Since the turn of the 21st century, because of the tremendous growth in social media, online resources, and websites such as Facebook, there has been a vast number of users who have been sharing a huge amount of private data such as texts, pictures, videos, and calls on the Android and iOS platforms through instant messaging applications like Messenger, WhatsApp, and so on. This chapter investigates how much privacy these applications can provide for users, along with how much information can we get through forensic investigation using digital forensic tools like FINALMobile, Mobiledit, and so on.
Introduction to Investigations of Popular Applications
Extracting Data of the Activities of the Instant Artifacts
Details of Device Seized for Examination
Gmail Application Artifacts
Gmail App Seizure Device Information for iOS and Android
Gmail App Physical Extraction
Mobile Forensics for Google Drive
Extracting Data of the Activities of the Instant Artifacts
In previous chapters, we introduced the Android and iOS architecture. The iOS architecture includes an intermediate layer between the programs and the hardware such that they do not communicate directly. Also, the lowest levels provide fundamental services, while the upper layers give the user interface and advanced visuals. The Android architecture incorporates a variety of components to support the demands of any Android device. Android software has an open source Linux kernel that includes a collection of C/C++ libraries that are accessed via application framework services.
This chapter is divided to three sections: the first section introduces the process of extracting the data remaining from instant messaging and other applications on an Android and iOS platforms. The second section extracts data from Gmail application artifacts using both the recent iPhone operating system and Android 10, and describes the proliferation of mobile phone industries, which caused an increase in the opportunities for the intruder’s chance to do their activities beyond the challenges of the new techniques. The third section explains how to analyze evidence from Google Drive by applying a mobile forensic method on an Android smartphone on which the Google Drive application is installed.
Implementation and Examination Details
This study uses two smartphones with an installation of Facebook Messenger, WhatsApp, and so on. It focuses on extracting the data remaining from instant messaging and other applications on Android and iOS platforms. This chapter studies the user’s behavior, including logging on to these applications, uploading images, exchanging information, and so on. All the experiments are conducted on real systems and iTunes backup files. It performs on OPPO Reno5 F under the Android operating environment and on IPhone7 under the iOS platform; instant messaging applications are already installed in all cases.
Details of the reporting agency: Dr. Mohammed Moreb
Case identifier: 741994
Date of evidence receipt: 24th April 2021
Identity of the submitter: PalMobileCenterTest
Forensic investigator: Rawan Samara

