In this chapter:
11.1 User Registration Requirement Pattern 284
11.2 User Authentication Requirement Pattern 295
11.3 User Authorization Requirement Patterns 305
11.4 Specific Authorization Requirement Pattern 308
11.5 Configurable Authorization Requirement Pattern 313
11.6 Approval Requirement Pattern 318
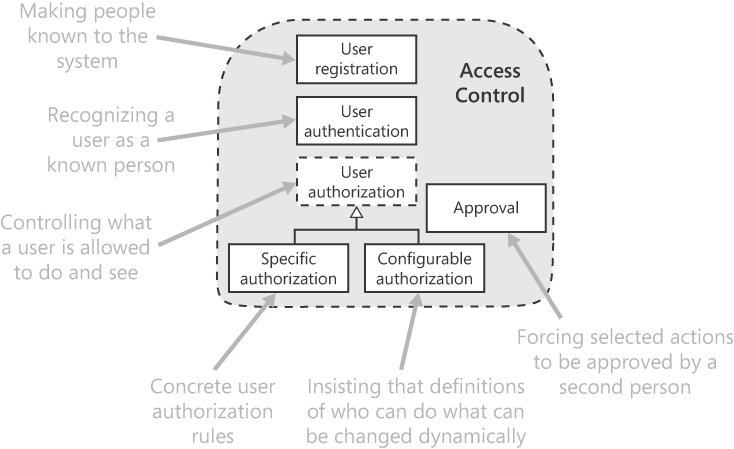
Access control lets us nominate all the people we're prepared to let in, check each one's identity when they visit, limit their access to only what they should see and do, and see who did what—so we needn't trust anyone more than we have to. These are essential features of almost every serious commercial system, and few do it well.
Access control comprises three main activities, which are the subjects of the following requirement patterns (as shown in Figure 11-1):
Making people known to the system (user registration).
Recognizing a user as a known person (user authentication).
Controlling what a user is allowed to do and see (user authorization). This is divided into two requirement patterns, because there are two different types of requirement: the first is for stating a concrete access control rule (specific authorization); the second says that the definitions of who can do what can be changed dynamically (configurable authorization), so you can avoid the nitty-gritty in the requirements.
In summary, registration decides which people we'll let in; authentication lets them in; authorization decides what they can do when they're in. The third is the goal, and the first two merely prerequisites.
There's one further requirement pattern in this domain: approval, for situations where one user needs to approve the action of another before the action is allowed to proceed. This takes us a little beyond strict access control, but it's so closely related that it fits comfortably within this domain.
Another important aspect of access control is recording who did what ("audit trails"). This topic is covered in the chronicle requirement pattern in Chapter 7 which includes several example requirements that relate to access control-related activities. Write requirements to demand that the use of all functions related to access control be recorded: it's hard to envisage reasons why you wouldn't.
Access control is the only aspect of security for which this book has requirement patterns, though there are many other aspects. The reason is that it's the only aspect that needs to be specified in detail in requirements, because access control forms an integral part of a software system itself. The recording of important "audit trails" in chronicles does, too, for the same reason. But most other forms of security can be implemented externally, like a cocoon around our precious software: a secure physical environment, firewalls, vetting of trusted employees, security procedures, and so on. You need to specify whichever of these things are within your scope—but little more than a straightforward statement of its necessity often suffices (for example, "The system shall be protected from external attack by a respected firewall product"). You can go into more detail if you like, but you must determine for yourself what else to say; that's beyond the scope of this book.
Access control-related requirements are necessarily often written by people who don't know a lot about security, because few organizations have a security expert on hand or can justify the expense of engaging one just to help write a few requirements. Fortunately, the requirements don't need to grapple with the intricacies of the subject or worry about the implementation challenges, which are considerable. As a result, neither do the requirement patterns here: they don't attempt to say what to do to make a system secure. So if you're going to bring in an expert, it can be more effective to do so after specifying the requirements. Anything to do with security is harder to achieve than it appears—because it doesn't merely have to function; it must also remain steadfast under attack, leaving no holes. Any bricklayer can build a wall, but one that resists determined assault is another matter.
Related patterns: | User authentication, user authorization, data structure |
Anticipated frequency: | One or two requirements |
Pattern classifications: | Functional: Yes; Affects database: Yes |
Use the user registration requirement pattern to specify how new users are registered (set up in the system), with emphasis on capturing those details by which a user can later be authenticated (log in).
Users are special. They are people, and they drive the bulk of what happens in a typical commercial system, so it's critical to know who each user is—to a greater or lesser degree of confidence depending on what we let them do. User registration, then, is more important than just another data maintenance activity. The primary aim of user registration is to record enough information to facilitate user authentication (login); everything else is secondary, though there could be quite a lot else to record.
Letting a user perform their own registration is the most convenient way, but anything they enter must be regarded as suspect (untrusted). They could supply false details (such as lying about their age), or they could enter details about someone else (which is, in some circumstances, a form of identify fraud). Alternatively, a user could be registered by a person who's already trusted, which is usually done when that person is in a position to attest to the prospective user's identity (such as if they're physically present). This is inherently much more dependable, so use it whenever it's practical (for example, for registering new employees). There is scope for more complex registration processes: to have some details entered by the user and some by someone else, or to check the veracity of certain information supplied by the user (against electoral rolls, credit reference agencies, the telephone directory, and such). This might sound invasive, but it depends on the nature of your system, the type of user, and how much faith you need in the accuracy of what the user tells you about their identity. These steps can raise the trustworthiness of the information in question, but they involve extra effort—both in operation and in development.
A user registration requirement should contain:
Class of users This identifies the type of user that is created by the registration process described by this requirement. If all users are registered in the same way, but the system treats different classes of users in different ways, explain how the user class is determined.
User details What information do we want to record about each user? You can either list every item individually, or refer to a data structure (as per the data structure requirement pattern) that defines them, or a mixture of both. Alternatively, some details can be defined in extra requirements. Indicate which information is mandatory and which is optional. Not all information about a user needs to be entered when they register: concentrate on what information the system must be able to handle, rather than on which items must be entered during registration. It's useful to divide this information into the following five categories:
Identification details, such as user ID, name, and email address—things used to distinguish this person from someone else. Sometimes other facts about a person are used to assist identification (for example date of birth), but they should be regarded as identification details in their own right only if they are essential to uniquely identify a particular person.
Authentication information, most commonly a password. It might be augmented by further information that's called upon if the user forgets their password (such as a "secret phrase" or a few questions and answers that an impostor is unlikely to know). These details indicate that a person who knows them when logging in is the same person who registered.
Criteria for an acceptable password can be stated here, or they can be the subject of a separate requirement. See the "Password Format" subsection of the Extra Requirements section of this pattern for suggestions on what to say.
Facts about the person (that aren't used for identification), such as date of birth, title, gender, address, and phone number(s).
If you use a biometric reader when authenticating a user, allow anyone who's physically incapable of using such a reader to be identified. (See the "Accessibility" point in the Extra Requirements section of the user authentication requirement pattern for more explanation.)
Preferences. Define a user preference for each aspect of how the system behaves that the user is able to control. We needn't force a user to express their preferences when they register, but it's a good opportunity to let them do so.
Access privileges, that define what this user is permitted to do and see. One way is for the user registration requirement to mention that one or more "roles" can be assigned to a user. This subject is covered in greater depth in the user authorization requirement patterns—though it is the registration process that assigns at least some initial access privileges to the user.
Registration process This can be as simple as entering information about the user, or it can involve additional steps. The latter are typically to check the correctness of what we know about this user, including obtaining evidence that the user who wants to be registered is actually the person whose details have been provided. (That is, they're not an impostor.)
Extra registration steps usually involve interacting with external systems (such as a credit reference agency) or manual activities (such as examining a faxed copy of an identity document). A commonly-used step is to send an email to the user's email address and ask for a response; this merely proves that this person receives the mail sent to that address. Describe whatever you need in your case.
Even one class of users could have more than one level of registration. You might have rudimentary registration for basic access, but ask for more (and check more thoroughly) if a user wants to do more (that is, to be trusted more). A user's access privileges can thus be affected by which stage a non-trivial registration process has reached.
