In this chapter:
5.1 Inter-System Interface Requirement Pattern 51
5.2 Inter-System Interaction Requirement Pattern 62
5.3 Technology Requirement Pattern 65
5.4 Comply-with-Standard Requirement Pattern 71
5.5 Refer-to-Requirements Requirement Pattern 79
5.6 Documentation Requirement Pattern 81
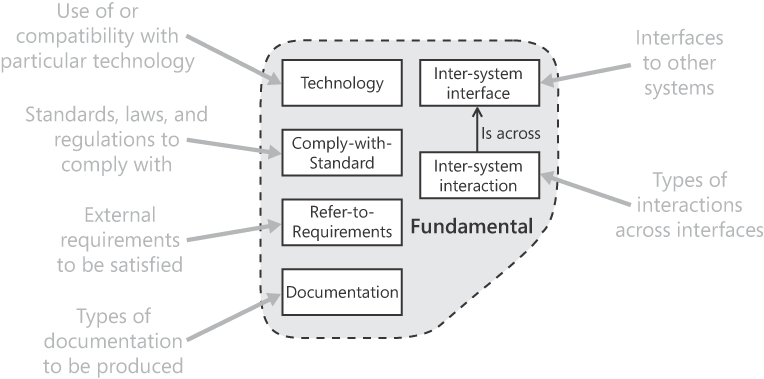
Fundamental requirement patterns are for various things that might be needed in any kind of system, as summed up in Figure 5-1.
Use the inter-system interface requirement pattern to specify basic details for an interface between the system being specified and any external system or component with which it needs to interact.
Do not use the inter-system interface requirement pattern for user interfaces (though you can treat interactions to user devices and user interface infrastructures as inter-system interfaces if they behave in a similar way to an external system). Also, do not use this pattern for internal interactions between different parts of the system, unless an external system might participate in those interactions at some time in the future (that is, if it might become an external interface).
Getting one system to cooperate with another can be a time-consuming and unpredictable undertaking. Developers might have little idea how hard it will be to implement a particular interface until they get their hands dirty. If we're using an interface defined by someone else, it might not do exactly what we want or might not work as we expected; if we're designing the interface ourselves, we're dependent on the owners of the other system to implement it properly. As a result, it's important that we treat inter-system interfaces with respect and that we don't underestimate their complexity: give them plenty of visibility, pin them down as early as possible, and allocate them sufficient resources. Often these don't happen, in many cases because the requirements specification glossed over the interfaces—or even failed to recognize some altogether. As a result, a system's interfaces might be weak links.
This requirement pattern cares neither about the nature of the interface nor whether the external system is local or remote. It uses the general term "interaction" to describe an activity across the interface (which usually means an exchange of information).
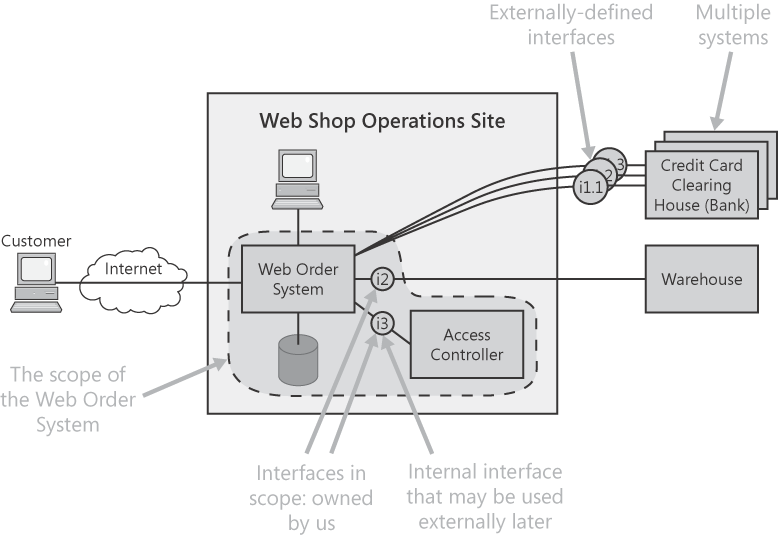
Every requirements specification should contain a system context diagram, and it should be near the beginning. (See the Scope section in Chapter 2.) This is where interfaces make their first appearance, so take the opportunity to give them star billing. On the context diagram, show all external systems (and other components) with which our system needs to interact, and label every connection to them explicitly with an interface ID. Figure 5-2 shows a sample context diagram with features related to interfaces indicated.
There are several points to observe. First, each interface is identified by its unique interface ID (using the convention described in the Content section later in this pattern). Next, each interface ID is either inside or outside the boundary line of the system's scope. Every interface must eventually be either wholly inside or wholly outside. If ownership of the interface has yet to be determined, the interface can be shown straddling the scope boundary; highlight this unresolved issue with a large question mark. Finally, when there are multiple similar systems to which to interface (such as the multiple credit card clearing houses in Figure 5-2), each must be treated separately, because they are all different. The connection to each is a separate interface. Don't lump an indeterminate number together. See the Interface Adapters section that follows for a discussion on how to handle interfacing to multiple systems for the same purpose. If we need to be able to handle multiple instances of a particular type of interface, then there are various extra factors to consider—such as deciding which to use and when. These factors are discussed in the extendability requirement pattern in Chapter 10 .
Between two systems, there might be more than one interface (for example, a custom messaging protocol for transactions and email for sending monthly reports). Treat each different communication medium as a separate interface, because they'll have to be built and tested separately and will function independently.
Interfaces that are wholly within the system's scope (and don't involve any component outside that scope) normally don't need to be dealt with in requirements. One exception is if development is to be split between multiple teams (especially if one team is not in-house or if the teams are physically remote from each other). Requirements can only deal with this if it's known at requirements time and if the system is clearly segregated—in effect, if we're specifying a "federation" of systems. Another exception is when we envisage part of our system being spun off in the future and used by other systems (as for the Access Controller in Figure 5-2).
If interfacing to a third-party system, it is reasonable to define requirements that its supplier must satisfy: documentation, performance, availability of a test system, test accounts and so on—everything we need to be able to build and test our end of the interface. Bear in mind that third parties might have very different standards and abilities from those of your organization; they might be capable of meeting far higher professional standards than you need—and might charge you accordingly if you use them. At the other end of the scale, they might have poorer practices and skills than your own developers.
An inter-system interface requirement contains the following:
Interface name Give each interface a concise meaningful name—something convenient for people to use in discussion.
Interface ID Give each interface an identifier that is unique within the scope of this system so it can be easily and unambiguously referred to. One convention that works well is using "i" (lowercase to distinguish it from the numeral 1) followed by a sequential number. Where multiple interfaces serve the same purpose, use a two-part number, where the first identifies the purpose and the second distinguishes the interfaces (such as i1.1, i1.2, …).
The system at each end It's possible for the same interface to appear more than once on the system context diagram. But show the same interface ID only if two interfaces serve the same purpose. In this case, explain the roles the two systems play in the interface, or cite each pair of systems explicitly.