Details of the device seized for examination
Then, we create an image file for the physical memory of the smartphones and use forensic tools to extract and analyze the data extracted from the image files. After that, extract data and create image files from physical memory by connecting the mobile phone with the computer by using the phone cable after enabling developer options and allowing connection via USB (introduced in Chapter 2). Following that, when the two devices are connected, we use forensic tools and continue with the device connection, user settings, acquisition, examination, analysis, and reporting. During the acquisition for the iPhone7, there were some additional difficulties over what was seen during the acquisition for the OPPO mobile, namely, requesting the iTunes program to be open in the PC, needing the iTunes backup password, and being locked out of the iPhone multiple times.
Results and Analysis
Every operating system has its pros and cons; for example, iOS was very difficult in the acquisition process especially without jailbreak, and the process required a lot of time, authentications, and passwords, but on the other hand the iTunes backup folder was very helpful, and it could have a lot of valuable data without undergoing the jailbreak process. Also, the jailbreak is not an easy task, and it has many disadvantages, of which voiding the warranty is just one. As for Android, the problem was that without rooting, the data was not enough, but with rooting, there are a lot of disadvantages (e.g., Installing incompatible apps, It can brick your device, No more warranty, Tweaking risks, and Update problems) and the rooting process itself is very difficult and complicated especially with the new versions of Android. However, if rooting were to be done, which we couldn’t do in our situation, it would allow access to important files, which would have made the acquisition much easier and would have produced a lot of data, but this is for future work.
Acquisition for iOS - iPhone 7
Normal acquisition without jailbreak: We tried to do normal acquisition using FINALMobile4 and Belkasoft without jailbreaking for the iPhone but it was not successful, because it got an extremely limited data (some images, videos, and device information).
Acquisition using the database stored in iTunes backup folder: Using this method was the most suitable solution to extract a lot of data for a nonjailbreak iPhone; although the acquisition took a lot of time compared to the normal acquisition, the results were amazing, from passwords, notes, contacts, call logs, chats on SMS, Instagram, Facebook, Messenger, WhatsApp, and so on. Of course, the result was different in every program as shown in the following:
Belkasoft: We used Belkasoft Evidence Center X, and it extracted a lot of data compared to other programs and other features like charts. It extracted data like pictures, videos, call logs, notes, chats from WhatsApp, Messenger, SMS, and so on. Also, it extracted a lot of data that did not show in other programs like audio files, calendars, visited websites, chats in TikTok, files in DropBox and GoogleKeep, documents, emails, passwords, and deleted files.
FINALMobile Forensics 4: This program was remarkably effective in extracting all types of data like GoogleKeep, cloud documents, Google translate history, notes, account details, pictures , videos, and contacts, call logs, and chats for Facebook, Instagram, WhatsApp, and account details for Snapchat and LinkedIn, except data from SMS like messages, contacts and call logs, documents, device information, calendar and web browser information like accounts and history. Unfortunately, FINALMobile did not support SQLite analysis.
Magnet Axiom: There is a specialty in Axiom that does not exist in other programs: the real-time preview for chats, documents, and everything exactly as you see in your smartphone. In addition, the extracted data was incredibly good; it also was the only program that extracted data from Zoom, Skype, and iOS call logs. It did extract data from Tok-Tok, WhatsApp, Messenger, Instagram, notes, documents, audio, pictures, and videos, but very little data from Safari. Also, it does SQLite analysis.
Mobiledit Forensic: This program was the most amazing one because it extracted every tiny detail in the phone with a report with 1,2435 pages; it holds everything and every detail in the phone, even the deleted data and the previous accounts. No SQLite was found but there were XML files and Excel files with data.
IExplorer: This was the best program for investigating the device’s built-in apps and data like contacts, messages, notes, calendar, call logs, Safari history and bookmarks, photos, and videos.
SQLiteSpy: The whole Apple device line relied heavily on SQLite databases to store data. Most built-in iOS applications, such as messages, phone, mail, calendar, and notes, save data in SQLite database tables. In addition, many third-party programs running on mobile devices use SQLite databases to store data. Databases are commonly given the SQLite db or “.db” file extensions, as well as other extensions and file formats.
Acquisition for Android Device - OPPO Reno5 F
Logical acquisition (Nonrooted device): We used this method on OPPO Reno5 F using many challenges as follows:
Mobiledit: Unfortunately, no data was extracted from any application in the device. The only information we got is the permissions that the device granted for every application.
FINALMobile: This program was one of the best when dealing with Android without rooting. It extracted a good amount of data like Messenger, Twitter, and Instagram chats. Also, it detected the true caller, which was a bonus.
Belkasoft: We used another version of Belkasoft with Android (the crack version of Belkasoft evidence center), which is not as good as Belkasoft X. Also, the fact that the device is unrooted reduces the amount of data extracted. This version extracted only the image, audio, video, document, location, and device information.
Axiom Magnet: It was the worst in extracting data. There was a problem with the application when it was installed on a nonfunctional phone which does not run, and I think the agent that uses it is not compatible with OPPO devices.
DB Browser (SQLite): The SQLite database is a free and open source database engine that is used as an in-process systematic library to deploy transactional SQL databases. The SQLite database is a full database that has multiple tables, programmable triggers, and data views in a single platform file. Because SQLite is a dependable, portable, and lightweight database format, it is the most often used database format in many mobile environments. Several attempts to root the phone (Redmi Note 7) were made using XRY, TWRB, MI Flash, and other tools as shown in Figure 4-2, but there was a problem when the app (find device) couldn’t activate the SIM card that associated with the MI account, which meant that we couldn’t unlock the bootloader to continue rooting. We also tried recovery boot and a variety of other approaches, but none of them worked. More research and study are needed on this subject to complete, as we explain in the next chapters. For the screen lock bypassing technique, there’s a Halab Tech tool that can remove the lock screen, but the device must be rooted.

