Chapter 8
Network Forensics and Incident Response
Learning Outcomes
After reading this chapter, you will be able to understand the following:
The importance of network forensics;
Hardware devices that contain network logs that are valuable to a forensic examiner;
IPv4 and IPv6;
The OSI Model;
Mistakes made when investigating networks;
Windows artifacts;
Advanced persistent threats: perpetrators, vectors of attack, and indicators of compromise; and
How to investigate a network intrusion.
Network forensics is extremely important, but very few people understand it. This domain of forensics is so important because of the explosion in network breaches. The Sony PlayStation breach in 2011 alone is estimated to have cost the company $170 million when more than 100 million customer records were compromised. The NotPetya ransomware attack of 2017 cost Merck as much as $1.3 billion. As a nation, we have relied on security and general information technology personnel to handle these incidents. However, with so much at stake, in terms of financial liability and bad publicity, it is imperative that organizations think more in terms of in-house forensics investigators who have the legal and technical expertise to adequately handle these breaches, especially with the risk of civil lawsuits.
The lack of expertise in the community stems from the fact that forensic examiners focus on client computers and devices during investigations and obtain server-side evidence from a variety of service providers. For example, when Hotmail email messages are required, only a court order is needed to obtain the records. The method by which this evidence is retrieved is irrelevant. Additionally, the prevalence of advanced persistent threats (APTs) means that there is a greater need for network forensics examiners. These examiners need to understand a very different file system, operating system, and type of evidence. The abbreviation APT includes the word advanced, meaning that attacks on networks are more sophisticated, with tremendous resources supporting them, and are allegedly supported by national governments, like China.
The success of economies that rely on digital information, such as the United States, will remain intact only if competent network forensics investigators are effectively trained and hired in government and corporate organizations. Universities that conduct research for the Department of Defense and other government agencies, as well as law firms that house vast quantities of intellectual property during civil litigation cases, are prime targets for government-sponsored attackers. More recently, we have read about managed service providers (MSPs) being compromised as an effective means to access related networks. A managed service provider (MSP) generally provides IT infrastructure services, like cloud storage, to an organization.
Finally, we should not think of network forensics as simply being associated with organizations. Home networks have grown in importance tremendously. For example, think about the “Apple Environment”, which can be comprised of a Mac computer, an iPad, Apple TV, HomePod, and iCloud. A home router can be compromised to provide an attacker with a device from which to sniff traffic and modify the DNS (Domain Name System).
The subject of network forensics could take several textbooks to cover in depth. This chapter provides an overview of some of the main domains and key concepts associated with this subject.
Note
A network forensics investigator should understand the infrastructure of networks in terms of hardware and software. This knowledge will lead the investigator to know where the evidence is located.
The Tools of the Trade
There are two approaches to network forensics: (1) real-time capture and analysis, and (2) retroactive analysis of captured data. Tremendous resources are required to perform real-time analysis—you need very large storage and a lot of horsepower (RAM). To cater to the large storage requirement, you could use a RAID (redundant array of independent disks). Optimally, you will use a RAID 0, which allows for high performance, large storage, and low redundancy. Kali Linux is an open source Linux tool that is often used for real-time packet capture. However, numerous other network forensics and analysis tools also work, although many are quite expensive to purchase and maintain. These tools include the following:
EnCase Endpoint Investigator
RSA NetWitness
Kibana
Carbon Black
Splunk
These open source tools also work well:
tcpdump
WinDump
Xplico
Wireshark
Kismet
TCPflow
Ettercap
Traceroute
TCPtraceroute
NGREP
WGET
CURL
Packet sniffers are used to capture data packets on a wireless or wired network. Wireshark and tcpdump are examples of packet sniffers. The network interface card (NIC) only responds to packets addressed to its MAC address, but a packet sniffer puts the NIC into promiscuous mode. Promiscuous mode enables a NIC to listen to communications broadcast on a network, regardless of the intended recipient. Packet sniffers are used in conjunction with protocol analyzers by network forensics investigators. A protocol analyzer is used to analyze and interpret traffic over a network.
Networking Devices
When learning about network forensics, it is imperative to learn about devices that have logging capabilities and therefore contain historical evidence for investigators. Investigators must note all of the different system times for each networking server or device. In other words, data can be routed through several networking servers, and these server timestamps will differ from one another. A defense attorney might challenge prosecutors about this on the witness stand. All of the following network devices have logging capabilities:
Proxy servers
Web servers
DHCP servers
SMTP servers
DNS servers
Routers
Switches
Hubs
IDS
Firewalls
Proxy Servers
A proxy server is a computer that relays a request for a client to a server computer. This is important to know because a suspect might actually use another user’s computer, or multiple computers, as an intermediary to request information from a server. Therefore, investigators might seize a web server hosting illicit photographs of minors, but the client requests to download pages or images might show the IP addresses of unsuspecting individuals, who had their computers compromised by hackers. Squid is a caching proxy service that can be used to increase performance on a web server, by caching popular requests, and it can also cache DNS, Web, and network lookups. Web cache is of interest to forensics investigators because it can provide invaluable information about Internet activity through requests to a web server. Most proxies are web proxies. All traffic through Port 80, Port 8080, Port 80443, or Port 443 must go through a web proxy.
Web Servers
A web server stores and serves up HTML documents and related media resources in response to client requests. In other words, when you type a URL into your web browser, and then press Enter, a data packet is sent to that web server that includes your IP address. In turn, the webpage (HTML file and associated media files) is sent to your computer and saved in cache. For example, if you visit a friend’s Facebook page, you download the HTML profile page and any photos or videos (media files) embedded on that profile page. A forensics investigator can analyze client user requests from the web server logs.
When reviewing log files on a web server, the following information can be obtained:
Date and time
Source IP address
HTTP source code
Resource requested
There are several folders on a Linux computer that will be of interest to a forensics investigation, and they are as follows:
/etc: Contains system configuration files and some other file types.
/etc/passwd: Configuration file that contains local user information. You can find user login information in this file. The file uses data encryption standard (DES).
/etc/group: Contains user group information.
/etc/shadow: You can find user login password hashes here. The file is only readable by the root user.
/home: Location where all user home directories are created.
/.bash_history: Logs a history of all commands that have been run in the file.
/etc/ssh & /.ssh: Holds private and public keys for the host.
/var/log: Contains logs of several running services. On a web server this may be Apache (a popular open source web server software) or SSH (a cryptographic network protocol for securing network communications).
/var/www: Apache stores web server files and subdirectories in this folder.
/var/www/html: Stores the content of a website running Apache.
Uniform Resource Identifier (URI)
A Uniform Resource Identifier (URI) is used to locate a resource on the Internet. The most common type of URI is a uniform resource locator (URL), which consists of the following:
Transmission protocol (generally HyperText Transfer Protocol [HTTP])
Colon (:)
Two slashes (//)
Domain name, translated to an IP address
Resource HTML document or file, e.g., a .jpg file
Web Browsers
On the client side, a web browser is used to render the HyperText Markup Language (HTML). Before the advent of the web browser, File Transport Protocol (FTP) was used to download and upload files from servers on the Internet. Now we primarily use FTP to securely upload files to a web server. A web browser is used to (1) work with a DNS server to resolve DNS addresses, (2) make HyperText Transfer Protocol (HTTP) requests, (3) download resources, and (4) display the contents of the file with Browser Help Objects (BHOs). A Browser Help Object (BHO) is used to add functionality to a web browser; the object starts every time the user opens the browser. For example, an Adobe BHO allows users to view PDF documents within the browser window. A BHO is slightly different than a plug-in because it is specific to Internet Explorer (IE), and Microsoft provides an interface and guidelines for developers who wish to create a BHO. Microsoft Edge browser does not support ActiveX and BHO technologies.
HyperText Transfer Protocol (HTTP)
HyperText Transfer Protocol (HTTP) is a standard for requests and responses between a client and a server. HTTP contains common methods used for client-server requests. The following are referred to as “safe” methods:
GET: Retrieves the resource in the requested URI.
HEAD: Similar to the GET request but does not include the body of the file being requested. This can be used when testing a hypertext link.
OPTIONS: Requests information about the options that are available with communications involving the URI.
Certain client methods are potentially harmful to a server and include the following:
POST: Calls upon a server to accept an enclosed entity, which could be a file, in the request.
PUT: Requests that an entity at a specified URI be added.
DELETE: Erases a specific resource.
