CHAPTER
Man-in-the-Middle |
6 |
INFORMATION IN THIS CHAPTER
![]() How Man-in-the-Middle Attacks Work
How Man-in-the-Middle Attacks Work
![]() Dangers with Man-in-the-Middle Attacks
Dangers with Man-in-the-Middle Attacks
![]() Future of Man-in-the-Middle Attacks
Future of Man-in-the-Middle Attacks
![]() Defenses against Man-in-the-Middle Attacks
Defenses against Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks have been one of the most successful attack vectors for attackers for quite some time. The concept is old, but new methods of attack continue to surface as new technologies are developed and techniques are discovered. In short, MITM attacks are the act of unauthorized individuals or parties placing themselves in the path of a communication to eavesdrop, intercept, and possibly modify legitimate communications. Although the focus of this chapter is how MITM attacks apply to computing resources, examples of these attacks stretch back for centuries.
A classic and easy to relate to type of MITM attack could be experienced by playing a game of “telephone” like many of us did as children. A few children would sit in a line next to one another with the game starting at one end and finishing at the other end. The first child in line would whisper a message to the next child in the line. The child receiving the message would then repeat the message to the next person in line. This would occur until the message eventually reached the last person. However, sometimes, kids can be mischievous and alter the message as it travels down the line. Finally, the last person in the line would stand up and say the message received out loud. The actual message received may sometimes vary greatly from the original message. If the original message was “The chair is blue,” it would be pretty funny if the final message received was “I have blue hair.” Well, it would be funny if you were 8 years old.
Another example of an attack still in use today is wiretapping. Traditionally, wiretapping has been the act of eavesdropping on phone conversations by using an electronic “tap” to place the attacker on the same communication path as the telephone being monitored. This allows the attacker to monitor and record conversations as they occur. Recording the conversations allows the attacker to review the conversations at a later time or use the recorded conversation for other reasons such as evidence or extortion.
NOTE
The term man-in-the-middle has been used for quite some time by the network security industry; however, this type of attack has many other nicknames as well. Some of the other nicknames for this attack include monkey-in-the-middle, bucket-brigade attack, session hijacking, and Transmission Control Protocol (TCP) hijacking.
Wiretapping may also be used by law enforcement and government organizations. During the presidency of George W. Bush, the National Security Agency (NSA) was authorized to conduct warrantless wiretappingA of phone conversations, e-mail, and other media for the purpose of monitoring suspected al-Qaeda communications. This type of monitoring serves as an example of how wiretapping can be used in various situations.
Attackers have been able to learn from the techniques and successes of traditional wiretapping and extend the attack vectors by applying the concept to monitor network traffic. When we observe the similarities between wiretapping as it applies to a traditional phone system and MITM attacks on networks, we can identify with and appreciate the threats associated with such attacks. Discussions of the impact of MITM and wiretapping and their impact on confidentiality and integrity are explored later in the section “Dangers with Man-in-the-Middle attacks.”
One of the fundamental concepts of MITM attacks that make them so dangerous is the fact that there is virtually no reliance on operating system or network-specific vulnerabilities to perform these types of attacks. In other words, even though all your operating systems and network-enabled devices are 100 percent up to date with the manufacturer’s patches, they can still be exploited by using MITM attacks in many situations. For this reason, MITM attacks can prove to be a lucrative attack avenue for attackers who wish to access sensitive information. Many vendors and working organizations have identified this threat and have slowly implemented features to hinder successful execution of these attacks. Examples of some of the controls and defensive strategies to prevent or reduce the likelihood of MITM attacks are covered in the section “Defenses against Man-in-the-Middle Attacks.”
HOW MAN-IN-THE-MIDDLE ATTACKS WORK
A MITM attack can be accomplished by a variety of techniques, depending on the access the attacker has to the target network and the types of protocols being used to facilitate the attack. As a review, a MITM attack occurs when an attacker injects himself or herself between one or more communication endpoints or redirects legitimate network traffic in an attempt to eavesdrop on data communications as they occur on the network or other communications platform.
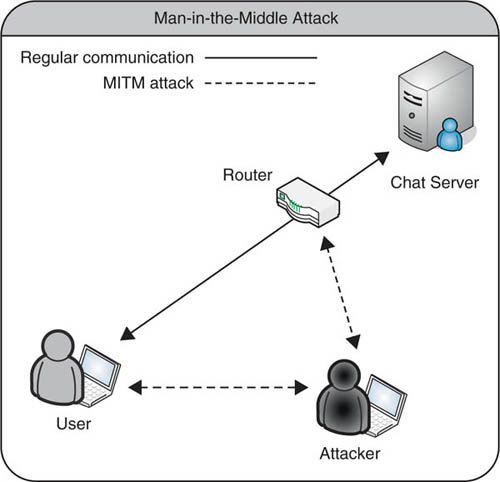
Figure 6.1 provides an overview of the anatomy of a MITM attack. Although the figure is simple in its illustration of the concept, the goal is to provide a glance of what a classic MITM attack scenario may look like. In Figure 6.1, the regular flow of data is depicted by the solid lines going to and from a chat server. Normally, communications from the user to the chat server would be accomplished by sending data from the user’s computer through the router and then traverse the network backbone until it establishes communications with the chat server. Once the protocols have negotiated the connection requirements, the chat client and the chat server can begin transmitting data back and forth to each other so users can communicate. Normal setup and communications only takes a few seconds to occur before users can start chatting.
