CHAPTER
Penetration “Testing” |
3 |
INFORMATION IN THIS CHAPTER
![]() How Penetration Testing Software Works
How Penetration Testing Software Works
![]() Dangers with Penetration Testing Tools
Dangers with Penetration Testing Tools
![]() Future of Penetration Testing Tools
Future of Penetration Testing Tools
![]() Defenses against Penetration Testing Software
Defenses against Penetration Testing Software
The practice of penetration testing and the use of specific tools to conduct penetration testing activities are vital parts of vulnerability identification and securing networks. Penetration testing also helps an organization determine how susceptible or resilient to attack it really is. The process of penetration testing involves a great deal of time and dedication to ensure a positive outcome for both the penetration tester and the organization being evaluated. Comparing penetration testing to other real-world types of assessment can help clarify the value of penetration testing.
In 2005, Discovery ChannelA aired a television series named “It Takes a Thief.”B This television show was hosted by two former burglars who would identify homes and businesses with weak security controls protecting the valuables stored within. The hosts of the show would obtain permission from home and business owners to demonstrate how easily a burglar could break into the property and walk away with thousands of dollars in valuables. After the burglary was completed, the hosts would explain how they gained access to the property and provide the owners with constructive advice on how to protect themselves from future burglaries. The hosts would also arrange for new security controls to be implemented to help protect the owners from future attacks and then test the controls by trying to break into the property again several weeks later.
“It Takes a Thief” provided value to the home and business owners involved with the TV series, and that value is almost identical to what penetration testers provide businesses today. So how does this tie us into the content of this chapter? How about the tools used to break into the houses and businesses? In many cases, the hosts of the show used readily available tools to circumvent controls. A lock-picking kit can be used by locksmiths to help you out when you’re locked out of your home or car, but it can also be used by a thief. A credit card can be used to buy your children ice cream but can also be used to bypass the locking mechanism on a door. This chapter presents a view of “penetration testing” tools and techniques that can be used for both good and immoral purposes.
Just as it took the hosts of “It Takes a Thief” time to perfect their trade, penetration testers and malicious attackers spend many years learning the art of exploitation and the tools used to help them become successful. Some of the concepts and attacks covered in this chapter are very elementary as they apply to securing your organization. Learning more about the tools used by penetration testers and attackers and how they can be used to gain access is a vital part of securing any network. Although, always ensure your defensive strategy is focused more on reducing the likelihood of a threat being realized and not so much on the defense against a particular tool.
HOW PENETRATION TESTING SOFTWARE WORKS
Any good handyman always has a well-equipped tool kit for taking care of repair tasks around the house. While making repairs, we must make sure the appropriate tools are readily available to complete the tasks properly. Having the proper tools allows us to expedite the completion of tasks, which can free up more time for us to spend with our families. Additionally, making sure you have reliable up-to-date tools is important to making sure you maximize your efforts.
As with the handyman and his toolkit, penetration testing software has to be as reliable as possible to make testing networks for vulnerabilities both accurate and efficient. The tools used to perform penetration tests should be field-tested to ensure the reliability of the tools and the safety of the network the tools are being used against.
Another important aspect to consider is the frequency with which tools are updated. Tools in active development and maintenance cycles must stay current to continue detecting the most recent vulnerabilities as well as exploiting them. For this reason, many network security tool developers will provide updates for tools to ensure the tools continue to grow to meet the demands of the security community. Updates to tools not only include feature enhancements and extension to the core components of the tools but also include the libraries required to support them. Additionally, updates to tools may be as simple as deploying new “signatures” for detection purposes.
The groups and individuals who spend time developing security-related assessment tools are dedicated to providing accurate detection and exploitation of vulnerabilities and are usually very skilled at what they do. From simple Ruby or Perl scripts to advanced frameworks, the tools available today for penetration testing and hacking are becoming available to the white hat and black hat communities more rapidly than ever before. Social media, collaboration sites embracing open-source development, and the ability to collaborate freely have made assessment tools significantly easier to develop and distribute than in the past.
Before getting too immersed into the discussion on how penetration testing software works, let’s address an important detail regarding who uses the tools and how to determine whether the tools are for penetration testing or hacking. This is a really tricky question and is not always something easy for people to identify. Many of the penetration testers working in the field today refer to themselves as “hackers” even though corporate America has provided them fancy titles like Security Analyst, Vulnerability Researcher, Penetration Tester, and Ethical Hacker.