Summary | Definition |
|---|---|
«User class» self-registration | A person shall be able to self-register as a «User class», by «Registration process description». They shall be asked to enter the following personal information:
|
«User class» registration | It shall be possible to register a person as a «User class», by «Registration process description». The following information shall be entered about them:
|
A user registration requirement can be accompanied by various kinds of extra requirements, most of which relate to the ongoing protection and maintenance of information initially provided at user registration. Consider which of the following areas you feel warrant requirements. Each area is discussed further in its own subsection that follows:
Password format What criteria must a password satisfy to be acceptable?
User de-registration If users can be created, it must also be possible to remove them.
User data protection How well must we protect personal and private information about people? Are there any data protection laws we must comply with?
Good security practices Are there any steps we want taken to encourage protecting user information? Are there any particular bad practices that we want to guard against?
Special processes for new users Is there any more to be said about the user registration process? Are there any situations that arise with new users (such as how to tell them their initial password)?
Day one considerations Who'll be able to use the system when it's first installed? Make sure someonecan—and that in doing so, no security hole is left open.
Any of these things that affect users should be documented, so they can read what they're supposed to do. The documentation requirement pattern has an example requirement for a security procedures manual.
Password Format Settling on criteria for an acceptable password involves making compromises. The best balance depends on the nature of your environment: how frequently users log in (and thus how likely they are to forget their password and need to write it down), the potential damage if a password is discovered, how likely an interested party is to discover a password that's written down, and so on. It can make sense to have separate rules for different classes of users: one for employees who use a system all day, every day, and another for visitors to a Web site. Making passwords convoluted makes them harder to guess, but also much harder to remember—and thus makes it much more likely that users will write them down. (Long passwords aren't necessarily unmemorable, though: a password made up of several words can be hard to crack, especially when accompanied by deviant spelling and with an unusual symbol or two thrown in.) Many apparently sensible steps that look like they improve security can actually have the opposite effect, especially when taken to extremes. Specify whatever password criteria you wish, but don't go overboard.
Summary | Definition |
|---|---|
Customer passwords shall:
All passwords shall be regarded as being case-sensitive. Thus typing "open1sesame" isn't good enough if the password is "Open1Sesame." These criteria apply to every function that can set or change a password. This requirement is based on the Windows Vista password complexity requirements as stated at http://www.microsoft.com/technet/windowsvista/security/security_group_policy_settings.mspx. |
Summary | Definition |
|---|---|
There shall be a table of values (dictionary of words) that may not be used as passwords. Any complete string in a password (that is, any complete sequence of alphabetic characters, but not substrings within an alphabetic sequence) that is an entry in this table shall not be allowed. |
For good measure, you could ask for a utility to hunt for poorly-chosen passwords:
Summary | Definition |
|---|---|
There shall be a "password guesser" utility that can be run periodically to create a list of all users whose password it was able to guess. |
Changing Password Users should be able to change their password whenever they want—for example, if they suspect that it's been compromised (because someone else might have discovered it). But unless you specify a requirement to this effect, the system is acceptable if delivered without a change password function. You might also want to force users to change their password from time to time or to restrict what they can change it to (such as not allowing the same value every time). The situation by which a user forgetting their password eventually leads to the password being changed is discussed in the user authentication requirement pattern's Extra Requirements section.
User De-Registration For each function that creates users, there needs to be at least one function that removes them. Normally it should be possible to de-register them in the same manner as they were registered—which means that if a user can self-register, they can de-register on their own initiative; and if a user is added by someone else, then someone else must be able to de-register them. It might be worth writing a separate de-registration requirement for each relevant class of user, as in the following two examples:
Summary | Definition |
|---|---|
Customer de-registration | A customer shall, provided they have no outstanding business, be able to de-register, after which they shall never be able to use the system again (unless they re-register). A customer is deemed to have outstanding business if their account has a non-zero balance or if they have one or more incomplete orders. When a customer is de-registered, all information of a personal nature held about them shall be deleted (except insofar as it is needed in order to comply with other legal or regulatory demands). Contact details (such as physical address or email address) and transaction details shall not be regarded as being of a personal nature for the purposes of this requirement. |
Employee de-registration | It shall be possible to de-register an employee, after which they shall never be able to use the system again (unless they are re-registered). |
User Data Protection We return to the theme of users being special, this time not because they drive the system, but because they are people who are sensitive about what is known about them and about how information about them is used (and not abused). A well-specified system (and a responsibly-run business) will provide reasonable protection for user information, but that might not be enough. You need to worry about data protection and privacy laws that make further demands. These vary considerably around the world, so don't assume that what's acceptable where you live is good enough everywhere. Europe is generally stricter than the rest of the world, for instance.
Data protection is a large topic in its own right, deserving of more than this backwater subsection. But there isn't space in this book to do it justice, so we'll confine ourselves to suggestions on how to tackle this subject, list a few general guidelines, and give a few example requirements.
Here's a basic high-level process for specifying data protection requirements:
Find out which countries' data protection laws apply to the system. Obviously this includes the country (or all countries) in which the system is to be installed, but that might not be all. For instance, European Union data protection provisions extend to data recorded about EU residents by systems outside the EU.
Investigate the implications of all the applicable data protection laws, and write requirements for them. It's not good enough simply to write requirements that say, "such-and-such a law shall be complied with"—because that encumbers someone else with figuring out what it means. (See the comply-with-standard requirement pattern in Chapter 5 for more.)
Ask whether all demands of all data protection laws must apply from the first day the system operates, or you can obtain some leeway and postpone delivery of some features. Assign priorities to requirements accordingly.
Think beyond strict legal demands. Are there any practices that could cause your company embarrassment or loss of business if they became known? If so, write requirements that prevent these practices or render them unacceptable by the system. Laws that are tougher than any you need to comply with can be a source of ideas: they do, after all, exist to protect people. A list of a few key provisions follows. What's popularly regarded as acceptable can (and does) vary from one country to another, too.
If, along the way, you spot that a business activity that your organization is contemplating (or conceivably might contemplate in the future) could be illegal in some jurisdiction, don't let it pass. For example, you might be concerned that your company could be tempted to earn extra revenue by selling customer data. Deal with it either via a requirement, an informal note in the specification, or by bringing it the attention of senior management (depending on how likely or unlikely you feel it is to happen).
Some of the key data protection provisions are:
Capture only those personal details that you actually need and use.
Don't capture sensitive data about any person (unless it's vital to that person's use of the system, and they agree to it).
Don't use personal information for any other purpose than that for which it was gathered.
Let people know how information about them is used. In general, when a person supplies personal information, they are implicitly giving their approval for it to be used thus. But it might be appropriate for you to go further and ask them to express their consent. If the information is to be used in multiple ways, consider whether to let the user to choose which they accept. For example, you could let them opt out of receiving emails of various kinds.
Delete personal information as soon as it's no longer needed (including out-of-date and incorrect—and subsequently corrected—information). Because there could be other laws that mandate that we retain financial information for several years, there might be some data that we must keep and some that we must not.
Make provision for a person to see what information is held about them.
Store information about people only in the country in which the main system resides; don't move it to any other country.
A system that's built sensibly shouldn't have difficulty complying with these provisions. Don't regard this list as complete, though. Here are example requirements covering a few of these steps:
Summary | Definition |
|---|---|
The system shall not record any sensitive information about any person. For the purposes of this requirement, "sensitive information" shall include all of the following:
These provisions are in accordance with the U.K. Data Protection Act (1998), which is in line with European Union Directive 96/46/EC on data privacy. See http://www.dataprotection.gov.uk. | |
Explain use of personal information | There shall be a Web page that describes how the system uses the information it knows about a person, and the ways in which personal information is protected. |
Let a person see information about them | It shall be possible to print out all the information the system stores about a selected person (except secret items used expressly for authentication, such as their password). The motivation for this requirement is to be able to respond to a person's request to see what information is held about them. Manual processes are needed to verify that the request comes from that person and to then furnish the print-out to them. |
Good Security Practices First of all, we want passwords to be handled securely. Requirements can't guarantee this, but you might want to force developers to make some basic precautions, as these two examples do:
Then you might want to outlaw a few bad practices such as loopholes, ways to bypass security precautions, and proliferation of software that asks users to enter secret information (such as their password). There are situations in which developers might be tempted—for honest reasons—to do something that weakens security. A few examples are:
Special Processes for New Users Whenever a user is set up by someone else, we have the pesky problem of how to assign a password that only the new user knows, without the risk of someone else logging in as that new user first. Options include:
- Option 1
Have the system automatically generate a password for the new user, which is then told to them. One way is to use a simple algorithm for the new password (as in the second preceding example user registration requirement), and for the new user to be told that algorithm. Always insist that a different password be generated for each user, rather than a standard password being used for everyone—because of the risk of the latter becoming widely-known. A second way to tell the user their password is to display the new password to the person setting up the account, who then tells the new user.
