Wireshark has been one of the important tools for network analysis and troubleshooting. Wireshark gives complete visibility of how a packet is treated at various stages of its propagation from one application endpoint to the other over the network. This visibility powers a network operator to understand what an application is doing, if it’s behaving as expected or there is an unexpected malicious attempt to disrupt the network, application, and IT resources.
The Internet has helped people come closer and isolated networks get interconnected. However, it is also the common entry point for security attacks. The threat origin is not limited to the Internet, most of them are traced to internal sources. With clouds spanning both local and the Internet, the threat landscape has expanded manyfold. The overall cybercrime cost for year 2021 is estimated as $6 trillion and expected to double in the next four years.
Network security attack identification, postmortems, and prevention
Discovering malware and covert communications
Tips and tricks for Wireshark forensics
DDoS and malware step-by-step analysis with real attack pcap files
Network Attack Classification
Cyber-attacks have evolved with time, and there are hundreds of new variants of these getting discovered each day. Every attack type tries to exploit some vulnerability on the end hosts, networks, networking protocols, and even firewalls and security appliances too.
Every attack type can be completely different or may be minor or major variants of any known vulnerability exploit. However, the popular ones can be broadly categorized into a few buckets. The following section will discuss the same in more detail. We will discuss in detail how their signature can be detected through Wireshark.
Packet Poisoning and Spoofing Attacks
With the ARP spoofing type of attacks, the attacker sends ARP replies of the same IP with a different MAC.
In ARP poisoning, the attacker sends ARP replies with different IPs for the same MAC.
ARP spoofing aims at impersonating another machine, thereby redirecting data meant for the victim machine toward itself. ARP poisoning on the other hand is normally aimed at corrupting the ARP table of a victim machine. Both ARP poisoning and spoofing have a common motive and operate through malicious ARP or gratuitous ARP replies.
Often, both of these terms are used interchangeably. The following figures will demonstrate the subtle difference between these techniques.

A screenshot of Address Resolution Protocol spoofing. It contains no, time, source, destination, protocol, length, and info. It exhibits different M A C claiming as the owner of the same I P.
ARP spoofing

A screenshot illustrates Address Resolution Protocol poisoning. Hardware type, info details that indicate the same M A C is sending ARP reply for 2 IPs are highlighted in green.
ARP poisoning
DHCP Spoofing
Like ARP spoofing, in this type of attack the attacker machine waits for DHCP requests and sends DHCP offers and ACK with its own address as the default gateway or DNS server. This directs all traffic from the victim machine to the attacker and creates the perfect scenario for a man-in-the-middle attack. The attacker machine may also act as a proxy for all communications of the victim machine with any destination, thereby stealing sensitive information, passwords, etc.

A screenshot of Dynamic Host Configuration Protocol verification. Highlights the source details, D H C P offer on line 2 and Magic Cookie, D H C P to Padding, 00000000. Comment on left displays make sure the D H C P server and offer information are correct.
DHCP verification
DNS Spoofing and Poisoning
Consider the previous scenario of ARP or DHCP spoofing causing traffic to be diverted to the attacker machine. Also, it can act as a DNS server if the DHCP offer is compromised by specifying the attacker's IP as the DNS server IP.
Like ARP poisoning, the DNS server cache entry can be poisoned with adding incorrect entries by an attacker DNS client.

A screenshot of Domain Name System spoofing. Two colors indicate wrong mapping injected by an attacker with a higher Time to live.
DNS spoofing
Prevention of Spoofing Attacks
Apart from ARP, DHCP, and DNS discussed earlier, practically any networking protocol (e.g., OSPF, BGP, STP) can be spoofed or poisoned unless protected. Most of the protocols these days have authentication built in for every packet. Some also have antireplay and encryption protection built into the protocol. Both must be used wherever available. DNSSEC (authentication and integrity protection) and DNS over TLS (encryption) are recommended over traditional DNS.
For ARP and DHCP spoofing, layer 2 switches have port security, and dynamic ARP inspection (DAI) features are available and recommended for secure operation.
Network Scan and Discovery Attacks
These types of attacks are not meant to cause any real damage but are used as a reconnaissance method before a real attack. With these attacks, the attacker gains an understanding of the network topology, endpoint IP/IPv6 addresses, open ports, what kind of operating system is being used, what kind of security infrastructure is in place, etc. This is a very vital and sensitive information as it can be further used to exploit the known vulnerabilities on those network and infrastructure devices. The following subsections discuss in more detail some of the common attacks.
ARP and ICMP Ping Sweeps
This type of scan sends ICMP echo or ARP request messages for every host within the defined subnet. Attackers prefer doing an ARP scan if the attacker is in the same subnet as the scanned device.

