Identification and Authentication
In this chapter, we cover the security principles of identification and authentication. We discuss identification as a process by which we assert the identity of a particular party, whether this is true or not. We talk about the use of authentication as the means of validating whether the claim of identity is true. We also cover multifactor authentication and the use of biometrics and hardware tokens to enhance surety in the authentication process.
Keywords
Authentication; biometrics; hardware tokens; identification; multifactor authentication; mutual authentication; passwords; security tokens
Information in This Chapter
Introduction
When we are developing security measures, whether on the scale of a specific mechanism or an entire infrastructure, identification and authentication are likely to be key concepts. In short, identification is the claim of what someone or something is, and authentication establishes whether this claim is true. We can see such processes taking place on a daily basis in a wide variety of ways.
One very common example of an identification and authentication transaction can be found in the use of payment cards that require a personal identification number (PIN). When we swipe the magnetic strip on the card, we are asserting that we are the person indicated on the card. At this point, we have given the identification but nothing more. When we are prompted to enter the PIN associated with the card, we are completing the authentication portion of the transaction.
Some of the identification and authentication methods that we use in daily life are particularly fragile and depend largely on the honesty and diligence of those involved in the transaction. Many such exchanges that involve the showing of identification cards, such as the purchase of items restricted to those above a certain age, are based on the theory that the identification card being displayed is genuine and accurate. We also depend on the person or system performing the authentication being competent and capable of not only performing the act of authentication but also being able to accurately detect false or fraudulent activity.
We can use a number of methods for identification and authentication, from the simple use of usernames and passwords, to purpose-built hardware tokens that serve to establish our identity in multiple ways. We will discuss several of these methods and how they are used throughout the chapter.
Identification
Identification, as we mentioned in the preceding section, is simply an assertion of who we are. This may include who we claim to be as a person, who a computer system claims to be over the network, who the originating party of an e-mail claims to be, what authority we claim to have, or similar transactions. It is important to note that the process of identification does not extend beyond this claim and does not involve any sort of verification or validation of the identity that we claim. That part of the process is referred to as authentication and is a separate transaction.
Who we claim to be
Who we claim to be is a tenuous concept, at best. We can identify ourselves by our full names, shortened versions of our names, images of ourselves, nicknames, account numbers, usernames, ID cards, fingerprints, DNA samples, and an enormous variety of other methods. Unfortunately, with a few exceptions, such methods of identification are not unique, and even some of the supposedly unique methods of identification, such as the fingerprint, can be duplicated or spoofed in many cases.
Who we claim to be can, in many cases, be an item of information that is subject to change. For instance, our names can change, as in the case of women who change their last name upon getting married, people who legally change their name to an entirely different name, or even people who simply elect to use a different name. In addition, we can generally change logical forms of identification very easily, as in the case of account numbers, usernames, and the like. Even physical identifiers, such as height, weight, skin color, and eye color, can be changed. One of the most crucial factors to realize when we are working with identification is that an invalidated claim of identity is not reliable information on its own.
Identity verification
Identity verification is a step beyond identification, but it is still a step short of authentication, which we will discuss in the next section. When we are asked to show a driver’s license, Social Security card, birth certificate, or other similar form of identification, this is generally for the purpose of identity verification, not authentication. This is the rough equivalent of someone claiming the identity “John Smith,” us asking if the person is indeed John Smith, and being satisfied with an answer of “Sure I am” from the person (plus a little paperwork). As an identity verification, this is very superficial, at best.
We can take the example a bit further and validate the form of identification—say, a passport—against a database holding an additional copy of the information that it contains, and matching the photograph and physical specifications with the person standing in front of us. This may get us a bit closer, but we are still not at the level of surety we gain from authentication.
Identity verification is used not only in our personal interactions but also in computer systems. In many cases, such as when we send an e-mail, the identity we provide is taken to be true, without any additional steps taken to authenticate us. Such gaps in security contribute to the enormous amount of spam traffic that we see, estimated to have accounted for 70.7% of all e-mails sent in Q2 of 2013 [1].
