Network Security
In this chapter, we examine how we might protect our networks from a variety of different angles. We go over secure network design and segmentation, ensuring that we have the proper choke points to enable control of traffic and that we are redundant where redundancy is needed. We look into the implementation of security devices such as firewalls and intrusion detection systems, the protection of our network traffic with virtual private networks (VPNs) and security measures specific to wireless networks when we need to use them, and the use of secure protocols. We also consider a variety of security tools, such as Kismet, Wireshark, Nmap, honeypots, and other similar utilities.
Keywords
Design; firewall; honeypot; IDS; intrusion detection; Kismet; network; network security; Nmap; segmentation; traffic; virtual private network; VPN; Wireshark
Information in This Chapter
Introduction
In the world of network security, we may face a number of threats from attackers, misconfigurations of infrastructure or network-enabled devices, or even from simple outages. As network dependent as the majority of the world is, loss of network connectivity, and loss of the services that such networks provide, can be annoying, at best, and can be potentially devastating to businesses.
In early September 2013, civil unrest in Sudan reached a high point, with large-scale protests prompted by a decision on the part of the Sudanese government to end subsidies on fuel. In what appears to have been an attempt to reign in the protestors, the government deliberately disconnected almost the entire country from the global networks that comprise the Internet. This was accomplished by removing all routes from the global routing tables, as well as closing down the gateways that provide access to the Internet [1]. Sudan remained off-line for approximately 24 h, before access was restored. The impact of such an event can be felt in a wide variety of social, personal, and business-impacting ways.
Although the situation in Sudan may be an extreme example, we can see serious impact from the wide variety of smaller network outages and issues that occur all over the world every day. Some of these problems may be the result of technical issues, some may be the result of distributed denial of service (DDoS) attacks (discussed later in this chapter), and some may be temporary and due to causes entirely unknown to the network users.
In this chapter, we will discuss some of the issues in protecting networks, and the various infrastructure and devices we might put in place to do so. We will also talk about protecting network traffic as it moves over networks, and some of the tools we might use to verify our security.
Protecting networks
We can look to a variety of avenues to protect our networks and network resources against the array of threats we might face. We can add security in the form of network design by laying out our networks in a fashion that makes them inherently more secure and resistant to attack or technical mishap. We can also implement a variety of devices at the borders of, and within, our networks to increase our level of security, such as firewalls and intrusion detection systems (IDSes).
Security in network design
Proper network design provides us with one of the chief tools we have to protect ourselves from the variety of network threats we might face. A well-configured and patched network is the foundation of any security program. With a properly laid out network, we can prevent some attacks entirely, mitigate others, and, when we can do nothing else, fail in a graceful way.
Network segmentation can go a long way toward reducing the impact of such attacks. When we segment a network, we divide it into multiple smaller networks, each acting as its own small network called a subnet. We can control the flow of traffic between subnets, allowing or disallowing traffic based on a variety of factors, or even blocking the flow of traffic entirely if necessary. Properly segmented networks can boost network performance by containing certain traffic to the portions of the network that actually need to see it and can help to localize technical network issues. Additionally, network segmentation can prevent unauthorized network traffic or attacks from reaching portions of the network to which we would prefer to prevent access, as well as making the job of monitoring network traffic considerably easier.
Another design factor that can be of assistance in the goal of securing our networks is to funnel network traffic through certain points where we can inspect, filter, and control the traffic, often referred to as choke points. The choke points might be the routers that move traffic from one subnet to another, the firewalls or proxies that control traffic moving within, into, or out of our networks or portions of our networks, or the application proxies that filter the traffic for particular applications such as Web or e-mail traffic. Choke points come with some risk because if they fail the network is compromised. We will discuss some of these devices at greater length in the next section of this chapter.
Redundancy in network design can prove to be another major factor in helping to mitigate risk to our networks. Certain technical issues or attacks may render unusable portions of our networks, network infrastructure devices, border devices such as firewalls, or a number of other components that contribute to the functionality of our networks. Good network design includes planned redundancy for devices failing, connectivity being lost, or coming under attack to the point that they are rendered useless or we lose control of them. For example, if one of our border devices is being subjected to a DDoS attack, there are few steps we can take to mitigate the attack. We can, however, switch to a different connection to the Internet, or route traffic through a different device until we can come to a longer-term solution.
