 Legal Issues and Ethics
Legal Issues and Ethics

Computer security is no different from any other subject in our society; as technological changes result in conflicts, laws are enacted to enable desired behaviors and prohibit undesired behaviors. The one substantial difference between this aspect of our society and others is that the speed of advancement in the information systems world, as driven by business, computer network connectivity, and the Internet, is much greater than in the legal system of compromise and lawmaking. In some cases, laws have been overly restrictive, limiting business options, such as in the area of importing and exporting encryption technology. In other cases, legislation has been slow in coming, and this fact has stymied business initiatives, such as in digital signatures. And in some areas, legislation has been both too fast and too slow, as in the case of privacy laws. One thing is certain: you will never satisfy everyone with a law, but it does delineate the rules of the game.
The cyber-law environment has not been fully defined by the courts. Laws have been enacted, but until they have been fully tested and explored by cases in court, the exact limits are somewhat unknown. This makes some aspects of interpretation more challenging, but the vast majority of the legal environment is known well enough that effective policies can be enacted to navigate this environment properly. Policies and procedures are tools you use to ensure understanding and compliance with laws and regulations affecting cyberspace.
 Cybercrime
Cybercrime
One of the many ways to examine cybercrime is to study how the computer is involved in the criminal act. Three types of computer crimes commonly occur: computer-assisted crime, computer-targeted crime, and computer-incidental crime. The differentiating factor is in how the computer is specifically involved from the criminal’s point of view. Just as crime is not a new phenomenon, neither is the use of computers, and cybercrime has a history of several decades.
![]()
There are three forms of computer involvement in criminal activity:
![]() The computer as a tool of a crime
The computer as a tool of a crime
![]() The computer as a victim of a crime
The computer as a victim of a crime
![]() The computer that is incidental to a crime
The computer that is incidental to a crime
What is new is how computers are involved in criminal activities. The days of simple teenage hacking activities from a bedroom have been replaced by organized crime–controlled botnets (groups of computers commandeered by a malicious hacker) and acts designed to attack specific targets. The legal system has been slow to react, and law enforcement has been hampered by its own challenges in responding to the new threats posed by high-tech crime.
What comes to mind when most people think about cybercrime is a computer that is targeted and attacked by an intruder. The criminal attempts to benefit from some form of unauthorized activity associated with a computer. In the 1980s and ‘90s, cybercrime was mainly virus and worm attacks, each exacting some form of damage, yet the gain for the criminal was usually negligible. Enter the 21st century, with new forms of malware, rootkits, and targeted attacks; criminals can now target individual users and their bank accounts. In the current environment, it is easy to predict where this form of attack will occur—if money is involved, a criminal will attempt to obtain a cut. A common method of criminal activity is computer-based fraud. Advertising on the Internet is big business, and hence the “new” crime of click fraud is now a concern. Click fraud involves a piece of malware that defrauds the advertising revenue counter engine through fraudulent user clicks.
eBay, the leader in the Internet auction space, and PayPal are frequent targets of fraud. Whether the fraud occurs by fraudulent listing, fraudulent bidding, or outright stealing of merchandise, the results are the same: a crime is committed. As users move toward online banking and stock trading, so moves the criminal element. Malware designed to install a keystroke logger and then watch for bank/brokerage logins is common on the Internet. Once the attacker finds the targets, they can begin looting accounts. The risk of getting caught and prosecuted is exceedingly low. Walk into a bank in the United States and rob it, and the odds are better than 95 percent that you will be doing time in federal prison after the FBI hunts you down and slaps the cuffs on your wrists. Do the same crime via a computer, and the odds are even better for the opposite outcome: less than 1 percent of these attackers are caught and prosecuted.
The low risk of being caught is one of the reasons that criminals are turning to computer crime. Just as computers have become easy for ordinary people to use, the trend continues for the criminal element. Today’s cybercriminals use computers as tools to steal intellectual property or other valuable data and then subsequently market these materials through underground online forums. Using the computer to physically isolate the criminal from the direct event of the crime has made the investigation and prosecution of these crimes much more challenging for authorities.

Tech Tip
FBI Priorities
In the post-9/11 environment, federal law enforcement priorities shifted toward terrorism. During the reassessment of national law enforcement priorities, cyber-related crimes increased in importance, moving to number three on the FBI priority list. Currently, the priorities for the FBI (per https://www.fbi.gov/about/mission) are as follows:
1. Protect the United States from terrorist attack.
2. Protect the United States against foreign intelligence operations and espionage.
3. Protect the United States against cyber-based attacks and high-technology crimes.
4. Combat public corruption at all levels.
5. Protect civil rights.
6. Combat transnational/national criminal organizations and enterprises.
7. Combat major white-collar crime.
8. Combat significant violent crime.
The last way computers are involved with criminal activities is through incidental involvement. Back in 1931, the U.S. government used accounting records and tax laws to convict Al Capone of tax evasion. Today, similar records are kept on computers. Computers are also used to traffic child pornography and engage in other illicit activities—these computers act more as storage devices than as actual tools to enable the crime. Because child pornography existed before computers made its distribution easier, the computer is actually incidental to the crime itself.
With the three forms of computer involvement in criminal activities, multiplied by the myriad of ways a criminal can use a computer to steal or defraud, added to the indirect connection mediated by the computer and the Internet, computer crime of the 21st century is a complex problem indeed. Technical issues are associated with all the protocols and architectures. A major legal issue is the education of the entire legal system as to the serious nature of computer crimes. All these factors are further complicated by the use of the Internet to separate the criminal and their victim geographically. Imagine this defense: “Your honor, as shown by my client’s electronic monitoring bracelet, he was in his apartment in California when this crime occurred. The victim claims that the money was removed from his local bank in New York City. Now, last time I checked, New York City was a long way from Los Angeles, so how could my client have robbed the bank?”
U.S. Law Enforcement Encryption Debate
A debate arose in the 1990s concerning encryption policy that led to laws concerning the export of encryption technology and government access to keys. A project called the Clipper chip was conceived to provide cryptography yet maintain the ability of the government to decrypt messages. But this all died with the rapid rise of e-commerce and the need for SSL.
The debate has been raised again with the widespread use of mobile devices, due to them having more computing power than most enterprises had in the ‘90s. And with this digital power comes end-to-end encryption of data and devices. Law enforcement can seize devices yet still be unable to get to the data. Due to need, law enforcement and the government have attempted to get laws passed to allow their access. Currently, the debate rages on in the U.S., but the UK and Australia have both passed legislation giving the government access to user data via either a backdoor, tools, or keys. This debate will not be resolved soon. For the best analysis of the technical implications, read “Keys Under the Doormats: Mandating Insecurity by Requiring Government Access to all Data and Communications” (https://dspace.mit.edu/bitstream/handle/1721.1/97690/MIT-CSAIL-TR-2015-026.pdf). This is a 2015 report from many of the best cryptographers in the world and is regarded as a seminal work in applied cryptography.
