10. How Content Governance Will Facilitate Media Company Transformation
“Tweetable Moment: Content governance ensures that there are controls in place so that consistent brand storytelling is told across all channels.”
—#nextmediaco
Red Bull is a media company. They produce compelling content because they are creative, they understand their audience, and they have a well-oiled machine that facilitates the content supply chain within their company—from content ideation, to creation, to approval, and finally to distribution. Because of this, Red Bull has built its brand using social media and has been extremely successful at engaging with customers day in and day out and across all the major social networks. This has made it the model that many brands turn to when looking to become a media company. Red Bull has built a combined social audience of more than 42 million users on Facebook, Twitter, YouTube, Google+, and Instagram, and as you finish reading this sentence, the number has most likely already increased dramatically.
Facebook is Red Bull’s largest audience segment with more than 37 million fans and makes up nearly 90% of its community. This has been a key network for Red Bull, which now currently ranks among Facebook’s top 10 fan pages.
Visually stunning content has contributed to Red Bull’s success on YouTube, where it has cultivated a subscriber audience of two million, and on Instagram, the brand’s smallest but most engaged audience. Twitter is the brand’s most active channel and serves as a vehicle for distributing content from each network to an audience of nearly one million followers.
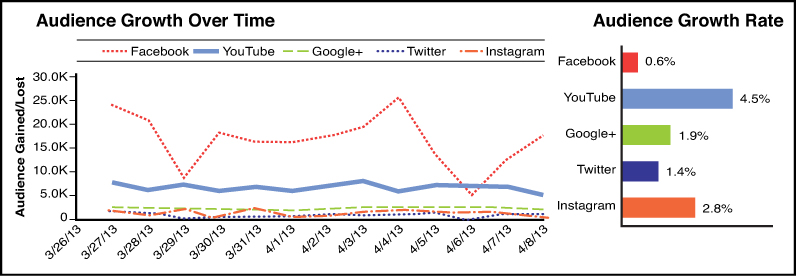
Red Bull’s network of highly engaged audiences are valuable channels for content distribution, and it is growing each one by providing a stellar customer experience coupled with compelling content. Figure 10.1 shows Red Bull’s growth from March to April 2013.
On Facebook, Red Bull added more than 200,000 fans in the same reporting period, according to Kevin Shively, Marketing Analyst for Simply Measured, a leading social media measurement and analytics vendor. Although Facebook accounted for the most new fans, YouTube has been Red Bull’s fastest growing channel, with a 4.5% subscriber growth rate month to month. Red Bull’s YouTube channel was established in 2006, but the brand’s steady stream of professional, highly produced video continues to build its subscriber audience.
Red Bull’s Instagram channel is also growing quickly; during the reporting period, it was the second fastest growing channel with a community growth rate of 2.8%, outpacing longer established channels Twitter and Google+ (see Figure 10.2).
It’s clear that visual content is a major contributor to Red Bull’s success in social media and continues to serve as a model for other brands that want to engage with customers using visual storytelling. Visual content captures our attention, and it’s often what comes to mind when we think about Red Bull and what they do in the marketplace.
What makes Red Bull successful is more than just their brand story or the epic content the company creates each day for the community. Their ability to make this happen is largely because of a content governance plan that controls what type of content is created and when it’s shared within each channel.
Defining Content Governance
Content governance is a strategic imperative when deploying an enterprise-wide content strategy for the purposes of the following:
• establishing content and workflow accountability
• auditing content engagements
• managing risk
• setting content permissions
Every contributor to your brand’s storytelling initiatives, whether employee or customer, has a specific role when it comes to managing the content supply chain. The content workflows that facilitate ideation, creation, approval, and distribution must be built to ensure consistent storytelling across paid, earned, and owned media.
By implementing a content governance framework layered across the entire organization, teams are enabled to collaborate through an approval process with distinct workflow and established audit trails, ensuring the right content is being utilized in the right channel. Audit trails through all processes and actions are an overall best practice for all large and small brands and must be a requirement regardless of what industry you work in. These audit trails should always be referenced for the purposes of displaying content and user action history with corresponding approvals. Documenting a governance hierarchy reduces risks during a crisis and can be used to “lock down” publishing access across all social accounts if certain situations arise.
Content governance can also be defined as a detailed framework of content delivery and management that ensures there are documented controls in place that facilitate consistent brand storytelling across paid, earned, and owned media. A content governance model should include
• Collaboration models for internal teams complete with audit trails
• An approval workflow for proactive content (unplanned and planned content)
• An escalation workflow for reactive content (crisis, customer support)
• Workflows that mitigate risks, such as access to social properties, employees leaving the company, accidental messages being sent, and so on
• Processes to handle rogue accounts and the creation of new branded accounts
• Enterprise-wide, single-point password control systems
• Establishing user roles within a content strategy (contributor, approver, publisher, administrator), which is discussed in Chapter 11, “Structuring Your Teams to Become a Content Driven Organization”
It might be easy to confuse content governance with a social media policy. Usually, content governance is a subset of a larger policy but it can certainly stand alone within an editorial team or department. A social media policy (sometimes referred to as social media guidelines) is a corporate code of conduct that provides guidance for employees who post content on the Internet or engage with external customers either as part of their specific job functions or just as employees. My book Smart Business, Social Business walks readers through the process of creating a policy, step by step.