- Option 2
Ask the new user to choose a password and type it in when their account is being set up. This insists that they be physically present, and runs the risk of the other person watching them enter their password—but at no time is it possible to log in as the new user with an artificial password.
- Option 3
Ask the user to type their chosen password into a special preregistration function, which makes it available for the registration function to pick up later. Such a function must comply with all requirements for the secure handling of passwords (such as storing them in an undecipherable form).
The second option doesn't need extra requirements. Here are a couple for the first option:
Day One Considerations More than a few systems have been installed and started up on their first day—only for the project team's pride to be replaced by red faces when it's realized that no one can log in and no one can register a new user. Since it's a one-off occurrence, this might sound like it doesn't deserve a place in the requirements. But solving it might leave an ongoing security flaw, so it's best that everyone be made aware of the potential risk. We don't want a surreptitious utility to be built that can set up new users and then hangs around in the hands of one or two developers or systems administrators. If such a utility is needed, make sure it's known about and kept under strict control. Here's an example requirement to prevent one cause of a bad first day:
Summary | Definition |
|---|---|
New system usable | When the system is freshly installed, it shall be usable by someone, at least to the extent that they can set up a new user and grant them access to system functions. The purpose of this requirement is to prevent a newly-installed system from being unusable by anyone. Any special processing needed to render the system usable before any real users have been registered shall be permanently disabled or removed from the system as soon as at least one real user has been registered. |
The range of topics raised in this requirement pattern makes it clear that there is much to think about. The best advice is simply to take user registration seriously and not to cut corners. Always handle secret values (such as passwords) securely: at the first opportunity, render them indecipherable, and destroy the clear form.
A user registration function is basically a data entry function and should be tested as such. Test the entry and validation of all values. Test that validation is not performed only on an untrusted client device (a remote user's PC). Test that any values that are intended to be secret (such as passwords) are treated as such, and cannot be viewed using the system (such as via inquiries or reports or obtained from logs or from querying the database).
Testing that a user registration process is secure cannot be done solely by using the system. It's a specialized activity (as discussed in the user authentication requirement pattern).
Use the user authentication requirement pattern to specify that a person must make their identity known to the system before they can access anything non-public or anything for which they cannot remain anonymous (in short, anything for which they must log in).
Authentication is the process by which a registered user declares who they are and proves this assertion to the system's satisfaction. This requirement pattern says little on the subject beyond what is of interest to requirements; it doesn't worry about the considerable challenges of implementing a secure system. The most widespread form of authentication in commercial systems is just asking the user to enter their user ID and password, and that's what this requirement pattern concentrates on. The common name for user authentication is "logging in." (This book prefers logging in to logging on—on the basis that entering a system is a better metaphor than climbing atop it. Let's also point out that, as a verb, to "log in" is two words: "to log someone in" sounds fine, and is only possible if there is a gap in which to squeeze "someone.")
There are three accepted ways to check that a person is who they claim to be: something they know (such as a password), something they have (such as an ID card), and something they are (using a part of their body that can be distinguished from that of everyone else—such as a finger or an eye). Depending on how secure you want your authentication process to be, you can ask for more than one (a password and an ID card and a fingerprint, if you insist). There are various factors that affect what's best in a particular situation, including:
- Factor 1: The potential damage that an impostor could cause
This depends on what the user has access to—not just which functions but also other assets (for example, a customer who has a large sum of money in their account), so you might want to consider stronger authentication for users who have the greatest powers (or valuables) in the system. Also consider possible indirect damage, such as to the company's reputation if unauthorized access became public knowledge.
- Factor 2: The type of device on which the user self-authenticates
This could preclude certain kinds of authentication. For example, you can't expect the average Internet user to have a card reader attached to their PC (at least, not at the time of writing).
- Factor 3: The local environment of the user
How trusted or untrusted is the user's device by virtue of where it resides? Is it snug inside a company office, or in the wilds outside? Is the user likely to have someone looking over their shoulder when self-authenticating? (Note that when using an ATM, you don't enter both a user ID and PIN; your bank card—which a spy can't see—says who you are.)
Authentication can be regarded as creating a user session, which grants the user access until the session ends. This might sound like an implementation contrivance, but it's not—and it makes some aspects easier to discuss (especially a few of the extra requirements that follow). It appears a good idea to prevent a user from having more than one session at the same time, but it can be problematic, due to technical unreliability (especially with communications). A user is liable to get frustrated if they "return" after a failure, attempt to log in, and are refused because they already have a session (which they cannot use). On the other hand, letting a user have many active sessions can cause problems, too. If you allow a user to have more than one session simultaneously, a history of their actions only makes sense if you show each session separately. One option is for logging in to terminate all previous sessions—but there are circumstances where that's awkward, too (for example, if a user is active and someone who has purloined their password then logs in).
A user authentication requirement should contain:
Class of users Which users does this requirement apply to? "All users" is an acceptable class.
Authentication mechanism(s) How do you expect the users to identify themselves? You could be specific (entry of a user ID and password, for example), or you could just describe the level of security needed and leave the details up to the development team. Avoid mention of specific technologies as far as possible.
You could also keep the login function for one class of user separate from that for other classes of users. For instance, you might not want Web customers anywhere near the login function used by employees.
Initiated by When do users need to authenticate themselves? You could force users to log in to gain any access, or you could let them wander around anonymously and invite them to log in only if they want to do something that demands it. Both approaches have their place, and you might choose to treat different classes of users differently. For example, force employees to log in before they can do anything, but let Web site visitors log in when they want to. Another factor to bear in mind is that knowing who someone is as early as possible lets you record their actions, though you might irritate users if you insist on them logging in earlier than strictly necessary.
Alternatively, you could leave the matter open—though for completeness, you could state that users must have authenticated themselves before doing anything that depends on their identities being known.
Summary | Definition | |
|---|---|---|
«User class» authentication/ login | A «User class» shall be able to self-authenticate (log in) by «Authentication step(s)». | [«Initiated by description».] |
Don't simply copy any of the requirements given here or in the Extra Requirements section. None of them suits all situations.
Observe that the first example doesn't mention any particular authentication mechanism.
A user authentication requirement looks straightforward and self-contained, but there are various related matters you can specify in extra requirements, mostly to limit the misuse of user accounts. These include the following (each of which is covered in its own subsection that follows—except accessibility, which is covered in the accessibility requirement pattern in Chapter 8).
Forgotten password handling People forget things. They forget their passwords, especially if you force them to be long or to use strange combinations of characters. What happens then?
User de-authentication (Logging out.) If you let someone in, you should let them out again—to tell you they've finished for now.
Ending user sessions We can't allow a user session to last forever, so we need at least one way to bring it to an end. First, limit the duration of each session. It's also useful to let an operator terminate a selected user session (if a user appears to be up to no good, for instance) or all—or nearly all—sessions prior to shutting the system down.
Absent user protection If a user's done nothing for a while, they might have stepped away from their machine, so we might want to try to stop someone else nipping in and doing things in that user's name.
Helping users spot breaches Users themselves represent an army of people with a strong interest in discovering any abuse of their own accounts. So why not help them do it? Help them detect whether someone else has logged in with their user ID, and give them a way of signaling security breaches.
Blocking users (So they can't log in.) There are several reasons for denying a user access to the system, including repeated entry of the wrong password, because they're going away (an employee taking a vacation, say), or simply because they've misbehaved. If users can be blocked, we need a way to unblock them. Finally, the ability to prevent anybody from logging in is handy—shortly before shutting down the system, if at no other time.
Viewing user sessions Looking at current user sessions can tell you about what's going on in the system now. Storing session information and being able to study it later can help you investigate a breach of security and is a good source of statistics.
