CHAPTER
War Dialing |
2 |
INFORMATION IN THIS CHAPTER
It’s the mid-1990s and the Internet boom is really getting underway; however, high-speed “always-on” connections are extremely expensive, and neither cable nor phone companies are providing home service as of yet. In this era before being hardwired into the Internet was a standard idea, the way people connected to networks was by utilizing devices called modems. Modems connect to a computer on one side and the standard analog telephone system on the other side. This allows users to use a modem connected to their computer to “dial in” to a network by calling a modem that is connected to that network and set to answer.
NOTE
The term modem is an abbreviated combination of the words “modulation” and “demodulation.” Modulation is the process of encoding a digital signal into an analog signal. Demodulation is the reverse of modulation and used to encode an analog signal into a digital signal.
As with many innovations, private and public entities looked for ways to use the technology to save money. NYNEX was the regional telephone company for New England that resulted from the breakup of Bell Telephone in the mid-1980s. Like many companies, NYNEX saw the value in the idea of using modems to allow technicians to remotely connect to their systems for maintenance purposes. Unfortunately, the added convenience this brought also created opportunities for others.
Jester was an underage teen who also had a modem and enjoyed playing around on the networks he could find. He utilized his modem to dial a range of numbers until he identified modems that he could connect to, a process known as war dialing. This term came from the title of the 1983 movie War Games in which Matthew Broderick’s character utilizes a modem to dial a series of numbers looking for modems to connect to and ultimately almost destroys the world. At some point, Jester found the NYNEX modem connected to communications equipment servicing the community of Rutland, Massachusetts, and the Worcester Airport.1
Unfortunately, for the people of Rutland and anyone trying to use the airport on March 10, 1997, Jester defeated the security of the computer the modem was connected to and used his access to shut down the entire loop carrier system. In turn, this blacked out the telephone service for the community and all communication at the airport, including the system that allowed aircraft to activate the runway lights before landing, for about six hours. Obviously, this was a big deal for both the phone company and the government who went after Jester (so nicknamed because that is what he changed the system identification to) and led to one of the first prosecutions of a juvenile for hacking.
The use of Internet-based connectivity to internal networks using virtual private network (VPN), rather than directly dialing into the network over a private line, has become the standard way that users remotely connect to networks today. This standard operating procedure has steadily removed the need for organizations to use modems within their own networks on a massive scale and instead limits their use to unique devices that provide a very specific value to the person who implemented it. The value could be that the organization or a vendor requires a modem to be directly connected to a device as a redundant method to access it or simply for access to legacy systems that do not have access to broadband connections.
It may be counterintuitive, but the fact modems are utilized less and less in modern organizations can actually make them more dangerous. In the late 1990s, the publicizing of the prosecutions of Jester (as well as others, such as members of the “Legion of Doom”A) and the depiction of attackers on TV and in movies such as Hackers and The Net made organizations aware of the security concerns associated with attaching modems to their networks. This drove most organizations to focus on the security of the systems connected to these devices.
Because modems are much less pervasive, attackers and defenders focus much more attention on subverting and protecting firewalls or other perimeter devices. This reduced focus means it is much more likely that organizations will not put the proper security in place for modems (or even know they exist in the network) because “nobody attacks them anymore.” Not securing a device because nobody is looking for it is known as security through obscurity and is not security at all.
Modems are not totally gone from today’s networks. Organizations still use dial-up connectivity for administration of network devices, supporting legacy network implementations, and even employee remote access where high-speed connections are still unavailable or too expensive. This means that war dialing may result in fewer responses than in the 1980s and 1990s, but the opportunities are still there.
HOW WAR DIALING ATTACKS WORK
Attackers and penetration testers perform war dialing attacks to identify telephone numbers directly connected to modems. A war dialing attack consists of several steps that may ultimately allow complete access to otherwise secured network resources. Some of the goals of war dialing attacks may be to obtain network access achieved by circumventing weak controls or identifying poorly implemented communication channels that can be leveraged by an attacker for the purpose of toll fraud activities.
Attacks focused on a specific target require the attacker to identify a range of telephone numbers belonging to the target. This information can be found using a wide range of sources, including the telephone book crammed in the bottom drawer of your nightstand. Random attacks will usually consist of attackers scanning large blocks of numbers in an effort to locate any numbers connected to live modems.
