CHAPTER 15
Turning the Tables on Risk
The survey of the major operational risk categories covered in the preceding chapters is noteworthy for the breadth and depth of their impacts. The losses discussed alone add up to over $60 billion. Table 15‐1 provides a summary of the various incidents that occurred in each category. It also highlights the fact that in many cases, a high‐profile incident is often followed by one that is very similar in the same category. Very significant losses in credit trading by Genius Traders in 2007 were repeated in 2012; Rogue Traders in 2007; and in late 2011 both sat on the Delta One Desk. Multiple hedge fund managers conducting insider trading in popular company stocks were repeat offenders across multiple years; Madoff's Ponzi scheme was soon followed by Peregrine's; the 2010 Flash Crash was followed by the Knight Capital incident; issues in mortgage underwriting resulted in issues in mortgage foreclosing; and manipulation of credit securities' prices was followed by manipulation of interest rate quotes. Meanwhile, external threats are not going away: hurricanes, tsunamis, volcanic eruptions occur with regularity while cyber security incidents are reported every month.
Table 15‐1 Repeat Operational Risk Incidents
| Category | First Incident | Year | Loss (in US billions) | Repeat Incident | Year | Loss (in US billions) |
| Genius Trader | Credit trading | 2007 | Undetermined | Credit trading | 2012 | $6 |
| Rogue Trader | ETFs | 2007 | $7 | ETFs | 2011 | $2.3 |
| Price Manipulator | Credit securities | 2007 | $1.3 | LIBOR rates | 2009–2010 | Multiple |
| Rogue Computer | Futures algorithm | 2010 | Undetermined | Equities algorithm | 2012 | Undetermined |
| Ponzi Scheme | Hedge funds | 2008 | Multiple | Futures brokerage | 2011 | TBD |
| Insider Trading | Hedge funds | 2009 | Undetermined | Hedge funds | 2010 | Undetermined |
| Mortgage | Underwriting | 2006 | Multiple | Foreclosure | 2011 | Multiple |
| Natural Disaster | Japanese tsunami | 2011 | Multiple | Hurricane Sandy | 2012 | Multiple |
The general pattern is clear. What to do about it is the key question. In the first half of the book we discussed specific ways and tools to mitigate some of these risks. In the second half, we look at the broader frameworks and tools—cultural, risk, and regulatory—that need to be in place to address these risks in the broader sense. It just might be that financial institutions have more weapons at their disposal to address these risks than they are actually aware of. Trying to put them all together as part of a single coherent strategy is the goal.
Banks and financial institutions have a number of control functions focused on these type of issues: firm risk management, operational risk management, compliance, audit, finance, IT and operations control, legal, and embedded risk management. These functions are buffeted by internal risks on the one hand and external risks on the other as shown in Figure 15-1. (This is not intended to be comprehensive of all the risks faced by a bank.)
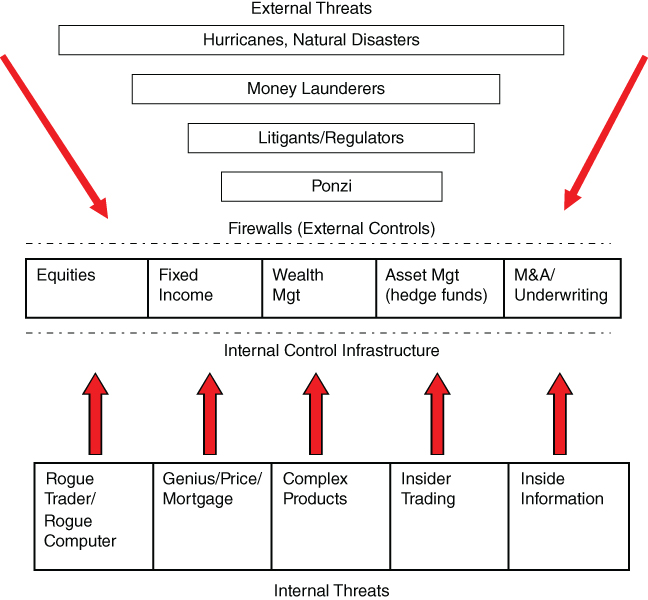
Figure 15-1: Threats—Internal and external
How effectively these groups coordinate their activities has a critical impact on risk management. Each department has its own mandate and area of focus—it's easy to miss the forest for the trees. Equities risk managers may be focused on threats from rogue trading and insider trading, while missing the threat tracked by compliance officers around Ponzi or money‐laundering schemes using equity trades to move foreign currency into US dollar accounts. Even within risk management, it is easy to get sucked into silo views of risk. At one investment bank, close to 60 different surveillance activities are being tracked. How are these different activities coordinated and the evidence correlated across these silos?
In the second half of this book, we will focus on overarching strategies and tools necessary to manage big risk more effectively going forward.
We start by looking at firm culture. This is a broad concept, but has a special significance for risk management. Several aspects of culture are worth exploring to identify that a firm has the cultural tools to manage its operational risks effectively:
Building Connections throughout the Firm's Culture
- Seeing the value of your contribution
- Removing silos
- Closing the gap from the top to the bottom
- A shared language
- An open society
The risk management function should not be a separate, cloistered group of cerebral individuals unconnected to the day‐to‐day reality of the firm that they serve:
Building a Risk Management Function That Is Connected and Interconnected
- Starts with business strategy
- Business is in the business of risk management
- Connecting each risk management function
- Upgrade operational risk
Risk management should adopt a common set of terms and ideas that are widely understood within the firm so that when we talk about risk leadership and subordinates are on the same page:
Building a Common Risk Language
- Common framework
- Risks and control dictionary
- Agreed top risks
Firms should adopt a common set of tools that are consistently adopted across lines of business and function for the analysis and mitigation of risks:
A Common Set of Tools
- Risk and control self‐assessment
- Incident analysis
- Scenario analysis
Firms should adopt new tools to better mitigate and prevent risks from taking place:
New Tools at the Leading Edge
- Putting people to better use
- Uses of big data
- Heuristics
- A better operational risk department
Firms should adopt artificial intelligence and cognitive‐based tools to pinpoint and prevent emerging threats and risks:
Cognitive Surveillance Tools
- Regulatory change management
Regulations and the Regulators
- Coordination
- Cooperation
- Beyond the letter
