Smart home scheduling and cybersecurity: fundamentals
Abstract
The modern power system is undergoing a transformative shift from the classical electricity grid to a smart grid. There are four components in a smart grid, namely, smart power generation, smart transmission, smart distribution, and smart end use. Among them, the smart home technique controls the energy consumption of each end user, also known as customer, which potentially impacts the energy generation, transmission, and distribution.
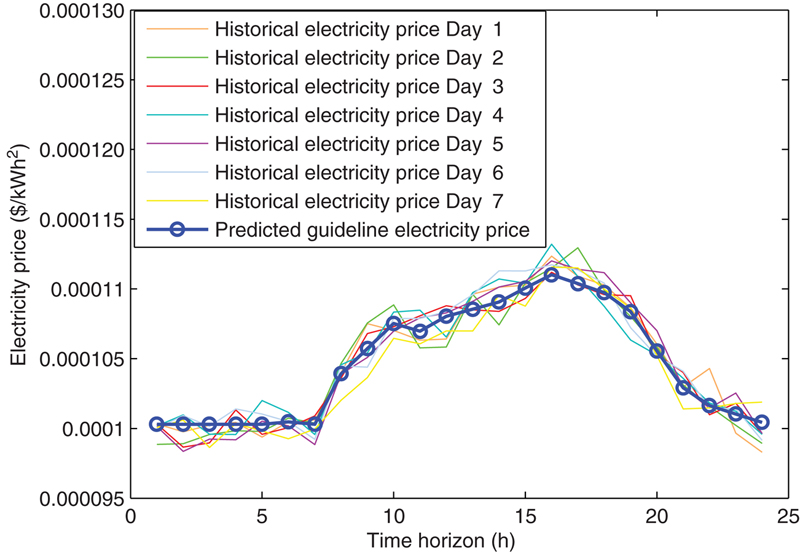
The smart home infrastructure features the automatic control of various interconnected modern home appliances. Together with the salient scheduling algorithms, it enables the customers to schedule the energy consumption, thus avoiding using electricity energy during the peak hours. This results in the reduction of electricity bill from the customer’s perspective and improved balance of the energy load from the utility’s perspective. The aforementioned process involves the usage of guideline pricing which estimates the future electricity price added by smart home controller. Despite its effectiveness, the smart home system is vulnerable to malicious cyberattacks. A hacker can manipulate the received guideline price and mislead the schedulers to make wrong decisions of energy scheduling. This can impact the bills of the customers and the peak energy usage of the power system. This chapter presents the state-of-the-art research on the smart home scheduling technique, explores the vulnerability of the smart home infrastructure, and describes the recent development of detection technologies against those cyberattacks.
Keywords
1. Introduction
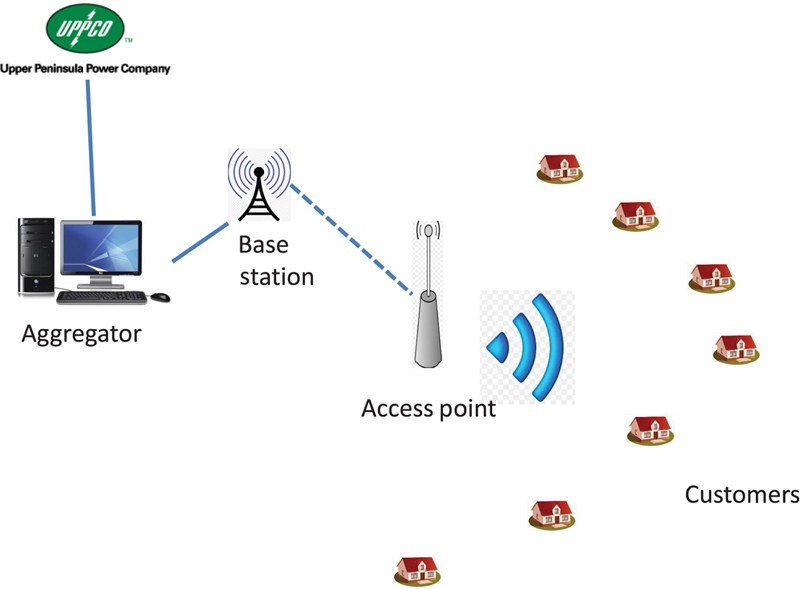
2. Smart home system preliminaries
2.1. Smart home system model
 (10.1)
(10.1)
 (10.2)
(10.2)
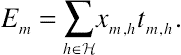 (10.3)
(10.3)
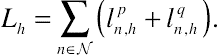 (10.5)
(10.5)
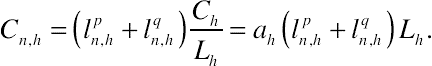 (10.7)
(10.7)2.2. Smart home scheduling
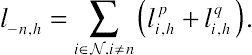 (10.9)
(10.9)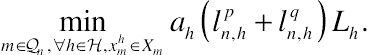
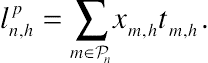
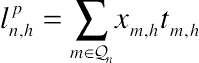
