7
Options and Actions (Response Planning)
The steps in the First Risk Assessment of the ATOM risk process described so far (Identification and Assessment) can be viewed as analysis, scoping the extent of the risk challenge for the project, seeking to understand the risks to which the project is exposed. However, simply understanding and describing the risks does not change them. It is vital that the risk process move on to action, actually dealing with the risks in order to change the project’s risk exposure. This is the purpose of the last element of the First Risk Assessment, which in ATOM is called Response Planning.
In many ways Response Planning is the most important step of the risk process, because effective risk responses result in minimized threats and maximized opportunities, optimizing the project’s chances of achieving its objectives. Conversely, poor response planning can worsen the position, not only by failing to address identified risks but also by introducing new risks as a result of ineffective actions. This step is where key decisions are made on how to manage risks, using risk information to modify project strategy where necessary and positioning the project to gain the benefits offered by the risk process.
The key word in Response Planning is appropriateness. Recognizing that risks include both threats and opportunities, the aim of the project team is to make the negative risk exposure from threats as small as possible while increasing the positive risk exposure from opportunities. The appropriate response to each type of risk is clearly different. For some threats it might be appropriate to panic, or even cancel the project. It could be right to embrace some opportunities and actively seek the additional benefits they offer. For other risks the appropriate response may be to do nothing and wait to see what happens. Obviously, a project should not panic over risks for which the appropriate thing is to do nothing, and it should not do nothing when a risk should be actively embraced. Choosing the appropriate response is an important decision requiring careful judgment, and is best done by people with the necessary level of experience and expertise.
As a result, it is vital that sufficient attention and effort be applied to Response Planning. Time and effort invested at this step in the process pays dividends in process effectiveness, whereas shortcuts have negative repercussions.
The purpose of the Response Planning step in ATOM is to:
• Consider all identified risks and select an appropriate response strategy for each
• Develop specific actions that put into practice each response strategy, with enough definition to allow effective implementation
• Ensure that each action is assigned to an Action Owner.
In order to do this, the following inputs are required:
• Risk Management Plan, defining risk tools and techniques for this project
• Initial Risk Register, containing information on identified risks from the risk workshop, including the following:
• Prioritized list of risks, each with a proper risk description and agreed-upon assessments of probability and impacts
• Nominated risk owner for each risk
• Initial responses proposed during the Identification step
• Information on available generic response strategies.
In ATOM, Response Planning requires the following activities:
• Response strategy selection
• Action development
• Assessment of post-response risk exposure
• Consideration of secondary risks.
The Response Planning step produces the following outputs:
• Appropriate response strategy and agreed-upon actions for each risk (including possible escalation)
• Nominated Action Owners for each agreed-upon action
• Updated Risk Register containing response information for all identified risks
• Updated assessment results reflecting the post-response situation
• Updates to the project plan (both schedule and budget) to include agreed-upon risk actions.
These inputs, activities, and outputs are illustrated in Figure 7-1 and described in detail in the following sections.