It is common for attackers to compromise systems that have no direct ties to the real target. These unrelated compromised systems can be used against the target solely for hiding the identity of the true attacker or can also be used to amplify the power of the attack against the real target. As related to a wartime scenario, we can think of these compromised systems as “collateral damage.” They are not the primary target, but they are serving a purpose.
For instance, let us assume that the attacker wants to attack our favorite neighborhood electronics retailer, “Buy More.” Instead of going toe-to-toe and attacking the retailer directly, the attacker will most likely conduct attacks from systems that cannot be tied directly back to him or her (certainly our attacker wants to reduce the chances of being sent to the state penitentiary). The attacker can compromise many other systems with poor security postures first and then use those systems to “pivot” off or proxy the attack, making it appear the attack came from a totally different source.
In some cases, attacks may appear to be coming from entirely different countries. When dealing with tracing the source of an attack, it is very difficult to get people within the same legal jurisdiction to work together. Now, imagine trying to get international cooperation if an attack appears to be sourced from different countries alltogether. These types of attacks make it significantly harder to track down the attacker. However, even though our attacker is using a pivot attack, caution should still be taken, or the risk of getting caught is still very real.
Gathering Numbers for War Dialing
The attacks may be attempted against a single number, a block of numbers assigned to a company, or an entire exchange of telephone numbers. The scope of the attack and the amount of numbers dialed will depend on the attackers’ goal. Regardless of the total number of phone numbers dialed, the goal remains the same; identify telephone numbers that may provide an attacker alternate points of entry into a network or system.
If a specific target is the goal of an attacker, the first task that needs to be completed is to build a list of telephone numbers owned by the organization. This can be accomplished by a variety of ways, and sometimes the simplest methods of information gathering will provide the desired results.
One obvious place for attackers to look while building a list of telephone numbers is the Web site of the organization the attacker is targeting. An important thing to remember here is that businesses want to sell you their product, and generally this means they are not trying to hide from legitimate consumers. Visiting the organization’s Web site and its “contact us” or “support” links will likely provide attackers with a list of telephone numbers to start with or at least provide the attacker with information about the blocks of telephone numbers the organization uses.
Another popular method of obtaining telephone numbers is using various online resources that may provide telephone number information not traditionally listed on the main corporate Web site. One resource that provides helpful information is the “whois” service provided by InterNIC,B as well as domain registrar’s sites such as Network SolutionsC and GoDaddy.D This service allows attackers to obtain information about administrative and technical contacts and usually several valid telephone numbers belonging to an organization. An example of the type of information gathered from one of these resources is displayed below:
Registrant: Hometown Business USA One Fake Address Plaza Port Jefferson Station, NY 11776 US Domain Name: ICHDONTHINKSO.COM Administrative Contact: [email protected] One Fake Address Plaza Port Jefferson Station, NY 11776 US Phone: 631-555-1234 fax: 631-555-1288 Technical Contact: [email protected] One Fake Address Plaza Port Jefferson Station, NY 11776 US Phone: 631-555-1235 fax: 631-555-1289 Record expires on 13-May-2020. Record created on 12-May-2005. Database last updated on 23-Aug-2009 20:11:13 EDT.
Sweeping for Live Modems
Once the attacker has performed some research and has gathered phone numbers, the real fun begins. Loading the phone numbers into a war dialing program and waiting to see the results is one of the most interesting and fruitful parts of the attack. While conducting war dialing attacks, the attacker may observe several different types of responses from the war dialing software, depending on what types of answers are received from the numbers dialed. Additionally, if large blocks or telephone numbers are scanned, it may take quite some time to complete dialing all the numbers, depending on how many modems and lines are used by the attacker. Most of the existing war dialing software provides support for performing war dialing attacks with multiple modems at the same time. Additionally, the use of some Voice over Internet Protocol (VoIP) war dialers let attackers use a large number of lines to perform war dialing with minimal configuration changes. The more modems an attacker can use, the less overall time will be needed to dial large blocks of telephone numbers.