Firewalls
A firewall is a mechanism for maintaining control over the traffic that flows into and out of our network(s). The concept and first implementations of firewall technologies can be traced back to the late 1980s and early 1990s. One of the first papers to discuss the idea of using a firewall is titled “Simple and Flexible Datagram Access Controls,” written in 1989 by Jeffrey Mogul [2], then at Digital Equipment Corporation (DEC). We can also see the first commercial firewall from DEC, the DEC SEAL, which shipped in 1992 [3].
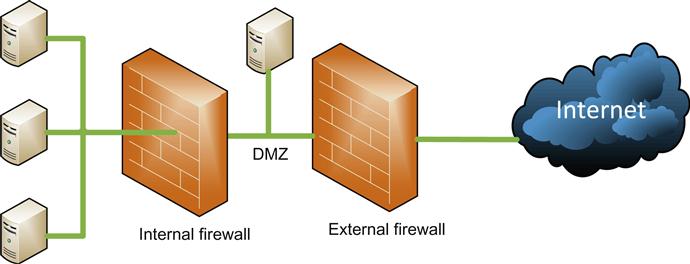
A firewall is typically placed in a network where we see the level of trust change. We might see a firewall on the border between our internal network and the Internet, as shown in Figure 10.1. We may also see a firewall put in place on our internal network to prevent network traffic of a sensitive nature from being accessed by those that have no reason to do so.
Many of the firewalls in use today are based on the concept of examining the packets that are coming in over the network. This examination determines what should be allowed in or out. Whether the traffic is allowed or blocked can be based on a variety of factors and largely depends on the complexity of the firewall. For example, we might allow or disallow traffic based on the protocol being used, allowing Web and e-mail traffic to pass, but blocking everything else.
Packet filtering
Packet filtering is one of the oldest and simplest of firewall technologies. Packet filtering looks at the contents of each packet in the traffic individually and makes a gross determination, based on the source and destination IP addresses, the port number, and the protocol being used, of whether the traffic will be allowed to pass. Since each packet is examined individually and not in concert with the rest of the packets comprising the content of the traffic, it can be possible to slip attacks through this type of firewall.
Stateful packet inspection
Stateful packet inspection firewalls (generally referred to as stateful firewalls) function on the same general principle as packet filtering firewalls, but they are able to keep track of the traffic at a granular level. While a packet filtering firewall only examines an individual packet out of context, a stateful firewall is able to watch the traffic over a given connection, generally defined by the source and destination IP addresses, the ports being used, and the already existing network traffic. A stateful firewall uses what is called a state table to keep track of the connection state and will only allow traffic through that is part of a new or already established connection. Most stateful firewalls can also function as a packet filtering firewall, often combining the two forms of filtering. For example, this type of firewall can identify and track the traffic related to a particular user-initiated connection to a Web site, and knows when the connection has been closed and further traffic should not legitimately be present.
Deep packet inspection
Deep packet inspection firewalls add yet another layer of intelligence to our firewall capabilities. Deep packet inspection firewalls are capable of analyzing the actual content of the traffic that is flowing through them. Although packet filtering firewalls and stateful firewalls can only look at the structure of the network traffic itself in order to filter out attacks and undesirable content, deep packet inspection firewalls can actually reassemble the contents of the traffic to look at what will be delivered to the application for which it is ultimately destined.
To use an analogy, if we ship a package via one of the common parcel carriers, the carrier will look at the size and shape of the package, how much it weighs, how it is wrapped, and the sending and destination addresses. This is generally what packet filter firewalls and stateful firewalls can do. Now, if the parcel carrier were to do all of this as well as open the package and inspect its contents, then make a judgment as to whether the package could be shipped based on its contents, this would be much more in line with deep packet inspection.
Although this technology has great promise for blocking a large number of the attacks, we see today it is slower and introduces some delay. Additionally the question of privacy is also raised. In theory, someone in control of a deep packet inspection device could read every one of our e-mail messages, see every Web page exactly as we saw it, and easily listen in on our instant messaging conversations.