Also identify which of the two systems can initiate an interaction; both might be able to.
Interface purpose(s) Describe each distinct purpose—all of them.
Interface owner Which organization is responsible for the definition of the interface? It could be designed cooperatively, but one organization should be the ultimate arbiter (to avoid misunderstandings and to settle arguments definitively). See the previous section titled "The Ups and Downs of Interface Ownership" for the relative merits of owning or not owning the interface's definition.
Standard defining the interface (if any) Also state its version explicitly. Refer to the comply-with-standard requirement pattern later in this chapter for guidance on what else to say about the standard: the location of the standard, in particular.
Technology to be used for the interface (if relevant ) If particular technology must be used for the interface, describe it. Otherwise omit this item: don't make technology choices. See the technology requirement pattern later in this chapter for further details on what to say.
A single requirement like this usually isn't sufficient to fully specify the interface (although it might refer to a standard that does). Its main role is to give the interface "official recognition," so it's treated with the respect it deserves.
Summary | Definition | |
|---|---|---|
«Interface name» interface («Interface ID») | There shall be a clearly defined interface (called «Interface ID») between «Component 1» and «Component 2». |
1. «Interface purpose 1». 2. … Interactions across this interface can be initiated by «Initiating components». This interface's definition is the responsibility of and owned by «Interface owner organization». [This interface shall comply with version «Standard version» of the «Standard name», whose definition can be found at «Standard location».] [«Technology statement».] |
Summary | Definition |
|---|---|
Payment clearing interface (i4) | There shall be a clearly defined interface (called i4) between the system and payment clearing houses. It is invoked by the system only. Its purpose is to allow a customer to pay for an order. Ownership of this interface is within the scope of the system. |
There shall be a clearly defined interface (called i5) between the system and an external alarm monitor. It is invoked by the system only. Ownership of this interface is within the scope of the system. Its purpose is to notify appropriate personnel of any event that is relevant to them (which usually means only serious problems). | |
There shall be a clearly defined interface (called i6) to an external accounting system. It is invoked by the system only. Ownership of this interface is within the scope of the system. Its purpose is to pass accounting entries (or information from which accounting entries can be generated) resulting from all activities in the system that have financial consequences. | |
Certification authority interface (i7) | There shall be a clearly defined interface (called i7) between the system and a certification authority (CA). It is invoked by the system only. Its purpose is to verify a digital certificate presented by a customer. It shall be possible to support multiple CAs (for example, eSign, Baltimore). Each CA shall prescribe its own interface (though at least some are expected to use the PKCS #10 standard—see http://www.rsasecurity.com/rsalabs/pkcs/pkcs-10 for details). |
An inter-system interface requirement might be followed by several extra requirements, although sometimes none are needed. Run through the following list of topics to see which you need to address:
Individual types of interaction The main interface requirement states the purpose(s) of the interface, but you might wish to say more about the main types of interactions. There might also be secondary interactions that deserve a mention; apply the inter-system interaction requirement pattern for each one.
Throughput How much traffic must the interface be able to handle? Follow the throughput requirement pattern.
Scalability How well must the interface cope with increases in throughput? Follow the scalability requirement pattern.
Extendability Do you need to be able to slot in extra interfaces of this type? This has been referred to several times in this requirement pattern. If you do, write suitable requirements as described in the extendability requirement pattern.
Also, do you need to be able to switch the interface on and off? And what configuration parameters does it need? The extendability requirement pattern tackles these questions, too.
Resilience and availability Do we need to detect missing or duplicated traffic? How well and how quickly must the interface recover from a failure? During what hours does it need to be running?
Traffic verification and recording Must we be able to tell exactly what was sent and received? To prove we sent or received something? Or that the other system acknowledged receipt of something?
Upgrading What happens when the interface changes? Must we be able to support old and new versions simultaneously?
Security An interface is a door into (and out of) our system. To what lengths must we go to verify access and to stop intruders? Are we worried about strangers getting their hands on the information that is passing along the interface?
Documentation and third-party interface development If you're defining the interface, how are you going to tell the developers of the system(s) at the other end what they need to do? How will they test their part?
The first four topics are covered in their own requirement patterns; each of the last five is discussed in its own subsection that follows. This list looks daunting, but it isn't as tough as it appears. The requirements for a typical interface need worry about few of these topics; most can be left to the development team to sort out.
The extra requirements are most readable if they immediately follow the main requirement for the interface to which they relate. But it can be beneficial to group all the main inter-system interface requirements together and then have the extra requirements later on (perhaps even in a later section of the requirements specification). This has the advantage of giving a clear overview of all the interfaces in one go without getting bogged down in the details.
Most interfaces involve some sort of communications mechanism, which occasionally have traffic hiccups. Resilience in an interface means being able to identify anomalies and deal with them: to spot when messages are missed and ask for them to be re-sent and to spot duplicate copies of messages. Some message protocols and other types of interfaces take care of these things for us, but if you want to play it safe, you can write a requirement demanding this kind of resilience, which acts as an instruction to the developers to take care of it. The requirement needn't worry about how it's achieved. If the developer knows that the underlying messaging protocol handles resilience already, there's nothing more they need to do.
Here's an example interface resilience requirement:
Summary | Definition |
|---|---|
Warehouse interface fixes omissions | The interface between the system and the warehouse (i2) shall detect missing messages and arrange for them to be re-sent and shall detect and ignore duplicates of messages already received. |
Requirements for the availability of an interface—both its normal availability window and downtime targets—can be written in the same way as for the availability of a system as a whole. Follow the availability requirement pattern but limit your focus to the interface only. Clearly identify the interface to which each resulting requirement relates.
This is a mixed bag of features that collectively act as a sort of passport control for the interface. They come into play once messages have safely completed their journey (or before they set out). Consider whether you need to do any of the following:
Verify the identity of the sender This could mean the identity of the other system, the organization to which it belongs, an individual (such as the author of an email)—or all these things.
Record messages (logging) Think about incoming and outgoing traffic separately: do we need to know what we sent? Do we need to know what we received? Do we need to record all types of traffic, or just some? The volumes might be large if we record everything, making it awkward to store and harder to find an individual message—even if only marginally so, in this high-capacity age. Refer to the chronicle requirement pattern in Chapter 7 for information on what to say.
Record acknowledgment of receipt This is a special case of recording a message for the special purpose of being able to prove that the other party received the information we sent them. It can be used, for example, along with other steps, to prove that both they and we possessed particular information (or a document or another resource) at a particular time.
The motivation for such steps is sometimes legal: to provide proof that another party requested, saw, possessed, or did something. This being so, you need to understand the level of proof needed in your country (or in all the countries in which your system will operate). You might be in for some nasty surprises. You might, for example, need to record messages on a write-once read-many (WORM) medium, to prove that it hasn't subsequently been tampered with.
Here is an example requirement for each of the three topics discussed:
An interface can be tough enough merely to get going in the first place, so why on earth would you want to change it? Well, the functionality might need to change, or a new version of an interface standard might come along. There are two strategies for switching over to a new version of an interface:
- Strategy 1: Change the software at both ends of the interface at the same time.