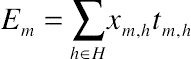
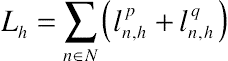
Table 10.1
Electricity Bill Corresponding to Each Power Level
| Monetary Cost ($) | Time Slot 1 | Time Slot 2 | Time Slot 3 | Time Slot 4 |
| Power level 1 | 1 | 1.2 | 1.5 | 1.1 |
| Power level 2 | 2 | 2.5 | 2.8 | 2.4 |
| Power level 3 | 3 | 3.8 | 4.1 | 3.6 |


Table 10.2
Daily Energy Consumption and Regular Execution Duration of Automatically Controlled Home Appliances [20]
| Home Appliance | Daily Consumption | Execution Duration |
| Washing machine | 1.2–2 kWh | 1–3 h |
| Dish washer | 1.2–2 kWh | 1–3 h |
| Cloth dryer | 1.5–3 kWh | 1–3 h |
| EV | 9–12 kWh | 4–8 h |
| Air conditioner | 2–3 kWh | 2–3 h |
| Heater | 2–3 kWh | 2–3 h |
3. Pricing cyberattacks
3.1. Cyberattack for bill reduction
3.2. Cyberattack for forming the peak energy load
4. Single event detection technology
 and the PAR increase is computed as
and the PAR increase is computed as 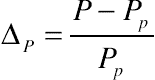 . If ∆B > δB or ∆P > δP, an alert will be signaled.
. If ∆B > δB or ∆P > δP, an alert will be signaled.5. Long-term detection technique
5.1. Motivation
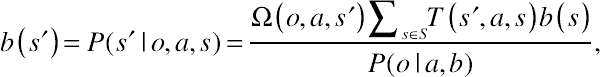 (10.10)
(10.10)
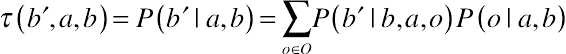 (10.11)
(10.11)
 (10.12)
(10.12)
 (10.13)
(10.13)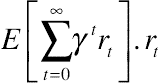 is the reward in step t. The optimal value of the discounted expected reward given the current belief state b is denoted as V*(b) such that [27]
is the reward in step t. The optimal value of the discounted expected reward given the current belief state b is denoted as V*(b) such that [27]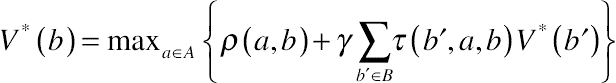 . Each time the decision maker intends to find the optimal action. He or she needs to consider both the reward in the present step and the discounted expected reward in the long future. During the long run, the decision maker receives the update of the observation each time slot, from which he/she estimates the belief state of the system. Given the belief state of the current system state, the decision maker obtains the optimal action by solving the optimization problem P3. The procedure for solving a POMDP problem is presented in the example given later.