Common Internet Crime Schemes
To find crime, just follow the money. In the United States, the FBI and the National White Collar Crime Center (NW3C) have joined forces in developing the Internet Crime Complaint Center (IC3), an online clearinghouse that communicates issues associated with cybercrime. The IC3 website has several useful links, including the following:
![]() For industry alerts, go to https://www.ic3.gov/Home/IndustryAlerts.
For industry alerts, go to https://www.ic3.gov/Home/IndustryAlerts.
![]() For consumer alerts, go to https://www.ic3.gov/Home/ConsumerAlertsChoice.
For consumer alerts, go to https://www.ic3.gov/Home/ConsumerAlertsChoice.
![]() To file a complaint, go to https://www.ic3.gov/Home/ComplaintChoice.
To file a complaint, go to https://www.ic3.gov/Home/ComplaintChoice.
Sources of Laws
In the United States, three primary sources of laws and regulations affect our lives and govern our actions. A statutory law is passed by a legislative branch of government, be it the U.S. Congress or a local city council. Another source of laws and regulations is administrative bodies given power by other legislation. The power of government-sponsored agencies, such as the Environmental Protection Agency (EPA), the Federal Aviation Administration (FAA), the Federal Communication Commission (FCC), and others, lies in their ability to enforce behaviors through administrative rule making, or administrative law. The last source of law in the United States is common law, or case law, which is based on previous events or precedent. This source of law comes from the judicial branch of government: judges decide on the applicability of laws and regulations.
![]()
Three types of laws are commonly associated with cybercrime: statutory law, administrative law, and common law (also called case law).
All three sources have an involvement in computer security. Specific statutory laws, such as the Computer Fraud and Abuse Act (CFAA), govern behavior. The CFAA is designed to deal with cases of interstate computer fraud and cases of accessing national security information. The law has been amended several times to keep pace with technology. The primary charge from CFAA is typically one of accessing without authority, or exceeding authority on, a system involved with interstate commerce or national security. Administratively, the FCC and Federal Trade Commission (FTC) have made their presence felt in the Internet arena with respect to issues such as intellectual property theft and fraud. Common law cases are now working their ways through the judicial system, cementing the issues of computers and crimes into the system of precedents and constitutional basis of laws.
Computer Trespass
With the advent of global network connections and the rise of the Internet as a method of connecting computers between homes, businesses, and governments across the globe, a new type of criminal trespass can now be committed. Computer trespass is the unauthorized entry into a computer system via any means, including remote network connections. These crimes have introduced a new area of law that has both national and international consequences. For crimes that are committed within a country’s borders, national laws apply. For cross-border crimes, international laws and international treaties are the norm. Computer-based trespass can occur even if countries do not share a physical border.
Computer trespass is treated as a crime in many countries. National laws against computer trespass exist in many countries, including Canada, the United States, and the member states of the European Union (EU). These laws vary by country, but they all have similar provisions defining the unauthorized entry into and use of computer resources for criminal activities. Whether called computer mischief, as in Canada, or computer trespass, as in the United States, unauthorized entry and use of computer resources is treated as a crime with significant punishments. With the globalization of the computer network infrastructure, or the Internet, issues that cross national boundaries have arisen and will continue to grow in prominence. Some of these issues are dealt with through the application of national laws upon request of another government. In the future, an international treaty may pave the way for closer cooperation.
![]()
Computer trespass is a convenient catchall law that can be used to prosecute cybercriminals when evidence of other criminal behavior, such as online fraud, identity theft, and so forth, is too weak to achieve a conviction.
Convention on Cybercrime
The Convention on Cybercrime is the first international treaty on crimes committed via the Internet and other computer networks. The convention is the product of four years of work by the Council of Europe (CoE), but also by the United States, Canada, Japan, and other non-CoE countries. The convention has been ratified and came into force in July 2004, and by September 2006, 15 member nations had also ratified it. The United States ratified it in the summer of 2006, with it entering into force in the United States in January 2007.
One of the main objectives of the Convention, set out in the preamble, is “to pursue, as a matter of priority, a common criminal policy aimed at the protection of society against cybercrime, inter alia, by adopting appropriate legislation and fostering international cooperation.” This has become an important issue with the globalization of network communication. The ability to create a virus anywhere in the world and escape prosecution because of the lack of local laws has become a global concern.
The convention deals particularly with infringements of copyright, computer-related fraud, child pornography, and violations of network security. It also contains a series of powers and procedures covering, for instance, searches of computer networks and data interception. It has been supplemented by an additional protocol making any publication of racist and xenophobic propaganda via computer networks a criminal offense. This supplemental addition is in the process of separate ratification.
One of the challenges of enacting elements such as this convention is the varying legal and constitutional structures from country to country. Simple statements such as a ban on child pornography, although clearly desirable, can run into complicating issues, such as constitutional protections of free speech in the United States. Because of such issues, this well-intended joint agreement will have variations across the political boundaries of the world.
Significant U.S. Laws
The United States has been a leader in the development and use of computer technology. As such, it has a longer history associated with computers as well as with cybercrime. Because legal systems tend to be reactive and move slowly, this leadership position has translated into one from a legal perspective as well. The one advantage of this legal leadership position is the concept that once an item is identified and handled by the legal system in one jurisdiction, subsequent adoption in other jurisdictions is typically quicker.
Electronic Communications Privacy Act (ECPA)
The Electronic Communications Privacy Act (ECPA) of 1986 was passed by Congress and signed by President Reagan to address a myriad of legal privacy issues that resulted from the increasing use of computers and other technology specific to telecommunications. Sections of this law address e-mail, cellular communications, workplace privacy, and a host of other issues related to communicating electronically. Section I was designed to modify federal wiretap statutes to include electronic communications. Section II, known as the Stored Communications Act (SCA), was designed to establish criminal sanctions for unauthorized access to stored electronic records and communications. Section III covers pen registers and tap and trace issues. Tap and trace information is related to who is communicating with whom, and when. Pen register data is the conversation information.
A major provision of ECPA was the prohibition against an employer’s monitoring an employee’s computer usage, including e-mail, unless consent is obtained (for example, clicking Yes on a warning banner is considered consent). Other legal provisions protect electronic communications from wiretap and outside eavesdropping, as users are assumed to have a reasonable expectation of privacy and afforded protection under the Fourth Amendment to the Constitution. It is of note that these constitutional protections only apply to searches and seizures by U.S. government agencies and law enforcement (federal, state, or local jurisdiction), but do not apply to private individuals or employers.
![]()
Cross Check
Cybercrime and Privacy
Cybercrime and privacy are concepts that are frequently interconnected. Identity theft is one of the fastest-rising crimes. How does using your personal computer to access the Internet increase your risk in today’s world? Can you list a dozen specific risks you are personally exposed to? Privacy issues, being a significant topic in their own right, are covered in Chapter 25.
