Summary of Trusted Platform Concepts
Before assessing the nature and value of Trusted Platforms in more detail, we summarize the need for Trusted Platforms, how this relates to the Trusted Computing Alliance and its specifications, and the basic concepts behind Trusted Platform technology.
Why Are Trusted Platforms Being Developed?
Computer platforms are ubiquitous; they are central to the growing reliance on electronic business and commerce, and the need for information protection is increasing, particularly on client platforms. Although businesses have deployed Secure Operating Systems on servers (for example, [HP 2001]) and have physically protected individual server platforms, no overall corresponding improvement in client platforms has occurred because of the ad hoc way in which client platforms develop, the sheer number of them, and the cost.
The flexibility and openness of the PC platform has enabled phenomenal business growth, and attempts to prohibit that flexibility and openness have been met with resistance. Most users, given a choice between convenience and security, opt for convenience. This makes improving confidence in client platforms, and in particular PCs, a big challenge.
No single company dictates the architecture of all platforms on the network or the plan of the network itself. Although other types of platforms are increasingly being used for Internet access, the diversity of software and hardware available for PCs continues to mean that the principal client platforms of the Internet are still PC-based. As conventional businesses increasingly depend on PCs and the Internet for their success—even their very existence—the trustworthiness of platforms and PCs is an increasingly vital issue. The development of e-services and the convenience of using the same computer platform for both personal and business use mean that users increasingly need to store and use sensitive data on their platforms. Of course, they naturally expect their data to be protected from misuse even when they are connected to the Internet.
However, the ability to protect a PC or other computing platform through software alone has developed as far as it can and has inherent weaknesses. The degree of confidence in software-only security solutions depends on their correct installation and execution, which can be affected by other software that has been executed on the same platform. Even the most robust and tightly controlled software cannot vouch for its own integrity. For example, if malicious software has bypassed the security mechanisms of an operating system (OS) and managed to corrupt that OS's behavior, it is by definition impossible to expect that the OS will necessarily be aware of this security breach. It is often possible to find out whether software has been modified when one knows what modification to look for (e.g., looking for a known virus). However, current computing platform technology does not allow a local or remote user to easily test whether a platform is suitable to process and store sensitive information. For example, currently it is possible to identify an employee accessing a corporate network through a virtual private network (VPN) gateway, but it is impossible to establish with confidence whether the computing platform used by the employee is a corporate machine and whether it runs only the required software and configurations.
Experts in information security conclude that some security problems cannot be solved by software alone, for example, trusted hardware is needed as the basis for software security mechanisms such as those described by [Lampson et al., 1992], and even conventional Secure Operating Systems depend on hardware features to enforce separation of user and supervisor modes. Furthermore, privacy issues have arisen, such as the conflict of duty between providing confidence in a computing platform's behavior to the owner of a company PC and providing confidence in the platform's behavior to the individual user of that PC. Also, differences exist between providing confidence in a platform's behavior to a local user and providing that confidence to a remote entity across a network.
The Trusted Computing Platform Alliance and the TCPA Specification
These issues, coupled with emerging e-business opportunities that demand higher levels of confidence, have led to the Trusted Computing Platform Alliance (TCPA) designing a specification for computing platforms that creates a foundation of trust for software processes, based on a small amount of hardware within such platforms. A brief history of the Trusted Computing Platform Alliance (the organization set up to develop and standardize Trusted Platform technology), including its organizational structure and objectives, can be found in Appendix A.
The TCPA specification is intended for use in the real world of electronic commerce, electronic business, and corporate infrastructure security. The specification is a mixture of informative comment and normative statements (that give a list of all the things that must be done); this book attempts to provide more explanation than is given in the specification.
What Is a Trusted Platform?
A Trusted Platform (TP) is a computing platform that has a trusted component, probably in the form of built-in hardware, and uses this to create a foundation of trust for software processes. The computing platforms specified in the TCPA specification are one such type of Trusted Platform; although different types of Trusted Platforms could be built, we concentrate in particular on the instantiation specified by the TCPA industry standard. (Note that terms like Trusted Platform are italicized in this chapter because we are using them in a specific way.)