A screenshot of sweep attacks. The above window in the screenshot indicates Address Resolution Protocol sweeps from attacker 192.168.1.3 and the bottom window points to Internet Control Message Protocol sweeps from attacker 192.168.1.3.
Sweep attacks – ARP and ICMP
UDP Port Scan
With UDP port scan, the attacker sends a burst of UDP packets to the target victim, sequentially increasing the destination port value from 1 to max 65535.
If there is no service running on the UDP port, the victim replies with an ICMP unreachable message saying the port is not reachable. However, some hosts do not do. Sometimes, if the port is open and the application behind this port consumes the packet and if the packet payload is not the expected format, the attacker may not get a response. Based on this logic, the attacker gets an understanding of open and closed ports on a device.

A screenshot illustrates the User Datagram Protocol port scan. It has two sections of details, one reads, U D P port scan being done by attacker 192.168.1.3, and the second reads, Not all hosts reply with I C M P unreachable for the non-existing port. Here host 192.168.1.2 did not.
UDP port scan
TCP Port Scan
If the port is closed, a TCP packet with RST is returned.
- If the port is open, a TCP packet with SYN ACK is returned.
The attacker then quickly sends RST and moves on to scan the next port.
Like SYN scan, the attacker can utilize other TCP flags (ACK, FIN, PSH, URG) when sending the packet by setting any of these flags. By interpreting the response type, it can be determined whether a port is open, closed, or filtered by any access list or firewall.

A screenshot of Transmission Control Protocol. Highlight info details suggest the T C P port scan being done by attacker 192.168.1.3.
TCP port scan
OS Fingerprinting
There may be minor differences between operating systems in the way they respond to a TCP/IP connection attempt. For example, one OS may have a different initial sequence number than the other. Similarly, the IP Identifier field, TCP options support, and TCP initial window size may be different too.
An attacker may use this to its advantage and try to identify the victim’s operating system version.

A screenshot illustrates Operating system fingerprinting. Highlight details suggest a T C P scan followed by I C M P and T C P scan with some predefined pattern.
OS fingerprinting
Preventing Port Scan Attacks
The use of a good firewall and intrusion detection/prevention systems will help with this. Honeypots can be useful too. After the scan is detected, it can be redirected to a honeypot instead of forwarded to the victim.
Brute-Force Attacks
Brute-force attacks are used to gain access to any device by guessing the username or password. Although guessing the username or password can take a long time to crack, there are a lot of techniques like rainbow table, dictionary of known credentials, hybrid brute force, etc. which can make it quicker.
All of these techniques generate a flood of traffic like port scans and can be easily detected through Wireshark analysis. Also, at the end device side, multiple failed attempts should raise a red flag.
In Figure 8-9, we have demonstrated a telnet brute-force connection attempt. We can see a flood of TCP connection attempts from sequential source ports. Further, the TCP data can be inspected by clicking one of the packets and navigating through the Wireshark menu Analyze ➤ Follow ➤ TCP stream.
Preventing Brute-Force Attacks

A screenshot illustrates Brute-force attack detection. It has two windows, the above one displays two highlights in green in which the first information about the port suggests a burst of TCP connection and the second points to the bottom window. The details in the bottom window suggest random login attempts.
Brute-force attack detection
DoS (Denial-of-Service) Attacks
Denial-of-service attacks aim to disrupt a network or service by generating authorized data or connections in such volume that it overwhelms the capacity.
For example, if a server can handle 100,000 connections at a time, and if an attacker generates connections that exceed this number, the server is overloaded and cannot handle legitimate connections. Similarly, if a service provider has a 10 Gbps Internet link and an attacker generates data that clogs the network capacity, then the legitimate data and users are affected.
Most of the time, the attack doesn’t come from a single source. Either the attacker has a huge globally distributed infrastructure or infects multiple devices with malware and controls them to generate a coordinated attack against the victim network or service endpoint. Such distributed DoS attacks are termed DDoS attacks. DDoS attacks can cripple a network and server very quickly due to the distributed, synchronized nature that generates a huge load on the infrastructure.