Proxy servers
Proxy servers are ultimately a specialized variant of a firewall. These servers provide security and performance features, generally for a particular application, such as mail or Web browsing. Proxy servers can serve as a choke point (discussed earlier in the chapter) in order to allow us to filter traffic for attacks or undesirable content such as malware or traffic to Web sites hosting adult content. They also allow us to log the traffic that goes through them for later inspection, and they serve to provide a layer of security for the devices behind them, by serving as a single source for requests.
Proxy servers are nearly ubiquitous in the business world, largely due to the filtering capability they provide. Many companies rely on them to keep the large amounts of spam that flow over e-mail from reaching their users and lowering productivity. We also see them used to filter Web traffic in such environments in order to keep employees from visiting Web sites that might have objectionable material and to filter out traffic that might indicate the presence of malware. Again the major issue with them is delay introduced with additional step of inspection.
DMZs
A DMZ, or demilitarized zone, is generally a combination of a network design feature and a protective device such as a firewall. As we discussed earlier in the “Security in Network Design” section, we can often increase the level of security on our networks by segmenting them properly. When we look at systems that need to be exposed to external networks such as the Internet in order to function, such as mail servers, proxy servers, software as a service application, and Web servers, we need to ensure their security and the security of the devices on the network behind them. We can often do this by putting a layer of protection between the device, such as our mail server, and the Internet, and between the rest of our network and the device, as shown in Figure 10.2.
This allows only the traffic that needs to reach the mail server—for instance, Internet Message Access Protocol (IMAP) and Simple Message Transfer Protocol (SMTP) on ports 143 and 25, respectively—to reach our mail server, and the same ports to pass through on our network. Presuming that no other services are running on the same system, we could restrict the traffic going into and out of the DMZ where our mail server sits to those particular ports.
Network intrusion detection systems
IDSes monitor the networks, hosts, or applications to which they are connected for unauthorized activity. There are several types of IDSes, including host-based intrusion detection systems (HIDSes), application protocol-based intrusion detection systems (APIDSes), and network-based intrusion detection systems (NIDSes). We will focus on NIDSes in this chapter, returning to HIDSes and APIDSes in Chapters 11 and 12, respectively.
NIDSes will typically be attached to the network in a location where they can monitor the traffic going by, but they need to be placed carefully so that they are not overloaded. Placing an NIDS behind another filtering device, such as a firewall, can help to eliminate some of the obviously spurious traffic in order to decrease the traffic the NIDS needs to inspect. As NIDSes need to examine a large amount of traffic on a typical network, they can generally do only a relatively cursory inspection in order to determine whether the situation on the network is normal or not. Because of this, an NIDS may miss some types of attacks, particularly those that are specifically crafted to pass through such inspections. Packet crafting attacks involve very specifically designed packets of traffic that carry attacks or malicious code, but are designed to avoid detection by IDSes, firewalls, and other similar devices. Combining functions like firewalls and IDSs into one correlated capability starts the defense in depth security program organizations depend on today.
IDS detection methods
IDSes are often classified by the way they detect attacks. In general, they are divided into two main categories: signature-based detection and anomaly-based detection.
Signature-based IDSes work in a very similar fashion to most antivirus systems. They maintain a database of the signatures that might signal a particular type of attack and compare incoming traffic to those signatures. In general, this method works well, except when we encounter an attack that is new, or has been specifically constructed in order to not match existing attack signatures. One of the large drawbacks to this method is that many signature-based systems rely solely on their signature database in order to detect attacks. If we do not have a signature for the attack, we may not see it at all. In addition to this, the attacker crafting the traffic may have access to the same IDS tools we are using and may be able to test the attack against them in order to specifically avoid our security measures.
The other major method of IDS detection is anomaly-based detection. Anomaly-based IDSes typically work by taking a baseline of the normal traffic and activity taking place on the network. They can measure the present state of traffic on the network against this baseline in order to detect patterns that are not present in the traffic normally. Such methods can work very well when we are looking to detect new attacks or attacks that have been deliberately assembled to avoid IDSes. On the other hand, we may also see larger numbers of false positives from anomaly-based IDSes than we might from signature-based IDSes. If the traffic on the network changes from what was present when we took our baseline, the IDS may see this as indicative of an attack and likewise for legitimate activity that causes unusual traffic patterns or spikes in traffic.