. Each time the decision maker intends to find the optimal action. He or she needs to consider both the reward in the present step and the discounted expected reward in the long future. During the long run, the decision maker receives the update of the observation each time slot, from which he/she estimates the belief state of the system. Given the belief state of the current system state, the decision maker obtains the optimal action by solving the optimization problem P3. The procedure for solving a POMDP problem is presented in the example given later.5.2. Our POMDP-based detection
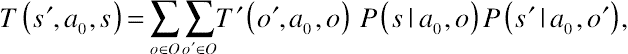 (10.15)
(10.15)
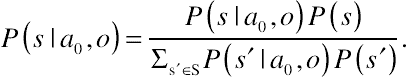 (10.16)
(10.16)
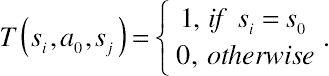 (10.17)
(10.17)
 (10.19)
(10.19)
 (10.20)
(10.20)
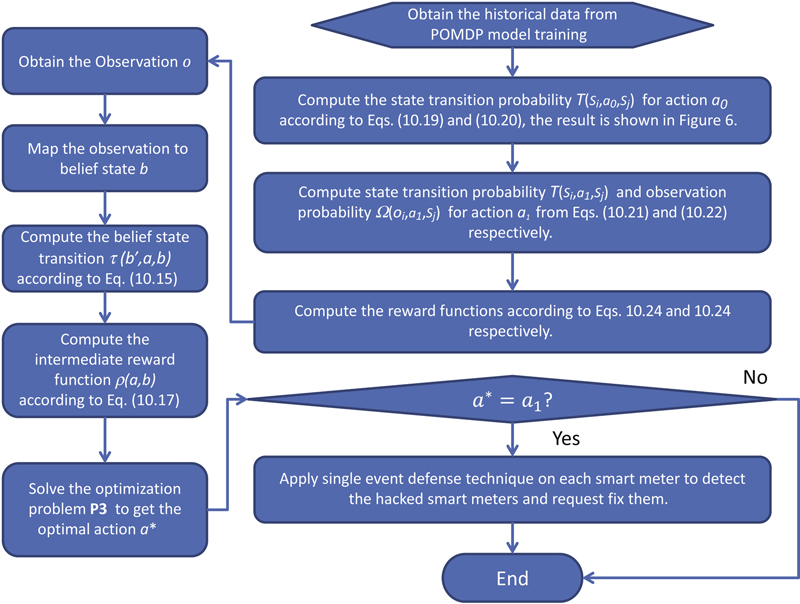