There is no standard used to classify what is a penetration testing tool used by “penetration testers” and what is a hacking tool used by hackers. The truth of the matter is hackers use “penetration testing tools” and penetration testers use “hacking tools,” and the way the tools are used depends on the undertaking of the user. For instance, one popular tool for password attacks against a variety of protocols is THC-Hydra.C This tool may be used by both “malicious hackers” and “penetration testers”; however, depending on the purpose of the attack, the tool can be a penetration testing or hacking tool.
A penetration tester may explain his or her use of the tool during a penetration test as “I used Hydra to perform a dictionary attack on the secure shell (SSH) interface of the Cisco router, but no valid credentials were identified. XYZ company should continue using strong passwords that helped make this device secure,” whereas a malicious attacker may articulate “I tried to break into my school network, but Hydra did not find any good passwords.” What is the real difference between these statements? Nothing except the fact that the penetration tester was using the tool for proactive identification of potential vulnerabilities and the malicious hacker was using the tool for nefarious reasons.
Many people will make the argument that it is bad for penetration testers to make tools public so that not only other security professionals but also attackers with malicious intent will have access to them. However, compare this to going to your local retailer and buying a knife for cooking. Bad guys can buy knives also; is it the knife that is dangerous or how it is intended to be used?
One of the key things that may determine how tools are used is the scope of testing a penetration tester can perform based on Service Level Agreements (SLAs). Testing needs to be accurate and provide value to identifying vulnerabilities, but one disadvantage is that sometimes business contracts and the criticality of systems will limit some of the attacks that can be performed. As a penetration tester, it would be bad business for you to accidently cause a denial of service (DoS) against a critical network asset causing revenue loss for an organization. However, an attacker with malicious intent is not bound by the same rules.
Sometimes organizations will request testers to refrain from assessing entire networks because they contain “critical assets.” Many times the reason for the exclusion of specific targets is to ensure customers do not experience a degradation of service quality. This is understandable from a business perspective; however, from a testing methodology standpoint, it is a severely flawed practice. |
Business rules and SLAs are in place during penetration tests to protect the reliability of service provided to internal and external customers. However, excluding the assessment of resources can provide a false sense of security for organizations that do not ensure penetration tests emulate real-world attacks. |
Critical systems should be tested just as any other system to ensure critical operations are not exposed to significant vulnerabilities. If the system is critical, it should have load-balancing capabilities and redundancy implemented to protect against possible outages or degradation. Consider allowing the assessment to be conducted during nonpeak hours to reduce the impact if an unexpected condition occurs. This will be far better than finding out an attacker has taken control of critical systems because of a poor configuration or missing patch that was not identified. |
Penetration testers and malicious attackers may use the same tools; in some cases, penetration testers will not be able to use all the functionality of the tools if they reduce the stability of the systems being assessed. If the goal of penetration testing activities is to test for a DoS condition, this limitation may not apply.
DANGERS WITH PENETRATION TESTING TOOLS
Having spent a good amount of time talking about penetration tools and the gray area about what a hacker tool is and is not, let us look at some attacks and how penetration testing tools can be used to maximize the effectiveness and efficiency of an attack. Although several tools will be discussed, it is impossible to cover every tool an attacker may require in one chapter or even an entire book. The tools and scenarios that follow provide an overview to help us understand the potential impact penetration testing tools can have on your organization.
Nessus Vulnerability Scanning
NessusD is a tool that has been used by security professionals for many years. This tool is a vulnerability scanner that allows network security professionals and administrators to audit their networks by scanning ranges of Internet Protocol (IP) addresses and identifying vulnerabilities with a series of plug-ins. These plug-ins are written using a language called the Nessus Attack Scripting Language (NASL).
NASL plug-ins are a core part of the Nessus platform and are used to identify specific vulnerabilities and flaws in network resources. One of the great features of Nessus is that anyone can write NASL plug-ins and implement them as part of the scanner. Custom plug-ins can be written to detect vulnerabilities specific to the organization that developed the plug-in. Additionally the plug-ins can be shared with the Nessus development team and may be included in updates to the Nessus platform.
