Chapter 2
Security Basics: A Foundation
The Systems Security Certified Practitioner (SSCP) must understand the (ISC)2 SSCP Common Body of Knowledge (CBK) in order to pass the (ISC)2 SSCP exam. In professions such as plumbing, welding, computer programming, and commodities trading, there are fundamental concepts, techniques, and tenets of information that form a basic foundation for all other information and skills to follow. The professions of network security and cybersecurity are no different. Because it is the responsibility of the security practitioner to safeguard the resources and data of an organization, this individual must be able to identify risks, formulate strategies, and apply controls that ultimately reduce the likelihood of a threat exploiting a weakness or vulnerability.
When examining the (ISC)2 SSCP CBK, it's important to understand what is required to successfully pass the examination. As established by the (ISC)2 organization, the SSCP CBK contains knowledge a security practitioner with at least one year of IT security experience must have to adequately carry out the tasks assigned to them. What this means is that every concept contained in this book is explained to the depth required.
The Development of Security Techniques
Commercial use of digital computers in business has a history of only about 70 years, with less than half of that featuring any sort of external access or communication with other external entities such as on the Internet. Although data maintained on mainframe computers required security and protection during the 1960s and early 1970s, it would still be a while before hackers would have online access to corporate data and would take delight in attacking machines. During the 1950s and 1960s, various security techniques that originated and migrated through the years were combined with newer security techniques as requirements arose. This is the legacy of the security methodology and techniques we use today.
Following the birth and growth pattern of various industries—such as the automobile, railroad, communications, and even electricity distribution industries, to name a few—several growth concepts and such constants remained the same. One of the primary constants was, “We'll do it our way and let everyone else follow.” This led to no one in the industry deciding upon or agreeing on a similar method or standard. Parts were not interchangeable, devices did not work together, and communication between computer systems was impossible.
A second primary constant was of course the “for-profit” enterprise. Even when a firm or company came up with a great idea for solving a problem, the idea was often patented and a license made available at a cost to other firms in the industry. This led to other companies deriving a similar answer to the exact same problem.
During the path to understanding security in general and specifically computer and network security, you will see several instances of both of these constants in practice. This creates the confusion of everybody wanting to do it their way, which in turn results in several tools and devices that all appear to do the same thing. As with just about everything, in a free market economy, competition has driven this industry forward. We are constantly becoming aware of new and better devices, techniques, and methodologies of solving everyday problems. It's the challenge of the security practitioner to understand the problem and know what has come before to be able to understand the new solutions coming down the pike.
Understanding Security Terms and Concepts
The (ISC)2 organization requires candidates to have one year of IT security experience prior to receiving the Systems Security Certified Practitioner certification. Although some individuals may have prior educational courses in college or trade schools involving security, there will inevitably be gaps in experience or training. The CBK includes the areas of knowledge that a skilled Systems Security Certified Practitioner should know to perform the typical job tasks expected of them. By taking the practice exams and studying the subjects in this book, you will gain an understanding of the information required to pass the examination and perform as an SSCP.
We will use several learning techniques as we examine the SSCP (ISC)2 CBK. In the following sections, I will discuss looking at complex information, understanding its origin, and determining how the security practitioner may use this information on the job. Throughout the book, you will see “exam points,” which are specific concepts you should know for the exam. Real-world examples, notes, and other general information sections will assist you in remembering the perspective and application of various security concepts.
The Problem (Opportunity) and the Solution
Although most folks go through life seeking solutions to problems, some folks like to refer to these as “opportunities.” For instance, when employees bring their cell phones to work and connect with the company network, it can definitely present a possible problem for the security practitioner. The flip side is that there is a tremendous opportunity to increase productivity and therefore profitability for the firm by allowing these employees rapid access to data and applications. Therefore, both a problem and an opportunity exist in search of a solution.
While learning about the terms (and their definitions) and concepts of security in the SSCP Common Body of Knowledge, picture in your mind the problem or opportunity and the solution. If you can understand this relationship, you will be able to use these techniques in everyday practice and of course ultimately be able to pass the SSCP exam. Throughout this book, strive to understand the concepts behind the solutions to various problems or opportunities. If you thoroughly understand the concepts, the exam answers will come very easy for you.
It is not important that you be a great artist. The drawing on your notepad to assist you in learning the relationship between all of the items in this process might look something like the drawing in Figure 2.1.

Figure 2.1 This figure illustrates a notepad drawing of a remote user logon
The takeaway from this is that we identified an opportunity, such as giving an employee the ability to log on remotely. We now see the relationship between the VPN concentrator and other devices and the roles they play during this process. We have illustrated where a VPN tunnel exists, and we have seen that remote users might be authenticated by a RADIUS server.
The reason for this scenario is to understand the roles of each item, whether software or hardware, and to draw out or illustrate to the best of our ability the process to assist us in understanding the concepts.