Accessibility If you're using biometrics to check a person's identity, you should provide an alternative for people who are unable to offer the required body part to the device that reads it (because they don't possess it, lack mobility, or some other reason). This is a provision of Section 508 of the U.S. Rehabilitation Act. See the accessibility requirement pattern in Chapter 8 for more, including an example requirement (in the "General Accessibility" subsection of its Extra Requirements section). Beware of opening a security gap if you allow biometric authentication to be bypassed. Don't allow just anyone to say they're incapable of using a biometric reader; only allow nominated users to do so.
Forgotten Password Handling We must be able to get a user back on track when they forget their password, for which occasion, we need another way for them to prove their identity. This is straightforward enough in an environment where the user is known personally to someone who can vouch for their identity (such as colleagues in an office): a trusted user can run a function into which the hapless user can enter a new password.
In the absence of a trusted second person who can verify a user's identity (for instance, when a customer wishes to use our Web site), we're likely to be forced to resort to more dubious means. A common stratagem is to ask the user for additional "secret" information when they register—either a "secret phrase" or one or more questions along with their answers. (Registration can suggest questions: what was the name of you first pet? The make of your first car?) This typically results in values that are easier to guess than a password, and often not secret at all. In recognition of this, it's best not to depend solely on this "secret" information to identify the user. Two extra steps are as follows. First, to ask the user to speak on the telephone to an operator, who can bring to bear their personal judgment about whether the user is genuine (and ask extra questions). Second, test whether this person is able to receive communications sent to the user (which can use any of the user's contact details—such as their home address or telephone number, but most often their email address, because it's quick and the sending of an email can be automated). Both these steps are weak from a security standpoint.
Whenever you're thinking about involving an operator in the forgotten password process, consider the potential operational cost, especially if the number of users is large. For systems that don't handle forgotten passwords automatically, this is one of the most numerous types of calls to help desks.
Summary | Definition |
|---|---|
Customer forgets password | If a customer forgets their password, they shall be able to log in by entering the "secret phrase" they supplied when they registered plus a verification code sent to their email address. This shall be achieved by using the following process:
|
Customer forgets secret phrase | If a customer forgets both their password and secret phrase, there shall be a means of last resort whereby they can prove their identity and have a new password assigned to them. This shall be achieved by using the following process (or one equivalent to it):
|
User De-Authentication (Logging Out) Give users the opportunity to log out explicitly, so they can prevent someone else from slipping into their seat after they've gone and performing actions in their guise. Do this even in environments where users rarely log out. For example, visitors usually leave a Web site simply by moving on to another one, or by exiting their browser—but someone in an Internet café won't want a complete stranger to be able to carry on where they left off. Logging out has the effect of ending the user's session. If you allow a user to have multiple sessions simultaneously, you must decide whether logging out applies to all of them or just to the one in which the logout was performed (both of which have their down sides)—or you could let the user choose.
Summary | Definition |
|---|---|
A user shall be able to de-authenticate (log out). After de-authentication, the system shall treat them just as if they had not been authenticated in the first place and shall regard all subsequent actions as being performed by an unknown user. |
Ending User Sessions It's good practice to limit the duration of a user session, to force a user to prove it's really them from time to time. Without such a limit, a user could log in once and continue to use the system indefinitely. When a session is about to end, ask the user to establish their identity again, and don't permit them to continue to use the system until they do so. If possible, do this in a natural break in what the user is doing (at the end of a transaction, say): be polite. It also helps to let the user know that we're doing this for their own security. The duration of a session should be somewhat longer than users are typically continuously active, so we might set it at twelve hours for an employee, or three hours for a Web site customer. Logging out also ends a user session (as described in the previous subsection). If you can reliably discern that a user is leaving, you can end their session; this depends on the technology being used.
Summary | Definition |
|---|---|
User session timeout | Every user session shall automatically end (time out) a length of time after it began. The length of time shall be configurable per class of user. When a timeout is imminent, the user shall be invited to reauthenticate (log in again), which shall allow them to continue using the system without interrupting any functions they happen to be using at the time. If they do not reauthenticate, the system shall reject any further requests from this session. |
Exiting client application ends user session | When a user exits the client application, any user session opened by that application shall be terminated. |
Notice that the first preceding example carefully sidesteps the question of whether it extends the existing user session or creates a new one. Developers might have strong views on the subject, but it's solely a matter for them: it doesn't concern the requirements, so steer clear of it here.
Next, it's useful for an operator to be able to peremptorily terminate a selected user session: without it, you'd be hamstrung in halting a user who's discovered performing nefarious activities. Taking this one small step further gives us the ability to terminate all active user sessions (or all sessions for a particular class of users—such as all customers), which can be useful if we want to shut the system down. Oh, and remember not to terminate the killer operator's own session!
Summary | Definition |
|---|---|
Terminate user session(s) | An employee shall be able to terminate a selected active user session, all active sessions for a selected class of users, or all active user sessions. They shall not be able to terminate their own user session. |
If we can give a user advance notice that their session will end shortly, it's polite to do so. For example, if their session is nearing its time-out time, we could notify them, so they can log out and log in again with minimal inconvenience.
Absent User Protection If an active user suddenly stops doing anything, it could be because they've walked off and left their machine all alone. A Web site customer who simply goes to another site (or shuts down their browser) without logging out can leave an open session. In these situations, we don't want someone else to be able to wander up (metaphorically in the case of an Internet attacker) and, as far as the system's concerned, impersonate the original user. If you want to prevent this, you can either write a requirement that expresses this intent, or write one for a specific way to prevent it—the commonest being an inactivity time-out, after which we ask the user to type in their password upon their return before they are allowed to proceed. We can then take this one stage further and let the user tell the system they're leaving their machine temporarily: that is, effectively to trigger the inactivity time-out immediately.
One awkward feature of locking a session can be (depending on the technology used) that it prevents anyone else from using the machine—which can be irritating. One way around this is to allow someone else to break the lock (though not to take over the original user's session, nor to see what they were doing). A further refinement is to let a user locking their session to say whether they're prepared to let it be broken.
Summary | Definition |
|---|---|
User inactivity time-out | If a user with an active session has had no interaction with the system for longer than a configurable length of time, then the next time they make a request, they shall be asked to enter their password before they can proceed. The motivation for this requirement is to protect against someone attempting to take over a user's session when the user has walked away from their machine. |
Lock user session | A user shall be able lock their current session, to indicate that they are about to leave their machine unattended. They must enter their password before they can proceed. When initiating the session lock, the user shall be able to indicate whether another user can break the lock. (Ordinarily, they should allow it to be broken, but might want to prevent it if they're in the middle of an important task.) |
It shall be possible to break a user session that has been locked as a result of an inactivity time-out or an explicit lock. The person wishing to break the lock must enter their user ID and password, which terminates the original user's session and creates a session for the new user. |
Helping Users Spot Breaches A system cannot tell the difference between a legitimate user and someone else who's discovered their user ID and password, so a system can never detect a security breach of this kind. But if we tell the user a little about their last session (typically, the time they last logged in), they're in a position to judge whether someone else has been impersonating them in the meantime. Here's a requirement for the commonest way:
If we help users detect misuse of their account, we should provide them with a way to tell us about it. You might think existing means of communication suffice, but it can be worth doing a little more. Here's one suggestion:
Think about what an operator should do when notified of a suspected breach of this kind. Have you specified requirements for tools that enable them to investigate (such as to view user sessions—discussed shortly)? Bear in mind that false alarms will probably greatly outnumber genuine misuses.
Blocking Users By "blocking" a user, we mean preventing them from logging in to the system. There several situations in which we might want to block a user, including:
The user enters their password incorrectly too many times in a row when logging in—because this might suggest someone else guessing and trying to impersonate them. It might be convenient for everyone for such a block to last for a short period of time only (an hour, say). We can afford to be relatively generous in the number of attempts to give a user to enter their password (25 or 50, say), because the chances of an attacker guessing the password in this way is still tiny (despite what Hollywood might have you believe). Systems that give a user only three attempts merely irritate the user and lead to more requests to whoever looks after unblocking user accounts (plus, for employees, loss of productivity until it's done).
A user might wish to block their own access for a certain length of time, if they know they're going to be away (such as before leaving on vacation).
An operator might wish to block a user who has been acting improperly or suspiciously.
