Chapter 3
Handling Computer Hardware
Learning Outcomes
After reading this chapter, you will be able to understand the following:
The importance of being able to recognize different types of computer hardware;
The various disk drive interfaces that an investigator can encounter;
The types of devices used to forensically extract data from different storage devices;
The variety of storage media used and how this evidence should be handled and analyzed; and
The use of storage media in actual investigations.
As an aspiring computer forensics investigator, you should develop an understanding of computer hardware, for several reasons. The first reason is that certain types of systems and hardware will only support certain types of software, in terms of operating system, file system, and applications. For example, it is important to understand that an Intel-based Macintosh computer can support macOS and its related APFS or HFS+ file system and that same computer can also support a Windows operating system and related NTFS file system when Boot Camp is running. Boot Camp is a utility that is included with macOS that enables a user to run a Windows operating system on an Intel-based Mac.
Being cognizant of the diversity of computer hardware is also necessary because you need to know how systems can be connected to external devices, like routers or external hard drives. These connected devices, like routers, will often contain digital evidence and may need to be seized if a warrant permits. The investigator might also need to be able to reconstruct the computer and its devices when she returns to the laboratory.
Computer hardware, operating system(s), and applications also determine the kind of computer forensics tools necessary to acquire evidence from that system. For example, BlackLight software might be better suited to image (a strategy you learn about later in this chapter) a MacBook Pro running macOS, while Guidance Software’s EnCase can be used to image a computer running Windows. Knowing that a computer is running Windows may not always be enough, however, because the version of the operating system may influence an investigator’s decision regarding the type of forensic software to use. Additionally, the type of investigation determines the value of different types of evidence and guides the investigator to choose the most appropriate forensic tool. For example, in a case against an alleged sex offender, a computer forensics investigator might choose to use X-Ways Forensics, which has a particularly effective filtering feature for searching images for skin tones. Realistically, though, many local police departments simply do not have the budget to purchase the full array of forensic tools and thus do not have the luxury of selecting the most appropriate tool. Moreover, even if they could purchase some of these tools, they do not have the training budget to support their usage.
Proper planning for an investigation is critical. This entails knowing about different computer hardware, like hard drives and other devices, in order to purchase the appropriate equipment. As you will learn in this chapter, many of the connections and related forensic hardware cannot be purchased at a local Staples stationary store if you need something; much of the forensic hardware is specialized and is only available from a very limited number of suppliers.
Finally, the way in which computer hardware is handled, during an investigation, has legal ramifications. Evidence must be seized and handled in accordance with standard operating procedures that follow the law in that jurisdiction. Ultimately, the process by which you acquired the evidence is just as important as the evidence itself.
Hard Disk Drives
In Chapter 2, “Windows Operating and File Systems”, we discuss the components of a computer’s hard disk drive and also describe how files are physically saved and retrieved. It is, however, necessary now to discuss the various types of hard disk drive interfaces that a computer forensics investigation will encounter.
Small Computer System Interface (SCSI)
Small Computer System Interface (SCSI) is a protocol for both the physical connection of devices and the transfer of data. SCSI devices can include hard disks, tape drives, scanners, and CD drives. It is important to understand that SCSI also refers to a command protocol. Larry Boucher is credited with much of the SCSI development and advances, which began at Shugart Associates. It was developed as a vendor-neutral protocol for devices and therefore enabled the same device to work on either a personal computer or on an Apple Macintosh computer. SCSI devices can also be connected to UNIX systems. The benefits of using SCSI are not limited to its compatibility with various systems; it also enables high rates of data transfer. Another tremendous advantage introduced with SCSI is that several devices can be connected in a chain to a single SCSI port.
Forensic Investigations Involving SCSI
From an investigator’s point of view, it is important to understand that there are still computers that utilize devices with SCSI connectors (see Figure 3.1). Therefore, you may need older systems in your lab to operate these devices, and you must also think about the relevant drivers that will need to be installed. SCSI hard disk interfaces are uncommon today. However, there are still forensic imaging devices that can be used with SCSI hard disks. For example, the RoadMASSter 3 Mobile Computer Forensics Data Acquisition and Analysis Lab is a system that supports the SCSI interface.

Figure 3.1 SCSI connector
Integrated Drive Electronics (IDE)
Integrated Drive Electronics (IDE) is a drive interface, connector, and controller, which is largely based on IBM PC standards, for devices like hard disk drives, tape drives, and optical drives. The disk (or drive) controller is built into the drive itself. The disk controller facilitates communication between a computer’s central processing unit (CPU) and hard disks (or other disk drives). See Figure 3.2.
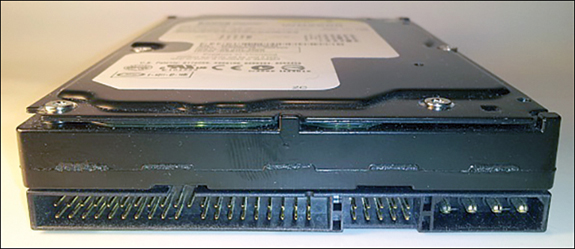
Figure 3.2 IDE interface on a hard disk
The IDE interface was developed by Western Digital, and IDE drives were first installed in Compaq computers in 1986. This initial version of IDE can be referred to as ATA/ATAPI (Advanced Technology Attachment with Packet Interface). IDE and EIDE have been retrospectively called Parallel ATA or PATA.
Western Digital later introduced Enhanced IDE (EIDE) in 1994. IDE and EIDE connectors typically have 40 pins, although there are 80-pin versions, and the cable is generally 3.5 inches wide (see Figure 3.3).