Falsifying identification
As we have discussed, methods of identification are subject to change. As such, they are also subject to falsification. While many drivers’ licenses now have holograms or barcodes that make them harder to counterfeit, there is an underground industry that allows underage kids in America to buy very valid looking licenses from overseas companies. This constant struggle between security measures and criminals is also going on in the virtual world. On a slightly more sinister note, such falsified means of identification are also used by criminals and terrorists for a variety of tasks of a nefarious nature. Certain primary means of identification, such as birth certificates, also provide a way to gain additional forms of identification, such as Social Security cards or driver’s licenses, thus strengthening the false identity.
Identity theft, based on falsified information, is a major concern today, costing US consumers an estimated $20.9 billion in 2012 [2]. This type of attack is unfortunately common and easy to execute. Given a minimal amount of information—usually a name, address, and Social Security number are sufficient—it is possible to impersonate someone to a sufficient degree to be able to act as that person in many cases. Victims of identity theft may find that lines of credit, credit cards, vehicle loans, home mortgages, and other transactions have taken place using their stolen identity.
Such crimes are made easier due to the lack of authentication requirements for many of the activities in which we engage. In most cases, the only check that takes place is identity verification, as we discussed in the preceding section. This process is a small obstacle, at best, and can easily be circumvented using falsified forms of identification. To rectify this situation, we need to complete the process of identifying and authenticating the people involved in these transactions, in order to at least more conclusively prove that we are actually interacting with the people we believe we are. In the case of individuals, this is not an unsolvable technical problem by any extent, but it is more of a people problem.
When we look at similar issues for computer systems and environments, we can see many of the same difficulties. It is entirely possible to send an e-mail from an address that is different from the actual sending address, and this tactic is used by spammers and social-engineering-based attacks on a regular basis. We can see the same problems in many other systems and protocols that are in daily use and are part of the functionality of the Internet. We will discuss such issues at greater length in Chapter 10.
Authentication
Authentication is, in an information security sense, the set of methods we use to establish a claim of identity as being true. It is important to note that authentication only establishes whether the claim of identity that has been made is correct. Authentication does not infer or imply anything about what the party being authenticated is allowed to do; this is a separate task known as authorization. We will discuss authorization at greater length in Chapter 3, but the important thing to understand for now is that authentication needs to take place first.
Factors
In terms of authentication, there are several methods we can use, with each category referred to as a factor. Within each factor, there are a number of possible methods we can use. When we are attempting to authenticate a claim of identity, the more factors we use, the more positive our results will be. The different factors are something you know (password), something you are (Iris scan), something you have (swipe card), something you do (gait (walking) recognition), and the place you are (at a specific terminal).
Something you know is a very common authentication factor. This can include passwords, PINs, passphrases, or most any item of information that a person can remember. We can see a very common implementation of this in the passwords we use to log in to our accounts on computers. This is somewhat of a weak factor because if the information the factor depends on is exposed, this can nullify the uniqueness of our authentication method.
Something you are is a factor based on the relatively unique physical attributes of an individual, often referred to as biometrics. This factor can be based on simple attributes, such as height, weight, hair color, or eye color, but these do not tend to be unique enough to make very secure identifiers. More commonly used are more complex identifiers such as fingerprints, iris or retina patterns, or facial characteristics. This factor is a bit stronger, as forging or stealing a copy of a physical identifier is a somewhat more difficult, although not impossible, task. There is some question as to whether biometrics truly is an authentication factor or whether it really only constitutes verification. We will discuss this again later in the chapter when we cover biometrics in greater depth.
