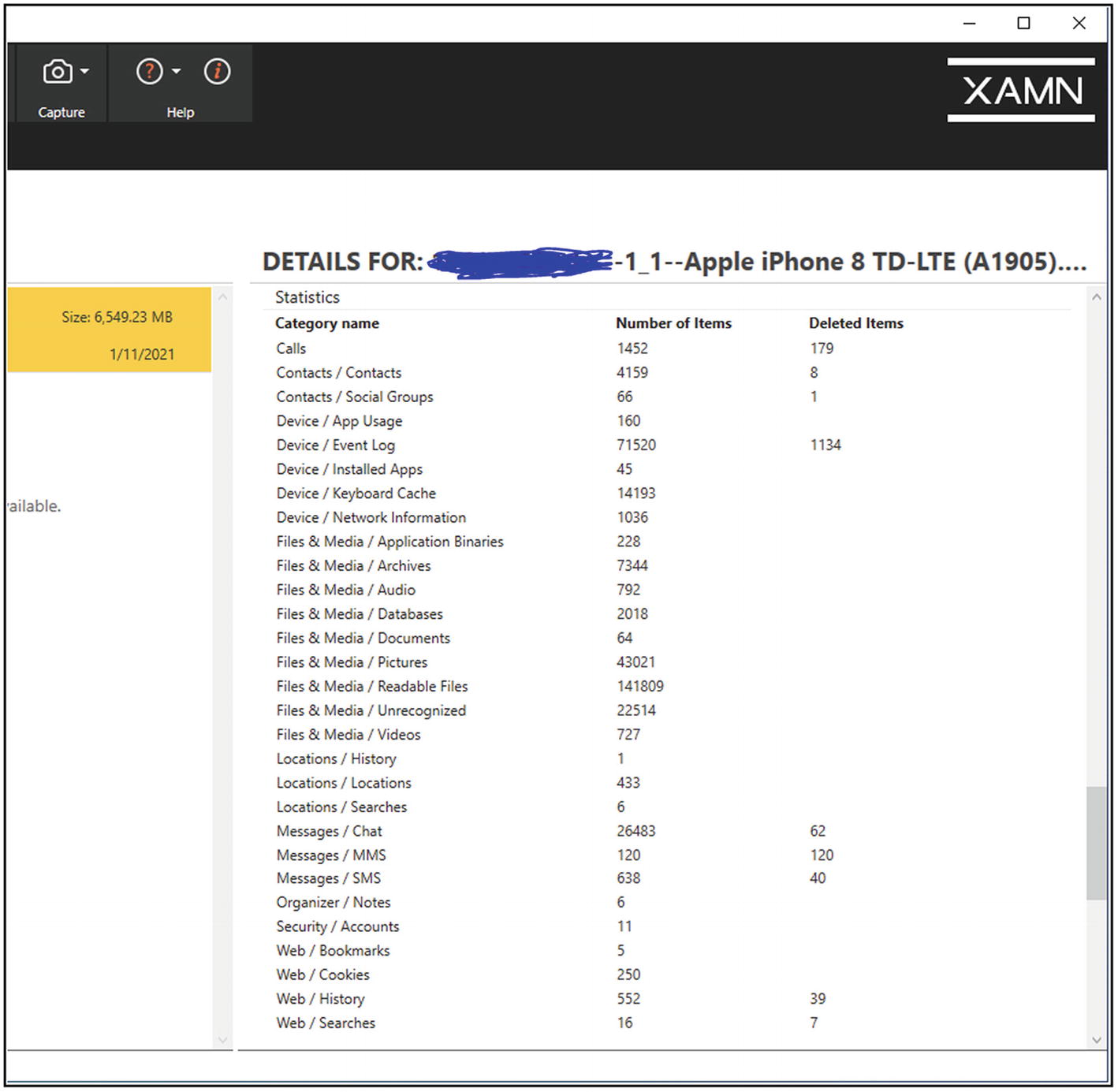
XAMN summary

XAMN main menu
Using Belkasoft