This is the easiest option to implement, but it demands careful coordination of the upgrading of the systems at both ends. It's often impractical even if only two systems are involved, and it becomes steadily more impractical as the number of systems grows.
- Strategy 2: Have each participating system accommodate both the old and new versions.
This is necessary until every system has stopped using the old version, and then it can be dropped. If it takes a long time to switch all systems (or, indeed, if some never switch), then more than two versions must be supported at once. The complications don't end there: to be smart, each system needs to be able to tell which version(s) are supported by each other system it talks to. This involves storing this information and/or including an interaction that allows a system to ask another system what it supports. Life is easier if interactions of this sort are present in the first version of the interface.
These sound like design questions, but they must be addressed in the requirements because they affect external systems. If an interface development guide is written, it should say which strategy is to be used—although it is conceivable for one version to use a different strategy than the previous version used.
For an interface not owned by us, the requirements should say the extent to which we are committed to keeping our system compatible with future versions of the interface. If nothing is said, readers can reasonably assume the system merely has to work with the stated version (or whichever is the current version when the system is built). Refer to the comply-with-standard requirement later in this chapter for further discussion on this subject.
Here are example requirements for strategies and situations discussed in the preceding section:
Summary | Definition |
|---|---|
Any change to the interface between the system and the warehouse system shall be installed simultaneously by both systems. The intent of this requirement is to simplify the interface and its implementation by eliminating the need to support more than one version of it at a time. | |
Multiple versions of affiliate interface | The system shall support multiple versions of the affiliate interface concurrently. All versions of the interface released within three years shall be supported. The intent of this requirement is to avoid forcing all affiliates to upgrade whenever a new version is released, and to have to do so at the same time. |
Credit reference interface upgrade | Whenever the credit reference agency releases a new version of the interface to its credit reference service, the system shall be amended to use the new version. Amendments of this nature shall be installed within three months of the new version being released. |
Whenever the subject of security arises, it's likely to be complex and tricky. This little section has no pretensions to being systematic or comprehensive; it merely raises a few issues for you to consider. Let's divide the problem into two parts: the communication medium used by the interface and the traffic that travels along it.
The communication medium used by the interface needs to be protected to prevent intruders from using it to gain general access to our system (hacking in). Requirements can easily address this in solution-independent terms. (No mention of firewalls or virtual private networks or such here!) Unfortunately, it's difficult to decide or express how much protection we need: it can't be quantified. Here's an example requirement of this kind:
Summary | Definition |
|---|---|
Warehouse interface intrusion protection | The communications medium used by the warehouse interface (i2) shall be protected to prevent an intruder from using it to gain unauthorized access to the system. |
As for the traffic, there are various kinds of attacks we could be subjected to, but they boil down to the active and the passive. In an active attack, an attacker modifies the traffic: creates bogus messages, modifies genuine messages, or prevents the transmission of traffic. A passive attacker simply listens to our traffic to get hold of sensitive information. You need to write a requirement to protect against each type of attack you're worried about. Again, specify what you aim to achieve: avoid specifying in terms of solutions—though you can mention an approach if it's obvious. (Common approaches include encryption to prevent the reading of information, hash codes to detect tampering, and digital signatures to verify who sent messages.) Here are a couple of example requirements:
Summary | Definition |
|---|---|
It shall be possible to detect bogus traffic on the warehouse interface (i2). Bogus traffic is any message that was not generated by one of the components legitimately participating in the interface, or any message generated erroneously by a legitimate component. | |
Warehouse interface traffic not readable | It shall not be possible for an intruder who can listen to the traffic across the warehouse interface (i2) to read its content. (It is anticipated that this be achieved by encrypting all messages.) |
In sensitive applications, an eavesdropper can glean useful snippets merely by knowing that there is traffic or knowing its quantity—but this is unlikely to be a concern in commercial environments. If it is, engage a security expert to work out your security requirements
If we own the interface, the developers of the system(s) at the other end will need to know what to do, and it's our responsibility to inform them. This means we need to write some kind of "Interface Developer's Guide" for this interface—even if it's rudimentary. How thorough a job we need to do depends on who they are and how many of them there are: if we're building a product, and lots of customers will be implementing this interface, we'll need a slick and comprehensive guide; we don't want our developers spending all their time explaining it over the phone or in emails. Here's an example requirement for an interface developer's guide:
Summary | Definition |
|---|---|
Warehouse interface development guide | A development guide shall be written containing sufficient information to allow a competent software engineer with suitable skills to develop software that implements the warehouse interface (i2). |
This sort of requirement is very similar to requirements to allow third-party development of drivers, as described in the extendability requirement pattern. See also the documentation requirement pattern, discussed later in this chapter, for further details on what to say.
The external developers also need to be able to test their interface software. This probably means making a test system available for them to use and running it for as long as necessary. If we're writing software to help test the interface, perhaps we can make that available to them—which involves packaging it up neatly. Last, the developer's guide needs to explain all these testing issues. Write requirements covering everything that you decide is needed, and point out suggestions that were rejected.
When designing an inter-system interface, start by running through the topics in the list at the start of the "Extra Requirements" section of this pattern. Some of these topics might be covered in requirements, but most probably aren't. A well-rounded interface design and implementation take these matters into account and can cope without panic when changes are made in the future.
Consider writing software to simulate the interface (and the system at the other end). The value of this depends on the importance of the interface (does your company's future depend on it?), its complexity, and the availability of a test system by the other system's owners. Testing error conditions can be difficult and tedious; some are impractical to cause at all. Sometimes it's useful to have the test software simulate certain types of errors. (One system I worked on let us specify, in the messages themselves, the type of error to simulate during testing. This was very powerful. But we had to take great care that all trace of this feature was removed—compiled out—before the software went into production. I'm not promoting this approach.)
The organization who builds a system must test every component, within the system's scope, that participates in the interface. Treat each participating component separately. Identify, from three sources, all the kinds of interaction that can occur across an interface:
Explicit interaction requirements (as per the inter-system interaction requirement pattern that follows).
Implicit interactions, which help to satisfy goals stated indirectly. For example, resilience, traffic verification and security requirements (and possibly others) might involve additional kinds of interactions.
Interactions not discernable from the requirements at all.
See the inter-system interaction requirement pattern that follows for more about how to test each kind of interaction.
Most commonly, one end of an interface is outside the scope of the system being implemented. Check that a test "other end" system is available. Things become tricky and risky if not. This is often an important issue—especially when dealing with big, powerful organizations such as financial institutions (to test, say, credit card transactions) and government bodies. Sometimes, it even becomes necessary to build a working simulation of another system, which can involve considerable extra time and effort.
See the previous Considerations for Development section. Encourage the development team to build software to test the interface, and then make use of it. But don't rely on test software of this sort for all testing, in case it's incomplete or doesn't simulate the interface faithfully.
Use the inter-system interaction requirement pattern to specify a particular type of interaction across an inter-system interface.