Figure 3.3 IDE 40-pin connector
Serial ATA (SATA)
Serial ATA is an interface that connects devices like hard disk drives to host bus adapters. SATA provides higher data transfer rates than Parallel ATA (PATA). SATA was introduced to the market in 2003 and largely replaced EIDE devices. A SATA drive is generally the most common hard disk drive interface that an investigator will encounter, whether it is a desktop or a laptop, or an iMac or a MacBook. Figure 3.4 shows a SATA data cable for desktop, server, and laptop computers.

Figure 3.4 SATA data cable
The SATA power cable is a wider, 15-pin connector, distinguished by red and black wires (see Figure 3.5).

Figure 3.5 SATA power cable
In some investigations, an investigator may come into contact with eSATA connections. Therefore, eSATA connectors should also be a part of the computer forensic investigator’s toolbox. eSATA is a variation of SATA that is used for external drives. See Figure 3.6.

Figure 3.6 eSATA connector
SATA disk drives come in different sizes. For example, Figure 3.7 displays a 1.8-inch hard drive. There are significantly smaller hard drives found in Dell D420 and Dell 430 laptops. Toshiba manufactures these hard drives for Dell. The significance for an investigator is that the ZIF cable (see Figure 3.8) and adapter are very specialized and can be difficult to source.

Figure 3.7 1.8-inch Hitachi hard disk drive

Figure 3.8 ZIF cable
Cloning a PATA or SATA Hard Disk
There are two processes used by computer forensics examiners for making a bit-for-bit copy of a hard drive:
A disk clone is an exact copy of a hard drive and can be used as a backup for a hard drive because it is bootable just like the original.
A disk image is a file or a group of files that contain bit-for-bit copies of a hard drive but cannot be used for booting a computer or for other operations.
The image files can also be different because they can be compressed, unlike a disk clone, which is not compressed. When cloning, the bit-for-bit copy is transferred to a second hard drive that is of equal size or larger than the source drive. Another difference is that specialized software, like EnCase, X-Ways, or FTK, is needed to view the contents of the image files. In general, image-viewing software is read-only, and files cannot be added. Nevertheless, some applications allow image files to be edited; WinHex, which is produced by X-Ways Forensics, is one such example.
Cloning Devices
The process of cloning a hard drive is a faster process than imaging a hard drive. The time difference between the two processes is substantial. Therefore, when a computer forensics examiner is working undercover or perhaps needs to obtain a copy of a hard drive and leave the computer with the custodian, then cloning the drive is more practical. On average, successfully cloning a SATA drive takes less than an hour. Of course, the time to clone depends on the size of the source hard drive and the cloning equipment being used.
One forensic cloning device used in investigation is the Disk Jockey PRO Forensic Edition (see Figure 3.9). The device is write-protected and allows the user to copy directly from a SATA or IDE hard disk drive to another SATA or IDE hard disk drive. Write-protected refers to the fact that it can copy the device storage without writing to the drive or volume.

Figure 3.9 Disk Jockey PRO Forensic Edition
Before the investigation, all harvest disk drives must be sanitized. The Disk Jockey PRO has a function that performs a Department of Defense (DoD)–approved seven-pass secure erase. When a new hard drive is removed from its packaging, it should be securely erased because an attorney might question a forensic investigator on this. Later, when we discuss evidence admissibility, we will emphasize the importance of establishing crime scene and forensic lab protocols for handling and examining evidence so that best practices are established to defend against potential objections from counsel. Other devices, like the WipeMASSter Hard Disk Sanitizer from Intelligent Computer Solutions, are used solely to securely erase hard disk drives.
Before embarking on an investigation, it is also helpful to identify the specifications of a suspect’s machine (the make and model), where possible. This enables the investigator to research the computer that they will be working on and learn how to remove the hard drive. This might sound like common sense, but removing a hard drive from a Dell Inspiron 6400 laptop for cloning is very different from removing the drive from a Dell Latitude D430. The equipment required to clone each of these hard drives is also very different. A Dell Inspiron 6400 is relatively easy to remove, and then you can connect a SATA data cable and a SATA power cable. For a Dell Latitude D430 (or D420) laptop, the battery must be removed. Then a thin cable must be removed from the hard drive and a rubber casing around the drive also must be removed. A special ZIF cable, ZIF adapter, and IDE interface cable are necessary to connect the 1.8-inch SATA hard drive to the Disk Jockey PRO, as shown in Figure 3.10. If possible, also try to predetermine the target computer’s operating system.

