Bluetooth is a very popular near-field wireless communication technology used extensively for gadgets that go cordless. Almost all modern audio/video and telephony equipment like wireless speakers, earphones, smartwatches, computer peripherals, and smartphones can use Bluetooth to communicate with external devices wirelessly. There are lots of other interesting use cases with Bluetooth Low Energy technology like indoor direction finding, inventory management, low-power data transfer, and near-field device networking. By 2021, the number of Bluetooth-enabled devices shipped annually touched one billion and is expected to reach seven billion by 2026.
Evolution of Bluetooth standards
Introduction to the Bluetooth protocol stack and filtering through Wireshark
Wireshark tools required for Bluetooth capture (macOS, Windows, Linux)
Wireshark Bluetooth packet capture analysis and troubleshooting scenarios
Introduction to Bluetooth
Bluetooth 1.0 was introduced in 1999 as a short-range packet-based wireless communication technology, and it has evolved since then to Bluetooth 5.3 released in 2021. Version 4.0 onward supports Bluetooth Low Energy (LE) technology, which uses less power and is in the range of 0.1–0.5 times the classic Bluetooth (before version 4).
Bluetooth was standardized by IEEE as 802.15.1 back in 2002, but since then all the development is controlled and maintained by the Bluetooth Special Interest Group (ISG), an industry-led group of 35,000+ companies. All Bluetooth products in the market should meet ISG standards.
Communication Models
Bluetooth Classic uses a hub and spoke communication model in which the hub (also known as the main) can communicate with up to seven spokes (also known as the follower). The main and followers can change roles based on agreement. Also, there is a Bluetooth mesh technology implementation which operates on a flood networking model (send the packet to all other peers except those who sent the packet to it). Bluetooth LE can operate in either of the models depending on the application profile. The device roles and negotiation can be tracked in the Wireshark Bluetooth captured packet type of HCI_CMD or HCI_EVT.

A screenshot illustrates commands for Bluetooth device role negotiation. Command executed in steps, Bluetooth Sent command. Create Connection with subcommands, Opcode, packet type, Clock offset Valid Flag, and Allow Role Switch.
Bluetooth device role negotiation
Radio and Data Transfer
The Bluetooth radios use an unlicensed but regulated spectrum at 2.40–2.483 GHz. Bluetooth Classic (BR/EDR) uses 79 channels 1 MHz each, which includes 32 channels for discovery purposes, whereas Bluetooth LE uses the same band with 40 channels, each 2 MHz wide with only 3 channels for discovery. This makes discovery quicker in LE as fewer channels to scan. The range, power output of the radios, modulation, and data rate vary between Bluetooth versions (1–5) and standards (Classic/LE).

An image illustrates Bluetooth bandwidth and channel comparison for Bluetooth Classic Versus L E. Bluetooth Classic uses 79 channels, one Mega Hertz each, and Bluetooth L E uses 40 channels, two Mega Hertz each.
Bluetooth Classic vs. LE
Bluetooth Radio Specifications
Bluetooth Classic | Bluetooth Low Energy | |
|---|---|---|
Radio class | Type 1: 10–100 mW Type 2: 1–2.5 mW Type 3: 0.01–1 mW | Mostly Type 3 Consumption range 0.01–0.5 mW |
Frequency band | 2.4–2.483 GHz | 2.4–2.483 GHz |
Number of channels | 79 total including 32 for discovery | 40 total including 3 for discovery |
Channel width | 1 MHz | 2 MHz |
Modulation | BR: FSK/GFSK EDR2: π/4-DQPSK EDR3: 8 DQPSK HDR4: π/4-DQPSK HDR8: π/4-DQPSK | FSK/GFSK |
Data rate | BR: 1 Mbps EDR2: 2 Mbps EDR3: 3 Mbps HDR4: 4 Mbps HDR8: 8 Mbps | 125 Kbps to 2 Mbps |
Range | Up to 100m depends on radio, data rate, and modulation | Up to 100m depends on radio, data rate, and modulation |
Encryption | 56/128-bit physical and application | AES 128-bit physical and application |
BR: Basic rate
EDR: Enhanced data rate
HDR: High data rate
G/FSK: Gaussian/frequency-shift keying
PSK: Phase-shift keying
Bluetooth Protocol Stack
Bluetooth uses a completely different protocol stack specified and maintained by Bluetooth SIG standards. The protocols in the stack can be distributed across the hardware (controller) and software (host) portions of the device. The hardware or the Bluetooth chip is known as the controller and can be internal or external to the device. The software or OS is known as the host and runs the protocols that interact with the local controller and Bluetooth peer host.
Between the host and controller, there is a middle layer known as the Host Controller Interface (HCI) which provides a software interface to the host OS to interact with the controller hardware.
In some implementations where both host and controller are integrated together (like an audio headset), HCI may be absent. But as a standard implementation, most vendors still retain the HCI layer in such scenarios.