While war dialing, an attacker may decide to dial entire exchanges in search of listening modems. Our example list happens to be some of the exchanges dialed in the movie WarGames.2
311-555-0000 311-399-0000 311-555-0001 311-399-0001 311-555-0002 311-399-0002 311-555-0003 311-399-0003 … … 311-555-9996 311-399-9996 311-555-9997 311-399-9997 311-555-9998 311-399-9998 311-555-9999 311-399-9999
Note: The number for the W.O.P.R. computer modem in WarGames was 311-399-2364. We will save you some time; the password is “Joshua,” but please do not start a game of Global Thermonuclear War.
Modem Reply Types
Much like when a person picks up a phone and dials a telephone number, the expected response is to hear a person answer the phone call. This is not always the case, as I am sure most of us have experienced calling a number and expecting to hear a person but instead being greeted by the annoying screeching of a FAX machine. Most war dialing software has the capability of detecting several different types of call responses and can provide details and statistics based on the number of calls attempted. A few of the call response statuses are described below.
• Carrier. Telephone numbers classified as carrier lines means end-to-end connectivity is possible for data exchange. For the sake of the context of this chapter, we will refer to a carrier line as one that is connected to a modem.
• Tone. A telephone number that is dialed and classified as tone may be of interest for attackers who are interested in performing toll fraud attacks. In these cases, it may be possible for attackers who detect tone lines to dial into the number and then make an outbound call from that number. Imagine an attacker calling into a line with tone enabled and then making long-distance calls to friends in Germany. Whom do you think is stuck with the bill?
• Voice. Advanced modems have the capabilities of detecting a human voice or voicemail system. Telephone numbers identified as voice or voicemail are usually classified as a voice system and pose little threat, as they are most likely not directly connected to a modem.
• Busy. This category consists of telephone numbers that were busy during the initial war dialing attempt. The numbers identified as busy can be manually dialed after the completion of the test. Some war dialing software will tag the telephone number as busy and attempt to redial the number again at the end of the test.
• FAX. As many businesses still rely on fax machines, most modems and war dialing programs are capable of detecting and classifying fax lines.
• Timeout. In the event a number is dialed and no response is received or detected by the war dialing software, the software may indicate it had experienced a timeout for the number.
War Dialing Tools
Some of the tools that attackers use today have been around for many years and are still used because of the quality, reliability, and ease of use of the tool. Efficiency and accuracy are important parts of war dialing attacks, and thus many great tools have been developed to help automate and record results for attacks that are performed.
ToneLoc
This DOS application programmed in C is the creation of Minor Threat & Mucho Mass. The program was released in 1994 and derives its name from “Tone Locator.” This application was one of the most used war dialing programs in its day and is still used by war dialers today. The source codeE for ToneLoc was released to the public several years ago, and user manualsF are still very easy to find.
THC-SCAN
THC-SCAN was originally released in 1995, and the current release is at version 2.0.1. The current release was published in 2005 and was updated to offer support for newer operating systems. The logging capabilities and ease of configuration of THC-SCAN make this a great choice for a low-cost open-source war dialing application. The source code and documentation for THC-SCAN are still available at the THC Web site.G The test setup used during the development of this book included THC-SCAN 2.0.1 installed on Windows Vista using a USB-to-serial cable connected to an AOpen FM56EXV external serial modem. Amazingly enough, the entire investment was less than $15.00 to set up, thanks to a local Goodwill store.
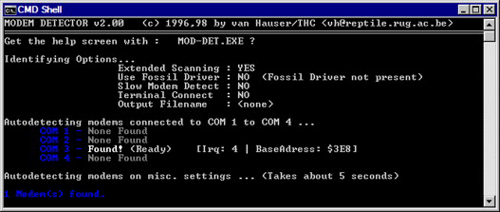
Several utility programs come with THC-SCAN, making the initial setup of this war dialing software fairly painless. MOD-DET.exe is a Windows executable file used to help detect modems that are connected to the computer. If a modem is detected, the MOD-DET.exe application will provide information that will be needed for the next step in setting up the computer for war dialing. In particular, the information about the COM port, interrupt request (IRQ) number, and base address the modem is assigned will be required. Figure 2.1 illustrates the information gathered while setting up the war dialer in our test environment.