If user accounts can become blocked, we need a way to unblock them. A useful related function is the ability to prevent all users (or a whole class of users—such as all customers) from logging in. This can be invoked prior to shutting down the system, to avoid frustrating users by kicking them out soon after they log in.
Viewing User Sessions User sessions contain valuable information—both about what's currently happening in the system and about which users accessed the system when. It's wasteful to simply discard or ignore this potential treasure. So store it, and let it be exploited. It might help identify a breach of security (after the fact), if nothing else.
Requirements related to user authentication merely specify necessary features; they don't worry about the complexities, of which there are many—too many to relate here.
Coding a login function is almost as easy as a "Hello World" program. But doing it securely is considerably more difficult. Take into account all the good practices described in this requirement pattern, even if they're not formally required. Turn the password entered by the user into an undecipherable form as soon as possible, and overwrite the clear form in memory.
The testing of user authentication needs to be performed at two very different levels:
Functional Does the authentication process work properly in all circumstances normally encountered in the running of the system? Test it just as you would any user function: the entry and validation of values, expected responses, and so on. Test that a user who has not logged in has no non-public privileges. Test that after a user logs in, they can access whatever they are authorized to.
Similarly, test all features discussed in the Extra Requirements section: the action and effect of logging out, session time-out, and so on.
Security Not only must user authentication work, it must also do so in a secure manner. It must prevent anyone else from learning sensitive information (especially user passwords). It must prevent the authentication process from being bypassed, subverted, or otherwise tricked. This is a specialized field. It involves replicating the wide variety of techniques that potential attackers could exploit, most of which are very sophisticated and highly technical. For example, someone listening to traffic between a user's machine and a central system can attempt a "replay" attack; this can only be tested by undertaking this kind of attack. This subject is beyond the scope of this requirement pattern; refer to specialized resources and consider bringing in an expert.
Ask for features that will assist testing. These include a way to view details about user sessions (especially when they end, so you can test that they time-out properly). To achieve this, we need the beginning and end of every user session to be recorded.
The purpose of access control is to restrict users to doing and seeing only what they should. This section talks about "what a user can do and see" as a concise way of referring respectively to the functions and the information they can access. Collectively they are referred to as privileges that they confer upon a user (or "access rights" or "permissions," though this book calls them privileges throughout). It's also worth recognizing that as far as a system is concerned, a user never does anything directly, so we mean what various parts of the system do on a user's behalf.
Access control is used most widely to control which functions someone can use. For example, a customer service operator could be granted access to all customer service functions, but little else. Functional access control can be extended to individual actions within a function (such as the ability to change, but not to add)—and while greater granularity gives more control, it takes more work both to develop and to maintain. Access control requirements can also restrict the information a user can see and can be used for other purposes (the commonest of which are spelled out in the specific authorization requirement pattern). These ways can be applied in combination. For example, a user might be granted access to one set of functions for one company and a different set of functions for another company. But this can get complicated: if you get away with authorizing access to functions and to information independently, life is much simpler.
There are two types of user authorization requirements: the first defines specific privileges (according to some access rule, such as for a named set of users); the second demands a general ability to configure who can do what. Each has its own requirement pattern. You can use both in a specification, in which case a configurable authorization requirement guides the capabilities of the system, and to guide its configuration, you can use specific authorization requirements (acting as a useful place to put knowledge gathered, to make setting up the system easier). A configurable authorization requirement is in effect an instruction to implement an access control infrastructure.
Regardless of how you choose to define who can do what, you should start by stating what access is allowed in absence of any guidance to the contrary. After all, a requirement saying that "A can do X" has little force if there's nothing to prevent everyone else from doing X. The most sensible approach to take is denial by default. That is, everything is to be inaccessible to every user, unless permission is granted to them either explicitly or by defining some things as publicly accessible.
The denial by default rule can either be specified as a special kind of specific authorization requirement, or it can be incorporated within the main configurable authorization requirements (as the first two example requirements in the configurable authorization requirement pattern do).
Bring as much of the system's activities within the ambit of access control as possible. Many system administrators, database administrators, and developers believe they're exempt from controls that apply to mere mortals. This mentality permeates many products, unfortunately, which can make it difficult to control them. Another difficulty with products is that they're unlikely to be amenable to cooperating with any access control regime you put in place. This could influence product selection decisions if you're serious about security.
Regardless of how you choose to specify user authorization, there are a few extra topics worth considering:
Presentation and usability To bring navigation of the system into line with what the user can actually do and see, rather than wasting their time by showing functions they're not allowed to use.
Delegating authority To let one person act on another's behalf.
Preventing loopholes To prevent our efforts at access control being circumvented.
Each of these topics has it own subsection that follows. One more does not, because it's covered in its own requirement pattern:
Approval Some activities might warrant approval by a second person (or even a third) before they can proceed. This topic is discussed in the approval requirement pattern.
Presentation and Usability Systems have a natural inclination to appear stupid unless special steps are taken to prevent it. Denying access is one thing; not looking stupid in the process is something else—and one worth treating carefully, because it can save much time, effort, and frustration during the life a system. Don't clog menus with functions that the user isn't authorized to use; don't let them choose values that they're not allowed to, only to slap them in the face if they try.
How much should we tell users about the existence of things to which they're not allowed access? It's naïve to assume they'll not be aware of most of them in one way or another. (It's impractical to produce lots of different sets of user documentation, for instance—though online documentation attached to each function suffers less from this difficulty.) It's counterproductive to hide the existence of some functions, because a user might need to ask someone with extra privileges to do something for them—so they must be aware that other person can do more than they can. Awareness of inaccessible data is a different matter; in a multi-company system, for example, it might be essential to hide other companies completely.
Here are a few example requirements that aim to make access control more friendly in various ways:
Delegating Authority Real businesses are intricate beasts whose managers quite reasonably want to decide who performs what tasks. If managers need a system to offer a particular kind of operational flexibility, it must be expressly built into the system. One kind of operational flexibility involving access control is the ability to delegate authority to someone else, as in this example:
Summary | Definition |
|---|---|
Delegate authority | An employee shall be able to grant authority to another employee to act on their behalf. The delegator shall be able to nominate which privileges the delegatee can exercise in their name, including setting access-related limits. The motivation for this requirement is to allow a personal assistant to perform administrative tasks in place of the manager for which they work. |
Assume delegated authority | An employee who has the authority to act on another employee's behalf shall be able to indicate to the system that they wish to do so. Any action they take thereafter shall carry the imprimatur of both users (done by B on behalf of A). When they have finished, they shall be able to indicate they have stopped acting on the other employee's behalf. Note that assuming delegated authority can grant a user privileges they do not normally have. |
Preventing Loopholes It's possible to implement access control as a thin veneer around a system that, once punctured, leaves the system completely unprotected. It's not the responsibility of requirements to figure out every kind of attack and the provisions needed to guard against it, but we can write requirements that point out potential loopholes we want to guard against, like this one:
Related patterns: | Extends user authorization; refers to configurable authorization |
Anticipated frequency: | Up to a dozen requirements |
Pattern classifications: | None |
Use the specific authorization requirement pattern to specify that a set of users is authorized (or is not authorized) to do or see certain things.
Do not use the specific authorization requirement pattern to specify that user authorization is to be configurable; use the configurable authorization requirement pattern for that.
A specific authorization requirement makes a statement—of any kind—that affects what a certain set of users can see and do. These requirements can vary considerably, but they generally fall into one of the following categories (or possibly more than one—which is most frequently seen in combinations of Categories 2 and 4):
- Category 1: Universal denial-by-default rule
To assert that nothing of value in the system is accessible unless permission is expressly granted.
- Category 2: Functions
Functions that certain kinds of people are authorized to use. A requirement can either name an individual function or a class of functions.
- Category 3: Actions within functions
For example, a user might be authorized to change details but not add or delete something or other.
- Category 4: Data
- Category 5: Limits
Limits on values a user is allowed to work with—such as a monetary amount up to which they are authorized to perform a certain action (for example, a refund to a customer).
- Category 6: Time
To restrict when certain privileges can be used (what times of day and/or days of the week).
- Category 7: Environment
To apply restrictions to certain environments (such as remote access).
- Category 8: Strength of authentication
To allow a user to do more if they logged in using a strong authentication mechanism (such as a smartcard) than they could do if they used a weaker mechanism (such as when they have mislaid the card and just entered their password).