Figure 3.10 Cloning a hard disk drive with Disk Jockey PRO Forensic Edition
A simple Internet search for “removing the hard drive dell 430” will result in helpful documentation (including pictures) that Dell has made available online. In fact, Dell maintains a web page for most of its computer models that details hard disk drive removal. For other computers, manufacturers provide similar documentation. Removing the hard drive from an iMac is a very involved process that requires some unique tools. Apple provides comprehensive instructions on the removal of hard drives from iMacs. YouTube also hosts numerous helpful videos to assist the investigator. The website ifixit.com also provides helpful tips for teardowns of Macs and PCs. Nevertheless, you should initially refer to either your own internal guidelines for hardware devices and also other agency best practice guides. The National Institute of Justice provides a number of best practice guides, for example.
The Disk Jockey has both a “Disk Copy” function and a “Disk Copy (HPA)” cloning function. An investigator should first attempt to use the “Disk Copy (HPA)” clone function. This function makes a copy of the disk that includes the Host Protected Area (HPA). The Host Protected Area (HPA) is a region on a hard disk that often contains code associated with the BIOS for booting and recovery purposes. Manufacturers use the HPA to assist in the recovery process, and this feature replaces the need for a consumer recovery CD. An investigator should try to make a copy of this area because criminals have been known to hide incriminating evidence in this region of the disk. Sometimes the Disk Jockey PRO is unable to recognize and copy the HPA. When an error message appears on the Disk Jockey PRO’s LCD display, the investigator must then use the Disk Copy function instead of Disk Copy (HPA).
Alternative Copy Devices
The ImageMASSter Solo IV Forensic is a much more expensive device than the Disk Jockey PRO, but it has the ability to image two devices simultaneously. The investigator can select either a Linux DD file or an E01 image file.
Solid State Drives
A solid state drive (SSD; see Figure 3.13) is a non-volatile storage device found in computers. Unlike on a hard drive, files on a solid state drive are stored on memory chips in a stationary layout of transistors, and not on metal platters. In other words, a solid state drive has no moving parts—no read/write heads or spinning disks. Most solid state drives are flash memory NAND devices. It is important to know about these drives because they are growing in importance; they can be found in Chromebooks, the MacBook Air/Pro, and numerous personal computers today.

Figure 3.13 Solid state drive
In a single-level cell (SLC) NAND flash, each cell in the SSD has 1 bit. In a multi-level cell NAND flash, each cell has two or more bits. An MLC has higher density but generally requires more voltage than an SLC.
There are more than 80 SSD manufacturers, while there are very few hard disk drive manufacturers. There are numerous controller manufacturers who have different manufacturing requirements for SSD manufacturers. Therefore, this complicates the life of a computer forensics investigator, i.e., an SSD from one manufacturer can have different controllers with varying firmware. The proprietary firmware associated with the controller affects garbage collection, caching, wear-leveling, encryption, compression, bad block detection, and more.
Consider the following examples of SSD controller manufacturers:
Marvell
Hyperstone
SandForce
Indilix
Phison
STEC
Fusion-io
Intel
Samsung
In many ways, solid state drives are a more efficient alternative to hard disk drives, given their more efficient use of power, faster retrieval and storage of files, and greater resistance to environmental factors, including heat and vibration. Nevertheless, solid state drives suffer from ware-leveling. Ware-leveling is the process by which over time areas of a storage medium become unusable.
From a file storage perspective, solid state drives are very different from hard disk drives, and they do not use the traditional 512-byte storage sectors.
In terms of computer forensics, recovering deleted files on a solid state drive is more challenging as a result of the garbage collection process. Garbage collection is a memory-management process that removes unused files to make more memory available. Garbage collection is rather unpredictable with solid state drives and is particularly problematic from a forensics perspective. Changes to files stored on a solid state drive can occur without warning, regardless of the best efforts of a computer forensics examiner. Garbage collection and other automated functions associated with an SSD mean that once a hash is forensically created for a hard drive, and then another hash is generated, on the same drive, the two hashes might not match, which is different with a HDD.
Unlike a hard disk drive, with an SSD, data must be erased before a write can occur. Writes are completed in large blocks with high latency. Another difference is that the operating system does not keep track of the physical location of files; the File Translation Layer (FTL) is responsible for this. The File Translation Layer (FTL) maps a logical block address to a physical block address. TRIM is an operating system function that informs a solid state drive which blocks are no longer in use, and this allows for greater write performance. TRIM runs immediately after the Recycle Bin is emptied. However, there are a couple of important points that should be made. First, techniques have been developed to prevent the TRIM function and garbage collection from operating, which can be explored in recently published academic literature. Secondly, there are many instances in digital forensics today where one copy of a volume is not an exact match to another, based on the MD5 or SHA-1 verification process. This is largely because of the introduction of NAND flash storage in smartphones and hard drives, which is more volatile. Nevertheless, we know from case law that this evidence is still admissible.
Random Access Memory (RAM)
Random Access Memory (RAM) is volatile memory that is used for processes currently running on a computer. Please see Figure 3.14, which display some sample RAM. Its volatile nature comes from the fact that, when a computer is powered off, the contents of RAM are generally erased. However, if a system is powered on, RAM can provide a forensics examiner with a treasure trove of information, which can include Internet searches, websites visited, and possibly even passwords. There are numerous forensics tools, including Volatility, which can perform a RAM capture (acquisition).

Figure 3.14 RAM chip
Redundant Array of Independent Disks (RAID)
A Redundant Array of Independent (or Inexpensive) Disks (RAID) is commonly referred to with the acronym RAID. A RAID (Redundant Array of Independent Disks) is where two or more disks are used in conjunction with one another to provide increased performance and reliability through redundancy (see Figure 3.15). In the case of a RAID, reliability refers to fault tolerance, which means that if one component in a system, like a hard disk drive, fails, then the system will continue to operate. This kind of reliability is worth the investment for many critical systems in an organization. More recently, organizations have installed RAIDs to increase storage. Although RAID contains multiple hard disks, the operating system views the RAID as one logical disk with the use of hardware controllers.
From a computer forensics perspective, it is important to know that a computer may have multiple hard drives connected to it, all of which have evidentiary value. It is also important for an investigator to note the order in which each drive was added to the RAID and which drive adapter is connected to which drive, as this can be confusing.