Once the information needed to configure THC-SCAN is obtained, the next step is to use the TS-CFG.exe application to prepare the THC-SCAN configuration files, so the software can use the modem for war dialing. In our test environment, we simply changed the COM port, IRQ, and base address to match what was detected when MOD-DET.exe was run.
FIGURE 2.1
Detecting the Modem for Configuration
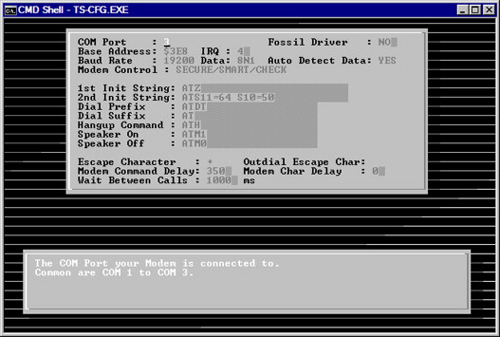
In addition to the options discussed, several other options can be modified, depending on what type of environment the war dialing attack is being conducted from. One commonly configured option is the “dial prefix.” This option is sometimes modified when the modem first needs to dial an initial series of numbers before being provided access to an outside line. For instance, if the number 8 needs to be dialed to access an outside line, an attacker would modify the dial prefix to dial the number 8 before dialing other numbers. Figure 2.2 illustrates the configuration screen that TS-CNF.exe provides.
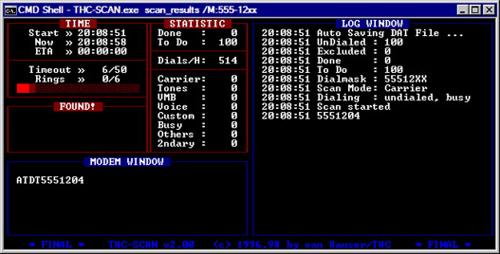
Figure 2.3 illustrates the THC-SCAN interface as it begins a test war dial. The information provided within the command shell is verbose and provides good visual feedback on the progress of the scan. Some of the information provided includes the number of calls made and how many are left, as well as the reply types from the numbers that were tested.
Information from the war dial is also logged to a series of files for review after the scan is completed. THC-SCAN is a good tool for war dialing and has proven its worth over many years.
PhoneSweep
PhoneSweep by Sandstorm EnterprisesH is a commercial war dialer that provides many of the same benefits as some of the previously mentioned tools. The application is easy to use and supports multiple modems for outbound calls, which can drastically reduce overall scan time for larger assessments. PhoneSweep also has detection capabilities that allow it to identify over 470 types of dialed systems, as well as the capability to perform dictionary attacksI against identified systems.
FIGURE 2.2
Configuring the Modem
FIGURE 2.3
Viewing the THC-SCAN Statistics and Progress
WarVOX
The crew over at MetasploitJ has done a great job with extending the capabilities of war dialing with the release of WarVOX. This war dialing tool is a Ruby on RailsK applications, which runs on a standalone Ruby WEBrick HTTP server.L The most fascinating part of this tool is that it performs war dialing attacks without using a traditional modem.
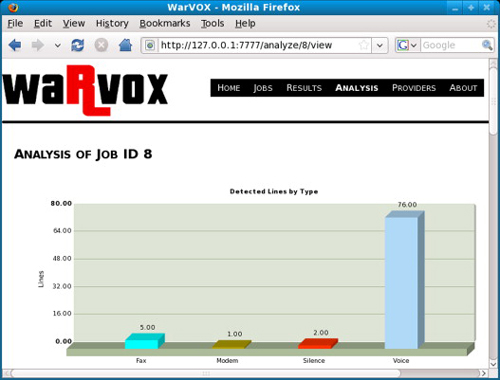
WarVOX classifies dialed numbers by analyzing the actual audio from the calls. This allows attackers the ability of determining the type and classification of the responses from the numbers dialed. Another interesting aspect about WarVOX is that it will record each call for offline analysis. Attackers can listen to the actual audio from each call made and use information gleaned from the recordings for future attacks. Figure 2.4 shows the visual feedback on the number of calls attempted and the classification of the numbers analyzed within WarVOX.