Content governance is just as important as it ensures that there are controls in place that govern when, what, and why content is being created, approved, and distributed. It’s a strategic imperative that enables a brand to tell a consistent story across all forms of media.
The first step at deploying content governance is to build a collaboration model that helps facilitate internal communications, integration, and best practice sharing between all of your internal stakeholders.
Building a collaboration infrastructure is important to ensure consistency and that everyone involved in the content supply chain understands the business and marketing goals and proactively shares knowledge. This is more than just a conference call. It must be a collaborative, ongoing working session and a place where new ideas are welcomed with open arms.
Building an Effective Collaboration Model
Collaboration is a working practice whereby teams and individuals work together for a common purpose to achieve positive business outcomes—in this case, the journey to become a media company. Collaboration is based on the concept that sharing knowledge through cooperation helps solve business or marketing problems more efficiently. In the enterprise, this principle couldn’t be truer; especially as more and more employees engage with one another through asynchronous, real-time technology platforms such as Yammer or Chatter.
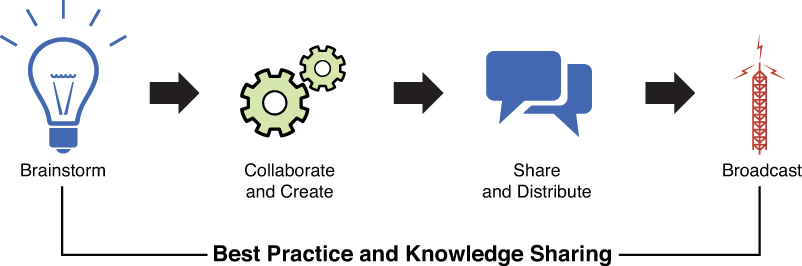
Charles Darwin, an English Naturalist in the 1800s said, “In the long history of humankind, those who learned to collaborate and improvise most effectively have prevailed.” And if you think about this and apply it to your content strategy, it makes perfect sense. If you can tap into the collective knowledge and brainpower of others on your team, the positive business outcome will be the production of better content, smarter marketing, and more effective customer relationships. Figure 10.3 is one way to look at a collaboration framework.
Collaboration models can be complex and detailed. It is simplified here so that you can easily adapt it to make it work in your organization. The elements that make up this framework are
• Brainstorming: All stakeholders meet periodically (daily, weekly, monthly) to discuss content with high engagement numbers, as well as content that might integrate with current marketing campaigns or other initiatives. This meeting can also serve as the daily gathering of the creative newsroom team to identify trending topics in the news cycle and determine whether or not there is an opportunity to capitalize on it.
• Collaborating and Creating: Stakeholders work together to create, co-create, aggregate, and curate content from third-party sites. Again, this could be a situation where the team is creating content in real-time or be more of a longer-term content planning cycle.
• Sharing and Distributing: Content and editorial teams share content direction, assets, and general strategy with brand, product, or regional teams. Content can be housed in a content library for easy consumption and sharing or placed into a content platform such as Sprinklr, Spredfast, or Kapost for dynamic delivery to stakeholders.
• Broadcasting: Content teams publish content and provide strategic counsel to regional teams. Regional teams localize and publish content within their social media channels.
There are also several technologies in the market place that can help facilitate collaboration whether you work for a large organization or small business. If you work for a large company, most likely you may have access to some of these tools. If not, you will have to invest in a platform that can help you achieve better collaboration with your teams.
Yammer is probably the most well-known internal collaboration platform for small to medium-sized businesses. With Microsoft’s recent acquisition of its platform, Yammer now stands to compete with other enterprise-level collaboration systems.
At a high level, Yammer is a social network that’s entirely focused on your business. For you to join the Yammer network, you must have a working email address from your company’s domain. You can also create external networks to allow for non-employees, such as suppliers and customers, to communicate with your company. Yammer allows you to share and discuss documents, images, videos, and presentations with your coworkers. It also enables you to upload new versions of files to ensure everyone sees the latest draft and maintain older versions as well.
You can also work with a team to create, edit, and publish content; you can display team goals, compile notes, and draft documents together online, viewing character-by-character changes in real time as others make edits. Finally, you can stay on top of activity from across your company as it happens—discover newly created documents, new members of your groups, recently shared images, active discussions, and activity taking place in other business applications. Other platforms that offer similar capabilities to Yammer are VMware’s Social Cast, Jive, IBM Connections, and Salesforce’s Chatter. Following are a few other collaboration platforms that you might not have heard of:
• Co-op is a free application with a simple user interface similar to Twitter. The features allow you to post updates, ask questions, share links, and track time. Co-op also enables you share your daily agenda with your coworkers so everyone knows what projects that you are currently working on. Their web application automatically stores records of you and your team’s activity, allowing you to review what your team has accomplished each day.