Figure 3.15 RAID
Removable Memory
Today, it is rare for an investigator to simply seize a laptop computer and then only analyze that computer’s hard drive. The investigator must also consider the myriad of removable storage devices that are so pervasive today because of the low cost of removable memory. It is important to consider all potential storage when drafting a warrant and when conducting a search. You must understand how these devices are connected to the computer, understand trace evidence, and know the types of files that may be stored on these devices. This is easier said than done, given that removable memory has become smaller and more varied, with more wireless capabilities. This section provides some helpful advice on how to deal with removable memory.
FireWire
FireWire is the Apple version of IEEE 1394, which is a serial bus interface standard for high-speed data transfer. FireWire (see Figure 3.16) provides for higher data transfer speeds than USB wire, with speeds up to 400Mbps (megabits per second). FireWire 400 (1394-1995) can transfer data between devices at speeds ranging from 100, 200, or 400 megabits per second full duplex, and the cable length can measure up to 14.8 feet. FireWire 800 (1394b-2002) can transfer data at rates of 782.432 megabits per second full duplex. Apple, which has been largely responsible for the development of FireWire, has been slowly phasing out this protocol in favor of its Thunderbolt interface. Chapter 12, “Mac Forensics”, details how helpful FireWire can be for acquiring a forensic image from an Apple Mac using an Apple Mac.

Figure 3.16 FireWire cables
USB Flash Drives
As noted in Chapter 2, each time a device is connected to a computer, information about that device is recorded in Windows File Registry. Figure 3.17 shows exactly where in the Registry USB device connections are recorded.
These file registry entries are important in showing a history of what devices were connected to a computer. Every USB device has a serial number that is recorded in the subkey for that USB registry.
Access to files on a USB is not a forgone conclusion, however, because many of these storage devices have built-in utilities. For example, Ironkey USB devices use AES 256-bit encryption to protect files on the device. These devices protect the user and enterprise from theft of intellectual property. After a series of unsuccessful attempts to access the device, the device automatically reformats the drive.
The file system found on a USB flash memory device is usually a version of FAT, which is a file system that most computers recognize, although the device can be formatted to support other file systems.

Figure 3.17 Registry Editor
External Hard Drives
There are generally two types of external hard drives: a USB-powered hard drive and an external drive that uses the USB interface for data transfer while using an adapter to power the drive. Housed within the casing, an investigator usually finds a Serial ATA hard disk drive. This is important to know because if there is a limited amount of time to acquire evidence or the external hard drive cannot be removed from the premises, then it is probably advisable to remove the hard disk drive from the outer casing. By removing the drive from the casing, a cloning device can be used to make a copy of the external drive. If the hard disk drive is not removed from its casing, then the drive must be imaged using a write-blocker connected to a laptop. The Western Digital external hard disk drive in Figure 3.18 houses a 2.5-inch drive. A mini USB port is used for both power and data transfer to a computer.

Figure 3.18 Western Digital (WD) external hard drive
In some cases, a cloning device may not be feasible, so an investigator should always carry a write-blocker (including a USB write-blocker). For imaging and validating the drive, an investigator can bring FTK Imager Lite on a USB or another imaging tool. Imaging a 250GB drive, with verification, using FTK Imager Lite could take many hours, whereas cloning that same drive could take approximately 40 minutes. When cloning or imaging a hard drive, it is proper protocol to place the source and destination hard drives on an antistatic, rubberized mat to avoid any electromagnetic interference. Hard drives should also be transported in antistatic bags.
External hard drives are mostly used today for backups or as an extension to a computer’s memory. An examiner should be aware that an external hard disk drive could contain any number of file systems, including NTFS (Windows) or APFS (Mac). More importantly, if the external drive is connected to a PC with Windows 10 installed and BitLocker Drive Encryption is running, then disconnecting the drive from the computer can make it problematic to subsequently decrypt an external drive. In other words, think before you remove any USB device that is connected to a live system. Of course, external drives can also be eSATA. Newer drives may also have software installed for backing up the drive, perhaps to a cloud service. It is important to check for all installed software utilities on the suspect’s drive and note that backup software and other data integrity utilities can be present on a separate partition.
MultiMediaCards (MMCs)
A MultiMedia Card is storage memory that was developed by Siemens AG and SanDisk for use in portable devices, like cameras. MMCs are not as popular as they once were because they have largely been replaced by secure digital (SD) cards. An MMC has a standard size of 24mm × 32mm × 1.4mm. MultiMedia Cards replaced SmartMedia cards, which Toshiba developed in 1995, and had a storage capacity of 16 MB–128 MB. As you can see in Figure 3.19, a SmartMedia card is very similar in appearance to an SD card.