Several types of telephone numbers were tested during the writing of this book, and all numbers tested were classified correctly. Initial setup of the WarVOX tool and service provider configuration took approximately 25 minutes (this includes the time it took to register an account with our VoIP service provider). Our test setup included Fedora 10, WarVOX version 1.0.1, and one of the service providers recommended in the WarVOX project documentation. The ease of setup, configuration, and initiation of war dialing attacks makes WarVOX a valuable tool for attackers and penetration testers alike.
Table 2.1 provides a quick reference to some of the war dialer software this chapter has covered, as well as some other alternatives.
FIGURE 2.4
Viewing the WarVOX Scan Analysis
WarVOX |
ToneLoc |
THC-SCAN |
ModemScan |
TeleSweep |
iWAR |
ShokDial |
Telescan |
THE DANGER OF WAR DIALING
Modems can cause organizations to incur significant risk if best practices are not implemented during their deployment and use. Although there has been a decline in the use of modems for legacy connectivity, the threat is still very real. Penetration tests still reveal a significant amount of modems of which many have been implemented to provide organizations a solution for administration or remote access. However, there are still cases where administrators need to hunt down rogue modems implemented without the knowledge of the Information Technology (IT) department.
Out-of-Band Support Channels
Although many network administrators have moved as far away from dial-up access as possible, there still exists a need to implement modems for communications for a variety of situations. One of the most frequent implementations encountered involves using modems as an out-of-band communications solution for managing network equipment such as routers and switches. Out-of-band communications provide administrators the capability of remotely managing devices should traditional local area network or wide area network connectivity become unreliable or unavailable.
Although modems may be implemented for the purpose of out-of-band communications, poor implementation of such devices may provide an avenue of attack allowing attackers to gain access to the core backbone of the network. If an attacker is able to connect to a router via a poorly secured modem and successfully authenticate, there are many type of attacks that can be performed that may reduce the confidentiality, integrity, and availability of the network and the data that passes through it.
If an attacker has appropriate access, he or she may set new passwords for the router, essentially hijacking the device. Administrators may have a difficult time reclaiming administrative access to the router, depending on whether or not physical access to the router is required to regain control. This may take a considerable amount of time if the network administrators are not prepared. Additionally, many network administrators fail to implement proper logging for failed logon events, which allows attackers to perform extensive dictionary or brute-force attacks without detection. Successful authentication attacks may allow attackers to maintain access for long periods without detection by administrators. Once this level of access is achieved, the attacker can cripple the entire network by reconfiguring the router.
Attackers may use router software to sniff network traffic as it passes through the router. This obviously is a great concern, as many network administrators fail to implement encrypted protocols. Sniffing network traffic can also provide attackers with a wealth of information about the protocols and the types of traffic that traverses the network. This type of attack will most likely allow attackers to sniff legitimate usernames and passwords, allowing for further attacks against services available on the network.
The attacker may be able to perform denial-of-service (DoS) attacks, as explained in Chapter 1, “Denial of Service,” by configuring the router to route all traffic to a nonexistent address, also known as a null route or black hole. This of course will cause a total loss of data, as it traverses this point within the network.
Remote access for out-of-band communications should be secured to prevent these types of attacks. The previous attacks described only account for a small amount of what an attacker can do if modems connected to support devices are compromised.
Unauthorized Employee Access
One of the oldest war dialing attack scenarios deals with an employee who must have access to his or her work desktop computer while he or she is away from the office. Unfortunately, sometimes employees who are trying to do good deeds for the organization can unknowingly introduce vulnerabilities that weaken the organization’s security posture.
In this scenario, our technically savvy sales manager purchases a modem from his or her favorite electronics retailer and installs the modem in his or her work computer without the approval of the IT department and without consulting the organization’s remote access policies. Thanks to the ease of installation of hardware components and software installation wizards, this task is simple to complete. All the salesperson needs to do now is connect the FAX line or any other spare phone line to his or her modem and he or she is ready to dial-in from his or her home computer.