Evolution of Items
Technology continues to evolve, and there always seems to be something new and shiny just around the corner that works better, faster, or cheaper than what we are already using. The unfortunate consequence is that all of this new technology begins stacking up. To anyone just coming into the field, it is sometimes difficult to understand the concepts behind all of these names and acronyms, several of which appear to do the same thing, and discern why they all exist. As mentioned, sometimes it is advantageous to group similar items in a group to which they relate. This may assist in understanding the evolution of the item or concept, how much weight to place on learning about it, and ultimately where we would use it in everyday security protection as a security practitioner.
Group Similar Items into Concept Families
Another memorization technique is to group similar items or terms into a “concept family.” For instance, the following list illustrates a family of terms and technology around the single sign-on (SSO) concept:
- Kerberos
- Kerberos authentication server
- Kerberos ticket=granting server
- Tickets
- Ticket-granting ticket
- Federated access
- Sesame
- KryptoKnight
- Centralized authentication
- Decentralized authentication
Should you see any of these terms either in a question or as part of an answer on any exam, you might quickly conclude that the general subject is related to single sign-on or at least user authentication. Of course, seeing one of these terms as an option for a totally unrelated question would mean that the option is most likely a distractor.
Once you create a list of a family or group of similar concepts, I suggest you write at least one or two sentences as a description of each item. Writing the description out in your own words is a significant memorization technique and far surpasses just reading it in a glossary.
Same Item, Different Name
It's not unusual in some industries for the same item to be named differently. In some cases, this might be due to different companies marketing and branding the same item. For instance, a network device called a switch might also be referred to as an L2 switch, a smart switch, an intelligent switch, a NexGen switch, a VLAN switch, or an intelligent hub. You might assume that all of these basically provide a switch function, and the name might be created by the manufacturer and its branding department.
You might also come across devices that provide basically the same functionality but are generically called something different. For example, in the early years of networking there was a device called a passive hub. This simple device featured one Ethernet jack in and usually four Ethernet jacks out, with no amplification of the signals. The device evolved into powered or amplified hubs powered by a wall-wart transformer and then finally switches as we know them today. It is almost impossible to walk into a store and purchase a simple hub.
How Do We Agree to Agree?
One of the most difficult aspects of any industry is deciding upon a standard. For instance, most laptop computers feature an SVGA 15-pin D-shaped connector for video out to a projector or monitor (Figure 2.2). In years past, the same connector was located on the rear panel of a desktop computer and was used to connect a video monitor, a keyboard, a mouse, and a scanner, and for serial communications such as a RS-232 serial port, it was used for an external modem.

Figure 2.2 A typical 15-pin D-shaped connector
Who decided upon this design and how was it decided that everybody would do it? Industry standards evolve through a number of different means and generally refer to a method or design that is accepted by a majority, or at least a significant group, within the industry. For various reasons, which might include technical disagreement, proprietary patents and licensing fees, or just political reasons, not everyone within an industry accepts the standardization effort.
Within the information technology industry, as with many other industries, there are two types of standards:
- Mechanical Standards Mechanical standards feature specific specifications for the mechanical design, materials, signal paths, waveforms, communication methods, and hardware design.
- Standard of Practice, or Procedural Standards Procedural standards take the form of recommendations or regulatory requirements. Recommendations generally originate with a committee, consortium, or industry organization and take the form of recommended best practices. Regulatory standards, on the other hand, are generally enforced by a governmental regulatory body or a self-regulatory industry organization.
Industry standards or best practices may come from any of the following sources:
- Proprietary This type of manufacturing design or practice is not an industry standard but generally fulfills the needs and requirements within a specific company. For instance, in the early days of PCs, IBM created the Industry Standard Architecture (ISA) bus standard for the personal computers it was creating at the time. Of course these computers became very popular, and many other manufacturers wished to build circuit boards and computers that were compatible with this bus. Several years later, in an effort to be compatible, a group of industry manufacturers known then as the Gang of Nine created an enhanced version of the ISA bus and named it Extended Industry Standard Architecture (EISA) to avoid infringement. This is typical of how a large industry player's proprietary design evolves into an industry standard through slight modifications and renaming.
- Standards Organization Various organizations are chartered with the ability of establishing industry standards or industry recommendations. These may take the form of committee-based or working group organizations that create recommendations, trade groups that create standards to be used in their specific trade, and consortiums that form to create everything from best-practice recommendations to industry regulations.
- Government Various governments around the world create laws, regulations, and statutes that govern the design, manufacture, import, use, or sale of various products and technologies within their control.
- Regulatory Agency An agency may be either created by a government entity or agreed upon by a specific industry group. Generally, an agency may be charged with not only creating a specification but also in enforcing its use.