CONNECT: Can be used to allow Transport Layer Security (TLS) communications and also can be used to create an HTTP tunnel that circumvents firewalls and intrusion detection systems.
TRACE: Takes a request made by a client to be sent back by the client. However, TRACE can be used to trick a web browser into issuing a TRACE request to another site.
Status codes within HTTP inform the client about the status of a request or the server. For example, sometimes you enter a URL in your web browser and the browser displays an error code of “404”, meaning that the resource being requested (the website) was not found. This is probably because the user entered an incorrect URL, or perhaps the resource has moved. A 404 error might mean that the server does not wish to disclose the reason for a resource not being found. Here are some other common HTTP status codes for client errors:
400: Bad request
401: Unauthorized
403: Forbidden
405: Method not allowed
406: Not acceptable
407: Proxy authentication required
408: Request timeout
409: Conflict
410: Gone
Here are some examples of HTTP status codes on the server side:
500: Internal server error
501: Not implemented
502: Bad gateway
503: Service unavailable
504: Gateway timeout
505: HTTP version not supported
Scripting Language
It is important to understand how scripting languages on websites work. The vast majority of scripting languages have a legitimate purpose, like checking to see whether a client computer has an application installed (plug-in) to view embedded content, like Audacity for a sound file. Nevertheless, certain scripts can be malicious. Other scripts can be used by law enforcement to identify a suspect on a network who is using a proxy service. An investigator may be called upon to explain how scripts on a webpage were executed on a suspect’s computer, or perhaps the suspect was operating a web server with malicious or illicit content.
A script can run either on the client side or on the server side. Scripting languages, like JavaScript (the most popular), JScript, or VB Script, are embedded in HTML pages to enable dynamic elements and interaction. For example, a currency or temperature converter can be created with JavaScript and is interactive because it requests a number and then converts it (output) for the client (user).
Of course, some scripts run on the server side:
Python
PHP (
.php)PERL (
.pl)Java
Ruby
ColdFusion Markup Language (
.cfml)Active Server Pages (
.asp/.aspx/asp.net)
DHCP Servers
Dynamic Host Configuration Protocol (DHCP) is a standard for allowing a server to dynamically assign IP addresses and configuration to hosts on a network. This dynamic addressing means that a new client can join a network without having to possess a preassigned IP address. The DHCP server assigns a unique IP address, and then after a client leaves the network, that IP address is released and can be used for a new host that enters the network. DHCP means that a network administrator does not need to manually assign IP addresses and keep track of clients using those IP addresses but can have DHCP client software perform those tasks automatically. An Internet service provider (ISP) can use DHCP to allow customers to join its networks. Similarly, on a home network, a broadband router uses DHCP to add clients to its network—these can include a PC, a smart TV, a tablet, or a smartphone. At a minimum, a DHCP server provides an IP address, subnet mask, and default gateway. A subnet mask facilitates the communication between segregated networks. An IP address has two parts: network and host address. A subnet mask separates an IP address into network and host addresses. We will discuss subnetting in more detail later in this chapter. The default gateway is the node on a network that serves as the forwarding host (router) to other networks. For example, on a home network, the default gateway might be the broadband router.
A router maintains an ARP (Address Resolution Protocol) table, which is based on ARP requests and responses. When a packet is sent across the Internet, it is sent to the MAC address of the router interface that is the default gateway. ARP binds a static IP to a MAC address in a device’s ARP table. DHCP, on the other hand, always assigns the same IP address to a device. ARP is used to get the MAC address from an IP address and is primarily used on a LAN (Local Area Network).
The routing table contains the following:
Destination network IP addresses;
Destination gateway IP address; and
Corresponding interface.
When the router receives a packet, it will check for the destination network IP address in the routing table. If the packet is destined for a network that is directly connected to the router, then the destination MAC address will be obtained from the ARP table. MAC addresses (Layer 2 of the OSI Model) are mapped to IP addresses (Layer 3) using ARP. ARP responses are cached on hosts that make up the LAN. The ARP cache can be queried on a Windows system to identify MAC—IP address mappings using the following command:
arp -a
You can view DHCP service activity on your personal computer by launching the Event Viewer application. As you can see in Figure 8.1, an event is created every time DHCP starts and stops.
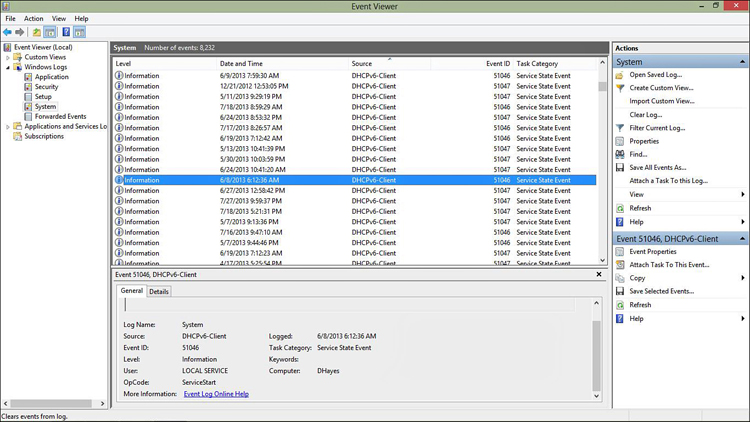
Figure 8.1 Windows Event Viewer: DHCP
DHCP is a client/server protocol that provides an IP host with an IP address and other configuration information, e.g. a subnet mask or default gateway. Static IP addresses are assigned to networking equipment, including routers, firewalls, and servers. Host computers, including tablets and smartphones are generally assigned a dynamic IP address.
An examination of DHCP logs will display the MAC addresses of devices that connected to a router. If an organization uses a DHCP server, then the logs, with MAC addresses, may be extensive. DHCP can be handled by a router or a server. You may be able to identify a DHCP server by monitoring traffic on Ports 67 and 68.
There are a number of known DHCP attacks, which includes DHCP poisoning and DHCP starvation. It is therefore important to understand that you might find evidence of this type of spoofing in DHCP logs. Thus, an attacker might impersonate a legitimate user, and therefore the investigator needs to be cognizant of this possibility.
Sometimes you will see the following messages in DHCP logs:
Message Use
------- ---
DHCPDISCOVER - Client broadcast to locate available servers.
DHCPOFFER - Server to client in response to DHCPDISCOVER with
offer of configuration parameters.
DHCPREQUEST - Client message to servers either (a) requesting
offered parameters from one server and implicitly
declining offers from all others, (b) confirming
correctness of previously allocated address after,
e.g., system reboot, or (c) extending the lease on a
particular network address.
DHCPACK - Server to client with configuration parameters,
including committed network address.
DHCPNAK - Server to client indicating client's notion of network
address is incorrect (e.g., client has moved to new
subnet) or client's lease as expired
DHCPDECLINE - Client to server indicating network address is already
in use.
DHCPRELEASE - Client to server relinquishing network address and
cancelling remaining lease.
DHCPINFORM - Client to server, asking only for local configuration
parameters; client already has externally configured
network address.
DHCP Logs
A DHCP server will log the following:
Startup
Shutdown
DHCP leases
DHCP assignments
DHCP requests
On a Linux DHCP server, leases are stored in the file dhcpd.leases, which can be found here:
/var/lib/dhcp/dhcpd.leasesThe configuration file is dhcpd.conf and can be found in the following directory:
/etc/The dhcpd.conf file will provide the following information:
Default lease time
Maximum lease time
Syslog* logging
Range of dynamically allocated addresses
Syslog is used by network devices to send event messages to a logging server.
Hub
A hub is a hardware networking device that broadcasts data packets to all devices on a network regardless of the MAC address. A hub is a Layer 1 (OSI Model) device.
Switch
A network switch is an intelligent hardware device that connects devices on a network. It is also referred to as a switching hub, bridging hub, or MAC bridge. The difference between a hub and a switch is that the latter only forwards packets to the required destination device on a network. A network switch operates at the data link layer (Layer 2 of the OSI Model), although some switches can also operate at the network layer (Layer 3 of the OSI Model). Content Addressable Memory (CAM) is a type of memory used by Cisco switches, and a CAM address table may be available for an investigator to analyze.