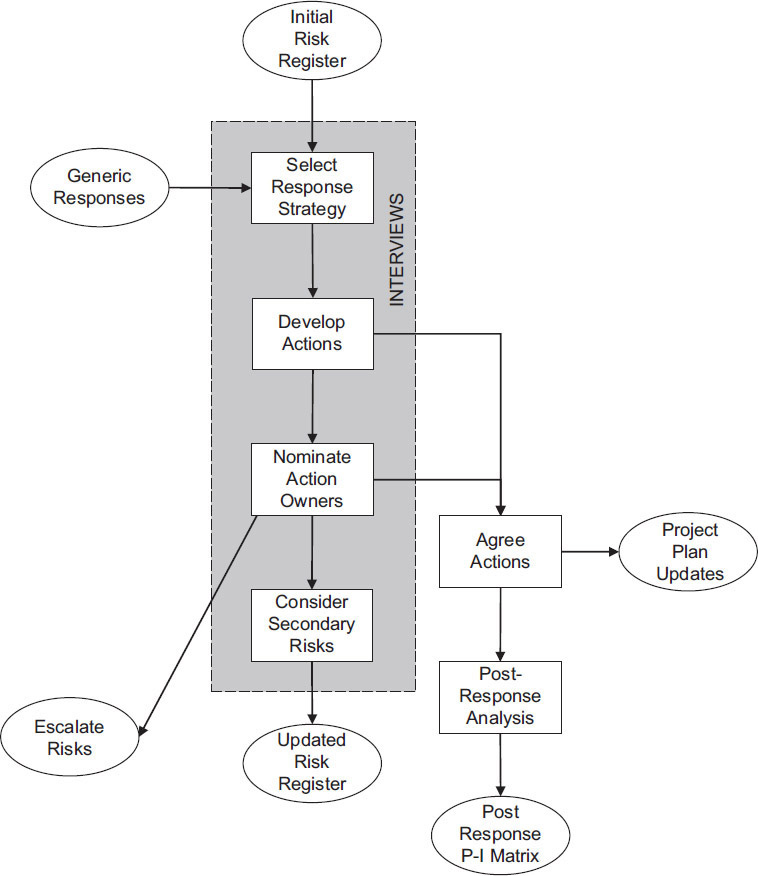
Figure 7-1: Flowchart for the Response Planning Step
Inputs
Like other steps in the risk process, the Risk Management Plan defines the detail for the risk process as it is to be applied to this project. Where necessary, the risk champion refers to the Risk Management Plan to clarify the requirements for this step.
The Assessment step allows identified risks to be prioritized, using the Probability-Impact (P-I) Matrix, into at least three groups (red or high priority, amber or medium priority, green or low priority), and possibly with more detailed prioritization using a P-I scoring scheme, as discussed in Chapter 6. Assessment also allocates to each identified risk a single risk owner, who is responsible for determining how the risk will be managed. This information is held in the Risk Register, which forms the main input to the Response Planning step. It is, however, recommended that the risk champion prepare subsets of the Risk Register, listing risks by risk owner, so that each owner can receive a list of his or her risks prior to the risk interview.
For some risks, initial responses may have been identified during the Identification step, and these will also have been recorded in the Risk Register. These responses are presented to risk owners for validation during this Response Planning step to confirm that they are appropriate and acceptable.
The final Response Planning input is information on what response strategies are available to risk owners. This information might exist within the organization as part of a knowledge base, or it might be prepared by the risk champion as a pre-brief for risk owners.
Activities
Response Planning can be undertaken as part of the risk workshop if there is sufficient time available. However, workshop time is frequently limited and may run out before responses can be considered for any or all identified risks. When time is available for Response Planning during the workshop, risks are considered in priority order, dealing first with the worst threats and best opportunities. Following the risk workshop, the risk champion holds a series of interviews with risk owners to deal with those risks not covered during the workshop. This section describes risk interviews, assuming that the risk workshop time is fully taken up by the Identification and Assessment steps, and that all response planning will take place this way.
Activities relating to risk interviews can be divided into three groups: preparation, interviewing, and post-interview tasks. These are described in the following paragraphs.
PREPARING FOR RISK INTERVIEWS
The risk champion schedules interviews with all risk owners immediately after the risk workshop, with the goal of completing all interviews within one week. Each interview should be scheduled for two hours, though the full time may not be required, depending on the number and difficulty of risks to be addressed in each interview. When scheduling interviews with risk owners, the risk champion sends an extract from the Risk Register, containing the risks assigned to them, listed in priority order, as well as practical arrangements for the interview, including time, venue, agenda, etc. For risk owners new to the process, it might also be useful to send a reminder of the generic response strategies available. An example is given in Figure 7-2.
Prior to the risk interview, each risk owner prepares by considering his or her risks and possible options for responses and actions. This maximizes productivity during the interview.