6. Case study for long-term detection technique

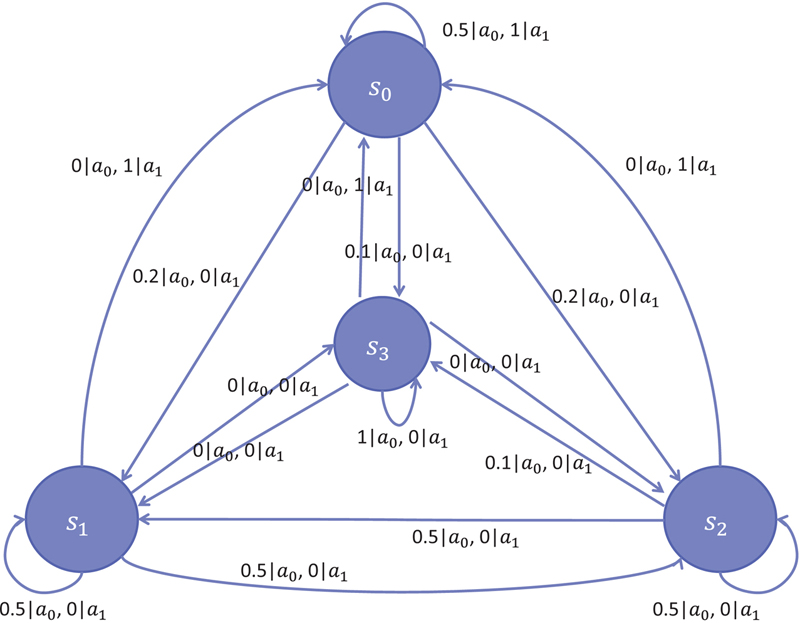
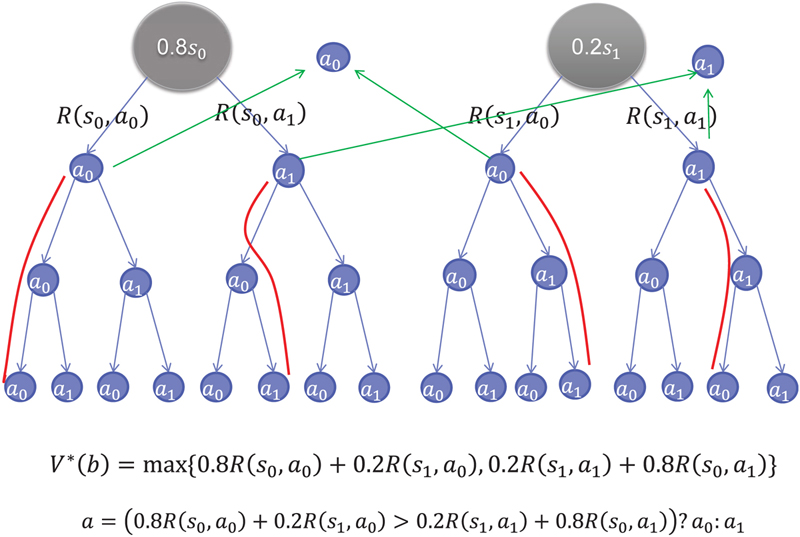
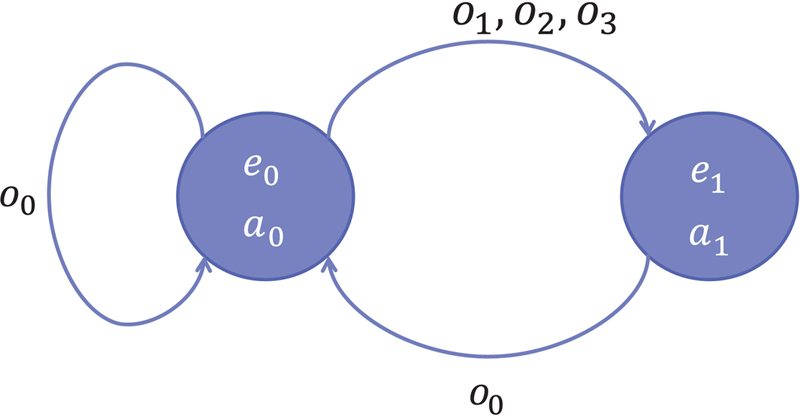
7. Simulation
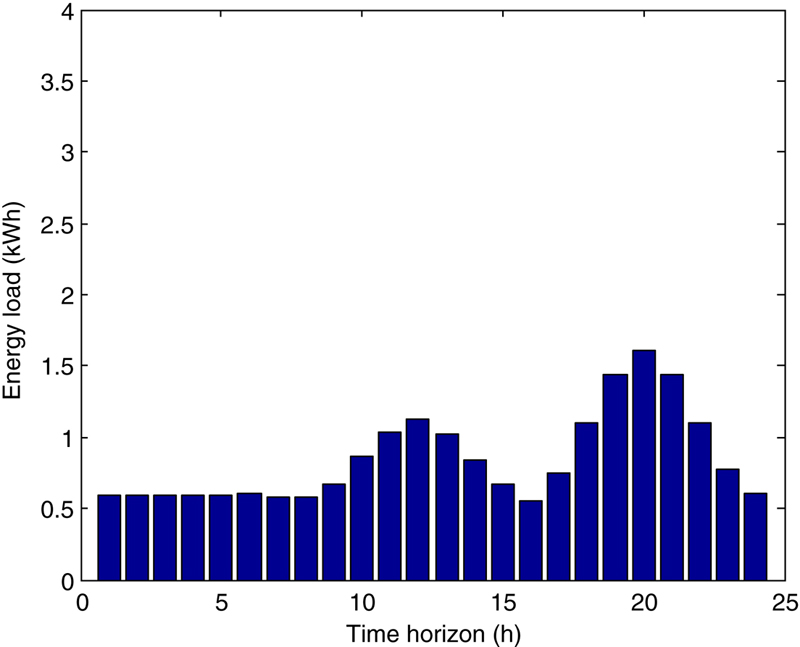
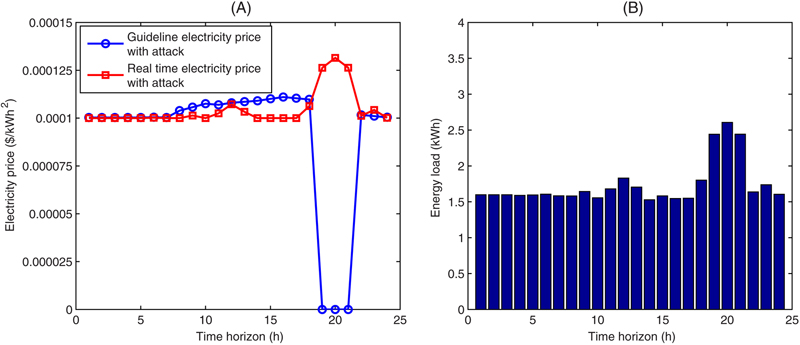

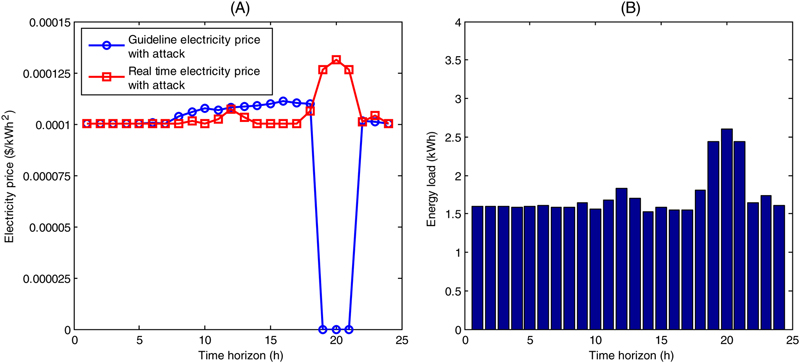

7.1. Cyberattack for bill reduction
7.2. Cyberattack for forming a peak energy load
7.3. Single event detection technique
7.4. Long-term detection technique
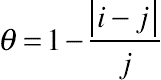 if the observation is oi and the system state is sj (ie, j smart meters are actually hacked while i smart meters are reported to be hacked). The observation accuracies of the proposed method and the heuristic method for different testcases are shown in Figs. 10.12 and 10.13A, B, and Fig. 10.14, respectively. The results on bill increase, PAR increase and labor cost are shown in Table 10.3. For the 500-customer testcase, we make the following observations.
if the observation is oi and the system state is sj (ie, j smart meters are actually hacked while i smart meters are reported to be hacked). The observation accuracies of the proposed method and the heuristic method for different testcases are shown in Figs. 10.12 and 10.13A, B, and Fig. 10.14, respectively. The results on bill increase, PAR increase and labor cost are shown in Table 10.3. For the 500-customer testcase, we make the following observations. and
and  , respectively.
, respectively.
(A) Observation accuracy for 100-customer testcase. (B) Observation accuracy for 200-customer testcase.

(A) Observation accuracy for 300-customer testcase. (B) Observation accuracy for 400-customer testcase.