Acquisition data using different tools
Gmail Application Artifacts
This section will introduce the process of Gmail investigation artifacts on both operating systems: iOS and Android. The revolution of the development of smartphones in the last few years, especially the variation in developed applications, has made life easier, and such applications are fast enough to handle such problems in real life. The statistics show that the number of smartphones running worldwide is 3.6 million in 2020, and the expectation in 2023 to be 4.3 million (Statista, 2021).
Here is a brief introduction to a famous artifact on mobile devices that may help make the overall picture of mobile investigations more easily understood. A mobile web browser is an application used to access the Internet. Using a web browser, a user can search information, communicate with others using social networks, send/receive emails, and so on. The forensic artifacts that are left by a web browser like Google Chrome as a session ends are not only website visits, downloads, and cookies, but other artifacts like time of access and some keywords. Web browsers store a large amount of data on the user’s hard disk, and either Safari or Google Chrome stored data about the user such as usernames, emails, downloads, temp files, and cache in a database of SQLite at the user’s side. Investigations on mobile web browsers are also known as mobile forensics, which is divided into two techniques: live and static (Sariboz, E., & Varol, C., 2018).
A technique that allows investigators to restore deleted files is relying on the journaling file system in iOS. The forensic analysis to confirm the suggested technique (A. Ariffin, C. D’Orazio, K. R. Choo, and J. Slay, 2013). In addition to that, there are multiple methods for collecting data and extracting evidence, as well as corresponding policies. However, combined with rapidly changing technology, many challenges in the forensic investigation process. In iTunes backup utility the data of forensic value like email messages, text, and messages, calendar, browsing history, call history, and others may be found using iPhone capture dump. Despite their research professionalism they did not mention live data forensics (Bader, M., Baggili, I., 2010). Android forensic for extracting Gmail data from mobile device has received recent attention: researchers have successfully found extracted data from the database of the Gmail application under /data/data/com.google.android.gm directory. The one thing that has not been solved is how to find the encrypted files residing in the database directories for Gmail (Kim, D., & Lee, S., 2020).
International cooperation in cybersecurity law is taking place in constituencies to bring international support to cybercrime issues. International Telecom Union (ITU) in 2014 in WASIS initiated an initiative in cybercrime cooperation in five regions worldwide (ITU Cybersecurity Activities, 2020).
On May 25, 2018, the European Union (EU) launched the General Data Protection Regulation (GDPR), which is security and privacy law (What is GDPR, 2019). On the other hand, in June 2017 the Republic of China approved the cybersecurity law addressing most features of security, but there is not one single word regarding mobile security (Translation: Cybersecurity Law of the People’s Republic of China, 2017), which is a weakness in this law. The Budapest Convention against Cybercrimes, the first convention related to digital crimes, took place in the Hungarian capital Budapest on November 23, 2001. It highlights the cooperation and international solidarity in combating cybercrime. The signing of that international convention is the first step in the field of building international solidarity against those crimes that take place through the Internet (Budapest Convention and Related Standards, n.d.).