Figure 3.19 SmartMedia card
Secure Digital (SD) Cards
A Secure Digital (SD) card is a file storage device that was developed for use in portable electronics, like cameras. The association that developed SD cards and set the standard for this memory is a joint venture between Matsushita Electrical Industrial Co., Ltd. (Panasonic), SanDisk Corporation, and Toshiba Corporation.
The standard size for an SD card is 24mm wide and 32mm long, with a thickness of 2.1mm (see Figure 3.20). This standard size SD card has often been used in digital cameras, and many laptops come with an SD card slot and reader as standard. SDHC (Secure Digital High Capacity) cards have also still sold. SDHC cards generally go up to around 32GB. More recently, 64GB cards began to appear with the emergence of SDXC (Secure Digital eXtended Capacity). Micro SDXC cards are now available with 1TB of storage. Secure Digital cards are formatted with the FAT32 file system.

Figure 3.20 Secure Digital card
Note that some SD cards are Wi-Fi enabled with preinstalled utilities. Some of these utilities can automatically send photos to a mobile device, upload files to social media sites, or even add files to a cloud service. Generally, a logo on the SD card indicates that the card is Wi-Fi enabled, but this might not always be the case. The investigator should be cognizant of potential wireless capabilities.
If you encounter an SD card during an investigation, it is proper protocol to set the write-protect switch to on, when present on the card, to prevent any data from being written to this memory. Of course, the investigator will use a write-blocker before examining any removable memory, like an SD card.
A miniSD is 20 mm wide and 21.5 mm long. The microSD format was developed by SanDisk. A microSD card can be used in a Standard Digital card reader with the use of an SD adapter. microSD cards are sometimes found in cellular telephones, and therefore they can be a valuable source of evidence. Additionally, many cellphone forensic imaging or cloning devices cannot read the contents of the microSD card, so the card may have to be removed and imaged separately.
CompactFlash (CF) Cards
CompactFlash (see Figure 3.21) is a memory card that was first developed by SanDisk for use in portable electronics, like digital cameras. A CompactFlash (CF) can have two different dimensions: (a) Type I is 43mm × 36mm × 3.3mm, and (b) Type II is 43mm × 36mm × 5mm. CompactFlash cards are not as popular today as Secure Digital cards, but they do have an effective file storage system and can potentially support up to 1TB of memory.

Figure 3.21 CompactFlash
Memory Sticks
A Memory Stick (see Figure 3.22) is Sony’s proprietary memory card that was introduced in 1998. Unlike many other flash memory manufacturers, Sony also produced many of the electronic devices that support its memory card. Sony manufactures televisions, laptops, cellular telephones, digital cameras, video recorders, game consoles, MP3 players, and numerous other electronic devices, all of which often supported additional memory through the use of a Memory Stick. The original Memory Stick was replaced by the Memory Stick PRO in 2003, to enable a greater storage capacity. The PRO series utilized FAT12, FAT16, and FAT32 file systems. The Memory Stick Duo was a smaller memory card that was developed to fit well into small handheld devices. Other versions of the Memory Stick were developed to increase memory capabilities and to support high-definition video capture.
The Memory Stick XC (Extended High Capacity) series was released by Sony and SanDisk. These memory cards have the potential to store up to 2TB of memory. The XC series uses the exFAT (FAT64) file system. This series has maximum data transfer rates up to 160 Mbps and 480Mbps depending upon the XC model.
The important point for investigators to note is that if a suspect owns Sony products, Memory Sticks could be present in these devices. For example, a Sony television might have a Memory Stick inserted. Moreover, that memory card will probably contain files uploaded from a computer.

Figure 3.22 Memory Stick
xD Picture Cards
Introduced in 2002, xD (Extreme Digital) Picture Cards were developed by Olympus and Fujifilm for digital cameras and some voice recorders. These memory cards have been slowly phased out by Olympus and Fujifilm in favor of the more popular SD cards.
Hardware for Reading Flash Memory
There are a few ways to securely view the contents of flash memory cards. One tool is Digital Intelligence’s UltraBlock Forensic Card Reader and Writer (see Figure 3.23). This device is connected to a computer via the USB port (2.0 or 1.0) and can read the following media:
CompactFlash
MicroDrive
Memory Stick
Memory Stick PRO
Smart Media Card
xD Picture Card
Secure Digital Card (SD and SDHC)
MultiMediaCard
A regular memory card reader could be used in addition to a USB write-blocker to ensure that the data is viewed forensically. A write-blocker is a hardware device that allows an individual to read data from a device, like a hard drive, without writing to that device. An investigator could connect a media card reader to Digital Intelligence’s UltraBlock USB Write Blocker, which would be connected to a computer, where the media card’s contents would be viewed or acquired.