Configuring the initial setup of the Nessus server and client application takes only a few minutes. After setting up the application and determining the scope of the vulnerability scan, the attacker can configure the scanner to scan a single IP address or entire blocks of IP addresses. The time required for a scan to complete depends on how many plug-ins are being used, throughput of the network, scan speed settings, and the number of IP addresses included in the scan.
Once Nessus is configured to scan a network and the scan completes, the vulnerabilities are reported back to the Nessus application. The Nessus application can then present the data gathered back to the user in a variety of helpful formats. In many cases, the Nessus Client application will present information about all the network elements (indicated by their IP addresses) identified during the scans, information gathered from services detected running on the elements, and information about the vulnerabilities that may be associated with the services. This information usually includes detailed information about the vulnerabilities found, including links to Web sites with more detailed information.
Nessus also indicates the severity of vulnerabilities as part of the report details, so administrators and security professionals can identify possible steps to remediate the issues identified. In some cases, Nessus will also present the user with possible remediation steps and general recommendations for fixing identified issues, in addition to links to vulnerability databases that can provide more information on the inner workings of how vulnerabilities can be leveraged.
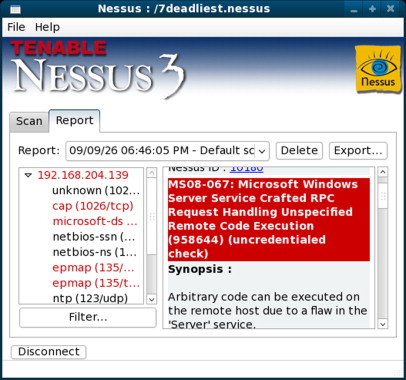
The system the attacker scanned (in the simulated virtual machine lab environment) is a Windows XP computer with missing security patches. The scan provided many results; however, the vulnerability the attacker appears to be interested in is the MS08-067 Security BulletinE identified in his or her scan report (Figure 3.1).
With the information provided by the Nessus scanner and the reports it generates, it is easy to see how an attacker can use this tool to identify vulnerabilities in network resources. You may also be considering the value this tool can provide for identifying missing patches in your own organization. Once an attacker has used a tool such as Nessus to identify vulnerabilities, he or she will then use the information learned to move on to the exploitation phase of the attack.
NOTE
Scanners such as Nessus are “noisy” when being used with the default settings. Noisy means if Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) is properly configured, it should detect a large amount of network traffic targeting individual or multiple systems with what appears to be suspicious activity. However, attackers may use IDS or IPS evasion technique to elude detection by these systems. Nessus also has the option of using one plug-in at a time to reduce the attack fingerprint and the chances of the malicious activities being detected.
FIGURE 3.1
There are many options for configuration within the Nessus scans, including some options for performing DoS attacks. Refer to Chapter 1, “Denial of Service,” for more information on how DoS attacks can cripple networks or even countries. In most cases, the use of DoS attacks is not recommended against production systems unless the specific intent is to verify whether or not a DoS condition is possible for a specific application. These types of tests should be reserved for evaluation during nonpeak hours and ideally with redundant systems in place to take over processing of data should the DoS be successful. Although a penetration tester may have to take all of this into consideration, an attacker may elect to use the DoS plug-ins specifically to cause a disruption or degradation of service. This type of activity can be used to execute a deliberate attack against a primary target or even to distract administrators while the attacker focuses on another target.
Nessus is a great tool for administrators and security professionals to use in their efforts to maintain and assess security within their networks. However, this is an example of a tool attackers can easily use as well. A good part of understanding the best defense is to learn and know the attacks work and how to identify them. It is a good idea to download Nessus to become familiar with the tool and how it can help your organization.
Metasploit Framework
One of the most popular (for good reason) tools out there today is Metasploit.F Actually, Metasploit is far more than a tool; it is a framework that encompasses many different capabilities. The Metasploit framework has many different components that make up its functionality. The users, contributors, and developers of Metasploit are very active in its development and maintenance.
The framework can be used for exploit development, penetration testing, creating malicious payloads for client-side attacks, fuzzing, active exploitation, and almost anything you could imagine a penetration tester might need. It can even be used to verify operating system patches applied by network and server administers. A detailed guide for using the Metasploit framework and many of its features can be found at www.offensive-security.com/metasploit-unleashed/. The framework was recently migrated from Perl to Ruby; however, some of the components are implemented with assembler and C.