A common practice with respect to computer access today is the use of a warning banner. These banners are typically displayed whenever a network connection occurs and serve four main purposes. First, from a legal standpoint, they establish the level of expected privacy (usually none on a business system). Second, they serve notice to end users of the intent to conduct real-time monitoring from a business standpoint. Real-time monitoring can be conducted for security reasons, business reasons, or technical network performance reasons. Third, they obtain the user’s consent to monitoring. The key is that the banner tells users that their connection to the network signals their consent to monitoring. Consent can also be obtained to look at files and records. In the case of government systems, consent is needed to prevent direct application of the Fourth Amendment. And the last reason is that the warning banner can establish the system or network administrator’s common authority to consent to a law enforcement search.
Computer Fraud and Abuse Act (1986)
The Computer Fraud and Abuse Act (CFAA) of 1986—amended in 1994 and 1996, in 2001 by the USA PATRIOT Act, and in 2008 by the Identity Theft Enforcement and Restitution Act—serves as the current foundation for criminalizing unauthorized access to computer systems. CFAA makes it a crime to knowingly access a computer that is either considered a government computer or used in interstate commerce, or to use a computer in a crime that is interstate in nature, which in today’s Internet-connected age can be almost any machine. The act sets financial thresholds for defining a criminal act, which were lowered by the PATRIOT Act, but in light of today’s investigation costs, these are easily met. The act also makes it a crime to knowingly transmit a program, code, or command that results in damage. Trafficking in passwords or similar access information is also criminalized. This is a wide-sweeping act, but the challenge of proving a case still exists.
Controlling the Assault of Non-Solicited Pornography and Marketing Act of 2003 (CAN-SPAM)
The CAN-SPAM Act was an attempt by the U.S. government to regulate commercial e-mail by establishing national guidelines and giving the FTC enforcement powers. The objective of the legislation was to curb unsolicited commercial e-mail, or spam. The act has applicability to mobile phones as well. Heralded as action to curb the rise of spam, since its enactment, the act has a very poor record.

Tech Tip
Header Manipulation
Falsifying header information is a serious violation of the CAN-SPAM Act. This can be considered an indicator of criminal or malicious intent and can bring the attention of other law enforcement agencies besides the FTC.
CAN-SPAM allows unsolicited commercial e-mail as long as it adheres to three rules of compliance:
![]() Unsubscribe It must include an obvious opt-out provision to allow users to unsubscribe, with these requests being honored within ten days.
Unsubscribe It must include an obvious opt-out provision to allow users to unsubscribe, with these requests being honored within ten days.
![]() Content The content must be clear and not deceptive. Adult content must be clearly labeled, and subject lines must be clear and accurate.
Content The content must be clear and not deceptive. Adult content must be clearly labeled, and subject lines must be clear and accurate.
![]() Sending behavior The sender must not use harvested e-mail addresses, falsify headers, or use open relays.
Sending behavior The sender must not use harvested e-mail addresses, falsify headers, or use open relays.
CAN-SPAM makes specific exemptions for e-mail pertaining to religious messages, political messages, and national security messages. The law also blocks people who receive spam from suing spammers and restricts states from enacting and enforcing stronger antispam statutes. The law does permit ISPs to sue spammers, and this has been used by some major ISPs to pursue cases against large-scale spam operations. Major firms such as AOL have considered the law useful in their battle against spam. Regarded largely as ineffective, statistics have shown that very few prosecutions have been pursued by the FTC. The act permits both criminal charges against individuals and civil charges against entities involved in suspected spamming operations.
USA PATRIOT Act
The USA PATRIOT Act of 2001, passed in response to the September 11 terrorist attacks on the World Trade Center in New York City and the Pentagon building in Arlington, Virginia, substantially changed the levels of checks and balances in laws related to privacy in the United States. This law extends the tap and trace provisions of existing wiretap statutes to the Internet and mandates certain technological modifications at ISPs to facilitate electronic wiretaps on the Internet and for ISPs to cooperate with the government to aid monitoring. The act also permits the Justice Department to proceed with its rollout of the Carnivore program, an eavesdropping program for the Internet. Much controversy exists over Carnivore, but until it’s changed, the PATRIOT Act mandates that ISPs cooperate and facilitate monitoring. In recent actions, the name Carnivore has been retired, but the right of the government to eavesdrop and monitor communications continues to be a hot topic and one where actions continue. The PATRIOT Act also permits federal law enforcement personnel to investigate computer trespass (intrusions) and enacts civil penalties for trespassers.

Tech Tip
Computer Misuse
Two major laws, ECPA and CFAA (as amended), provide wide-sweeping tools for law enforcement to convict people who hack into computers or use them to steal information. Both laws have been strengthened and provide significant federal penalties. These laws are commonly used to convict criminals of computer misuse, even when other charges may have applied.
Gramm-Leach-Bliley Act (GLBA)
In November 1999, President Clinton signed the Gramm-Leach-Bliley Act (GLBA), a major piece of legislation affecting the financial industry that includes significant privacy provisions for individuals. The key privacy tenets enacted in GLBA include the establishment of an opt-out method for individuals to maintain some control over the use of the information provided in a business transaction with a member of the financial community. GLBA is enacted through a series of rules governed by state law, federal law, securities law, and federal rules. These rules cover a wider range of financial institutions—from banks and thrifts, to insurance companies, to securities dealers. Some internal information sharing is required under the Fair Credit Reporting Act (FCRA) between affiliated companies, but GLBA ended sharing to external third-party firms.
Sarbanes-Oxley Act (SOX)
In the wake of several high-profile corporate accounting/financial scandals in the United States, the federal government in 2002 passed sweeping legislation, the Sarbanes-Oxley Act (SOX), overhauling the financial accounting standards for publicly traded firms in the United States. These changes were comprehensive, touching most aspects of business in one way or another. With respect to information security, one of the most prominent changes was the provision of Section 404 controls, which specify that all processes associated with the financial reporting of a firm must be controlled and audited on a regular basis. Since the majority of firms use computerized systems, this places internal auditors into the IT shops, verifying that the systems have adequate controls to ensure the integrity and accuracy of financial reporting. These controls have resulted in controversy over the cost of maintaining them versus the risk of not using them.
Section 404 requires firms to establish a control-based framework designed to detect or prevent fraud that would result in misstatement of financials. In simple terms, these controls should detect insider activity that would defraud the firm. This has significant impacts on the internal security controls, because a system administrator with root-level access could perform many if not all tasks associated with fraud and would have the ability to alter logs and cover their tracks. Likewise, certain levels of power users of financial accounting programs would also have significant capability to alter records.
Privacy Laws
A wide range of privacy laws are relevant to computers. There are laws for healthcare (HIPAA) and education records (FERPA), as well as other types of records, including video rental records. These laws are described in detail in Chapter 25.
Payment Card Industry Data Security Standard (PCI DSS)
The payment card industry, including the powerhouses of MasterCard and Visa, through its PCI Security Standards Council, designed a private-sector initiative to protect payment card information between banks and merchants. The Payment Card Industry Data Security Standard (PCI DSS) is a set of contractual rules governing how credit card data is to be protected (see the Tech Tip sidebar “PCI DSS Objectives and Requirements”). The current version is 3.2, which was released in April 2016. A new release of PCI DSS version 4.0 is expected in mid-2021, but with the pandemic of 2020, this date may slip. This is a voluntary, private-sector initiative that is proscriptive in its security guidance. PCI DSS rules apply to any organization that processes, stores, or transmits cardholder data or provides services that control or could impact the security of cardholder data or the card holder data environment. Merchants and vendors can choose not to adopt these measures, but the standard has a steep price for noncompliance; the transaction fee for noncompliant vendors can be significantly higher, fines up to $500,000 can be levied, and in extreme cases the ability to process credit cards can be revoked.