The security practitioner should be aware of a number of different organizations that are involved in generating standards and specification recommendations throughout the industry. Some of these organizations include the following:
- National Institute of Standards and Technology (NIST) NIST is a non-regulatory agency of the United States Department of Commerce. NIST offers an incredible variety of standards, best practices, research results, and programs for not only the IT industry but everything from weather reporting to manufacturing. The NIST website is at
www.nist.gov. - Internet Engineering Task Force (IETF) IETF develops and promotes Internet standards that may be voluntarily adopted throughout the industry. At one time supported by the federal government, IETF now performs a standards development function under the Internet Society. Standards are developed through various committees and the participation of a large number of interested volunteers. The IETF website is at
www.ietf.org. - Institute of Electrical and Electronics Engineers (IEEE) IEEE (aka I Triple E) is a professional organization for the advancement of computer engineering and computer science, among other aspects of electronics and communications. As one of the leading standards organizations, it is responsible for the 802 group of standards, which includes the IEEE 802.3 Ethernet standard and the IEEE 802.11 wireless networking standard. Its website is located at
www.ieee.org. - American National Standards Institute (ANSI) ANSI is a nonprofit organization that oversees the development of standards that are approved by consensus and are applied on a voluntary basis across a given industry. ANSI manages and maintains the ASCII standard. You can find out more at
www.ansi.org. - World Wide Web Consortium (W3C) W3C is a standards organization in which members, staff, and the public collaborate to develop web standards. The web technologies include the recommended implementation of Cascading Style Sheets and XHTML, among many other recommendations. The W3C website is located at
www.w3.org. - International Organization for Standardization (ISO) ISO is a true standards organization. It tests various products and provides its seal of approval once they pass rigorous tests. The organization administers over 13,000 standards across many industries. The website is at
www.iso.org. - The Unicode Consortium The Unicode Consortium is a standards organization that manages and maintains the Unicode standard. This standard provides a number for every possible character in every possible language used on the Internet. This allows the development of international versions of websites. Go to
www.unicode.orgfor more information about the work of the Unicode Consortium. - Telecommunications Industry Association (TIA) TIA is accredited by the American National Standards Institute (ANSI) to develop voluntary, consensus-based industry standards for a wide variety of information and communication technologies (ICT) products and currently represents nearly 400 companies. Its website is at
www.tiaonline.org. - SANS Institute The SANS Institute is a private company formed in 1989 that provides training to the cyber security industry. SANS is a trade name, short for SysAdmin, Audit, Networking, and Security. It is also known for industry reports and policy templates. The website is at
www.sans.org.
Security Foundation Concepts
From the beginning of the computer age and throughout the evolution of all the products and concepts we currently use in information security, the fundamental underlying principles and objectives have not changed. These basic principles are referred to as the CIA (or AIC) security triad (Figure 2.3), which consists of confidentiality, integrity, and availability.

Figure 2.3 The CIA triad
CIA Triad
Although most textbooks and literature on computer security refer to this as the CIA triad, the order of these letters does not matter; it could also be referred to as the AIC triad. These three concepts, confidentiality, integrity, and availability, form the basis for security objectives that are the essence of security for all information systems. Security policies, controls, safeguards, countermeasures, and even threats, vulnerabilities, and security processes can and should be considered within the framework of the security objectives.
The security practitioner is constantly weighing every security requirement against one of these three objectives. Generally, the problem or opportunity facing the security practitioner impacts confidentiality, integrity, or availability. Information stored in the Department of Defense computer systems requires confidentiality, whereas credit card transactions in business require information integrity, and of course an e-commerce website owner is concerned with availability. The following represents each leg of the triad:
- Confidentiality The objective of confidentiality applies to both data and system information and is sometimes referred to as the secrecy object. To ensure confidentiality, information must be protected to eliminate the loss or disclosure of the information. The actions taken to protect information from disclosure include numerous controls put in place to create defense in depth. The primary action to encrypt data is to select and use a well-known and unbroken encryption algorithm. The encryption algorithm might be used to protect data when in transit and while it is being stored. Other techniques to ensure confidentiality include hiding data or making it nonaccessible; wiping or erasing data, such as if a cell phone is stolen; and using extremely strong identification and authentication techniques.
- Availability Availability ensures accessibility to all hardware, software applications, and data throughout the system. Availability concepts include hardware and data physical availability, system hardware redundancy, connection and transmission availability, and restoration of services, systems, and data as required. Availability is also ensured through the use of vulnerability mitigation techniques such as the reduction of denial-of-service attacks, scanning systems for malware, and the use of hardware concepts such as automated backups or raid drives.
- Integrity Integrity ensures that the system resources are protected from unauthorized, unanticipated, or unintentional modifications. This objective can apply to both the data and the hardware system. Data integrity is the fundamental concept that data has not been altered by any manner while in storage, during processing, or while in transit unless authorized. Integrity can also refer to system integrity. This is the integrity or quality the system has to perform its intended function in an unimpaired manner free from unauthorized manipulation, design flaws, or intentional or unintentional actions.
Primary Security Categories
All the differing roles within the world of security, whether police officer, firefighter, home security alarm company, IT security professional, or a disaster recovery federal agency, are vital to our businesses and our families, neighbors, and community. Each of these individuals or organizations performs a central role in supporting a primary goal of security.