In a MITM attack, represented by the broken lines in Figure 6.1, the attacker will use various techniques to reroute data between a user and the chat server. Ultimately, the attacker wants to make all communications pass through his or her computer, so he or she can sniff or modify the data while it is in transit. First, the attacker will carry out an attack to fool the user’s computer into thinking the attacker’s computer is the router. Then, the attacker will perform another attack to fool the router into thinking the attacker’s computer is the user’s computer. Once the attacker has performed these attacks against both the user’s computer and the router, all the data intended to be transmitted between the router and the user’s computer will be routed through the attacker’s computer. The attacker now has the capability of sniffing and modifying the data intended to be viewed only by the user, router, and chat server. Although this method of attack sounds complex, the availability of several different tools makes it very easy to accomplish by even the lesser experienced attacker. Some of the tools and techniques used to perform MITM attacks are discussed later in the section “Dangers with Man-in-the-Middle Attacks.”
FIGURE 6.1
MITM Overview
Once an attacker has been able to successfully insert himself or herself into the communication stream, he or she is capable of performing a variety of attacks. These attacks may include sniffing network traffic, command injection, malicious code injection, and public-key cryptosystem attacks. Although several attacks have been mentioned, many more can be used by an attacker depending on the purpose of his or her attack.
Sniffing Network Traffic
Sniffing is perhaps one of the most common and least complicated types of attacks initiated after a successful MITM attack is executed. As outlined in Figure 6.1, an attacker can inject himself or herself between a target user or system and a router to view all traffic passing between the two points. As communications between the systems continue, the attacker can use tools to identify user credentials and many other types of sensitive data. Upon capturing valid credentials, the attacker may use the credentials to access services within the network only available to authenticated individuals.
Replay Attacks
Replay attacks can also be conducted as a result of successful sniffing attacks performed during MITM. A simple scenario involves capturing network traffic between the two users or a user and a service and saving the authentication session. The attacker can then replay the authentication session at a later time to gain access to resources or masquerade as a legitimate user. This may be possible with encrypted or clear-text protocols, depending on the controls implemented as part of the infrastructure. Replay attacks may also involve sending a duplicate transmission of data, resulting in data corruption or modification.
Command Injection
Command injection attacks allow attackers to use sessions that are already active for interaction with a service or an application. The premise of the attack may include injecting commands under the context of the application or service without the attacker authenticating first. This can be helpful to an attacker who wishes to inject data to a server or a client system when the session being hijacked has already undergone the initial authentication process.
Internet Control Message Protocol Redirect
Internet Control Message Protocol (ICMP) redirect attacks are another form of MITM attack. Some MITM tools will allow the attacker to create an ICMP redirect message (Type 5) to advertise that a better route is available for traffic traversing the network. An attacker can use this type of attack to force all traffic on the local area network through his or her computer. Once all data is traversing the attacker’s computer, he or she may wish to sniff or modify it, depending on the goal of his or her attack.
Denial of Service
Denial-of-service (DoS) attacks can also be performed once an attacker has injected himself or herself between a victim and a remote resource. Attackers can route or drop traffic traversing his or her system to cause a DoS conditions. More information about DoS attacks is covered in Chapter 1, “Denial of Service.”
DANGERS WITH MAN-IN-THE-MIDDLE ATTACKS
MITM attacks target users and systems by intercepting the data that flows between network endpoints. These attacks target not only the actual data that flows between endpoints but also the confidentiality and integrity of the data itself. When a user or a system falls prey to a MITM attack, all confidentiality of the communication should be considered lost. Since there is no more inherent trust between the endpoints of the communication, the confidentiality of the data can no longer be attested for.
Consider this example: Rob is sending instant messages to David using a plain text protocol. During the conversation, an attacker performs a MITM attack and starts eavesdropping on the conversation. During the conversation, Rob asks David to keep it a secret that he is meeting with an undercover agent, Alan, for lunch at a local Thai food restaurant. He also indicates that the meeting is private because they will be discussing recent reconnaissance operations conducted against potential threats to national security. Since our attacker has already performed a MITM attack, he or she knows the details of the meeting and all the confidentiality is now lost.
Continuing with the previous example, if the attacker were to modify the conversation between Rob and David, the integrity of the information passed between Rob and David would be lost. If the attacker changed the conversation outcome to invite David to the lunch meeting with the undercover agent, you could probably imagine the look of surprise on Rob and the undercover agent’s face when David sits down and orders some Pad Thai. Some popular tools used for and during MITM attacks are listed in Table 6.1.
The following scenarios provide you with an overview of how some MITM attacks can be accomplished and introduce you to some of the tools used to facilitate MITM attacks.
