Attestation for Platform Identity Mechanisms
The basic structure of the endorsement, platform, and identity credentials is introduced in this section. The conformance credential has no structure as such, because it amounts to merely a reference to a successful conformance test. Only its background is discussed here.
The credentials contain sufficient information to express the social trust in the platform identity mechanisms. As mentioned previously, the endorsement, platform, and identity credentials are instantiated as X.509 digital certificates. These are designed for unambiguous interpretation, and their structure is more complex than the basic credentials. For clarity, therefore, the credentials (rather than the certificates) are described in this section. Nevertheless, it is worth noting that TCPA has registered as an “international body” in the ISO registration hierarchy. This leads to shorter OIDs (object identifiers) in X.509 certificates and gives TCPA autonomy in the management of its own object identifiers in those certificates. TCPA's full object identifier is 2-23-133 (joint-ISO-ITU=2, international-organizations=23, TCPA=133).
For maximum flexibility, TCPA uses a different term to describe each entity, or organization, that vouches for each different type of credential. In some circumstances, these will actually be different entities. In other circumstances, they could be the same entity. For example, the TPM manufacturer will probably act as the Trusted Platform Module Entity (TPME) and vouch for the TPM, but the TPME could be a platform original equipment manufacturer (OEM) or even someone in a closed user group in which the TP will be used. The platform OEM will probably act as the Platform Entity (PE) that vouches for the platform that hosts a particular TPM, but the PE could be a value-added reseller (VAR) or someone in a closed user group. A conformance laboratory will probably act as the Conformance Entity (CE) that vouches for the design of the TPM and the design of the host platform, but it could be the platform OEM in some circumstances. A public Certification Authority is probably the Privacy-CA that vouches for a platform identity, but the Privacy-CA could well be a corporate IT department or even simply the owner of an individual TP. In all cases, the important thing is that the attestation is acceptable to entities that receive data from the TP. If this is not the case, a recipient of data cannot trust the basic behavior of the alleged TP. A discussion of how these credentials may be used to provide evidence of trustworthiness of a platform is provided in Chapter 2.
Endorsement Credential
As briefly discussed in Chapter 2, the Trusted Platform Module Entity (TPME) attests that a TPM is a genuine TPM by installing an endorsement key pair in a TPM and embedding the public key of the pair into an endorsement credential. This credential binds the public endorsement key to information about the characteristics of the TPM and provides the “social trust” in the TPM. Before installing an endorsement key in a TPM, a TPME must be certain that a TPM correctly implements the TCPA capabilities. In many cases, this means that the TPM must be kept in conditions of good physical security until installation of the endorsement key, to minimize the chance of installing an endorsement key in a bogus TPM. After installation, maintaining such a degree of protection is not necessary, because the TPM's own mechanisms should be sufficient to protect it from attack.
The structure of an endorsement credential is illustrated in Figure 5-1. The credential contains the following items:
The value of the actual public endorsement key
A general description of the type of TPM and its security properties
A reference to the TPME
Figure 5-1. Endorsement credential

The credential is signed by the TPME. Most of the fields are self-explanatory. The description of the TPM is not permitted to identify an individual TPM (to protect privacy) and contains just generic information such as the TPM model number. The contents of the “security properties” field are manufacturer-specific, but they probably contain information about the level of tamper-protection, etc., provided by the TPM. “Security properties” is often redundant, because such information is implicit in the TPM model number. The field is present to accommodate those trusted entities that will be presented with the endorsement credential (see the section “TPM Identity Creation” later in this chapter). Such entities will require information about the protection provided by a TPM, but they may be unable to access a network to obtain that information.
Platform Credential
The manufacturer of a platform must provide analogous proof that a platform is a genuine TP. A so-called (PE) (for example, the manufacturer of the platform or the manufacturer's agent) does this by attesting via a certificate called a platform credential that a particular TPM has been correctly incorporated into a design that conforms to the TCPA specification.
The evidence required to produce this credential includes the following:
The endorsement credential, which provides proof that the TPM in the platform is a genuine TPM
The conformance credential, which provides proof that the design of the platform meets the TCPA requirements
Other information about the particular platform
A platform has exactly one platform credential. The structure of a platform credential is shown in Figure 5-2. The credential contains these items:
A statement that it is a platform credential
A reference to the actual endorsement key in the actual TPM in the platform (which will be in the form of an identifier of the endorsement certificate issued by the TPME)
A reference to the conformance credential that describes the TPM and the platform
A general description of the type of platform and its security properties
A reference to the PE
Figure 5-2. Platform credential

The credential is signed by the PE. The description of the platform is not permitted to identify an individual platform (to protect privacy) and contains only generic information such as the platform model type. The contents of the “security properties” field are manufacturer-specific.
Identity Credential
As discussed in Chapter 2 and earlier in this chapter, a Privacy-CA (chosen by the owner of the platform) uses the endorsement credential, the platform credential, and the conformance credential to verify that a platform is a TP with a genuine TPM. The Privacy-CA attests to a TPM's identity by creating an identity credential. The structure of an identity credential is shown in Figure 5-3. The credential contains these items:
A statement that it is an identity credential
The name allocated by the TPM-owner to this identity
The public key belonging to this identity
A general description of the type of TPM and its security properties (copied from the endorsement certificate)
A general description of the type of platform and its security properties (copied from the platform certificate)
A reference to the Privacy-CA (in the form of a distinguished name and unique identifier of that Privacy-CA)
Figure 5-3. Identity credential
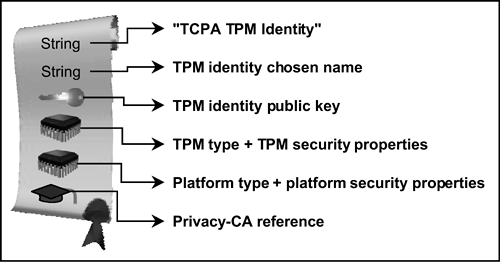
The credential is signed by the Privacy-CA. Again, most of the fields are self-explanatory. The credential permits a recipient to believe that an entity with knowledge of a particular private key is actually a TP that conforms to the TCPA specification. The identity is, however, pseudonymous.
Conformance Credential
A conformance credential is essentially merely a reference to a document that vouches that a particular design of TPM and platform meets the TCPA specification. It may simply be a statement from a manufacturer. More probably, it will include the number of a certificate from a test laboratory, stating that this type of equipment meets the requirements of the TCPA's “Protection Profiles.” This type of conformance certification simplifies the international distribution and acceptance of information security equipment in general, and TPs in particular.
Protection Profiles (PPs) are a method of describing the security properties of equipment. The method is described in an international standard called the “Common Criteria” [Common Criteria]. TCPA has produced two PPs. One describes the TPM; the other describes the attachment of the TPM to the platform and the properties of the platform that are necessary to properly support the TPM. Manufacturers can write documents called “Security Targets” (STs) describing particular designs of equipment, which demonstrate that the equipment meets the security requirements described in particular Protection Profiles. These documents are scrutinized by accredited conformance laboratories, which issue a certificate if the ST satisfies the PP. In any country that has signed up to follow the Common Criteria, a conformance certificate issued in one country is valid in another country. So possession of a Common Criteria conformance credential is an internationally recognized means of proving the level of security provided by equipment.