Tech Tip
PCI DSS Objectives and Requirements
PCI DSS v3 includes six control objectives containing a total of 12 requirements:
1. Build and Maintain a Secure Network
Requirement 1 Install and maintain a firewall configuration to protect cardholder data.
Requirement 2 Do not use vendor-supplied defaults for system passwords and other security parameters.
2. Protect Cardholder Data
Requirement 3 Protect stored cardholder data.
Requirement 4 Encrypt transmission of cardholder data across open, public networks.
3. Maintain a Vulnerability Management Program
Requirement 5 Protect all systems against malware and regularly update antivirus software or programs.
Requirement 6 Develop and maintain secure systems and applications.
4. Implement Strong Access Control Measures
Requirement 7 Restrict access to cardholder data by business need-to-know.
Requirement 8 Identify and authenticate access to system components.
Requirement 9 Restrict physical access to cardholder data.
5. Regularly Monitor and Test Networks
Requirement 10 Track and monitor all access to network resources and cardholder data.
Requirement 11 Regularly test security systems and processes.
6. Maintain an Information Security Policy
Requirement 12 Maintain a policy that addresses information security for all personnel.
PCI DSS has two defined types of information: cardholder data and sensitive authentication data. The protection requirements established for these elements are detailed in Table 24.1.
Table 24.1 PCI DSS Data Retention Guidelines
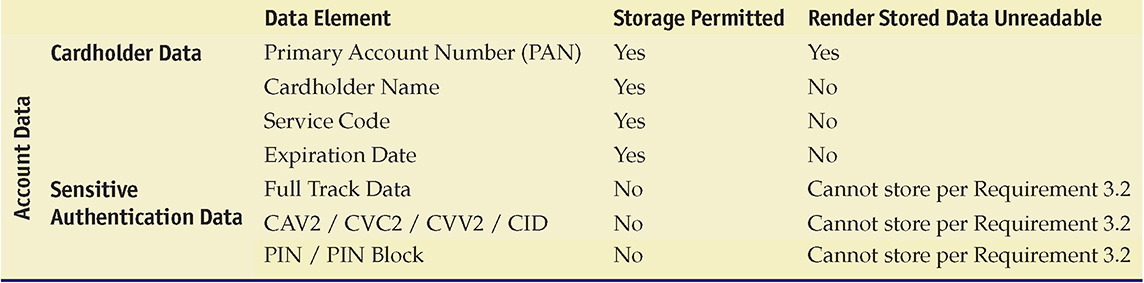
![]()
The Payment Card Industry Data Security Standard (PCI DSS) protects customer credit card information and is designed to reduce fraud. The standard has a steep penalty for noncompliance.
Import/Export Encryption Restrictions
Encryption technology has been controlled by governments for a variety of reasons. The level of control varies from outright banning to little or no regulation. The reasons behind the control vary as well, and control over import and export is a vital method of maintaining a level of control over encryption technology in general. The majority of the laws and restrictions are centered on the use of cryptography, which was until recently used mainly for military purposes. The advent of commercial transactions and network communications over public networks such as the Internet has expanded the use of cryptographic methods to include securing of network communications. As is the case in most rapidly changing technologies, the practice moves faster than law. Many countries still have laws that are outmoded in terms of e-commerce and the Internet. Over time, these laws will be changed to serve these new uses in a way consistent with each country’s needs.
U.S. Law
Export controls on commercial encryption products are administered by the Bureau of Industry and Security (BIS) in the U.S. Department of Commerce. The responsibility for export control and jurisdiction was transferred from the State Department to the Commerce Department in 1996 and updated on June 6, 2002. Rules governing exports of encryption are found in the Export Administration Regulations (EAR), 15 C.F.R. Parts 730–774. Sections 740.13, 740.17, and 742.15 are the principal references for the export of encryption items.

Tech Tip
Wassenaar Arrangement
The United States updated its encryption export regulations to provide treatment consistent with regulations adopted by the European Union (EU), easing export and re-export restrictions among the EU member states and Argentina, Australia, Canada, Croatia, Japan, New Zealand, Norway, Republic of Korea, Russia, South Africa, Switzerland, Turkey, Ukraine, and the United States. The member nations of the Wassenaar Arrangement agreed to remove key-length restrictions on encryption hardware and software that is subject to certain reasonable levels of encryption strength. This action effectively removed “mass-market” encryption products from the list of dual-use items controlled by the Wassenaar Arrangement. The latest update to the Wassenaar agreement came in December of 2019, with updates to the list of dual-use goods and technologies and munitions lists.
Violation of encryption export regulations is a serious matter and is not an issue to take lightly. Until recently, encryption protection was accorded the same level of attention as the export of weapons for war. With the rise of the Internet, widespread personal computing, and the need for secure connections for e-commerce, this position has relaxed somewhat.
The U.S. encryption export control policy continues to rest on three principles: review of encryption products prior to sale, streamlined post-export reporting, and license review of certain exports of strong encryption to foreign government end users. The current set of U.S. rules requires notification to the BIS for export in all cases, but the restrictions are significantly lessened for mass-market products, as defined by all of the following:
![]() They are generally available to the public by being sold, without restriction, from stock at retail selling points by any of these means:
They are generally available to the public by being sold, without restriction, from stock at retail selling points by any of these means:
![]() Over-the-counter transactions
Over-the-counter transactions
![]() Mail-order transactions
Mail-order transactions
![]() Electronic transactions
Electronic transactions
![]() Telephone call transactions
Telephone call transactions
![]() The cryptographic functionality cannot easily be changed by the user.
The cryptographic functionality cannot easily be changed by the user.
![]() They are designed for installation by the user without further substantial support by the supplier.
They are designed for installation by the user without further substantial support by the supplier.
![]() When necessary, details of the items are accessible and will be provided, upon request, to the appropriate authority in the exporter’s country in order to ascertain compliance with export regulations.
When necessary, details of the items are accessible and will be provided, upon request, to the appropriate authority in the exporter’s country in order to ascertain compliance with export regulations.
![]()
Mass-market commodities and software employing a key length greater than 64 bits for the symmetric algorithm must be reviewed in accordance with BIS regulations. Restrictions on exports by U.S. persons to terrorist-supporting states, as determined by the U.S. Department of State (currently Iran, Sudan, and Syria), their nationals, and other sanctioned entities are not changed by this rule.
As you can see, this is a very technical area, with significant rules and significant penalties for infractions. The best rule is that whenever you are faced with a situation involving the export of encryption-containing software, first consult an expert and get the appropriate permission or a statement that permission is not required. This is one case where it is better to be safe than sorry.