• Cynapse’s Cyn is an open source community and has a complete collection of enterprise-grade collaboration tools. Three versions of their platform are available:
• The free community edition includes Active Directory integration, application source code, web-based appliance management console, and more.
• The other editions sell for several thousand dollars a year and have features such as wikis, blogs, file repositories, event calendars, discussion boards, image galleries, collaboration spaces, status logs, people directory, crowd rating and voting, and more.
• CubeTree, recently acquired by SuccessFactors, is an on-demand enterprise collaboration suite available in free and premium versions. The free version includes user profiles, micro-blogging, file sharing, wikis, and 10MB of storage per user. Their standard features include the above as well as status updates of 140 characters; a commenting feature (similar to that of Facebook’s); feed filtering, which lets you choose who to follow and what feed items you’d like to receive; direct addressing (similar to Twitter’s @name function); and open APIs that allow for the integration with several third-party systems and applications.
• Hashwork is a simple internal social network for small- to medium-sized businesses. It doesn’t require a company administrator, and it’s as easy as entering a company email address to sign up and get access. The user interface and functionality is similar to Twitter with features like 140-character posts, direct addressing, groups, hashtags, and so on. You can get more robust features with paid versions of their application.
The second step for building a content governance framework is creating workflows for planned and unplanned content, which is discussed in the next section.
Proactive Content Workflows for Planned and Unplanned Content
The ability to control content is imperative to becoming a media company. Having controls in place helps deliver content that’s integrated, and it also ensures that the content shared externally is aligned with your brand’s storytelling narrative. There are two sets of workflows you should consider as you build your content governance model: proactive workflows and reactive workflows. The good news is that many of the Content Management Systems (CMS) mentioned in this book allow you to build and customize these workflows. Figure 10.4 is an example workflow for proactive (planned) content creation.
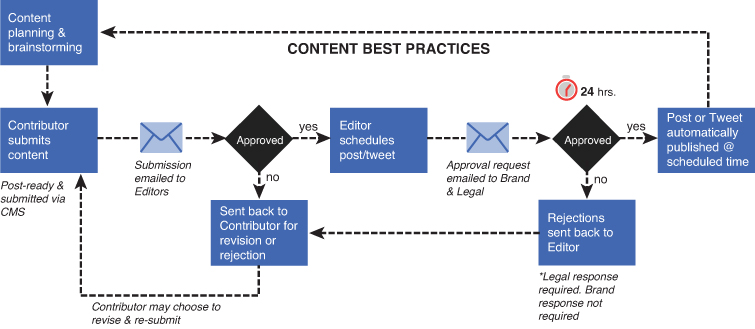
Figure 10.4 Example proactive workflow for planned content ©Edelman Digital. Used with permission from Daniel J. Edelman, Inc.
The foundation of this workflow starts at the beginning with content planning. As discussed in Chapter 3, “Establishing a Centralized ‘Editorial’ Social Business Center of Excellence,” your Social Business CoE (or centralized editorial team) is responsible for driving the content strategy and facilitating your content planning sessions. This can be done daily, weekly, biweekly, or monthly. It depends on how far out you are building your editorial calendars. Many of the topics discussed at these meetings include brainstorming content topics or themes, assigning content to various contributors, discussing historical content performance, sharing best practices, and trendspotting.
The next phase in the workflow is when the contributor submits the content for approval. This can be done via email or a CMS that has this built-in capability. After the editor is notified that there is content submitted, he or she approves the content or sends it back for revision. If approved, the editor can schedule it to be published or add it directly to the editorial calendar for the next round of approval. If not approved, the editor sends it back for revision or rejection. At that point, the contributor can choose to revise the content and resubmit it for approval.
The next phase of this workflow comes after the editor approves the content. The editor then sends the content to be approved by your brand or legal team. If approved, the content will go live at the day and time the editor scheduled it. If not approved, the content gets sent back to the editor for revision.
There are a couple of things you should remember when designing your content workflows. First, content approvals can be sequential or simultaneous. With a simultaneous approval workflow, when the content is submitted for approval, it goes to all the approvers at the same time. Each approver can “approve” or “reject” the content, and then it is sent back to the contributor. With the sequential approval workflow, the content goes through each approver in order: editor, brand, legal. In this case, for example, the legal team would not be notified that they need to approve the content until after it’s approved by the editor and the brand team.
What you find in this process is that there will always be bottlenecks in the content approval process. And based on my experience, that usually happens with the legal team. What you might want to do is build a workflow that gives each approver a certain amount of time (say, 24 hours) to approve content before it goes live. In other words, if legal does not approve the content within the allocated time, the content goes live automatically. This approach ensures that any and all approvers are held accountable in this workflow.