- Category 9: Transference
Where a restriction applied in one situation is transferred to apply in the same way to something else (such as data copied into a chronicle being subject to the same protection as the original data).
- Category 10: Operational rules
To achieve such things as division of responsibility (so that the same person can't both perform and then approve a transaction, for instance).
- Category 11: Blanket bans
Things that no one may have access to—mainly functions that are present anyway but which it's bad practice to use day-to-day in a commercial system (such as unrestricted access to the database or operating system).
- Category 12: Blanket permission
Things that everyone can access without restriction. Publicly available things normally don't warrant a separate requirement to say so, but you might encounter a situation that deserves it.
Use this list to help identify what you need: go through each point in turn. Each one can be regarded as an access rule that the organization wishes to apply to the operation of its system. (If you'd like to apply certain rules more widely than just within one system, pull them out into a separate requirements specification—"common requirements"—and then refer to them in the requirements for each system to which they apply, as per the refer-to-requirements requirement pattern.) Recognize the bounds of what the system can realistically restrict access to—and don't waste your time trying to control anything beyond those bounds. That might include hardware, other systems, and third-party software used to implement part of the system. You might be forced to make unpleasant compromises.
A specific authorization requirement needs to convey two things: who and what. The preceding list is of various kinds of what. As for who, express it in whatever terms are appropriate—but be clear. Don't name particular users (people). Mention roles or job titles, if you like, but if you do, define them either within the requirement or elsewhere (as informal material). This is important, because if you don't, readers are apt to interpret them differently. (Someone else's picture of a "systems administrator" might not accord with yours, for example, aside from theirs having green hair and yours purple.) If you're building a system to be used in multiple places, they might be organized very differently; make it as easy as possible for everyone to see how your system would fit their environment.
A specific authorization requirement should contain:
Privilege description (What.) It can be anything to which access can be granted (or denied), but is most commonly the name of a function.
Access rule (Who, and in which circumstances.) Most commonly, it identifies a type of user, and at its simplest, it says that such users are granted the relevant privilege. But put whatever you want into a rule—including conditions and other logic.
Summary | Definition |
|---|---|
«Privilege summary» access | «Privilege description» shall [not] be accessible «Access rule description». |
«Privilege summary» access | A «Type of user» shall [not] be able to «Privilege description». |
The examples here are presented according to the categories listed in this pattern's Discussion section (along with a few that are combinations of Categories 2 and 4).
Category 1, a universal denial-by-default rule:
Category 2, functions (starting with one you might regard as so obvious that it goes without saying, although a stickler could argue that without it, unrestricted access is acceptable):
Summary | Definition | ||||||
|---|---|---|---|---|---|---|---|
A user shall not have access to non-public functions or information if they have not logged in or have logged out. | Limited casual visitor access | A casual visitor to the Web site (who has not been authenticated as a customer) shall have only limited access. They shall not be able to even initiate any function that involves money (such as placing an order). | Employee maintenance access | The ability to maintain information about an employee (add, change, and remove) shall be limited to members of the human resources department. | Employee access to customer inquiries | A customer service operator shall be able to access all inquiries accessible by customers, to view exactly what any selected customer would. The operator shall be able to do this only for customers of the company for whom the operator works. It is not acceptable to achieve this by having an operator log in as the customer. The purpose of this is to allow an operator to explain to the customer any information they have difficulty understanding, and to see exactly what the customer sees: identical data in an identical format. |
Category 3, actions within functions:
Summary | Definition |
|---|---|
Customer maintenance | Each type of action that can be performed within the customer maintenance function shall be subject to separate access privileges. "Type of action" shall include changes to address and credit limit. |
Category 4, data:
Categories 2 and 4 combined, both functions and data:
Category 5, limits:
Summary | Definition |
|---|---|
Customer refund limit | An employee shall be able to approve a refund to a customer up to (and including) the refund limit set for them. |
Category 6, time:
Summary | Definition |
|---|---|
Initiate transactions only during nominated hours | An employee shall be able to initiate transactions during nominated hours of the day. It shall be possible to specify these hours of the day for each employee, but if they have not been set for an employee, a configurable default range of hours shall be used. |
Category 7, environment:
Summary | Definition |
|---|---|
Employee remote access | An employee shall be able to access the system from outside company premises if authorized to do so (and not otherwise). |
Category 8, strength of authentication:
Summary | Definition |
|---|---|
Reduced access by employee without smartcard | An employee who has been issued a smartcard but who logs in without it shall not during that session be able to initiate or approve financial transactions. |
Category 10, operational rules (of which there is a further example in the "Cannot Approve Own Action" section in the approval requirement pattern):
Summary | Definition |
|---|---|
Cannot extend own authority | No user shall be able to modify their own access privileges. In particular, no user shall be able to extend their own privileges. |
View own orders only | The system shall permit a customer to view only orders that they placed, not orders placed by other customers. |
Specific authorization requirements can be varied, and the ways to implement them can be equally varied. Deal with each one on its merits. Don't seek a grand mechanism that can solve them all: they might be too diverse.
The biggest decision is whether configurable access control is worth implementing, even if there's no explicit requirement for it. You can't expect a requirements specification to specify every little detail of who's allowed to access what. Judge for yourself how big the gaps are. Maybe there's an unspoken expectation of configurable access control; if so, bring it out into the open and resolve it quickly.
Testing a specific authorization requirement is reasonably straightforward: can that kind of user access whatever it refers to? Are all other kinds of users prevented from accessing it? If a user is able to delegate their authority to another user, test that a delegatee is authorized whenever the delegator is. Change the kind of a user (if that's possible, for example by assigning them a different role), and test that their authorizations change accordingly.
An invaluable tool when testing authorizations is for all rejected authorization requests to be chronicled (logged). When reviewing requirements, check that this feature is included. If not, insist on it.
Use the configurable authorization requirement pattern to specify that the definition of which users can do what is to be configurable (that is, can be changed dynamically).
Do not use the configurable authorization requirement pattern to specify what a set of users is authorized to do or see; use the specific authorization requirement pattern for that.
Configurable authorization control is wonderful: it lets you change who can do what, whenever you like. An employee needs more authority to do their job properly? No problem! A company restructure? Bring it on! At the same time, it's a millstone, with major drawbacks: it's difficult and expensive to implement; it can incur performance penalties; it's time-consuming to set up and subsequently to maintain; ill-considered (or malicious) changes can have major consequences; and it introduces security risks of its own. So ask for access control to be configurable only if it's worth it; even then, keep it as simple as possible and use it only in those areas that justify it. (That is, don't use it everywhere just because it's there.) Also, take care to make clear what's needed and what isn't, so you don't inadvertently end up with an over-fancy solution.
Configurable authorization is most fruitful when used to control access to functions, because in any serious system, the functions are too numerous to fix their access correctly up front, for all time. Configurable authorization to data is rarely called for, because a normal system simply doesn't need the ability to partition data in arbitrary ways; the cases that do occur are usually isolated and best dealt with using specific authorization requirements. (Note that even without requirements for configurable authorization to data, the system might still be implemented with access control at the database level, on tables and SQL procedures and so on. That doesn't concern us here.) Sometimes, though, several sets of access configuration to functions are needed—one for each of a set of data values. For example, a multi-company system might allow permissions to be defined differently for each company within it—such that one user can access one collection of functions for one company and other functions for a different company. This renders configurable authorization more complex to implement and to manage, so avoid it if you can.
Give configurable authorization requirements a high priority, because if you need access control, you can't very well live without it for an extended period until it's delivered in a later phase—and any attempt at an interim solution could be a mess. In any case, its priority must be at least as high as any specific authorization requirements that depend on configurability.
A configurable authorization requirement should contain:
Class of users For which users do we want to make access configurable? Do it only for classes of users that need flexibility. Avoid it for classes of users that have largely fixed privileges—which, in most systems, includes customers. If possible, avoid it for high-volume classes of users (again, customers)—because of the likely performance impact.
Nature of access Are we asking for configurable access to functions, or to data, or to a combination of both? Describe what's needed in as much detail as you can. Make clear the significance of what you're asking for; don't let a massive undertaking look innocuous.
Motivation Why do we want this to be configurable?