We can, of course, put an IDS in place that gives us some of the advantages of each type of detection and use both the signature-based and anomaly-based methods in a single IDS. This will allow us much more flexibility in detecting attacks, although perhaps at the expense of operating a bit more slowly and causing a lag in detection.
Protecting network traffic
In addition to protecting our networks from intrusion, we also need to look to the traffic that flows over them. In line with the concept of defense in depth, we want to put in place as many layers of security as is appropriate for the value of what we are securing. Even when we are in an environment that we consider to be secure, we may be subject to a variety of attacks, and we would be foolish to not put protections in place in anticipation of such an eventuality occurring.
The impact of intercepted data
One of the largest concerns when we are sending sensitive data over a network is of having the data intercepted by someone that might misuse it. Given the many networks available today in offices, hotels, coffee shops, restaurants, and other places, the opportunity to accidentally expose data to an attacker is large.
When we send data over networks that are not secure or trusted, an eavesdropper can glean a large amount of information from what we send. If we use applications or protocols that do not encrypt what they are sending over the network, we may end up giving our login credentials, credit card numbers, banking information, and other data to anyone that happens to be listening.
Data can be intercepted from both wired and wireless networks, often with very little effort, depending on the design of the network. We will discuss some of the tools that can be used to perform such interception later in the chapter.
Wireless exposure
Wireless networks, in particular, are one of the major security risks when we consider places where our data might be exposed. Free wireless Internet access is commonly provided today in a number of places. Although it may be nice to be able to get network access for free, many people do not understand the security risk that accompanies such a service. In general, such networks are set up without a password and without encryption of any kind, which we would normally see in place in order to protect the confidentiality of the traffic flowing over the network. Even in cases where a password is required to access the network, such as we might find in a hotel, if everyone else in the hotel is on the network as well, they may be able to see our data.
Although such insecure networks are a security problem, they are not an insurmountable one. We will discuss one of the tools we might use to secure such connections in the next section.
Virtual private networks
The use of virtual private networks (VPNs) can provide us with a solution for sending sensitive traffic over unsecure networks. A VPN connection, often referred to as a tunnel, is an encrypted connection between two points. This is generally accomplished through the use of a VPN client application on one end of the connection and a device called a VPN concentrator on the other end. The client uses the software to authenticate to the VPN concentrator, usually over the Internet, and after the connection has been established, all traffic exchanged from the network interface connected to the VPN flows through the encrypted VPN tunnel.
VPNs are often used to allow remote workers to connect to the internal resources of an organization. When such a connection has been established, the connected device is able to act as though it were connected directly to the internal network of the organization hosting the connection. This can be very useful as it allows us to enable greater access for a remote worker than we would normally be able to do securely when the worker is outside the borders of our network.
In addition to allowing us access to the internal resources of our organization, VPNs may also be used to protect or anonymize the traffic we are sending over untrusted connections. Companies such as StrongVPN sell their services to the public for exactly such purposes, allowing us to protect the contents of our traffic from logging by our Internet service providers (ISPs) or being sniffed by others on the same network, to obscure our geographical location and bypass location-oriented blocking.
Such services are also popular with those that engage in peer-to-peer (P2P) file-sharing services. Such activity is often flagged by ISPs and by organizations such as the Motion Picture Association of America (MPAA) and the Recording Industry Association of America (RIAA) in order to prosecute those engaged in copyright infringement. VPNs can allow both the traffic and the actual IP addresses of those that engage in such activities to remain hidden from those that would seek them out.
Wireless network security
As we discussed earlier in this chapter, unsecured wireless networks freely broadcast our data for anyone with the appropriate (and very common) technology to hear. The present record for an unamplified 802.11 wireless connection is about 237 miles [4]. Although this was under ideal conditions, it does give us some idea of how far our wireless signals might carry. This means that, even in a much less favorable radio frequency (RF) environment, such as we might find in a residential area, someone miles away, with the right antenna, could potentially be eavesdropping on our network traffic.
In addition to the issues with our traffic being potentially listened in on, there is also the possible issue of wireless devices being placed without our knowledge. In particular, wireless access points being attached to our network without authorization, commonly known as rogue access points, can present a serious security issue.