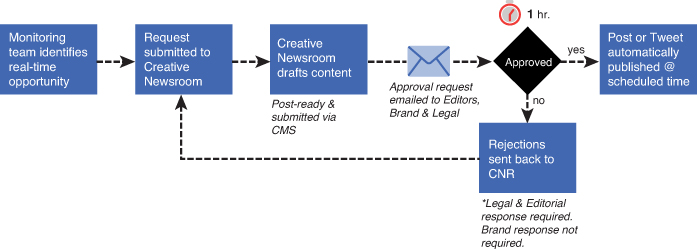
Having a 24-hour approval process is “nice to have” especially if you work for a large organization, but 24 hours is way too long to take to capitalize on real-time marketing. Chapter 9, “The Role of Converged Media in Your Content Strategy,” discussed Edelman’s Creative Newsroom, which is a real-time content marketing approach that can help you transform a trending conversation into a brand-relevant piece of content that resonates with your audience in hours instead of days. Figure 10.5 is an example workflow in the Creative Newsroom.
In this workflow, a community manager or monitoring team identifies a real-time opportunity to insert your brand into a trending conversation. As discussed in the last chapter, there are several tools in the marketplace today that can surface real-time trending data: the Dachis Group’s Real-time Marketing Dashboard, SocialFlow, Trendspotter, and Rt.ly. When the content is spotted, you must determine whether your brand has license to actually talk about it (that is, it’s somewhat relevant to your brand and what it stands for).
After the trend is spotted, it then kicks the Creative Newsroom operation in gear to start creating the content. Copywriters and designers are then deployed to create a piece of visual content and then submit it to the approvers. In this case, it can be the editor and brand and legal team, sequentially or simultaneously. The main difference between this workflow and the previous one is the approval time. For real-time marketing to actually be in real time, approval cycles should be no more than one hour. This is certainly much easier said than done, but if you can establish a level of trust with the approvers, specifically brand and legal, eventually you can work your way to under an hour approval time.
As much as proactive content workflows are important to your media company transformation, you must also be prepared to be reactive and respond to issues when they arise.
Reactive Escalation Workflows and Risk Assessment
As with most content marketing and community management initiatives, there is always the possibility of running into disgruntled customers or even a potential crisis. It will happen, and these issues cannot be ignored. Having a crisis escalation plan is important to ensure that all content contributors, community managers, and customer support teams understand the process if they have to escalate conversations and to whom they should escalate them.
Escalation workflows are nothing new. Back in 2008 (yes, five years ago), the United States Air Force created and made public their Web Posting Response Assessment. It’s a 12-point plan developed by the Emerging Technology Division of the U.S. Air Force’s Affairs Agency that illustrates how U.S. Airmen should respond to social media conversations online. The plan provided a specific workflow that Airmen should use when responding and engaging with the public. It was created in response to negative opinions about the U.S. government and also to bolster support and credibility for content that was positive about the Air Force.
Figure 10.6 is an example of escalation workflow that takes into consideration when you should respond to a compliment, complaint, or potential crisis.
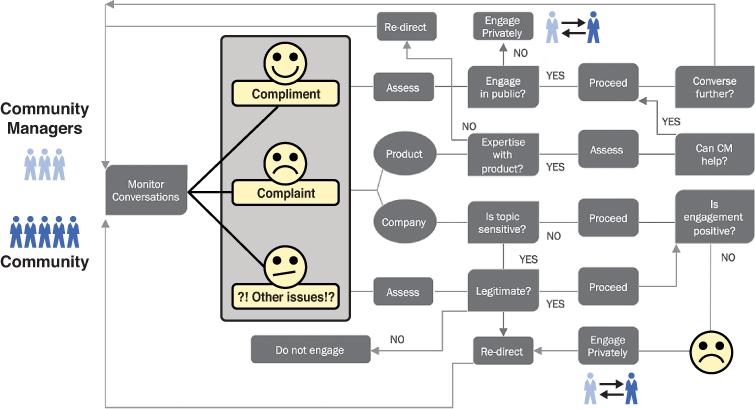
Figure 10.6 An example of reactive escalation workflow ©Edelman Digital. Used with permission from Daniel J. Edelman, Inc.
This might seem complicated at first glance, but after you go through the process of putting the workflow together and identify the right teams to be involved, it will become second nature when it’s time to put it into action.
As you are building these workflows, it’s important to also create a risk assessment guide so when your team members are engaging externally, they can be smart when they identify and flag potential risks. The simplest way to do this is to create a green, yellow, and red flag assessment guide.
Similar to traffic stop lights, green symbolizes that the conversation is good to go and that community managers can respond without escalation. Yellow means to “proceed with caution,” and careful consideration should be made when responding and/or escalating. Red means to stop what you are doing and force teams to meet and decide what the appropriate next steps will be. Following is a break down of potential topics that would fall into each of these flag categories.