Summary | Definition |
|---|---|
Employee access to functions | An employee shall be able to access only those internal functions in the system to which they have been granted permission (by virtue of the roles assigned to them). An internal function, for the purpose of this requirement, is one that is not intended to be available to customers. Within each function, the ability to perform each distinct type of action (view, create, modify, delete, approve, and so on) shall also be restricted in the same manner. The motivation for this requirement is to allow the system to adapt to the skills of the workforce that uses it and to be able to react to reorganization of the company. |
Employee access to data | An employee shall be able to access only those classes of data to which they have been granted permission (by virtue of the roles assigned to them). For the purpose of this requirement, "class of data" means any body of data that can be defined precisely such that no item of data shall belong to more than one body of data. This is not to say that explicit access must be granted to every item of data; it means control can be given for specific things that warrant it. A user shall have no access to data that is subject to such control, unless permission is explicitly granted to them. (That is, a denial by default approach shall be taken.) The motivation for this requirement is to allow data to be segregated in various ways so that a range of powerful inquiries can be made available to any user while still permitting them to view only the data relevant to them. |
Employee access to functions per company | An employee shall be able to access only those internal functions for a particular company to which they have been granted permission (by virtue of the roles assigned to them) for that company. "Internal function" shall be taken to have the same meaning as in the requirement before last. The motivation for this requirement is to allow the operation of each company to be defined separately, while still permitting employees to do work for more than one company. |
The first two examples spell out the two main "natures" of access control (functions and data). A more common way to express these sentiments might be, "A user shall be able to access only those functions and that information to which they have been granted permission," but that fails to address what information it might apply to, and it hides the enormity of what it's asking for to such an extent that only an eagle-eyed reader would spot it.
A configurable authorization requirement can have the following kinds of extra requirements, in addition to those common to both types of user authorization requirement (each of which is discussed in its own subsection that follows):
Defining user roles We need a way to set up user roles and define what privileges each role has.
Authorization inquiries Access configuration is hard enough to manage at the best of times, so provide inquiries to make it as easy to understand as possible: what each person is allowed to do, which people have each privilege, and so on.
Chronicle authorization changes Keep track of changes to any of the configuration that controls who can do what.
Defining User Roles It's most convenient to discuss roles in a reasonably abstract way (because it avoids repetition), which makes sense only if we assume that a user can assume several such roles. A role, then, doesn't necessarily equate to a job description—nor to an "actor" or "class of user." (Roles are likely to be more numerous than any of these other things.) Even if roles are to be configurable, it's useful for the requirements specification to list candidate roles informally; it gives readers a better idea of what we're talking about and can give the configuration a head start.
We need to specify a tool for defining user roles:
Summary | Definition |
|---|---|
User role maintenance | There shall be a function for the creation and editing of user roles. Each role shall have a name and a description of its purpose. It shall be possible to maintain a list of the access privileges granted to any user with this role. |
If we're defining roles, we could be picky and make sure the software actually uses the roles when deciding what a user is allowed to do:
Summary | Definition |
|---|---|
Access control per role | The privileges a user has shall be determined by the roles to which the user is assigned. Privileges shall not be given directly to each user. |
Authorization Inquiries Why systems act as they do is always shrouded in mystery—invariably far more than necessary. The workings of serious access control can be equally mysterious if it doesn't let you see what's going on. A set of inquiries for this purpose is invaluable. The two most important ways in which authorizations should be viewable are by user (to see what each user can do) and by privilege (to see everyone who can access each thing). The latter can also point out anything to which no one has access, which means parts of the system are lying idle. Here are a couple of basic examples:
Summary | Definition |
|---|---|
There shall be an inquiry that lists all the access privileges granted to a selected user. For each privilege, it shall indicate which of the user's role grants it. Every user (except customers) shall be able to inquire on their own access privileges. | |
There shall be an inquiry that lists all the types of access privilege known to the system. For each privilege, it shall name all the user roles that grant it (and, in so doing, identify privileges granted to no one). |
The second example leaves open the question of where the information about privileges "known to the system" comes from and how it gets there. The most obvious answer is that it's stored somewhere and there's a way to edit it. If you want to make that explicit, write a requirement to that effect; something like this:
Summary | Definition |
|---|---|
Privilege type maintenance | There shall be a function for the creation and editing of information about access privileges. Each privilege shall have a name and a description of its purpose. |
Chronicling Authorization Changes Changes to the configuration of access control can have major consequences, so insist that all changes to access control are chronicled (as per the chronicle requirement pattern in Chapter 7). If a malicious user granted their own access to an extra function, used it, and then revoked access, chronicle entries could be essential in piecing together what happened. Refer to the chronicle requirement pattern for more.
If access control logic is simple and fixed, you can hard-code it. If it's not simple, or if it's liable to change, it's better to build a general, configurable mechanism—regardless of whether the requirements say you should. However, developing an underlying mechanism for access control is difficult and not for the faint-hearted. Apparently sensible and logical approaches can turn out to be a nightmare to manage in practice, because of the sheer quantity of configuration data. If you think a general access control mechanism will be worthwhile, bite the bullet early. Trying to retrofit it later is likely to be unpleasant.
First of all, recognize that you're testing the requirements, not the privileges of whatever roles might have been set up: testing isn't responsible for checking that every user can do what they need to do their job. Having said that, it's always sensible to configure a test system as closely as possible to the live environment—which means defining roles and their privileges as realistically as possible.
When testing access to functions, for each function, test two things: first, that access to the function is controlled; and second, that the correct privilege is checked. This is exceedingly tedious to do manually. It helps if the system lets you observe each authorization check (down to the name of the privilege being checked); then you can see directly whether the correct privilege is used for each function. One way to observe authorization checks is to record them in a chronicle, and there is an example requirement for doing this in the "Chronicling Authorization Changes" subsection of the Extra Requirements section in this pattern.
A simpler test is to create a user role that can do everything, and verify that a user with that role can indeed do everything. Also create a user role that can do nothing, and verify that a user with that role can do nothing but publicly-accessible things.
One difficulty is that the number of privileges could keep growing. You'd have to be inhumanly diligent to insist on trying to test every new one that comes along.
Related patterns: | None |
Anticipated frequency: | Often no requirements; rarely more than half a dozen requirements |
Pattern classifications: | Functional: Yes; Affects database: Yes |
Use the approval requirement pattern to specify that a particular action (or set of actions) must be approved (or, in some circumstances approved) by a second person before it takes place.
Any function in a system can be constructed so as to require approval before it takes effect. We usually think of one person approving an action requested by another, but it is also possible to allow a person to approve actions suggested by the system itself. ("An upgrade is available for the Whizzo Happiness Calculator. Would you like to download it now?" is an example.)
Imagine a bank in which a teller must have any large cash withdrawal approved by a supervisor. This sounds straightforward enough. But what constitutes large? Does it vary from teller to teller: are some more trusted than others? What is meant by supervisor? Can any supervisor approve it, or just the teller's direct superior? If a supervisor performs a withdrawal, must it be approved by another supervisor—and does that mean someone more senior still? Approving an action is invariably significantly trickier than it at first appears (or if you imagine that it will be tricky, you'll be proven right). It's also commonly neglected in both requirements specifications and software.
And when a system has to handle approval of actions, there are further complexities, because every system lacks the common sense possessed by every human being. How do we bring something needing approval to the attention of someone who can approve it? What if more than one person is able to approve it: do we bring it to the attention of all of them? If not, how do we decide which? What if a usual approver is absent? What if someone else wants to perform an action that affects the pending action (for example, if we're waiting for approval to debit a bank account, and another debit to the same account comes along); there are no easy answers to this one. Every little detail must be figured out and specified—and commonly they aren't, resulting in systems that don't behave sensibly and are awkward to use.
The approval of an action is best specified as an extra requirement following that for the function that carries out the action. Approval requirements should answer some or all of the following questions, as appropriate:
Which action(s) require approval? That is, to what does this approval requirement apply? This is what happens when approval is granted. If it's not simply a matter of performing an action specified somewhere else, explain what else is involved.
Under what circumstances is approval needed? It could be always. If not, specify the conditions—such as up to some limit set for the user, or class of user (up to a specified monetary value, say).