Why is this type of access dangerous? Implementing modems should be closely scrutinized by IT employees and must be controlled. Poorly implemented devices may allow anyone to connect to the modem and thus the organization’s internal network. Once successful authentication to the modem is performed, the remote access may not only allow access to the computer but likely allow access to the entire network the computer has. An attacker may be able to gain unrestricted access to the internal network and be able to do so without ever passing through a firewall or VPN device.
Vendor Support Modems
Many hardware and software vendors offer support services to customers who purchase and implement their products. For example, many building environmental control systems such as heating, ventilation, and air-conditioning (HVAC) can now be managed and serviced remotely. This provides a tremendous value to building management personnel and the companies that support service and regular maintenance of the system.
Some vendors require dial-up or network access to the equipment installed as part of the service level agreement (SLA) for a support contract. This provides the vendor with the appropriate access required to troubleshoot problems and perform upgrades as required by the SLA.
As an example, you may be able to see how an attacker can connect to a modem used to manage a HVAC system and gain unauthorized access to building environmental controls. This type of attack can allow attackers to cause serious disruption to the workflow of an organization. Imagine sitting in your office and the building temperature being raised to 85 degrees and not a Piña Colada machine in sight! Even worse, imagine the attacker shutting off the cooling to your data center. Additionally, if the control system is connected to the network, the attacker may be able to traverse the connection to the control and gain access to network resources. Compound this with the premise that most networks are not properly segregated and you now have a recipe for disaster.
THE FUTURE OF WAR DIALING
The methods discussed within this chapter are well established and not likely to change any time soon. However, the same thought process behind war dialing for modems is being repeated in many innovative ways and will continue to influence the way attackers look at things. The type of scanning discussed in Chapter 3, “Penetration ‘Testing,’” follows the same general methodology as war dialing, only from a network perspective.
Instead of using a modem to dial phone numbers within an exchange, network scanners and penetration testing programs probe a series of Internet Protocol addresses within a range. Both war dialer and scanner software listen for specific responses from the target devices and then provide you with information regarding possible targets to attack. Another scanning approach actually derives its name from war dialing, and that is war driving.
War driving is a method used by attackers to discover wireless networks. Originally, the term was coined because attackers would drive around in their cars using wireless scanning software to find unsecured wireless networks. By finding an unsecured wireless network, an attacker has circumvented the perimeter security of the network in the same way finding an unsecured modem does. More information on war driving can be found in WarDriving and Wireless Penetration TestingM and Kismet Hacking.N You will also note that most of the actions mentioned in the section “Defenses against War Dialing” also have equivalents in wireless security.
Another way this attack methodology is being adapted is social war dialing or vishing. This is a combination of the use of “robo” or “auto” dialers and VoIP to call a series of numbers in a range and then use social engineering attacks to try to trick the person on the other end of the phone into giving out personal information. This type of attack is based on having control of the VoIP system the war dialer is utilizing so that the attacker can spoof the information the victim sees on his or her caller ID system.
Attacking using this method usually starts with identifying a small community with only a single local bank to increase the likelihood of success. The attacker then programs the VoIP system that he or she controls to display the name of the bank and a valid phone number for that bank. When someone answers the phone, the VoIP system plays a prerecorded message that states that the user’s bank account has been compromised and the customer needs to change his or her PIN code to avoid charges to his or her account. The VoIP system then uses an automated menu to ask for and gather information such as account numbers, credit card numbers, and the victim’s current PIN.
Since the caller ID shows what may be valid information for the victim’s bank, this is a particularly effective attack for compromising someone’s identity. Social war dialing continues to evolve as new technologies emerge. It is now being utilized to “auto text” messages to ranges of phone numbers owned by cell phone providers in attempts to trick a user into providing personal information to an attacker. This type of constant adaptation of the thought process behind war dialing shows that some version of it will be with us for a long time.
DEFENSES AGAINST WAR DIALING
The best defense against any type of attack is to eliminate the attack surface itself. In the case of war dialing, you can accomplish this if you are able to eliminate modems from your network. An attacker who war dials your phone exchange when no modems exist comes up empty and moves on (unless he or she is just trying to annoy you by randomly making your phones ring). For many different reasons, you may not be able to accomplish this, and even if you are able to, there is no guarantee that your network will stay modem-free. Therefore, you should put in place policies, procedures, and implementation strategies regarding the proper use of modems, even if modems do not currently exist in your environment.