Green flag issues include questions about
• New account setup
• Account management
• Positive brand experiences and praise
• Career opportunities
• Company information
• Partner information
• Innovation requests and ideas
Potential Crisis
• Negative blog/media mentions about your brand
• Negative mentions from celebrities of influencers
• Negative mentions from employees (previous or current)
• Critical feedback about products and/or services
• Negative feedback or criticism about a current marketing campaign
Customer Support
• Product or transaction requests
• Dispute resolution regarding customer orders
• IT-related issues or website errors
Last red flag issues include
Potential Crisis
• Hacking claims or account security-related issues
• Legal threats
• Suicide or criminal threats
• Negative news articles mentioning your brand
• Key sensitive topics
Customer Support
• Customer service complaints
• Major account issues (shipping, transaction, order not received)
• Fraud complaints
Although some of these issues might not be relevant to your brand, you should go through this exercise and categorize each of these issues accordingly. This helps you train your team to be able to engage with customers, identify potential issues, and escalate accordingly.
Governing New “Brand” Account Creation
As mentioned in Chapter 2, “Defining Social Business Strategy and Planning,” the “bright and shiny” object of social media has caused a craze in many companies today and quite possibly yours, whereby hundreds of siloed teams create social media channels resulting in poor integration, disjointed content, and lackluster community management practices. And if you are the person who is driving this organizational change, you have to audit and potentially close down certain social media channels for a variety of reasons:
• Community is abandoned; no one is posting content.
• Content strategy doesn’t align with the brand.
• Community was created around a product that does not exist anymore.
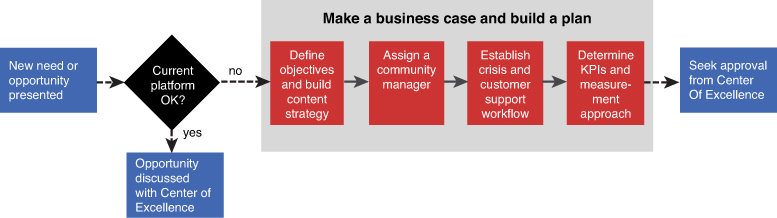
Hundreds of other reasons for consolidating or shutting down existing social media channels can exist, so you must create a process that prevents these things from happening in the future. Figure 10.7 is an example of a process that governs new brand account creation.
Usually in a situation like this, a specific marketing (or regional) team identifies a need to create a new social media channel. There could be a variety of reasons for this request. Perhaps the company is launching a new product. Perhaps the company is expanding into new geographical territories, or maybe there is a huge event happening that you are sponsoring.
The first step in this process is to evaluate whether or not an existing channel can be used to support the initiative. In some cases, it will, and in other cases, it won’t. When you evaluate specific requests, each one should be carefully considered before making a decision. The good news about using Facebook as a part of your content strategy is the launch of Global Pages, which helps address this issue head on.
Instead of a single Facebook page in the specific language that it was originally created, Global Pages now have the benefit of both global and regional content. In essence, it’s one page with one URL, for example, Facebook.com/YourBrand. Instead of users searching for your brand by country and in the language they prefer to read, they will only have one option to Like your page.
With the new Global Pages structure, you can create localized versions of your cover and profile photos, apps, milestones, and “about” info and provide locally relevant and regionally specific content to your community in the their news feeds. An English version’s cover photo might say “Hello,” but users visiting from Italy would see a different version welcoming them with a “Ciao!”
Your Facebook administrators can set up local versions for different single or multi-country language regions, plus a default for everyone else. A single, global URL dynamically directs users to the appropriate local version. This can help consolidate workflow, content creation, and analytics and at the same time, provide a seamless experience for your customers. So in the case of launching a new Facebook page for a region, you can potentially leverage the new Global Pages feature. In some cases, there is certainly an opportunity to create a new channel. However, you must ensure that the teams that want a new channel have the following documented and well planned out before they move forward to create one:
• Content narrative: What are the goals, and do they have a content narrative that is consistent with the brand’s storytelling objectives? Do they have content themes/categories and a documented editorial calendar?
• Community manager: To prevent communities from going stale and customers from falling “out of love” with your brand, there must be community managers who are not only responsible for creating content, but also responding to the community when necessary. They are the face of the brand, and they should advocate on behalf of them.
• Moderation and escalation policy: This chapter is all about governance, so it’s possible that new teams requesting a new channel will adopt many of the governance models you create as a part of the CoE. However, part of that model should include identifying the proper “regional” resources for escalating customer support issues or handling crises.
• Measurement framework: Before launching a new channel, the teams should have a solid understanding of how they are going to measure success and determine KPIs.
When the internal teams have their plans of action documented, the final step in this process is to seek approval for the Center of Excellence.
Managing the Security of Social Media Passwords
2013 has certainly been the year of “social media password” challenges. And although this is amusing to watch and read about from the outside looking in, it can cost you your job if it happens to your company. Two significant incidents happened this year, one at HMV and one at Burger King, each making it clear why carefully managing your passwords is a huge deal.
HMV is a British entertainment retail company located in the United Kingdom. In January, employees fired by HMV decided to get even by live tweeting their “mass execution” on the company’s official Twitter account, which at the time, had almost 64,000 followers. According to the Independent, HMV attempted to delete the posts from the @hmvtweets account, but it was too late. The tweets had already been copied on screen shots and widely distributed across the social web via retweets and blog posts.