Table 6.1 Man-in-the-middle tools |
|
Cain |
dsniff |
Ettercap |
Karma |
AirJack |
wsniff |
Ucsniff |
ARPoison |
Wireshark |
The Middler |
SSLStrip |
webmitm |
Address Resolution Protocol Cache Poisoning
This first scenario describes the classic attack method of using Address Resolution Protocol (ARP) cache poisoning to inject an attacker in-between a user and the default gateway (router) to intercept and read data as it traverses the network. Before moving into the scenario, a quick refresher in ARP may help with your understanding of how this scenario is possible.
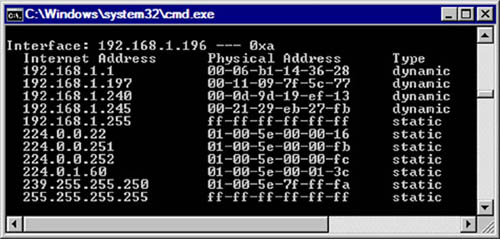
ARP (RFC 826B) is used in networks today to provide mapping of Open Systems Interconnection Reference Model (OSI) Layer 3 (Network) addresses to Layer 2 (Data Link) hardware addresses. Details and a good overview of the OSI model can be found at Cisco’s Web site,C as well as in Chapter 5, “Spanning Tree Protocol.” This mapping allows logical addresses, such as Internet Protocol (IP) addresses, to be associated with a physical hardware device such as a network interface card. Figure 6.2 provides an example of what an ARP table looks like when using the arp –a command from the Windows command prompt. Several different types of network implementations including Ethernet, Fast Ethernet, Fiber Distributed Data Interface, and wireless utilize ARP.
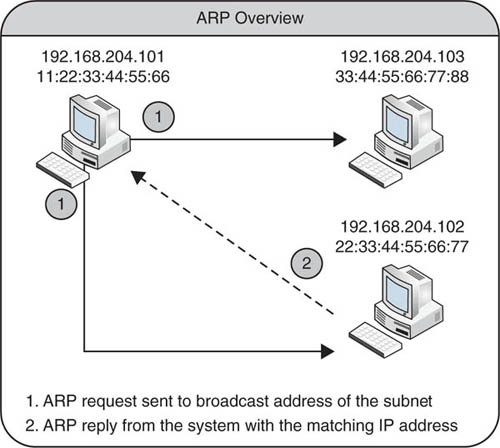
The following explanation assumes we are on a network using TCP/IP as the primary networking protocols. Communication using ARP is facilitated by the exchange of messages between hardware devices using ARP messages. The messages we are primarily concerned with are the ARP request and ARP reply. When requesting the hardware address of another system on the network, an ARP request is sent to the network broadcast address and includes the IP address and hardware address of the requestor and the IP address of the target system. Once a system receives the ARP request, it will check the local ARP table to see if it is the owner of the IP address broadcast in the original request. If the system does have an entry in its ARP table indicating it does own the IP address, an ARP reply is sent directly to the system that made the original request. The computer that made the original request will then add the hardware address to its ARP table for future use. A high-level overview of this operation is depicted in Figure 6.3.
The entire process of sending responses and receiving replies takes only seconds to complete in most cases, and this type of interaction is implemented on a variety of systems. ARP is used not only on computers but also on switches, routers, printers, wireless-enabled cell phones, and many other types of equipment.
FIGURE 6.2
Windows XP ARP Table
FIGURE 6.3
ARP Overview
Now that our refresher on ARP is complete, let’s focus on a MITM attack using a technique referred to as ARP cache poisoning. The attacker wishes to perform a MITM attack in an effort to gain access to valid credentials that could allow him or her to interact with other network services. With the understanding of how ARP works and the availability of several common MITM tools, this attack is fairly easy to perform.
Several tools for performing ARP cache poisoning attacks are freely available via the Internet, and usage of the tools is usually well documented. The tool our attacker chooses for this scenario is Ettercap.D (See Chapter 7, “Password Replay” for an example of ARP poisoning using a different tool, Cain & Abel.) Some of the interesting features of this tool include host discovery, target selection interface, capability of performing several types of MITM attacks, sniffing, and a variety of plug-ins to use during attacks. The tool is also capable of being run on a several different computing platforms, and users have a choice of running the tool in a graphical user interface, ncurses,E or text-based environment.
TIP
The last paragraph explained the availability of tools and how well documented they are based on their popularity and developer documentation. Popular sites such as YouTubeF allow people to create videos that will walk you through the common usage for many of the tools used for penetration testing and hacking. This is far from the days of reading text files and communicating on Bulletin Board Systems as a means of learning how to use and exchange tools. The learning curve today is significantly reduced for those getting started in security research and exploitation. Take a quick break, visit YouTube (or any other similar site), and search for “ettercap MITM.” Also try searching for some of the tools or concepts we have discussed in this book.
