Apply Your Knowledge
Exercises
2.1. Attempting an ICMP Attack
In this project, you use a Winnuke program to send an ICMP attack against another system. Any system you attack with Winnuke will likely repel the attack (especially any operating system beyond Windows 95). Regardless, if the attack succeeds, this project shows you how quick and easy it is to use a Winnuke attack against a system.
Estimated Time: 15 minutes
1. | Start your computer and log on, if necessary. |
2. | Install Winnuke GUI on your Windows 2000 system. Note that you can also obtain Winnuke as a script for Linux/Unix, or for DOS/Windows. |
3. | Run Winnuke. A GUI appears asking you to insert an IP address and enter a message to display on the screen when the nuke is successful. Type the IP address for a Windows system that can be attacked safely. |
4. | Click the NUKE button. After a few seconds, either Winnuke reports a successful nuke or it reports “nuke failed” or “couldn't connect,” if the system being attacked is either patched or was an unrecognized operating system. |
5. | If the nuke was successful, the system attacked should show the attack message you entered in a pop-up box, and the system should display either a General Protection error or be entirely unstable and crash after a bit of usage. |
6. | Close Winnuke. |
2.2. Viewing Active TCP and UDP Connections
In this project, you learn how to see currently active UDP and TCP connections on a system using Netstat, a simple utility included with Windows (any version). Netstat can provide you with information about the network connection(s) in your computer, including open ports, the amount of data transferred, and more. This information can help you see what ports are open on your system that may have to be closed.
Estimated Time: 10 minutes
1. | To open a command-prompt window, click Start, click Run, type cmd in the Open text box, and then click OK. |
2. | On the command line, type netstat -a, and then press Enter. Running the netstat utility with the –a switch tells netstat to display all active connections and open ports on the system. A sample output of this command is shown in Figure 2.8. This particular output is from a Windows 2000 Server system with Exchange 2000 installed and running. NOTE The first column indicates the protocol (TCP or UDP), the next signifies the name of the system (the port number for this particular connection or port comes after the colon), and the final column generally gives connection information including whether it is established or closed. |
3. | After you finish viewing the output of this command, close the command-prompt window by typing exit and then pressing Enter. |
2.3. Creating an IPSec Policy
In this project, you learn how to create a quick and simple IPSec security policy in Windows 2000. Windows 2000 allows for an easily manageable way to provide stronger IP security right out of the box, without the use of additional software. Even the basic IPSec included in Windows 2000 is flexible enough to allow you to create simple or even very specific IPSec rules and security settings for you to use on your network.
Estimated Time: 20 minutes
1. | To open the Local Security Settings console, click Start, point to Programs, point to Administrative Tools, and then click Local Security Policy. The console is shown in Figure 2.9. In this console, you can configure various security-related settings for Windows 2000, but the option you focus on in this project is the IP Security Policies on Local Machine. |
2. | Right-click IP Security Policies on Local Machine in the Tree pane, and then click Create IP Security Policy to open the IP Security Policy Wizard. |
3. | In the Welcome to the IP Security Policy wizard window, click Next to start the wizard. The IP Security Policy Name dialog box opens. |
4. | In the Name text box, delete the default name and type Test Security. In the Description text box, type "Testing the security policy wizard". Click Next. The Requests for Secure Communication dialog box opens. |
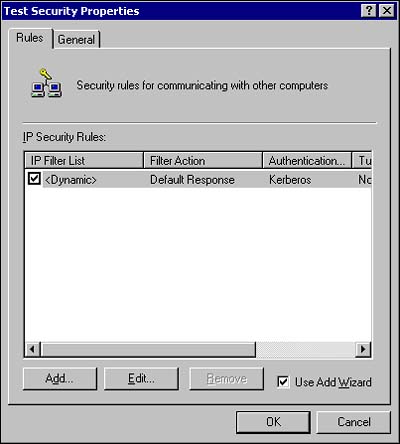
5. | This dialog box allows you to specify that the default response rule is enabled, which allows IPSec to respond to any requests for a secure communication when using this policy. Verify that there is a check mark next to the <Dynamic> option (as shown in Figure 2.10), and then click Next. The Default Response Rule Authentication Method dialog box opens. Figure 2.10. Test Security Properties dialog box.
|
6. | You must specify the type of security rule you want to use for this policy. If the only systems you will connect to are Windows 2000 systems, use the Windows 2000 default (Kerberos V5 protocol) option. If you connect to other operating systems, you should use a certificate from a certificate authority, or a key that you type in yourself. For this project, verify that Windows 2000 default (Kerberos V5 protocol) is checked, and then click Next. The Complete the IP Security Policy Wizard dialog box opens. |
7. | It states you have successfully created a new policy and gives you the option to edit the properties of the policy after the wizard is complete. Verify that Edit Properties is checked, and then click Finish to complete the wizard. |
Review Questions
| 1: | After data has passed through the various layers of the TCP/IP model and all the header and frame information has been added to the packet, the result is called a ________________. |
| 2: | What two popular attacks can be used to flood ICMP data in the hopes to crash the targeted server? |
| 3: | How could having your FTP server configured to allow uploads on the same partition as your operating system lead to potential problems with intrusion and other attacks? |
| 4: | To secure data passed between Web browsers and Web servers, you can use Secure Sockets Layer (SSL) to improve data security. What technology is used when implementing SSL to secure this data? |
| 5: | What is the main benefit of having a negotiated TCP/IP connection as you would with TCP rather than an unnegotiated connection using UDP? |
Exam Questions
| 1: | In 1985, Bob Morris noticed problems in the way TCP/IP handshakes took place when systems were connecting to one another. These problems could lead to hackers doing what?