Attack Surface Reduction
For many reasons, many organizations prefer the outright banning of modems. This does not mean that remote access can no longer occur, but rather it is more cost- effective to use a combination of the Internet and VPN access to provide this rather than the use of modems. Since VPNs have become the standard for remote access solutions in these organizations, the use of modems now represents a second perimeter that must be secured.
The banning of modems begins with setting company policies against the use of modems within the network. Written policies are only as good as your enforcement of those policies, however. For this reason, you should view the banning as a first step that also includes security testing to find modems (war dialing yourself) and a well-known penalty for anyone who adds a modem to your network in violation of your policy.
If it is not possible to ban modem use from your environment because some vendors still require them to support their equipment, then you should look at whether these vendors will ever use them without your knowledge. For example, your televisor robot has stopped working because its positronic brain is trying to resolve a conflict between the first law of robotics (a robot may not injure a human being or, through inaction, allow a human being to come to harm3) and allowing you to watch the latest installment of a VH1 reality TV series. The question is whether the support team from US Robots and Mechanical Men, Inc., would automatically detect this issue and dial in to the wireless support modem installed in your robot to correct the problem or whether this type of repair would only occur after a support call and with you on the phone.
TIP
The banning of modem access to your network is not always something that you can accomplish even in today’s world. If you are completely based in the United States (or other countries) and have constant high-speed access to the Internet, then banning modems as a remote access solution is possible. In the Asia/Pacific countries, including Australia, this is not necessarily the case, and modems are still being used to connect to networks and work remotely.
Even in these areas of the world, you can still eliminate the attack surface from your network by removing your listening modems and requiring that all your users dial in to an Internet service provider then connect to your infrastructure using the Internet and VPN. However, this may not be cost-effective if this decision would require you to pay for your user’s monthly Internet charges.
If the manufacturer’s support team would only connect with the malfunctioning device after you initiated the action, then there is no reason for you to leave the modem engaged during normal operations. Therefore, your policies and procedures surrounding this modem would require that the modem remain turned off, disconnected from the phone system, or set to dial out only during normal operations in order to reduce the attack surface. During an authorized support procedure, you would change the mode of operation of the modem, making it available for use by the manufacturer. In our example, you would disable the modem again after the US Robots support team has cleared the conflict. You should also follow their recommendation to avoid using a televisor robot for this type of programming and watch Ninja Warrior to get your reality TV fix instead.
Modem Hardening
Besides leaving modems disconnected or turned off when not specifically in use, you can harden modems by utilizing the logical access controls that are available within the modem settings themselves. Modems can be set to automatically return a call or “call back” a modem that is dialing into the network before allowing access to occur. This setting forces an attacker to provide a legitimate phone number for a modem he or she is using and provides investigators information that can be used while attempting to identify the source of an attempted or successful breach. You can also define a list of authorized phone numbers that the modem will accept calls from. Although this setting will still allow spoofing to occur, an attacker must first figure out what the legitimate phone numbers are.
System Hardening
An attacker does not get access to your network just because his or her modem negotiates a connection with yours. After connecting, the attacker must provide a valid logon to the system the modem is connected to. Insuring that this login is as strong as possible is therefore very important. Regardless of the system that the modem is connected to, the login should be integrated with your normal authentication mechanisms for your environment rather than just a local login. This ensures that all the standard password policies around format and complexity are integrated. In addition, you are able to integrate the removal of these logins into your standard processes for removing access for people who no longer need it.
NOTE
The two main types of authentication services that are available to for authorizing access to your network through a modem are Remote Access Dial-In User Service (RADIUS) and Terminal Access Controller Access Control System Plus (TACACS+). RADIUS is an open specification defined in RFC 2865O and is utilized extensively even though it is not as secure at TACACS+. The TACACS+ specification is a protocol defined by Cisco, which makes it proprietary rather than open, but is available for use with non-Cisco devices, including Windows-based systems.