Mobile forensic process
In this section, experiments with both iOS and Android will take place with all stages of the forensic life cycle as described next.
iOS Seizure Device Information
In this section, we will obtain all information about the iOS device, which is the iPad; Table 4-1 describes all information about the iPad’s status to emphasize the health of the device before the case investigation.
iPad Obtained
Color | Gold |
|---|---|
Scratches | No scratches found |
Wallpaper | Default Apple wallpaper |
Accessories | Just cover |
External storage | Not found |
SIM card | No |
- [1].
Isolation: Before starting acquisition, and because we did not have a box for isolation such as a Faraday box, we did isolation for the device from other external connections, putting the device in Flight mode to disconnect it from Wi-Fi, Bluetooth access, or cabling. This operation is done on all devices in both iOS and Android.
- [2].
Acquisition To acquire mobile phones, there are three types of extractions used: manual, logical, and physical extractions.
- [3].
Manual Acquisition: This method of extraction is used to verify the accuracy after the physical extractions for both iOS and Android OS. It is done simply to view the data on the mobile directly from its touch screen in a human way. Here the error tolerance for the data is based on human error.
- [4].
Logical Acquisition: In this case, we did a logical acquisition. The iOS device connected the USB-Lighting cable to the computer; then we connected the iPad to the iTunes software, and we got specific information about the device as shown in Figure 4-4.
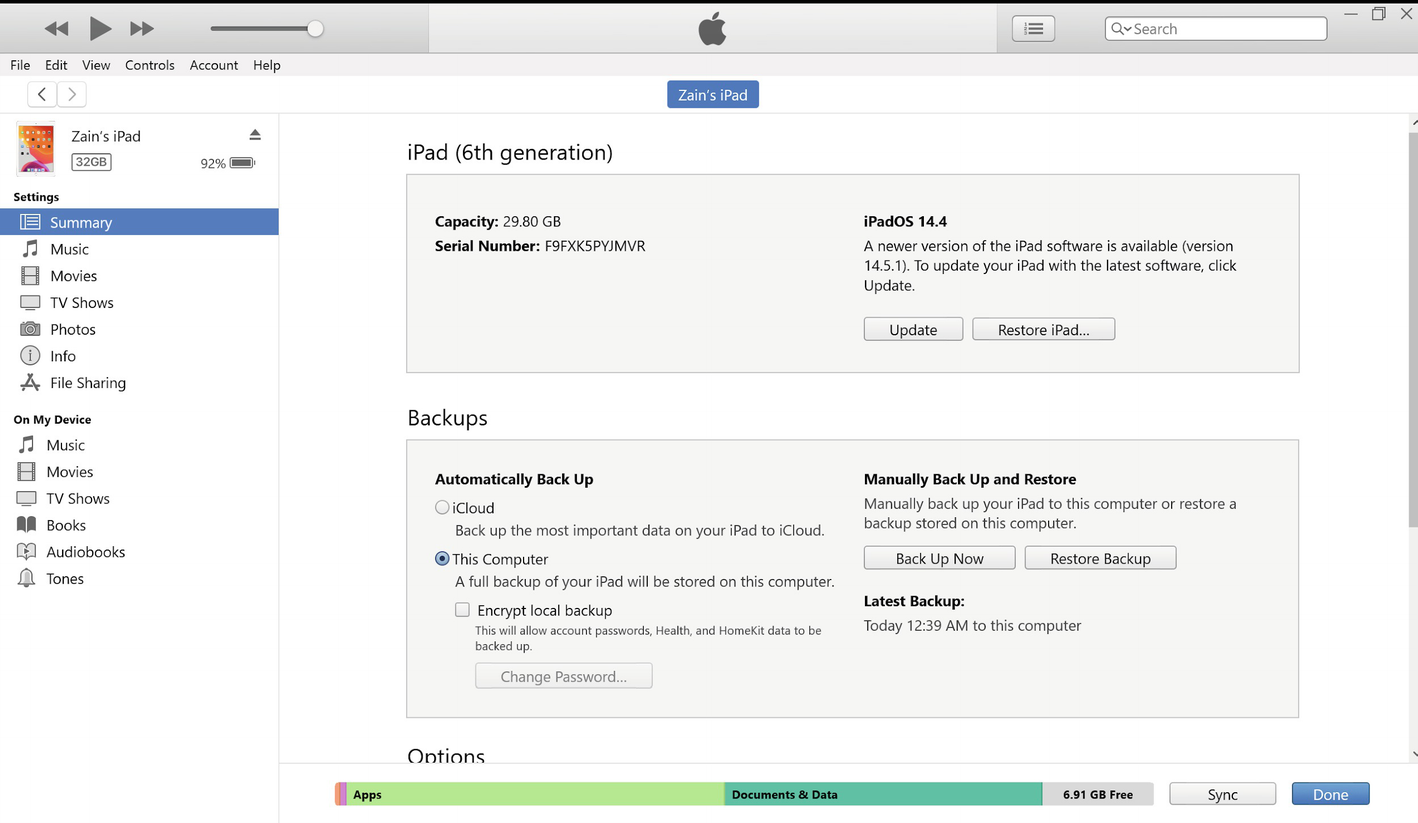
iTunes Dev status

Android file structure
From our practical case, we can summarize the comparisons between logical backup and device backup; the iOS logical acquisition is fast and compatible with all iOS versions running on Apple devices using iTunes. Also, it gets shared application information but not all data files and databases of the iOS. In device backup, which is bit by bit, the backup will include all file systems with database and SQLite files, and deleted files also will be there. Android devices using ADB backup may get logical backup, since the device is not rooted, but if we have a rooted device, we can get physical backup reaching a low level of the file system with all database files.
- [5].
Analysis: In this section, we will analyze the data acquired from iOS and Android OS, also comparing the acquisition tools used. The acquisition proceedings were conducted according to the iPad device while it’s unlocked, and we used the logical acquisition because the physical acquisition did not occur while the iPad was not jailbroken. We moved over the backup files that iTunes generated from the device on the preceding path, and then we browsed the “Manifest.db” database SQLite using the DB SQLite viewer as shown in Figure 4-11.
- [6].
Verification: After the acquisition, we did a verification on the backup file that matches the real device data by comparing the data in the backup file with device data. Also, we took the hash value of the file to make sure that there were no changes in data. The hash file was taken using PowerShell in Windows. Figure 4-6 shows the process of calculating the hash file, also in text representation as SHA256:
00D32E16FE52AE6E69F5448778338344E12FC30FF46D2FDE4D0C5CC282F29F4F

Hash SHA256
- [7].Analysis and Findings: Finally, we had the backup file for iPad as shown in Figure 4-7. The system gives a name for the backup as unique identifier c3929606ab580d10ee494d31528706f879f34915, and has the following files:
info.plist
manifest.plist
status.plist
manifest.db

Backup folder
info.plist:
Applications: All applications installed on iPad
Build version: iOS build version: 18D52
Device name and display name: Device owner name: Zain’s iPad
Globally Unique Identifier (GUID): 1FE45D6A5076661CD28000DCC71C30D7
Last backup date: 2021-05-30T22:51:54Z
Serial Number: F9FXK5PYJMVR

info.plist view
manifest.plist:
Backup keybag: Key backup
Version: Backup version 10.0
Date: Last backup or updated 2021-05-23T21:38:56
WasPasscodeSet: To find whether a passcode was set or was not. NO
Lockdown: Holds iPad details, and other information.
Applications: All third-party applications installed.
Is Encrypted: To find whether backup taken in with encryption or not: False.