Figure 3.23 UltraBlock Forensic Card Reader and Writer
Compact Discs
A compact disc (CD), also known as an optical disc, is a polycarbonate plastic disc with one or more metal layers, used to store data digitally. A CD is usually 1.2mm thick and weighs 15–20 grams. Aluminum is generally used for the metallic surface. Data is stored to the disc and read from the disc using a laser. The laser that writes data to a disc reaches a temperature of 500–700 degrees Celsius. Because the data is stored using a laser, CDs are not vulnerable to electromagnetic charges. The high temperatures used in storing the data cause the metal alloy to liquefy, and the reflective state changes. Lands are the reflective surfaces on a CD burned flat by a laser. Pits are the less reflective surfaces on a CD that have not been burned by a laser. The differences between the reflective and less reflective surfaces can be translated to binary (0s, 1s).
CDs were initially developed by Sony and Philips to store and play audio files. Later the CD-ROM was developed for data storage. A CD-R allows data to be stored once. Because a CD-R can only have data written to it once, handling this type of CD in a forensically sound manner does not require a write-blocker. A CD-RW, on the other hand, allows data to be written multiple times to the disc. Today a standard CD generally has a storage capacity of 700MB.
ISO 9660, introduced in 1988, refers to the standard for optical discs and their file system. ISO 9660 is also called CDFS (Compact Disc File System), and it was created to support different operating systems, like Windows and macOS. Other file systems that can also be supported by CDs include Joliet, UDF, HSG, HFS, and HFS+. Joliet allows for longer filenames, which are associated with more recent versions of Windows. Because other file systems can exist on a CD, it is important to remember that a CD used in a Windows computer may show that it is invalid if an HFS+ file system resides on the disc. This means that specialized tools may be required to access the files stored on a CD. IsoBuster, for example, is a data recovery tool for CD, DVD, and Blu-ray. InfinaDyne’s CD/DVD Inspector is a specialized tool for a forensic acquisition of files from CDs and DVDs. It should be noted that an .iso file, which is an image of an optical disc, may be saved on the hard drive of a suspect’s computer or on another storage device.
The International Standardization Organization (ISO) in Geneva, Switzerland, has created this standard to facilitate the use of CDs on Windows, Macintosh, and UNIX computers. Frames consist of 24 bytes and are the smallest unit of memory on a CD-ROM. A sector on a CD-ROM consists of 98 frames (2352 bytes).
Compact Disc–Rewritable (CD-RW)
A CD-RW usually stores less data than a CD (570MB instead of 700MB). A track on a compact disc is a group of sectors that are written to at one time. A session on a compact disc is a group of tracks recorded at the same time. The table of contents (TOC) records the location of the start address, the session number, and track information (music or video) on a compact disc. The TOC is an example of a session, and every session contains a TOC. If the TOC cannot be read by the computer’s CD-ROM drive, then the compact disc will not be recognized. A full erase of a CD-RW deletes all data on a disc. However, a quick erase will only remove all references to tracks and sessions, leaving the land and pits unchanged. Nevertheless, the CD-RW will not be recognized because the sessions have been removed.
CnW Recovery is a tool that claims to recover disc data that has been through the quick erase process. Ultimately, when a quick erase has been performed, it is possible to recover the data on a CD-RW. When a full erase has been executed, the data cannot be recovered.
DVDs
A Digital Video (or Versatile) Disc (DVD) is an optical disc with a large storage capacity that was developed by Philips, Sony, Toshiba, and Time Warner. A single-sided DVD generally has a capacity of 4.7GB. Other DVD formats can store more than 17GB of data. Their large storage capacity makes them ideal for storing video files, which are often very large in size. A DVD player uses a red laser (650 nanometers [nm]) to read data from a DVD disc.
Blu-ray Discs
A Blu-ray disc (BD) is a high-capacity optical disc that can be used to store high-definition video. A single-layer disc has a storage capacity of 25GB, while dual-layer disc can store 50GB of data. Also available are 3D Blu-ray players and discs. A firmware upgrade available for Sony’s PlayStation 3 facilitates 3D Blu-ray playback as well. The name of this storage media comes from the blue laser (405nm) used to read the disc. This laser enables more data to be stored than the red laser used in DVDs. Standards for these optical discs have been developed and are maintained by the Blu-ray Disc Association (www.blu-raydisc.com).
From a forensics perspective, Blu-ray discs have limited value because both the Blue-ray burner and recordable discs can be prohibitively expensive for the average consumer. A suspect is more likely to store video on a hard drive or burn video files onto a DVD. Nevertheless, there are two different recordable formats. A BD-R disc can be written to once, while a BD-RE can be used for re-recording.
Companies like Digital Forensics Systems produce devices for imaging and analyzing CDs, DVDs, and BDs.
Floppy Disks
While floppy disks have been replaced by other storage media, it is not inconceivable that an investigator could still encounter these. A floppy disk is a thin, flexible, plastic computer storage disc that is housed in a rigid plastic rectangular case. Files are stored on the disk magnetically. These disks have historically come in 8-inch (see Figure 3.25), 5¼-inch, and 3½-inch (see Figure 3.26) sizes. Initially, these disks were used to store a computer’s operating system. Subsequently, they were used for general file storage purposes. The 3½-inch disk was introduced in 1987 and its storage capacity ranged from 720KB to 1.4MB.
IBM invented the floppy disk drive, which was used to store and read data from floppy disks.
Floppy disks have been largely replaced by flash memory, optical disks, and external hard drives. An investigator who encounters floppy disks during an investigation is more likely to find the PC-compatible 1440KB format. Floppy disks are formatted with the FAT12 file system. All of these disks will only have either one or two clusters.

