Tunneling Web Traffic Through a Proxy
Bill and Ted, our pairing partners from the previous section, need to do more than edit code. They also need to execute code and test it from an end-user’s perspective. High bandwidth solutions such as screen sharing simplfy this task, but a low bandwidth option exists if Bill and Ted are developing a web application. Bill can access a web server running on Ted’s machine as if it were running locally by using a Socket Secure (SOCKS) proxy. This kind of proxy routes web traffic through an SSH tunnel.
We’ll create a SOCKS proxy and configure it to use the tunnel we created earlier. Then we’ll reroute our web browser traffic through the proxy and gain access to a remote web server. This technique is particularly handy for web application development, but it’s also useful in situations where our remote partner has a VPN connection we are not privy to.
The following examples work best when the users bill and ted are represented by two distinct computers. If possible, run the steps for ted on your primary machine and the steps for bill on another machine. The ted user is already running the tunnel we created earlier. From bill’s terminal, run the following command, which creates a SOCKS proxy.
| | bill@localhost$ ssh -D 8080 -C -N -p 5900 |
| | > ec2-0-0-0-0.compute-1.amazonaws.com |
In conjunction with the tunnel, the SOCKS proxy creates an end-to-end channel for traffic of all kinds. The -D 8080 option instructs the ssh command to forward local traffic on port 8080 through the tunnel. The -C option requests the compression of all data, including images and large javascript files. The -p 5900 option instructs the command to use the port we opened on the EC2 Server.
As before, the -N option tells the command not to bring up a terminal session, and ec2-0-0-0-0.compute-1.amazonaws.com is our cloud server, which you must replace with the address of the server you created. Because we have not included a username with the connection string, the command will attempt to connect as bill because we are currently logged in as bill. However, this requires a bill user be present on the remote machine, which it will if the same machine is used for both sides of the pair. But you may want to replace bill with the tmux user you created in Chapter 2, Collaborating with Text Only. If so, replace the last argument in the ssh command with [email protected]. Then you can use the github-auth Gem to add bill’s private key to the tmux account.
Before bill can use the end-to-end channel, we must tell the software on his machine about the SOCKS proxy. For the Firefox browser, on all platforms, we configure this in the Advanced Network settings dialog. On Mac, open Firefox>Preferences>Advanced>Network. On Ubuntu, open Edit>Preferences>Advanced>Network. And on Windows, open Tools>Options>Advanced>Network. On any platform, select the “Settings...” button from the Connection section as shown in the following figure.
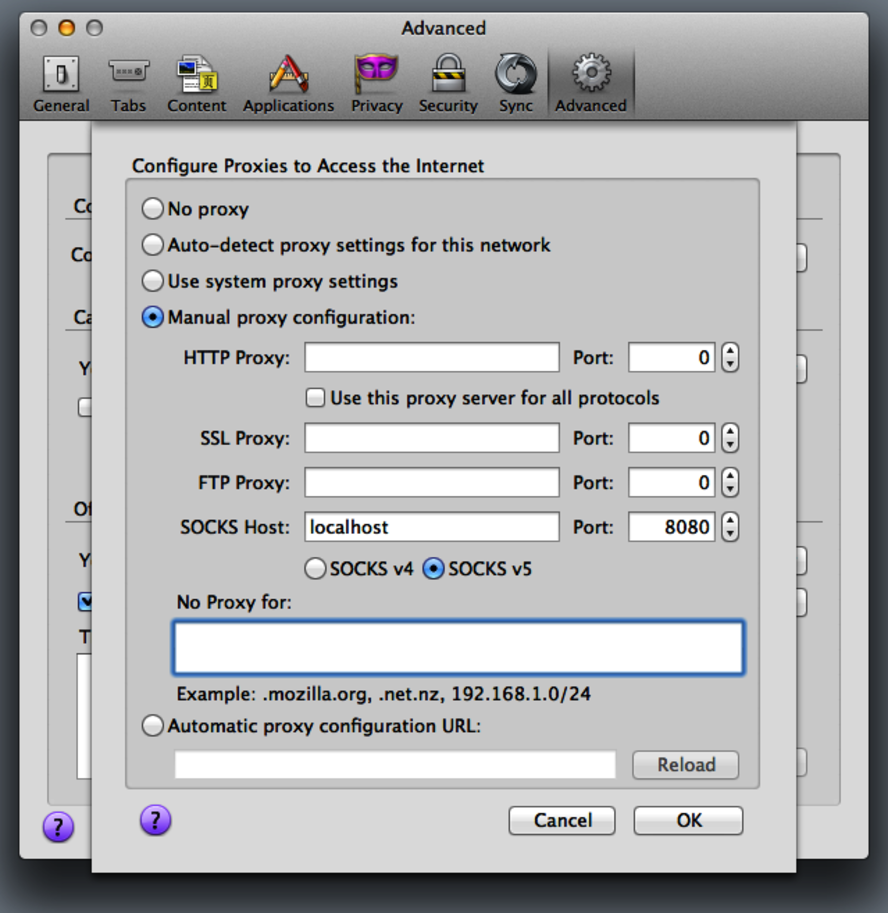
Figure 17. The Firefox proxy settings dialog
Select “Manual Proxy Configuration” and enter localhost for the SOCKS host and 8080 for the port. Then remove the localhost and 127.0.0.1 entires from the “No Proxy for:” field so it is empty.
For other browsers and platforms, this will be set in different ways. On Linux, most applications will obey the SOCKS_PROXY environment variable. On Mac, it can be set globally in the System Preferences>Network>Advanced>Proxies dialog.
Let’s test our proxy. In Firefox, browse to http://www.whatsmyip.org/ or any other website that will display the IP address we are accessing it from. We’ll find the address it displays is the address of the remote computer we are tunneled through (that is, ted’s computer). If you are running this example with a single computer and the IP addresses for bill and ted are the same, you can simulate the experiment by tunneling through the EC2 server only. Replace port 5900 in the command above with 22, and the username with ubuntu. You’ll find the website displays the address of the EC2 server instead of your own address.
Now we can use Firefox to get the same view of the web as our partner. If ted is connected to a VPN, bill will be able to access the same intranet sites. If ted is running a local web server, bill can browse to it with the same localhost address—even if it’s running on a different port.
Before we move on, kill the tunnel and the proxy by pressing Ctrl-c in the terminal window where each is running. In the next section, we’ll use a tool that creates its own tunnel.