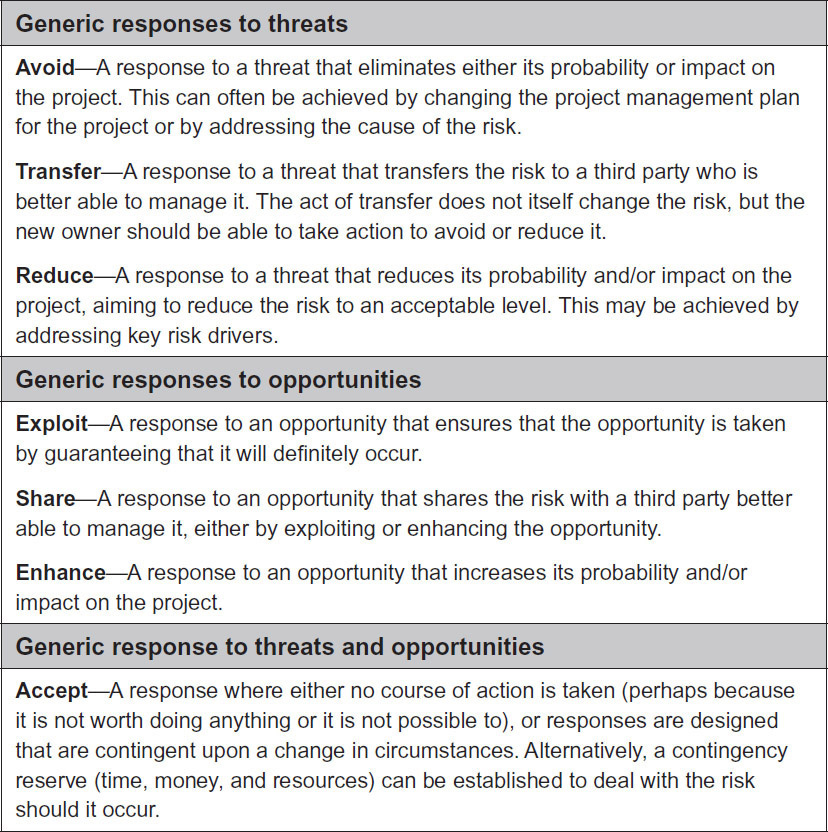
Figure 7-2: Generic Response Strategies
CONDUCTING RISK INTERVIEWS
At the start of each interview, the risk champion confirms the interview’s purpose and agenda, and emphasizes its confidential nature. For each risk, the risk owner, in discussion with the risk champion, will:
• Select an appropriate response strategy
• Identify possible actions to implement that strategy
• Assign Action Owners to each action
• Assess post-response probability and impacts
• Identify any secondary risks.
Any valid risks that are outside of the remit of the project in question should have been escalated as part of the Assessment step. However, it is possible that after further inspection during a risk interview, the risk champion and owner may decide to escalate a risk. In this situation, the risk champion should inform the project manager, who must ensure that the risk is properly escalated.
The role of the risk champion is to prompt and encourage the risk owner, facilitate the interview to maintain momentum and ensure good timekeeping, answer questions relating to the risk process or risk management theory and practice, and suggest possible response strategies and actions based on his or her own experience. However, it is the risk owner’s responsibility to decide which response strategy and actions are appropriate for the risks that he or she owns.
Each risk allocated to the risk owner is considered in turn and worked through in priority order, as follows:
1. Red/high-priority opportunities
2. Red/high-priority threats
3. Amber/medium-priority opportunities
4. Amber/medium-priority threats
5. Green/low-priority opportunities
6. Green/low-priority threats.
Considering opportunities before threats is recommended because people are less familiar with including opportunity in the risk process.
When addressing high-priority risks, often the proposed response strategies also address some of the medium- or low-priority risks. The risk champion must bear in mind this potential risk management efficiency when carrying out further interviews and developing responses to less important risks.