SMTP Servers
A Simple Mail Transport Protocol (SMTP) server is used to send email for a client. The email is subsequently routed to another SMTP server or other email server. For example, when you use Microsoft Outlook to send an email, this email application informs an SMTP server of the sender and recipient email addresses, as well as the body of the message. When sending an email to another domain (for instance, an email from Hotmail to Yahoo!), the SMTP server communicates with a DNS server and requests the IP address of the SMTP server. The DNS then responds with the IP address or addresses for SMTP servers that Yahoo! (in this example) operates. SMTP servers communicate with one another using simple commands, like HELO (introduction), MAIL FROM: (specify the sender), RCPT TO: (specify the recipient), QUIT (quit the session), HELP (get help), VRFY (verify the address), and DATA (To, From, Subject, Body of message). Internet Message Access Protocol (IMAP) allows the user to access email from just about any type of Internet-enabled device. With IMAP, the user’s email is stored on an email server, and when an email message is requested, it is only temporarily downloaded to the user’s device. Post Office Protocol (POP) is a different electronic mail standard because the email is stored on the user’s device, not on the server. Some email services, like Gmail, can be set as a POP or IMAP email service by the user.
Electronic Mail (Email)
Analyzing email requires some knowledge of network forensics. The following listing shows a sample email that we will analyze from a network forensics perspective. Comments explaining certain parts are explained after the example:
1) Received: (qmail 29610 invoked by uid 30297); 27 Jul 2013 19:13:41 -0000 2) Received: from unknown (HELO p3plibsmtp01-05.prod.phx3.secureserver.net) [ic:ccc] ([10.6.12.128]) 3) (envelope-sender <[email protected]>) 4) by p3plsmtp10-06.prod.phx3.secureserver.net (qmail-1.03) with SMTP 5) for <[email protected]>; 27 Jul 2013 19:13:41 -0000 6) Received: from co1outboundpool.messaging.microsoft.com ([216.32.180.188]) 16) Received: from mail22-co1-R.bigfish.com (10.243.78.243) by 17) CO1EHSOBE025.bigfish.com (10.243.66.88) with Microsoft SMTP Server id 22) X-Forefront-Antispam-Report: CIP:198.105.43.6;KIP:(null);UIP:(null);IPV:NLI;H: exchnycsmtp1.pace.edu;RD:none;EFVD:NLI 55) MIME-Version: 1.0 58) X-FOPE-CONNECTOR: Id%0$Dn%*$RO%0$TLS%0$FQDN%$TlsDn% 63) Hello 64) Dr. Sherlock Holmes | [email protected]<mailto:[email protected]> | Dir= 65) Assistant Professor | The Moors | (212) 555-1234= 66) | Fax (212) 555-1234 | Pace University, 163 William Street, New = 67) York, NY 10038 68) Visit Us Online: http://www.pace.edu/pace/seidenberg/ 72) <html dir=3D"ltr"> 73) <head> 81) 10pt;">Hello<br> 136) </body> 137) </html>
Line 1: This is the start of the email header. The reference to qmail refers to mail software running on UNIX. The email includes unique IDs that should correspond to IDs in the server logs.
Line 2: This lists the IP address of the receiving server, which is as follows:
p3plibsmtp01-05.prod.phx3.secureserver.net
When initiating communication, the client uses the HELO command with the SMTP server.
Line 3: This is the sender of the email.
Line 4: Once again, this indicates the name of the server receiving the email for the recipient and shows that the SMTP messaging protocol is being used in transmission of this email.
Line 5: Here you see the email address of the recipient, along with the date and time the message was received.
Line 6: The IP address 216.32.180.188 is displayed, with domain name of co1ehsobe005.messaging.microsoft.com. If you type 216.32.180.188.ipaddress.com into the browser, you can see that Microsoft hosts the server and that it is located in Chesterfield, Missouri.
Lines 16–17: You can see several references to BigFish.com, which is a Microsoft Exchange Server. You can check by visiting http://who.is/whois/bigfish.com/. You can therefore assert that the sender of the email is using Microsoft Exchange (Outlook).
Line 22: You can see that Microsoft Forefront (a cloud service to protect companies from viruses, spam, and phishing scams) software has inspected the email. You can also see that the email was sent by an email server at pace.edu (exchnycsmtp1.pace.edu), which corresponds later to the name of the sender—[email protected], noted in Line 41. This is important because it appears that this email has not been spoofed by the sender.
Line 55: You can see MIME noted. Multipurpose Internet Mail Extensions (MIME) is an electronic email protocol that extends character sets beyond ASCII and supports email attachments.
Line 58: This line includes a reference to FOPE-CONNECTOR. Microsoft Forefront Online Protection for Exchange (FOPE) has connectors for advanced email functionality.
Lines 63–68: These lines contain the body of the email.
Lines 72–137: These lines show the body of the message in an HTML format. If the sender had sent the message in plain text, this HTML code would not have been generated.
It should be noted that the header in an email can be spoofed. DomainKeys Identified Mail (DKIM) is a tool used to authenticate that a specific sender and domain, noted in the email, did in fact actually send an email.
DNS Servers
The Domain Name System (DNS) is a naming system for computers and other devices connected to the Internet. One function of DNS is to convert domain names to IP addresses. For example, the IP address for the domain name www.pace.edu is actually 198.105.44.27 (IPv4), but we use letter names because it is easier to remember when surfing the Internet. DNS servers are also referred to as nameservers. A DNS server will point a client to either the company that a domain was registered to or to the company that hosts their Website. Zone files contain the domain’s DNS settings.
DNS maintains different types of records. A primary “A” record is called “@” and this controls what your domain name does when a client visits your website. An “A” record provides the mappings between host names and IPv4 addresses. CNAMEs point your subdomains to a different server. “AAAA” records provide the mappings between host names and IPv6 addresses. “MX” records are mail exchange records, which are used to determine the priority of email servers for a domain. “PTR” records resolve an IP address to a domain name, which is the opposite of a client request to a server (domain name → server).
DNS is sometimes referred to as a query-response protocol. Generally, a client sends a request with a single UDP packet, and then the server responds with a single UDP packet. With larger systems, the server may respond via TCP.
As you can see in Figure 8.2, Windows Event Viewer records DNS resolution services.

Figure 8.2 Windows Event Viewer: DNS resolution service
The Hosts File
The hosts file is a text file found on Windows that maps hostnames to IP addresses. It is an operating system file. The host name may be mapped to both IPv4 and IPv6 addresses. Thus, the domain name resolution may occur on the host side. Sometimes a systems administrator may modify this file and the IP mappings. Unfortunately, hackers have also been known to compromise this file to redirect client computers. On a Windows PC (Windows XP and up), the file can be found here:
%SystemRoot%System32driversetchosts
On an Apple Macintosh, a similar file can be found here:
/private/etc/hosts
With DNS domains, there is a hierarchical structure. At the top are root nodes. Then we have “top level domain” nodes, e.g. .com, .net, .org. A top-level domain contains “domain nodes”, which are also referred to as “zones”, e.g., google.com. Within each domain there may be “sub-domains”, e.g. accounts.google.com.
DNS servers are referred to as “nameservers” and points a client to the company that controls the DNS settings, which is often the company that the domain name was registered to. Alternatively, the nameserver may be the company that hosts your website. A zone files are files that contains all of your domain’s DNS settings. A record will point your domain or sub-domain name to a specific server. There is always a primary A Record called “@” and controls what actions your domain name performs when a client visits. CNAMEs point your subdomains to a different server.
DNS Protocol
DNS is sometimes referred to as a query-response protocol. The client typically sends a request with a single UDP packet, and the server response generally fits into a single UDP packet. Again, UDP is a Layer 3 protocol. If the server response is too large to fit into a single packet, then the response may be sent via a TCP connection. An example of this is when a request is made for an AXFR record, which is also known as “zone transfer”. This query is basically a client request to send information about a particular domain. However, DNS over TCP Port 53 is often blocked by the administrator to prevent disclosure of DNS information to potential hackers.
Internet Corporation for Assigned Names and Numbers (ICANN)
ICANN is a non-profit organization that is responsible for maintaining databases related to namespaces on the Internet.
Traceroute
Traceroute is a tool used to track the path of IP packets from one system to another. Traceroute can be used to diagnose issues with transmitting IP packets.
Routers
A router is hardware that connects a network to one or more other networks and directs data packets from one node to another. The router inspects each packet, and then directs that packet based on the IP address contained in each packet. DHCP is a client/server protocol that provides an IP host with an IP address and other configuration information, e.g. a subnet mask or default gateway. Static IP addresses are assigned to networking equipment, like routers, firewalls, and servers. Host computers, including tablets and smartphones are generally assigned a dynamic IP address.