Manifest view
status.plist:
IsFullBackup: False.
UUID: E79B08BF-FD8E-41F5-9247-7E45474410D5
Date: 2021-05-30T22:51:43Z
BackupState: New
SnapshotState: Has the backup process finished successfully: Finished.

Status.plist view
manifest.db:

Manifest data view

Belkasoft tool
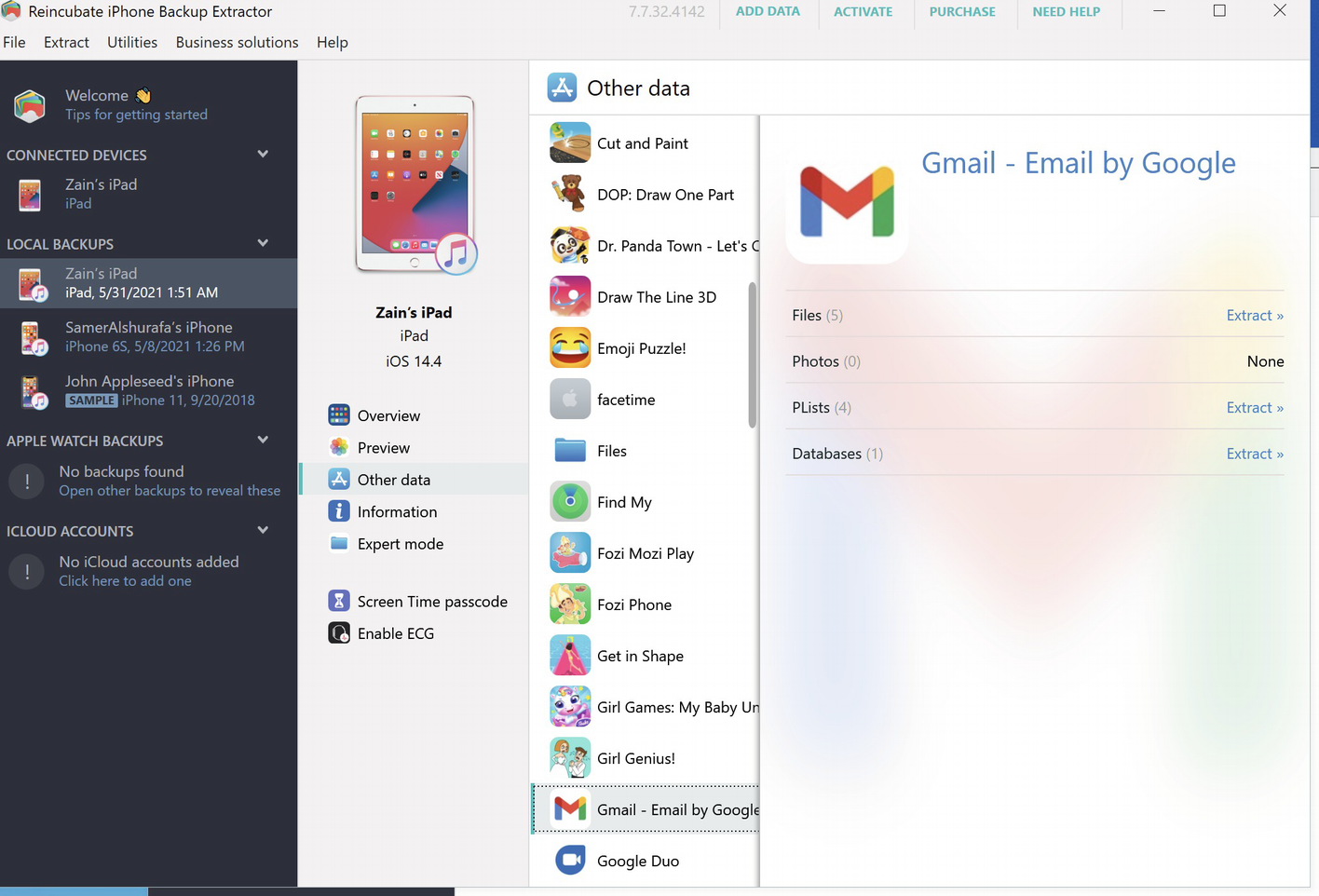
Gmail artifacts

Contact details
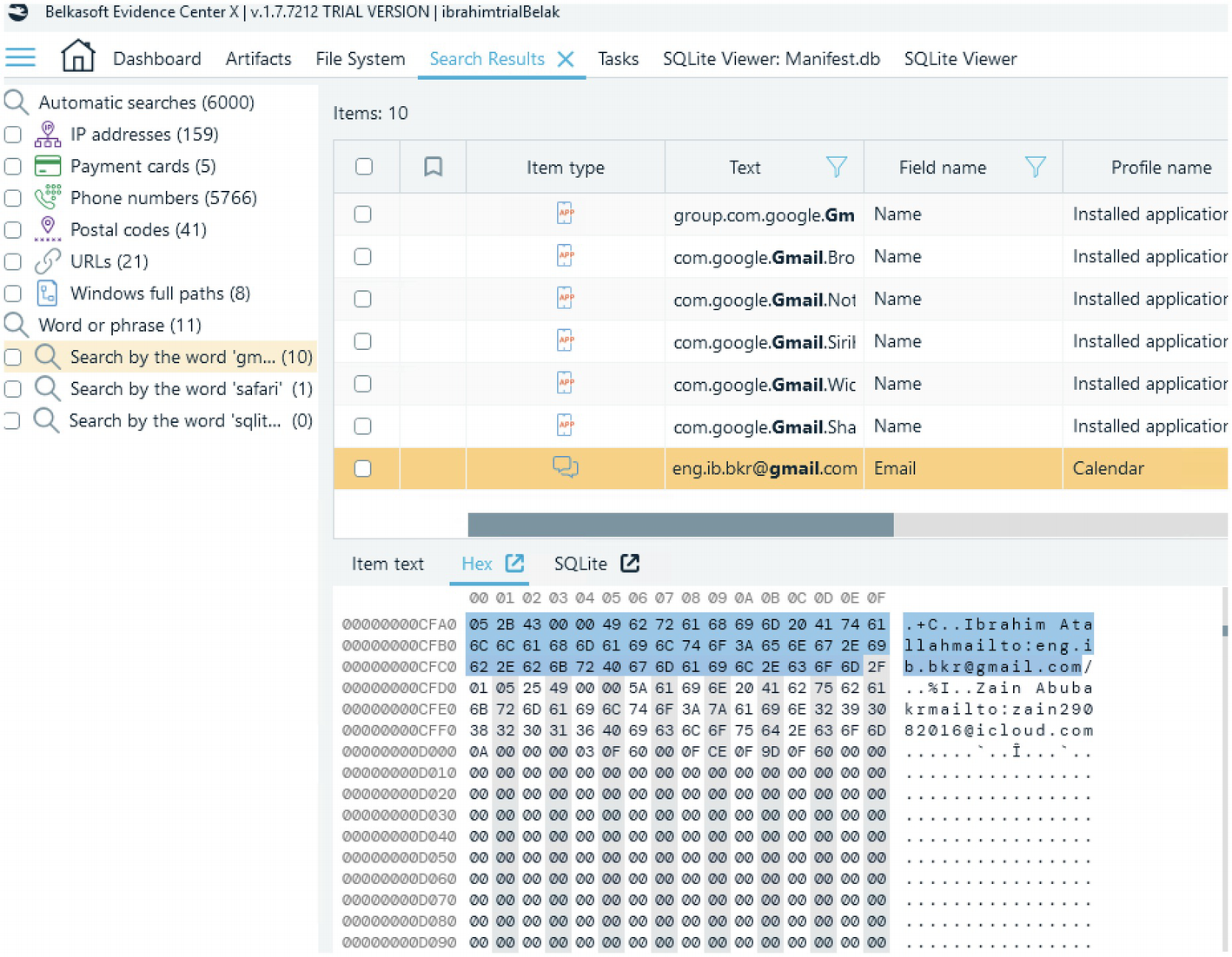
Gmail artifact
After extracting the backup file using elcomsoft, go to the home domain under the directory path C:UsershpcDesktopelcomsoftwaseemHomeDomainLibrarySafari. We found all directories needed in our investigation. We will look at the following:

Query result

Safari bookmark
Android OS
- 1.
Tecno Spark 6GO.
- 2.
Xiaomi Mi 8 lite (Figure 4-19 shows the Xaiomi mobile information)
- 3.
Nox virtual machine mobile.