Something you have is a factor generally based on the physical possession of an item or a device, although this factor can extend into some logical concepts as well. We can see such factors in general use in the form of ATM cards, state or federally issued identity cards, or software-based security tokens, as shown in Figure 2.1. Some institutions, such as banks, have begun to use access to logical devices such as cell phones or e-mail accounts as methods of authentication as well. This factor can vary in strength depending on the implementation. In the case of a security token, we would actually need to steal a specific device in order to falsify the authentication method. In the case of access to an e-mail address being used as this type of factor, we have a measure of considerably less strength.
Something you do, sometimes considered a variation of something you are, is a factor based on the actions or behaviors of an individual. Such factors may include analysis of the individual’s gait, measurement of multiple factors in his or her handwriting, the time delay between keystrokes as he or she types a passphrase, or similar factors. These factors present a very strong method of authentication and are very difficult to falsify or create false positive. They do, however, have the potential to create false negative and incorrectly reject legitimate users at a higher rate than some of the other factors, resulting in denials for some users that should actually be authenticated.
Where you are is a geographically based authentication factor. This factor operates differently than the other factors, as its method of authentication depends on the person being authenticated as being physically present at a particular location or locations. The most common implementation of this is for servers to only be accessible from a terminal in the server room. This factor, although potentially of less utility than some of the other factors, is very difficult to counter without entirely subverting the system performing the authentication or gaining physical access.
Multifactor authentication
Multifactor authentication uses one or more of the factors we discussed in the preceding section. This practice is also referred to, in some cases, as two-factor authentication when we are using only two factors, but multifactor authentication encompasses this term as well.
We can see a common example of multifactor authentication in using an ATM. In this case, we have something we know, our PIN, and something we have, our ATM card. Our ATM card does double duty as both a factor for authentication and a form of identification. We can see a similar example in writing checks that draw on a bank account—in this case, something we have, the checks themselves, and something we do, applying our signature to them. Here, the two factors involved in writing a check are rather weak, so we sometimes see a third factor, a fingerprint, applied to them. We could also argue that the signature and fingerprint are, in this case, not actually authentication, but rather verification, a much less robust process that we discussed when talking about identity earlier in the chapter.
Depending on the particular factors selected, we can assemble stronger or weaker multifactor authentication schemes in a given situation. In some cases, although certain methods may be more difficult to defeat, they are not practical to implement. For example, DNA makes for a very strong method of authentication but is not practical for regular use. As we discussed in Chapter 1, when discussing security, we need to be careful to build security that is reasonably proportionate to what we are protecting. We could install iris scanners on every credit card terminal instead of having the customer sign his credit card receipt and certainly enhance our security, but this would be expensive, slow down transactions causing delays, and could upset our customers who don’t trust the technology.
Mutual authentication
Mutual authentication refers to an authentication mechanism in which both parties authenticate each other. In the standard authentication process, which is one-way authentication only, the client authenticates to the server to prove that it is the party that should be accessing the resources the server provides. In mutual authentication, not only does the client authenticate to the server, but the server authenticates to the client as well. Mutual authentication is often implemented through the use of digital certificates, which we will discuss at greater length in Chapter 5. Briefly, both the client and the server would have a certificate to authenticate the other.
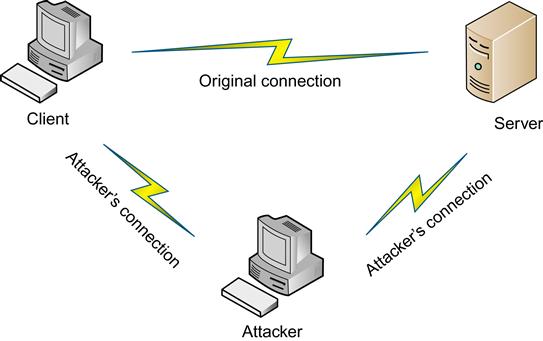
In cases where we do not perform mutual authentication, we leave ourselves open to impersonation attacks, often referred to as man-in-the-middle attacks. In the man-in-the-middle attack, the attacker inserts himself between the client and the server and impersonates the server to the client, and the client to the server, as shown in Figure 2.2. Using our ATM example, this would be like placing a skimmer over the normal ATM that intercepts the information. This is done by circumventing the normal pattern of traffic, then intercepting and forwarding the traffic that would normally flow directly between the client and the server. This is typically possible because the attacker only has to subvert or falsify authentication from the client to the server. If we implement mutual authentication, this becomes a considerably more difficult attack to carry out for the attacking party.