Belkasoft full logical backup
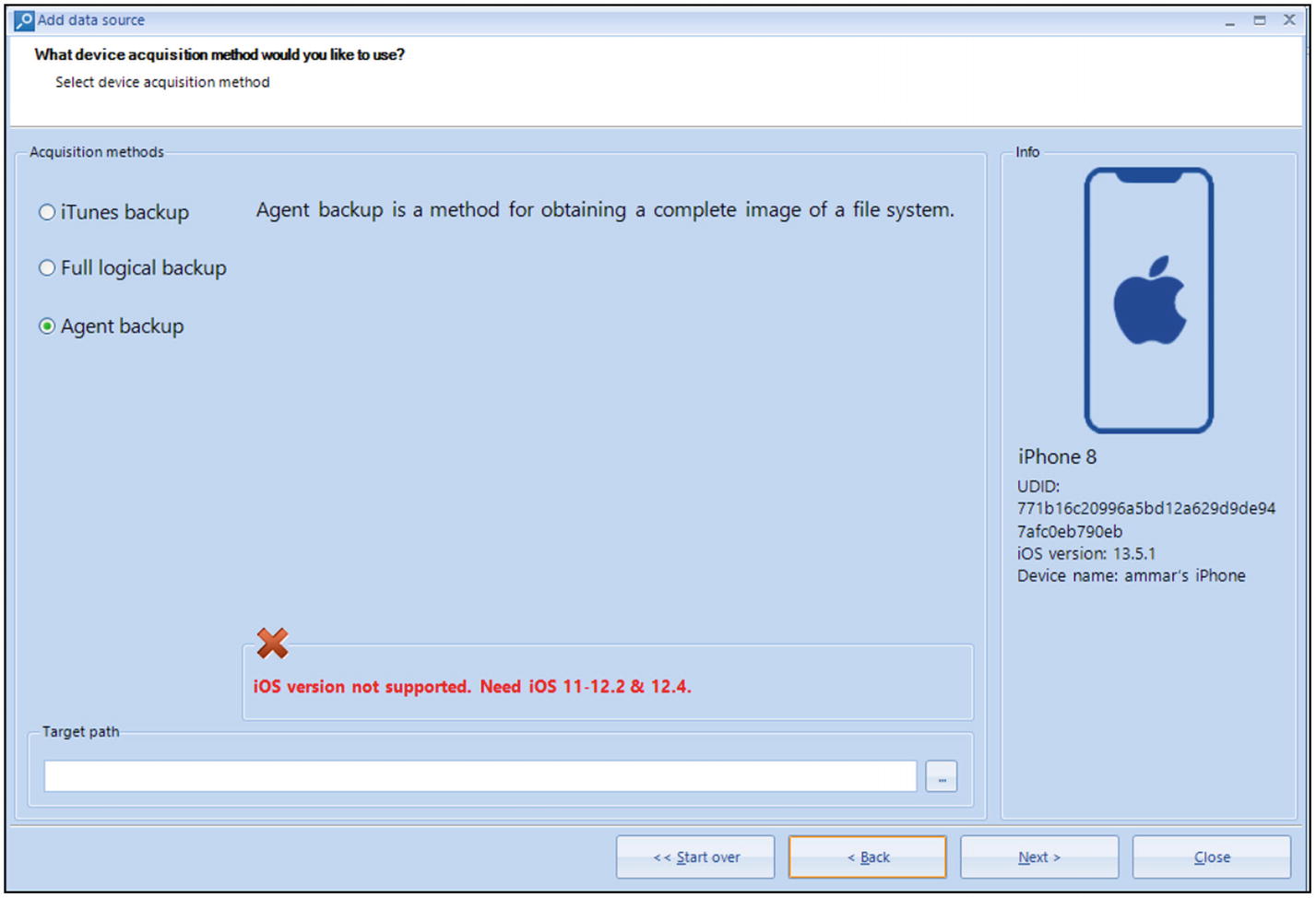
Belkasoft Agent backup