One rogue employee tweeted: “We’re tweeting live from HR where we’re all being fired! Exciting!!” Another tweet, apparently from an iPhone, reported “60 of us being fired at once.” A subsequent posting read: “Just overheard our Marketing Director (he’s staying, folks) ask ‘How do I shut down Twitter?’” The fiasco lasted about 20 minutes before the company removed the tweets, which began trending with the hashtag, #HMVXFactorFiring. Later on, more tweets appeared, apparently from a different member of HMV personnel, referring to the earlier comments.
In this situation, several HMV employees had access to post directly to the brand’s social media channel. Unfortunately, they didn’t have a content governance model to prevent this from happening.
In Burger King’s case, they faced an entirely different challenge.
In February, the Huffington Post reported that someone apparently hacked Burger King’s Twitter account and changed its photo to the McDonald’s logo and name to “McDonalds.” During a series of tweets rife with poor grammar, the hacker claimed Burger King was sold to McDonald’s and then posted a host of other raunchy messages. The account’s bio was also changed to:
“Just got sold to McDonalds because the whopper flopped =[ FREDOM IS FAILURE.”
The perpetrator referenced several Internet hacker groups, including LulzSec, Anonymous, and DFNTSC. About an hour after the unruly tweets began, the fast food chain’s Twitter account was suspended. It was reported that Burger King reached out to Twitter to have the account frozen.
What happened to Burger King, and then a day later to Jeep, is every marketer’s nightmare. Bu they weren’t alone. Other prominent accounts have fallen victim to hacking, including those for NBC News, USA Today, Donald J. Trump, the Westboro Baptist Church, and even the “hacktivist” group Anonymous.
So what does this mean for you?
These specific situations should raise question marks about the security of your social media passwords and the ease of gaining access to your branded accounts. The good news is that Twitter launched a new login verification feature in May 2013. The new login verification levels-up the account security, preventing the possibility of email phishing schemes, as well as breaching of passwords. With the login verification enabled, your existing applications continue to work without disruption.
Both Twitter and Facebook have begun introducing a number of paid advertising options, raising the stakes for advertisers. Brands that pay to advertise on Twitter are assigned a sales representative to help them manage their accounts, but they are not given any more layers of security than those for a typical user.
One way to minimize your risk is to deploy the content workflows mentioned previously. Doing so provides two layers of security. If you have invested in a content publishing platform, users are given login credentials to the system, not the social network itself. Second, if you build your workflows correctly, content has to go through a series of approvals before it becomes public.
Of course, if your community manager is terminated for some reason, that’s a completely different story. In that case, you need to ensure that you are in constant communication with Human Resources. You might even consider them to be a member of the CoE.
You should also look into investing in password management software. This type of software can help you create unhackable passwords, secure them, and log in to your accounts automatically without having to memorize them or write them down. Every single day in the media, we hear of a large number of accounts being hacked, from online banking to social media and email accounts. Password management software can help you avoid the risk of people stealing your login info, accessing your accounts, and posting objectionable content. Not only is this bad for your brand but if hackers can get into your Twitter account, what’s stopping them from accessing your work email account or bank information?
The way password software works is simple. You basically secure your login information into a platform and automatically log in to any of your accounts through the software or a browser button add-on. With a portable version of your software installed on a USB drive, you can use it to view and log in to your accounts on other computers. Many of these platforms also provide sync-able versions for smartphones.
One of the reasons accounts are easily hacked is that many people have a hard time remembering their passwords, so they use common words like their last name, family name, kid’s date of birth, their own date of birth, Social Security numbers, or sometimes they even use “password” as their password. To escalate the problem, they might also use the same password for numerous accounts. Password software can help you create complex passwords, store them in a database for you and use them to log you in to your accounts quickly and easily. All passwords are encrypted and locked behind a single master password that only you know.
Beyond the security benefits of using this type of software, it also helps you stay organized by storing all of you password details in one, secure place. Many applications also provide mobile tools so that you can take your secure passwords with you, especially if you are mobile worker or use multiple computers.
Here are some basic criteria you can use when you are evaluating password management software:
• Basic management: The best password software platforms can automatically create accounts as you log in to websites and automatically log you into a group of your favorite accounts simultaneously. Other tools include auto-filling long forms and templates for popular account types.
• Security: Because password software can store your login information and account numbers all in one place, security is critical in this situation. The best applications encrypt your files using 256-bit (or higher) encryption protocols, generate complex passwords, and protect you from keylogging and phishing attempts. Keylogging is the practice of using a software program to record all keystrokes on a computer keyboard. Phishing is a scam to try and obtain financial or other confidential information by sending an e-mail that looks as if it is from a legitimate company, usually a bank, but contains a link to a fake website that looks just like the real one.
• Mobile capabilities: Many employees use smartphones and tablets to log in to their online and social media accounts. Some password programs have mobile versions of their software that operate independently, or in conjunction with the PC or Mac.
Most password management tools offer many of the same features. Useful features to look out for include
• Centralized deployment where one administrator has complete control over accessibility to specific social media channels such as a blog, Twitter or Facebook accounts, and for how long. Easy to update when someone joins the company, leaves the company, or is assigned to a new role.