Mutual authentication can also be used in combination with multifactor authentication, with the latter generally taking place on the client side only. Multifactor authentication from the server back to the client would be not only technically challenging but also impractical in most environments. Conceivably, we could implement mutual multifactor authentication in an extremely high security environment, but this would result in a very large loss in productivity.
Passwords
Passwords are familiar to the vast majority of us who use computers regularly as they are still the most common form of validation. In combination with a username, a password will generally allow us access to a computer system, an application, a phone, or similar devices. Passwords, although only a single factor of authentication, can, when constructed and implemented properly, represent a relatively high level of security.
When we describe a password as being strong, we do not provide an immediately accurate image of what we are discussing. A better descriptive term might be complex in order to communicate the important concepts inherent to building a password. If we construct a password that is all lowercase letters and is eight characters long, we can use a password-cracking utility, which we will discuss further in Chapter 12, to crack the password in a minute or two, given a reasonably strong computer on which to run the cracking tool. If we use the same eight-character password but use both upper- and lowercase letters, it will take the password cracker around 6 days to break the password. If we add numbers into the mix, it will take a little more than 25 days to break our password. If we use multiple computers, these times can be reduced. If we use the recommended password construction method for creating strong passwords, we would create a password that was constructed of uppercase letters, lowercase letters, numbers, and symbols, such as punctuation marks. So, although we would end up with a password that is potentially more difficult to remember, such as $sU&qw!3, we would have a password that would take more than 2 years to crack with an average workstation [3].
More advanced
The type of password cracking we are discussing here is called brute force cracking. This involves trying every possible combination of characters that the password could be composed of, in sequence, until we try them all. Given a powerful system on which to run the cracker and a poorly constructed password, this can be a very effective means of recovering passwords. We will discuss this at greater length in Chapter 12. This type of attack can be mitigated by limiting the number of attempts before the user is locked out. The problem with locking users out lies in impact to productivity and cost of the administrators time to subsequently unlock accounts.
In addition to constructing strong passwords, we also need to be careful to practice good password hygiene. One problem with strong passwords is that they can be difficult to remember. This might encourage us to take steps to remember our passwords, such as writing them down and posting them in a handy place, perhaps under our keyboard or on our monitor. This, of course, completely defeats the purpose of having a password if someone comes snooping around our desk.
A number of applications exist, generally under the label of “password managers,” also known as “password safes/wallets” that will help us manage all the logins and passwords we have for different accounts, some as locally installed software and some as Web or mobile device applications. There are a number of arguments for and against such tools, but when they are used carefully, they can be of assistance in maintaining good password hygiene.
Another password security issue is manual synchronization of passwords—in short, using the same password everywhere. If we use the same password for our e-mail, for our log-in at work, for our online knitting discussion forum, and everywhere else, we are placing the security of all our accounts with each system owner where we use the same password. If any one of them is compromised and its password exposed, we have a serious problem. All an attacker needs to do is look up our account name, luv2knit, on the Internet to find some of the places where the same name is used and start trying our default password. By the time the attacker gets into our e-mail account, the game is over.
Biometrics
When we look at biometrics, we should consider what exactly it is when we use it as an authentication factor. As we discussed in the “Identification” section at the beginning of the chapter, there is a difference between authentication and verification. When we complete an authentication transaction with a biometric identifier, we are essentially asking the user to provide evidence that he or she is who he or she claims to be; this is, by definition, verification, and not authentication. Although some biometric identifiers may be more difficult to falsify than others, this is only due to limitations in today’s technology. At some point in the future, we will need to develop more robust biometric characteristics to measure or stop using biometrics as an authentication mechanism.