Xaiomi Mi 8 lite information

FINALMobile data acquisition
It is important to know that all acquisition methods will not take a full backup if the device does not root state. Otherwise, it will be a logical backup.

Root user logged in
Using Mobiledit and FINALMobile Forensic Software

Mobiledit ADB logical backup

FINALMobile software data analysis
Rooted Device

ADB device list

Root user logged in

List of directories

Gmail database
List of Commands Used
Tar -cvf new.tar /database/ | Compress database directory to new.tar |
Mv new.tar /sdcard | Moving archived file to sdcard in order to pull it to our machine |
Adb pull /sdcard/new.tar c: emp | Copy new.tar to temp directory in C drive |

Database files pull process
By using Linux command, the extracted data is obtained easily rather than the next one using GUI of SQLite, because the encrypted file is not manipulated in GUI but it is easy to decode it in Linux scripting shell as shown in Table 4-2.

Gmail database files

Data analysis in Linux command
And this could be opened on SQLite software. But when trying to open a Write Ahead Log (WAL) file, this could not be opened in GUI as SQLite because this software did not support the extension of this file.
Line starting with (↔thread-a) means it is a sent message and has subject and body.
Line starting with (sg-a) means sender email address.
Line starting with (∟thread-f) means it is an inbox message and has subject and body.
Line starting with (deleted email) means it is a deleted email and found in a trash folder.
Line starting with (▲thread-a:) means it is a draft message.
Attachment and time creations found in the next section.

WAL file content
SQLite Viewer
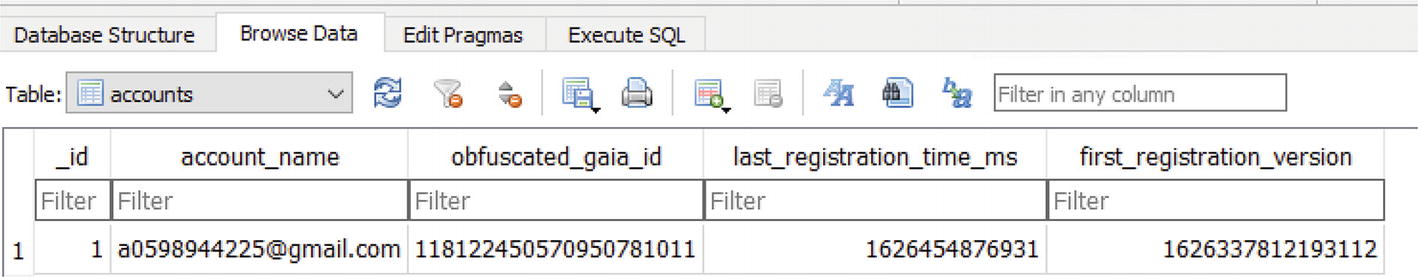
SQLite viewer Gmail account table
Epoch convert time

Attachment details
Forensic Tools Comparisons
Android Forensic Tool Comparison
ADB Shell | Mobiledit | FINALMobile | |
|---|---|---|---|
Acquisition via connected USB ADB | Yes | Yes | Yes |
Gmail data files | Yes | (NO) Only XML | (NO) Meta data |
Gmail data file from backup | No | (Yes) Only XML | (Yes) Meta data |
SQLite database | SQLite3 built in | No | Yes |
Mobile Forensics for Google Drive
Cloud computing is a form of Internet-based computing that allows computers and other devices to access shared information-processing resources and data on demand. Because of the rapid technological evolution related to mobile devices and cloud computing, users could access their resources from any place and at any time. Nowadays, the use of cloud storage media is very popular among Internet users, especially with the Google Drive cloud storage media on smartphones. Google Drive is a file storage and sharing platform that provides storing and synchronizing many types of users’ files, which can be accessed via their Google accounts. Google Drive applications can be installed on Apple and Android smartphones, so viewing, editing, uploading, sharing, and synchronizing documents are available on these devices.
This section’s case is an exercise in analyzing evidence by applying a mobile forensic method on an Android smartphone, on which the Google Drive application is already installed. To analyze the evidence, a crime situation has been created in which the user saves a photo of drugs on the smartphone’s Google Drive. Many forensic software programs were used to acquire the Google Drive data. Firstly, the Belkasoft Evidence center was used but it gives an error “Operation completed with errors” and not all the data required could be opened. Another one is the Mobiledit Forensic Express; the data was acquired but hashed.
Evidence collection is the first step in securing evidence discovered by police or investigators is preservation. In this case, the prosecutor received proof from the owner in the form of a Xiaomi Redmi Note 8 Pro smartphone with the operating system Android 9.0 Pie, 4GB RAM, and the Google Drive application installed on it. The isolation process is required to avoid changing data on the smartphone by triggering the Airplane mode feature. This feature is allowed to disable all data access that might compromise the smartphone’s data integrity. This procedure is followed in order to ensure data integrity. Data integrity is achieved by imaging files from the physical evidence using Mobiledit Forensic Express. The phone image was created but hashed.

