Chapter 13
Case Studies
Learning Outcomes
After reading this chapter, you will be able to understand the following:
Investigating Dark Web marketplaces;
The importance of computer forensics in proving intent to commit a crime;
How computer forensics is used at trial and the types of objections that may arise;
The role of a computer forensics examiner as an expert witness;
How digital forensics can potentially be used in any type of investigation or court proceeding;
The problem of cyberbullying and digital evidence used to investigate these types of crimes;
Anti-cyberbullying legislation; and
How the use of digital files was challenged in the investigation of steroid use by Major League Baseball players.
Case studies that effectively illustrate the use of computer forensics at trial, or in investigations, are often hard to find. Exhibits from trial often are simply unavailable to the public. This happens in child abuse trials or trials that are subject to appeal. In other situations, the trial exhibits might be available from a court system but have a charge associated with access to them.
This chapter provides very different examples of cases involving digital forensics, from attempted murder, to serial killings, to bullying, to drug abuse in sports.
Silk Road
Ross Ulbricht, later known as “Dread Pirate Roberts”, was a self-proclaimed libertarian, Graduate Research Assistant, from Austin, Texas, who was studying at Pennsylvania State University (see Figure 13.1). He decided to create a Dark Web marketplace called Silk Road. The marketplace was home to numerous criminal retailers who sold a plethora of narcotics and many other illegal products, including fake government documents, like drivers’ licenses and passports, weapons and ammunition, and other illegal goods. At one point, there were 13,000 listings of controlled substances and more than 100,000 buyers. Over a period of two and a half years, 9.5 million Bitcoin were transacted, which at the time of trial was the equivalent of $1.3 billion USD. Silk Road allegedly pocketed $85 million in commissions.

Figure 13.1 LinkedIn profile of Ross Ulbrict
During the trial, Ulbricht’s defense team argued that their client began the Silk Road as a class experiment, which he ultimately abandoned years before he was arrested. Thus, the use of digital evidence in this case was of the utmost importance to federal prosecutors.
Genesis of the Silk Road
In 2011, Ulbricht registered the website silkroad420.wordpress.com. During this time, Ulbricht created a user account on shroomery.org, with the username “Altoid” and submitted a post promoting Silk Road (see Figure 13.2):
I came across this website called Silk Road. It's a Tor hidden service that claims to allow you to buy and sell anything online anonymously. I'm thinking of buying off it, but wanted to see if anyone here had heard of it and could recommend it.
I found it through silkroad420.wordpress.com, which, if you have a tor browser, directs you to the real site at http://tydgccykixpbu6uz.onion.
Let me know what you think…

Figure 13.2 Shroomery.org website with Ulbricht posting
Ulbricht also created a user account on Bitcointalk Forum and then posted an advertisement for an employment opportunity, as follows:
the best and brightest IT pro in the bitcoin community [to] be the lead developer in a venture-backed bitcoin startup company
Those interested were asked to contact [email protected] (see Figure 13.3).

Figure 13.3 Bitcointalk Forum with Ulbricht posting
Investigators linked Ulbricht’s email to his Google+ account (see Figure 13.4), and Google was later subpoenaed for information related to his Google accounts. In April 2012, Ulbricht posted on Google+, “anybody know someone that works for UPS, FedEX, or DHL?”
Figure 13.4 Ulbricht’s Google+ account
Ross Ulbricht also posted a question under the name “Ross Ulbricht” on the website Stack Overflow:
How can I connect to a Tor hidden service using curl in php?
I'm trying to connect to a tor hidden service using the following php:
$url = 'http://jhiwjjlqpyawmpjx.onion/'
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_PROXY, "http://127.0.0.1:9050/");
curl_setopt($ch, CURLOPT_PROXYTYPE, CURLPROXY_SOCKS5);
$output = curl_exec($ch);
$curl_error = curl_error($ch);
curl_close($ch);
print_r($output);
print_r($curl_error);
when I run it I get the following error:
Couldn't resolve host name
However, when I run the following command from my command line in ubuntu:
curl -v --socks5-hostname localhost:9050 http://jhiwjjlqpyawmpjx.onion
I get a response as expected
the php cURL documentations says this:
--socks5-hostname
Use the specified SOCKS5 proxy (and let the proxy resolve the host name).
I believe the reason it works from the command line is because Tor (the proxy) is resolving the .onion hostname, which it recognizes. When running the php above, my guess is that cURL or php is trying to resolve the .onion hostname and doesn't recognize it. I’ve searched for a way to tell cURL/php to let the proxy resolve the hostname, but can't find a way.
There is a very similar question here: CURL request using socks5 proxy fails when using PHP but works through the command line
Death Threat
According to court records, in March 2013, a Silk Road seller, with the username “Friendly Chemist”, threatened to reveal the real name of DPR (Dread Pirate Roberts) unless hush money, in the amount of $300,000 (later $500,000), was paid. DPR then allegedly asked a user on the Silk Road, called “redandwhite”, to execute FriendlyChemist, in exchange for $150,000 (1,760 Bitcoins). DPR subsequently provided the real name and address for FriendlyChemist.
Silk Road Takedown
Ulbricht decided to order some fake drivers’ licenses from a criminal retailer on the Silk Road (see Figure 13.5). In June 2013, U.S. Border Control agents at the Canadian border interdicted these fake licenses. In July 2013, Homeland Security visited the residence to where these licenses were being shipped, and they encountered Ross Ulbricht. Ulbricht himself actually informed Homeland Security about a great website called the Silk Road, where he made the purchase.
Ultimately, federal investigators tracked Ulbricht to the Bay Area (San Francisco, CA). They determined that his Gmail account was accessed from a computer in the area and also realized that the Silk Road server had been accessed from an Internet café beside the residence of Ulbricht’s friend. Investigators had subpoenaed Comcast for information related to the secure server that had been accessed via a virtual private network (VPN).

Figure 13.5 Fake drivers’ licenses sent to Ulbricht
The Takedown of Ulbricht
DHS Special Agent, Jared Der-Yeghiayan, managed to infiltrate the Silk Road by posing as a site administrator, with the username “cirrus”. Investigators had two major concerns: (1) that Ulbricht likely had encryption running on his laptop, which would later be problematic for forensics investigators and (2) that he would later deny involvement in the Silk Road site.
At one point, Ulbricht was staying at his friend’s place in the San Francisco Bay Area. When the Internet connection was cut to the apartment, Ulbricht decided to use the free Wi-Fi at the Glen Park Library, where investigators planned an undercover operation to take down Ulbricht. At 15:08, Ulbricht opened his laptop and logged into the staff chat for the Silk Road site (see Figure 13.6). Special Agent Der-Yeghiayan contacted Ulbricht, who had logged in as “dread” and the following chat transpired:
cirrus: hey
can you check out one of the flagged messages for me?
dread: you did bitcoin exchange before you worked for me, right?
cirrus: yes, but just for a little bit
dread: not any more then?
cirrus: no, I stopped because of reporting requirements
dread: damn regulators, eh?
ok, which post?
cirrus: lol, yep
there was the one with the atlantis

Figure 13.6 Screenshot of the Silk Road support page (administrator view)
Once Ulbricht (“dread”) said “ok, which post?”, Special Agent Der-Yeghiayan knew that Ulbricht was on the flagged message page and therefore had administrator access. Two undercover agents, male and female, feigned an argument near Ulbricht, in the Science Fiction section of the library. Ulbricht stood up and turned around. The woman held onto Ulbricht while the male agent grabbed Ulbricht’s laptop, so that the computer remained on, and so that any potential encryption would not be implemented. Ultimately, it was determined that the seized Samsung 700z laptop was in fact running TrueCrypt (full disk encryption software). The agents could then show that Ulbricht was still logged into the Silk Road and he was using TorChat with backups, which would later assist investigators.