A screenshot of distributed denial-of-service examples, random User Datagram Protocol, and Internet Protocol. Highlights source, and protocol details.
DDoS examples, random UDP and IP protocols
Figure 8-11 shows two examples from real DDoS attacks. The first example shows TCP packets with SYN ACK flags and are coming from the same source and destination ports.

Two screenshots illustrate distributed denial-of-service examples. Highlights the above screenshot suggests T C P S Y N A C K with the same port, and the bottom one suggests a domain name system reply from Secure Shell 22.
DDoS example: TCP SYN ACK with the same port, DNS replies amplification with an SSH port
Preventing DDoS Attacks
Normally, it's not possible to completely block the ports or links that bring in offending connections and data as they are legitimate traffic. For example, web traffic directed to a web server and upload or download data on an Internet link. However, if the pattern of the attack is unusual, the specific sources can be blocked or redirected to a honeypot.
A good network design with proper segmentation and redundant systems and servers should help lower the damage and help recover quicker in case of attacks seen.
Network and infrastructure should be beefed up with web security, good firewall, and intrusion detection and prevention policies. Endpoint security, antivirus, and antimalware tools should be deployed to protect the edge devices.
Malware Attacks
This type of attack constitutes a significant portion of the overall cyber-attacks recorded. Malware stands for malicious software. Malware has a broad category of software that infects and exploits networks, servers, and end hosts in various ways.
Virus, worms, and trojan horses: They enter a computing device through physical, Internet, emails, file attachments, and all possible digital transfer means. They infect the system, can encrypt or delete all data, and replicate and propagate to other computers by exploiting existing vulnerabilities. Sometimes, they can act like ransomware too.
Spyware, adware, keyloggers, and phishing: These types of malware aim at collecting sensitive information from the victim and don’t cause much damage. They can replicate and propagate like viruses and worms through all possible means.
Botnet and crypto miners: These types of malware use the computing resources of the victim system to cause DDoS-type attacks or earn money through crypto mining.
Ransomware: This type of malware after infecting the victim device or network demands ransom to not cause damage to the system.
Every malware has its own way of communicating over the network and replicating. By monitoring the same Wireshark can detect malware communication signatures through packet capture. However, some of them can be extremely stealthy and may not communicate at all. Those are difficult to analyze through Wireshark.

A screenshot suggests a Turkish malware redirect. Highlight suggests redirecting to a spyware website, and green highlight suggests the user tries to download a skype setup, but malware does TCP inject.
Turkish malware redirect
Prevention of Malware Attacks
Following a proper network and security hygiene will go a long way in preventing malware attacks.
Network and infrastructure should be beefed up with web security, good firewall, and intrusion detection and prevention policies. Multifactor authentication, endpoint security, and antivirus and antimalware tools should be deployed to protect the edge devices.
All devices should have updated software, and any known vulnerabilities should be patched at the earliest. Email, web, and cloud security protection mechanisms must be deployed.
Most malware attacks rely on social engineering and phishing techniques which trick the end user into clicking malicious links and opening malicious attachments. User education is important to prevent malware attacks through all such means.
Wireshark Tweaks for Forensics
Autoresolving Geolocation
It is very important to know the attacker's source IP geolocation. Wireshark supports the integration of the Country, AS number, and City database provided by MaxMind. The details can be downloaded free of cost from MaxMind as a .mmdb file format at the following location after creating an account:
www.maxmind.com/en/accounts/767404/geoip/downloads

A screenshot illustrates the Wireshark preferences window. Highlights name resolution option and Edit button on MaxMind database directories.
Enabling geolocation
Changing the Column Display

A screenshot illustrates the Wireshark display custom column. It has 5 categories, displayed, Title, Type, Fields, and Field occurrence. Highlights line with Title, Country, Window, Time to Live, Source Port, and Destination Port.
Wireshark display custom column
Frequently Used Wireshark Tricks in Forensics
Find Exact Packets One at a Time
Though the display filter has good features, if regular expression matching or packet hex matching is required, this method is useful.
This process finds one packet at a time and moves to the next one once the Find button is clicked again.
Hex: Find a packet with a hex pattern matching the specific hex value.
Regular expression: It matches the string in the dissected text shown in the packets.
String: The string matches the text in the info field.