For example, if we worked in an area where wireless was prohibited, we might find that an enterprising individual decided to bring in an access point of his or her own and install it under his or her desk, in order to provide wireless access to a nearby outdoor smoking area. Although this might not have been done with bad intentions in mind, this one simple action may have invalidated the entire set of carefully planned network security measures we have put in place by creating a back door.
If the rogue access point in our example was set up with poor security or no security at all, our well-intentioned access point installer would have just provided anyone within range of the access point with an easy path directly into our network, bypassing any border security that we might have in place. There is a possibility that a network IDS might pick up the activity from the rogue access point, but there is no guarantee of this. The simple solution to finding such rogue equipment is to carefully document the legitimate devices that are part of the wireless network infrastructure and regularly scan for additional devices using some of the wireless scanning tools which we will discuss later in this chapter.
For the legitimate and authorized devices on our network, our chief method of protecting the traffic that flows through them is the use of encryption. The encryption used by 802.11 wireless devices, the most common of the wireless family of network devices, breaks down into three major categories: Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and Wi-Fi Protected Access version 2 (WPA2). Of these, WPA2 is the most current and offers the strongest inherent security.
Secure protocols
One of the simplest and easiest ways we can protect our data is to use secure protocols. Many of the more common and older protocols, such as File Transfer Protocol (FTP) for transferring files, Telnet for interacting with remote machines, Post Office Protocol (POP) for retrieving e-mail, and a host of others, deal with data in an insecure manner. Such protocols often send sensitive information, such as logins and passwords, in cleartext (remember back to Chapter 5) over the network. Anyone listening on the network with a properly positioned sniffer can pick up the traffic from such protocols and easily glean the sensitive information from the traffic they send.
Many insecure protocols have secure equivalents, as we will discuss at greater length in Chapter 12. In brief, we can often find a secure protocol with the type of traffic we wish to carry. Instead of operating over the command line with Telnet, we can use Secure Shell (SSH), and instead of transferring files with FTP, we can use Secure File Transfer Protocol (SFTP), which is also based on SSH.
SSH is a very handy protocol for securing communications as we can send many types of traffic over it. It can be used for file transfers and terminal access, as we mentioned, and to secure traffic in a variety of other situations, such as when connecting to a remote desktop, communicating over a VPN, mounting remote file systems, and any number of other tasks. The encryption used by SSH is RSA, a public key encryption algorithm.
Mobile device security
As mobile devices become more prevalent all the time, they also represent a number of security issues. Such devices are fairly powerful in the sense of hardware resources and capabilities, and are generally connected to a network of some variety at all times. They move in and out of environments with regularity, store and transmit data without notice, and may or may not be compliant with basic security measures that we would consider normal on any standard “nonmobile” computer.
What is a mobile device?
When we hear the term mobile device discussed, we typically think of smartphones and tablets, at the present time largely running IOS from Apple or Android from Google, with a smattering of others thrown in. Additionally, there are a variety of head-mounted devices, smartwatches, and all manner of other devices. Finally we have USB or thumb drives. Mobile devices are used to send and receive e-mail, surf the web, manipulate documents, play videos, listen to music, play games, and numerous other activities; in short, these devices can perform most of the same functions as a nonmobile device.
The definition of what is and is not a mobile device has become considerably more blurred in recent years. Presently we have smartphones which rival the processing power and storage of some computers and have similarly capable operating systems. On the other hand, we have computers, including very small and light ultrabooks and devices such as the Raspberry Pi which run on minimal hardware and use very little power, some even running “mobile” operating systems such as Android. As distinguishing between these devices is largely a question of design philosophy rather than physical capability, the general inclination is to treat them the same from a security perspective. The most practical definition is any device that can access external systems or be acceded while not behind the organizations’ security infrastructure.
One of the potential areas where the difference between mobile and other devices actually is visible, from a security perspective, is centralized management of the data on them.
Mobile device management
While most devices that are not running a mobile operating system, that is, Windows, OS X, Linux, etc. have a well-established seat of tools and features that allow them to be centrally managed, this may not hold true with mobile devices. We generally want to be able to mandate patching and software upgrades, force changing of passwords at some interval, regulate and track installed software, adjust settings to a standard dictated by our policies, and a number of other similar functions. In order to enable these types of tasks, we generally turn to an external Mobile Device Management (MDM) solution such as those developed by Good Technologies, MobileIron, and a number of others.