Who can approve, and under what circumstances? Answering this question involves several steps:
Step 1: Identify all the users (or classes of users) who can approve this particular type of action. Also identify the circumstances under which they can approve—which can involve similar conditions to those in the previous question (on when approval is needed). For example, we might need some sort of limit up to which a user (or class of user) can approve a particular action (distinct from the limit up to which the user can perform the action without approval).
Step 2: Identify the prospective approver (or approvers) for each user, or a way of working out who they are. For example, only people in the same department might be eligible. And we could nominate a supervisor for each user and state that they're to be the approver of first resort. When a bank teller needs approval for a large withdrawal, confine approval to the same bank branch (or havoc will reign!).
Step 3: Consider what happens if a prospective approver is absent. If you identify only one person as approver, you're in trouble. You need some fallback position. If someone else is performing this job temporarily, how does the system know? Getting a system to behave smartly based on the information already at its disposal (such as it knowing who is logged in at the moment) takes a lot of thought.
Step 4: Prevent a user from approving their own actions. This is covered in the Extra Requirements section in this pattern.
How promptly is approval needed? An approval requirement doesn't itself need to answer to this question, although it has a major bearing on the best way of bringing something needing approval to a potential approver's attention (which is the next question). If approvals are only needed by the end of the day, a relatively simple implementation will suffice; if an action must be approved within two minutes, it's a very different matter.
How is something awaiting approval to be brought to an approver's attention? There's no universal answer to this question: every way has its drawbacks. Which is the most suitable depends on the answers to the previous two questions. Decide how prescriptive you wish to be: either choose a specific mechanism, or merely specify the characteristics you want. Possible approval mechanisms (along with a few strengths and weaknesses) include:
An approve subfunction within the data entry function itself Where the user calls an approver over to their machine, who then self-authenticates and signifies approval (or rejection). This is the easiest mechanism to implement—and perhaps the most reliable, too, because it can take advantage of the user's human common sense. But it involves people walking around (how low tech!), and the risk of the approver's password being observed (plus the temptation for an approver to give their password to someone else to save all this trouble).
A stand-alone approval function This deserves a requirement of its own, which is why it's described in the Extra Requirements section of this pattern.
An electronic communication medium Email, SMS, or pager—or some other way of getting a message to a prospective approver. But that's just half the story: we still need a function by which they can grant approval. Use this sort of messaging mechanism only if the number of approval requests received by one person is relatively small.
The last two mechanisms need us to decide which approver(s) are to be informed of something awaiting approval. Typically just a subset of the people authorized to approve are informed. If using a notification mechanism that expects the recipient to respond, send a message to only one person: it would be frustrating to respond only to find that someone else has already approved the action.
What happens if an approver denies approval? You must always ask this question. It's surprising how often specifications fail to say what is to happen in this case, and as a result, systems sometimes struggle to deal with rejection (a surprisingly human trait for a system!). Actually, there are three distinct situations here:
An approver says, "I reject this. It must not be approved." Usually rejection is the end of the matter, but you might want to consider providing a way for the original user to challenge it: to let them pass it to someone else who might approve it.
An approver says, "I can neither approve nor reject this." This represents a firm and final decision on their part. They would do this if, for example, they believe they're not in a position to decide. The item needs to be passed on to another prospective approver for their consideration. You might decide that in your system, this situation will never arise—that every approver will always know what to do—but if so, you should make this a conscious decision; otherwise a user might be forced into making a judgment they don't want to.
An approver says, "I need more information before I can decide." In this case, consider whether the system needs to provide the prospective approver with the ability to explain what else they need. If so, specify that feature.
This assumes that just a single extra person needs to give their approval. It can be extended to cover two (or even more) people needing to approve. Sometimes this is best done as a "chain" of approvals (one person after another); sometimes they can each approve independently in any order. An example of the latter might be a system that allows the members of a committee to sign off on documents.
Summary | Definition |
|---|---|
«Action name» approval | A «Action description» must «Approval circumstances» be approved by «Approver description». [«Approval promptness statement».] [«Approval mechanism statement».] [If approval is denied «Rejection action description».] |
Summary | Definition | |
|---|---|---|
Large cash withdrawal approval | Any cash withdrawal larger than a teller's withdrawal limit must be approved by another employee within whose withdrawal limit it falls. Approval is granted by the withdrawal function on the teller's machine allowing the second employee to enter their user ID and password and then signify approval. The second employee shall also have the ability to reject the withdrawal, which results in it being canceled. | Employee vacation subject to approval Every request for vacation of more than two days must be approved by the human resources department. |
These examples demonstrate that while there's a large number of aspects to consider when specifying approval, the end result can be straightforward.
By now it should be clear that the business of approval is tricky and complicated. (That's why you still see bank tellers running around looking for supervisors to approve things, despite banks automating almost everything else in sight. Go and watch them before they end up in a museum.) Properly defining your approval workflow could take a variety of extra requirements, a couple of topics for which are:
Preventing a user from approving an action that they have initiated.
An approval function—either a special one for a particular kind of approval, or a general approval mechanism for managing anything that's waiting to be approved.
Each of these is discussed in its own section that follows.
Cannot Approve Own Action It is unacceptable to allow a user to approve an action that they have performed. Apply this rule to every kind of approval. There is nothing to be gained by not having it: simply let users perform the action without approval being necessary if that's what you want. But it's important to state this restriction explicitly in a requirement—or be prepared for it to be forgotten. Note that an approval step is sometimes used simply to involve a second person, who could be at the same level as the first user (not a supervisor)—hence the elegantly descriptive German term Vieraugen, four eyes. In such a case, both users might have the same permissions, and an explicit restriction of this sort is the only way to prevent one person from both entering and approving. Insisting that a user be unable to approve their own action is an example of an operational rule as per the specific authorization requirement pattern.
Summary | Definition |
|---|---|
Cannot approve own action | A user shall not be able to approve an action that they initiated. For any action that requires more than one approval, a user shall not be able to approve an action they have already approved. This requirement applies to every type of action that is subject to approval. It does not, however, preclude one user from being granted the ability to perform a function without approval (even if another user must obtain approval). |
Approval Mechanism An approval mechanism lets you see and pick items awaiting approval and go ahead and act on them. The simplest case looks after just a single kind of item (or a small number of fixed kinds).
If your system has more than one or two functions for which approval is needed, it could be worthwhile building or buying (and hence specifying) a general approval mechanism that can manage everything that's awaiting approval, to save duplicating the messy parts. This might include, for example, a function to display all items pending approval by the current user, regardless of what sorts they are. It could incorporate some kind of workflow support, and it could involve an infrastructure deserving of its own requirements specification. You would need to specify requirements for the pieces that make up a general mechanism of this sort. Such requirements could be wide-ranging and complex.
If prompt approval is needed, approvers must have an approval mechanism running all the time (or utilize some kind of notification mechanism). But what if they don't have it running? To work well for prompt response, this function must refresh itself (which is harder with some technologies than others).
Here's an example of a specific approval function:
Summary | Definition |
|---|---|
Employee vacation request approval | There shall be a function (intended to be used by the human resources department) that lists all pending vacation requests by employees in departments that are the responsibility of the current user. This function shall allow the user to select and view the details of any vacation request (as well as the employee's accrued vacation) and to approve or reject the request. |
If more than a couple of types of action need approval (or might in the future), consider building a generalized mechanism for storing any kind of unapproved action. This must be able to store anything that's yet to be approved, for which it needs to be flexible. Depending how sophisticated you want this mechanism to be, it could also provide a means for other functions to find out whether anything of interest to them is awaiting approval. For example, if a large bank account debit is awaiting approval, another function that wishes to know the balance of that account probably needs to take the pending debit into account. Also take care to protect this pending-action store against tampering.
Note that if we build a place to store pending (yet-to-be-approved) actions, this can also be used as the basis for handling timed and co-ordinated changes, as described in the introduction to the Chapter 7 chapter. So if you build a mechanism for one, you have a head start towards the other.
Concentrate on what sorts of things could happen between the action being initiated and its being approved. Has someone already figured out all the extra actions that users could take that could interfere with the action awaiting approval? A workflow (or equivalent) diagram is a particularly helpful form. If not, produce one—and be suspicious that the system might be incomplete. Identify all the possible states an approval request can be in, and the ways it can change state. Figure out all the actions that any of the people involved could take at any stage. Then test these possibilities and verify that the system handles them satisfactorily.