A model indicates Bluetooth protocol stack. It has three layers. The host contains application layer protocols L 2 C A P. H C I has H C I protocol. Controller link manager and radio.
Bluetooth protocol stack
Controller Operations
The Bluetooth controller hardware normally takes care of the physical and data link layers of the communications. It has protocols running in the link manager and radio layers.
Radio and Baseband Processing
Bluetooth radio takes care of the modulation and demodulation of the baseband signal, transmission, and reception of the packets, synchronization through clocking, etc. Details on this were discussed in the “Radio and Data Transfer” section.
Link Management Protocol (LMP)
Collect device identification (like device name, MAC/hardware address)
Negotiate authentication and encryption key
Set up and tear down the link
- Negotiate link modes/types
ACL: Asynchronous Connection Less links are meant for packet-oriented communication and don’t wait for any signaling or time slot to transmit the packet. For error detection, a CRC bit is appended along with actual data bits. Packets with CRC errors are retransmitted with an ACL type of link.
SCO: Synchronous Connection Oriented links are normally used for voice. The device must wait for its reserved time slot to transmit. SCO links support FEC, but no retransmissions are done.
LMP provides error detection through CRC check and error correction through forward error correction (FEC). Packets with CRC that are uncorrectable are retransmitted until an acknowledgment is received.
The LELL (Low Energy Link Layer) protocol is the simpler version of LMP used on Bluetooth LE devices.
HCI
All commands from the host to the controller are addressed to the HCI, and a response is sent from HCI to the host.
All data communication through L2CAP also passes through HCI, and in the captured packets, you will see the HCI header.
On a hostless system where HCI is absent, data and control packets are directly handed off by L2CAP to the link layer.

A screenshot of the H C I packet filter. The window has the option to check commands upon selection and indicates display filter H C I H four command.
HCI packet filter
Host Layer Operation
L2CAP
- Multiplexing multiple applications over a single link
All upper layer application, control, or discovery protocols data passes through L2CAP
Fragmentation and reassembly of data
Handling one to many replications (hub and spoke topology)
Quality of service (QoS)

An image of L 2 C A P packet filter. It illustrates display filter B T L 2 C A P. It has sub commands; Information response which includes, Identifier Length, Information Type and Result; Fixed channel supported.
L2CAP packet filter
Application Profile–Specific Protocols
Bluetooth supports a wide variety of applications like telephony, audio/video, TCP/IP communication, medical or fitness equipment communication, computer I/O (mouse, keyboard, etc.), and many more. For every application, there is a standard protocol and parameter specifications defined by SIG, known as Bluetooth profiles.
The following are some of the protocols which run on top of L2CAP and help in application discovery and operation.
SDP

An image illustrates Session Discovery Protocol filter.The command indicates, Bluetooth S D P protocol has three sub commands, Service search request, Transaction ID and Parameter Length. Protocol type and information reflects at central pane.
Filtering SDP frames
Telephony Control
The Telephony Control Protocol – Binary (TCS-Bin) takes care of use cases related to telephony control like answering a call, disconnecting a call, call volume control, etc. from a connected Bluetooth device.
Audio/Video Control and Transport
For audio control like music play, pause, forward, volume control, etc., a Bluetooth device uses the AVTCP (Audio Video Transport Control Protocol). For audio distribution, AVDTP (Audio Video Distribution Transport Protocol) is used by the A2DP profile.
RFCOMM
Radio Frequency Communication is a protocol used to emulate serial data connections the same as EIA-232/RS-232 over a radio link. Many protocols like Telephony Control can use RFCOMM to send control commands. Many other protocols also can use RFCOMM as it’s natively available and simple to use.
Other Adopted Protocols
There are many protocols which are not native to Bluetooth but still have use cases and are being used. For example, PPP and TCP/IP-based protocols are foreign to Bluetooth. Still, they can be used and encapsulated over L2CAP and transported between peers.
Tools for Bluetooth Capture
All the popular operating systems don't support promiscuous mode (packets in the air not meant for local devices) for Bluetooth packets. For capturing promiscuous mode Bluetooth packet communication, an external Bluetooth sniffer like Ubertooth is required.
Only Linux natively provides support for capturing Bluetooth packets directly through Wireshark. For Windows and macOS, third-party tools are required.
Linux