The activities of each one of these individuals or organizations generally fall into three security categories:
- Prevention These are the actions taken or the products purchased and installed in an effort to reduce the likelihood that something bad may happen. In the family home, this might be accomplished by installing a strong front door with a deadlock. Prevention represents the efforts taken to reduce the likelihood of fire, theft, physical harm, intrusion, or other potential undesired or bad occurrences. Although owning a fire extinguisher may reduce the spread of the fire once it has begun, the removal of items such as waste paper or flammable liquids represents the acts of fire prevention.
As a security professional, your responsibility is to design and deploy mechanisms that stand in the way of a potential intruder or other bad actor wishing to do harm to your data or resources. This could be as simple as placing locks on server cabinets, creating a strong identification and authentication system, providing user training, and utilizing strong security rules on firewalls and routers.
- Detection In a home, a typical detection method might be a burglar alarm system, swimming pool alarm, baby monitor, or smoke alarm. In our automobiles, we might notice a check engine light or a low oil indicator. In some instances, we might hear something such as a potential intruder in the backyard, strange noises in the house, or the incessant barking of a dog. Each of these might indicate that something unusual is happening.
As a security professional, you are expected to deploy various methods of detecting unauthorized access to or unauthorized removal of data or resources. You might perform this action by placing detection mechanisms such as an intrusion detection system, automated log monitoring that generates various alerts, or continuous monitoring that utilizes a security operations center to ensure that data and assets are protected 24/7.
- Recovery These are the actions any of us must take after an unwanted occurrence. If you are in an automobile accident, for example, the medical recovery of the individuals involved and physical recovery such as repair or replacement of the assets might both need to be addressed. Or a broken window may need to be replaced after unauthorized access by a burglar.
As a security professional, you are expected to be ready to implement various plans and programs should systems be damaged, databases corrupted, or secrets such as passwords divulged. These plan should be well conceived, practiced, and ready to put into place should any emergency occur.
Access Control
A responsibility of security professionals is to protect the data and the resources of the organization. The first step in protection is to properly identify and authenticate those individuals or users desiring access to the physical premises, the network, and ultimately the corporate data stored on the network. A series of identity checks and verification steps will be undertaken prior to granting access. The steps include identification, authentication, authorization, and accounting.
Identification
Identification is the first step of the access process. Every user, application, or system begins the access process by providing some form of identification. This identification claim will be compared to data on file, and if it matches, the process will continue.
Each of us is identified by two names, our first name and last name. We may also be identified as being a member of a group, such as an employee of XYZ Corporation, a Boy Scout, a Texan, an American, and, sooner or later, an inhabitant of the planet Earth. As you can see, as the group gets larger, the less integrity a logon system can provide to denote a specific user signing on. This concept might be referred to as granularity of identification.
Authentication
Authentication is the second step of the access process. Where any user or device can make an identification claim, authentication is a request for a second type of identification called a factor. Ideally, this factor should be something unique to the user or the system, providing strong evidence that this individual or system is actually who they claim to be. Numerous authentication mechanisms may be applied in sequence to enhance the reliability of the authentication process.
Authorization
Authorization is the third step of the access process. Upon satisfactory authentication, the user is assigned rights and privileges based upon a profile they have in storage. Various limits may be placed on access to resources or data; the limits are included in an access list, which is based upon the user identity. Other limits may include access to resources or data based upon a label issued to the user who matches the highest label of the resource or data.
Accounting
Accounting refers to tracing and recording the use of network assets and resources by users or intruders. The process of accounting may be performed to achieve a specific purpose, such as monitoring trends or capacity, allocating expenses and costs for the use of resources, and monitoring proper usage of resources. The accounting process as it relates to IT security is involved with monitoring and recording users' access to resources, proper authorization levels of users, changes made to resources (such as changes to a database), and general actions and activities such as creating or deleting files.
Auditing is the act of reviewing or monitoring the data obtained during the accounting process. This may involve reviewing log files or forensic information. Real-time monitoring, also called continuous monitoring, not only creates log files but also can create immediate alerts, emails, and console warning screens for operators and administrators.
Nonrepudiation
Nonrepudiation is a process whereby a user may be directly identified as the sender of a message. Through the use of nonrepudiation methods, this person may not deny an action that they have taken. For example, Jack wants to send a message to Jill. Jill requests that Jack digitally sign the message, thus providing irrefutable proof that he was the originator of the message. On the other hand, Jack may request that Jill also cannot deny receiving the message. This is achieved through strong identification and authentication of Jill and the use of system logs that provide proof that Jill was the user that actually received the message as sent. In this case, nonrepudiation can be achieved by both parties. This is an application of the integrity rule.
Risk
Risk is a chance of damage or loss based upon the exposure to a potential hazard or threat. This sounds like a simple concept. Do I increase risk by leaving my front door unlocked? Do I decrease risk by placing chains on my front door? The responsibilities of a security practitioner are to be aware that there is constant risk. This individual may be placed in a role of identifying risks and selecting various tools and methods that might be used to reduce it. Reducing risk is referred to as mitigating risk. By locking the door, I reduce the risk, and by placing chains around the door, I mitigate the risk even further.