A screenshot illustrates the process to find exact packets one at a time. It displays the selected option Hex value on the left side drop-down list, finds a button on the right, and a table with categories such as protocol, country, length, window, time to live, source port, and destination port.
Contains Operator
This is a useful search operator in the display filter. We can have flexible searches like the following:
frame contains GET: Looks for the value GET inside the complete frame
http contains facebook: Looks for the text value facebook in the HTTP fields
data-text-lines contains “javascript”: Finds all web pages containing a certain string
Following a TCP Stream
This helps stitch payload fields in the TCP and decode. This gives visibility into what the application is doing and is very useful while analyzing HTTP streams.
This option can be triggered with the menu option Analyze ➤ Follow ➤ TCP stream.
Wireshark Forensic Analysis Approach
Wireshark packet inspection can help identify the type of attack. In this section, the analysis approach for two important types of attacks is discussed in detail.
The basic approach here is to find out the IOCs (Indicators of Compromise) and logically determine whether the packet communication behavior is legitimate or malicious. IOCs can be an IP, domain name, user agent, hostname, geolocations, communication pattern, etc.
Wireshark DDoS Analysis
When did the issue start?
What are the targets?
What is the IP source of the attack?
What are the geographical locations and is traffic expected from them?
Is the traffic pattern similar to the baseline?
What are the protocols involved?
- Are the TCP/IP fields and communication pattern normal?
TCP/UDP port matching
HTTP string and substring matching
Check for embedded URLs in the TCP stream
Check the authenticity of the websites in use
Is the packet flow expected or indicate a DDoS attack?
The analysis in this section considers a packet capture from a real-world DDoS attack. The sample is taken from the StopDDoS GitHub repository:
https://github.com/StopDDoS/packet-captures

A screenshot of the distributed denial-of-service capture file. It illustrates the details of the display filter of time, source, destination, protocol, country, length, window, time to live, source, destination port, and info. Highlights the twelfth line.
DDoS capture file display
When did the issue start?
What are the targets?
What is the IP source of the attack?