The attacker in this scenario, Michael, works as a design engineer for a large company in the sleepy town of Seguin, Texas. The company sells and distributes a large product line of aftermarket motorcycle parts for those motorcycle enthusiasts who wish to add a little personality to their motorcycles. Recently, Michael was in an accident and had some extensive damage done to his personal motorcycle (although Michael was okay). It turns out the motorcycle was deemed a total loss by his insurance company and Michael ended up purchasing a new motorcycle. One thing that Michael dearly missed was his shiny and loud tailpipes; you could hear them coming from a mile away, and the tailpipes were the envy of everyone.
Being a team player, Michael decides to order replacement tailpipes for his new motorcycle from the company he works for so he can get back to cruising in style. However, he discovers the company has discontinued the model tailpipes he used to have and will not bring them back into production. This obviously makes Michael angry, and he decides to take some action to show the company what happens when they disrespect loyal employees and customers.
Since Michael has internal access to the network, he decides to use a MITM attack, so he can steal someone else’s credentials to do some damage. Michael does this to reduce the likelihood the forthcoming attack will be traced back to him. Michael decides to use Ettercap to perform a MITM attack against Chip, the company Web and database developer. Michael first scans the local network to obtain a list of IP addresses and host names on the network and is able to identify a Windows XP computer named webdev with an IP address of 192.168.204.139. The name of this computer sounds like it would be the one a Web developer may use so he takes note of the IP address and moves down his scan list. Michael also notices a Windows Server 2008 system named corpweb with an IP address of 192.168.204.131.
In an ARP cache poisoning attack, the attacker identifies two systems he wants to attack and then places himself in the middle of the communication stream. This is accomplished by using a tool such as Ettercap send false information to modify the ARP cache on the two target systems. The tool will send ARP packets to poison the ARP cache on the Windows 2008 Server indicating the MAC address of Chip’s workstation is that of the attacker’s computer. At the same time, ARP packets will be sent to poison the ARP cache on Chip’s Windows XP computer to notify it the MAC address of the Windows 2008 Server is now that of the attacker’s computer. Once the ARP cache poison completes, both of the victim systems will unknowingly route traffic intended for each other through the attacker computer. During this exchange of data, the Windows 2008 Server and the Windows XP computers both believe they are still directly communicating with each other.
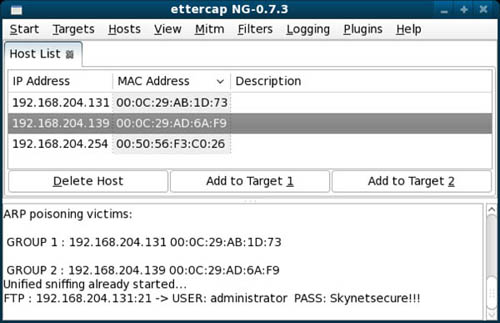
Using Ettercap, the attacker is able to select the two systems identified previously and start an ARP cache poisoning attack against these systems. Upon successfully injecting himself or herself between Chip’s computer and Web server, the attacker can sniff the traffic as it traverses his or her computer. Tools such as Ettercap have built-in filters to notify the attacker when credentials for specific protocols are sniffed during the attack. Figure 6.4 displays an active MITM attack as described in the scenario. It appears Michael was able to capture a File Transfer Protocol (FTP) login session originating from Chip’s computer and authenticating to the Web server.
FIGURE 6.4
ARP MITM Password Capture
Since Michael knows that Chip is the company Web developer, there is a good chance that these credentials are used to upload Web site content and for routine access to the Web server and Web site files. Michael uses the login credentials against the FTP server and discovers not only that the credentials are valid but they place him in the root directory of the company Web site. With this type of access, Michael can possibly delete all the content, replace legitimate files, and browse for other credentials or important information on the server. Michael decides to upload an updated version of the main page of the Web site that reads “This week only, all parts are 50 percent off normal price!”
Obviously, the great deal on motorcycle parts being advertised on the Web site spreads fast and causes an increase in sales calls. After being tipped off by a customer that it is “great you’re selling everything at half-off,” the sales department goes into a panic. Selling most parts at 50 percent off normal price is costing the company money. What is a company to do? Honor the advertised special? Tell the customers there was a glitch and there is no sale? Tell the customers the site got hacked? You can draw your own conclusions, but the point is that a very simple attack can cause a company many messes to clean up.
Losing customer loyalty and tarnishing a good reputation can cause many companies to experience reduced revenue. In some cases, it can impact the company in such a way that it forces the company to reduce staff or even close their doors. Although this scenario was primarily about the execution of a MITM attack, any attacks with significant enough magnitude can really hurt the company overall.
Secure Sockets Layer Man-in-the-Middle
In the last scenario, we looked at the inner workings of how a typical ARP cache poison MITM attack works. Some of the tools used to perform these attacks are very powerful in themselves; however, with some additional tools, it is possible to increase the capabilities of the attacker. For instance, the last attack scenario allowed the attacker to obtain credentials sent to a FTP server. FTP provides no protection against sniffing attacks, which may expose credentials transmitted in clear text to an attacker using some of the techniques already discussed.