Secure Data Transmission
Secure Data Transmission is the process of sending data over a secure channel, whereby the channel remains secure with the use of encryption. In wireless networks, secure data transmission is facilitated with the protocol Wi-Fi Protected Access (WPA/WPA2/WPA3), while Web-based transmission often relies on Transport Layer Security (TLS). When you are on the Web, you can tell if you are using TLS because a website will have “https” at the start of the URL. The purpose of secure data transmission is to prevent eavesdropping and confidential data from being leaked to hackers.
Pretty Good Privacy (PGP) Encryption
PGP is an encryption program that is used for the secure transmission of email and encryption of files, directories, and volumes (disks). PGP is the most widely used email encryption program in the world. In 1991, Phil Zimmermann created the PGP program and made it freely available to the public. It also became popular outside of the USA. Given that PGP uses an RSA encryption algorithm, RSA Data Security sued Pretty Good Privacy for patent infringement in a licensing dispute (https://cryptome.org/jya/rsavpgp.htm). Interestingly, the United States Customs Service then initiated a criminal investigation against Zimmermann for violating the Arms Export Control Act and termed cryptographic software as “munitions”. Thus, Zimmermann was suspected of “arms trafficking” and arrested at Washington’s Dulles Airport by U.S. Customs agents. Fortunately for him, he was arriving into the USA. If he had been leaving the USA, with PGP encrypted files, then he could have been arrested on federal charges for exporting weapons without a license. Charges against Zimmermann were later dropped, and he was never indicted. Zimmermann later went on to work for Silent Circle, the company that created the Blackphone (encrypted smartphone).
How Does PGP Work?
PGP combines symmetric key encryption and public key encryption. The message is first encrypted with symmetric key encryption. The symmetric key is a one-time-only session key that is sent to the receiver during transmission, and the message is also encrypted with the receiver’s public key. The receiver can only decrypt the symmetric (session) key with their private key. PGP also uses a digital signature, using either RSA or DSA algorithms to ensure message authentication. PGP also supports integrity checking to ensure that the message was not altered during transmission; if the message was altered, then the receiver will not be able to decrypt the message.
PGP and the Dark Web
PGP is of particular interest to investigators because it is widely used for secure email communication between Dark Web marketplace vendors and their customers; PGP is used to prevent eavesdropping by law enforcement. These vendors have made their PGP public key available on Dark Web marketplaces, like Hansa, Honest Cocaine, and AlphaBay. Kleopatra is a tool, which is available from OpenPGP, that can extract the email address used to generate a PGP key, using the public PGP key.
What Does a PGP Key Look Like?
Figure 8.3 shows an example from a Dark Web marketplace vendor:

Figure 8.3 Example of a PGP key
OpenPGP
Patent issues associated with using RSA encryption licensing issues have continued to be a concern. Thus, PGP Inc. approached the IETF and proposed a new standard called OpenPGP. There is now an OpenPGP Working Group, which is administered by the IETF.
IPv4
Currently, most traffic on the Internet uses IPv4. Internet Protocol version 4 (IPv4) is the fourth version protocol for connectionless data transmission on packet-switched internetworks. A packet is a block of data transmitted across a network. On the Internet, these packets are transmitted in sequence, and each packet is uniform in size and structure. An IP packet (block of data sent across the Internet) contains a header section and a data section. An IPv4 header has 14 fields, as outlined in Figure 8.4.

Figure 8.4 IPv4 header
Version: The version (a value of 4 bits shows that it is IPv4).
Internet Header Length (IHL): The length of the header.
Differentiated Services Code Point (DSCP): Differentiated Services (DiffServ) code for real-time data streaming.
Explicit Congestion Notification (ECN): An optional feature that allows for notification of network congestion.
Total Length: A 16-bit field that denotes the size of the packet (header and data).
Identification: A unique identifier.
Flags: A unique identifier used to identify fragments.
Fragment Offset: A 13-bit value used to specify the offset of a fragment.
Time To Live (TTL): The time that a datagram may live. A router decrements this number and discards the packet when it reaches 0.
Protocol: The protocol used in the data part of the IP datagram, as defined by IANA.
Header Checksum: Used for error checking by the router.
Source IP Address: The sender’s IP address.
Destination IP Address: The recipient’s IP address.
Options: Infrequently used but can hold data from the IHL.
IPv4 uses 32-bit addresses, which are usually represented in four octets of dotted decimal notation—see the previous example for www.pace.edu, where 198.105.44.27 is an IPv4 address.
IPv4 uses 32-bit addresses, which are usually represented in four octets of dotted decimal notation, like the example above for www.pace.edu where 198.105.44.27 is an IPv4 address. An IPv4 address is broken into two parts: (1) Network and (2) Host. The host refers to a specific device on a network. For example, a device could be a computer, fax machine or printer. IANA (Internet Assigned Numbers Authority) is the organization responsible for assigning IP addresses (iana.org). IANA assigns blocks of IP addresses to Regional Internet Registries (RIRs), which in turn allocate IP addresses within their region:
AfriNic (Africa)
APNIC (Asia Pacific)
ARIN (North America)
LACNIC (Latin America & Caribbean)
RIPE (Europe)
Subnet Mask
Subnetting allows an administrator to create multiple (logical) networks within a Class A, B, C network. The subnet mask is used by TCP/IP to locate a specific host on a subnet. Ultimately, the purpose of the subnet mask is to determine where the network part of an address ends and where the individual device address begins. An IP address is comprised of 32 binary bits. These 32 bits can be divided into four octets (1 octet = 8 bits). The value of each octet ranges from 0 to 255 decimal, i.e. 00000000 – 11111111 (binary).
In the first example below, we convert an octet when all bits are set to 1.
1 |
1 |
1 |
1 |
1 |
1 |
1 |
1 |
27 |
26 |
25 |
24 |
23 |
22 |
21 |
20 |
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
128 + 64 + 32 + 16 + 8 + 4 + 2 + 1 = 255 |
|||||||
Here is another example where all bits are not set to 1. As you can see, we use the same formula and multiply the binary value (top row) by the value in the third row (128, 64, …)
0 |
1 |
0 |
0 |
0 |
0 |
1 |
0 |
27 |
26 |
25 |
24 |
23 |
22 |
21 |
20 |
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
64 + 2 = 66 |
|||||||
Class A Network
For a Class A network, which has a major network address range of 1.0.0.0 - 127.255.255.255, the first octet is for the network. Octets 2, 3, and 4 (24 bits) are for the network manager to divide into subnets and hosts.
Class A network addresses have more than 65,536 hosts.
Class B Network
For a Class B network, which has a major network address range of 128.0.0.0 - 191.255.255.255, the first two octets are for the network. Therefore, octets 3 and 4 (16 bits) are for the network manager to divide into subnets and hosts.
Class B network addresses have between 256 and 65,534 hosts.
Class C Network
For a Class C network, which has a major network address range of 192.0.0.0 - 223.255.255.255, the first three octets are for the network. Therefore, octet 4 (8 bits) is for the network manager to divide into subnets and hosts.
Class C networks addresses have less than 254 hosts.
Network Masks
The default masks are as follows:
Class A: 255.0.0.0 (or 11111111.00000000.00000000.00000000 in binary)
Class B: 255.255.0.0
Class C: 255.255.255.0
An example of a Class A network that has no subnet is 8.20.15.1 255.0.0.0:
8.20.15.1 = 00001000.00010100.00001111.00000001
255.0.0.0 = 11111111.00000000.00000000.00000000
The network id (8) is in bold, and the remaining octets represent the host id (20.15.1), which is in italics.
In Table 8.1, the first column indicates the class of network, while the second column shows the IP address range. For example, an IP address that looks like 101.x.x.x is a Class A address. We will discuss the “Mask” in column three shortly, but basically it means that a Class A network may assign many more hosts/IPs on a network than a Class B or Class C network.
Column four shows the possible number of hosts for each class of IP address. Therefore, in a Class C network, only the last octet can be used for the host address.