Non-U.S. Laws
Export control rules for encryption technologies fall under the Wassenaar Arrangement, an international arrangement on export controls for conventional arms and dual-use goods and technologies (see the Tech Tip sidebar “Wassenaar Arrangement”). The Wassenaar Arrangement was established to contribute to regional and international security and stability by promoting transparency and greater responsibility in transfers of conventional arms and dual-use goods and technologies, thus preventing destabilizing accumulations. Participating states, of which the United States is one of 41, will seek, through their own national policies and laws, to ensure that transfers of these items do not contribute to the development or enhancement of military capabilities that undermine these goals, and are not diverted to support such capabilities.

Tech Tip
Cryptographic Use Restrictions
In addition to the export controls on cryptography, significant laws prohibit the use and possession of cryptographic technology. In China, a license from the state is required for cryptographic use. In some other countries, including Russia, Pakistan, Venezuela, and Singapore, tight restrictions apply to cryptographic uses. France relinquished tight state control over the possession of the technology in 1999. One of the driving points behind France’s action is the fact that more and more of the Internet technologies have built-in cryptography.
Many nations have more restrictive policies than those agreed upon as part of the Wassenaar Arrangement. Australia, New Zealand, United States, France, and Russia go further than is required under Wassenaar and restrict general-purpose cryptographic software as dual-use goods through national laws. The Wassenaar Arrangement has had a significant impact on cryptography export controls, and there seems little doubt that some of the nations represented will seek to use the next round to move toward a more repressive cryptography export control regime based on their own national laws. There are ongoing campaigns to attempt to influence other members of the agreement toward less-restrictive rules or, in some cases, no rules. These lobbying efforts are based on e-commerce and privacy arguments.
Digital rights management, secure USB solutions, digital signatures, and Secure Sockets Layer–secured connections are examples of common behind-the-scenes use of cryptographic technologies. In 2007, the United Kingdom passed a new law mandating that when requested by UK authorities, either police or military, encryption keys must be provided to permit decryption of information associated with a terror or criminal investigation. Failure to deliver either the keys or decrypted data can result in an automatic prison sentence of two to five years. Although this seems reasonable, it has been argued that such actions will drive certain financial entities offshore, as the rule applies only to data housed in the United Kingdom. As for deterrence, the two-year sentence may be lighter than a conviction for trafficking in child pornography; hence, the law has not been as useful as was envisioned. Similar questions have been raised over recent laws in Australia which permit the government to force companies to decrypt data when requested. Although these questions are still open, the effect of them is beginning to become evident as LinkedIn is no longer available in Russia because the service owner chose not to comply with Russia’s local storage requirements.
Digital Signature Laws
Whether a ring and wax seal, a stamp, or a scrawl indicating a name, signatures have been used to affix a sign of one’s approval for centuries. As communications have moved into the digital realm, signatures need to evolve with the new medium, and hence digital signatures were invented. Using elements of cryptography to establish integrity and nonrepudiation, digital signature schemes can actually offer more functionality than their predecessors in the paper-based world.
U.S. Digital Signature Laws
On October 1, 2000, the Electronic Signatures in Global and National Commerce Act (commonly called the E-Sign law) went into effect in the United States. This law implements a simple principle: a signature, contract, or other record may not be denied legal effect, validity, or enforceability solely because it is in electronic form. Another source of law on digital signatures is the Uniform Electronic Transactions Act (UETA), which was developed by the National Conference of Commissioners on Uniform State Laws (NCCUSL) and has been adopted in all but four states—Georgia, Illinois, New York, and Washington—which have adopted a non-uniform version of UETA. The current situation, 20 years later, is that UETA and E-Sign are still not aligned. Both have an effect on the use of digital signatures, and while there are technical differences, vendors have been able to craft systems that comply with both sets of directives, making digital signatures legal and growing in popularity. The pandemic of 2020 probably did more to increase use of digital signatures than any legislation.
The E-Sign Act sets forth protections for consumers engaging in transactions with financial institutions. The E-Sign Act requires financial institutions to do the following:
![]() Obtain the consumer’s affirmative consent to the use of electronic records.
Obtain the consumer’s affirmative consent to the use of electronic records.
![]() Inform the consumer of any hardware or software requirements for accessing the electronic records.
Inform the consumer of any hardware or software requirements for accessing the electronic records.
![]() Provide a clear and conspicuous statement indicating
Provide a clear and conspicuous statement indicating
(i) the consumer has a right to have a record provided in paper or non-electronic form,
(ii) how the consumer can exercise that right, and
(iii) details on any fees associated with obtaining the record in paper or non-electronic form.
![]() Maintain electronic records in such a way that they are retrievable and accessible to all parties who are legally entitled to access them.
Maintain electronic records in such a way that they are retrievable and accessible to all parties who are legally entitled to access them.
Many states have adopted digital signature laws, the first being Utah in 1995. The Utah law, which has been used as a model by several other states, confirms the legal status of digital signatures as valid signatures, provides for use of state-licensed certification authorities, endorses the use of public key encryption technology, and authorizes online databases called repositories, where public keys would be available. The Utah act specifies a negligence standard regarding private encryption keys and places no limit on liability. Thus, if a criminal uses a consumer’s private key to commit fraud, the consumer is financially responsible for that fraud, unless the consumer can prove that they used reasonable care in safeguarding the private key. Consumers assume a duty of care when they adopt the use of digital signatures for their transactions, not unlike the care required for PINs on debit cards.
From a practical standpoint, the existence of the E-Sign law and UETA has enabled e-commerce transactions to proceed, and the resolution of the technical details via court actions will probably have little effect on consumers beyond the need to exercise reasonable care over their signature keys. For the most part, software will handle these issues for the typical user.
![]()
With the broad movement of people to isolate during the pandemic of 2020, digital signature adoption has become widespread for many transactions. Financial institutions, mortgages, auto lenders, and many other institutions have adopted the use of electronic signatures to replace direct contact with customers.
UN Digital Signature Laws
The United Nations has a mandate to further harmonize international trade. With this in mind, the UN General Assembly adopted in 1996 the United Nations Commission on International Trade Law (UNCITRAL) Model Law on Electronic Commerce (MLEC). To implement specific technical aspects of this model law, more work on electronic signatures was needed. The General Assembly then adopted in 2001 the UNCITRAL Model Law on Electronic Signatures (MLES). These model laws have become the basis for many national and international efforts in this area.
Canadian Digital Signature Laws
Canada was an early leader in the use of digital signatures. Singapore, Canada, and the U.S. state of Pennsylvania were the first governments to have digitally signed an interstate contract. This contract, digitally signed in 1998, concerned the establishment of a Global Learning Consortium between the three governments (source: Krypto Digest Vol. 1, No. 749, June 11, 1998). Canada went on to adopt a national model bill for electronic signatures to promote e-commerce. This bill, the Uniform Electronic Commerce Act (UECA), allows the use of electronic signatures in communications with the government. The law contains general provisions for the equivalence between traditional and electronic signatures (source: Bloomberg BNA ECLR, May 27, 1998, p. 700) and is modeled after the UNCITRAL Model Law on E-Commerce (source: Bloomberg BNA ECLR, September 13, 2000, p. 918). The UECA is similar to Bill C-54, the Personal Information Protection and Electronic Documents Act (PIPEDA), in authorizing governments to use electronic technology to deliver services and communicate with citizens. PIPEDA provides for electronic equivalents to paper-based documents and signatures, including using a stylus on a tablet touchscreen to write a signature by hand and capture it in electronic form.