An image of Linux Wireshark depicts Bluetooth packet capture. It has Bluetooth Zero highlighted in green rectangle indicates Bluetooth capture in progress.
Linux Wireshark Bluetooth packet capture
Windows
On the Windows operating system, Wireshark cannot access the Bluetooth adapters directly. To capture Wireshark packets, the BTP (Bluetooth Test Platform) utilities provided by Microsoft are required. The BTP packages can be downloaded from Microsoft Through the link, https://learn.microsoft.com/en-us/windows-hardware/drivers/bluetooth/testing-btp-setup-package. The installer by default installs into the C:BTP folder.
This opens a small GUI window which shows the packet statistics and a button to select the capture type (full packet/partial packet).
If capture mode is defined as “Wireshark” (default mode), it automatically dumps the captured packets to a TCP pipe (port 24352 default) and starts Wireshark with the capture interface as the TCP pipe.
In the following example, we have a specified mode and a non-default TCP port 23456.
This may trigger a pop-up screen from Wireshark to allow the opening of the port.

An image of Windows Bluetooth Wireshark capture with B T V S. It has Command Prompt window indicates; port I D, two three four five six; Frame count and option of full packet logging. The other window highlights details capturing from T C P port Id reflect in Command prompt
Windows Bluetooth Wireshark capture with BTVS
macOS

An image of mac O S packet logger Bluetooth capture. It illustrates process, open file tab, click on export and select B T Snoop to export.
macOS packet logger Bluetooth capture
Unlike Windows and Linux, live packet inspection cannot be done. The capture by “packet logger” can be exported to a file in btsnoop mode and inspected by Wireshark. The file extension may need to be manually changed to .pcap post export. The packet logger may truncate the payload portion of the packet if it’s big.
Bluetooth Packet Filtering and Troubleshooting
Wireshark analysis of Bluetooth packets helps understand the communication at a very low level and also helps troubleshoot failure scenarios. The following section discusses some important scenarios where Wireshark may come in handy.
Controller-to-Host Communication
Sometimes, the local Bluetooth host or controller (Bluetooth hardware) may misbehave. Also, if there are interoperability issues with an external controller, for example, a Bluetooth dongle connecting the host through a USB, then Wireshark can be used.

An image of program illustrates communication between Host and controller. Program number 16 depicts; source, controller; Destination, host; Protocol, H C I underscore E V T; length, 10; Info, received command complete.
Host and controller communication
Pairing and Bonding
Pairing is used to authenticate a device and establish a bond by storing it as a known trusted device if the pairing is successful. Pairing normally requires a user to start the pairing process, but it can be done without user intervention also.
Once a device is paired and bonded, an authentication key is generated which is used to encrypt the communication data link. Once paired for subsequent attempts, no user intervention is required to connect two devices.
From a regular channel scan, discover the presence of a device.
SDP sets up an L2CAP encapsulated ACL link as usual and exchanges information to discover device profiles.
- Devices exchange and discover I/O capabilities (have a keyboard, display, etc. or not). Some devices like a Bluetooth mouse and audio headsets do not have any capability to enter a key or display to see any code.
If no I/O, just connect once the user manually triggers a pairing.
If both the devices have a display and key entering capability, the user must enter or acknowledge (yes/no) a displayed key.
If both devices support NFC, instead of manually entering the pairing key information can be learned out of band.

An image illustrates program locates presence of device by regular channel scan. It highlights code, page scan repetition, class of device and reflects Device Name colon P L T Focus.
Regular channel scan: discover the presence of a device

An image illustrates S D P initiates an A C L link over L 2 C A P for Service discovery. Info row in program window indicates several commands to discover services.
Discover services: SDP sets up an L2CAP encapsulated ACL link