Initial responses to particular risks proposed during the Identification step are considered first. The risk owner decides whether the proposed response would be appropriate and effective, and this decision is recorded in the Risk Register.
If there is no previously identified response, or if the initial response is rejected by the risk owner, they must select an appropriate response strategy for each risk. For opportunities, this is either exploit, share, enhance, or accept. Available threat strategies include avoid, transfer, reduce, or accept. It is recommended to consider strategies in the order shown in Figure 7-3, since the best option, if possible, is to avoid a threat or exploit an opportunity. This may be achieved by addressing the cause of the risk, as recorded in the description of the risk using the metalanguage. Where this is not feasible or cost-effective (see below), alternative parties should be sought who are better able to manage the risk effectively, allowing a threat to be transferred or an opportunity to be shared. The third option is to modify the level of risk exposure by reducing a threat or enhancing an opportunity. The last option is to accept the risk, with possible development of a contingency plan, taking into account the effect of the risk as defined in the risk metalanguage.

Figure 7-3: Priorities for Selecting Response Strategies
Factors to be considered when deciding which strategy is appropriate include:
• Manageability. To what extent can the risk be influenced?
• Impact severity. Can the impact be borne if the risk occurs, or is the potential impact so severe that something has to be done?
• Resource availability. Are resources available to implement the chosen response within the desired time frame?
• Cost effectiveness. Can the desired effect on the risk be achieved at a reasonable cost?
For each risk, a single response strategy is selected that represents the current best choice for managing the risk effectively. This recognizes that a different strategy may be selected in the future if the one first chosen proves ineffective, but at this stage in the process each identified risk must have just one strategy.
Next, the risk owner determines specific actions that could be implemented to achieve the selected strategy. These are described in as much detail as possible, ideally including what is to be done, by whom, when, and at what cost, and with completion criteria. The aim is to define each action at the same level of detail and as a normal activity in the project schedule. A particularly important step is to nominate suitable owners for each action (Action Owners) who have the necessary skills and experience to perform the action effectively.
After defining actions, the risk owner provides an assessment of the risk, assuming that the actions are completed successfully. Using the same P-I scales from the risk workshop, the post-response probability of occurrence and impacts on objectives for the risk are estimated. This gives an indication of how “risk-effective“ the proposed actions are expected to be, and whether additional actions are required.
Finally, the risk owner considers whether the proposed actions will introduce secondary risks, defined as risks that arise from implementation of an agreed-upon response to another risk, as illustrated in Figure 7-4. Of course, a secondary risk can be either a threat or an opportunity. Where such secondary risks are identified, the risk owner and the risk champion together:
• Produce an agreed-upon risk description for the secondary risk, using the metalanguage, with the action recorded as the cause of the secondary risk
• Assess the probability and impacts of the secondary risk against the agreed-upon scales
• Select an appropriate response strategy for the secondary risk, and determine actions with nominated Action Owners.
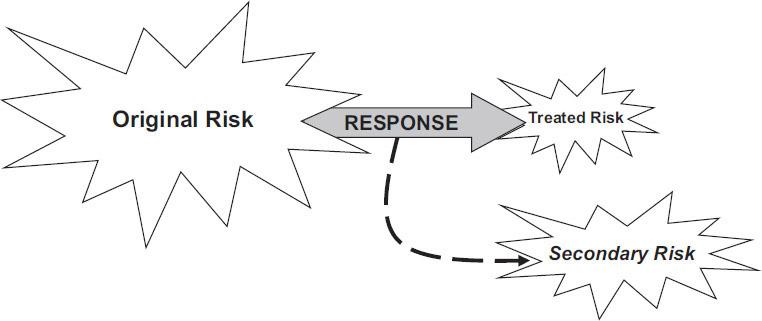
Figure 7-4: Secondary Risks
At this point the risk owner and risk champion may decide that the secondary risks associated with the proposed actions make them infeasible (particularly where significant additional threats would be introduced), in which case the proposed actions are rejected and new ones developed; in some cases, this requires selection of an alternative response strategy. If, however, it is decided to proceed with the actions as originally planned, the associated secondary risks are recorded in the Risk Register and treated as any other risks.