Additional resources
Biometrics-equipped devices and readers are becoming common enough that we have begun to see very inexpensive (some less than $20) versions of them on the market. It pays to research such devices carefully before we depend on them for security, as some of the cheaper versions are very easily bypassed.
This being said, we can use biometric systems in two different manners. We can use them to verify the claim of identity that someone has put forth, as we discussed earlier, or we can reverse the process and use biometrics as a method of identification. This process is commonly used by law enforcement agencies to identify the owner of fingerprints that have been left on various objects and can be a very time-consuming effort, considering the sheer size of the fingerprint libraries held by such organizations. We also see similar use in the comparison of DNA samples taken from suspects in crimes compared to physical evidence recovered from the crime scene.
To use a biometric system in either manner, we need to put the user through the enrollment process. Enrollment involves recording the chosen biometric characteristic from the user—for instance, making a copy of a fingerprint—and recording the characteristic in the system. Processing of the characteristic may also include noting certain parts of the image, depending on the characteristic in question, to use for later matching in the system.
One issue with biometrics is the lack of laws protecting user’s data today. An iris scan data file can be compromised and there is no requirement that they be notified. Additionally some biometrics can relive personal information. For example an iris scan can identify changes that indicate that a woman is pregnant.
Characteristics
Biometric factors are defined by seven characteristics: universality, uniqueness, permanence, collectability, performance, acceptability, and circumvention [4].
Universality stipulates that we should be able to find our chosen biometric characteristic in the majority of people we expect to enroll in the system. For instance, although we might be able to use a scar as an identifier, we cannot guarantee that everyone will have a scar. Even if we choose a very common characteristic, such as a fingerprint, we should take into account that some people may not have an index finger on their right hand and be prepared to compensate for this.
Uniqueness is a measure of how unique a particular characteristic is among individuals. For example, if we choose to use height or weight as a biometric identifier, we would stand a very good chance of finding several people in any given group who are of the same height or weight. We can select characteristics with a higher degree of uniqueness, such as DNA, or iris patterns, but there is always a possibility of duplication, whether intentional or otherwise.
Permanence tests show how well a particular characteristic resists change over time and with advancing age. If we choose a factor that can easily vary, such as height, weight, or hand geometry, we will eventually find ourselves in the position of not being able to authenticate a legitimate user. We can instead use factors such as fingerprints that, although they can be altered, are unlikely to be altered without deliberate action.
Collectability measures how easy it is to acquire a characteristic with which we can later authenticate a user. Most commonly used biometrics, such as fingerprints, are relatively easy to acquire, and this is one reason they are in common use. If we choose a characteristic that is more difficult to acquire, such as a footprint, the user will need to remove his shoe and sock in order to enroll (and to authenticate again later), which is considerably more troublesome than taking a fingerprint. These can change over time. Today there are efforts to be able to collect iris scans from a distance so the users can be identified while they walk toward the device and they never even have to stop.
Performance is a set of metrics that judge how well a given system functions. Such factors include speed, accuracy, and error rate. We will discuss the performance of biometric systems at greater length later in this section.
Acceptability is a measure of how acceptable the particular characteristic is to the users of the system. In general, systems that are slow, difficult to use, or awkward to use are less likely to be acceptable to the user [5]. Systems that require users to remove their clothes, touch devices that have been repeatedly used by others, or provide tissue or bodily fluids will likely not enjoy a high degree of acceptability.
Circumvention describes the ease with which a system can be tricked by a falsified biometric identifier. The classic example of a circumvention attack against the fingerprint as a biometric identifier is found in the “gummy finger.” In this type of attack, a fingerprint is lifted from a surface, potentially in a covert fashion, and is used to create a mold with which the attacker can cast a positive image of the fingerprint in gelatin. Some of the newer generations of biometric systems have features specifically designed to defeat such attacks by measuring skin temperature, pulse, pupillary response, and a number of other items.