Ross Ulbricht Pre-trial
The defense counsel argued that the FBI hacked into a server in Iceland without a warrant. The defense subsequently filed a motion to suppress the evidence from that server. This server was supposedly used to host the Silk Road Dark Web marketplace. On June 12, 2013, a request was made to the Icelandic authorities to:
(1) obtain subscriber information associated with the Subject Server; (2) collect routing information for communications sent to and from the Subject Server, including historical routing data from the prior 90 days; and (3) covertly image the contents of the Subject Server
Subsequently, the Reykjavik Metropolitan Police (the “RMP”) acted upon this request. It appears that these results, by the RMP, were shared with U.S. authorities on July 29, 2013. Going back to the motion to suppress, the judge ruled that Ulbricht “failed to submit anything establishing that he has a personal privacy interest in the Icelandic server or any of the other items imaged and/or searched and/or seized.” The issue for Ulbricht’s defense counsel is that showing a personal privacy interest in the Icelandic server could imply that he was in fact still involved with the Silk Road at that time and they wanted to argue that he created the idea of the Silk Road but then abandoned the site.
The U.S. government did not just rely on digital evidence at trial but could also rely on the testimony of a number of people, including a narcotics dealer associated with the Silk Road. His name was Cornelis Jan Slomp, aged 22, from Woerden, the Netherlands (see Figure 13.7). Also known as “SuperTrips”, Jan Slomp was the largest vendor on the site and was responsible for 10,000 transactions, which were worth 385,000 Bitcoin. Jan Slomp was arrested at Miami Airport, as he was about to get into his rented Lamborghini. Investigators found his fingerprints on DVD cases that he used to ship the drugs. In a plea deal, he offered to testify about his activities during the Ulbricht case, but he was never called to testify. His plea led to a more lenient sentence of 10 years, instead of potentially 40 years behind bars.
Figure 13.7 LinkedIn profile of Cornelis Jan Slomp, a.k.a. SuperTrips
Unfortunately, prior to testimony, the U.S. government inadvertently leaked a list of exhibits online that they intended to use at trial, which included potential objections by defense counsel. Figure 13.8 shows some of the leaked exhibits and potential objections.

Figure 13.8 U.S. government leaked exhibits with potential objections
Ross Ulbricht on Trial
Special Agents Chris Tarbell and Illhwan Yum, CY2 (Cyber Crimes Squad), FBI, both worked on the case and gave testimony at trial. Illhwan Yum testified that investigators had tracked 3,760 Bitcoin transactions to Ulbricht after the time that Ulbricht had claimed that he had abandoned to site. Yum cross-checked transactions on the public ledger (Blockchain) with data pulled from Ulbricht’s laptop and the Silk Road web server. Evidence was also presented that showed Bitcoin transfers from servers located in Philadelphia, Pennsylvania, and from Reykjavik, Iceland.
According to the “Declaration of Christopher Tarbell”, the location of the Silk Road server was a result of the login interface, for the site, leaking its IP address. During the login process, some packets sent by the web server contained an IP address that was different from the IP addresses of known Tor nodes. It appears as though the IP address for the web server was leaked as a result of a misconfigured CAPTCHA, which was an application used to prevent automated bots from logging into the site.
Laptop Evidence
A logbook was found on Ulbricht’s laptop, which detailed his day-to-day activities. Ulbricht’s PGP private key was also recovered from the laptop, and this key was used for signing messages from DPR (Dread Pirate Roberts). Numerous .php files, used to create the Silk Road website, were also retrieved from his laptop (see Figures 13.9–13.11). Investigators also discovered an application for economic citizenship in Dominica. Ulbricht perhaps thought that he would become a legend because of his marketplace and therefore kept a journal on his laptop. In one entry he wrote the following:
I am creating a year of prosperity and power beyond what I have ever experienced. Silk Road is going to become a phenomenon and at least one person will tell me about it, unknowing that I was its creator
His entry in December 2011 stated the following:
I felt compelled to reveal myself to her. It was terrible. I told her I have secrets. She already knows I work with bitcoin wich [sic] is terrible. I’m so stupid. Everyone knows I am working on a bitcoin exchange. I always thought honesty was the best policy and now I don’t know what to do. I should have just told everyone I am a freelance programmer or something, but I had to tell half-truths. It felt wrong to lie completely so I tried to tell the truth without revealing the bad parts, but now I am in a jam. Everyone knows too much, dammit.

Figure 13.9 FTK image from Ross Ulbricht’s laptop
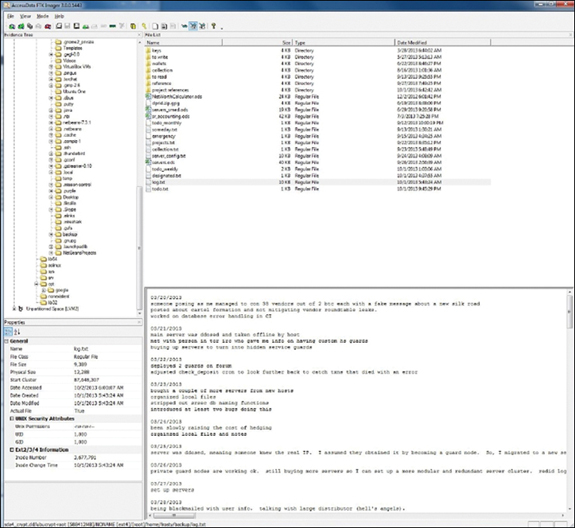
Figure 13.10 FTK image from Ross Ulbricht’s laptop, showing files related to the Silk Road
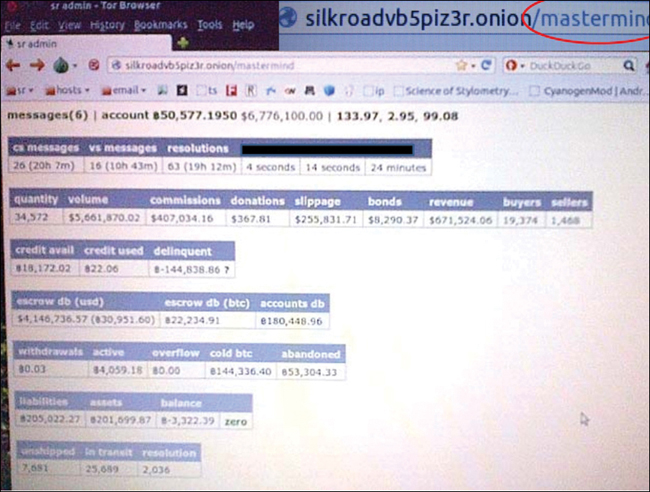
Figure 13.11 Screenshot of bitcoin transactions from Ulbricht’s laptop
Trial Verdict
The trial of Ross Ulbricht lasted 13 days and was followed by 3.5 hours of jury deliberations. Ulbricht was found guilty on the following charges:
Narcotics trafficking conspiracy
Computer hacking conspiracy
Money laundering conspiracy
Las Vegas Massacre
On October 1, 2017, 64-year-old, Stephen Craig Paddock, from Babbling Brook, Mesquite, Nevada, who was staying at the Mandalay Bay in Las Vegas, shot and killed 58 people and injured 700 others in the largest massacre in U.S. history. The motive for the attack still remains a mystery, although an investigation of his digital devices does provide some indication of his intent. The Las Vegas Metropolitan Police Department (LVMPD) released a report that provided some preliminary findings about the crime and evidence that was obtained from his digital devices. According to the report, 21,560 hours of video were reviewed, 251,099 images were analyzed, while four laptops and three cellphones were also examined.