The framework has many exploits and payloads to choose from to make short work of obtaining administrative access to computers, servers, and network equipment. Exploits are used to leverage flaws or vulnerabilities found in software. Payloads are the code and instructions that allow attackers to interact with compromised systems. This scenario will demonstrate the use of Metasploit to leverage a vulnerability in a computer using the Windows XP operating system and then to use information gleaned from the system to exploit other parts of the network.
Several techniques are used by attackers to discover network resources. Some of the techniques involve mapping the layout of a network, port scanning, and service identification. The focus of this chapter is penetration testing tools and how they can be leveraged for attacks and not a specific tutorial on the use of these techniques for host identification and classification. This first scenario assumes that the target has already been identified and classified by the attacker. The system the attacker has identified is the same system that was previously scanned in the section “Nessus Vulnerability Scanning.”
Although Metasploit provides several ways to interact with the framework during attacks in this example, the attacker uses the msfconsole. After an attacker has identified and classified a target system, he or she will determine the exploit and payload to use to help him or her achieve his or her goals. In our scenario, the initial goal of the attacker is to compromise a single computer in an effort to learn more information about the network before attacking the Windows Active Directory domain directly.
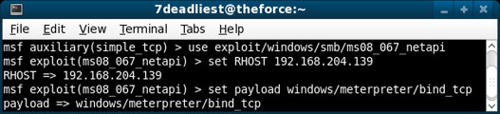
Figure 3.2 is a screenshot of the attacker preparing his or her exploit and pay-load to attack a Windows XP operating system that is missing critical patches. The exploit is leveraging the Microsoft Security Bulletin MS08-067G vulnerability that affects many of the Microsoft platforms outlined in the referenced link. Metasploit has exploits and payloads to fit many situations including attacks leveraging a large number of Microsoft vulnerabilities.
FIGURE 3.2
Exploit Selection
Once the exploit is successfully executed, the attacker has an opportunity to interact with the operating system and perform a variety of information gathering and other post-exploitation tasks. In this scenario, the attacker decided to use the meterpreter/bind_tcp payload to perform some advanced attacks and interact with the compromised computer.
TIP
Meterpreter is a part of the payload that is injected into memory and does not place files on the hard drive. This is achieved by injecting a dynamic link library (DLL) into a process that is already running using a technique called Remote Library Injection.H The DLL allows attackers to perform tasks that were once complicated in a faster and more efficient manner.
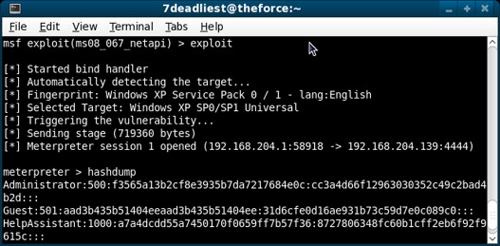
Figure 3.3 demonstrates the attacker executing the previously configured exploit and payload against the Windows XP target. Upon completion of a successful attack, a meterpreter session is started, and the attacker can now take advantage of the functionality meterpreter provides. In our scenario, the attacker uses the hashdump command to obtain a copy of the hashed passwords stored on the operating system.
Once the attacker has obtained the password hashes, he or she can crack them offline to obtain the clear-text equivalent and use the passwords obtained to conduct further attacks against the network. Some of the popular tools used for cracking passwords include RainbowCrack,I Ophcrack,J and John the Ripper.K Password attacks and storage are covered in depth in Chapter 1, “Windows Operating System–Password Attacks,” of Seven Deadliest Microsoft Attacks, another book in the Syngress Seven Deadliest Attacks Series. In many cases, depending on the password complexity, it only takes a few minutes or even a few seconds to crack passwords using these tools. For those of you who wish to crack the super top-secret password found in Figure 3.3, we will save you the time and let you know the Administrator password will result in a clear-text password of “Skynetsecure!!” (This is one of the passwords used in the VMWare lab environment while working on this book and has no significance outside the lab.)