A typical interface involves a range of different types of interactions. A credit card payment service might exist primarily to enable retailers to debit a cardholder, but its interface will do various other things, such as reverse a transaction and check a card's credit limit. These are business-related functions, but the interface might also possess a number of more technical and supporting interactions: initiating a connection (and shutting it down); requesting resend of a previous message; notifying status; and so on. An interaction type, for the purposes of this requirement pattern, means the exchange of a particular type of information—which could involve messages in both directions. For example, a request and corresponding response count as an interaction.
Whether we want our requirements to address specific types of interactions depends very much on who owns the interface. There are four distinct situations in which we might find ourselves, and they have a direct bearing on our reasons for wanting to specify individual types of interactions, which in turn affect how much we should say:
Situation 1: We own the interface. It's our responsibility to make the interface complete, so use the requirements to prevent something from being forgotten. You don't have to scratch your head trying to think of all the secondary interactions the interface needs; certain capabilities can be stated in very general terms.
Situation 2: We don't own the interface but can influence its design. Use the requirements to identify and describe features we'd like to see in the interface. Treat the interface owners as the primary audience for these requirements, so aim to make a strong case for the inclusion of each one.
Beware that each of these requirements is outside our control, so until the interface owner accepts it, we don't know that the interface will satisfy it.
Situation 3: We don't own the interface and cannot influence its design, but know what it looks like. Rather than force all readers of the requirements specification to refer to the interface specification to understand what it involves, it can be useful to sum up the individual interactions in requirements. Our requirements can capture the essence of the interface—to make effort estimation easier, for example. The earlier we get a feel for the difficulty of implementing this interface, the better.
Alternatively, you can write an informal summary of the interface rather than formal requirements. (You still must include it within the requirements specification, though.) This gives you the opportunity to include subjective judgments (such as on the quality of its documentation, its overall complexity, and so on). You could ask a developer to study the interface and write a summary.
Situation 4: We don't own the interface, cannot influence its design, and don't know what it looks like. This is a risky situation to be in, but it happens. We're obliged to commit to building an interface without knowing what it involves—how extensive or tricky it will be. Flag this as an area of concern, and do all you can to obtain the necessary information as quickly as possible. We won't be able to write interaction type requirements until we know what the interface looks like.
An inter-system interaction requirement needs to contain the following:
Interaction type name This allows us to refer to it.
Interface name and ID The interface over which the interaction occurs must be clear; the requirement's context (for example, following the interface's main requirement) is not enough. When referring to an interface, mention its interface ID to prevent misunderstanding.
Interaction purpose Describe what this interaction is for. Make clear who initiates it.
The information to pass This needn't be comprehensive. (Indeed, sometimes there's no need to say anything at all.) Concentrate on the important information. If the interaction involves flows of information in both directions, you can spell out what each one contains—but if the requirement grows too large (perhaps over half a page), split each flow into a separate requirement.
Summary | Definition |
|---|---|
«Interaction summary» | The «Interface name» interface («Interface ID») shall «Interaction purpose description» [that passes at least the following information: «Information to pass»]. |
Here are a couple of example inter-system interaction type requirements for interfaces we own:
Summary | Definition | |
|---|---|---|
Raise alarm with alarm monitor | The alarm monitor interface (i6) shall allow the system to raise an alarm (that is, to pass an alarm message and cause all appropriate people to be notified). A raise alarm request shall include at least the following information: |
The alarm monitor shall respond with an acknowledgment (or an error response indicating that it has been unable to raise the alarm). |
Warehouse interface status | The interface between the system and the warehouse (i2) shall provide the ability to verify the operational status of both the interface and the warehouse system itself. |
Refer to the inter-system interface requirement pattern earlier in this chapter.
Refer to the inter-system interface requirement pattern for the big picture of testing an interface as a whole.
An inter-system interaction requirement specifies only what the interaction must achieve, its goal. The implementation might turn out to be more complex. For example, a requirement might imply there will be one request and one response, whereas in practice, it takes two of each. Therefore, testing an interaction requirementmust be concerned with only whether the goalis achieved, not the intricacies of the implementation. Additional testing should be done to verify that the physical interactions work properly. Data flow diagrams can be useful in devising tests for the physical interactions but will be less so for the logical interactions.
Formulate both valid cases and invalid (erroneous) cases. In the first case, identify valid but unexpectedcases. Does the interface deal properly with valid interactions that won't happen every day but can come along at any time? It's never possible to test every eventuality, but try to cover as representative a spread of situations as possible.
Related patterns: | Comply-with-standard, inter-system interface, accessibility |
Anticipated frequency: | Usually no more than six requirements |
Pattern classifications: | Pervasive: Maybe |
Use the technology requirement pattern to specify technology that must (or must not) be used to build or run the system, or with which the system must be capable of interacting or otherwise compatible.
Do not use the technology requirement pattern to make technology choices.
Technology is any externally-produced hardware or software that is used in building, installing, and running a system. That's what it means here, at any rate. Requirements must not make decisions about which technology to use; they must describe whatever is known about the technology landscape into which the system must fit—to constrain in some way the technology that can be used in the system. We can conveniently divide that landscape into the following three areas:
Area 1: To use in production Hardware, operating system, database, Web server, firewall, uninterruptible power supply, and any other paraphernalia needed to provide life support for our application software.
Area 2: To interact with in production Such as a Web browser. This includes indirect interaction, such as exporting files or data that are to be read by some other application (and vice versa, importing files).
All inter-system interfaces should be specified according to the inter-system interface requirement pattern. Each inter-system interface requirement must state the technology to be used for the interface, insofar as it is mandated.
Sometimes you need to make a judgment call about whether to regard something as technology or as a standard; some things can be regarded as both. For example, if our system needs to produce HTML pages to be displayed in a Web browser, are we complying with the HTML standard, or are we interacting (indirectly) with a browser? The best way to decide is to look at the underlying purpose: why are we doing this? If the purpose is to allow use of a Web browser, no one will care whether we use HTML (nor what version of HTML) providing the browser is able to present our output satisfactorily. In this case, specify the technology rather than the standard.
Area 3: To use in development Such as a programming language. Documenting, testing, and installing are regarded as falling within this area too. Common motivations for development technology requirements are
For the skills needed to build the new system to match those that the organization already has.
To be compatible with existing software (so we can reuse as much as possible).
To fit in with existing development practices.
To allow use of development tools already purchased and familiar.
Specifying development technology is most important when outsourcing development, especially if maintenance and ongoing development will be done in-house: constrain the external developers so the system suits our existing environment and skills. When developing in-house, we can usually rely on the development team to pick technology that is compatible with other systems and their skills, but not always. A developer might have their pet programming language or might just want the chance to learn a popular new skill—and you might have good reasons for keeping them to tried and true old ways. Carelessly introducing a hotchpotch of technologies contributes—invisibly, and probably significantly—to incompatibilities between systems—and thus inflexibility as well as extra development cost.
All requirements for technology to be used in development must have the highest priority; it's not practical to change these things after development starts.
It's not necessary to specify all this stuff—or, indeed, any of it. Just specify whatever is a given. The less we specify, the more freedom the development team has to pick whatever technology best fits the constraints placed upon it plus the goals of the system.