Belkasoft iTunes backup

Belkasoft main menu
Using FINALMobile

FINALMobile main menu

FINALMobile OS selection

Final Mobile main menu after the acquisition
Using iTunes Backup

iTunes backup
Using iBackup

iBackup tool main menu
Using iExplorer

iExplorer main menu
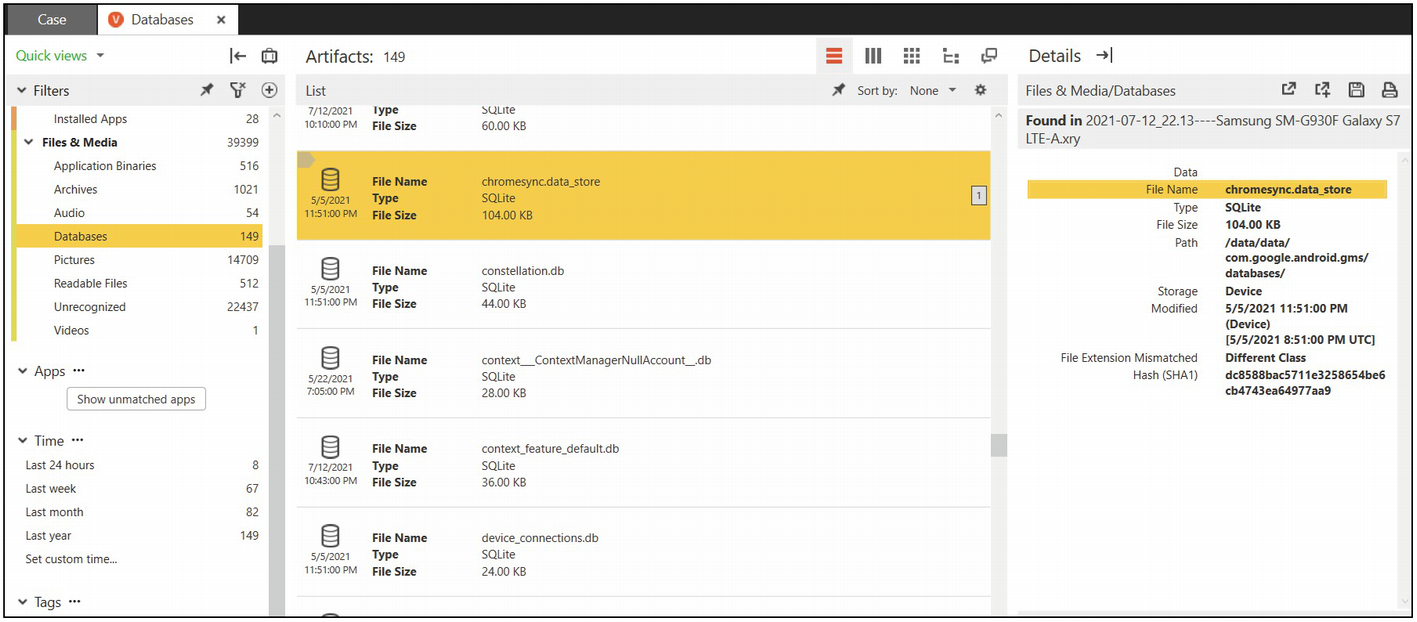
SQLite Database

SQLite XAMN
Evidence Extraction Process for Android Mobile Phone
In this section, we performed the process of extracting data from an Android phone using multiple tools, after we rooted the device, as we rooted a Samsung Galaxy S7 phone, and we displayed the images and results obtained by using different tools.
The Collection Phase
Seized Phone Specifications
Brand | Samsung Galaxy S7 | Model No. | SM-G930F |
IMEI1 | 532587624892 | Color | Gold |
IMEI2 | 532587612891 | SIM | Jaw*al |
SD | Not found | Phone lock | Yes (password:0000) |
Other Notes: - There is a break in the protection screen. - The device was powered on. | |||
Mobile photos: Shown in Figure 1-18. | |||
The Examination Phase

Unrooted Android device

Rooted device
When we root the device, a new firmware is installed on the device, all applications are gone, and a new ROM is also installed.
Using XRY and XAMN
Using ADB Command

Connected device in ADB shell
Using FINALMobile

File explorer and SQLite database
Mobile Forensic Challenges on iOS and Android
Comparison between Tool Results for iOS Implementation
Used Tool | Logical Image | Required Jailbreak | Internal /external Jailbreak | Export Files | Deleted Files | View Hex Dump | Geolocation | Accounts |
|---|---|---|---|---|---|---|---|---|
XRY | ✅ | ✅ | Internal | ✅ | ✅ | ✅ | ✅ | ✅ |
Belkasoft | ✅ | ✅ | External | ✅ | ✅ | ✅ | ✅ | ✅ |
Final Data | ✅ | ✅ | External | ✅ | ✅ | ✅ | ✅ | ✅ |
iBackup | --- | --- | --- | ✅ | --- | ✅ | ✅ | ✅ |
iExplorer | --- | --- | --- | ✅ | --- | ✅ | ✅ | ✅ |
XAMN | --- | --- | --- | ✅ | --- | ✅ | ✅ | ✅ |
Comparison between Tool Results for Android Implementation
Used Tool | Logical Image | Physical Image | Root Required | Export Files | Deleted Files | View Hex Dump | Geolocation | Accounts |
XRY | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
Belkasoft | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
Final Data | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
ADB command | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
XAMN | --- | --- | --- | ✅ | --- | ✅ | ✅ | ✅ |
Summary
In this chapter, we have introduced mobile forensics by using different programs and tools to acquire the data from iOS or Android devices for both rooted and jailbreak mobile; the XRY software tool ranked first in terms of its ability to recover deleted materials. As for the rest of the programs, although they were able to extract all the data from the phone, they were not able to retrieve deleted data because the iPhone has not been jailbroken. In addition, the XRY tool jailbreaks the phone without using any third-party software or tool. Rather, through the tool itself, the phone was successfully jailbroken, and all its data was retrieved and extracted. As for using other tools and programs, it requires jailbreaking the phone using external tools to be able to complete the extraction process.
References
- [1].
Al-Dhaqm, A., Razak, S. A., Ikuesan, R. A., Kebande, V. R., & Siddique, K. (2020). A Review of Mobile Forensic Investigation Process Models. IEEE Access, 8(September), 173359–173375. https://doi.org/10.1109/ACCESS.2020.3014615
- [2].
Anwar, N., & Riadi, I. (2017). Analisis Investigasi Forensik WhatsApp Messanger Smartphone Terhadap WhatsApp Berbasis Web. Jurnal Ilmiah Teknik Elektro Komputer Dan Informatika, 3(1), 1. https://doi.org/10.26555/jiteki.v3i1.6643
- [3].
Kuittinen, T. (2013). Exclusive New Survey Shows BlackBerry’s BBM Beating WhatsApp And SnapChat In Key Markets. Available at www.forbes.com/sites/terokuittinen/2013/11/26/exclusive-newsurvey-shows-blackberrys-bbm-beating-whatsapp-and-snapchat-in-keymarkets/#4a0055b92dd8
- [4].
Riadi, I., Umar, R., & Firdonsyah, A. (2017). Identification Of Digital Evidence on Android’s Blackberry Messenger Using NIST Mobile Forensic Method. International Journal of Computer Science and Information Security, 15(5), 3–8.