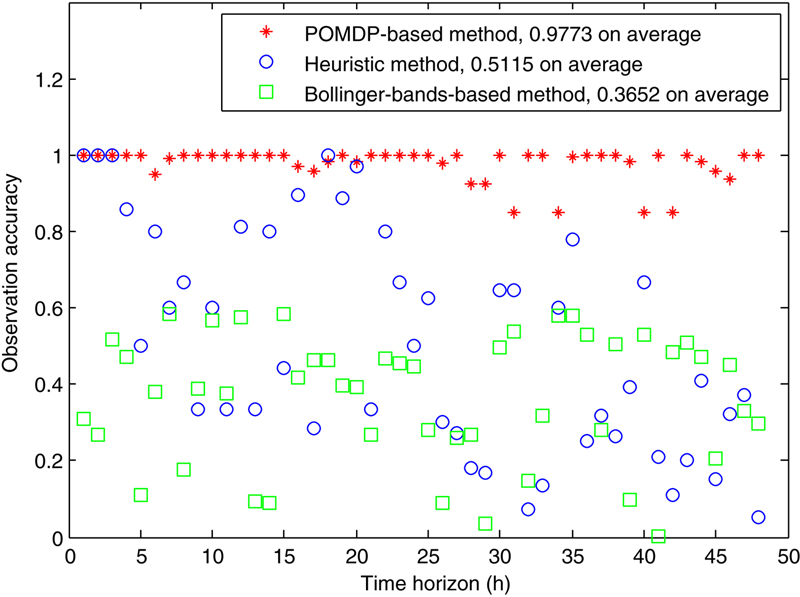
Table 10.3
Simulation Results of Detection Techniques
| Testcase | Parameter | No Detection | Bollinger Bands Method | Heuristic Method | POMDP-Based Method |
| 100-Customer | PAR increase | 32.1% | 4.03% | 6.85% | 2.87% |
| Normalized bill increase | 1 | 0.115 | 0.284 | 0.098 | |
| Normalized labor cost | — | 1.690 | 1 | 1.093 | |
| 200-Customer | PAR increase | 30.4% | 4.29% | 7.33% | 3.26% |
| Normalized bill increase | 1 | 0.118 | 0.289 | 0.102 | |
| Normalized labor cost | — | 1.601 | 1 | 1.074 | |
| 300-Customer | PAR increase | 31.8% | 4.47% | 7.82% | 3.24% |
| Normalized bill increase | 1 | 0.121 | 0.296 | 0.107 | |
| Normalized labor cost | — | 1.635 | 1 | 1.058 | |
| 400-Customer | PAR increase | 30.6% | 4.52% | 8.29% | 3.31% |
| Normalized bill increase | 1 | 0.125 | 0.309 | 0.112 | |
| Normalized labor cost | — | 1.669 | 1 | 1.087 | |
| 500-Customer | PAR increase | 31.3% | 4.57% | 8.40% | 3.42% |
| Normalized bill increase | 1 | 0.127 | 0.313 | 0.118 | |
| Normalized labor cost | — | 1.731 | 1 | 1.0816 |

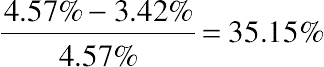 and the normalized bill increase by
and the normalized bill increase by 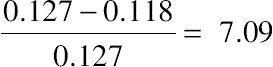 , while still saving the normalized labor cost by
, while still saving the normalized labor cost by  . This is because the Bollinger-bands-based detection technique is a general statistical data analysis method without considering the specific problem nature of the smart home pricing cyberattacks.
. This is because the Bollinger-bands-based detection technique is a general statistical data analysis method without considering the specific problem nature of the smart home pricing cyberattacks. and
and  , respectively, at the expense of increasing the labor cost by only
, respectively, at the expense of increasing the labor cost by only 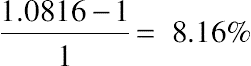 comparing with heuristic method since more smart meters need to be fixed. Again, the large improvements in detection accuracy, PAR and bill outweigh the small expense increase for our POMDP method. It demonstrates that our proposed long-term detection technique can more effectively detect the cyberattacks considering the cumulative effect, which cannot be handled by the single event detection technique. The results of the other testcases are shown in Fig. 10.12A, Fig. 10.12B, Fig. 10.13A, and Fig. 10.13B, respectively, which are similar with those 500-customer testcase.
comparing with heuristic method since more smart meters need to be fixed. Again, the large improvements in detection accuracy, PAR and bill outweigh the small expense increase for our POMDP method. It demonstrates that our proposed long-term detection technique can more effectively detect the cyberattacks considering the cumulative effect, which cannot be handled by the single event detection technique. The results of the other testcases are shown in Fig. 10.12A, Fig. 10.12B, Fig. 10.13A, and Fig. 10.13B, respectively, which are similar with those 500-customer testcase.8. Conclusions