What about encrypted protocols such as SSL? By nature of its design, SSL is supposed to provide a layer of protection for those who wish to conduct transactions and log into services containing sensitive information. By using other tools such as webmitmG or sslstrip,H attackers can circumvent some SSL implementations to allow attackers to gain access to credentials and data that should have been protected from MITM attacks.
For this scenario, we observe our attacker as he uses a technique to obtain credentials from victims who believe they are accessing a secure SSL-enabled Web site. The attacker is at his or her local book store enjoying a large hazelnut coffee while finishing some research for one of his or her last classes for college. After a few hours of studying the inner workings of XML, he or she takes a break to clear his or her mind and observe some of the other coffee shop patrons.
Across from the attacker sits a man who appears to be very focused on finishing up some tasks on his work laptop. The attacker assumes it is a work laptop because of the sticker on the cover that makes it look like a work laptop—you know, the ones that say “PROPERTY of XYZ Company.” This intrigues the attacker, so the attacker decides to perform a MITM attack to see what the man is up to. The attacker first identifies legitimate targets on a network by performing a discovery scan similar to the last scenario. During the scan, the attacker is most interested in identifying the victim computer and the default gateway.
After completing the scan, the attacker has identified the victim computer and the default gateway and can now prepare for his or her MITM attack. The attacker decides he or she is going to perform a SSL MITM attack to see if he or she can capture some credentials that the victim may be using. Specifically, the attacker will be using a tool called sslstrip.
The sslstrip tool created and supported by Moxie Marlinspike allows attackers to gain access to credentials transmitted using the HTTP and HTTPS protocols. The process includes setting up iptables to redirect all traffic sourced from the victim’s computer to a predefined port running on the attacker’s computer. The attacker then starts the sslstrip tool and performs an ARP MITM attack using tools such as arpspoof or Ettercap to inject himself or herself between the victim and the default gateway. At this point, sslstrip tracks the connections and listens for HTTP to HTTPS redirects to otherwise secure Web sites. When a victim attempts to log into a Web site using his or her credentials, sslstrip will write the username and password and the Web request to a log file for later viewing. The attacker can now reuse the captured credentials to access the victim’s private data and quite possibly the data for the company the victim works for.
Now that we have an understanding of how sslstrip works, let’s get back to the attack at hand. The commands in the following examples are executed on a Linux operating system with the appropriate PythonI software installed. In the following command, the attacker creates a rule using iptables to accept all traffic from the victim’s computer destined for TCP port 80 and redirect it to TCP port 10000 on the attacker’s computer:
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
Although the port used in this scenario is TCP port 10000, any available port can be used. Once the iptables rule is in place, the attacker can start the sslstrip tool and begin listening for inbound TCP traffic that was redirected from port 80 to port 10000, as seen in the next command:
./sslstrip.py --listen=10000
The final step of this attack involves using the arpspoof tool to perform a MITM cache poison attack against the victim’s computer. In the following code example, arpspoof uses the attacker’s eth0 network interface to perform the MITM attack between the target computer 192.168.204.139 and the default gateway address of 192.168.204.1:
arpspoof –i eth0 -10 192.168.204.139 192.168.204.1
After a few minutes of running the sslstrip tool, the attacker views the log files for the tool and can then use the credentials obtained to access accounts that would have been otherwise secure. The execution of this type of attack is fairly straightforward, and the consequences for falling victim to the attack can be disastrous, depending on the type of credentials obtained.
Domain Name System Spoofing
The final scenario we discuss in this chapter involves an attacker using the Domain Name System (DNS) to transmit false information about the true location of services requested by legitimate users. Before moving too far into how the attacker performs this type of attack, let’s look at a high-level overview of what DNS does in normal operation.
When DNS is functioning normally, it answers requests of users who are trying to contact services by using domain names. For example, if a user wanted to go to the Microsoft Web site and see what new products are coming out soon, he or she would simply type www.microsoft.com into his or her Web browser. DNS would resolve the friendly and easy-to-remember address to its corresponding IP address. The browser would then direct the user to the IP address associated with www.microsoft.com, and the user can start browsing for the latest and greatest in Microsoft product offerings.
This DNS spoofing attack is performed by an attacker who runs an application capable of listening for and responding to DNS queries. One such tool is part of the dsniff suite of tools and is called dnsspoof. Once an attacker is running an application such as dnsspoof, he or she can listen for DNS requests that are sent from the DNS clients to a DNS server for resolution. Upon identifying a DNS request, the attacker can reply to the DNS client that made the request with an IP address for the requested domain. However, the attacker may decide to provide an IP address that is not really the address the DNS client was attempting to resolve.
As an example, if a user was attempting to connect to www.microsoft.com and an attacker was able to reply with the IP address of the fedoraproject.org Web site before a legitimate DNS server could reply, then the user would most likely redirected to the http://fedoraproject.org/ Web site instead of the site he or she intended on visiting.