Where do technology requirements come from? We can expect demands for the technology that must be used (or not used) and interacted with in production to become apparent during the requirements process: someone's likely to mention them. On the other hand, we're likely to discover development environment matters only if we go looking for them—by talking to the development team. But that doesn't mean we should mechanically record such information: only specify it in requirements if there is a good reason to.
A technology requirement should contain:
Description of technology What technology are we talking about? This can be as specific or as general as appropriate. It doesn't have to name specific products. It can embody a formula for determining one product or more, in a similar fashion for working the version(s) of technology that must be supported, in point 3(c) below (though formulae of this kind can become intricate).
Usage of the technology What role must this technology play in our system? At a minimum, convey which of the preceding three areas it relates to (use in production, interact with, use in development). Usage can be negative as well as positive: "the system must not use such-and-such technology."
Version(s) of the technology (if relevant) Mentioning versions in a requirements specification is always problematic, because we don't want to tie the system just to specific versions that are liable to become out of date; neither do we want to make an open-ended commitment to each and every new version that might come along in the future. We also don't want to be unnecessarily specific or restrictive. There are three possible approaches:
Don't mention versions at all. Sometimes there's no point in making a fuss. If everyone's likely to understand what's needed and what is customarily involved when a new version of this particular technology is released, or if there won't be a problem whenever a new version comes along, there's little to be gained by talking about versions.
Mandate one or more specific versions. This is likely to be fine in the short term, but it conflicts with the goal of a timeless specification. What happens when a new version is released? Taken literally, the requirement says that any new version needn't be supported. But if that's what we mean, say so explicitly—because the average reader won't see it that way. If we expect the system to work with future versions, it's better to express the versions in a formula—which is approach (c).
Devise a formula, based around the most recently released version, that is expressed in terms that don't mention that version explicitly and that identifies one or more versions that must be supported. For example, we could describe the most recent version and the two previous versions, or all versions that have been, at any time in the past two years, the most recent version. Do your best to minimize the number of versions that must be supported at once. For example, you could add a caveat to rule out any version that was soon superseded (and thus not widely used).
Bear in mind that accommodating a new version might involve significant extra development effort. This, in turn, means there might be a delay between when that new version is released and when our system begins supporting it. If so, it's worth having the technology requirement grant the system some leeway, in case anyone expects instantaneous conformance.
Always give at least a little thought to the matter of versions, even if you end up deciding not to mention them in the requirement itself.
Motivation Why are we mandating this technology? The reasons for some technology requirements can be far from obvious; in fact, they are all liable to appear arbitrary if not justified in some way. People can have strong opinions on particular technologies (even stronger when they're negative opinions), so stating good reasons why one technology is essential can prevent a potentially vehement argument before it raises its head.
If the system must work with a range of technologies (for example, a couple of popular Web browsers), write a separate requirement for each one. This makes it harder for any one of them to be neglected (that is, it's easier to trace that each technology is supported), and it allows each one to be assigned its own priority.
Summary | Definition | |
|---|---|---|
«Technology summary» | «Technology description» shall be used for «Technology usage». [«Technology version statement».] | «Motivation statement». |
«Technology summary» | The system shall use «Technology description» for «Technology usage». [«Technology version statement».] | «Motivation statement». |
Use one of these templates as a starting point only. As the examples that follow demonstrate, the most suitable phraseology varies considerably depending on what an individual requirement says.
The following examples should not be regarded as advocating (or deprecating) any of the technologies they mention. This is not a coherent set of requirements that apply to one system: a few contradict one another. The second example demonstrates how expressing technology and versions in terms of a "formula" can be tortuous to specify precisely.
Observe that these examples are not divided into the three areas discussed (use in production, interact with, and use in development), yet mixing them up does not confuse the role of each requirement.
Some nonfunctional requirements that we wish to impose on our system also need to apply to technology that we use. In this case, write extra requirements for the purpose. One example is accessibility: our system can't be regarded as satisfying its accessibility requirements if some of its functions are implemented using a third-party product that doesn't satisfy them. (See the accessibility requirement pattern in Chapter 8 ) Write extra nonfunctional requirements for each of the technologies used. That's usually preferable to attempting to broaden the original nonfunctional requirements so they also apply to the technology used. The latter is certainly easier to specify, but it isn't helpful to developers because the work involved in building a feature into our own software is of a different nature than that of choosing a compliant product. It's equally unhelpful to testers for similar reasons.
Technology is too varied to be able to make suggestions here on how to tackle particular types. But it is possible to say a little about how to react to the two main kinds of technology requirement, because they are very different as far as development is concerned:
Technology the system uses (or must not use). This kind of requirement influences (often in profound ways) the process of building the system, including who will build it. For example, once you mandate the programming language, you need a development team competent in that language. But a technology use requirement typically has less effect upon the design of the system. For example, a given design could be implemented in many different programming languages.
When reviewing this kind of requirement, development representatives should check that adequate technology that satisfies the requirement can be found. Also check that the prospective development team has suitable skills to use this technology.
Technology with which the system must be compatible. This kind of requirement directly affects the software that needs to be built. It might mean that at least one developer must be (or must become) an expert in this particular technology. For example, if our system must interact with a particular credit card clearing service, someone will have to get to know it in detail and develop software for it.
When reviewing this kind of requirement, developers should scrutinize it and contemplate its implications. Try to get an early feel for how difficult it will be to implement.
As with development, the two main kinds of technology requirements place very different demands on testing:
Technology the system uses (or must not use). This is generally straightforward to test: for each technology requirement, find out what technology was used in that area, and verify that it's in accordance with the requirement.
Technology with which the system must be compatible. There are no shortcuts here: it must be tested in detail—occasionally in excruciating detail. For example, if the system must be accessible via a particular Web browser, then every type of page delivered by the system must work.
For both kinds of requirement, pay special attention to any requirement that insists that the system work with multiple different technologies (and/or multiple versions of each one), especially if the number of permutations looks impractically large. Be alarmed if two or more technology requirements have impact on each other, yielding vastly more permutations. This situation is likely to be hard to test—because you have to acquire, configure, and run all the technologies to test them. Then tests must be repeated for each one. It's tolerable for client technologies with which the system must interact (such as several Web browsers and browser versions). But it's a major headache when it relates to the system's own environment, such as testing that server applications run on several different operating systems or types of hardware.
Use the comply-with-standard pattern to specify that the system must comply with a particular standard.
A standard, for the purpose of this pattern, is any document or collection of documents that makes demands on how things in its sphere are to be done. It includes laws (tax, privacy, access by people with disabilities), government regulations, industry-specific regulations and codes of conduct, company standards, quality standards (such as ISO 9001), information standards (such as currency and country codes), and technical standards of diverse kinds (for example, file formats, communication protocols, and user interface conventions).
Comply-with-standard requirements tend to be very straightforward: you must comply with whatever-it-is. But more often than not, it isn't good enough to leave it at that, and you should write extra requirements that expound the implications. See the Extra Requirements section later in this pattern for more. (Note that this pattern has been named "comply-with-standard" for clarity: calling it the "standard" requirement pattern would invite misreading its purpose.)