After all risks have been considered, the risk champion asks whether the risk owner is aware of any additional risks in his or her area of responsibility that are not currently captured in the Risk Register. Any new risks are identified and assessed, and responses and actions developed.
The outcome from this discussion is captured by the risk champion during the interview, preferably directly into the risk management tool being used to support the project risk process. Where direct data entry is not possible, the risk champion takes full notes during the interview and transfers them into the tool immediately following the interview.

Figure 7-5: Pre-and Post-Response P-I Matrices
POST-INTERVIEW ACTIONS
After each interview is complete, the risk owner is responsible for liaising with nominated Action Owners to ensure that they agree with the proposed action and accept responsibility for its implementation. Risk owners and Action Owners together may decide to refine actions at this point, and the risk owner informs the risk champion of any agreed-upon changes.
After feedback from risk owners that all Action Owners have accepted their proposed actions, the risk champion ensures that the Risk Register is updated to reflect the strategy and agreed-upon actions. The risk champion also uses the information generated during risk interviews to update assessment results to reflect the post-response situation. This includes producing a post-response double P-I Matrix (Figure 7-5) to show the predicted position of each risk if planned actions were fully effective (the risk management tool might produce such an output automatically). For example, Figure 7-5 shows, among other things, the result of avoiding threat 1.3, reducing threats 2.3 and 3.1, exploiting opportunity 2.1, and enhancing opportunity 1.2.
The risk champion also liaises with the project manager to raise new activities for inclusion in the project schedule to reflect agreed-upon actions. Risk actions must be treated with the same degree of importance and attention as other project activities, and including them in the project schedule ensures this because they will then be subject to monitoring and control along with other activities. It is also essential to make appropriate funds and resources available to carry out risk actions, and to include them in the project budget.
Finally, the project manager considers the need for change control if it is required after modifying the project plan; in some cases, contract changes may also be necessary.
Outputs
The main output from the Response Planning step is an updated Risk Register containing current information on selected responses, agreed-upon actions with Action Owners, post-response assessments, and secondary risks (if any). This information forms an important part of the risk reports that are prepared in the next step of the ATOM risk process.
The risk champion also generates analysis outputs showing the predicted effect of planned actions on levels of risk exposure, such as the post-response P-I Matrix.
Another important output from this step is a set of updates to the project schedule and budget to include agreed-upon actions. The project manager ensures that this is done with minimal delay.
One key factor in preparing outputs from Response Planning is timeliness. It is vital to communicate and implement response strategies and actions as quickly as possible after identifying them. This is because risk is dynamic and fast-changing, and any delay in the risk process might result in the outputs becoming outdated. The risk champion should therefore aim to complete Response Planning within less than a week after the Identification/Assessment workshop.
If it has been appropriate to escalate any risks, the project manager should notify the person who would be affected by such escalated risks and ensure that he or she takes ownership.
Summary
The Response Planning step ensures that appropriate actions are identified for each identified risk. Implementation of these actions minimizes threats to the project and maximizes opportunities, optimizing the chances of project success. To complete this step, the following activities should be undertaken:
• Arrange interviews with all risk owners
• Consider all risks with their respective risk owners, and determine an appropriate response strategy, plus actions to implement the selected strategy, with a nominated Action Owners for each action
• Confirm and refine proposed actions with Action Owners
• Update the Risk Register with response strategies and agreed-upon actions
• Update analysis outputs to reflect post-response expectations
• Modify the project schedule and budget to include agreed-upon actions.
When the Response Planning step of the First Risk Assessment is complete, the ATOM process continues with reporting current results and implementing agreed-upon actions, as detailed in the next two chapters.