• Shared password data on a person-by-person basis or for teams, departments, or regions within a company.
• Options to hide a password from an employee while still allowing access to a brand’s social media channels via auto-fill functions.
• Generation of secure, unhackable passwords and an option to replace old passwords with unique, randomly generated ones.
• Password data stored and encrypted online, allowing secure access to passwords when on the go via mobile devices.
• One-time passwords are useful if using an untrusted shared computer.
Vendor Spotlight—Spredfast
Governing your brand’s social activity requires a great deal of organization across people, accounts and content, as well as the need to uphold your company brand standards. Spredfast, a social media management system provider, helps brands organize and orchestrate social media, specifically content, to facilitate the ideal interactions between brands and their communities.
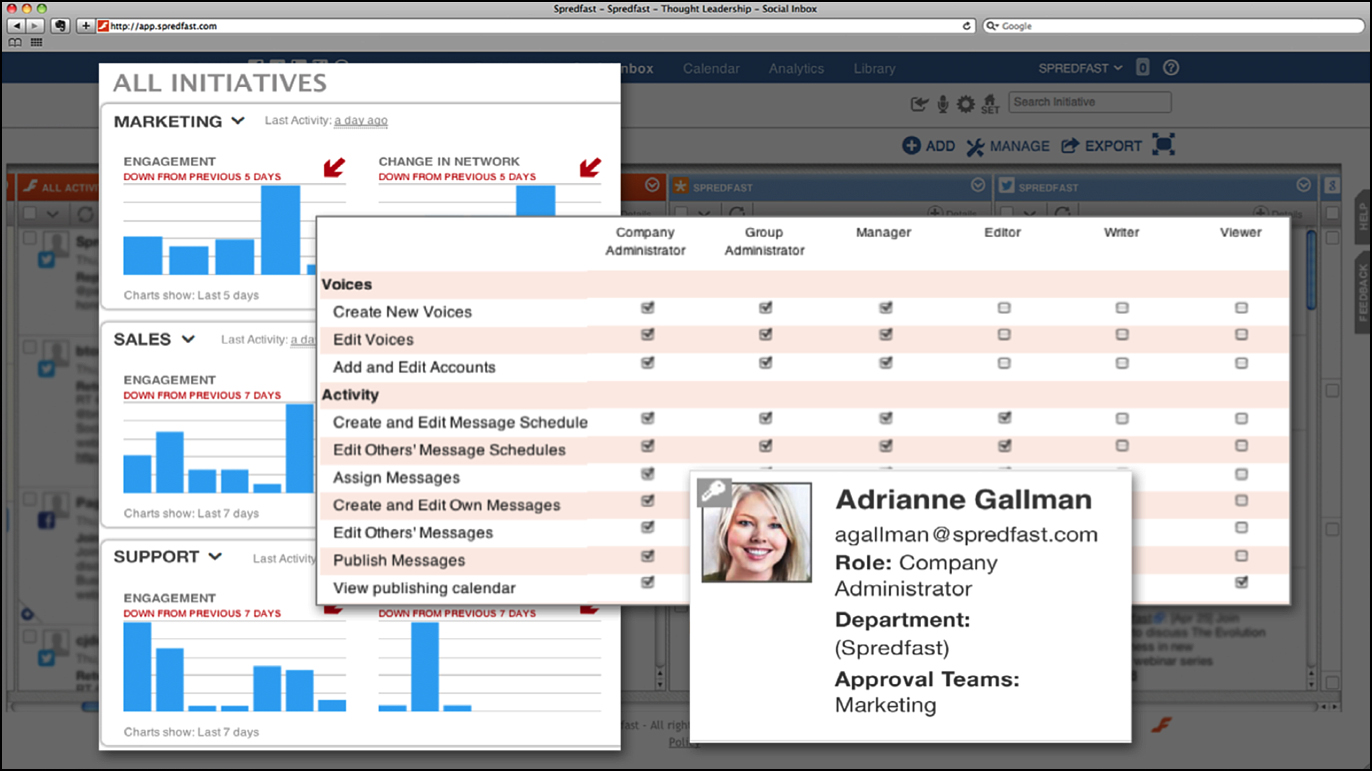
Each company has its own unique structure and guidelines. As shown in Figure 10.8, Spredfast can adapt to organizations of all sizes and structures by managing all groups and social accounts in a single location. Each department can be self-sufficient in governing its own social programs and accounts by authenticating social accounts across networks such as Facebook, Twitter, LinkedIn, Google+, and blogs from one centralized location. Content contributors can be assigned roles and manage complex user permissions so the right people have access to create content and engage with the right audiences.