Let's divide standards into a few categories for the purpose of saying a little about how to approach them:
Industry-specific legislation, regulations, and codes of practice Complying with these sorts of standard often involves a lot of work, which is justified because they usually have a major bearing on the central purpose of the system. But you might still be in for a nasty surprise when you find out just how extensive and tough they are, especially if you're new to the industry in question.
Legislation that applies to all companies within the jurisdiction to which it applies (Such as sales tax and financial regulations.) Usually, it's not necessary to study the laws themselves: turn to an expert in that area, such as the company accountant, lawyer, finance department, or auditors, to ask them what's needed. Often it's not necessary even to mention the laws that underlie the need to support taxes and such.
Company standards These are usually concerned with software quality and consistency, though they might mandate certain support functions (such as system monitoring). The line between company standards and company-mandated use of common software or common requirements can be blurred. If you have any control over these things, it's best for company standards to stick to nonfunctional matters, and to have common requirements specifications for the rest.
Technical standards(Such as file formats and communication protocols.) Normally, you don't need to go into detail here: if you find that building your system involves developing your own implementation of a general technical standard (when that is not central to the purpose of your system), it might be a sign that something's wrong. For example, if someone asks for the system to support a peculiar file format for which no off-the-shelf software is available, you should seriously question whether it's justified.
A requirement that mandates a standard should specify:
The name of the standard State the name clearly, such that it cannot be confused with any other standard. To achieve this, you might need to prefix it with the name of the organization who produced the standard (which means the jurisdiction in the case of laws and government regulations).
The purpose of the standard If the name of the standard does not convey its purpose, include a summary of what the standard is for. Usually you can do this apparently in passing (for example, "ISO3166, the international standard for country and region codes, …"). You can't expect your readers to know what an arcane code for a standard means, especially one that is numbered, and it's rude to force readers to go find out for themselves.
The version of the standard with which to comply If the system must comply with more than one version, or must comply with the latest version on an ongoing basis, see the preceding "Complying with Multiple Versions of a Standard" section for the extra factors you must consider. When specifying compliance with a law or government regulation, state the year it was enacted if it has no "version." If the system will only ever need to support one particular version of the standard and never any other version, say so explicitly—to avoid anyone having to worry about the awkward multiple version questions.
Parts of the standard with which to comply (if relevant) If the system need only comply with some parts of the standard, identify them—but be brief. If there are more than a handful of items to identify, do so using extra requirements. If you need lots of extra requirements, consider splitting them off into a separate requirements specification. Also identify any parts for which you have or might be able to obtain a temporary dispensation from compliance.
Location State where a copy of the standard can be found. Cite all sources likely to be available to members of the project team: the URL (Uniform Resource Locator) of a publicly available online source, hard copies (where they are stored, or who possesses them), the location of a soft copy on disk, and so on. It is advisable not to follow the location by a period ( "."), to avoid the risk of it being interpreted as part of the location.
If a suitable standard exists for a particular aspect of a system, it is generally a good idea at least to seriously consider using it before devising something in-house for the same purpose. If you're not sure whether a standard exists, go and look. There are plenty out there. (This is not quite the same as the famous saying, "The nice thing about standards is that there are so many of them to choose from.") A few good starting points are
http://www.iso.org: ISO, the International Organization for Standardization, produces a wide range of standards related to quality (the ISO 9000 series), company organization, and management, as well as industry-specific and domain-specific standards.
http://www.w3c.org: The World Wide Web Consortium is responsible for a wide range of standards that define key aspects of the Web and adjacent subjects, including many XML-related standards.
http://www.ietf.org: The Internet Engineering Task Force (IETF) manages the RFC (Request For Comment) standards which cover a broad range of software-related subjects, including many pertaining to the Web.
http://www.ieee.org: The Institute of Electrical and Electronics Engineers (IEEE) produces a very large number of technical standards, including many areas of computer technology, telecommunications and quality.
http://www.omg.org: The Object Management Group produces standards for software analysis and design (including the UML—Unified Modeling Language—standard), security, business modeling, security, and for a few specialized areas.
http://www.oasis-open.org: The Organization for the Advancement of Structured Information Standards (OASIS) has a range of standards related to XML and connected areas, including for business processes and security.
Summary | Definition |
|---|---|
Comply with «Standard name» standard | The system shall comply with [parts «Standard parts list» of] the «Standard description» standard [in order to «Standard purpose»]. «Standard version statement». Source: «Standard location». |
All the examples that follow relate to real standards (except for a couple for a fictitious company). They are divided into the four types already discussed: industry-specific, applicable to all companies, company-specific, and technical. Examples relating to accessibility legislation can be found in the accessibility requirement pattern. The first examples are industry-specific:
Summary | Definition |
|---|---|
The system shall protect the privacy of all protected health information in compliance with the privacy rule of the U.S. Health Insurance Portability and Accountability Act (HIPAA), 1996. Protected health information is any information about an individual that concerns their health, the provision of health care to them, or payment for health care. Source: http://www.hhs.gov/ocr/hipaa | |
HIPAA security | The system shall comply with the security provisions of the U.S. Health Insurance Portability and Accountability Act (HIPAA), 1996 with respect to the secure storage, use of and access to protected health information (as per the previous requirement). Source: http://www.hhs.gov/ocr/hipaa |
These examples demand compliance with various laws:
Summary | Definition |
|---|---|
The system shall comply with the U.S. Sarbanes-Oxley Act, 2002 (commonly referred to as SOX) to the extent of faithfully recording, protecting from improper modification, monitoring, and providing accountability for all activities within the system that have financial consequences. The intent of this requirement is to be confident that the financial information embodied in the system accurately reflects the business transacted by it, and to provide means by which auditors can verify the correctness of this information. Source: http://frwebgate.access.gpo.gov/cgi-bin/getdoc.cgi?dbname=107_cong_bills&docid=f:h3763enr.tst.pdf | |
The system shall protect personal information in accordance with the U.K. Data Protection Act, 1998. | |
All usage of information about customers and their activities, and exchange of this information between organizations, shall be in accordance with the provisions of the Australian Federal Privacy Act, 1988. Source: http://www.austlii.edu.au/au/legis/cth/consol_act/pa1988108 |
Here are a couple of example requirements for company-specific standards:
Summary | Definition |
|---|---|
All software shall be written in compliance with the company's coding standards for the programming language in which it is written. Whenever a new programming language is introduced, a suitable coding standard shall be adopted for it. | |
All Web pages produced by the system or written in association with it shall comply with the company's Web style guidelines. |
Here are example requirements for a few technical standards:
Summary | Definition |
|---|---|
Spoken languages shall be identified internally in the system by codes defined in ISO 639, the international standard for natural languages. (Note that this requirement does not cover the display of language choices to users—for which it is preferable to use the names of the languages.) | |
Countries and geographic regions (subdivisions) shall be identified internally in the system by codes defined in ISO 3166, the international standard for such codes. (Note that this requirement does not cover the display of countries and their subdivisions to users. It is strongly advised that only their names be shown unless there is a good reason to do otherwise.) Source: http://www.iso.org/iso/en/prods-services/iso3166ma/02iso-3166-code-lists/list-en1.html | |
The currency of all monetary amounts shall be identified internally in the system by codes defined in ISO 4217, the international standard for currency codes. (Note that this requirement does not cover the display of currencies to users. It is strongly advised that only currency names and symbols be visible to them unless there is a good reason to display the ISO code.) Source: http://www.xe.com/iso4217.htm | |
Digital certificates used for user authentication shall comply with X.509, the ITU-T's standard for public key and attribute certificate frameworks. (Note that this requirement does not mandate the use of digital certificates, merely that if they are used, they must be X.509-compliant.) Source: http://www.itu.int/itu-t/asn1/database/itu-t/x/x509/1997/ | |
PKCS #10 | Interactions between the system and Certification Authorities shall comply with PKCS #10 (RSA Laboratories' standard for the syntax for certification requests sent to a Certification Authority). It is recognized that PKCS #10 defines message syntax in an abstract manner (ASN.1), so compliance with it is not in itself sufficient for a given calling system to be able to talk to a given Certification Authority. |
The natural reaction to reading a typical comply-with-standard requirement is bemusement: what's it mean? What are developers and testers supposed to do with it? If it's clear, the original requirement will suffice. If not, someone has to figure out the implications for the system by going through the standard in detail—and for consistency and efficiency, it makes sense to do this only once, rather than having several people independently making their own, uncoordinated interpretations. That person should be the analyst, and extra requirements should be their medium. It still makes sense for representatives of the development and/or testing teams to verify the analyst's interpretation against the standard itself, but the importance of that depends on the nature of the standard. Also, a small project might not have the resources to perform a lot of double-checking.