Table 8.1 Network Address Classes for IP Ranges in IPv4
Class |
IP Range |
Mask |
Addresses in Each Network |
A |
1–127 |
N.H.H.H |
16,777,216 |
B |
128–191 |
N.N.H.H |
65,536 |
C |
192–223 |
N.N.N.H |
256 |
D |
224–239 |
Multicasting |
|
E |
240–255 |
Experimental |
|
N = Network, H = Host |
Given that IANA has run out of IP addresses to assign, it is important to use a system called NAT. Network Address Translation (NAT) allows multiple network devices on a network to share a single IP address (see RFC 1631). Thus, a device, like a router, can use that one IP address, which may represent a plethora of network devices. A computer that is on an internal network can use private IP addresses in the range of 10.0.0.0–10.255.255.255 and some other ranges. Using the NAT process, the router will change the private IP address to a public IP address. The router also generates a source port number. NAT is used to overcome the shortage of IP addresses associated with IPv4. A NAT operates in a similar fashion as someone calling the main telephone number of a business, asking for a specific employee, and then being transferred to that employee.
Originally, IP addresses were allocated disproportionately because some companies were assigned Class A and Class B network IP addresses, which are not being utilized to their full potential. Class A network IP addresses were assigned in the 1990s to organizations that include General Electric (GE), IBM, Apple, Ford Motor Company, and the Department of Defense (DoD). Thus, does Ford really need more than 16 million unique addresses for their network? Probably not.
Reserved IP Addresses
There are some IP addresses that cannot be used to identify computers on a network, e.g., 127.x.x.x, e.g., 127.0.0.1 = localhost. Also, any IP address where the host portion is all 1s in binary, e.g. 255.255.255.255 (broadcast addresses). Similarly, any IP address when the network part is all 0s in binary cannot be used, e.g., 0.0.0.0.
There are also some private IP addresses that cannot be used on the Internet and these ranges are as follows:
10.0.0.0–10.255.255.255
172.16.0.0–172.31.255.255
192.168.0.0–192.168.255.255
169.254.0.0–169.254.255.255
These IP addresses are not routable but can be used on an internal network. The third category of IP addresses is used by business and home networks and can be used when a DHCP server is unavailable. The fourth category is used by different companies, including Microsoft, Apple, and Linux, who all have their own different schemes for using the IP addresses. APIPA (Automatic Private IP Addressing) is the scheme used by Microsoft Windows and allows DHCP to self-configure to an IP address and subnet mask when a DHCP server is unavailable.
Calculate an IP Subnet Mask
Let us take some time to determine the class of network for an IPv4 address.
Determine the network class (A, B or C)
Class A: IP Address begins with 1-126
1.0.0.0 - 127.255.255.255
Class B: IP Address begins with 128-191
128.0.0.0 - 191.255.255.255
Class C: IP Address begins with 192-223
192.0.0.0 - 223.255.255.255
Let’s use Ireland.com as an example. Using mxtoolbox.com we can determine that the IP address is 193.120.44.197. We can tell that it is a Class C IP Address (begins with “193”).
The subnet mask in a binary format is as follows:
11111111111111111111111100000000
To make it more readable we separate the binary string into groups of 8 bits:
11111111.11111111.11111111.00000000
The binary number 11111111 = 255
The binary number 00000000 = 0
Thus 11111111.11111111.11111111.00000000 can be represented as:
255.255.255.0
For a Class C IP address, the standard subnet mask will be 255.255.255.0 (see above).
How to Find the Subnet Mask on a Windows Computer
Go to the Run box (Windows Key + R).
Type cmd to open the Command Prompt.
Type the command ipconfig /all and press the Enter key.
MAC (Media Access Control) Addresses
A MAC address is a unique identifier (48-bit (6 byte) number) for network-enabled devices. These devices operate at the Data Link Layer (Layer 2). These network hardware devices can include the following:
Router
PC
Smartphone
Printer
How do I find the MAC address for a device?
Usually it is printed on the back or bottom of the device.
What does a MAC address look like?
BC:9E:EF:88:6E:0F
How do I find the MAC address on a PC?
For Windows 10:
Click the Start button.
In the taskbar Search box, type cmd and select the Command Prompt App. This will open the command window.
At the command prompt, type ipconfig/all.
Copy down the “physical address” (aka the MAC address) from the “Wireless LAN Adapter Local Area Connection” section (see Figure 8.5).
Close the Command Prompt window.

Figure 8.5 Finding the MAC Address on a Windows 10 PC
How do I find the MAC address on an Apple Macintosh?
From the Apple menu, select System Preferences.
In System Preferences, from the View menu, select Network.
In the left of the “Network” window that opens, click the name of your connection (e.g. Wi-Fi, AirPort, Ethernet, Built-in Ethernet).
Click Advanced, and in the sheet that appears, click the Hardware, Ethernet, or AirPort tab.
The address is the string of letters and numbers next to “MAC Address:”, “Ethernet ID:”, or “AirPort ID:”
How do I find the MAC address on an iPhone?
Click Settings.
Click General.
Click About.
View the “Wi-Fi Address”, i.e. the MAC address.
Notice that the Bluetooth address is only one letter off the Wi-Fi MAC address. Thus, if you have one, you can determine the other.
IPv6
IPv6 is the latest version and, like IPv4, was developed by the Internet Engineering Task Force (IETF). It was developed in response to the limited number of IP addresses associated with IPv4 (4,294,967,296 available addresses). The Internet Assigned Numbers Authority (IANA) is responsible for the allocation of IP addresses globally. All devices operating on the Internet need an IP address.
IPv6 is a 128-bit address and, therefore, has 2128 addresses available. The example of 198.105.44.27 converts to 2002:C669:2C1B:0:0:0:0:0 in IPv6. As you can see from this example, an IPv6 address has eight groupings of four hexadecimal digits, and semicolons are used to separate each grouping.
NetFlow is a helpful tool for network forensics investigators because it can capture transactions for IP network traffic. Cisco developed the tool in 1996, but it works with NetFlow-compatible routers and switches. Regardless of the manufacturer, most routers are NetFlow compatible. NetFlow version 9 has become the basis for an IETF standard called Internet Protocol Flow Information eXport (IPFIX). NetFlow is particularly helpful with incident response because it can potentially capture all connection activity between nodes on a network. This network flow activity is then forwarded to a collector, a server that captures, processes, and saves these transactions. The data stored includes the source and destination IP, source and destination ports, IP protocol used, and type of service, but not the content of packets saved. NetFlow is beneficial when full packet capture is not feasible.
IDS
An intrusion detection system (IDS) is hardware or software used to monitor network traffic for malicious activity. An IDS can provide alerts when suspicious activity occurs and provide detailed logging information with professional reporting capabilities. An IDS is generally a sophisticated system, in that these systems can alert the network administrator to anomalies on the network relative to normal activity instead of simply being preprogrammed. An IDS can work either heuristically or with predetermined signatures. This is important because anomalies differ from network to network. For example, data being transmitted from a government facility in the United States to China may trigger an alert, whereas Internet traffic between a U.S. university and Beijing may be an everyday occurrence. The IDS monitors both inbound and outbound network traffic.
Naturally, the IDS, with its logs and reports, is one of the first items a network forensics examiner analyzes. The efficacy of an IDS or an intrusion prevention system (IPS) is diminished by encryption because of the system’s inability to inspect these packets. In these cases, logs from network monitoring tools can be invaluable. FireEye provides one of these tools that checks for malware. Unfortunately, in the case of Target Stores, alerts from FireEye were largely ignored, and the data theft of millions of customers continued after the company was notified.
Many different types of IDS exist, and they all work in very different ways:
Network intrusion detection system (NIDS)
Network node intrusion system (NNIDS)
Host-based intrusion detection system (HIDS)
Intrusion prevention system (IPS)
Network Intrusion Detection System (NIDS)
The NIDS operates in promiscuous mode. Promiscuous mode means that a network adapter can capture and read all data packets on a particular network. A Network Intrusion Detection System (NIDS) is used to monitor the traffic on a subnet by matching that network traffic with known attacks. If an attack is identified, then the network administration is alerted.
Network Node Intrusion System (NNIDS)
A Network Node Intrusion System (NNIDS) is used to monitor traffic between a network and a host. One example of an NNIDS would be use for monitoring traffic connected to a VPN.
Host-Based Intrusion Detection System (HIDS)
A Host Intrusion System (HIDS) works on the premise of taking a snapshot of a system at a specific point in time and then compares the current snapshot with a previous snapshot to identify if any system-critical files were either modified or deleted. Often HIDSs are placed on critical systems to monitor changes.
Intrusion Prevention System (IPS)
An Intrusion Prevention System (IPS) is a network security tool that is placed in direct communication between the source and destination to detect attacks. Unlike the passive IDS, an IPS takes automated actions when a threat is discovered, which may include alerting the network administrator, dropping suspected malicious packets, blocking traffic, or resetting a connection.