An image illustrates Input and output capabilities and pair discovery. It has command window depicts, Command Opcode, Parameter total length, Display Yes or No, Authentication data not present.
Discover I/O capabilities and pair
Paired Device Discovery and Data Transfer
Devices do a link scan, signal strength measurement, etc.
Initiate a role discovery and agree on the master. Exchange the link encryption keys generated during pairing (both sides must have the same key). The key is not encrypted and can be seen as clear text.
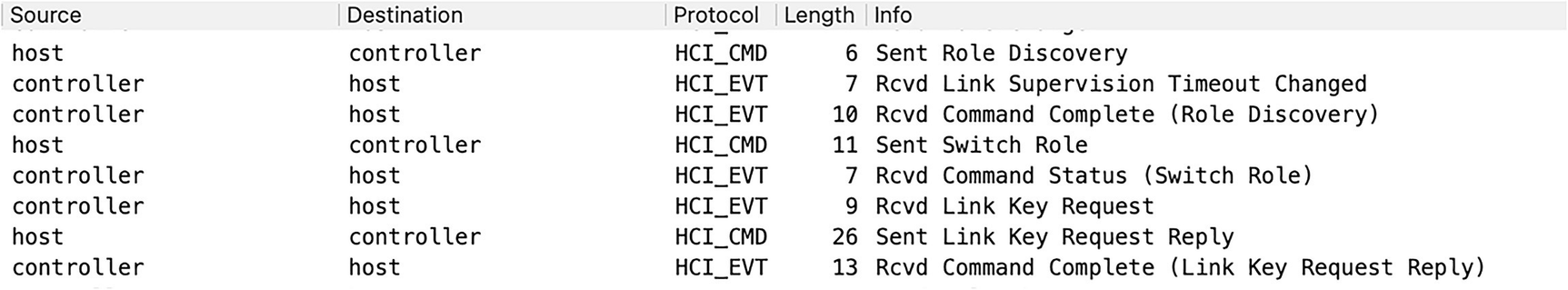
An image of program execution for link scan role discovery and key exchange. Steps reflects in info column; Role discovery; link supervision timeout changed; switch role; command status; Link key request; command complete. Two protocols involved; H C I underscore C M D; H C I underscore E V T.
Link scan role discovery and key exchange
SDP initiates an ACL link over L2CAP for peer service profile and capability discovery.
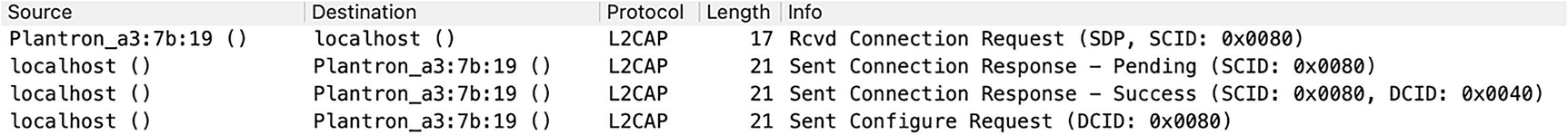
An illustration of connection initiation between S D P and A C L. It consists of L 2 C A P protocol in four steps; Connection Request; Connection Response hyphen Pending; Connection Response hyphen Success; Configure Request.
SDP ACL connection initiation

A program window of S D P service profile discovery. It runs on Session Discovery Protocol and info column respond search requests, Handsfree Audio Gateway, Phonebook Access Server; Audio Source; A forward slash V Remote control Target, A forward slash V Remote control controller, Unknown.
SDP service profile discovery
Based on the profile discovery required, upper layer protocols initiate additional connections for the exchange of configuration parameters.
In our example, the Bluetooth headset is connected to a laptop. So we can see RFCOMM for the configuration setup and AVCTP and AVDTP protocol connections for audio control and data.

A program window of upper layer connection setup. It involves four protocols; H F P; H C I underscore E V T; R F C O M M; L 2 C A P. info column indicates; connection Request and response as pending and success; Configure response hyphen Success and Number of completed packets.
Upper layer connection setup
After the upper layer connections are set up, actual data transfer can be seen. Here in our case, AVDTP is used to transport audio using aptX codec.

Data Transfer over Bluetooth. Program window represents five rows; Source; Destination; Protocol; Length; Info which indicates, Command hyphen start hyphen A C P S E I D, Number of completed packets, apt X.
Data transfer
Summary
Bluetooth standard evolution from versions 1 to 5.3
Overall architecture and protocol stacks of Bluetooth Classic (BR/EDR) and Bluetooth Low Energy (LE)
How to use Wireshark to filter out each protocol type in the protocol stack
Wireshark Bluetooth packet capture and tools used on Linux, Windows, and macOS
How to use Wireshark to understand the complete communication flow starting from device discovery, pairing, service discovery, and data transfer
References for This Chapter
Bluetooth specification: www.bluetooth.com/specifications/specs/
Bluetooth IEEE standard: https://standards.ieee.org/ieee/802.15.1/1180/
Bluetooth Test Platform: https://docs.microsoft.com/en-us/windows-hardware/drivers/bluetooth/testing-btp-tools-btvs?source=recommendations