Various components of risk exist:
- Threat This is a general term used to describe any incident or action that, if carried out, could cause harm or loss of data or an asset. For example, there is a threat of fire in the server room.
- Vulnerabilities These are the weaknesses within a network, host application or database that may be penetrated or exploited by an attacker.
- Controls These items are represented by safeguards, countermeasures, policies, and procedures that may be used to mitigate risk. Controls are grouped into three categories: physical, logical, and administrative.
Prudent Man, Due Diligence, and Due Care
These concepts may together or separately form the basis of actions and provide a measurement for the security professional to ensure that various security controls meet the highest standards possible. The goal of each of these concepts is to reduce risk to a manageable level.
- Prudent Man The prudent man concept refers to actions that may be reasonably taken (or are obvious) to safeguard corporate assets and data. This concept may also refer to, as a comparison, the security safeguards similar organizations within the same industry are taking to protect their corporate assets and data. For example, if all banks use a vault to protect the money kept on premises, is it obvious and prudent that your bank requires a vault also?
- Due Diligence Due diligence is verifying that a control or process is performing as intended. This concept may also be referred to as assuredness. For instance, placing an IDS into a network to perform traffic monitoring would be exercising due care, and monitoring the IDS to ensure that it is operating correctly is due diligence.
- Due care Due care refers to taking actions that are prudent and reasonable to protect the assets of the organization, such as installing controls. For instance, exercising due care would be installing an IPS in an effort to protect a network. In summary, due care is taking adequate precautions by installing effective controls to reduce or mitigate risk, while due diligence is performing activities to ensure that the control is functioning to established parameters.
User Security Management
The security professional's responsibility is to secure and protect the organization's assets, which fall into two general categories:
- Resources Physical resources include the general assets of the company, such as computer systems, network hardware, printers, wireless transmission equipment, telephone equipment, and cabling systems. Virtual resources include assets that have been created or are running on hardware devices. This includes virtual servers, virtual networks, cloud-based technology, and the software applications that run the business.
- Data Data refers to the content placed on the company network and storage devices. The three states of data are referred to as data at rest, data in process, and data in transit. While a company may own a database, the software database itself is referred to as a relational database management system (RDBMS), and the actual information contained in each row and cell of every table is the content data that requires protection. Data in transit is encapsulated with a header block that contains metadata such as the destination, the length of the data packet, and the various protocols used, among other information. The actual data content in transit is referred to as the payload. Data in process is content data that is either being changed or being currently used by a software application. A common security practice is to maintain the most recent version of the content data and work with a copy of the data. If anything goes wrong during the processing of the change transaction, the transaction itself can be “rolled back” to the last known good copy of the data.
Company assets need to be protected and secured against a number of risks. Primary threats to the assets of the company are people. People may be referred to as authorized users, intruders, or attackers. Intruders and attackers intend to do harm or steal from the company. Authorized users may do harm, either by an innocent mistake or intentionally as a disgruntled employee.
Various security controls and user management techniques may be employed by the security professional. These are discussed in the sections that follow.
Least Privilege
The principle of least privilege establishes that users, systems, and applications should have only the minimal level of access that is absolutely necessary for them to perform the duties required of them.
AAA
The three As of security, also known as AAA, are authentication, authorization, and accounting (Figure 2.4). These three processes work together to provide the assurance that access is granted only to authorized users. The implementation can be provided by independent means, such as referring to access control lists (ACLs), using directories such as LDAP or Active Directory, or through a completely unified system that provides all three AAA services.
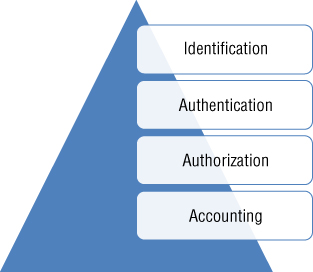
Figure 2.4 An access process illustrating the three AAAs, known as authentication, authorization, and accounting
Mandatory Vacation
Requiring mandatory vacations is a security technique that allows for the review of employee activities. Most corporate mandatory vacation policies require an individual take at least one vacation each year for a minimum duration of five days. During the employee's absence, various audits may be performed to discover any abnormalities in the employee's work.
Separation of Duties
A separation of duties policy ensures that no one person has too much power or control. Duties and responsibilities within an organization should be divided among several individuals, each with assigned responsibilities to complete the task. For instance, authorization and approval of purchase orders, check requests, and payments should be assigned to different individuals or departments within an organization. This eliminates the capability of one individual to commit fraudulent acts against the organization.
M of N Requirement
An M of N process requires a certain number of individuals to agree prior to action being taken. M represents the minimum number of individuals that must agree on a course of action. N represents the total number individuals involved. For instance, a corporate approval policy may require that 3 (M) executives are required to agree on a course of action out of a total group of 10 (N) executives. It is not unusual for an organization to require at least two signatures on a bank check. The policy might also state that four individuals may be authorized to sign checks. This redundancy can act as a safeguard in the event that one of the check signers is on vacation.