There are three levels of detail at which compliance with a standard can be specified by using requirements:
A single requirement (As per this requirement pattern.) This suffices only if this requirement says all that needs to be said. For example a requirement that says "The 'Save as HTML' function shall produce output that complies with the HTML 4.0 standard, which resides at …" is sufficient. There's no need for the requirements to delve into the HTML 4.0 standard: it's clear to developers what HTML constructs are allowed, and testers can rigorously verify whether output complies.
A set of requirements in the system's requirements specification If only a handful of requirements are needed to specify in detail how to comply with the standard, then include them directly. In this situation, you can omit the comply-with-standard requirement itself—though it's advisable to preface these requirements with an explanation of what they're for.
A separate requirements specification If the standard's requirements are so numerous that they would cause the main specification to grow significantly, or they'd dominate it, create a separate requirements specification for them. Make this separate specification as general as possible: aim to specify what any system must do to comply with the standard—with a view to reuse. This isn't always possible, though, because you might write the requirements to suit the particulars of your system. So make clear whether the separate specification is suitable for reuse or not, and, if so, in what circumstances. (In an ideal world, standards would be written to be usable as requirements specifications in the first place—but I've never seen one that is.)
If you write a separate requirements specification for the standard, the original comply-with-standard requirement must identify the separate specification (its name, version, and where it can be found), and state explicitly that all its requirements must be satisfied. The comply-with-standard requirement then takes on the role of a refer-to-requirements requirement, and you should use that pattern instead.
Usually, you need to specify requirements for everything that the system must do to comply with the standard—just as if the standard were replaced by a customer who insists on everything in the standard. There are a couple of situations where it's not necessary to go into such detail: first, if you are outsourcing development to an external organization that can be expected to properly determine the implications of the standard for themselves; and second, if you intend to purchase a product. But beware of suppliers that comply with the letter of the standard but not its spirit. If you're worried about this, add requirements covering areas of potential concern.
Standard-related requirements needn't all have the same priority. For example, when a new standard is introduced, it might introduce its provisions gradually over time. (Some imposers of standards are reasonable!) Or a compliance auditor (say, for a government regulator) might grant dispensation from some demands for a given time (just like a health inspector granting a restaurant time to clean its dirty kitchen).
Some requirements that have been requested already might contribute to compliance with a standard. Add a note to this effect to each such requirement. Every requirement that contributes to compliance with a standard should say so explicitly, unless it is obvious from its context (such as being in a section of the requirements specification devoted to that standard).
If you're supplying your requirements specification to a third party (outside your organization), they must have access to all the standards you expect them to comply with. This means you must make internal organization standards available to them, and supply industry standards if the third party is unable to obtain them because they don't belong to the requisite industry body (or to save them the expense of buying them). Wherever possible, distribute copies of standards to third parties along with the requirements specification itself: it saves everyone the time of asking for and supplying them later, and it brings to light any supply problems before you suffer any embarrassment. Also bear in mind that standards can be relatively expensive, and those available only in hard copy can take significant time to order and receive. This can cause considerable difficulties if you're asking for responses (bids) from third parties, especially if you impose a closing date (for example, for a tender). This reinforces the fact that it's always helpful to your readers to spell out in detail the implications of a standard, so they don't have to pore over it themselves. It's a much better use of time for one person to figure out the implications than for multiple readers each to do it for themselves, particularly since they know less about the author's intent. It also minimizes differences in interpretation.
Many standards appear to be intentionally mean and bloody-minded. But if we consider they're nearly all written by people who aren't directly accountable for any unreasonablenesses, ambiguities, contradictions, and omissions in them, and who don't have to pay for or carry out the work necessary to comply with them—well, perhaps we should be grateful that standards aren't worse than they are.
Developers are strongly advised to consider the factors discussed in the Complying with Multiple Versions of a Standard section.
Be especially careful when a standard defines an interface (for example, for a communications protocol) or some other aspect of system interoperability (for example, when one system must read files produced by another system). It's very easy for two systems built to the same standard not to be able to talk to each other: it only takes very small differences in interpretation of the standard. If possible, coordinate development as closely as possible with the other organization(s) implementing the same standard.
Standards vary considerably, so testing depends on the nature of the standard. The key to thorough and sensible testing against a standard is to get to know it firsthand.
If requirements have been specified for all the detailed implications of the standard, the parent requirement for the standard itself need not be tested.
Related patterns: | None |
Anticipated frequency: | Up to six requirements, but usually fewer |
Pattern classifications: | Pervasive: Maybe |
Use the refer-to-requirements requirement pattern to specify that some or all requirements in an external requirements specification must be satisfied as if those requirements were present in the current specification.
A detailed requirements specification for a serious commercial system is a significant document that takes considerable effort to write and, equally importantly, to read and review. Moving certain parts into separate specifications makes it easier to deal with. Spinning off the less visible or more technical parts gives the main specification a clearer focus on the matters closer to the heart of the business, but at the risk of masking from key stakeholders the overall scale and complexity of the system. Improved clarity and manageability is one good reason for referring to external specifications. Another is that those specifications can be referred to by other systems, thus saving effort (via reuse) and increasing consistency between systems. A third reason is that a specification on a specific subject tends to be written more diligently than when it's an afterthought in another specification.
