Everyone knows the decades-old scheme of password-based login. Records about users known to the application are stored in the database table called users. Each record has the username and password fields (the actual information tokens necessary for authentication) along with other information about the user.
The basic table looks like this in the MySQL Workbench (http://www.mysql.com/products/workbench/):
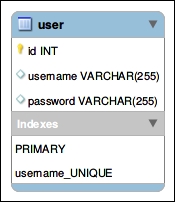
The username field is used to actually identify the user among others. Therefore, it has the UNIQUE constraint.
The password field contains a special string known, by definition, only to the user and the application. To further protect the password, the application does not store it as plain text, but as its cryptographically secure hash value, which is generated by an algorithm such as bcrypt. In this way, the application has no way to know the original plaintext version of password.
Note
The most important part of password storage is the cryptographically secure part. So, the algorithm of hashing should exhibit the following traits useful for our purposes:
- It should use the cryptographic hash function, the main characteristic of which is being one-way, that is, you can compute hash from plaintext easily but getting plaintext from hash is very hard.
- It should ideally use a different hashing function for each given plaintext. This is done by the technique called salting.
- It should be slow.
When authenticating, a user provides the username to claim who he is and the password to prove it. As the application knows which algorithm it used to hash the password when the user was registering, it hashes the provided password in the same way and compares the resulting string with what it has in the database for the provided username. If hashes are found identical, then the user is really who he claims to be and we consider him authenticated.
Well, you probably know that already. Let's implement this authentication method in our example CRM application.
Note
Note that username/password authentication is not the only way to authenticate the user. There are other methods, varying both in complexity of security checks and the user interface. To name a few, there is the OpenID initiative (http://openid.net/) and the OAuth protocol (http://oauth.net/2/) to authenticate in an application using credentials of another application, and signed and confirmed SSL certificates (https://developer.mozilla.org/ru/docs/Introduction_to_SSL#_Client_Authentication_).
We will ultimately perform the following steps:
- Build the user records management interface.
- Build the user login form.
- Introduce the indicator to display user status (logged in/logged out).