Two-Man Rule
The two-man rule is a procedure popular in very high-security locations and situations. It features two individuals who must agree upon action yet are physically separated and must therefore take action independent of the other. Consider, for example, U.S. Air Force officers stationed in Minuteman Missile silos. The officers had to turn their keys at exactly the same moment. As neither officer could reach the others key and turned both at the same time, this prohibited any one person from being able to initiate a launch sequence.
Job Rotation
A job rotation policy states that an individual in a critical position does not stay in that position for too long (Figure 2.5). Primarily used as a fraud prevention mechanism, rotating individuals between positions provides not only for cross training but also for the capability of cross-checking individuals' work. Job rotation reduces the possibility of fraudulent actions, repetitive mistakes, or position abuse by retaining an individual for a limited length of time in a critical position.

Figure 2.5 A typical job rotation scheme
Geographic Access Control
Restrictions may be placed on users based upon where they are currently located. It's not unusual for security policy to state that any network access originating outside the continental United States must be blocked. Additionally, various applications, data, or organization resources may not be available to users logging in remotely. If a specific company resource or certain data is always and accessed only by users in a local office, persons logging in from another location in the country will not be allowed access.
Temporal Access Control, Time of Day Control
Temporal or time-of-day restrictions may be placed on various resources. For instance, users within a certain department who are not required to work on weekends may have their account logons restricted to only working hours Monday through Friday.
Privacy
Through the use of the Internet, it is now possible to retrieve an extensive amount of information about individuals, companies, and organizations. Because of this, a number of laws and regulations have been established to protect personal information. Personal health and medical information is protected by the Health Insurance Portability and Accountability Act (HIPAA) of 1996, a federal law that protects the privacy of a person's medical information.
Information security and privacy is the major focus of several European laws that basically state that personal information can be used only for the purpose for which it was collected.
Transparency
The principle of transparency is that it allows anyone to access, view, and test hardware or software systems. During testing by the general public or computer specialists, flaws can be found and announced. The operation of all encryption algorithms is completely open and known. This allows anyone to test an algorithm in an attempt to find flaws. Conversely, items that are secret or nontransparent are difficult to test and verify.
Implicit Deny
The concept of implicit deny is that access to data or resources is denied unless specific permission has been granted. Implicit refers to the fact that no action needs to be taken to restrict access. It will just happen automatically. Explicit refers to actions such as writing rules for a firewall or router that specify access that is granted. A simple example is the act of providing two users with a key to a padlock. Providing each user with a key is an explicit action giving permission and granting access. By default, all other users are implicitly denied access because they simply do not have a key.
Personal Device (BYOD)
Bring Your Own Device (BYOD) requirements apply to personal cell phones, tablets, pads, and personal laptops. The requirements may be grouped into two main categories:
- Administrative Requirements These take the form of policies, rules, or regulations that may include statements as to where a user may use a cell phone or personal device, whether a cell phone with a camera can be used, and what corporate data can be saved on a device. While some companies allow users to use their personal cell phones to log onto a company network, many provide users with a company phone for company use.
- Physical Requirements Specific attributes or capabilities of a device or software contained on the device fall under the category of physical requirements. For instance, a corporate policy may state that any personal cell phone containing company data must have the capability of being “wiped” or totally erased remotely in the event of theft or loss. Security professionals may enact a security program that restricts various devices, including personal devices, from connecting to a network if they fail to conform to policy. Network access control (NAC) is a general term for software or hardware implementations that inspect a device prior to allowing connection. Policies that might be enforced include the device having the latest software updates, up-to-date antivirus protection, or even access to certain types of applications and software. Network Access Protection (NAP) is the Microsoft implementation of network access control.
Privilege Management, Privilege Life Cycle
During a human resources onboarding event, an individual is granted various rights and privileges to the organization's resources and data. As their employment with the company progresses, users may be promoted, reassigned, or rotated into other positions requiring additional or lesser rights and privileges. Eventually individuals are terminated, resign, or retire from an organization, and thus removal of the rights and privileges granted to them is required. These events may be referred to either as privilege management or privilege life cycle. There are two important tasks that should be undertaken during the privilege life cycle:
- Rights and Privilege Audit As users progress through their assignments within an organization, they may gather additional rights and privileges. They may also be temporarily escalated and provided with privileges based upon a project or special situation. An audit should be undertaken on all individuals' access accounts to ensure that their existing rights and privileges match the minimum requirement (least privilege) for them to do their existing job.
- Account Deactivation This is the immediate removal of access rights during a termination event. Security professionals should ensure that a program is in place whereby an assigned individual in the IT department is made aware of the event and takes immediate action to withdraw user access to organization resources. Ideally, this action is performed during the exit interview or prior to an individual exiting the building. The term orphan accounts refers to resource access accounts that still exist yet do not belong to anybody. Orphan accounts should be discovered during a rights and privileges audit and immediately closed.