Attackers can use techniques to redirect users to Web sites that appear safe but actually contain malicious code. In some cases, the attacker may create a Web site that looks almost identical to the real site and the user may never notice the difference. To put this into context, consider the scenario where you are going to visit online banking Web sites to check your account balance. An attacker performs a DNS spoofing attack to redirect you to a Web site that looks very similar to your online banking site. Upon visiting the Web site, you attempt to log into the Web site to check your account balance; however, after logging in the site displays a message indicating it is temporarily down for maintenance. Most people would not think anything of it and come back later to check their balance. However, the malicious Web site has already collected your username and password, and the attacker has already started selling your account information to other malicious people.
Although this technique varies quite a bit from the other two scenarios we already discussed, you can see how MITM attacks can be executed using a variety of methods. As time goes on, we find new methods are becoming more robust and deceptive as far as the capabilities of MITM attacks are concerned.
FUTURE OF MAN-IN-THE-MIDDLE ATTACKS
The future of MITM attacks is hard to predict; however, from the trend of attack development and research of similar attacks, it is expected to continue growing in scope. As recent as within the last year of the writing of this book (2010), presentations at network security conferences such as BlackHatJ and DefConK continue to highlight the importance and new developments of these types of attacks.
EPIC FAIL |
One of the reasons network security initiatives and awareness fail is because administrators and designated security professionals are not provided proper funding for training to stay abreast of current threats. The threat landscape continues to evolve as can be witnessed by monitoring security-related Web sites, reading periodicals, and attending industry conferences. |
As mentioned at the beginning of this section, many of the newest attacks and tools are released at security conferences such as BlackHat and DefCon every year. It is a wise investment to attend these conferences to really know what the threats are and witness the speed at which they are evolving. |
Probably one of the most aggravating things to hear as a security professional is when administrators indicate they don’t have time to stay up to date on the current threat landscape. Even better yet is sometimes hearing “we don’t have any Internet facing services, so we are safe” from those who do not understand the threats. With proper training, with research, and by attending security-related conferences, the threat becomes more apparent. |
Far too many times advice is given by security practitioners to make sure “end users are trained.” However, it is just as important to ensure the people who are responsible for the overall network security posture are trained as well. Account for training and conference attendance into yearly budgets. Do it for the sake of your company’s security preparation and awareness! |
Tools used to conduct these attacks continue to mature and are widely available to those who wish to use them. Several open-source projects continue to enhance their capabilities of making these attacks easy to conduct and provide attackers with a significant advantage. Thankfully we can help reduce the exploitable footprint of these types of attacks by implementing mitigating controls.
DEFENSES AGAINST MAN-IN-THE-MIDDLE ATTACKS
The previous examples have provided us with a pretty good overview of some of the dangers associated with MITM attacks. In this part of the chapter, we explore some of the possible countermeasures that can be deployed to help thwart MITM attacks and the impact they can have on your network. A few of the defensive considerations may allow for a stronger security posture for multiple parts of the overall network infrastructure, while others will focus specifically on defenses against MITM attacks.
Knowing the Threats
You have already taken the first step in securing your network by reading this chapter! Knowing the threats against your organization and how the threats can be identified and mitigated will provide the information you need to implement defensive controls. Whether the controls implemented are active controls to stop attacks in their tracks, or passive controls used to monitor for attacks, knowing the types of attacks used by attackers is one of the greatest things you can do to prepare.
Remember, the threat landscape is always changing, so a one-time investigation into the threats will only be a snapshot in time of what the threats are. Continued awareness of the threats and attack techniques will allow you to prepare defenses and stay vigilant in your defensive initiatives.
Defense-in-Depth Approach
The lack of defensive controls implemented on internal network segments is a primary reason many organizations fall victim to successful attacks. A prime example of this is the ability for an attacker to capture credentials and steal the network by way of MITM attacks. Implementing defensive security controls at various layers within the network allows for more challenges an attacker will have to overcome to be successful at obtaining his or her objective. This is often referred to as “defense-in-depth” by many security practitioners, and the notion of deploying defenses in this manner has been urged for many years. Protecting your perimeter assets is only a small part of a solid security plan.
Consider a real-world example of defense-in-depth: when planning military operations, it is common for leaders to deploy defensive measures to deter successful attacks on military installations, equipment, and personnel. For instance, let’s explore the defensive posture for an US Army Airborne Infantry unit protecting a command and control outpost. For a first line of defense, the infantry unit will most likely have several Observation Point/Listening Points forward of the main defensive positions to give early warning of pending attacks. Additionally, early warning devices that trigger flares and noisemaking devices can also alert units to possible threats. In the information security world, these would be similar to the capabilities Intrusion Detection Systems (IDSes) provide. Early detection is vital to minimizing the impact of attacks, reducing potential losses.
A secondary defensive measure for protecting the command post would be using physical barriers to impede swift movement of the enemy. These barriers can be landscape and terrain that form a nature barrier such as a hill or trench. In information security, they may be equivalent to a well-placed proxy or firewall device. The goal of this line of defense is to slow attacks or at least to make it very tedious to perform them.