Firewalls
A firewall is a software or hardware mechanism used to inspect data packets on a network and determine, based on its set of rules, whether each packet should be allowed through. The network administrator can set these rules. For example, an administrator might prohibit inbound/outbound traffic from IP addresses from China. Chinese hackers have been known to get around this by using Google Groups and other U.S. IP addresses for command and control so that they can access a network without being flagged by the firewall. The network administrator should add known malware sites to the firewall as blocked websites. These malware sites are published on websites, like www.malwaredomainlist.com, and are also available from federal law enforcement.
A firewall can perform detailed inspection at Layer 4 (TCP and ICMP), while other firewalls can inspect Layer 7 data, including FTP and DNS requests. A firewall is sometimes used to implement a Virtual Private Network (VPN).
One of the first things that a hacker may try to do is to change the firewall settings so that they can send and receive data without interruption. A network forensics examiner will check to see if the firewall rules have been changed. A firewall can be built into an operating system or could be a part of a network router.
There are different types of firewalls:
Proxy firewalls
Stateful inspection firewalls
Unified threat management (UTM)
Next-generation firewalls (NGFW)
A proxy firewall is a server and acts as an intermediary between a user and an Internet connection. Stateless firewalls monitor traffic and unblock packets based on the source and destination addresses or other predetermined values. A stateless firewall filter is often referred to as an access control list. A stateful firewall monitors traffic streams in an end-to-end fashion. These firewalls can support IP security or IPsec functions, which includes encryption and tunnels. Stateful firewalls are generally better at flagging unauthorized communications. Unified threat management (UTM) provides multiple layers of security, and its functionality includes content filtering, Web filtering, and antivirus. UTM devices are marketed as network security appliances, which can be a network hardware appliance, virtual appliance, or cloud service. Unified threat management can include intrusion detection and intrusion prevention technologies. For example, they may detect an attack, based on malware signatures or other anomalies. UTM also supports virtual private network (VPN) functionality. In terms of Web filtering for content, some UTMs can scan websites for security vulnerabilities that may be harmful to the requesting computer. Next-generation firewalls (NGFW) are third generation firewalls, which are a mix of a traditional firewall, while incorporating other security applications. This includes deep packet inspection, which is an intrusion prevention system (IPS). An NGFW goes beyond the capabilities of a stateful firewall. A next generation firewall has the ability to block high-risk applications. Thus, an NGFW may detect and block network attacks, based on protocol, port, and application levels. An NGFW can perform full packet inspection by checking both the signatures and payload of packets to detect anomalies or even malware.
Firewall Evidence
An investigator can retrieve the following evidence from a firewall:
Access Control Lists: determine traffic allowed and blocked traffic;
Packet logs: include the origin/destination address, timestamps, packet size, and protocols; and
Data content: if it is a Layer 7 firewall.
Ports
A port is a communication channel that is specific to a running process or application on a computer. Ports are extremely important for network forensics investigators because ports that are typically not used by a system but have been active can indicate a compromise. The number of the port in system logs also indicates the type of application that was running on a computer. A total of 65,535 ports exist. The following is a list of commonly used ports:
20 and 21: File Transfer Protocol (FTP)
22: Secure Shell (SSH)
23: Telnet remote login service
25: Simple Mail Transfer Protocol (SMTP)
53: Domain Name System (DNS) service
80: Hypertext Transfer Protocol (HTTP), used on the World Wide Web
110: Post Office Protocol (POP3)
143: Internet Message Access Protocol (IMAP)
443: HTTP Secure (HTTPS)
Port 80 is often used the most by clients because it is associated with a user’s Internet activity. Most webmail today uses SSL and Port 443.
Understanding the OSI Model
The Open Systems Interconnection (OSI) Model is a model used to define how data is transmitted across the Internet. This standard was introduced in 1984 by the International Organization for Standardization (ISO). The ISO introduced the notion that we communicate across the Internet using seven layers. (Other groups have a different model with fewer layers.) It is important to understand the different layers of communication (see Figure 8.6) because a forensics examiner might need to explain to a jury how we can be sure that an email received by the victim did, in fact, come from the criminal suspect. To do that, you would need to explain the header information in an email and tell how that message is routed through different hardware. I can send you an email, but how can you prove that the email was actually sent from me? A helpful way to remember the layers is APSTNDP—All People Seem To Need Data Processing or A Priest Saw Three Nuns Doing Pushups.

Figure 8.6 The OSI model
The Physical Layer
The Physical Layer (Layer 1) defines the hardware or medium through which data is transmitted and the power required for transmission. That power often is in the form of electrical impulses defined by 0s and 1s (binary). Physical hardware can include the following:
Coaxial cable
Fiber optic
Ethernet cable
Network Interface Card (NIC)
The Data Link Layer
Address Resolution Protocol (ARP) is a method by which the Network Layer (Layer 3) of the OSI is linked to the Data Link Layer (Layer 2). In other words, when you are using the Internet on your home network, the request is sent with an IP address for your home network. When the web server responds and sends a message back to that IP address, the router needs to route that message to the appropriate device on that network using ARP (that is, routing the message to the appropriate MAC address for the specific device that requested the information).
Two addresses are used on a LAN, a MAC address and an IP address. At the Data Link Layer, MAC addresses are used to find a destination computer listed in a table called the ARP cache. A MAC address is stored in the network card. Applications use an IP address to find a destination computer.
A router maintains an ARP table, which is based on ARP requests and responses. When a packet is sent across the Internet, it is sent to the MAC address of the router interface that is the default gateway. ARP binds a static IP to a MAC address in a device’s ARP table. DHCP on the other hand always assigns the same IP address to a device. ARP is used to get the MAC address from an IP address and is primarily used on a LAN (local area network).
The routing table contains the following:
Destination network IP addresses;
Destination gateway IP address; and
Corresponding interface.
When the router receives a packet, it will check for the destination network IP address in the routing table. If the packet is destined for a network that is directly connected to the router, then the destination MAC address will be obtained from the ARP table. MAC addresses from Layer 2 are mapped to Layer 3 IP addresses using ARP. ARP responses are cached on hosts that make up the LAN. The ARP cache can be queried on a Windows system, to identify MAC to IP address mappings using the arp –a command.
The Network Layer
The Network Layer defines communications between networks or operation of the subnet and makes decisions about the physical path through which transmission should occur. At the Network Layer, logical addresses are translated to physical addresses. At this layer, routing frames between networks and frame fragmentation decisions are made.
Routers operate at this layer. A router is a hardware device with a motherboard, a central processing unit (CPU), and input/output ports. Routers also have memory, which contains startup configurations, operating system, and routing tables. A routing table contains information about the network and provides the most effective method of directing packets across that network.
The Transport Layer
Transmission Control Protocol (TCP) is a communication standard that is used in conjunction with the Internet. It is found in the Transport Layer (Layer 4) and is used for the reliable delivery of data over a network connection. Services like the World Wide Web (WWW), email, and FTP use this communication protocol. Applications that require faster communication, and can compromise on error checking, use User Datagram Protocol (UDP). VoIP and video often use UDP because of its speed and because it is no big deal if a data packet is sent out of order or is dropped. TCP, on the other hand, is more orderly and provides error checking to ensure that all data packets are sent in the correct sequence.
Note
User Datagram Protocol (UDP) is a connectionless communication protocol that has limited packet recovery functionality and operates at the transport layer.
TCP Three-Way Handshake (SYN–SYN–ACK)
TCP uses a three-message handshake, also known as SYN–SYN–ACK, to set up a TCP/IP connection (a connection over the Internet). Here is how it works:
Host A sends a TCP Synchronize (SYN) packet to Host B.
Host B then sends a Synchronize-Acknowledge (SYN–ACK) to Host A.
In response, Host A sends an Acknowledgment (ACK) to Host B.
Once Host B receives the ACK, the TCP socket connection is established.
Another three-way communication is used to “tear down” the TCP connection, once communication ends. The following protocols all use TCP and, therefore, use the three-way handshake:
FTP
HTTP
HTTPS
SMTP
IMAP
SSH
POP3
Telnet
TCP Retransmission
TCP Retransmission is a process used for error correction to TCP data packets. Retransmission will occur when the receiver determines that an error (or checksum) has occurred and subsequently does not transmit an “ACK” to the sender. The sender will then retransmit the packet. Once the recipient determines that there has been no error during transmission, an “ACK” packet will be sent to the sender. TCP retransmission also occurs if the packet was lost during transmission and no “ACK” was returned by the intended recipient.