Individual Canadian provinces have passed similar legislation defining digital signature provisions for e-commerce and government use. These laws are modeled after the UNCITRAL Model Law on E-Commerce to enable widespread use of e-commerce transactions. These laws have also modified the methods of interactions between the citizens and the government, enabling electronic communication in addition to previous forms.
European Laws
The European Commission adopted a Communication on Digital Signatures and Encryption titled “Ensuring Security and Trust in Electronic Communication—Towards a European Framework for Digital Signatures and Encryption.” This communication states that a common framework at the EU level is urgently needed to stimulate “the free circulation of digital signature related products and services within the Internal market” and “the development of new economic activities linked to electronic commerce” as well as “to facilitate the use of digital signatures across national borders.” Community legislation should address common legal requirements for certificate authorities, legal recognition of digital signatures, and international cooperation. This communication was debated, and a common position was presented to the member nations for incorporation into national laws.
On May 4, 2000, the European Parliament and Council approved the common position adopted by the council. In June 2000, the final version, the Electronic Commerce Directive (2000/31/EC), was adopted. The directive has been implemented by member states. To implement the articles contained in the directive, member states had to remove barriers, such as legal form requirements, to electronic contracting, leading to uniform digital signature laws across the EU. Electronic signatures are widely used throughout the EU. The use of electronic signatures is regulated by Regulation (EU) No 910/2014 of the European Parliament and of the Council of 23 July 2014 on electronic identification and trust services for electronic transactions in the internal markets of the EU.
Digital Rights Management
The ability to make flawless copies of digital media has led to another “new” legal issue. For years, the music and video industry has relied on technology to protect its rights with respect to intellectual property. It has been illegal for decades to copy information, such as music and videos, protected by copyright. Even with the law, people have for years made copies of music and videos to share, thus violating the law. Until the advent of digital copies (see Tech Tip sidebar “Digital Copies and Copyright”), this did not represent a significant economic impact in the eyes of the industry, as the copies were of lesser quality and people would pay for original quality in sufficient numbers to keep the economics of the industry healthy. As a result, legal action against piracy was typically limited to large-scale duplication and sale efforts, commonly performed overseas and subsequently shipped to the United States as counterfeit items.

Tech Tip
Digital Copies and Copyright
The ability of anyone with a PC to make a perfect copy of digital media led to industry fears that individual piracy actions could cause major economic issues in the recording industry. To protect the rights of the recording artists and the economic health of the industry as a whole, the music and video recording industry lobbied the U.S. Congress for protection, which was granted under the Digital Millennium Copyright Act (DMCA) on October 20, 1998.
The primary statute enacted in the United States to bring copyright legal concerns up to date with the digital world is the Digital Millennium Copyright Act (DMCA). The DMCA states its purpose as follows: “To amend title 17, United States Code, to implement the World Intellectual Property Organization Copyright Treaty and Performances and Phonograms Treaty, and for other purposes.” The majority of this law was well crafted, but one section has drawn considerable comment and criticism. A section of the law makes it illegal to develop, produce, and trade any device or mechanism designed to circumvent technological controls used in copy protection.

Tech Tip
DMCA Research Exemption Requirements
The DMCA has specific exemptions for research, provided four elements are satisfied:
![]() The person lawfully obtained the encrypted copy, phonorecord, performance, or display of the published work.
The person lawfully obtained the encrypted copy, phonorecord, performance, or display of the published work.
![]() Such act is necessary to conduct such encryption research.
Such act is necessary to conduct such encryption research.
![]() The person made a good faith effort to obtain authorization before the circumvention.
The person made a good faith effort to obtain authorization before the circumvention.
![]() Such act does not constitute infringement under this title or a violation of applicable law other than this section, including section 1030 of title 18 and those provisions of title 18 amended by the Computer Fraud and Abuse Act of 1986.
Such act does not constitute infringement under this title or a violation of applicable law other than this section, including section 1030 of title 18 and those provisions of title 18 amended by the Computer Fraud and Abuse Act of 1986.
Although, on the surface, this seems a reasonable requirement, the methods used in most cases are cryptographic in nature, and this provision had the ability to eliminate and/or severely limit research into encryption and the strengths and weaknesses of specific methods. A DMCA provision, section 1201(g), was included to provide for specific relief and allow exemptions for legitimate research (see the Tech Tip sidebar “DMCA Research Exemption Requirements”). With this section, the law garnered industry support from several organizations, such as the Software & Information Industry Association (SIIA), Recording Industry Association of America (RIAA), and Motion Picture Association of America (MPAA). Based on these inputs, the U.S. Copyright Office issued support for the DMCA in a required report to the U.S. Congress. This seemed to settle the issues until the RIAA threatened to sue an academic research team headed by Professor Edward Felten from Princeton University. The issue behind the suit was the potential publication of results demonstrating that several copy protection methods were flawed in their application. This research came in response to an industry-sponsored challenge to break the methods. After breaking the methods developed and published by the industry, Felten and his team prepared to publish their findings. The RIAA objected and threatened a suit under provisions of the DMCA. After several years of litigation and support of Felten by the Electronic Frontier Foundation (EFF), the case was eventually resolved in the academic team’s favor, although no case law to prevent further industry-led threats was developed.
One of the controversial issues associated with DMCA is the issue of takedown notices. Carriers such as YouTube are granted protection from content violation, provided they remove the content when requested with a takedown order. The publishing industry uses scanners and automated systems to issue takedown notices, and these sometimes go awry (see the sidebar on the Mars Rover mishap). The issue of fair use is one that is not delineated by bright-line regulations, making the system one that sides with the takedown requestor unless the content poster takes them to court.
Mars Rover Crashed by DMCA
NASA maintains a YouTube channel where it posts videos of space events, such as the landing of the rover Curiosity on the surface of Mars. The content was developed by NASA with U.S. taxpayer money, yet it was served a takedown notice by Scripps Howard News Service. The issue was remedied, but taxpayers lost early coverage and had to pay the legal bills to fight for their own content. This happens on a regular basis to the NASA channel, and although the law has provisions for prosecuting false takedowns, they are rarely used.
Exemptions are scattered throughout the DMCA, although many were created during various deliberations on the act and do not make sense when the act is viewed in whole. The effect of these exemptions upon people in the software and technology industry is not clear, and until restrained by case law, the DMCA gives large firms with deep legal pockets a potent weapon to use against parties who disclose flaws in encryption technologies used in various products. Actions have already been initiated against individuals and organizations who have reported security holes in products. This will be an active area of legal contention, as the real issues behind digital rights management have yet to be truly resolved.