Participating in Security Awareness Education
In many companies, it is the responsibility of the security practitioner to participate in and act as a facilitator of security awareness education programs. Not only must the security practitioner deliver the program in front of an audience, in many cases they must author the content of the course.
Types of Security Awareness Education Programs
Many companies, depending on their size, use different types of user awareness training programs:
- New Hire Orientation An indoctrination program is usually delivered within the first few days of employment. During this program, the individual is typically made aware of the dos and don'ts of the company's security policies. They also might sign an authorized use policy (AUP) acknowledging their understanding of the rules and regulations of accessing network resources and company data. Of primary concern in a new hire orientation is the use of personal devices in the work environment. Also, instruction is given on how to access the network from a remote location such as a home office.
- Mandatory Security Training Mandatory security training is required under various regulations such as HIPAA in the medical field as well as various privacy regulations with respect to financial, banking, and credit card industry information. Mandatory training is usually cyclical and is required on an annual or semiannual basis.
- Corporate-Wide Security Training This program is generally required at least once a year by most corporations. It may be offered as a refresher program and in many instances takes the form of computer-based training (CBT).
- Specialty Security Training Specialty computer training includes training programs made available for vendors, customers, extranet users, senior executives, and department managers or offered in special situations. These courses are typically custom designed specifically for the audience.
Working with Human Resources and Stakeholders
It is important to know that as a security practitioner, you may be obtaining information for a security presentation by interacting with other departments. There are two distinct department and groups:
- Human Resources Human resources as a department is charged with not only sourcing and onboarding new employees but also the management aspect of their career during their employment with the company. It is important to include human resources in any training module. The human resources department may include trainers who are expert at either designing courses or facilitating presentations. Also, they are specifically aware of all of the laws and regulations regarding the material that may be presented to individuals, specifically testing and evaluation. It is their responsibility to make sure all training and evaluation of employees complies with federal, state, and other mandates.
- Stakeholders Stakeholders may have an interest in security training. They may be internal to the company, such as department heads, network administrators, and corporate executives, but they may also be external to the company, such as regulators and auditors. Stakeholders may might be involved in creating the content of security awareness training courseware. It is important to make sure the information obtained from stakeholders coincides with the overall security policies of the company.
Senior Executives
It is important to note that senior executives have a serious interest in the security of the company. In many cases, they have signed off on a variety of policies and statements that set forth the direction of the corporate security policy.
- Senior Executive Presentation During a senior executive security presentation, facts and supporting information are presented to illustrate compliance with various corporate security policies.
- Senior Executive Security Training This is a very important training awareness program specifically designed for senior executives concerning the protection of information to which they have access. In many instances, it is the senior executives who are specifically targeted for information concerning mergers and acquisitions, information about change in financial structure, or specific information about new products, strategies, or corporate direction. In many instances, this training involves the protection of cell phones, pads, tablets, and other devices used by senior executives.
Customers, Vendors, and Extranet Users Security Awareness Programs
On many occasions, it is responsibility of the security practitioner to facilitate discussions, training, or webinars for a variety of external users. Depending upon the company, various customers, vendors, or extranet users require indoctrination into the proper use of company assets and company information. It is important to stress the impact of security on both your company and the partnering company.
Summary
This chapter discussed a number of techniques, processes, methods, hardware devices, and protocols that form the foundation for network security. Enacting security in any workplace environment is a complex endeavor, not only requiring knowledge of software and hardware but also understanding the behavior of individuals who may mistakenly or intentionally cause harm to resources and data.
You have seen that, as in many other industries, there is no single solution to a problem or opportunity. Therefore, many companies and organizations developed their own methods for providing a solution. This is a primary reason the security professional is required to be aware of all of the possible solutions.
Various techniques may be used by an (ISC)2 SSCP exam candidate to examine and understand the Common Body of Knowledge (CBK) required to pass the exam. One of the techniques is to visualize the solution from start to finish (the example cited was that of a remote user desiring to log in to a corporate network). You have seen how various hardware and software solutions have evolved over time. New and better techniques often replace older techniques. Another learning technique is to group all similar terms into a category. And it's important to note how the exact same item or process might be known by several different names.
During exam preparation, you will come across terms such as TACACS, X.509, 802.11n, AES, and CAT6. Each of these terms originated either through a private company or through some sort of standards organization. You have seen that the standards organizations use a variety of techniques to arrive at a recommendation for the industry. These recommendations, or standards, are for the security professional sources of information for industry-accepted best practices.
The CIA triad features the three central concepts of security objectives that are the essence of all information security systems. The security professional must be completely familiar with the concepts of confidentiality, integrity, and availability and be able to relate any other security topic to one of these three objectives. In addition, there are three categories of security goals: prevention, detection, and recovery. Controlling access to an organization's resources involves a multistep process, which includes identification, authentication, authorization, and accounting.
Finally, it's important to acknowledge that the largest threat to the organization's resources is people.
Exam Essentials
- The CIA triad Know the CIA triad, and be able to describe the concepts of confidentiality, integrity, and availability.