The following Google searches were discovered on one of Paddock’s laptops – an HP laptop:
On 05-18-17: Searches: "summer concerts 2017," "grant park functions," "biggest bear," "La Jolla Beach," "open air concert venues," "biggest open air concert venues in USA," and "how crowded does Santa Monica Beach get."
On 09-04-17: Searches: "Las Vegas rentals," "Las Vegas condo rentals," "Las Vegas high rise condos rent," and "Las Vegas Ogden for rent."
On 09-05-17: Searches: "life is beautiful expected attendance," "life is beautiful single day tickets," and "life is beautiful Vegas lineup."
On 09-15-17: Searches: "swat weapons," "ballistics chart 308," "SWAT Las Vegas," "ballistic," and "do police use explosives."
A Google search can of course be performed using any type of web browser. On a Windows PC, when a user uses the Google Chrome web browser, there is a wealth of Web artifacts that can be retrieved from the following directory:
%root%Users\%username%AppDataLocalGoogleChromeUser DataDefaultOn an Android you will find the evidence here:
datadatacom.android.chromeapp_chromeDefaultFor iOS devices, the Web-related artifacts can be found here:
%root%LibraryApplication SupportGoogleChromeDefaultA Bing search was also found:
On 09-05-17: Search: "Mandalay Bay Las Vegas," "Route 91 harvest festival 2017 attendance", and "Route 91 harvest festival 2017."
Digital forensics evidence, from Paddock’s laptop, did not yield a motive but, as you can see from the aforementioned searches, Paddock did use his laptop to identify a venue, with a lot of people in attendance when planning his attack.
A Dell laptop, Model E5570, belonging to Paddock, was also recovered from his room at Mandalay Bay. Hundreds of child exploitation images were retrieved from this laptop. He also performed numerous searches for open air venues. Police found a laptop, which was placed on a food service cart, which was connected to cameras that he had mounted to view anyone coming near his room (see Figure 13.12).

Figure 13.12 Paddock’s laptop, found in his hotel room, connected to cameras in the hallway
Zacharias Moussaoui
Only one terrorist stood trial for the atrocities of September 11, 2001. That person was Zacharias Moussaoui. As a case study, his trial provides a valuable insight into the various types of digital evidence examined by law enforcement investigators. Additionally, the case demonstrates how this type of evidence is admitted to court and shows the arguments by the defense counsel against its use. Finally, this case illustrates how both defense attorneys and prosecution attorneys use expert witness testimony.
Background
Zacharias Moussaoui was born on May 30, 1968, in France and was of Moroccan descent. Moussaoui received his master’s degree from South Bank University in London. During his time in Britain, he frequented the Brixton Mosque, which the “Shoe Bomber”, Richard Reid, also attended. Moussaoui also attended the more radical Finsbury Park Mosque in London. He connected with Islamist extremists in England and subsequently trained with Al Qaeda in 1998 at Khalden, Derunta, Khost, Siddiq, and Jihad Wal training camps in Afghanistan. He also lived in Hamburg between 1998 and 1999 and shared an apartment with Mohammed Atta, one of the 9/11 co-conspirators who crashed American Airlines Flight 11 into the North Tower of the World Trade Center.
In August 2001, Moussaoui attended flight school in Minneapolis and trained on 747 flight simulators. The Federal Bureau of Investigation (FBI) had Moussaoui under surveillance and wanted to search his Toshiba laptop in early 2001. Unfortunately, the FBI agent requests from the bureau office in Minnesota were apparently rejected by FBI headquarters.
Table 13.1 shows a timeline of Moussaoui’s actions leading up to the events of 9/11/01, as noted in the Virginia grand jury indictment (/www.vaed.uscourts.gov/notablecases/moussaoui/exhibits/).
Table 13.1 Moussaoui Events Timeline
Date |
Event |
September 29, 2000 |
Moussaoui sends an email to Airman Flight School in Norman, Oklahoma. |
February 23, 2001 |
Moussaoui flies from London to Chicago and then on to Oklahoma City. |
May 23, 2001 |
Moussaoui sends an email to Pan Am International Flight Academy in Miami. |
June 20, 2001 |
Moussaoui purchases flight deck videos for Boeing 747 from Sporty’s Pilot Shop. |
July 10–11, 2001 |
Moussaoui makes a credit card payment to Pan Am International Flight Academy for flight simulation training. |
August 13–15, 2001 |
Moussaoui attends Boeing 747 Model 400 simulator training at Pan Am International Flight Academy in Minneapolis. |
August 17, 2001 |
Moussaoui is interviewed by federal agents in Minneapolis. |
September 11, 2001 |
Four hijacked commercial jets crash into the World Trade Centers; the Pentagon; and a field in Somerset County, Pennsylvania. |
December 11, 2001 |
Moussaoui is charged. |
April 22, 2005 |
Moussaoui pleads guilty to all six charges. |
Moussaoui was indicted by a federal grand jury, in the Eastern District of Virginia, to stand trial on six felony charges:
Conspiracy to commit acts of terrorism transcending national boundaries
Conspiracy to commit aircraft piracy
Conspiracy to destroy aircraft
Conspiracy to use weapons of mass destruction
Conspiracy to murder United States employees
Conspiracy to destroy property of the United States
Digital Evidence
Government investigators examined numerous computers in the wake of 9/11. The computer that Mukkarum Ali owned, in the apartment where Moussaoui lived in Norman, Oklahoma, was seized. The apartment was owned by the University of Oklahoma, and a computer from the University of Oklahoma computer lab was also seized.
The FBI also visited a Kinko’s in Eagan, Minnesota, to examine a computer that the suspect used to access the Internet. FBI agents became aware of his use of a computer at Kinko’s after examining Kinko’s firewall logs. They discovered that Moussaoui had used the computer to access Hotmail. One of the email addresses the suspect used was [email protected]; the suspect listed it as one of his accounts in one of his pro se pleadings in July 2002. (Pro se refers to someone who advocates for him- or herself and does not use legal representation. Moussaoui requested to represent himself at trial.) The computer at Kinko’s was not seized because agents were informed that the data on the computer would have been scrubbed every 24 hours, as part of standard operating procedures, and 44 days had now passed.
Prosecutors had failed to link the computer’s Internet Protocol (IP) address at Kinko’s with Moussaoui’s Hotmail account because so much time had elapsed. After 30 days, the company deletes IP connection data and email content. Email account registration information is maintained for an additional 60 days, but this information then is deleted, and the account username once again becomes available to the public. Once investigators discovered the suspect’s claim that he had used [email protected], they contacted Hotmail (Microsoft). Alas, Hotmail had no saved information for this account.
The FBI found Moussaoui’s receipt from Kinko’s, related to his paid use of the Internet on a computer in the Eagan, Minnesota, store on August 12, 2001. The investigation concluded that the suspect had been connected to MSN/Hotmail for eight minutes. It also discovered that the other 19 9/11 hijackers had accessed the Internet on Kinko’s computers at other locations across the country.
