Understanding the Need for Security Controls
Identify the basic security issues associated with system/network design and configuration.
Think for a moment about the computer systems you use at work or home and about the information stored on those computers. Do you have information you consider confidential or highly sensitive? If it fell into the wrong hands, how much damage could result? What if your systems stopped working? How much time, money, and reputation would you lose if your company's Web site were no longer available? How could you protect your system from an outside attack?
When you think of how to make your network secure, you might consider protecting your information with passwords or encryption. You might also consider physically restricting contact with servers and other computers by locking your office and other rooms to prevent access to the system. Perhaps you have an Uninterruptible Power Supply (UPS) connected to your servers so that they continue to run in the event of a power outage.
Now think about the connections to these computers. Are they networked to other machines and to the Internet? If they are, you are even more vulnerable to attacks by unauthorized users. Such attacks can come from inside your network, from the Internet, or from other avenues of remote access.
NOTE
Hacker Versus Cracker Before you examine network security issues in depth, you should understand the difference between a hacker and a cracker. Traditionally, a hacker is someone who is very knowledgeable about computers and breaks in to systems with or without consent. For example, a hacker might be hired by a company to test its security system and procedures by trying to break in to a network. A hacker can also break in to a system or network without consent to expose a vulnerability to the security community. Generally speaking, hackers have benign intent. A cracker, on the other hand, breaks in to systems with malicious intent. Because the term hacker is familiar and commonly accepted, it is used in this book to indicate a person who breaks in to systems.
As computers become more powerful, more affordable, and more interconnected, security risks increase accordingly. Software development tools make it easier for programmers, as well as the less technically adept, to create sophisticated and dangerous applications. Thanks to the Internet, potential intruders have access to a growing quantity of easily available, ready-to-use hacking utilities. The Internet has become an open target for attacks, and any computer connected to it can be victimized. Because the geographical boundaries of network access have been dissolved, and because hackers can strike at any time from anywhere, protecting against computer attacks has become a full-time job.
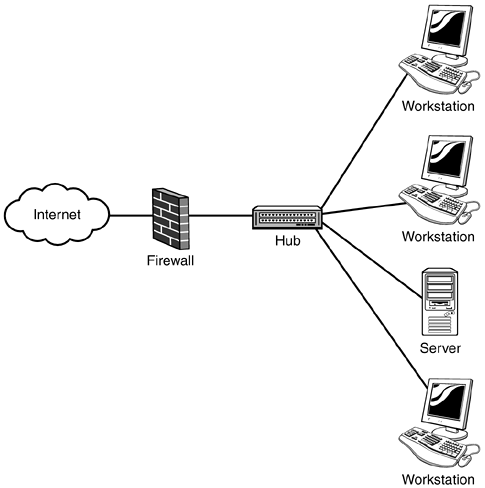
Figure 1.1 shows a network layout of a typical company's connection to the Internet. Client workstations and server machines are located behind the firewall. The machines inside the network are (or at least should be) protected from the outside world by the firewall. The rest of the outside world is also connected to the Internet. This is a common network configuration designed to protect network systems and data.
Figure 1.1. Connection to the Internet through a firewall.
EXAM TIP
Practical Information Remember that the TICSA exam focuses on practical, “real-world” information. Major areas of past security problems, such as the ones from the SANS Institute, are great fodder for TICSA exam questions.
However, this configuration alone does not protect the network. In May 1999, a group of nearly 2,000 computer security experts and managers met at the System Administration, Networking, and Security (SANS) conference in Baltimore, Maryland. The group determined the top seven management errors that lead to computer security vulnerabilities:
Assigning untrained people to maintain security
Failing to understand how information security relates to potential business problems
Failing to deal adequately with the operational aspects of security
Relying too heavily on a firewall to provide security
Failing to understand how much information is really worth
Applying short-term solutions to security problems and failing to fix problems correctly the first time
Pretending that the problem will go away
Most of these errors involve judgment or training, not system setup. Because companies face so many security issues on a daily basis, security administration is sometimes assigned to a team of four or five people, depending on the size of the organization. Unfortunately, your network is vulnerable to thousands of hackers. This is an unfair matchup from the start. Would you want to go into battle knowing that the bad guys outnumbered you a thousand to one? According to the CERT Coordination Center at Carnegie Mellon University, the Internet is an easy target for the following reasons:
The Internet allows millions of entry points worldwide, so attacks can come from virtually anywhere. Because of emerging technologies, such as wireless Internet, hackers can mount attacks even while on the move.
The Internet includes millions of interconnected machines. Using distributed processing, hackers can attack the Internet not with one computer, but with hundreds of machines working in unison.
Because the source code of many operating systems is readily available (Linux, for example), hackers can study the internal workings of these systems and find holes to exploit. Conversely, because the source code is available, developers can quickly correct the problems in the source code and, therefore, close the security vulnerability.
The Web and advances in rapid software development provide easy access to hundreds of ready-to-use hacker tools.
The ramifications of an attack on computer systems can be devastating. The effects can include destruction or alteration of data, financial loss, misuse of computer system resources, and damage to public confidence. According to vnunet.com, a group of hackers defaced more than 200 Web sites in one minute in August 2001. The previous year, a hacker used a public Web site to post the credit card numbers, names, and addresses of an online retailer's customers. Although the veracity of these claims may be questionable, attacks on Web sites, especially those that host electronic commerce services, can be among the most destructive.
The Computer Emergency Response Team (CERT) (www.cert.org) tracks computer security incidents and vulnerabilities. Figure 1.2 shows how vulnerabilities have increased since 1995. In fact, more vulnerabilities were reported in the first two quarters of 2001 than in the previous year as a whole.
Figure 1.2. Number of reported vulnerabilities.

CERT also tracks the number of attacks on computers. As shown in Figure 1.3, only six incidents were reported in 1988, but by the first half of 2001, the number had surpassed 15,000. And the statistics could be significantly higher; these figures represent only the vulnerabilities and incidents that were actually reported. It's a well-documented fact that many companies systematically suppress reports of attacks against their systems as a matter of policy. They fear (justifiably) that publicizing these events would result in a loss of customer and/or investor confidence.
Figure 1.3. Number of reported security incidents.

One of the most common security problems is viruses sent via email, such as the infamous ILOVEYOU virus. An innocent-looking email turned into a security nightmare for many organizations around the world. According to a study by the International Computer Security Association (ICSA), the likelihood that a medium or large company would encounter a virus increased almost a hundredfold during the six years between 1994 and 2000. Without proper security controls in place, companies are vulnerable to email viruses. Employee training, combined with a solid security policy and adequate antivirus-filtering software, can prevent many of these problems.
Computer system security is an ongoing process, and is not limited to virus protection or a few security patches to the operating system. Organizations rely on their computer systems to provide information and data access when they need it. Anything that limits such access can seriously damage a company's finances and its reputation.