The exact architecture of an MDM solution will vary from one vendor to another, but most utilize an agent on the mobile device that exists to enforce a certain configuration on the client. These agents typically regulate access to enterprise resources, such as e-mail, calendaring, or network resources, and can discontinue access by the client in the event that it becomes noncompliant in configuration, is stolen, or the user’s employment is terminated. Additionally, many MDM solutions enable the device to be remotely wiped, either completely or just corporate data, and/or disabled entirely.
As the distinction between mobile and nonmobile devices becomes narrower all the time, vendors of MDM solutions have begun to implement support of some devices that have been traditionally considered nonmobile. While this may seem like a considerable overlap with existing enterprise management tools, the ability to remotely manage both mobile and nonmobile devices using the same tools and techniques would result in less load on administrative resources, and would enable a greater uniformity across the set of devices in question.
Bring your own device
The term Bring Your Own Device (BYOD) is often brought up when discussing mobile device security. BYOD generally refers to an organization’s strategy and policies regarding the use of personal versus corporate devices. This can range from only corporate-owned devices being allowed to interact with enterprise resources to only personal devices being used and any combination in between. BYOD is very popular with folks managing the budget because they are leveraging equipment that the organization didn’t pay for. In some cases, they will push to move to BYOD without addressing the security because of the savings.
Allowing only corporate-owned devices can enable a considerably more uniform and secure base of mobile devices for the organization to manage. Depending on the policy implementation, we may choose to disallow the use of personal e-mail and file-sharing applications, for instance, and disable the capability of installing new applications that are not business related through an MDM solution, as discussed earlier in this section. We can also force users to install updates and security patches, change their password regularly, and any number of similar items which lead to a more secure mobile environment.
Choosing the other end of the spectrum, in which only personal devices are used and are not managed with MDM, precludes the use of many of these capabilities. Although some tools do exist that allow minimal control over devices as a function of connecting them to a centralized mail server, such as Microsoft Exchange, without active monitoring a savvy technical user can often subvert such measures with a small amount of effort. While this may be a good choice for a very small organization with minimal resources to administer a complex mobile infrastructure, this would likely not be optimal for a large enterprise.
The middle path, adopted by many organizations, is to allow some measure of each. In many cases, this results in a mix of personal and corporate-owned devices, perhaps with some restriction of capabilities for those with personal devices. In this way, we can allow the more secure and more trusted devices access to a greater set of resources, while still allowing personal devices to access basic services such as e-mail, providing that they agree to have these devices managed by an MDM tool and accept a reasonable set of security features. At the end of the day, this is a balance between cost and risk management.
Network security tools
We can use a broad variety of tools to improve our network security. Many of these tools are the same as those used by attackers penetrating our networks, and this is one of the main reasons they are useful to us. The only difference is security tools are used by authorized users. It would not be wise to use any of the tools discussed in this book without clear written permission. We can use the same tools attackers use to penetrate our defenses in order to shore them up. By using such tools to locate security holes in our networks, we can patch up these holes to keep the attackers out.
More advanced
An enormous number of security tools are on the market today, and many of them are free or have free alternatives. Many run on Linux operating systems, and some of them can be a bit difficult to configure. Fortunately, we can try out such tools without having to set them up by using one of the Security Live CD distributions that come with all of the tools preconfigured. One of the better-known and more thorough distributions is Kali, available for download at http://www.kali.org/.
The key to using such an assessment strategy is to conduct assessments thoroughly and regularly enough that we are able to find the holes before the attackers do. If we only perform such testing, commonly known as penetration testing, on an occasional and shallow basis, we will likely not catch all the issues present in our environment. Additionally, as the various network hardware devices and the software running on them are updated, added, or removed over time, the vulnerabilities present in our environment will change as well. It is also important to note that the vast majority of the tools we might use will only be capable of finding known issues. New or unpublished attacks or vulnerabilities, commonly known as zero-day attacks, can still take us by surprise when they surface.
Wireless
As we discussed earlier in the chapter, attackers accessing a wireless device can potentially bypass all our carefully planned security measures. Worse yet, if we do not take steps to ensure that unauthorized wireless devices, such as rogue access points, are not put in place on our network, we could be allowing a large hole in our network security and never know it.