FIGURE 3.3
Password Hashes Obtained
FIGURE 3.4
SMB Login Configurations
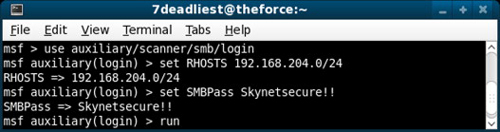
Now that the attacker has the clear-text equivalent to the hashed password he or she obtained by using the hashdump command from within the meterpreter session, he or she can start expanding his or her control ov er the network. Many times administrators will attempt to reduce the complexity of administration of network environments by reusing passwords across multiple systems. With this knowledge, the attacker will now take the credentials he or she obtained from reversing the captured hashes to check if the administrator accounts on other systems within the network are using the same passwords.
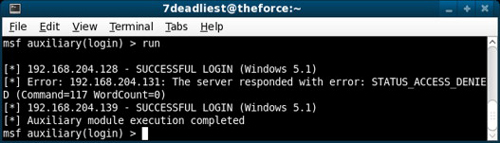
In Figure 3.4, the attacker configures one of the Metasploit auxiliary modules to use Server Message Block (SMB) login attempts against multiple systems to reveal if passwords are being reused within the network. The attacker has configured Metasploit to check an entire subnet for computers that accept the username and password using the credentials previously obtained.
FIGURE 3.5
SMB Login Results
The output in Figure 3.5 indicates our attacker was successful in identifying another system using the same password as the one previously compromised. Now the attacker has the ability to take full control of yet another system without having to go through the exploitation phase using a tool similar to Metasploit. This can save the attacker a lot of time while he or she starts taking total control of the systems within the target network.
The VMWare lab environment the attacker was using was limited to five target systems. However, in production networks with hundreds of systems the rewards are often much greater for an attacker. It is not uncommon for penetration testers and attackers to identify many systems reusing passwords, and Metasploit makes easy work of extending an attacker’s control of a target network.
Hydra Password Attacks
The last scenario for this chapter explores the types of attacks performed by using Hydra. This tool is one of the best login cracking tools available to penetration testers and attackers due to the number of protocols it supports and the reliability of the results it provides. Currently the tool supports login attacks for over 30 protocols and applications. Some of the protocols supported include SMB, Post Office Protocol 3, Simple Mail Transfer Protocol, telnet, Cisco telnet, Hypertext Transfer Protocol (HTTP), Microsoft Structured Query Language (MSSQL), and MySQL.
This scenario explores the dangers associated with the use of poorly configured management protocols. The attacker has identified what appears to be a Cisco router with telnet and Simple Network Management Protocol (SNMP) enabled. Both of these protocols are used by administrators to remotely administer the device or query performance statistics. The attacker first decides to perform a dictionary attack against the telnet interface but has no success in gaining access to the device.
The attacker decides to focus his or her attacks against the SNMP service running on the device. Attackers can use dictionary attacks against SNMP services just as they can against the telnet interface; however, with SNMP, the password is implemented in the form of a community string. This community sting allows administrators to apply access restrictions to the devices using the SNMP. Typically there are two community strings for management of devices: one of the community strings is usually a read-only community string and the other is a read-write community string.
NOTE
It is common for attackers to use word lists with tools such as Hydra to increase the chances of success while perform password attacks. These word lists may contain many different words that are common in English and other languages.
The “dictionary” part of “dictionary attack” really has two meanings. First, it means a list of words that are compiled to form a dictionary for use in password attacks. Second, a dictionary attack can actually use the entire list of words found in a dictionary. Oxford Dictionary’s Web site indicates over 171,000 wordsL in the second edition of their dictionary. This may be a little excessive for dictionary attacks, so it pays to know what the most common words used are.
Unfortunately, many times the SNMP services on devices are enabled by default and are configured with default community strings. Additionally, if the SNMP service is not enabled, many times administrators will configure SNMP with easily guessable community strings. A few of the most common SNMP community strings seen today are public, private, ro, rw, and internal. The knowledge of these common configurations allows attackers to use tools such as Hydra to automate the detection of default or easily guessable community strings. Figure 3.6 shows our attacker using Hydra to identify community strings on his or her Cisco router target.
After the scan is completed, the attacker is presented with the results. It appears from the results the attacker was been able to successfully identify two community names “public” and “private.” Up to this point, the attacker really did not have any success with gaining access to the network, but because he or she has the SNMP community strings for a Cisco device, he or she may be able to learn more information to perform additional attacks.