Government agents were aware of Moussaoui before 9/11. INS (Immigration and Naturalization Service) agents in Minnesota had arrested him on August 16, 2001, and actually seized his laptop and a floppy disk. Moussaoui had been staying in a Residence Inn in Eagan, Minnesota, while attending the Pan Am International Flight Academy. The FBI subsequently obtained and executed a warrant on September 11, 2001, to seize these items again. On the floppy disk, they found Moussaoui’s emails to flight schools. He had contacted these flight schools from [email protected].
The FBI appears to have been a lot luckier when examining Moussaoui’s [email protected] records. Investigators were able to match Hotmail IP address connection logs to determine that he had accessed his email account from an address in Malaysia, from the computer lab at the University of Oklahoma, from Mukkarum Ali’s apartment (in Norman, Oklahoma), and from Kinko’s (in Eagan, Minnesota). Al Qaeda operatives had met in Kuala Lumpur in January 2000. The discovery of the IP address for Kinko’s prompted investigators to search the computer at this location.
Standby Counsel Objections
Standby counsel argued that the government had failed to provide the defense with evidence recovered from the [email protected] account or from computers at Oklahoma University, at Kinko’s, or at Mukkarum Ali’s apartment. Standby counsel is a lawyer who assists a client who has invoked his right to self-representation.
Donald Eugene Allison provided computer forensics expert witness testimony for the defense in an affidavit dated September 4, 2002.
In this same court document, standby counsel questioned methods by which the prosecution authenticated digital evidence. They noted the following:
[The] authentication information (such as the MD5 message digest and other accepted computer forensic methods) is critical as without it, it is impossible to verify that the duplicate hard drives are an exact copy of those that exist on the original systems. Likewise, without such information it is impossible to determine if the material retrieved from the hard drives is accurate.
In the same document, standby counsel argued that more than 200 hard drives were produced during discovery, yet the defense lacked the resources to thoroughly examine the drives to the same extent as the prosecution.
Standby counsel then asserted that the hard drive from the University of Oklahoma must have been contaminated. The defense contended that evidence from the Hotmail account should have been available from temporary Internet files. This again relates to the lack of evidence concerning the [email protected] account. Additionally, the defense argued that there was a mismatch of IP addresses used as evidence by the prosecution. The defense contended that even though Kinko’s appeared to have erased data every 24 hours, investigators could theoretically have examined the computer for files that still existed, but they failed to attempt to retrieve any files. Moreover, the defense argued that the prosecution had not examined the file slack on Mukkarum Ali’s computer.
Prosecution Affidavit
Dara K. Sewell was a supervisory special agent for the FBI and a computer forensics investigator who worked on this case. Sewell submitted an affidavit rebutting the assertions made by defense counsel, particularly Donald Eugene Allison. Sewell noted that the FBI uses three methods of duplicating or imaging a hard drive: (1) Linux dd, (2) SafeBack, and (3) Logicube handheld disk duplicator. All of these tools had undergone validation testing.
Sewell responded to Allison’s assertion that NIST approves only one method of making duplicates by stating, “NIST does not ‘approve’ any computer forensic tools. Instead, it merely reports the results of its testing. Moreover, Mr. Allison wrongly identifies Linux dd as the ‘only one method. . . . approved by [NIST].”
Interestingly, Allison questioned the lack of a Message Digest Sum Version 5 (md5sum) or Secure Hash Algorithm Version 1 (SHA-1) hash verification being produced by the prosecution. Sewell responded by noting that a number of verification hashes can be used, including Cyclical Redundancy Checksum (CRC). Sewell continued that SafeBack and Logicube disk duplicators were used. They used an internal CRC and were tested by the FBI’s CART. Therefore, “there would not ordinarily be any MD5 or SH-1 hash values to disclose to the defense for any computer drives imaged with SafeBack or a Logicube disk duplicator.” However, even with confidence in SafeBack’s CRC verification process, Sewell went back and generated an md5sum for the original evidence and the duplicates, and they were a match.
Exhibits
Hundreds of exhibits were submitted at trial. In terms of digital evidence, the prosecution presented numerous emails, wire transfers, receipts, and other exhibits.
The following email demonstrates Moussaoui’s interest in learning how to fly:
From: |
zuluman tangotango <[email protected]> |
To: |
|
Sent: |
Monday, May 21, 2001 2:42 AM |
Subject: |
Simulator training |
Hi, I would like some information on if I can get a full Simulator Training on a Boeing or Airbus even if I am not a Commercial Pilot. I am doing my PPL, but my dream is to fly one of these big Bird (of course in a simulator). Will you consider me even if I have not pass all the exam, I know it is a bit peculiar, but I am 33 years so a bit late to start a pilot career and the school where I do my ppl now told me he will take me two year before being a full qualified atp pilot. But for the moment I just want the experience to Fly.
Ultimately, it was the Pan Am International Flight Academy that provided Moussaoui with training on a flight simulator:
From: |
|
To: |
zuluman tangotango <[email protected]> |
Sent: |
Wednesday, July 11, 2001 5:57 PM |
Subject: |
Home address for 747 manuals |
Zac;
I need the shipping address for your manuals. Operations want to send on thursday, July 12.
Please email or call with the address on thursday.
Thank you
The Pan Am International Flight Academy still provides flight simulator training today, according to its website (www.panamacademy.com).
A copy of a receipt from a store called Sporty’s, located in Batavia, Ohio, was also admitted into evidence. The receipt indicates that two VHS video tutorial tapes on the Boeing 747-200 and Boeing 747-400 were shipped to Moussaoui in Norman, Oklahoma, in June 2001. Receipts detailing payments to the Pan Am International Flight Academy were also produced at trial.
In August 2001, Moussaoui traveled to Eagan, Minnesota, to attend the Pan Am International Flight Academy. A hotel receipt for Moussaoui’s stay at the Residence Inn, from August 11 to August 17, 2001, in Eagan, Minnesota, was admitted into evidence.
From a computer forensics perspective, this case is important because much of the prosecution’s declarations depended on digital evidence. The case is interesting because it also highlights the types of objections that defense counsel can raise. Ultimately, the judge dismissed the objections made by Moussaoui’s defense counsel relating to the digital evidence provided by the prosecution.
BTK (Bind Torture Kill) Serial Killer
When reviewing cases involving digital evidence, it is important to understand that these cases also rely on traditional investigative techniques. The BTK (bind torture kill) case clearly illustrates how old-fashioned investigative skills were supported by digital evidence in capturing and convicting the perpetrator of these heinous crimes.
Profile of a Killer
Dennis Lynn Rader was born in Pittsburg, Kansas, on March 9, 1945. Rader grew up in Wichita, Kansas and attended Wichita Heights High School. After a brief stint at Wichita State University, he joined the U.S. Air Force. He left the Air Force to study at a couple of colleges, but he ultimately returned to Wichita State University. Ironically, he graduated with a major in the administration of justice, in 1979. Rader’s employment history included a part-time position in the meat department at an IGA grocery store and a job as an assembler at the Coleman Company, and he spent time working as an installation manager at ADT Security, where he had access to many homes, from 1974 to 1988. From 1990 to 2005, he was a supervisor for the Compliance Department at Park City.
Rader was also a father of two and, for three decades, was a member of the Christ Lutheran Church, where he was later elected president of the Congregation Council. Rader was even a Cub Scout leader. Yet even as he taught many kids how to tie knots, he plied his own trade when he bound, tortured, and killed his victims.