We can use several tools to detect wireless devices. One of the best-known tools for detecting such devices is called Kismet, which runs on Linux and can be found on the Kali distribution. Kismet is commonly used to detect wireless access points and can find them even when attempts have been made to make doing so difficult. A similar piece of software, called NetStumbler, exists for Windows, although it does not have as full a feature set as Kismet.
In addition to detecting wireless devices, some tools can enable us to break through the different varieties of encryption that are in use on such networks. Many tools for such purposes exist, but a few of the more common ones for cracking WEP, WPA, and WPA2 include coWPAtty and Aircrack-NG.
Port scanners
Scanners are one of the mainstays of the security testing and assessment industry. We can generally break these into two main categories: port scanners and vulnerability scanners. There is some overlap between the two, depending on the particular tool we are talking about.
One of the more famous port scanners that we might want to use is a free tool called Nmap, short for network mapper. Although Nmap is generally referred to as a port scanner, we actually do it a bit of a disservice to call it that. Although Nmap can conduct port scans, it can also search for hosts on a network, identify the operating systems those hosts are running, detect the versions of the services running on any open ports, and much more.
For the most part, in terms of network security, scanners are the most useful when used as a tool for discovering the networks and systems that are in our environment. We will discuss some of the uses for scanners that are more specific to operating system security in Chapter 11.
Packet sniffers
A network or protocol analyzer, also known as a packet sniffer, or just plain sniffer,1 is a tool that can intercept traffic on a network, commonly referred to as sniffing. Sniffing basically amounts to listening for any traffic that the network interface of our computer or device can see, whether it was intended to be received by us or not.
Alert!
One of the key elements in employing a sniffer is to place it on the network in the proper position to allow us to actually see the traffic we would like to sniff. In most modern networks, the traffic is segmented in such a fashion that we will likely not be able to see much traffic at all, other than what we are generating from our own machine. In order to be able to sniff properly, we will likely need to gain access to one of the higher-level network switches and may need to use specialized equipment or configurations to allow us access to our target traffic.
Tcpdump is a classic sniffing tool, and it has been around since the late 1980s. Tcpdump is a command-line tool that allows us to monitor the activities of the network to which we are attached and has only a few other key features, such as filtering of traffic. Tcpdump runs only on UNIX-like operating systems, but a version has been ported to Windows, called WinDump.
Wireshark, previously known as Ethereal, is a fully featured sniffer that is capable of intercepting traffic from a wide variety of wired and wireless sources. It has a graphical interface, as shown in Figure 10.3; it includes a large number of filtering, sorting, and analysis tools; and it is one of the more popular sniffers on the market today. Wireshark can also import data from other applications like Tcpdump. Wireshark is a great tool for troubleshooting traffic on the network so is used my many network operations teams as well as security teams.
Kismet, which we discussed in the “Wireless” section, is also a specialized sniffer. Although many of the other sniffers are network media agnostic, for the most part, Kismet will only sniff from wireless networks. Owing to this very specific focus, it can provide us with a much more specific set of tools.
We may also see packet sniffers in hardware form, such as the OptiView Portable Network Analyzer from Fluke Networks. Although we can definitely benefit from well-equipped portable analyzers such as this, they often tend to be very expensive and well beyond the budget of the average network or security professional.
Honeypots
Honeypots are a somewhat controversial tool in the arsenal of those we can use to improve our network security. A honeypot can detect, monitor, and sometimes tamper with the activities of an attacker. Honeypots are configured to deliberately display vulnerabilities or materials that would make the system attractive to an attacker. This might be an intentionally vulnerable service, an outdated and unpatched operating system, a network share named “top secret UFO documents,” or other similar items that might serve as bait for an attacker.
One of the interesting things about honeypots is that the vulnerabilities or data that is left out to bait the attacker is entirely false. In reality, honeypots are configured to display these items so that we can catch the attackers and monitor what they are doing on the system without their knowledge. This might be done in an effort to provide an early warning system for a corporation, as a method of researching what methods attackers are using, or as an intentional target to monitor the activities of malware in the wild.