|
| 2: | From the following selections, which two are possible causes for the lack of a single one-size-fits-all security model for every server and system?
|
| 3: | The address information in the IP header can be very useful, but it adds some additional size to a packet. What size is an IP header?
|
| 4: | Because of the way TCP/IP sends data across a network, a hacker can sometimes take advantage of TCP/IP data. Which of the following two options could cause vulnerabilities?
|
| 5: | Which layer of the OSI model is considered to be the base, or lowest level, of the model?
|
| 6: | Which command is used to end a TCP/IP handshake?
|
| 7: | Which layer of the OSI network model controls the flow of data between systems?
|
| 8: | Which layer of the OSI network model is considered the most difficult layer to secure?
|
| 9: | What is a major difference between the UDP and TCP protocols?
|
| 10: | Approximately how many ports are available on any given system for TCP connections?
|
| 11: | Which of the TCP/IP network model layers is often called the IP stack?
|
| 12: | Of the major TCP/IP network services that can be accessed, which would most likely be used to plant a Trojan horse on a server for a hacker to activate manually?
|
| 13: | Keeping Question 12 in mind, what TCP/IP network service would the hacker most likely use to activate that planted Trojan horse?
|
| 14: | Which two of the following options are components of a basic IP packet?
|
| 15: | An IP packet has frames added to every packet sent. These frames are used to tell the NIC sending and receiving the packet when to start receiving that packet and when to stop. What are the names used to signify the beginning and end of a frame of an IP packet?
|
Answers to Review Questions
| A1: | The resultant packet with the additional information is called a TCP Segment. See the section, “Basic TCP/IP Principles.” |
| A2: | Winnuke and Tribal Flood Network (TFN) are two very popular ICMP attacks that could, if effective enough, crash systems and servers that are not patched to protect against these attacks. Most common operating systems are now patched to stop these types of attacks from being effective. See the section “Network Layer.” |
| A3: | A hacker could potentially upload a Trojan or other malicious program and these could be executed remotely via a Web browser or if someone runs the Trojan or malicious program locally by accident. See the section “File Transfer Protocol.” |
| A4: | Encryption is the technology used behind SSL and most major TCP/IP security solutions. See the section “Secure Sockets Layer.” |
| A5: | When data is sent in segments, packets could become lost or corrupted on their way to the destination. By having a negotiated connection, TCP/IP can determine whether any packets are missing and rerequest the information from the connection sending the data. See the section “Transport Layer.” |
Answers to Exam Questions
| A1: | B. Bob Morris noticed problems that would allow hackers to force a network connection. See the section “Basic TCP/IP Principles.” |
| A2: | A, C. Possible causes for a lack of a one-size-fits-all security model are companies that have their own specific security needs and that software and configuration differs from organization to organization. See the section “The OSI Network Reference Model.” |
| A3: | D. The additional size added to a packet for the IP header is 20 bytes. See the section “Structure of an IP Datagram.” |
| A4: | A, B. Two circumstances in which vulnerabilities could exist are when the header in a packet can be modified and when a packet arrives out of order, which allows for possible rogue packets to be introduced into the packet stream. See the section “Structure of an IP Datagram.” |
| A5: | D. The Physical layer is considered to be the base level of the OSI model because it represents the layer that actually connects networks together, upon which the other layers are built. See the section “The OSI Network Reference Model.” |
| A6: | D. The command used to end a TCP/IP handshake is FIN. See the section “TCP Handshakes and Headers.” |
| A7: | B. The layer of the OSI model that controls the flow of data between systems is the Transport layer. See the section “The OSI Network Reference Model.” |
| A8: | C. The layer most commonly considered the hardest to secure is the Application layer because of the wide variance in software and configuration. See the section “The OSI Network Reference Model.” |
| A9: | B. The main difference between TCP and UDP. TCP allows for missing data to be re-sent. See the section “Transport Layer.” |
| A10: | A. There are typically 65,000 or more ports available for TCP connections on any system. See the section “System Ports.” |
| A11: | C. The layer that is commonly called the IP stack is the TCP & UDP layer in the TCP/IP network model. See the section “The TCP/IP DARPA Network Model.” |
| A12: | B. The most likely network service that would be used to plan Trojan horse programs is FTP because of its simplicity and generally direct access to the server's hard drive and directories if not set up properly. See the section “File Transfer Protocol.” |
| A13: | C. Once planted on the server, a hacker would likely use HTTP to activate the Trojan because it can be used to navigate directories and remotely execute programs. See the section “Hypertext Transfer Protocol.” |
| A14: | B, D. Both the IP header and IP footer are components of a basic core IP packet. See the section “Structure of an IP Datagram.” |
| A15: | A, D.The name of the beginning of an IP packet is a frame header, and the name of the end of an IP packet is a frame trailer. See the section “Structure of an IP Datagram.” |
Suggested Readings and Resources
1. www.microsoft.com/security/—General Microsoft security Web site
2. http://www.microsoft.com/ntserver/techresources/commnet/TCPIP/TCPIntrowp.asp—A general introduction to TCP/IP by Microsoft
3. http://www.microsoft.com/mind/1098/tcpip/tcpip.asp/inthisissuecolumns1098.htm—The ABCs of TCP/IP from the MSDN