- Security Categories Know the three security categories and be able to explain the actions required of each. The categories are prevention, detection, and recovery.
- Access Control Requirements. Be able to explain the requirements for access control.
- The Access Process Be able to explain the four steps of the access process. The steps include identification, authentication, authorization, and accounting.
- Nonrepudiation Be able to explain that nonrepudiation means that the sender cannot deny sending a message and that, provided special conditions, the receiver cannot deny receiving a message.
- Risk Explain that risk is a concept that indicates that there is a chance of damage or loss based upon exposure to potential threat.
- Vulnerability A vulnerability is a weakness that can be exploited by an attacker.
- Controls Controls, also called safeguards, countermeasures, policies, and procedures, are techniques that can be used to reduce or mitigate risk.
- Three Types of Controls The three types of controls are physical, logical, and administrative.
- Prudent Man, Due Diligence, and Due Care Prudent man, due diligence, and due care are measures taken by security professionals to protect the assets of an organization.
- Assets in an Organization Assets within an organization fall within two general categories: resources and data.
- Three As of Security The three As of security are authentication, authorization, and accounting.
- Principle of Least Privilege The principle of least privilege is the practice of providing users and applications with the least level of access required to perform a task or job.
- Account Life Cycle Privilege management, aka privilege life cycle, refers to the group of activities between user account initiation and the final termination and deprovisioning of an account.
Written Lab
You can find the answers in Appendix A.
- Write a paragraph briefly explaining the concept of implicit deny.
- Briefly describe the availability principle in the CIA triad.
- List the components of AAA.
- List the three primary security categories.
Review Questions
You can find the answers in Appendix B.
- What is the definition of the principle of least privilege?
A. Allowing all users full control over a network to keep administrative responsibilities to a minimum
B. Keeping the number of system users with access to a minimum
C. Granting users only the minimum privileges needed to accomplish assigned work tasks
D. Designing applications that do not have high levels of privilege
- What is the process of assigning groups of tasks to different users to prevent collusion and avoid conflicts of interest?
A. Principle of least privilege
B. Separation of duties
C. Mandatory access control
D. Integrity assurance
- To prevent any one person from having too much control or power, or performing fraudulent acts, which of the following solutions should not be implemented?
A. M of N control
B. Job rotation
C. Multiple key pairs
D. Separation of duties
- What is the primary goal of risk management?
A. Reduce risk to an acceptable level
B. Remove all risks from an environment
C. Minimize security cost expenditures
D. Assign responsibilities to job roles
- Which of the following best describes the use of a PIN number?
A. Authentication
B. Authorization
C. Auditing
D. Access control
- Nonrepudiation ensures which of the following?
A. That strong passwords are always used
B. The accounting of the user actions
C. That the sender cannot deny their actions
D. The confidentiality of the database
- Which item is not part of the primary security categories?
A. Prevention
B. Encryption
C. Detection
D. Recovery
- Which of the following is a nontechnical means of enforcing security?
A. Development of a disaster response plan
B. Separation of duties
C. User training
D. Safe testing
- Which option is not part of the prevention primary security category?
A. Placing a padlock on a fence
B. Using guard dogs instead of security guards
C. Using virus protection software on all users' machines
D. Using an alternate site after a disaster
- What is the most important step the IT department should take when an employee is fired?
A. Search their desk for USB drives
B. Erase all data on their laptop
C. Review the rights and privileges assigned to the user
D. Deactivate the user's account to prohibit access
- What is the foundational premise of risk management?
A. There is always some level of risk.
B. Computers can be completely secured.
C. As security increases, costs decrease.
D. Security and performance are cooperative measurements.
- What are weaknesses within a network?
A. Vulnerabilities
B. Mitigation
C. Risks
D. Controls
- Which of the following options is a part of the CIA triad?
A. Admission
B. Availability
C. Auditing
D. Administration
- Which of the following is not a security category?
A. Prevention
B. Remuneration
C. Detection
D. Recovery
- Which of the following types of controls restricts access based upon time?
A. Temporal time restriction
B. Date restriction
C. Time of day restriction
D. Authorized access hours
- Which of the following provides a catchall and prevents an action from being taken after everything else has allowed through on a network?
A. Explicit deny
B. Deny any
C. Implicit deny
D. Global deny
- Which of the following is a security program used in many banks to verify the ethics and job performance of a bank manager?
A. Ethical investigation
B. Mandatory vacation
C. Mandatory cruise
D. M of N
- When it comes to network security, the acronym AAA stands for which of the following?
A. Authorization, authentication, and accounting
B. Admission, authorization, and accounting
C. Authentication, authorization, and accounting
D. Administration, authorization, and auditing
- What is a restriction placed on users that denies them access to resources on the weekends?
A. Temporal differential
B. Time of week restriction
C. Time of day restriction
D. Time-based accounting
- During an access system audit a number of active accounts were discovered from employees who had left the company over the past two years. What are these accounts called?
A. Long-term accounts
B. Orphaned accounts
C. Pseudo-active accounts
D. Ghost accounts