Rader began his serial killing on January 15, 1974, when he killed four members of the Otero family in Wichita, Kansas. He went on to kill another six people. He strangled his final victim, Dolores Davis, age 62, with pantyhose on January 19, 1991.
Evidence
In March 2004, Rader began sending letters and packages to the local media describing his victims. Some of the packages actually included items belonging to the victims, to prove that he was the killer but still remained anonymous. Rader left one of these packages, a cereal box, in the bed of a pickup truck at a Home Depot. However, the owner of the vehicle discarded the box as trash. When Rader asked members of the media about the evidence, they had no knowledge. He subsequently went back to the Home Depot and retrieved the box from the trash. Investigators were later able to review surveillance footage from the Home Depot and noticed a black Jeep Cherokee returning to the scene to retrieve the evidence. This became a clue in the case. In 2005, Rader left a Post Toasties cereal box on a dirt road north of Wichita.
Rader then asked the police if it was possible to trace information to a floppy disk. Police posted their response in the Wichita Eagle newspaper by stating that it was “OK” to use a floppy disk. On February 16, 2005, an envelope arrived at KSAS-TV in Wichita. The package contained a translucent purple Memorex 1.44MB floppy disk. Randy Stone, from the Forensics Computer Crime Unit of the Wichita Police Department, examined the contents of the disk using EnCase forensics software. The disk contained one file, called Test A.rtf. The file metadata showed “Dennis” and Wichita’s “Christ Lutheran Church”. An Internet search then quickly indicated Dennis Rader as the suspect they would now search for.
Law enforcement began to monitor Rader and his residence. They noticed a black Jeep Cherokee parked outside the Rader residence. Investigators were then able to retrieve DNA from a Pap smear belonging to Rader’s daughter from a sample at the University of Kansas medical clinic. The DNA from the Pap smear was a match to the DNA found on one of the victims, thereby proving that the murderer was a member of the Rader family.
On February 25, 2005, Dennis Rader was arrested by a task force of agents from the FBI, the KBI, and the Wichita Police. In June 2005, Rader pleaded guilty and was sentenced to 10 life sentences. He is currently serving time at the El Dorado Correctional Facility.
Cyberbullying
Cyberbullying has become an epidemic in the United States and many other countries. The difference between cyberbullying and traditional bullying is that, years ago, when a child was bullied in the schoolyard, he or she could go home at the end of the day and escape the taunts of peers. Today, however, the taunting continues with the use of the Internet and cellphones. Unfortunately, many states have been slow to enact anti-cyberbullying laws, and much of this legislation has come as a result of a suicide. Statistics infer that the issue is a bigger problem with girls than with boys.
Federal Anti-harassment Legislation
47 USC § 223 is an anti-harassment act aimed to prevent those who use telecommunications from transmitting “any comment, request, suggestion, proposal, image, or other communication which is obscene or child pornography, with intent to annoy, abuse, threaten, or harass another person.”
State Anti-harassment Legislation
HB 479, The Offense of Stalking, is an act passed by the state of Florida that explicitly prohibits cyberstalking. It defines the term cyberstalk to mean communication by means of electronic mail or electronic communication that causes substantial emotional distress and does not serve a legitimate purpose. It includes within the offenses of stalking and aggravated stalking the willful, malicious, and repeated cyberstalking of another person. It also provides penalties and revises the elements of the offense of aggravated stalking to include placing a person in fear of death or bodily injury of the person or the person’s child, sibling, spouse, or dependent.
Numerous states, including Alabama, Arizona, Connecticut, Hawaii, Illinois, New Hampshire, and New York, prohibit harassing electronic, computer, or email communications.
Warning Signs of Cyberbullying
Warning signs generally arise when a child is being bullied. Signs can include the following:
Feelings of anxiety, sadness, or hopelessness;
A decline in school grades;
Diminishing interest in social and recreational activities;
Upset behavior after leaving a computer or cellphone;
Excessive use of digital devices;
Irregular sleep patterns; and
Changes in weight or loss of appetite.
What Is Cyberbullying?
Cyberbullying is not simply sending harassing emails or nasty text messages. Many forms of intimidating communications fall under this category:
Images and video: Cyberbullies commonly use social media sites such as Facebook to post images and videos in attempts to embarrass other children.
Sexting: In sexting, an individual illegally shares a sexually explicit image, usually via MMS from a cellphone. If an adult becomes involved and images of minors are being shared, charges of possession or distribution can ensue.
Outing: Outing occurs when an individual publishes confidential personal information online or shares it in an email to embarrass another individual.
Flaming: Flaming is online arguing, often including vulgar and offensive language to denigrate another person.
Bash boards: Bash boards are online bulletin boards used to post hateful comments about peers or teachers that people dislike. Twoo.com, formerly Spring.me, is a website often connected with Facebook that has been used as a bash board.
Tricking: Tricking is the process of duping an individual into divulging personal comments, with the intent to publicly publish those secrets to humiliate another individual.
Happy slapping: Happy slapping occurs when people organize to physically harm another person and also video the abuse and later post the content online or send it to others. The proliferation of smartphones has facilitated a disturbing growth in these types of attacks.
Online polls: Online polls are used to get classmates to vote on certain topics, such as the ugliest student in class.
Impersonation: Impersonation is when a person either illegally breaks into another person’s account and pretends to be that person or sets up a fake page purporting to be someone else.
Phoebe Prince
On January 14, 2010, Phoebe Prince, a 15-year-old who had immigrated to South Hadley in Massachusetts, from the West of Ireland, committed suicide after being consistently bullied by other teenagers. Unbelievably, highly disrespectful comments were posted to her Facebook memorial page after her death. Six teenagers were charged as adults with a variety of felony charges, including statutory rape, stalking, and assault with a deadly weapon. Like so many other cyberbullying cases, the perpetrators got off lightly—some with probation or community service. Nevertheless, the state legislature enacted Senate No. 2404, an anti-bullying law.
Ryan Halligan
Ryan Halligan, a middle school student from Vermont, was another victim of cyberbullying who committed suicide. Many of the nasty messages sent to him were inadvertently archived on his computer through an application known as DeadAIM. In the aftermath of his death, in 2004, Vermont enacted a Bullying Prevention Policy Law and, later, the Suicide Prevention Law (Act 114) in 2005.
Megan Meier
Megan Meier was a 13-year-old student from Ostmann Elementary School, in Missouri, who committed suicide by hanging herself. Lori Drew, a 47 year old, posed as a boy named Josh Evans. She created a fake MySpace page and befriended Megan. In the case of United States vs. Lori Drew, Drew was charged with the following:
Indicted on Charge of Conspiracy (Violation of 18 U.S.C. § 371)
Infliction of emotional distress (Violation of 18 U.S.C. §1030(a)(2)(c))
Computer Fraud & Abuse Act (CFAA)
Breach of MySpace Terms of Service Agreement
After becoming good friends online, “Josh Evans” (Lori Drew) began to send hurtful comments to Meier, which many believed led Megan to commit suicide. Josh Evans sent comments such as “everybody hates you” and the “world would be a better place without you”. Evans communicated first via MySpace but later through AOL IM. The trial culminated with Lori Drew ultimately being acquitted, without serving any jail time.
In the wake of Meier’s death, the City of Florissant, Missouri, changed the cyber-harassment law from a misdemeanor to a Class D felony. Proving that cyberbullying ultimately led to suicide is always challenging.