Measuring performance
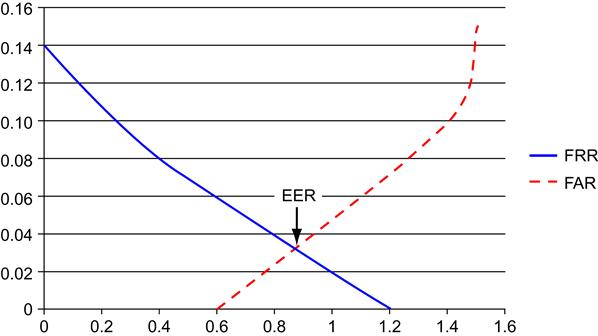
We can look at many factors when measuring the performance of a biometric system, but a few primary metrics stand out as being particularly important for gauging how well the system is working. False acceptance rate (FAR) and false rejection rate (FRR) are two of these [6]. FAR occurs when we accept a user whom we should actually have rejected. This type of issue is also referred to as a false positive. FRR is the problem of rejecting a legitimate user when we should have accepted him. This type of issue is commonly known outside the world of biometrics as a false negative.
Either of these situations is undesirable in excess. What we try to achieve with such systems is a balance between the two error types, referred to as an equal error rate (EER) [6]. If we plot out both the FAR and FRR on a graph, as we have done in Figure 2.3, the EER is the point where the two lines intersect. EER is sometimes used as a measure of the accuracy of biometric systems.
Issues
There are several issues common to biometric systems. As we mentioned when discussing circumvention, some biometric identifiers can be easily forged. Given a falsified identifier, we face a problem; we cannot revoke such a characteristic.
Although we can remove the particular identifier from the system and no longer allow it to be used to authenticate a user, in some cases, this is not practical. If we look at fingerprints as an example, we find such a commonly used identifier that someone falsely using our fingerprints could cause us great problems. Although we may currently be able to move to stronger biometrics that, at present, are not easily copied, such as an iris pattern, such efforts will not remain beyond the grasp of attackers forever.
We also face possible issues of privacy in the use of biometrics, both as owners of such systems and as users of them. When we are enrolled in a biometric system, we are essentially giving away a copy of whatever identifier is chosen, whether it is a fingerprint, iris pattern, DNA sample, or otherwise. Once such an item has been entered into a computer system, we have little, if any, control over what is done with the material. We can hope that once we are no longer associated with the institution in question, such materials would be destroyed, but we really have no way of guaranteeing this has actually taken place. Particularly in the case of DNA sampling, the repercussions of surrendering genetic material could be an issue impacting us for the rest of our lives.
Hardware tokens
A standard hardware token is a small device, typically in the general form factor of a credit card or keychain fob. The simplest hardware tokens look identical to a USB flash drive and contain a small amount of storage holding a certificate or unique identifier, and are often called dongles. More complex hardware tokens incorporate LCD displays, as shown in Figure 2.4, keypads for entering passwords, biometric readers, wireless devices, and additional features to enhance security.
Many hardware tokens contain an internal clock that, in combination with the device’s unique identifier, an input PIN or password, and potentially other factors, is used to generate a code, usually output to a display on the token. This code changes on a regular basis, often every 30 s. The infrastructure used to keep track of such tokens can predict, for a given device, what the proper output will be at any given time and can use this to authenticate the user.
Alert!
The simplest variety of hardware tokens represents only the something you have factor and is thus susceptible to theft and potential use by a knowledgeable criminal. Although these devices do represent an increased level of security for the user’s accounts, and are generally not useful without the account credentials with which they are associated, we do need to remember to safeguard them.