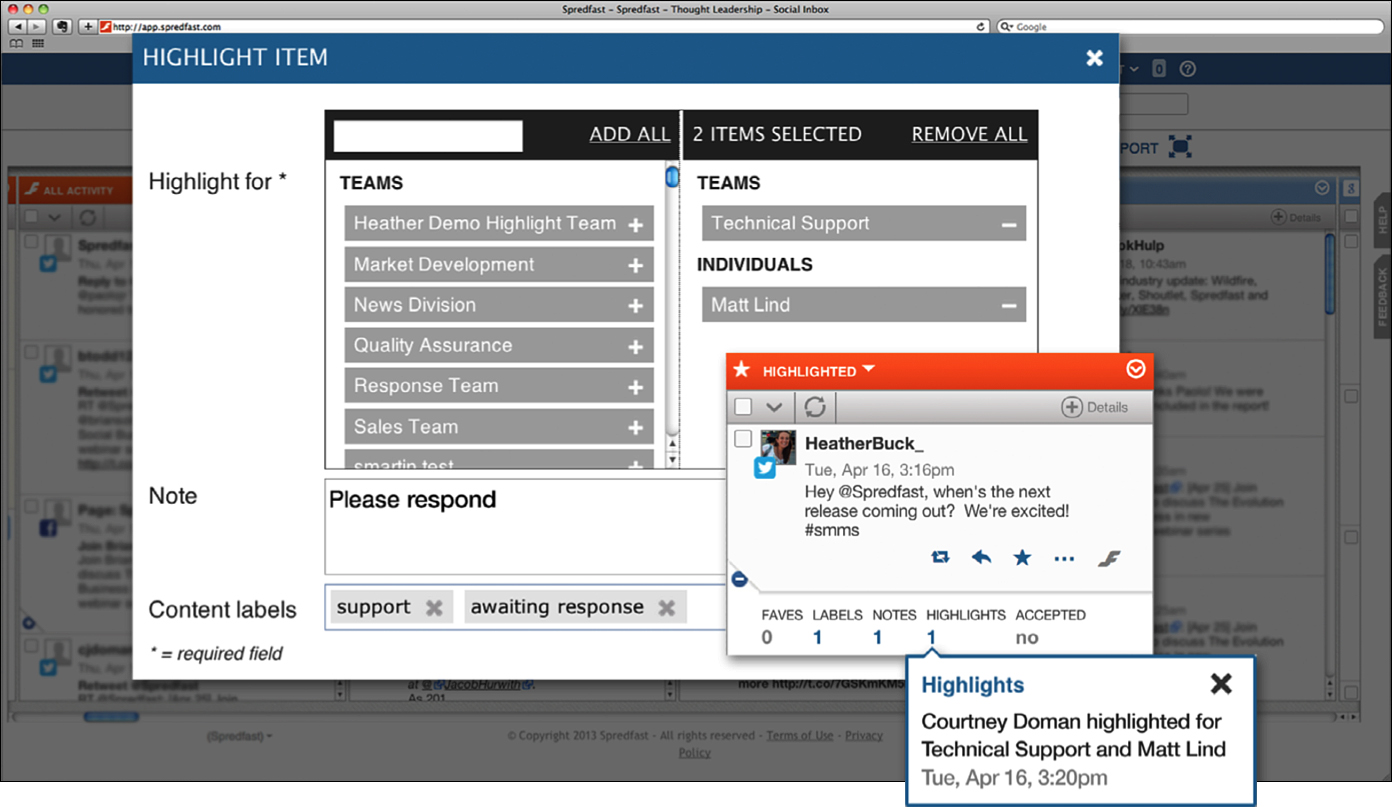
Spredfast can also help you collaborate so that workflows and approvals help teams engage productively. As shown in Figure 10.9, teams can highlight activity proactively to share with contributors for reference or assign activity reactively to entire teams based on response needs. This collaboration replaces long email threads with system notifications and workflow automation within Spredfast to provide visibility across the team of what’s been assigned, what needs prioritized attention, and what actions have been taken with visible audit trails.
Planned content can be organized and created across a team editorial calendar, with contributors having the ability to use preapproved content from the Spredfast Content Library. Content types and accounts with specific approval needs can be auto-routed based on user, account, or content type to ensure the proper oversight and approvals are in place before being publically published. All content published within Spredfast is archived so that teams can reference all historic activity, conversation histories, approvals, and audit trails at any point in time.
Spredfast protects the security and safety of brands by equipping administrators with the power to manage accounts, passwords, and user roles from within the platform. Content contributors are given access to engage directly within Spredfast rather than have direct access to the many passwords needed to access company social media accounts. For companies in regulated industries or those with additional security needs, Spredfast offers enhanced password management functionality, Single Sign-On, and IP restrictions.
Following are two Spredfast customers who use their tool for varying levels of governance:
• Whole Foods Market (Workflow, Processes, and Orchestration): In addition to maintaining globally managed presences on Facebook, Twitter, and Pinterest (among other social networks), Whole Foods enables over 2,500 employees at its 340+ stores to provide relevant, local, and timely content to their communities. This allows each region to share its own local flavor while preserving brand integrity (see Figure 10.10).
• AARP (Organization and Structure): There is no one right way to organize your social presence. A few common configurations include organizing by business unit, geographical location, or product offering. AARP blends corporate, business objective-focused accounts with state-level accounts to provide relevant local information to members of the nonprofit organization geared toward serving people 50+ (see Figure 10.11).