A screenshot illustrates the source of the attack window. It displays details for address, address B, packets, bytes, packets A to B, bytes A to B, rel start, I P v 6, T C P.7674, and U D P .19.
Source of the attack
What are the geographical locations and is traffic expected from them?
The endpoint graph statistics ➤ endpoints shows the geographic locations and AS numbers of sources in a tabular format. Also, it can be visually inspected by choosing the map option. It can be seen that most of the packets are concentrated at the United States; one of the origins shows 5000+ sessions, which doesn't look normal. Also, the conversation is not limited to a single IP. IP addresses seem to be increasing in sequence, which is also unusual. Mostly, it appears as a distributed botnet attack, or the IP addresses are possibly spoofed and manually generated by some DDoS attack tools.
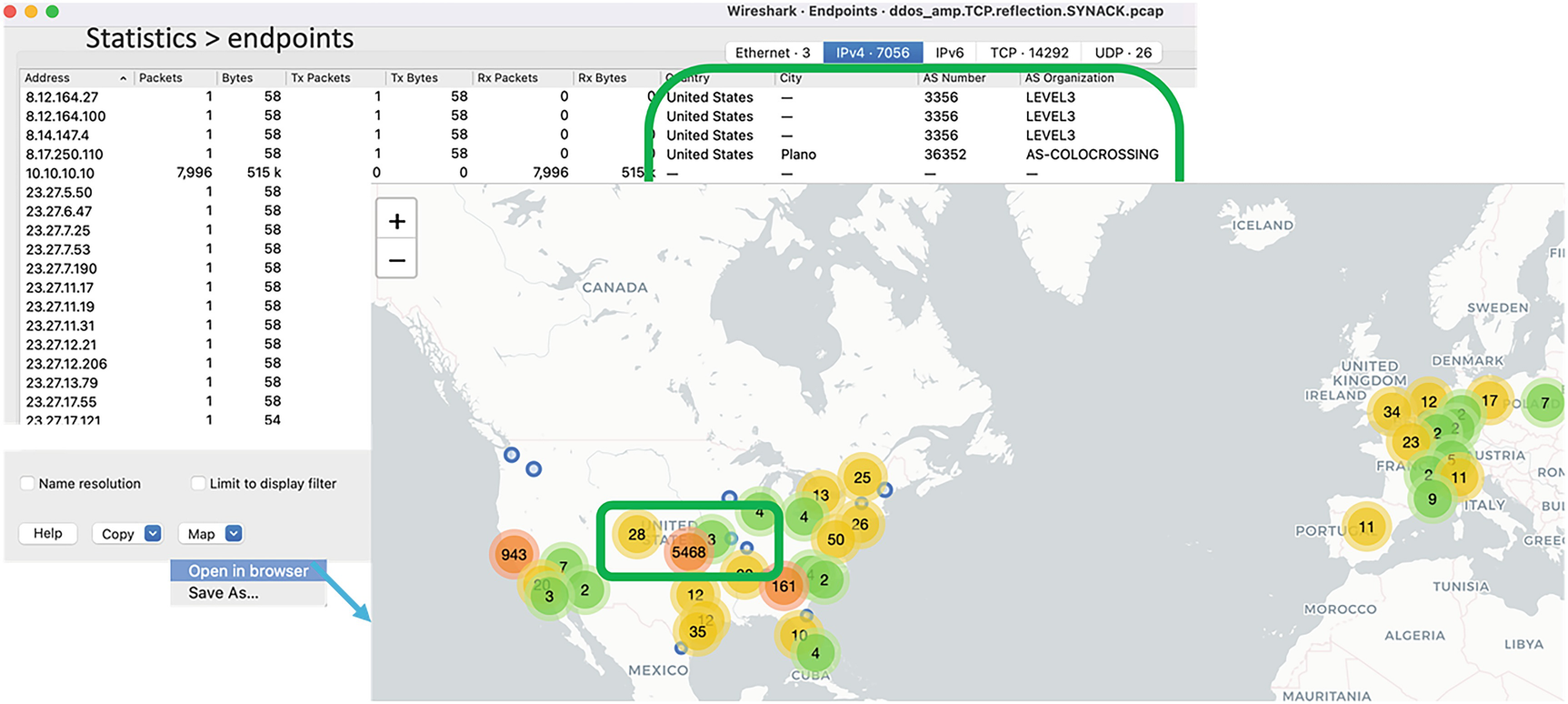
A screenshot illustrates the Geographic location of the attack on the source window. Highlights the endpoints and on the world map, displayed separately in a browser.
Geographic location of attack
Is the traffic pattern similar to the baseline?
Traffic TCP sessions look unusual, but the rate of traffic is very nominal (9 Kbps). The traffic rate can be verified from the I/O graph. All the sources in the 7000+ sessions are sending only a single SYN packet. They don’t attempt to establish the session also.
What are the protocols involved?
The statistics ➤ protocol hierarchy chart lists all the protocols seen in the capture file and is very useful to see all the applications and protocols involved on a single page. Based on the output, it can be seen it’s predominantly TCP traffic (96%), but no applications are involved on top of TCP. This also looks unusual.
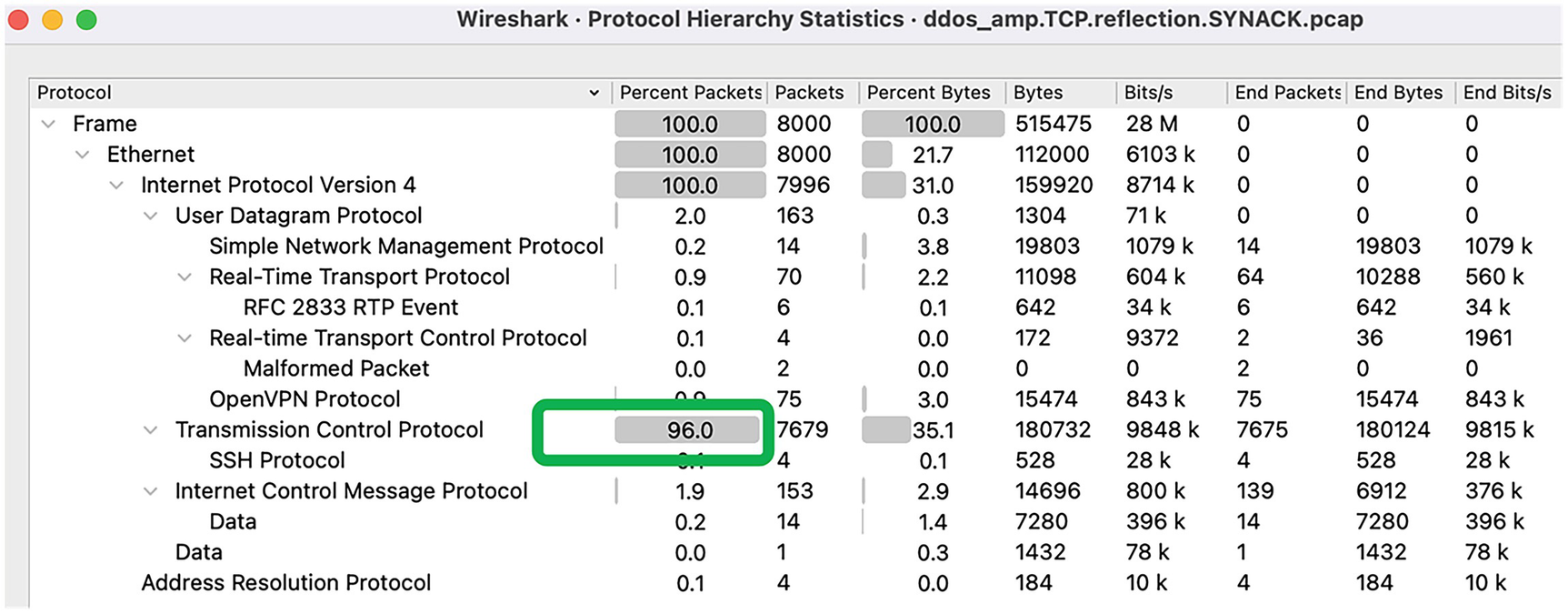
A screenshot of the window displaying protocol hierarchy statistics in the Wireshark file. It contains a protocol, percent packets, bytes, bits, end packets, end bytes, and end bits. Highlights transmission control protocol with 96.0 of percent packets.
Protocol hierarchy
- Are the TCP/IP fields and communication pattern normal?
- IP TTL field analysis
Seems in similar range but not exactly the same. Indicating the attack source is not the same device but geographically not too far