Figure 3.25 8-inch floppy disk

Figure 3.26 3½-inch floppy disk
A forensic image of a floppy disk can be made by using the following Linux command:
# dd if=/dev/fd0 of=/evidence/floppy1.img bs=512
In this command, /dev/fd0 refers to the floppy disk drive, and bs=512 refers to the block size (bs), which is 512 bytes.
Of course, prior to inserting any disk, you should make sure that the disk is set to write-protected. You should then make a bit-for-bit copy of the floppy disk and lock the original disk in an evidence locker, away from any potential magnetic interference. To view the files on the disk, you can use the following command:
# ls /dev/fd0
Zip Disks
A zip disk is a removable storage medium that was developed by Iomega in the early 1990s. Zip disks originally came with a 100MB capacity and subsequently increased to 750MB. They were introduced as a higher-capacity alternative to floppy disks. A zip drive, in which zip disks are loaded, can be either an internal drive or an external drive. Zip drives and their disks have largely been replaced by CDs and the more popular, smaller, flash memory devices.
Magnetic Tapes
Magnetic tape is a thin plastic strip with a magnetic coating that is used for storing audio, video, and data. Because data is stored magnetically, an investigator must be careful to keep magnetic tapes away from all types of magnetism. Magnetic tapes are unique in the way that data is retrieved because they must be read in a linear fashion, from the start of the tape through the end of the tape. This often makes the process of acquiring data from magnetic tape quite time-consuming.
The use of audio tapes in investigations has become less important than it once was. The same is true of videotapes used in video cassette recorders (VCRs).
Magnetic Tapes (Data Storage)
Forensic imaging and analysis of magnetic tapes (see Figure 3.27) used for data storage on servers is challenging. Many different proprietary server systems exist, which makes a single solution impossible. An analysis of the physical surface can be conducted using a complicated process known as magnetic force microscopy. This method can be used to uncover wiped or overwritten data.