Next we look at defenses that are a little closer to the command and control point. These would be razor wire, mines, and small-caliber weapons. (Although there are other layers of defense as far as military strategy is concerned, the goal of this example is to provide a general overview of strategies, not to make us all hardened military warriors.) These controls provide the last line of defense for the soldiers. In a networking environment, these can equate to desktop security such as malware and virus protection, host-based firewalls and IDS, patch management, and system auditing controls.
Implementing some of these controls will reduce the overall likelihood of an attacker being successful in his or her attacks. But just as a soldier needs to be fed, rested, and outfitted with the correct equipment, your network should also ensure that it is constantly being monitored for its health and well-being. Why is this important? Because you cannot go down to your local network equipment vendor to purchase a single product that will satisfy all the needs of your network security program. Security is a process, not a product, and each layer provides a part of the overall solution. Now that we have explored an overview of defense in depth, we can focus our attention to specific defenses for MITM attacks.
Public Key Infrastructure
One possible solution to address MITM attacks involves deploying a Public Key Infrastructure (PKI) that implements mutual authentication. PKI manages the use of public key cryptography as we know it today. Think of it as the system that is responsible for the “care and feeding” of public key cryptography. In a PKI, there are several components that handle the issuance and revocation of certificates as well as attesting for the validity of certificates that are implemented. These are important components as it is the basis of ensuring we can trust encryption, signatures, and the implementation a given PKI is responsible for.
As it relates to SSL and HTTPS connections, the process used to verify the validity of a certificate is as follows: when connecting to a server that is using a digitally signed SSL certificate, the server will send the certificate to the Web user’s browser. Upon verification of the validity of the SSL certificate, the browser will connect to the server using the SSL protocol. A session key is created and used to protect the data that travels between the user’s browser and the server. The session key is unique to the session and is used as a means of ensuring private communication between the user and the Web server.
WARNING
Implementing a PKI by itself is not enough to prevent MITM attacks. If an attacker can capture key exchanges at the beginning of a session, he or she may still be able to perform MITM attacks. For this reason, implementing other controls that complement PKI implementations should be considered.
Although PKI on its own is not a sufficient mitigating control against MITM attacks, when it is coupled with mutual authentication, the solution is more appealing. Mutual authentication is the concept of requiring not just a client to authenticate to a server but also the server to authenticate to the client. With many client and server implementations, the initial trust is only confirmed by a one-way verification between the client and the server. With mutual authentication, the server verifies the client and the client verifies the server to ensure legitimate communications are being exchanged. Verification can be conducted by using public and private keys.
As with many security control implementations, there may be additional costs with the configuration of PKI and mutual authentication. The overall solution provides a decent return on investment as far as defending against MITM attacks is concerned. Implementing mutual authentication and PKI together can increase the complexity of and significantly reduce the likelihood of successful MITM attacks.
Port Security
Many organizations do not take into account what access the public may have to the network infrastructure when designing the physical layout of the network access points and the location of network jacks. One of the dangers associated with deploying a network is that, in many cases, anyone who can access a network jack can connect to and access network resources. Although this concept may not be apparent to many, it is indeed a very real threat. Even in trusted areas, security can be compromised by allowing access to visitors who may require temporary Internet access.
Port security allows administrators to lock down some of the loose ends that may be left exposed to some of the threats we have discussed in this chapter. In addition to being able to restrict the access of unauthorized systems, the implementation of port security can also reduce the organization’s exposure to the MITM attacks. Several vendors offer products that allow network integrators to implement port security, including Cisco,L Juniper,M and HP.N
Port security allows administrators to assign rules to access interfaces to determine if devices connecting to ports are indeed authorized to connect and access the network. This type of filtering can be accomplished by the administrator configuring switches on a port-by-port basis manually or dynamically by switch software. Once configured correctly, the switch can identify suspicious network traffic and devices that may not be authorized to connect to the network and immediately restrict traffic while also notifying administrators of potential security issues.
Some implementations of port security will determine access based on what hardware addresses are connected to each port. For example, in a situation where port security is enabled and a desktop computer is plugged into the switch port, the switch will learn the physical address of the desktop computer and only allow that hardware device to connect on that port. Should someone disconnect the desktop computer and attempt to plug in a laptop or other device, the port would identify the change and shut down the port. Once again, a notification may be sent to administrators to warn of potential issues. Although this sounds like a logical method of restricting access, if an attacker has the physical address of the initial device connected to the port he or she may be able to spoof the physical address to gain access via the port.
Some devices have the capability of implementing dynamic ARP inspection as a method of detecting gratuitous ARP replies and preventing them from being relayed. This is accomplished by the device having the capability of determining what ARP traffic is allowed.
Use Encrypted Protocols
Although the threat of sniffing and MITM attacks has been around for some time, many organizations fail to implement the best security practices to help reduce the overall exposure of an organization to these types of attacks. Organizations should implement encrypted protocols whenever possible to reduce the likelihood credentials will be sniffed off the network by attackers.