SYN Flood Attack
A SYN flood attack occurs when a hacker sends SYN requests to a host at such a rapid rate that the server cannot handle all the requests and ultimately renders it useless. In other words, the client does not send the server the expected ACK request in the three-way handshake.
Note
The Importance of TCP
So why do we care about TCP? In network forensics, much of our work revolves around analyzing data packets. When monitoring network traffic, we might want to use a sniffer to analyze TCP/IP data packets. Most packet sniffers operate at Layer 2 or Layer 3 of the OSI Model.
A TCP/IP header includes the source port and IP address, and the destination port and IP address. For example, identifying the IP address can tell you whether there is communication with a server in China. The port number can tell you the type of service being used. For example, Internet Relay Chat (IRC) uses the TCP protocol and can be found operating on port 6667. But IRC has been used by bot herders (malicious hackers) for command and control (that is, they use your zombie computer to send out their spam). You can use the Ngrep (ngrep.sourceforge.net) tool to view IRC logs.
In summary, many network forensics examiners use TCP tools to analyze data packets on networks to see who is communicating on the network, what services they are using, and, ultimately, what mischievous activities they are conducting.
The Session Layer
As its name suggests, the Session Layer (Layer 5) is responsible for initiating, maintaining, and terminating processes on different systems.
The Presentation Layer
The Presentation Layer (Layer 6) prepares data for the Application Layer and is responsible for data conversion, compression, and encryption.
The Application Layer
The Application Layer (Layer 7) can be viewed as the closest to the end user and interacts with applications. Functionality at this layer includes email (SMTP), remote file access, remote printer access, File Transfer Protocol (FTP), HyperText Transfer Protocol (HTTP), and network management.
Tools are available to help an investigator understand more about wireless access points in an area. For example, Net Analyzer, which is available for the iPhone, can identify the closest access points, and the investigator can quickly determine how many devices are connected to that access point. Net Analyzer provides not only the MAC address of the device but will also provide the name assigned to that device and the manufacturer. In this case, the device may be a laptop, a Samsung Galaxy S20, an Xbox One, a Roku, or an IP camera—basically, any Wi-Fi-enabled device. This type of Wi-Fi analysis should be performed before executing a warrant, which did not happen in the case study just detailed.
If an open wireless signal is found, the investigators must account for it. Even if a wireless network is open, there is still probable cause to believe that evidence of the crime is located within the network equipment at the location. Some criminals even leave their wireless networks open intentionally to maintain some plausible deniability. The bottom line is that just because an IP address is traced back to a location, that is not sole proof that a person at the location is responsible for the incident.
Introduction to VoIP
The recent exponential growth of mobile communication applications means that investigations involving VoIP communications continue to grow in importance.
Voice over Internet Protocol (VoIP)
Voice over Internet Protocol (VoIP) is a protocol that takes analog audio signals, e.g. voice, and converts those signals to digital data that can be transmitted across the Internet. A traditional landline telephone uses an analog signal. VoIP, however, allows a user with broadband Internet access to use VoIP. VoIP calls are facilitated via a VoIP-enabled telephone or via a computer (desktop/laptop/smartphone). If your call ends up on a traditional telephone, then the signal will be converted back to an analog signal.
VoIP is an alternative to the traditional PSTN (Public Switched Telephone Network). VoIP includes open standards, like SIP, but also includes proprietary applications, like Skype and Google Talk.
Disadvantages of VoIP
Not all VoIP services connect directly with emergency services and locating the caller can be a challenge. VoIP will not work during a power outage unless you have a battery backup. Caller ID can be easily spoofed with VoIP, and the protocol has enabled the emergence of “robocalls”. The Federal Trade Commission (FTC) in the United States has initiated more than 100 lawsuits against more than 600 companies that have been responsible for billions of robocalls. The FTC has also conducted many competitions to detect and block robocalls.
PBX (Private Branch Exchange)
A PBX (Private Branch Exchange) is the telephone system within an organization that switches calls between users in that organization on local telephone lines, while enabling users to share a limited number of external telephone lines. The primary reason for using a PBX is the cost savings associated with sharing telephone lines, rather than paying for one telephone line for each employee. The PBX is owned and managed by the enterprise.
There are different types of PBX. For example, there is a traditional PBX with copper cables for telephone landlines attached to it. This type of PBX will accommodate a mixture of analog and digital signal transmissions. There is also a cloud-based PBX system that can be used by the enterprise.
An IP-PBX is an Internet Protocol PBX that uses digital telephone signals, rather than analog landlines, to facilitate calls. Ethernet cables connect telephones rather than traditional phone lines.
PBX Fraud
PBX fraud often results from criminals establishing premium calling services, then breaking into companies, and using the organization’s telephone lines to call premium services, thereby racking up tens of thousands of dollars in charges, often over the weekend, when office staff are at home.
How do these criminals gain access to a telephone system? When you call an office telephone number late at night, or over the weekend, the call will typically go to voicemail. Some corporate systems will enable employees to remotely access their voicemail with the use of a PIN. Sometimes the default PIN is set to the last four digits of the telephone number. On certain telephone systems, there is an option for the user to forward calls to another number. Once a criminal gains access to voicemail, she can use the call forwarding option to forward calls to a pay-per-minute premium service, which is owned by the criminal. Therefore, any call to that company telephone number is forwarded to the premium service. Consequently, the company would be billed an astronomical amount in premium call charges. The charges would only be noticed on the Monday when employees return to the office.
Most VoIP telephones lack intelligence. Thus, they require another system to function, i.e. a PBX. When someone picks up the telephone, the telephone then contacts a PBX for assistance. The PBX instructs the telephone to play a dial tone. When the user pushes a number, the telephone sends another request to the PBX. The PBX typically responds with an instruction to play a digit tone. This continues until the user pushes enough numbers for the PBX to connect the call. The PBX can however be too helpful, as it does not know who is authorized to make telephone calls. Thus, it lacks adequate security. Anyone who knows the IP address of an unsecured PBX can make phone calls that originate from that organization. Therefore, criminals that find the IP address of a PBX can make calls using a PBX. They can subsequently configure their telephone to pick up the handset and check for a dial tone. The criminal can then begin making calls to pay-per-minute premium numbers and use robotic dialers to dial hundreds of times a day, or perhaps thousands of times a week.
Unfortunately, in these situations, the company is liable for the charges. This is actually built into their contract with the telecom company, and they do not realize this until the fraud occurs. The PBX is internal for the company, and therefore if it is compromised it is viewed as negligence on the part of the company. Most companies do not have the in-house expertise to properly configure a PBX and therefore select a contractor, which may be the cheapest, and least knowledgeable, contractor.
A PBX must be on the Internet, to receive incoming calls and therefore you cannot block all incoming access to the PBX. To further complicate matters, some offices have remote workers who need to connect from home. This means that the PBX needs to be configured to facilitate calls initiated from the Internet. It is not uncommon for a company to find out on a Monday morning that calls made over the weekend total more than $30,000 and as much as $60,000.
It is often difficult for the police to investigate these cases or recoup these losses since many of these scams involve international calls to countries like Zimbabwe, Cuba, or Pakistan. Many of these crimes go unreported because companies fear the bad publicity or being found negligent. Some companies will call the FBI. However, these crimes may not reach the financial threshold to initiate an FBI investigation.
Session Initiation Protocol (SIP)
Session Initiation Protocol (SIP) is a peer-to-peer, multimedia signaling protocol developed by the Internet Engineering Task Force (IETF). The IETF develops and promotes voluntary Internet standards. SIP uses existing IP protocols, like DNS, and SDP (Static Dial Plan), and operates at the application layer control protocol. SIP is used to establish, modify and terminate multimedia sessions, i.e., voice, video, instant messaging over the Internet. SIP generally utilizes UDP or TCP.
STUN (Simple Traversal of UDP Through NATs (Network Address Translation))
STUN allows devices behind a NAT firewall or router to make telephone calls to VoIP provider hosts outside of their local network.