You should also ensure logins that give you access through modems are configured to lockout (at least for a period of time) after a few failed attempts. As we mentioned in the section “Scenario 1: Out-of-Band Support Channels,” one of the methods that attackers employ is to use brute-force dictionary attacks against the login page for the modem. If an account locks out after only three failed attempts, even if this lockout is only for 30 seconds at a time, it effectively defeats this type of attack (although it does also provide attackers with a way to create a DoS condition).
In addition to the requirement for strong authentication mechanisms, system hardening includes configuring logging and alerting mechanisms. The most important items to log are outgoing calls (this relates to requiring “call back” as described in the section “Modem Hardening”), successful and failed authentication attempts, and account lockouts. Finally, you must keep in mind that all modems represent a network edge, and therefore, any system that has a modem attached should have a firewall between that system and the rest of your internal network.
Discovery
As we discussed in the section “Scenario 2: Unauthorized Employee Access,” it is easy for an employee to set up a rogue modem within your environment. The only way to know no one has done this is to perform self-testing using the same war dialing software that an attacker might (see the section “War Dialing Tools” for specific software that you can use for self-testing). The best way to set up this self-testing is to schedule a war dialing scan of your entire range of valid numbers for each night. Returns from these scans should be integrated with your logging or alerting infrastructure, and any nonauthorized modems should generate an alert to a security administrator.
Another even more in-depth idea is to try to set up a “honeypot” to try to catch possible attackers without exposing your real resources to these attackers. Sandstorm Enterprises, whose PhoneSweep product was discussed in the section “War Dialing Tools,” has a product named Sandtrap that allows you to set up a modem (or use a modem that is already in use) to attract an attacker and record his or her actions. This includes allowing him or her to operate in a simulated environment in order to provide law enforcement with evidence of an attempted breach of your environment.
SUMMARY
War dialing is a classic attack methodology that seeks to find modems installed within your environment. Over the years, VPN access utilizing the Internet for connections has replaced dial-in telephone lines utilizing modems as the primary remote access solutions of most companies. However, this does not mean that modems have disappeared from modern networks. Modems are still deployed for many reasons, including remote administrative management and manufacturer support for equipment and remote access solutions for areas of the world where high-bandwidth Internet connections are still expensive or not available.
Attackers will utilize publicly available information and social engineering techniques to identify a valid range of phone numbers for an organization before using war dialing software to scan that range for possible targets. The same methodology behind war dialing has been adapted and utilized to form other attacking techniques including port scanning, war driving, and social war dialing. Organizations need to develop and maintain defensive postures against war dialing (even if they officially no longer have modems in their environment), and this should include the reducing or eliminating of modems, the hardening of both the modems and the systems they are connected to, and a system of testing their own environments for rogue modems.
Endnotes
1. Silverthorne S. Feds bust kid hacker, ZDNet, <http://www.infosecnews.org/hypermail/9803/0073.html/>; 1998 [retrieved 28.02.2010].
2. Badham J. WarGames (Movie), Perf. Matthew Broderick, United Artists; 1983.
3. Asimov I. I, Robot, New York: Gnome Press; 1950. Reprinted from New York: Bantam Spectra; 2008.
Ahttp://online.wsj.com/article/SB124136230988580795.html
Ewww.oldskoolphreak.com/etc/TL110SRC.ZIP
Fwww.textfiles.com/hacking/tl-user.txt
Ghttp://freeworld.thc.org/thc-scan/
I Given an encrypted password there are many different ways to proceed. A brute force attack is an exhaustive attack that literally tries every possible variation of characters, numbers, and symbols until the attack results in the discovery of the clear text password. Constraints can be put in place to narrow the scope of the attack based on implementation of specific considerations such as maximum or minimum password length. A dictionary attack tries all likely passwords from a list. The list may be much shorter and resemble the type of works you may find in a dictionary. For this reason, this type of attack usually requires less time to perform and is more of a focused effort. If a user has chosen a dictionary word or a common password, a dictionary attack will usually provide positive results in much less time compared to brute force methods. “Clever” (but common) variations of words can also be part of the dictionaries, such as “pa55w0rd”.
MWarDriving and Wireless Penetration Testing, ISBN: 978-1-59749-111-2 (Syngress)
NKismet Hacking, ISBN: 978-1-59749-117-4 (Syngress)