In this book, we concentrate on the issue of converting a platform into a Trusted Platform. The conversion process involves extra hardware roughly equivalent to that of a smart card, with some enhancements.
At the time of this writing, secure operating systems use different levels of hardware privilege to logically isolate programs and provide robust platform operation, including security functions.
Converting a platform into a Trusted Platform requires that TCPA roots of trust be embedded in the platform, which enable the platform to be trusted by both local and remote users. In particular, cost-effective security hardware acts as a root of trust in Trusted Platforms. This security hardware contains those security functions that must be trusted. The hardware is a root of trust in a process that measures the platform's software environment. (In fact, it could also measure the hardware environment, but it is the software environment that is important because knowing what the computing engine is doing is the primary issue.) If the software environment is found to be trustworthy enough for some particular purpose, all other security functions (and ordinary software) can operate as normal processes. These roots of trust are core TCPA capabilities.
Adding the full set of TCPA capabilities to a normal (non-secure) platform gives it some properties similar to that of a secure computer with roots of trust. The resultant platform has robust security capabilities and robust methods of determining the state of the platform. (Among other things, it can prevent access to sensitive data [or secrets] if the platform is not operating as expected.) Adding TCPA technology to a platform does not change other aspects of platform robustness, so a non-secure platform that is enhanced in the way described above is not a conventional secure computer and probably not as robust as a secure platform that is enhanced in this way. Nevertheless, we (the authors of this book) claim that the architectural changes proposed in the TCPA specification are the cheapest way to enhance security in an ordinary (non-secure) computing platform. (The architectural cost of converting a secure platform into a Trusted Platform is even less, because it requires fewer TCPA functions.) We further contrast trust and security mechanisms in the “Trust Versus Security” section later in this chapter.
Any type of computing platform (for example, a PC, server, Personal Digital Assistant or PDA, printer, or mobile phone) can be a TP. A TP is particularly useful as a connected and/or physically mobile platform, because the need for stronger trust and confidence in computer platforms increases with connectivity and physical mobility. Not only are there threats associated with connecting to the Internet, such as the downloading of viruses, but physical mobility increases the risk of unauthorized access to the platform (including physical theft). TP technology provides mechanisms that are useful in both of these circumstances.
The first Trusted Platforms containing the new hardware are expected to be desktop or laptop PCs. They will provide protection of secrets (i.e., keys that encrypt files and messages, keys that sign data, and keys that contain authorization data) using access codes, binding of secrets to a particular physical platform, digital signing using those secrets, plus mechanisms and protocols to ensure that a platform has loaded its software properly. Later, TPs will provide more advanced features such as protection of secrets depending on the software that is loaded (i.e., preventing a secret from being accessed if unknown software has been loaded on the platform, such as hacker scripts) and attestation identities for e-services. The technology is certain to evolve over the coming years.
Trusted Platforms are an unfamiliar concept, even to security specialists, but since the release of TCPA specification v1.0 in February 2001 and its backing by major industry players, they are set to become widespread. The adoption of Trusted Platforms is a building block to improving confidence in conducting business over the Internet and broadening the scope of e-services. TCPA technology allows existing applications to benefit from enhanced security and encourages the development of new applications or services that require higher or more ubiquitous security levels than presently available. (Some examples are presented in Chapter 2.) Applications and services that would benefit from using Trusted Platforms include electronic cash, email, hot-desking (allowing mobile users to share a pool of computers), platform management, single sign-on (removing the need for the user to be asked to authenticate himself or herself more than once when using different applications during the same work session), virtual private networks, Web access and digital content delivery.
The functions of the security hardware are relatively benign as far as product export/import regulations are concerned, and all export/import contentious security functions are implemented as security software (and can be changed as required for individual markets). Another important TP property is that the functions of the security hardware operate on small amounts of data, permitting acceptable levels of performance even though the hardware is low cost. In contrast, the normal platform processor is used by a TP's security software to manipulate large amounts of data and, hence, to take advantage of the excellent price-to-performance ratio of normal computer platforms.