 Ethics
Ethics
Ethics has been a subject of study by philosophers for centuries. It might be surprising to note that ethics associated with computer systems has a history dating back to the beginning of the computing age. The first examination of cybercrime occurred in the late 1960s, when the professional conduct of computer professionals was examined with respect to their activities in the workplace. If we consider ethical behavior to be consistent with that of existing social norms, it can be fairly easy to see what is considered right and wrong. But with the globalization of commerce, and the globalization of communications via the Internet, questions are raised on what is the appropriate social norm. Cultural issues can have wide-ranging effects on this, and although the idea of an appropriate code of conduct for the world is appealing, it is as yet an unachieved objective.
The issue of globalization has significant local effects. If a user wishes to express free speech via the Internet, is this protected behavior or criminal behavior? Different locales have different sets of laws to deal with items such as free speech, with some recognizing the right, and others prohibiting it. With the globalization of business, what are the appropriate controls for intellectual property when some regions support this right, while others do not even recognize intellectual property as something of value, but rather something owned by the collective of society? The challenge in today’s business environment is to establish and communicate a code of ethics so that everyone associated with an enterprise can understand the standards of expected performance.
A great source of background information on all things associated with computer security is the SANS Institute, which published a set of IT ethical guidelines (“IT Code of Ethics”) in April 2004 (see www.sans.org/security-resources/ethics.php).
![]()
Tech Tip
IT Code of Ethics
The SANS Institute’s “IT Code of Ethics,” Version 1.0,1 April 24, 2004:
I will strive to know myself and be honest about my capability.
![]() I will strive for technical excellence in the IT profession by maintaining and enhancing my own knowledge and skills. I acknowledge that there are many free resources available on the Internet and affordable books and that the lack of my employer’s training budget is not an excuse nor limits my ability to stay current in IT.
I will strive for technical excellence in the IT profession by maintaining and enhancing my own knowledge and skills. I acknowledge that there are many free resources available on the Internet and affordable books and that the lack of my employer’s training budget is not an excuse nor limits my ability to stay current in IT.
![]() When possible I will demonstrate my performance capability with my skills via projects, leadership, and/or accredited educational programs and will encourage others to do so as well.
When possible I will demonstrate my performance capability with my skills via projects, leadership, and/or accredited educational programs and will encourage others to do so as well.
![]() I will not hesitate to seek assistance or guidance when faced with a task beyond my abilities or experience. I will embrace other professionals’ advice and learn from their experiences and mistakes. I will treat this as an opportunity to learn new techniques and approaches. When the situation arises that my assistance is called upon, I will respond willingly to share my knowledge with others.
I will not hesitate to seek assistance or guidance when faced with a task beyond my abilities or experience. I will embrace other professionals’ advice and learn from their experiences and mistakes. I will treat this as an opportunity to learn new techniques and approaches. When the situation arises that my assistance is called upon, I will respond willingly to share my knowledge with others.
![]() I will strive to convey any knowledge (specialist or otherwise) that I have gained to others so everyone gains the benefit of each other’s knowledge.
I will strive to convey any knowledge (specialist or otherwise) that I have gained to others so everyone gains the benefit of each other’s knowledge.
![]() I will teach the willing and empower others with Industry Best Practices (IBP). I will offer my knowledge to show others how to become security professionals in their own right. I will strive to be perceived as and be an honest and trustworthy employee.
I will teach the willing and empower others with Industry Best Practices (IBP). I will offer my knowledge to show others how to become security professionals in their own right. I will strive to be perceived as and be an honest and trustworthy employee.
![]() I will not advance private interests at the expense of end users, colleagues, or my employer.
I will not advance private interests at the expense of end users, colleagues, or my employer.
![]() I will not abuse my power. I will use my technical knowledge, user rights, and permissions only to fulfill my responsibilities to my employer.
I will not abuse my power. I will use my technical knowledge, user rights, and permissions only to fulfill my responsibilities to my employer.
![]() I will avoid and be alert to any circumstances or actions that might lead to conflicts of interest or the perception of conflicts of interest. If such circumstance occurs, I will notify my employer or business partners.
I will avoid and be alert to any circumstances or actions that might lead to conflicts of interest or the perception of conflicts of interest. If such circumstance occurs, I will notify my employer or business partners.
![]() I will not steal property, time, or resources.
I will not steal property, time, or resources.
![]() I will reject bribery or kickbacks and will report such illegal activity.
I will reject bribery or kickbacks and will report such illegal activity.
![]() I will report on the illegal activities of myself and others without respect to the punishments involved. I will not tolerate those who lie, steal, or cheat as a means of success in IT.
I will report on the illegal activities of myself and others without respect to the punishments involved. I will not tolerate those who lie, steal, or cheat as a means of success in IT.
I will conduct my business in a manner that assures the IT profession is considered one of integrity and professionalism.
![]() I will not injure others, their property, reputation, or employment by false or malicious action.
I will not injure others, their property, reputation, or employment by false or malicious action.
![]() I will not use availability and access to information for personal gains through corporate espionage.
I will not use availability and access to information for personal gains through corporate espionage.
![]() I distinguish between advocacy and engineering. I will not present analysis and opinion as fact.
I distinguish between advocacy and engineering. I will not present analysis and opinion as fact.
![]() I will adhere to Industry Best Practices (IBP) for system design, rollout, hardening, and testing.
I will adhere to Industry Best Practices (IBP) for system design, rollout, hardening, and testing.
![]() I am obligated to report all system vulnerabilities that might result in significant damage.
I am obligated to report all system vulnerabilities that might result in significant damage.
![]() I respect intellectual property and will be careful to give credit for other’s work. I will never steal or misuse copyrighted, patented material, trade secrets, or any other intangible asset.
I respect intellectual property and will be careful to give credit for other’s work. I will never steal or misuse copyrighted, patented material, trade secrets, or any other intangible asset.
![]() I will accurately document my setup procedures and any modifications I have done to equipment. This will ensure that others will be informed of procedures and changes I’ve made.
I will accurately document my setup procedures and any modifications I have done to equipment. This will ensure that others will be informed of procedures and changes I’ve made.
I respect privacy and confidentiality.
![]() I respect the privacy of my co-workers’ information. I will not peruse or examine their information including data, files, records, or network traffic except as defined by the appointed roles, the organization’s acceptable use policy, as approved by Human Resources, and without the permission of the end user.
I respect the privacy of my co-workers’ information. I will not peruse or examine their information including data, files, records, or network traffic except as defined by the appointed roles, the organization’s acceptable use policy, as approved by Human Resources, and without the permission of the end user.
![]() I will obtain permission before probing systems on a network for vulnerabilities.
I will obtain permission before probing systems on a network for vulnerabilities.
![]() I respect the right to confidentiality with my employers, clients, and users except as dictated by applicable law. I respect human dignity.
I respect the right to confidentiality with my employers, clients, and users except as dictated by applicable law. I respect human dignity.
![]() I treasure and will defend equality, justice, and respect for others.
I treasure and will defend equality, justice, and respect for others.
![]() I will not participate in any form of discrimination, whether due to race, color, national origin, ancestry, sex, sexual orientation, gender/sexual identity, or expression, marital status, creed, religion, age, disability, veteran’s status, or political ideology.