Figure 3.27 Magnetic tape for data storage
Generally, data is recorded to a magnetic tape in blocks. Data at the block level can be accessed using the dd command. In computer investigations, dd is a UNIX command that produces a raw data image of a storage medium, like a hard drive or magnetic tape, in a forensically sound manner. The dd command is written in such a way that the image is copied to a hard drive, which allows for better search capabilities. A magnetic tape has no hierarchical file system because files are stored sequentially or in a tape partition. Partitions on magnetic tapes allow users to group files in “tape directories”, When a sector is only partially used by a file, the remainder of the sector is referred to as memory slack, buffer slack, or RAM slack. Similar to hard disks, file slack on magnetic tape can contain remnants of data from previously existing files.
Summary
It is important for computer forensics investigators to understand the vast array of digital devices that they may encounter at a crime scene. This knowledge is essential because each device needs to be handled differently, and investigators must maintain and update different power and data cables over time. Moreover, with each device, there are different types of evidence associated with each device, and a different methodology is required to acquire evidence from these devices.
Hard disk drives are a primary source of evidence for investigators. There are different types of hard disk drives, which are mainly differentiated by their drive controllers and connections. There are Small Computer System Interface (SCSI) hard disk drives and Integrated Drive Electronic (IDE) hard disk drives. However, Serial ATA (SATA) hard disk drives have become more prevalent. Hard disk drives are cloned rather than imaged when a hard disk drive needs to be copied quickly. Solid state drives have gained market share in recent times but present significant challenges for computer forensics investigators, given the unstable nature of these drives compared to traditional hard disk drives. Occasionally, an investigator will encounter a computer with multiple hard disk drives, referred to as a Redundant Array of Independent Disks (RAID).
USB thumb drives and other kinds of flash memory continue to grow in significance as they become cheaper and provide greater memory capacity. However, cloud storage has become even more important. Interestingly, though, connecting USB devices to a computer leaves a digital footprint in the Windows computer’s Registry, which the investigator then can view. This digital footprint is also often available on Mac and UNIX systems.
Key Terms
Blu-ray disc (BD): A high-capacity optical disc that can be used to store high-definition video.
Boot Camp: A utility included with macOS that enables a user to run a Windows operating system on an Intel-based Mac.
compact disc: A polycarbonate plastic disc with one or more metal layers that is used to store data digitally.
CompactFlash: A memory card that was first developed by SanDisk for use in portable electronics such as digital cameras.
dd: A UNIX command that produces a raw data image of a storage medium, such as a hard drive or magnetic tape, in a forensically sound manner.
Digital Versatile Disc (DVD): An optical disc with a large storage capacity that was developed by Philips, Sony, Toshiba, and Time Warner.
disk clone: An exact copy of a hard drive that can be used as a backup for a hard drive because it is bootable, just like the original.
disk controller: Facilitates communication between a computer’s central processing unit (CPU) and hard disks (or other disk drives).
disk image: A file or a group of files that contain bit-for-bit copies of a hard drive but cannot be used for booting a computer or other operations.
eSATA: A variation of SATA that is used for external drives.
fault tolerance: The ability of a system to continue to operate if one component in a system, such as a hard disk drive, fails.
File Translation Layer (FTL): Maps a logical block address to a physical block address.
FireWire: The Apple version of IEEE 1394, which is a serial bus interface standard for high-speed data transfer.
floppy disk: A thin, flexible, plastic computer storage disk that is housed in a rigid plastic rectangular case.
frame: The smallest unit of memory on a CD, consisting of 24 bytes.
garbage collection: A memory-management process that involves removing unused files to make more memory available.
Host Protected Area (HPA): The region on a hard disk that often contains code associated with the BIOS for booting and recovery purposes.
Integrated Drive Electronics (IDE): A drive interface, largely based on IBM PC standards, for devices such as hard disk drives, tape drives, and optical drives.
lands: The reflective surfaces on a CD that are burned flat by a laser.
magnetic tape: A thin plastic strip with a magnetic coating that is used for storing audio, video, and data.
Memory Stick: Sony’s proprietary memory card that was introduced in 1998.
MultiMediaCard: Storage memory that was developed by Siemens AG and SanDisk for use in portable devices such as cameras.
pits: The less reflective surfaces on a CD that have not been burned by a laser.
RAID (Redundant Array of Independent Disks): Two or more disks used in conjunction with one another to provide increased performance and reliability through redundancy.
Random Access Memory (RAM): Volatile memory that is used for processes that are currently running on a computer.
Secure Digital card: A file storage device that was developed for use in portable electronics such as cameras.
Serial ATA: An interface that connects devices such as hard disk drives to host bus adapters.
session (on a compact disc): A group of tracks recorded at the same time.
Small Computer System Interface (SCSI): A protocol for both the physical connection of devices and the transfer of data.
solid state drive (SSD): A nonvolatile storage device found in computers.
Table of contents (TOC): Records the location of the start address, the session number, and track information (music or video) on a compact disc.
track (on a compact disc): A group of sectors that are written to at one time.
TRIM: An operating system function that informs a solid state drive which blocks are no longer in use to allow for high write performance.
wear-leveling: The process by which areas of a storage medium become unusable over time.
write-blocker: A hardware device that allows an individual to read data from a device such as a hard drive without writing to that device.
xD (Extreme Digital) Picture Card: Memory storage developed by Olympus and Fujifilm for digital cameras and some voice recorders.
zip disk: A removable storage medium that was developed by Iomega in the early 1990s.
Assessment
Classroom Discussions
1. Under what circumstances is a computer forensics investigator required to conduct an investigation onsite instead of removing a computer for analysis back at the lab?
2. What major challenges do investigators face in regards to removable memory?
Multiple-Choice Questions
1. Which of the following facilitates the communication between a computer’s CPU and hard disks?
Actuator arm
ROM chip
Disk controller
FireWire
2. Which of the following is true of a disk clone?
It is a bootable copy.
It can be used as a hard drive backup.
Neither A nor B is true.
Both A and B are true.
3. Which of the following is true of solid state drives?
They have no moving parts.
Files are stored on metal platters.
It is volatile memory.
None of the above are true.
4. Which of the following is volatile memory that is used for processes that are currently running on a computer?
RAM
ROM
Hard disk drive
Flash
5. Which of the following refers to two or more disks used in conjunction with one another to provide increased performance and reliability through redundancy?
RAM
SCSI
IDE
RAID
6. FireWire is based on which of the following standards?
802.11
ANSI N42
IEEE 1394
ISO 9660
7. Which of the following memory cards is most likely to be found in Sony electronics?
Secure Digital card
CompactFlash
MultiMediaCard
Memory Stick
8. The reflective surfaces on a CD that are burned flat by a laser are referred to as which of the following?
Lands
Pits
Mirrors
Craters
9. Which of the following is a high-capacity optical disc that can be used to store high-definition video?
CD
DVD
BD
VCD
10. Which of the following is a UNIX command that produces a raw data image of a storage medium such as a hard drive or magnetic tape in a forensically sound manner?
aabbccdd
Fill in the Blanks
1. Boot __________ is a utility included with Mac OS X 10.6 (Snow Leopard) that enables the user to run a Windows operating system on an Intel-based Mac.
2. Integrated Drive __________ is a drive interface, connector, and controller that is largely based on IBM PC standards for devices such as hard disk drives, tape drives, and optical drives.
3. __________ ATA is an interface that connects devices such as hard disk drives to host bus adapters.
4. A disk __________ is actually one file or a group of files that contain bit-for-bit copies of a hard drive but cannot be used for booting a computer or for other operations.
5. The Host __________ Area is a region on a hard disk that often contains code associated with the BIOS for booting and recovery purposes.
6. __________ collection is a memory management process that involves removing unused files to make more memory available.
7. Fault __________ means that if one component in a system, such as a hard disk drive, fails, the system will continue to operate.
8. A(n) __________ is a hardware device that allows an individual to read data from a device such as a hard drive without writing to that device.
9. The less reflective surfaces on a CD that have not been burned by a laser are called __________.
10. A(n) __________ disk is a thin, flexible plastic computer storage disk that is housed in a rigid plastic rectangular casing.
Projects
Work with a Dual-Boot System
Find an Apple Mac computer running a dual-boot system or install Boot Camp and Microsoft Windows on an Apple Mac with macOS currently running. Create standard operating procedures to help computer forensics investigators identify whether a Mac computer is running more than one operating system and determine how to acquire digital evidence from this type of machine.
Identify Changes in Computer Hardware
Write an essay that discusses how computer hardware and memory are likely to be transformed over the next 5 years. Include in your discussion how computer forensics practices will have to change to keep pace with changing technology.
Identify the Use of RAID
Find out how an investigator can identify whether a suspect’s computer is running RAID. How should RAID be forensically examined?
Work with Volatile Memory
Random Access Memory (RAM) can provide an extraordinary amount of evidence. What computer forensics tools can be used to image RAM? Are there any issues with using RAM as a source of evidence in an investigation?
Explain USB Flash Memory
Explain the physical makeup of a USB flash drive. Include in your explanation how files are stored and organized on this type of storage device.
Reference
James Wardell and G. Stevenson Smith, “Recovering Erased Digital Evidence from CD-RW Discs in a Child Exploitation Investigation”, International Journal of Digital Forensics & Incident Response 5 (no. 1–2), 2008.