Determining the integrity of a platform (trusting a platform) is a critical feature of a Trusted Platform. Security mechanisms (i.e., processes or features) are used to provide the information needed to deduce the level of trust in a platform. The decision itself can be made only by the user who desires to use the platform, and this decision will change according to the intended use of the platform, even if the platform remains unchanged. The user needs to rely on statements by trusted individuals or organizations about the proper behavior of a platform. It is this aspect that ultimately differentiates a Trusted Platform from a conventional secure computer.
Basic Concepts in the Trusted Platform Model
Figure 1-1 illustrates the general setup that we consider in this book. The Trusted Computing Platform Alliance has published documents that specify how a Trusted Platform (TP) must be constructed. Within each Trusted Platform is a Trusted (Platform) Subsystem, which contains a Trusted Platform Module (TPM), a Core Root of Trust for Measurement (CRTM), and support software (the Trusted platform Support Service—TSS). The TPM is a hardware chip that is separate from the main platform CPU(s). The CRTM is the first software to run during the boot process and is preferably physically located within the TPM, although this is not essential. The TSS performs various functions, such as those necessary for communication with the rest of the platform and with other platforms. The TSS functions do not themselves need to be trustworthy, but they are nevertheless required if the platform is to be trusted. In addition to the Trusted Subsystem in the physical Trusted Platform, Certification Authorities (CAs) are centrally involved in the manufacture and usage of TPs in order to vouch that the TP is genuine.
Figure 1-1. The overall Trusted Computing Platform model
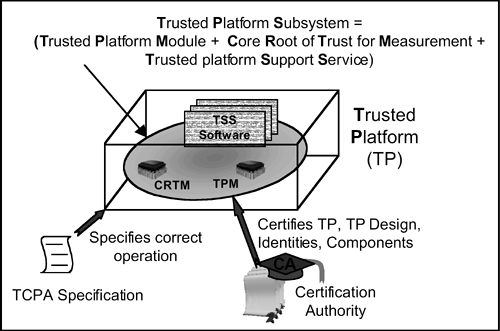
Readers with a background in information security know that a Trusted Computing Base (TCB) is the set of functions that provide the security properties of a platform (in other words, that enforce the platform's security policy). The TCB in a Trusted Platform is the combination of the Trusted Subsystem (mainly dealing with secrets) and additional functions (mainly dealing with the use of those secrets, such as bulk encryption). As such, the Trusted Subsystem is a subset of the functions of the TCB of conventional secure computers (which would normally include both dealing with secrets and using secrets). Critically, however, the Trusted Subsystem contains some functions not found in a conventional TCB. Conventional secure computers provide formal evidence that a TCB in certain states actually can be trusted. This is done by means of formal assessment and certification of the platform in a particular configuration. The accreditation shows that the platform can operate securely if it is operated in a particular way, but it is said to be unusual for platforms to actually be operated in tested configurations! In contrast, the Trusted Subsystem provides a less formal means of showing that the TCB is both capable of being trusted and actually can be trusted in a variety of configurations. The Trusted Subsystem first demonstrates that it can be trusted and then demonstrates that the remainder of the TCB in a Trusted Platform can also be trusted. This involves certification from trusted entities that are prepared to vouch for the platform in various configurations.
Basic DefinitionsPlatform A computing device, usually one that communicates with other such devices Trusted Computing Platform Alliance (TCPA) The organization that has specified how to produce Trusted Platforms Trusted (Computing) Platform (TP) A platform that creates a foundation of trust for software processes Trusted Platform Module (TPM) The hardware root of trust of a TP Trusted Platform Subsystem A set of capabilities inside a platform that are defined by TCPA Certification Authority (CA) An organization that vouches for an entity (e.g., for a cryptographic key, hardware or software component, platform, or organization) |