Tyler Clementi
On September 22, 2010, a distraught 18-year-old Rutgers student ended his life by throwing himself off the George Washington Bridge. The unfortunate case of Tyler Clementi highlights the importance of digital evidence in bullying cases. Clementi was from Ridgewood, New Jersey. Just before committing suicide, Clementi checked Dharun Ravi’s Twitter account for the 59th time. Sadly, he then posted one last message on his Facebook profile: “Jumping off the gw bridge, sorry”.
Ravi was Clementi’s roommate, and he had secreted a webcam in their dorm room to capture Clementi’s intimate encounters with another man, intending to stream the video over the Internet on September 19. He then viewed the video from a friend’s dorm room across the hall. Ravi apparently encouraged others to invade Clementi’s privacy and watch the video. Prosecutors contended that Ravi intended to use the video to humiliate his gay roommate. Ravi’s tweets on Twitter clearly illustrated his intent to do just that, with Twitter messages informing his friends that he was in a dorm mate’s room, watching a video of Clementi “making out with a dude”. Ravi intended to set up yet another video of an intimate encounter of Clementi when he tweeted, “Anyone with iChat I dare you to video chat me between the hours of 9:30 and 12. Yes, it’s happening again”.
Digital Evidence Used at Trial
Gary Charydczak, a computer forensics examiner from the Middlesex County Prosecutor’s Office, gave testimony at the trial. Charydczak had examined the hard drive from Clementi’s blue laptop, seized from his dorm room. He discovered tweets on his laptop with the names untitled.jpg and secondtime.jpg.
Text message exchanges were also discussed at trial. Michelle Huang texted Ravi, “Watch out, he may come for you when you’re sleeping”. Ravi responded that his computer would alert him if anyone used his bed, noting, “It keeps the gays away”.
Charydczak also noted a number of Internet searches conducted by Ravi between August 21 and 23 to determine whether his new roommate was homosexual. Ravi searched YouTube and Facebook to determine his sexual orientation, and there were 20 AOL instant messages discussing the topic. This evidence was important to support the charge of a bias crime.
Prosecutors also disclosed evidence that they had uncovered related to the videos streamed across the Internet. An examination of Molly Wei’s computer produced video chat files and AOL IMs relating to the tryst; Molly Wei’s computer was used by Ravi to view Tyler Clementi in his dorm on that fateful night. Under oath, Wei had confirmed the events that had occurred with the webcam. Timothy Hayes, an IT administrator at Rutgers, affirmed the claim that Ravi’s computer was used for two video chats on September 21. Charydczak testified that the computers of Molly Wei and Dharun Ravi contained video chat evidence from the same time that Wei stated she had witnessed Tyler Clementi kissing another man.
The Verdict
In March 2012, Dharun Ravi was found guilty of invasion of privacy and four counts of bias intimidation. He was also found guilty of tampering with evidence, tampering with a witness, and hindering apprehension. After declining a plea deal, Ravi was imprisoned, with the added potential of deportation. Molly Wei was granted leniency in return for her cooperation with the investigation, but she was still ordered to perform 300 hours of community service, undergo counseling, and obtain training in cyberbullying and alternative lifestyles.
Note
Doxing is the process of gathering personal information about an individual and then making that information publicly available. The word doxing is derived from documents (.doc). For example, in the Occupy L.A. protests, some protesters felt that they were manhandled by the Los Angeles police. In response, the hacktivist group CabinCr3w posted the personal information of more than two dozen police officers, including political contributions, property records, names of children, and other very personal information.
Sports
One might wonder how computer forensics could be linked to sports and, more specifically, Major League Baseball (MLB). In 2006, the government initiated a highly publicized investigation involving the alleged use of steroids by a large number of high-profile players. Player David Wells stated that many players were using steroids, and Jose Canseco, Alex Rodriguez, Mark McGwire, Barry Bonds, Jason Giambi, and others came under the spotlight for use of performance-enhancing drugs (PEDs).
Former Senator George Mitchell was appointed to lead an investigation into the use of steroids in professional baseball. The report indicated that the use of PEDs was rampant among players in MLB. Naturally, if you want to find out who is using steroids, you go to the source. Thus, federal investigators focused largely on one particular supplier to MLB players: the Bay Area Lab Cooperative (BALCO). The MLB Players Association agreed to allow “suspicionless drug testing” of its players, with the names of the players to remain anonymous. Comprehensive Drug Testing (CDT) conducted the urine tests of the players. Under the program, federal investigators learned of 10 players who had tested positive. The government then obtained a grand jury subpoena seeking all drug testing records and specimens. The players’ union sought to quash the subpoena. Subsequently, the government obtained a warrant to search CDT’s premises. The search was limited to the records of the 10 players for whom probable cause had been established. However, when government agents executed the warrant, they seized and reviewed the records of hundreds of MLB players. The records seized were computer records that were at the heart of a rehearing of the case en banc by the Ninth Circuit Court of Appeals. The term en banc refers to all members of an appellate court hearing an argument rather than just the required quorum.
Government agents seized computers, hard drives, and other storage media. They argued that they could not decide, on the spot, which computers or storage media contained evidence pertaining to the 10 players in question, and therefore they had seized all storage devices. They also argued that because information pertaining to the players in question could be in non-descript files or folders, they would need to review all the files.
The three-judge panel opined:
We disapproved the wholesale seizure of the documents and particularly the government’s failure to return the materials that were not the object of the search once they had been segregated. Id. at 596-97. However, we saw no reason to suppress the properly seized materials just because the government had taken more than authorized by the warrant.
Furthermore, government agents refused the offer of CDT to provide information directly related to the 10 suspects. Government investigators also failed to redact evidence seized on the players who were not a part of the investigation. However, the judges did acknowledge the challenges associated with electronic evidence and the potential of suspect data to be intermingled with those not party to an investigation.
Summary
Digital evidence was key to the successful prosecution of Ross Ulbricht, who made millions in commissions from sales on the Dark Web marketplace called Silk Road. The evidence included investigators analyzing Bitcoin transactions from Ulbricht’s laptop and matching those transactions to the Blockchain (public ledger). Additionally, the laptop evidence indicated that Ulbricht had not abandoned the site, as the defense had claimed, and even maintained a journal that recorded his daily activities.
Computer forensics is clearly not limited to computer crime or cybercrime but encompasses a host of criminal investigations. The use of digital evidence in the Zacarias Moussaoui trial was necessary as corroborating evidence on both his intentions and the events that led up to 9/11. Documents from the trial provide tremendous insight into the use of expert witness testimony by computer forensics experts. Moreover, the objections by defense counsel and the rebuttal by the government investigator clearly illustrated how important the process by which digital evidence is acquired, handled, and analyzed is to the successful admittance as evidence at trial.
Murder investigations often rely on digital evidence to catch and convict suspects. The case of the BTK Killer is an excellent example of how digital evidence and old-fashioned investigative skills are equally important in apprehending and successfully convicting a criminal.
Sadly, cyberbullying is here to stay, and growth in the use of computers and cellphones will continue to make it a priority for many investigators. The case of Tyler Clementi underscores how multiple sources of digital evidence are pivotal to the successful conviction of perpetrators who use technology to facilitate their ambitions to humiliate and denigrate others. Computers and devices belonging to Clementi and other students were examined, records from online service providers were gathered, and even the university’s IT administrator was called upon to provide corroborating evidence at trial. Although cyberbullying continues to menace many people, the good news is that the scope of the digital evidence trail is far reaching, and states have enacted more laws to bring the perpetrators to justice.