FIGURE 3.6
Hydra SNMP Dictionary Attack
Since the attacker now has the public and private community strings, he or she may try some advanced attacks that may result in further compromise of the network. The attacker uses the information learned to conduct his or her next attack against the network. By knowing the public community string, he or she is able to query configuration parameters of the device; however, with the private community string, he or she has read or write access to the device.
The attacker uses the knowledge of SNMP, Management Information Base (MIB), and Trivial File Transfer Protocol (TFTP) to transfer the Cisco router configuration file to a remote TFTP server. This is accomplished by the attacker setting up a TFTP server to listen for incoming TFTP write requests and then using the MIB Object Identifiers (OIDs) and the snmpset command to instruct the router to transfer its configuration file to the TFTP server. Once the attacker has performed the attack successfully, he or she can use TFTP to retrieve the file transferred to the TFTP server. A detailed explanation on how to use SNMP, MIB, and OIDs for this type of attack can be found on Cisco’s support site.M Although the Cisco Web site demonstrates the use of this type of functionality with the legitimate user in mind, we can see how an attacker can use it to his or her advantage.
Once the file is retrieved by the attacker, he or she can now review the router configuration file and learn more about the layout of the network, the protocols used, the access lists implemented, and possibly the password of the router. If the passwords configured for the device are stored in clear text, then the attacker may be able to use this password to gain access to network components or cause a DoS by reconfiguring the router to drop all legitimate traffic.
WARNING
In some cases, the Cisco passwords may be encrypted using the service password-encryption command. This will result in the encryption of the passwords using a weak Cisco “Type 7” proprietary encryption algorithm that can be reversed to its clear-text equivalent by using publicly available tools such as Cain and Abel.N
Although this scenario focused a lot on the exploitation of a router by manipulating SNMP, the tool that made this all possible was Hydra. There are many other types of attacks an attacker can perform against many protocols using this powerful tool.
FUTURE OF PENETRATION TESTING TOOLS
Many of the tools attackers and penetration testers have today are the work of years and years of labor by skilled tool developers. As the population of people who are interested in network security grows, the interest and support in tool and exploit development grows. The focus on frameworks has allowed many people to contribute to larger projects such as Metasploit. With the ease of use of these frameworks, we find that more people are willing to contribute to the development of the framework or projects that support the framework.
Table 3.1 Top 10 penetration testing toolsO |
|
Top 10 tools – sectools.org |
|
Nessus |
Hping2 |
Wireshark |
Kismet |
Snort |
Tcpdump |
Netcat |
Cain and Abel |
Metasploit Framework |
John the Ripper |
The number of tools available today is staggering. Tools are developed to support the assessment of almost every major protocol or application deployed on a wide variety of network types. Even those who work in the security field or those who are conducting malicious attacks on a regular basis cannot keep up with the abundance of tools available. However, there are tools used so often that they deserve to be mentioned. A comprehensive list of the top 100 tools in use can be found at http://sectools.org/. The list was the result of an extensive survey conducted in 2006 by Fyodor (Gordon LyonP) of Insecure.org, and many of the tools listed are still very relevant today and will be for years to come. The top 10 tools from the list are included in Table 3.1.
Although these have been identified as the top 10 tools from the survey, many other tools on the survey are used by penetration testers and attackers. It depends on the goal of the hack to determine what tools will be used to help achieve the desired results.
DEFENSES AGAINST PENETRATION TESTING SOFTWARE
So, what can we do about protecting ourselves from the dangers associated with penetration testing tools? It appears we are caught in the cross fire of good versus evil, and both sides have quite an arsenal of weapons to choose from. How do we protect ourselves against tools we are supposed to be using to evaluate our own security? In some cases, the answers to these questions will be very clear, but in other cases, it may take a little more creativity to arrive at a workable solution.
Password Complexity, Lockouts, and Logging
One of the tools discussed during this chapter was THC-Hydra. The tool provides malicious attackers, auditors, network administrators, and penetration testers with an automated method of testing network services for weak passwords. Administrators have a few things they can do to prevent or reduce the success of attacks using this and other similar tools.