TCP/UDP port, sequence number, window, and other fields
All the packets are SYN ACK packets coming from source port 80 to a random destination port. A group of sources have the same TCP window size. It looks like the end sources are tricked to send the packet to the victim. This looks like a TCP reflection attack.
HTTP string and substring matching: Not applicable
Check for embedded URLs in the TCP stream: Not applicable
Check the authenticity of the websites in use: Not applicable
Is the packet flow expected or indicate a DDoS attack?
The flow is not expected based on all the preceding observations. The sources are distributed across the United States mostly, and it looks like sources are tricked to send SYN ACK toward the victim in response to SYN from the attacker as the attacker has possibly spoofed the source IP in the SYN packet as the victim's IP. The sources are generating SYN ACK toward the victim based on the source field in the SYN packet.
Conclusion: It can be concluded as a distributed denial-of-service attack involving a TCP reflection mechanism.
Wireshark Malware Analysis
In this analysis, we have used a pcap file of a true malware download that happened when a user clicked a tiny URL link. The PCAP file is taken from the malware-traffic-analysis.net portal.
Be careful while handling this pcap file. Use a controlled and restricted environment to analyze.
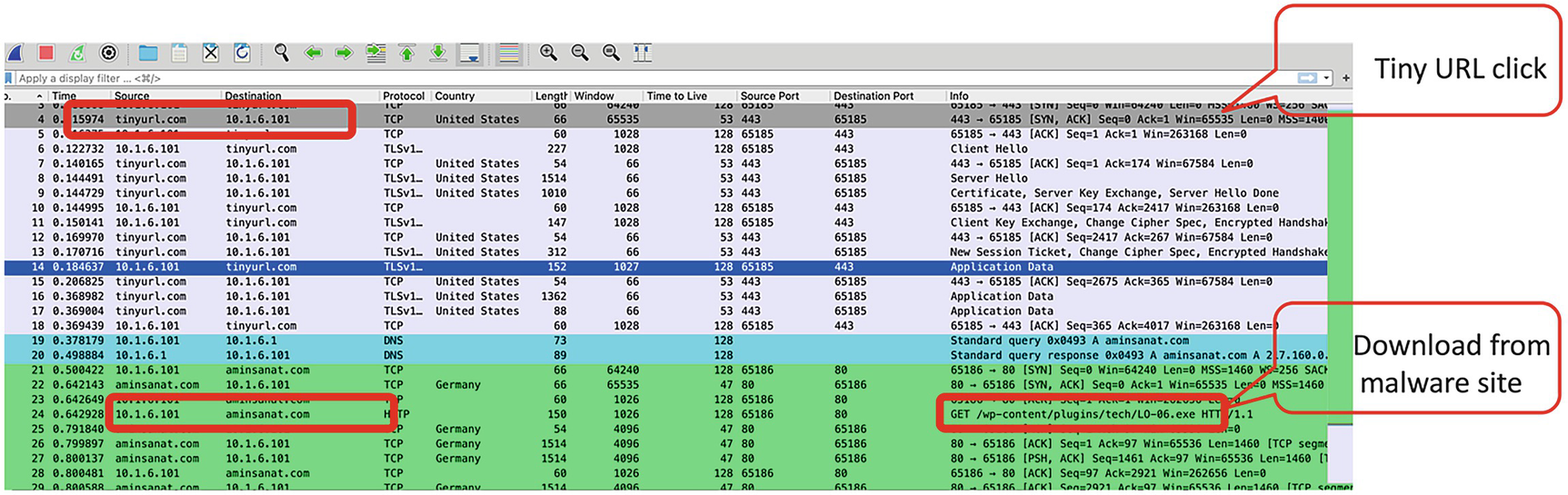
A screenshot of the window displays malware download. It indicates the source and destination details of the malware download site with a tiny U R L click.
Malware download
When did the issue start?
Ans: As per the first URL click, Jan 7, 2021, 01:52:24.437356000 IST
What are the targets?
Ans: The download was triggered from the IP 10.1.6.101.
What are the websites/download IPs involved? Check the authenticity of the websites in use.
Ans: The IPs are autoname resolved by Wireshark (GeoIP integration). The websites involved are tinyurl.com and aminsanat.com.
When a query is done for both on virustotal.com, the download website aminsanat.com is tagged as malicious.
What are the protocols involved?
Ans: The chart seen with Statistics ➤ Protocol hierarchy shows the majority of data is for HTTP. We can create a filter for the same.