Some examples of clear-text protocols still heavily used in networks today include FTP, TELNET, and HTTP. Most clear-text protocols today have an encrypted alternative that can provide an additional layer of security. Some of the popular alternatives for the previously mentioned protocols include SFTP, SSH, and HTTPS. It is important to keep in mind that encrypted protocols should be used for protecting communications for remote administration and for protecting sensitive data that is being transmitted for everyday applications.
Implementing encrypted protocols not only protects data while it is in transit but also can add an additional layer of complexity for attackers to deal with when trying to perform attacks such as an MITM attack. As a basic security recommendation, encrypted protocols should always be used instead of clear-text protocols, not just because of the threat of MITM attacks, but for the protection of data while in transit in general.
Low-Level Detection
Implementing controls at various points in the network will ultimately provide a good defensive strategy. However, looking at some of the low-level detection methods will also pay off. A few simple things you can do if you suspect MITM attacks are being performed include reviewing local ARP table information and network traffic.
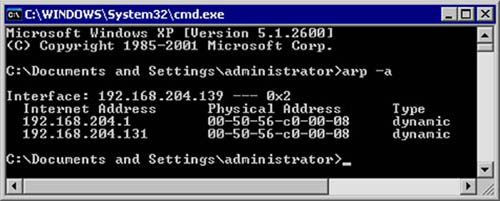
Although the intent is to use a more centralized and robust method of viewing the health of the network as a whole, a simple test you can perform to see if you are currently being attacked is to review ARP table entries. Figure 6.5 illustrates the ARP table for a Windows XP that is currently a victim of an ARP cache poison attack. This screenshot was actually taken from the victim computer in the lab environment while preparing for the section “ARP Cache Poisoning.”
After reviewing Figure 6.5, we can see that multiple IP addresses appear to have the same physical address. This means that the computer with IP address 192.168.204.139 has ARP table entries indicating both 192.168.204.1 and 192.168.204.131 reside at the same physical location. In this case, 192.168.204.1 is the IP address of the attacker’s computer and 192.168.204.131 is actually a Windows 2008 Domain Controller. If you detect something similar to this on your network, you should conduct further investigation to find out the source of the issue.
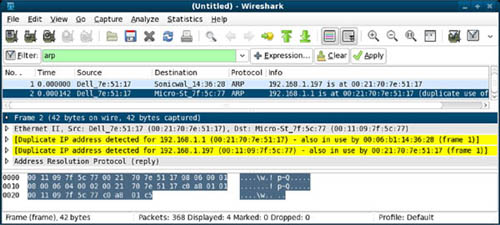
As you may recall from the section “ARP Cache Poisoning,” devices broadcast ARP requests to the broadcast address of the network in an effort to locate other systems on the network. During an active ARP cache poisoning attack, multiple IP addresses will have the same hardware address, as explained in the last paragraph. Figure 6.6 displays what an administrator may see while sniffing the network during such an attack.
Tools such as Wireshark will usually provide immediate identification of multiple devices using the same hardware address. Figure 6.6 is an example of a capture performed while performing a MITM attack on a network where the attacker was injecting himself or herself between a Windows XP computer (192.168.1.197) and the router interface for the subnet (192.168.1.1). The hardware address of 00:21:70:7E:51:17 is actually the address of the attacker’s computer.
FIGURE 6.5
Detecting ARP MITM
FIGURE 6.6
Protocol Detection of ARP MITM
One example of a network-based tool for monitoring the status of IP address to hardware address mapping is Arpwatch.O Arpwatch is an application developed several years ago by the Network Research Group at Lawrence Berkeley National Laboratory.P This tool monitors network traffic and builds a database of hardware-to-IP address relationships and time-stamps them to indicate when they were added to the database. The application has the ability to notify administrators via e-mail or syslog messages of changes to the hardware to IP address mapping. Changes may indicate MITM attacks are being performed. Although this tool is several years old, many applications used to monitor malicious traffic today still follow similar concepts.
SUMMARY
This chapter provided an overview, examples, and several defensive considerations for MITM attacks. The overview of MITM attacks provided valuable information about how the attacks work and how they can be performed using various methods of attack. This allows administrators and those responsible for security within their organizations to understand the threats that face the organization.
The examples of these types of attacks paint a picture of what a few scenarios for using MITM may look like and how various methods of attack can be used by an attacker in different situations. Although several scenarios were discussed and explained, it is important to stay abreast of new developments in MITM attack methods by following network security news sources.
The final portion of this chapter provided several options for administrators to consider when implementing controls to help reduce the likelihood of MITM attacks. Using defense-in-depth to protect the network at various levels was reviewed along with several recommendations for protecting against threats associated specifically with MITM attacks.
Awww.cnn.com/2005/POLITICS/12/17/bush.nsa/
Cwww.cisco.com/en/US/docs/internetworking/technology/handbook/OSI-Protocols.html
Dhttp://ettercap.sourceforge.net/
Ewww.gnu.org/software/ncurses/ncurses.html
Gwww.monkey.org/~dugsong/dsniff/
Hwww.thoughtcrime.org/software/sslstrip/
Oftp://ftp.ee.lbl.gov/arpwatch.tar.gz