First and foremost, do not use weak passwords. One of the easiest ways to compromise networks is by identifying services with weak or no passwords in place. Administrators must ensure complex passwords are being implemented to help prevent the success of attack using THC-Hydra and other logon cracking tools. Complex passwords should have certain attributes that qualify them as being strong.
Passwords should be at least 8 characters long. The larger the password the better, as it will require more computations and larger dictionaries for computers to process before finding the proper password. In time any password is crackable; it is the job of the administrator to ensure passwords are strong enough to defeat logon crackers and working with a longer password helps make it more challenging.
To offset the likelihood of passwords being cracked, administrators should also enforce the use of complex passwords. Complex passwords are usually long and use more of the key space found on keyboards. This means user should not only use uppercase and lowercase characters but also use numbers and symbols. Numbers and symbols can also be used to replace traditional letters found on the keyboard. As an example, the password “Skynetsecure!!” is fairly strong to begin with due to its complexity and length; however, additional modifications to the passwords can make it even more secure. By applying more of the key space, we can modify this passwords to be “$kyn3ts3(uR3!!,” which is certainly more complex than the previous example.
Implementing lockout policies is also a very important part of reducing the attack surface of logon cracking attacks. Lockout policies apply rules of how the system will react in the event multiple logon attempts fail. For instance, if a policy dictates that a user account will be locked out for 30 min after 3 logon attempts fail, this will limit the number of attempts an attacker can make in a given day. Modifying the policy to lock out the account for 60 min will reduce the likelihood of success even further.
Something to consider about usability and overhead associated with long, complex passwords and lockout thresholds is the overhead it may cause for support functions within the organization. Help-desk calls may increase causing additional overhead due to the length and complexity of the passwords and the human ability to properly enter their password when required. Careful consideration and research should be done before changing your network’s password policies. It is also recommended to notify employees that a password policy change may be coming in the future, so they have time to mentally prepare for the change and can adopt the change with little frustration.
Logging also plays an important role for defending against penetration testing or hacking tools and suspicious network activity. Configuring logging and most importantly notification of critical errors can provide advanced warning about active and pending attacks against the organization. Implementing lockout policies is important, but being able to identify accounts being locked out or multiple failed logon attempts may tip off administrators that something malicious may be taking place.
Finally, don’t just log it, review it. There is no sense in logging critical security events if no one is going to review or be notified of the events. Real-time notification should be considered, especially when you have a situation where an attacker is attempting to access network resources. It is not a good idea to wait for the help-desk group to notify you of something suspicious because of an increase in call volume due to user’s accounts needing to be unlocked. Get the information straight from the source and in real time by being notified of account lockouts automatically.
Endpoint Protection
Implementing standard virus and malware protection on the desktop can help identify malicious activity as well. Many antivirus software products can detect common tools and classify them as hacking tools. Although implementing antivirus protection should not be a standalone solution, it may help detect tools being used if an attacker is being sloppy with his or her work.
Once again, ensure notification of virus, malware, and hacking tools is being logged to a centralized server, and notifications are sent to administrators where possible. Many times the classification of an item being detected as a hack tool should raise specific concerns. This notification can mean an attacker has already gained access to a system and is uploading malicious tools, or a curious employee is installing malicious tools indicating a possible insider threat.
Egress Filtering and Proxies
Just as firewalls have rules to allow or deny access to resources within a demilitarized zone and between internal networks based on the type of network traffic, egress filtering addresses the data trying to leave your network. Many organizations focus too much attention on protecting the network from attacks sourcing from external threats, and not enough attention is focused on what is happening within the network.
Properly implemented egress filtering can help administrators detect malicious or suspicious traffic as it attempts to leave the network. Egress filtering also provides some flexibility while an organization is trying to reduce the effects of malware. Several vendors offer solutions to implement application layer proxies and content filters to help prevent malicious outbound connections from within the trusted network. Some of the concepts of egress filtering are covered in the National Institute of Standards and Technologies (NIST) special publications 800-61Q and 800-83.R
One of the most popular implementations of outbound proxies is its use for content filtering by forcing all HTTP traffic through a HTTP or a HTTPS proxy. This allows security administrators to keep better control of the flow of traffic in and out of the organization and an opportunity to identify malicious activity. The use of proxies also allows organizations to minimize the spread of malicious code as a result of viruses and malware.