A screenshot of the window displays Wireshark malware analysis through protocol hierarchy statistics. Highlights line with the protocol title, hypertext transfer protocol, and percent bytes 85.1. Two drop-down lists displays option, prepare as a filer and selected.
Protocol hierarchy
- If HTTP is involved, filter GET and POST requests: http.request
HTTP string and substring matching
Check for embedded URLs in the TCP stream
Check the authenticity of the websites in use
Ans: Found one GET request which contains a file download URI. The last packet shows the successful download of a file named LO-06.exe.
On virustotal.com, aminsanat.com is tagged as malicious.

A screenshot of the window displays hypertext protocol. Highlights the info category at the top on the right side. Request in the frame, 24 details are also highlighted.
Are the TCP/IP fields and communication pattern normal?
Ans: The TCP/IP flow looks normal. It’s a single flow which stops after the download is over.
Verify authenticity of downloads or content transferred.
Be careful with the malware content analysis. Only work within a controlled and restricted environment. Don’t open the content. We can verify the hash of the file without opening the same. And then compare the hash with a known database.
Ans: The file transferred through HTTP can be extracted through Wireshark by navigating through the menu File ➤ export objects ➤ HTTP.
Check the file hash (md5/sha1)
Is the packet flow expected or indicate any malicious activity?
Ans: Based on the website reputation and also the content verification, it is concluded as a malicious activity.
Summary
With the evolution of networks and the Internet, security threats are evolving too. Attacks by cybercriminals are getting more result oriented. Cyber war is real. While real war is being fought on the battlefield, cyber war is being used as a virtual aid for the same. Latest statistics show the overall cybercrime costs stand at $6 trillion and are projected to touch $10 trillion in the next three years.
Cyber security trends show that ransomware, crypto mining, supply chain attacks, deepfake, video conferencing attacks, and IoT attacks are hot. Cyber security and analysis need to keep pace with all the emerging threats.
All categories of network and security attacks and how to prevent them
How Wireshark can be used to analyze each of these attacks
Tips and tricks and filters for Wireshark forensic analysis
Step-by-step troubleshooting and analysis approach to DDoS and malware attacks through Wireshark
References for This Chapter
DDoS analysis pcap files: https://github.com/StopDDoS/packet-captures
Malware analysis pcap files: https://malware-traffic-analysis.net/
Wireshark geolocation database: maxmind.com
Cyber security trend statistics: forbes.com