Finally, the investigation by federal agents into MLB player use of performance-enhancing drugs clearly illustrates how computers and digital evidence are now used in every type of investigation imaginable. The case study also highlights how difficult cases that involve digital evidence can be highly problematic, given the narrow scope of a warrant garnered to investigate a computer or device on which only a few files out of millions of files might actually pertain to a suspected criminal act.
Key Terms
bash board: An online bulletin board used to post hateful comments about peers or teachers that people dislike.
doxing: The process of gathering personal information about an individual and then making that information publicly available.
en banc: Refers to all members of an appellate court, rather than just the required quorum.
flaming: Online arguing, often used with vulgar and offensive language, to denigrate another person.
happy slapping: People organizing to physically harm another person and also video the abuse and later post the content online or send to others.
impersonation: When a person either illegally breaks into another person’s account and pretends to be that person or sets up a fake page purporting to be someone else.
online polls: Polls used to get classmates to vote on certain topics, such as the ugliest student in class.
outing: Publishing confidential personal information about others online or in an email, to embarrass another individual.
pro se: Refers to someone who advocates for him- or herself and does not use legal representation.
sexting: Illegally sharing a sexually explicit image, usually via MMS from a cellphone.
standby counsel: A lawyer who assists a client who has invoked his right to self-representation.
tricking: The process of duping an individual into divulging personal comments, with the intent to publicly publish those secrets to humiliate another individual.
Assessment
Classroom Discussions
1. What objections did Ross Ulbricht’s defense counsel raise before and during trial?
2. Why were there quite a number of supporters of Ross Ulbricht during his trial?
3. How can you recognize a child who is a victim of cyberbullying, and how can you help?
4. What type of digital evidence can be used in a cyberbullying investigation?
Multiple-Choice Questions
1. Which of the following best describes sending a sexually explicit MMS on a cellphone?
Flaming
Happy slapping
Tricking
Sexting
2. Which of the following refers to someone who advocates for him- or herself and does not use legal representation?
Pro se
En banc
Impersonation
Certiorari
3. Which of the following describes convincing a person to provide confidential information, with the intention of later publicizing the information to embarrass the person?
Tricking
Happy slapping
Online polls
Flaming
4. Much like a blog, this online service is specifically used to post hateful comments about peers or teachers that some people dislike.
Online poll
Bash board
User group
Social media
5. Which of the following terms refers to all members of an appellate court hearing an argument rather than just the required quorum?
En banc
Certiorari
Per curiam
Per se
Fill in the Blanks
1. When an individual publishes confidential personal information with others online or in an email to embarrass another individual, it is known as __________.
2. A group that organizes to physically harm another person and then video the event to share with others is involved with __________ __________.
3. __________ occurs when a person breaks into another person’s account and pretends to be that person.
4. Arguing online with another person using obscenities is called __________.
5. When peers are asked to rank who they believe to be the ugliest in the class online, the peers are asked to contribute to an online __________.
Project
Analyze a Cyberbullying Case
The following is a made-up cyberbullying case study for you to read, analyze, and discuss in your class. Although the case is not real, you could very well imagine something like this taking place.
Scenario
A 16-year-old girl by the name of Jenny Foster was found hitchhiking along the Adirondack Mountains Highway in upstate New York. Mr. David Sykes, a driver on the highway, stopped to pick up the prospective passenger. Realizing that the hitchhiker was a scared, shivering young girl who had just run away from home, he drove Jenny to the local police station, where his brother-in-law was a police officer. The officer, Lt. Todd Gallagher, provided Jenny with a blanket and a mug of hot cocoa. While recuperating, Jenny told the officer that she had run away from home and was on her way to New York, where she knew an old school friend was now living. She was going to stay with her for a few weeks while she found a job as a waitress. The police officer asked for Jenny’s home telephone number to call her parents. After a few attempts the officer was able to reach Jenny’s parents, who were frantically searching for her and calling her friends’ houses.
The officer assumed that she had a disagreement with her parents, but in Jenny’s case, it was quite the opposite: Jenny loved her parents but felt that nobody else loved her. When questioned why she had left home, Jenny cried and said, “I wish I was dead. I have been thinking about killing myself because my so-called friends told me that I’d be better off dead”. She also confided in them that Rachel, one of her former friends, had posted a message on Facebook stating that she would be happy to push Jenny into oncoming traffic to help her end her “pathetic life”. The police officer was startled by this and asked Jenny if she minded if he took notes. She responded that she had no problem with this. The police officer then said that he wanted to bring in another police officer, Det. Margaret Schultz, to accompany them. Jenny did not object, and Det. Schultz joined them. Jenny continued to talk about herself. She felt that she was different from everyone else in the class. She had no brothers or sisters, and her family had recently relocated to the area after her father had been laid off from his job as an electrician. She explained that her mother had a part-time job at Target and that her father was only getting handyman jobs here and there; it was a real struggle in their house to make ends meet.
The police officer asked why Jenny was so upset and felt so alone in the world. She explained that she was continually taunted by friends at school, but it had not always been like that.
She proceeded to tell them that her mother used to be a secretary, but when her old company’s regional dealership folded, her boss had allowed her to take home the office computer. Luckily for Jenny (or unluckily, as it turned out), the family was able to access a Wi-Fi Internet connection. Therefore, like many teenagers, Jenny used Facebook after doing her homework, eating dinner, and washing up. She admitted that she spent a lot of time on the computer complaining about homework and chatting about boys in the class, mainly those on the school’s football team. She had befriended a group of girls who were cheerleaders for the team. However, Jenny was not part of the cheerleading squad. Jenny explained that another big difference between her and these girls was their economic situation. These girls all came from affluent homes, yet Jenny’s family was struggling to make ends meet.
According to Jenny, everything was great when she first started school, but then for no apparent reason, her friends started tormenting her. Everything started to go wrong after Jenny brought one of her friends over for dinner. Her friend was very surprised that Jenny lived in a small one-bedroom apartment and did not seem too happy that meatloaf and water was the menu for dinner. From that day on, Jenny noticed that things changed between her and her so-called friends. Gradually, the other girls began to say really hurtful things to Jenny. Now they knew that her family did not have a lot of money, so they purposely planned outings to expensive shops to buy clothes and made arrangements to go skiing, knowing that Jenny could not afford to join them. But things got worse when Jenny started going out with Brad Smalls, an 18-year-old senior who was the captain of the football team. Jenny explained to the officers that they had dated for a little while, but she had broken up with him because he had taken an inappropriate photograph of her with his BlackBerry and refused to delete it, despite her requests.
One of the cheerleaders, Charlene Davis, found out that he had this picture and asked Brad to forward it to her cellphone and email, which he did. Soon the picture was all around the school. In fact, Jenny saw Charlene and Jillian making copies of the photograph in the school’s library but was too afraid to confront them or report them. (Students were allocated 150 copies every semester through their student ID card.) Within days, the picture was posted in the girls’ bathroom and in the boys’ football changing room. Jenny removed the picture from the girls’ bathroom but heard that the picture in the boys’ changing room stayed up for weeks. Jenny had hoped the football coach would take the picture down, but that was not the case. Eventually, the photo ended up on Facebook. Jenny told the officers she had been so embarrassed and humiliated that she had worn a hat and glasses to school so that people would not recognize her. She dreaded going to school so much that she would get physically ill in the mornings. She had always been an honor student, but because of all the terrible things that were happening to her, she could not focus on her school work and even avoided going to class. She often ended up in detention on purpose so that she did not have to deal with those heartless cheerleaders.