Google Drive description

Deleted data

Odin for rooting

Backup from device to workstation

Mobiledit acquire (rooted device), database browse for Google Drive
Cloud Storage Services Artifacts
Amazon S3: By running Amazon’s S3 on an iPhone, a plist file and an SQLite database file will be generated. The plist file includes the user’s name, access key ID, and secret access key. These are used for accessing Amazon S3 on an iPhone [7].
Dropbox: By running Dropbox on an iPhone, a plist file and two SQLite database files will be generated. The plist file includes an email address for login, and the first login time using that iPhone [7].
Evernote: By running Evernote on an iPhone, many types of files will be generated such as applog.txt, which is a text file that reports the history of the use of Evernote [7].
iGoogDocs: By running iGoogDocs on an iPhone, a plist file and an HTML file will be generated. The plist file includes a value for auto-login that can be “true” or “false.” If the auto-login is “true,” the plist file contains user account information, including even the password. In Google Docs for the iPhone, it is possible to create text files. They are stored in a folder named “Local Files.” The contents of the files are in an HTML file [7].
Summary
Gmail is the only email that has come with default Android application in the last couple of years, and it is used to create accounts and define private (non-Gmail) accounts on it, which makes it easy for the users to handle their emails via Android mobiles.
Nowadays, the data forensic since is used for white and black purposes; we as students at Arab American University achieved the goal of the mobile forensics course, which is how to do successful mobile forensics in order to extract data from mobiles. My experiment shows that there is no way to extract Gmail data by logical acquisition nor by manuals unless you have an authorized access, and the only way to bring the application data from the device is if physical acquisitions are there. But physical acquisition will not be valid without root permission on Android devices or jailbreak on iOS.
Recently, iOS devices have been able to extract data information about the account and sender receiver subject of the email, but no data is given about the email body itself because of the nonjailbreak device; that is why we did not access superuser privileges.
The Android version had no vulnerability to do root easily, and the developers had hardened their codes to be increasingly robust and secure. In our experiment on both devices, Xiaomi Mi 8 lite and Techno Spark with Android 10 QKQ the rooting failed, but we succeeded to root on virtual mobile Galaxy Note 10 successfully.
Lastly, we got all the information in Gmail including accounts, creation date of accounts, sent email, inbox, draft, and deleted files.
References
- [1].
J. Starkey, “Google Drive,” The Charleston Advisor, p. 4, 2013.
- [2].
D. M. Rathod, “Google Drive Forensics,” csjournals, vol. 8, no. 2, p. 6, 2017.
- [3].
2018. Law by Decree No. 10 of 2018 on Cybercrime. [eBook] Available at: <https://security-legislation.ps/sites/default/files/law/Law%20by%20Decree%20No.%2010%20of%202018%20on%20Cybercrime.pdf> [Accessed 21 April 2021].
- [4].
R. Tamma, O. Skulkin, H. Mahalik and S. Bommisetty, Practical Mobile Forensics, 2020.
- [5].
A. Yudhana, R. Umar and A. Ahmadi, “Digital Forensics,” Scientific Journal of Informatics, vol. 6, p. 10, 2019.
- [6].
C.-T. Huang, H.-J. Ko, Z.-W. Zhuang, P.-C. Shih and S.-J. WANG, “Mobile Forensics for Cloud Storage Service on iOS Systems,” IEICE, vol. 1, p. 5, 2018.
- [7].
M. Faheem, M.-T. Kechadi and N.-A. Le-Khac, “The State of the Art Forensic Techniques in Mobile Cloud Environment: A”.
- [8].
H. Chung, J. Park and S. Lee, “Digital Forensic Investigation of Cloud Storage Services,” p. 20, 2018.
- [9].
DarrenQuick, B. Martini and R. Choo, “Google Drive: Forensic of Cloud Storage Data Remnants,” in Cloud Storage Forensics, Syngress, 2013, p. 95
- [10].
Y.-T. Chang, K.-C. Teng, Y.-C. Tso and S.-J. Wang, “Jailbroken iPhone Forensics for the Investigations and Controversy to Digital Evidence,” Journal of Computers, vol. 26, p.15, 2015.