Make sure that the referenced specification is accessible to the whole audience of the current system's specification. If that's not possible, either create a version of the referenced specification that everyone can access, or copy the individual requirements into the main specification. Developers mustbe able to read all requirements that they are expected to satisfy.
A requirement that refers to external requirements needs to contain:
Name of the referenced specification Use the name the specification calls itself, with extra clarification if it might be confused with some other similar specification.
Version of the referenced specification This is essential. Without it, confusion might result if there's more than one version—or if a new version is produced later. Don't commit to a moving target: we're saying the requirements in this version suit us, and satisfying them is enough. In due course, it might well be beneficial to switch to a later version of the referenced specification—indeed, we might be obligated to—but do that consciously. It might involve software changes, which mustn't slip in by the back door: deal with them the same as you'd deal with any requirement changes.
Including the date of this version of the referenced specification is helpful, too.
The requirements that apply Must our system adhere to the whole of the referenced specification or just some of it? If all its requirements must be satisfied, say so. If not, clearly identify which parts must be satisfied—which is best done by referring to the IDs of the requirements that apply. If you need to refer to several sets of requirements, write a separate requirement for each set. If it's more convenient, you can identify those parts of the referenced specification that don't apply—that is, that all requirements must be satisfied except for those identified.
If only one or two requirements are referenced, you could copy them into the main specification directly; the convenience to the readers probably outweighs the drawback of duplication.
Location of the referenced specification Where does the specification live? State where it can be found.
Information about priority Give serious consideration to the priority of the referenced requirements; don't gloss over this subject. The referenced specification might define the priority levels that it uses in a different way than our current specification does. If not, we're lucky—and we can adopt their priorities directly. Otherwise, we need to state the priorities explicitly, either by assigning one priority to them all, saying which requirements have which priorities, or defining a translation between the priority schemes used by the two specifications.
If this information can be expressed concisely, put it in the requirement's "priority" column; otherwise, explain it in the requirement definition and say, "various" or something suitable in the "priority" column. If a normal priority level is placed in the "priority" column, then that priority applies to all the referenced requirements—though it helps to state this explicitly in the requirement definition.
Summary | Definition |
|---|---|
«Domain description» requirements apply | The system shall satisfy «Requirements that apply» specified in «Specification version» of the «Specification name», which resides at «Specification location». «Priority statement». |
Treat each applicable requirement in the external specification as if it were present in the current specification.
The suggestion in the Considerations for Development section applies to testing, too.
Related patterns: | None |
Anticipated frequency: | Up to 10 requirements |
Pattern classifications: | Pervasive: Maybe |
Use the documentation requirement pattern to specify that a particular type of documentation needs to be produced.
Documentation can be regarded as anything that is written about a system, no matter what form it takes—not just traditional documents. Online help, presentations (in Microsoft PowerPoint, for example) and comments and other annotations in program source code all count as documentation. Some people might dispute whether anything in source code should count as documentation, but the output from utilities like Javadoc—which generates a coherent set of HTML pages about a body of Java software—must certainly count as documentation, and it seems artificial to include some types of annotations of source code but not others.
For the purpose of this requirement pattern, it's also possible to extend the definition of documentation beyond what's written, to include instructional videos, interactive tutorials, and informative material in other media. In an increasingly multimedia age it seems inappropriate to place artificial limits on what counts as documentation in the broad sense.
A requirement for documentation should contain those parts of the following that are appropriate:
The name and/or type of the documentation. What's this sort of document called?
A description of what the documentation is to contain. Go into whatever level of detail is necessary such that any documentation that complies is likely to satisfy you.
The format or medium to use, which can be as precise as necessary (such as a Word 2007 document or HTML 4.0 pages) but preferably left as open as possible (for example, "a document" or "online").
The name of a standard to which this type of documentation must conform, if any (for example, use of company document templates), along with a description of where this standard can be found. This typically applies when a company has internal standards for particular kinds of documentation. Also explain the extent to which adherence to the standard is mandated (if relevant).
The language the documentation is to be written in, if this is not obvious. In some cases, it might be necessary to state the dialect to use, too (for example, for English, whether it should be British, American, Australian, or some other kind). For a multilingual system, some documentation might need to be provided in multiple languages, in which case those languages must be explicitly identified.
Summary | Definition |
|---|---|
«Document type name» | There shall be a «Document type name» that contains «Document description». [It shall be in the form of «Document format or medium».] [It shall comply with the «Document standard name».] [It shall be written in the «Language name» language.] |
Here are representative requirements for several common (and one or two uncommon) types of documentation. The mention of a type of documentation here is not a suggestion that it should be produced for every system.
A documentation requirement is usually self-contained. There are the following rare cases when extra requirements might be needed:
If special software must be written to support the documentation, specify requirements for that software.
If the system's software must be written in such a way as to facilitate a special kind of documentation, specify requirements for what the software must do. An example might be special software hooks to drive an interactive tutorial. Unless you find a dedicated product to help you do it, this kind of thing is very exotic and to be undertaken only if you really know what you're doing. Writing a requirement that says "There shall be an interactive tutorial" is not adequate by itself; you need to provide a better idea of how extensive and how fancy it needs to be—for which extra requirements are necessary.
If you are outsourcing the development of your system, you might want to insist on being able to tailor its documentation. This is especially true for online help, user guide, and other instructional material—although you might as well insist on it for everything except material within source code. Here's an example:
Summary | Definition |
|---|---|
Documentation tailorable by «Our company name» | It shall be possible for «Our company name» to modify any piece of documentation written for the system, except that residing inside program source code. |
The development team's biggest interest in complying with documentation requirements is in producing whatever is expected of them. When reviewing documentation requirements, check that those demands aren't unreasonable.
It is, of course, good practice to comment source code when writing it. It's also very helpful to the whole development team to make good use of tools that generate source code–based documentation (such as Javadoc) and to generate it for the whole system regularly as a matter of course (say, whenever a build of all the software is performed).
For the purposes of testing, we can divide documentation into four types, each of which needs to be tested in a different way:
Traditional This means the sort you can print out and read anywhere. Test by reading it and checking its accuracy and completeness. Non-interactive instructional material using other media (principally video and/or audio) can be regarded as falling into this category, in the sense that testing it involves scrutinizing it from start to finish.
Online Test help pages by calling up the help page associated with each function and checking it for helpfulness and for compatibility with the function to which it relates. If there is a requirement that says every online function must have help, you need to invoke every function to check compliance.
Within source code It's better to give developers responsibility for source code quality, including commenting, through peer reviews (though in some organizations testers also participate in code reviews). But if testers are asked to check that a requirement in this area is satisfied, it's not necessary to expect them to verify the quality of comments and other annotations in source code. If they exist and appear to be coherent, that's good enough evidence that developers are taking the trouble to properly document their source code.
Interactive Any form of documentation that permits the user to interact with it (such as tutorials) means you have to devise a set of paths through it to exercise all options at each decision point. This can be a major undertaking.
Also test that all documentation complies with any accessibility requirements. See the accessibility requirement pattern in Chapter 8.