We can also expand honeypots into larger structures by setting up several such systems in a network, often referred to as a honeynet. Honeynets can allow us to set up multiple honeypots with varying configurations and vulnerabilities, generally with some sort of centralized instrumentation for monitoring all the honeypots on the network. Honeynets can be particularly useful for large-scale monitoring of malware activity, as we can emulate a variety of different operating systems and vulnerabilities for our target systems to display. These systems can be used internally to a network to detect insider threats as well as the threats that got inside.
Additional resources
An excellent resource for more information on honeypots and honeynets is the Honeynet Project at www.honeynet.org/. The Honeynet Project provides access to a variety of resources, including software, the results of research, and numerous papers on the subject.
Firewall tools
In our kit of network tools, we may also find it useful to include those that can map the topology of and help locate vulnerabilities in our firewalls. Hping3 is a well-known and useful tool for such efforts. It is able to construct specially crafted Internet Control Message Protocol (ICMP) packets in such a way as to evade some of the normal measures that are put in place to prevent us from seeing the devices that are behind a firewall. We can also script the activities of Hping3 in order to test the responses of firewalls and IDSes, so that we can get an idea of the rules on which they are operating.
We can also use a variety of the other tools we have discussed in this section to test the security of our firewalls. We can use port and vulnerability scanners to look at them from the outside in order to find any ports that are unexpectedly open, or any services running on our open ports that are vulnerable to known attacks. We can also use sniffers to examine the traffic that is entering and leaving firewalls, presuming that we can get such a tool in place in a network location that will enable us to see the traffic.
Network security in the real world
We can see the use of network security nearly everywhere on the Internet today. In businesses and in government organizations, we can see concerted efforts at designing secure networks, including the implementation of firewalls and IDSes. Depending on the industry we are referring to, our business may depend entirely on the success of such measures in keeping us secure. If we look at network-focused companies such as eBay and Amazon, the vast majority of their business is conducted directly over the Internet. If they did not have rigid security measures in place, and they did not continuously evaluate them in order to find weaknesses, their businesses would quickly fail due to lack of trust.
On the back end of such organizations, we can also find a variety of security measures that are put in place to keep the traffic and activities of their employees and users secure. Business use of VPN connections is very common, as this allows employees who are working from home or on the road to use internal network resources. We can also see the use of secure protocols when those that are outside the corporate firewalls are communicating with externally exposed servers in order to exchange e-mail, send files, communicate over instant messaging, and so forth.
As we mentioned, such companies also need to constantly evaluate their own security measures. We can use a number of tools to do so from a network perspective, including the few we discussed in this chapter, and many more. It is important to understand that such tools often do not fall cleanly across the lines of network security, operating system security, and application security, but often encompass one or more, if not all, of these aspects. This reflects the need to ensure security in all of these ways, and that these categories overlap heavily.
Summary
When we protect our networks, we do so from a variety of different angles. We use secure network design to ensure that we have our networks segmented properly, that we have the proper choke points in order to allow monitoring and control of traffic, and that we are redundant where redundancy is needed. We also implement security devices such as firewalls and IDSes in order to protect us both inside and outside our networks.
In addition to protecting the networks themselves, we also need to look to protecting our network traffic. Owing to the nature of our networks, whether wired or wireless, it is often possible to eavesdrop on the traffic that travels over them. In order to protect our traffic, we can use VPNs to secure our connections when we use untrusted networks, we can use security measures specific to wireless networks when we need to use them, and we can make use of secure protocols as a general security measure.
In our efforts to provide for our network security, we may use a variety of security tools. When dealing with wireless networks, we can use tools that are specifically suited to tasks, such as Kismet or NetStumbler. We can also listen in on network traffic with tools such as Wireshark or Tcpdump, scan for devices on our networks using tools such as Nmap, and test our firewalls using hping3 and other similar utilities. We can also place devices called honeypots on our networks specifically to attract the attention of attackers in order to study them and their tools and to alert us to their presence.
Exercises
1. For what might we use the tool Kismet?
2. Explain the concept of segmentation.
3. What risks might be present with a permissive BYOD policy in an enterprise?
4. What are the three main types of wireless encryption?
5. What tool might we use to scan for devices on a network?
6. Why would we use a honeypot?
7. Explain the difference between signature and anomaly detection in IDSes.
8. What would we use if we needed to send sensitive data over an untrusted network?
9. What would we use a DMZ to protect?
10. What is the difference between a stateful firewall and a deep packet inspection firewall?