Jenny shared with the officers that, one day, the cheerleaders asked her if she wanted to be friends with them again and go to the local diner for a milkshake. Jenny reluctantly agreed. Her initial instinct to not go with them had been correct: The trip to the diner had been a setup. She recounted the events of that afternoon: “They were all smoking, and the next thing I heard was ‘Now’ and then they stubbed my head and arms with their cigarettes. I cried, ran home, and luckily didn’t have to answer any questions because my parents were still at work. I couldn’t sleep that night and cried all night. The next day, I saw the nurse. She asked me about the marks on my body, and I told her what had happened. I also asked her not to say anything. She agreed, and as far as I know, she never said anything to anyone.”
Jenny told the officers that, the day after the diner, she had received taunting text messages and emails about the incident. When she got home, there were messages on Facebook about how she should kill herself and how they would help her do it. “That’s when I read Rachel’s posting about pushing me into oncoming traffic”, Jenny told the officers. Her mother had come home one night and found Jenny in tears. Jenny had told her mother about the emails, cellphone texts, and postings on Facebook. She had showed her mother her Facebook page and the emails she had received through her Yahoo! account. Her mother had taken a screenshot of the Facebook messages and printed the emails. After her mother printed the emails, Jenny deleted all of them because she did not want to see them ever again. Jenny could not show her mother all the harassing text messages because she had deleted them as soon as she had received them. “Anyway, my mother wouldn’t understand some of them because kids have a different language when texting—a language that adults simply don’t understand”, Jenny explained to the officers. She then proceeded to tell them that Brad had created a Facebook page about her, with that infamous photograph, and said Jenny liked to sleep around. Jenny broke down in tears as she said, “He even said that I was open to visits at my home and listed my address. I was sickened and very frightened.”
Jenny then continued with her story and said her mother had given the screenshots and printed emails to the assistant principal. At the meeting with the AP, Jenny not only mentioned the incident with the cigarettes, but also related how these students would trip her in the hallway, put chilies in her food, and pull her hair. “My mother was surprised and upset to hear all of this because I had never mentioned any of this before”, Jenny shared with the officers. Jenny also told them that she had been disappointed with the meeting because the assistant principal was not particularly interested in what had been happening to her. His response to Jenny’s allegations had been dismissive, to say the least: “I agree that these kids have been misbehaving, but this is 2010 and the world has changed—kids will say anything on Facebook. Look, they don’t have access to Facebook in the school, so we cannot be held responsible. What students do on their own time is not my business, and it’s actually your responsibility.” Jenny told the officers that her mother had shown the AP a couple of emails in which her life had been threatened. Jenny remembered very clearly the AP’s response: “This isn’t really evidence because these are not actual emails. How do I know that someone didn’t edit these? Tell me the truth—when you were a kid, did you ever say ‘I wish so-and-so was dead’? Frankly, Mrs. Foster, I’m more concerned about your daughter, who keeps ending up in detention every other day.” Jenny also remembered that her mother was annoyed with her because she did not know about her frequent visits to detention, since she was working most evenings.
At that point, Jenny’s parents arrived at the police station. They were happy to see Jenny and thankful to the police officers, but when Jenny’s father heard that they had interviewed Jenny and taken notes, he was very upset and said to the officers, “You have no right to take a statement from my daughter. I know my rights, and you need the consent of her parents before questioning my daughter.” The detective explained to Jenny’s father that the conversation had been very informal, that she had just talked and they had listened. They reassured him that they only wanted to help. The detective told Jenny’s parents that she believed they should refer the matter to the district attorney’s office to determine whether there was a case against the students or the school.
Scenario Considerations and Discussion
1. Did the police act appropriately by taking notes while they waited for Jenny’s parents to arrive?
2. Did the police require parental consent before speaking to Jenny?
3. Were Jenny’s Miranda rights violated? Research what the Miranda warning is.
4. Was it a good idea to bring a detective into the same room?
5. Are the email printouts made by Jenny’s mother admissible as evidence in this case?
6. How could the emails be authenticated?
7. What, if any, objections could be raised regarding the admissibility of the emails?
8. Is the snapshot of the Facebook page admissible as evidence in this case?
9. Did the school act appropriately? Could they be found negligent?
10. Are Brad’s and the cheerleaders’ actions protected under the First Amendment?
Legal Action Taken by the Prosecution
The Farmville County District Attorney has decided to prosecute the following people:
Brad Smalls, senior (former boyfriend)
Charlene Davis, sophomore (and football cheerleader)
Rachel Vasquez, sophomore (and football cheerleader)
Jillian Kopley, sophomore (and football cheerleader)
The district attorney has also taken an extraordinary move to prosecute the school and its administrators.
Defendant Statements to the Media
School Spokesman Statement
“The school is shocked by the unprecedented charges against the school and its administration. The school is not responsible for the actions of its students after school hours. The incident of injury to the student occurred outside the school. The intimidating emails, text messages, and Facebook postings noted in this case were beyond our control and were never reported by the victim. It was only when we spoke to the victim’s mother that these transgressions came to light. We did issue a warning to the perpetrating students. With regard to the issue of a photo being posted in the football changing room, the football coach did not post any photos and is not liable for the posting of such images. The victim never mentioned this in our conversation, otherwise, we would have removed the image, and the student responsible would have been suspended from school.
The school’s administration now feels that they are the ones being bullied. The school has very strict policies when it comes to bullying and has zero tolerance for this kind of behavior. In summary, we were never a part of this bullying and should not be singled out. In time, it will become clear that respect, honesty, and integrity are three principles that we live by. We will be proved innocent and our reputation will remain untarnished.”
Defense Attorney (Brad Smalls)
“My client’s name and reputation have been smeared. It will soon become apparent that Jenny Foster is a misguided child. Foster is relatively new to the area. Her poor parents were out working most evenings and were unable to supervise their daughter’s use of the Internet. This is a girl who simply wanted some attention. This case will demonstrate that Jenny Foster, a student who spends more time in detention and on Facebook than studying, needs some guidance and direction in her life, and I really hope that she gets better and gets the professional help that she needs. This case will never go to trial, and I hope that my client, an honors student, can get back to focusing on his studies as quickly as possible.”
Case and Evidence Considerations
1. Jenny Foster deleted her emails, and the email printouts are in some file in the assistant principal’s office. Can anything be done?
2. Could the school be found negligent? On what basis?
3. What charges do you think the district attorney would make against the school?
4. What charges do you think the district attorney would make against Brad Smalls?
5. What charges do you think the district attorney would make against Charlene Davis, Rachel Vasquez, and Jillian Kopley?
Assignment
Create two teams: (a) Prosecution and (b) Defense. A judge should preside over the case. Reenact the ensuing court case as you anticipate it would happen.
Assessment of Cases by Judges
Each team will be adjudicated by a panel of judges who have technical and legal expertise. The panel will judge the teams based on the following criteria.
I. Technical Ability
1. Detailing the evidence to be used in the case
2. Detailing the admissibility of the evidence
3. Detailing how the evidence was acquired and handled
4. Warrants issued
5. Subpoenas issued
II. Legal and Presentation Skills
1. Detailing the charges being brought by the prosecution
2. Detailing the prosecution’s arguments
3. Detailing the defense’s arguments
4. Detailing the prosecution’s objections and cross-examinations
5. Detailing the defense’s objections and cross-examinations
6. The judge’s facilitation of court proceedings