Hardware tokens represent the something you have authentication factor, sometimes implementing something you know or something you are as well. In the case of simple hardware tokens that only provide the something you have factor, the security provided by the device is only as strong as our ability to prevent it from being stolen, as it could easily be used by an attacker. In the case of more complex tokens that include the capability to enter a PIN, a password or read a fingerprint, the security of the device is enhanced considerably. In order for an attacker to utilize a stolen multifactor device, the attacker not only would need the hardware token itself, but also would need to either subvert the infrastructure that was synchronized with the information output from the device or extract the something you know and/or something you are factor(s) from the legitimate owner of the device.
Identification and authentication in the real world
Identification and authentication can be seen at work all over the world on a daily basis. One of the most common examples that we can point out is identity cards, commonly a driver’s license in the United States. Such cards are routinely used to prove our identity when making purchases, dealing with government officials and offices, registering for school, and performing a variety of other tasks. In many cases, identification cards are used as a method of verifying our identity while doing these things. Although this is a weak method of verification, it is a commonly used one. There is a trend for these cards to have a bar code or chip with additional information, making them harder to fake.
We can see authentication at work when we are carrying out a variety of activities as well. When we use a username and password to log on to a computer at work, or a web site, we are using the something you know factor. When we enter a PIN and withdraw money from an ATM, we are using the something you know and something you have factors, and we are using multifactor authentication. Many people will not get beyond the use of these two factors in their daily lives.
For those of us who have access to more secure facilities, such as data centers, financial institutions, or military installations, we may see more involved methods of authentication. In some such environments, we will see the use of biometrics, the something you are factor. Many such facilities have moved to the use of iris scanners, now an unobtrusive piece of equipment hanging on the wall near the area to be accessed and only requiring a glance at the lens of the device to proceed. This type of device not only is easy to use but also tends to be more acceptable to users, as we do not need to actually touch it in order for it to work.
We can also see the use of hardware tokens increasing, even for the general public. We can now buy an inexpensive token from VeriSign1 that will provide an extra layer when we log in to web sites run by companies such as eBay, PayPal, GEICO, T-Mobile, RadioShack, and hundreds of others. Owing to the large amount of online fraud and identity theft that we see now, any measures that we can use on both personal and organizational levels, such as good password hygiene, strong passwords, and the use of hardware tokens, will help to put us on a stronger security footing all the way around.
The type of security factors we chose to implement are based on the amount of risk we are willing to accept. For our personal e-mail or Facebook page we may be fine with a simple password. For critical financial or proprietary corporate information, we may need to invest in multifactor authentication.
Summary
Identification is an assertion of the identity of a particular party. This can be a person, process, system, or other entity. Identification is only a claim of identity and does not imply that this claim is correct or any privileges that might be associated with the identity, if it is proven true.
Authentication is the process we use to validate whether the claim of identity is correct. It is important to note that authentication and verification are not the same things and that verification is a much weaker test from a security perspective.
When we perform authentication, we can use a number of factors. The main factors are something you know, something you are, something you have, something you do, and where you are. When we use an authentication mechanism that includes more than one factor, this is known as multifactor authentication. Using multiple factors gives us a much stronger authentication mechanism than we might otherwise have.
Exercises
1. What is the difference between verification and authentication of an identity?
2. How do we measure the rate at which we fail to authenticate legitimate users in a biometric system?
3. What do we call the process in which the client authenticates to the server and the server authenticates to the client?
4. A key would be described as which type of authentication factor?
5. What biometric factor describes how well a characteristic resists change over time?
6. If we are using an identity card as the basis for our authentication scheme, what steps might we add to the process in order to allow us to move to multifactor authentication?
7. If we are using an 8-character password that contains only lowercase characters, would increasing the length to 10 characters represent any significant increase in strength? Why?
8. Name three reasons why an identity card alone might not make an ideal method of authentication.
9. What factors might we use when implementing a multifactor authentication scheme for users who are logging on to workstations that are in a secure environment and are used by more than one person?
10. If we are developing a multifactor authentication system for an environment where we might find larger-than-average numbers of disabled or injured users, such as a hospital, which authentication factors might we want to use or avoid? Why?