I will not participate in any form of discrimination, whether due to race, color, national origin, ancestry, sex, sexual orientation, gender/sexual identity, or expression, marital status, creed, religion, age, disability, veteran’s status, or political ideology.
1© 2000–2015 The SANS™ Institute. Reprinted with permission.
Chapter 24 Review
 Chapter Summary
Chapter Summary
After reading this chapter and completing the exercises, you should understand the following regarding the basics of legal and ethical considerations associated with information security.
Explain the laws and rules concerning importing and exporting encryption software
![]() Import and export of high-strength cryptographic software are controlled in many countries, including the United States.
Import and export of high-strength cryptographic software are controlled in many countries, including the United States.
![]() Possession of encryption programs or encrypted data can be a crime in many countries.
Possession of encryption programs or encrypted data can be a crime in many countries.
![]() The Wassenaar Arrangement is an international agreement between countries concerning the import/export of cryptographic software and has enabled mass-marketed products to generally flow across borders.
The Wassenaar Arrangement is an international agreement between countries concerning the import/export of cryptographic software and has enabled mass-marketed products to generally flow across borders.
Identify the laws that govern computer access and trespass
![]() Gaining unauthorized access, by whatever means, including using someone else’s credentials, is computer trespass.
Gaining unauthorized access, by whatever means, including using someone else’s credentials, is computer trespass.
![]() Exceeding granted authority is also computer trespass.
Exceeding granted authority is also computer trespass.
![]() Many nations have versions of computer trespass or misuse statutes, although the terminology varies greatly among countries.
Many nations have versions of computer trespass or misuse statutes, although the terminology varies greatly among countries.
Identify the laws that govern encryption and digital rights management
![]() Encryption technology is used to protect digital rights management and prevent unauthorized use.
Encryption technology is used to protect digital rights management and prevent unauthorized use.
![]() Circumventing technological controls used to protect intellectual property is a violation of the DMCA.
Circumventing technological controls used to protect intellectual property is a violation of the DMCA.
![]() In some countries, carrying encrypted data can result in authorities demanding the keys or threatening prosecution for failure to disclose the keys.
In some countries, carrying encrypted data can result in authorities demanding the keys or threatening prosecution for failure to disclose the keys.
Describe the laws that govern digital signatures
![]() Digital signatures have the same legal status as written signatures.
Digital signatures have the same legal status as written signatures.
![]() Digital signatures use PINs or other “secrets” that require end-user safeguarding to be protected from fraud.
Digital signatures use PINs or other “secrets” that require end-user safeguarding to be protected from fraud.
Explore ethical issues associated with information security
![]() Ethics is the social-moral environment in which a person makes decisions.
Ethics is the social-moral environment in which a person makes decisions.
![]() Ethics can vary by socio-cultural factors and groups.
Ethics can vary by socio-cultural factors and groups.
 Key Terms
Key Terms
administrative law (911)
case law (911)
click fraud (909)
common law (911)
Computer Fraud and Abuse Act (CFAA) (914)
computer trespass (912)
Digital Millennium Copyright Act (DMCA) (922)
Electronic Communications Privacy Act (ECPA) (913)
Gramm-Leach-Bliley Act (GLBA) (915)
Payment Card Industry Data Security Standard (PCI DSS) (916)
Personal Information Protection and Electronic Documents Act (PIPEDA) (921)
Sarbanes-Oxley Act (SOX) (916)
Section 404 (916)
statutory law (911)
Stored Communications Act (SCA) (913)
Wassenaar Arrangement (918)
 Key Terms Quiz
Key Terms Quiz
Use terms from the Key Terms list to complete the sentences that follow. Don’t use the same term more than once. Not all terms will be used.
1. IT controls were mandated in public companies by _______________, part of the Sarbanes-Oxley Act.
2. The contractual set of rules governing credit card security is the _______________.
3. A catchall law to prosecute hackers is the statute on _______________.
4. The _______________ is the primary U.S. federal law on computer intrusion and misuse.
5. The power of government-sponsored agencies lies in _______________.
6. A(n) _______________ is passed by a legislative branch of government.
7. _______________ comes from the judicial branch of government.
 Multiple-Choice Quiz
Multiple-Choice Quiz
1. Your Social Security number and other associated facts kept by your bank are protected by what law against disclosure?
A. The Social Security Act of 1934
B. The USA PATRIOT Act of 2001
C. The Gramm-Leach-Bliley Act
D. HIPAA
2. Breaking into another computer system in the United States, even if you do not cause any damage, is regulated by what law?
A. State law, as the damage is minimal
B. Federal law under the Identity Theft and Assumption Deterrence Act
C. Federal law under the Electronic Communications Privacy Act (ECPA) of 1986
D. Federal law under the USA PATRIOT Act of 2001
3. Export of encryption programs is regulated by which entity?
A. U.S. State Department
B. U.S. Commerce Department
C. U.S. Department of Defense
D. National Security Agency
4. For the FBI to install and operate Carnivore (or subsequent tool) on an ISP’s network, what is required?
A. A court order specifying specific items being searched for
B. An official request from the FBI
C. An impact statement to assess recoverable costs to the ISP
D. A written request from an ISP to investigate a computer trespass incident
5. True or false? A sysadmin who is reading employee e-mail to look for evidence of someone stealing company passwords is protected by the company-owned equipment exemption on eavesdropping.
A. False, there is no “company-owned exemption.”
B. True, provided they have their manager’s approval.
C. True, provided they have senior management permission in writing.
D. True, if it is in their job description.
6. True or false? Writing viruses and releasing them across the Internet is a violation of law.
A. Always true. All countries have reciprocal agreements under international law.
B. Partially true. Depends on the laws in the country of origin.
C. False. Computer security laws do not cross international boundaries.
D. Partially true. Depends on the specific countries involved, both of the virus author and the recipient.
7. Publication of flaws in encryption used for copy protection is a potential violation of which of the following?
A. HIPAA
B. U.S. Commerce Department regulations
C. DMCA
D. National Security Agency regulations
8. Circumventing technological controls to prevent reverse engineering is a violation of which of the following?
A. HIPAA
B. DMCA
C. ECPA
D. All of the above
9. Logging in as your boss to fix your time records is:
A. OK, if you are accurately reporting your time
B. One of the obscure elements of DMCA
C. A violation of the Separation of Duties Law
D. A form of computer trespass
10. You are arrested as a result of your hacking activities, and investigators find you have been breaking password files and sharing them across the Internet. Which law have you violated?
A. CFAA
B. ECPA
C. DMCA
D. HIPAA
 Essay Quiz
Essay Quiz
1. You are being hired as the director of IT for a small firm that does retail trade business, and you will be the source of knowledge for all things IT, including security and legal regulations. Outline the legal elements you would want to have policy covering and include how you would disseminate this information.
2. You have just been hired as a system administrator for a small college. The college’s servers are used for database storage and a website that serves the college community. Describe the laws that will potentially impact your job with respect to computer security. What actions will you take to ensure compliance with laws and regulations?