Intrusion Detection and Prevention
Intrusion detection and prevention implementations can also help detect malicious activity as it occurs within a network. Many vendors provide good solutions for detecting threats, and most have the ability to immediately report suspicious activity or attack signatures to network administrators and security personnel.
As an example, consider the possibility an attacker is currently performing a dictionary attack against the telnet interface on the router your company uses to connect to the Internet. This interface was left in place so the maintenance company contracted to perform routine maintenance and upgrades can have access when they need to troubleshoot problems. A properly placed and configured IDS or IPS should be able to trigger an alert when it notices hundreds of authentication attempts per minute are being made to the telnet interface from single or multiple IP addresses.
IDS and IPS platforms can also detect malicious network activity based on variances in what “normal” network traffic for your network looks like. This type of detection is referred to as an “anomaly”-based IDS or IPS. The advantage of using an IDS or IPS that detects suspicious traffic is that the system has an established baseline for how your network normally operates and can compare traffic patterns to the baseline. Should suspicious network traffic be identified, administrators can be notified so further investigation can be conducted.
Logical Access Controls
The final defensive measure covered in this chapter is the use of logical access controls to restrict access to services based on criteria set by administrators. The concept of logical access controls is nothing new, but the impact they can have on security if implemented properly can be profound. An easy-to-understand example of logical access controls is implementing access control lists to limit access to protocols used for remote administration.
Remote administration is a fact of life for many large organizations. Due to the geographical separation of administrators from the systems they manage, many times administrative functions occur from remote subnets, cities, or even countries. Because of the dynamic nature of networking and administration, many times administrators will implement remote administration interfaces without regard to who will actually have access to them.
One of the dangers associated to implementing administrative interfaces without proper controls in place is that anyone who can access the interface can attempt to authenticate and possibly gain access to administrative functions. Logical access controls can help bridge this security gap.
For example, administrators can implement logical access controls that only allow connection to administrative interfaces from IP addresses or management subnets that are predefined by the administrators. This allows legitimate administrators to connect to the management interfaces and conduct their business but denies access to those connections that are not defined as part of the logical access control rules.
Of course, there is always a caveat to what we think is a great plan. If one of the systems we defined as valid system to conduct administrative tasks with is compromised, an attacker will be able to circumvent the logical access controls altogether. This is why it is important to consider implementing controls in addition to logical access controls, such as the use of certificates for authentication.
SUMMARY
As discussed in the introduction, the use of penetration testing tools is a vital part of the assessment of networks. The content of this chapter provided some insight into how penetration tools can benefit both the penetration tester and the malicious hacker in the goal of identifying and exploiting vulnerabilities.
Some of the scenarios presented in the chapter also explained how common penetration testing and hacking tools work. The scenarios also displayed how such tools can have a significant impact on the security of those organizations that fail to implement proper security controls.
The penetration testing tools we talked about in this chapter are just the tip of the iceberg. Just like an iceberg, there is usually a lot more under the surface you may not readily see at first. Many more great tools exist in the security community, but in many cases, you do not discover them until you have had some time to explore and encounter situations where special tools are required.
Finally, some of the defensive techniques discussed can help reduce your exploitable footprint. It is likely many other defensive measures will need to be considered to mitigate threats, but the options discussed in this chapter should provide some sound advice to get you started.
Bhttp://dsc.discovery.com/fansites/ittakesathief/ittakesathief.html
Chttp://freeworld.thc.org/thc-hydra/
Ewww.microsoft.com/technet/security/Bulletin/MS08-067.mspx
Gwww.microsoft.com/technet/security/Bulletin/MS08-067.mspx
Hwww.nologin.org/Downloads/Papers/remote-library-injection.pdf
Ihttp://project-rainbowcrack.com/
Jhttp://ophcrack.sourceforge.net/
Lwww.askoxford.com/asktheexperts/faq/aboutenglish/numberwords
Mwww.cisco.com/en/US/tech/tk648/tk362/technologies_tech_note09186a008009463e.shtml
Qhttp://csrc.nist.gov/publications/nistpubs/800-61/sp800-61.pdf
Rhttp://csrc.nist.gov/publications/nistpubs/800-83/SP800-83.pdf