Incident Response (IR)
Incident response is often associated with network breaches, but it often has a much wider scope than that. Many larger organizations maintain a security operations center (SOC) and an incident response (IR) team. The SOC often focuses on information security and threat detection, which may include monitoring for unusual login attempts (multiple attempts or from a different location), malware, data exfiltration, and unusual external IP address connections attempts. The IR team may handle incidents as small as a lost/stolen smartphone to a more serious incident involving stolen credentials or a large network breach. Thus, the SOC will filter out false positive alerts, and then escalate notable incidents to IR personnel. Some incidents are low risk. For example, an encrypted iPhone with no client or customer data would be considered low risk because the primary asset is not the device but the potential data compromise. An iPhone may cost $1,000 but loss of intellectual property or client information can reach millions of dollars, as Target Corporation can attest to. Incident response is often a team response as it can involve technical digital forensics examiners, a legal team, public relations, human resources, client liaisons, and many more people.
Whether an incident is large or small, the first step is always the same – begin with triage. Triage is the initial step with incident response, and it involves mitigating the risk. Sometimes triage may involve capturing perishable data (data that quickly expires). Mitigating the risk generally means preventing the loss of data, money, or any potential threats to the organization. An example of triage would be to capture the latest state of the device (last login, last location, etc.), send a remote wipe to a stolen iPhone, inform the cellular carrier about the loss, file a police report, and have the user change her passwords to any network services that the device was used for.
Assembling the right team to deal with an incident is an important next step (after triage) and will often involve counsel (legal) staff, unless it is a low risk case. An attorney will help to assess the legal obligations of the organization. For example, different states in the United States have different laws relating to disclosures involving personally identifiable information (PII). A disclosure of health records may be impacted by the Health Insurance Portability and Accountability Act (HIPAA), while a disclosure of personal information for citizens of the European Union (EU) will be covered by the General Data Protection Regulation (GDPR) and perhaps nation state laws too.
Once triage has been performed, the team can begin an investigation. Once an investigation has concluded, a root cause analysis (RCA) report may recommend training for an employee and/or a review of processes to ensure that a similar incident will not occur. It is important to identify lessons that can be learned from incidents.
STIX, TAXII, and Cybox
Threat intelligence has become extremely important as organizations today encounter threats from hacktivists, individual hackers and nation states. Many individual industries encounter similar threats. For example, while the W32.Stuxnet malware variant targeted the centrifuges at the Iranian nuclear facility at Natanz, the Stuxnet worm impacted similar networks in Indonesia, India, and many other countries. Moreover, APT10, also referred to as Operation Cloud Hopper, targeted the managed service provider (MSP) industry, using similar types of malware. Therefore, sharing intelligence, especially within industries, and even among competitors, has become a more robust and effective strategy. As an example, we have sector-based Information Sharing and Analysis Centers (ISAC). There is a Financial Services Information Sharing and Analysis Center (FS-ISAC), one for the automotive industry, aviation and so forth. An ISAC provides actionable intelligence for security professionals. More information about the ISACs can be found on the National Council of ISACs website (www.nationalisacs.org). There are many other organizations that provide security training and provide security alerts to security professionals. The United States Secret Service hosts quarterly meetings, under the organizational name of the Electronic Crimes Task Force (ECTF). The Cybersecurity and Infrastructure Security Agency (CISA), within the Department of Homeland Security (DHS), provides extremely important security alerts for both organizational and personal security. InfraGard, a public-private organization of the FBI, also provides organizations with security alerts. Finally, Europol hosts a series of forums and provides security alerts, which are generally by invitation only.
Advanced Persistent Threats
An advanced persistent threat (APT) is a sophisticated, relentless, coordinated attack on a computer network, with the goal of stealing intellectual property. The term was first used by the U.S. Air Force in 2006. It is a well-known fact that the People’s Liberation Army (PLA) has been mandated not only to protect China, but also to engage in economic development; this involves economic espionage. Mandiant (now owned by FireEye) is just one organization that has disclosed how the Chinese government employs hackers to steal intellectual property from the United States. The Mandiant report has provided details about Unit 61398 in Shanghai, which is manned by hundreds or perhaps thousands of hackers.
APT10
As previously mentioned, APT10 was a cyber espionage attack, perpetrated by hackers in China, on managed service providers (MSPs). It is understandable why MSPs would be the target of an attack, given the vast amounts of intellectual property managed by cloud service providers. According to a report by PwC UK, in collaboration with BAE Systems, APT10 attacks began as early as 2014 and continued for a number of years. During those years, APT10 used a series of malware types, from Poison Ivy to PlugX to RedLeaves to QuasarRAT. APT10 used hundreds of domains for command and control of their compromised network hosts, thereby making it difficult to blacklist certain IP addresses from communicating with a network.
As with all APT attacks, it is difficult to identify when the network was initially compromised. Moreover, it is a challenge to contain the infection of the malware since these attackers move laterally throughout the network, and it becomes even more problematic if a large number of credentials have been compromised since successful logins do not raise flags like unsuccessful logins do. Finally, it is problematic to determine what data has been compromised since the attacker may encrypt the data that is being exfiltrated from the network and will use techniques, like timestomping, to thwart the work of forensics investigators. Timestomping is an anti-forensics technique used to manipulate the timestamps of a file.
Cyber Kill Chain
The whitepaper “Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains” details the six stages in an advanced attack on a computer network. This Intrusion Kill Chain explains what happens during a sophisticated attack on a network, usually an attack so advanced that it is government sponsored. Figure 8.7 shows how this chain of events occurs and then gives a detailed description of each phase.

Figure 8.7 The intrusion kill chain
Reconnaissance
During this phase, an attacker takes some time to learn about the structure of an organization. An adversary can collect information, about a target, in many ways, as detailed in the following sections.
Job Postings
An attacker can review job openings on an organization’s website or on a recruitment site like Monster.com—particularly those that relate to IT positions. Often the job requirements listed give an attacker a wealth of information related to the systems in use. The attacker then has information about the potential vulnerabilities associated with each system and application noted, including default passwords in case an administrator has not bothered to change them. The following is an example of qualifications for a database administrator posted on Monster.com:
Bachelor’s degree in computer science or equivalent years of work experience required; plus minimum of five (5) years relevant experience with Oracle 10g and 11g databases implementing RAC, ASM and DataGuard required
Functional and technical knowledge and experience supporting Oracle E_Business Suite in an R12 environment and/or Oracle Identity Management desirable
Experience supporting Oracle on Windows Server as well as Linux helpful
Some experience with Microsoft SQL Server
As you can see, this information can benefit an adversary during reconnaissance.
Press Releases
Many organizations unknowingly provide information to adversaries through press releases in a variety of ways. One way would be to announce a large purchase of IT systems for an organization.
Tech Forums
It is common for IT personnel to reach out to other IT professionals to get answers to issues that they are experiencing in their organizations on tech forums. The problem is that these Internet forums are generally open to the public. An adversary can gain a lot of information about an organization’s systems by reviewing postings on these forums.
Other Sources
Adversaries can also find a lot of information about an organization by reviewing social media websites, including Facebook and LinkedIn. These sites can provide invaluable information about events at an organization and also facilitate profiling key employees in that organization.
Some employees have posted sensitive information about their organization through websites, like WikiLeaks, SecureDrop, or Pastebin, which provide further information during the reconnaissance phase.
Other information that can help an adversary can be found on the company’s website. In one case, it was possible to view a sample employee identification card at a large healthcare provider and get details about the company that produces these ID badges. Other sources of information can include looking up the DNS records for a company. Some free services can allow you to find out the name of the individual who registered a domain name, as well as that person’s address.
Weaponization
In this phase, the adversary places malicious code into a payload. For example, the payload could be a PDF document with an embedded virus or perhaps a Trojan. A Trojan is a legitimate-looking application that is used to disguise malware. Other vectors of attack can also include spam, USB drives, and a hacked Wi-Fi connection.
Delivery
This phase merely involves delivery of the payload to the target. The delivery method could include SQL injection or spear phishing, using perhaps an electronic birthday card with a link to malware.
Exploitation
Exploitation is the successful execution of the payload. This could mean that an employee clicked the link in that e-card and executed malware on that machine, and the attacker now has access to that system and any network access associated with that computer.
C2 (Command and Control)
The command and control (C2) phase may or may not occur. This involves using some type of system to conduct your attack. C2 is used to obfuscate the attacker so that a request from a host or an IP address looks legitimate. If an unsuspecting host computer on a network is used to communicate with other systems on the network, this is termed a lateral attack. Sites like Twitter and Google groups have been used for command and control because the IP addresses of these sites are generally not blocked by organizations, but behind these legitimate sites is a hacker located perhaps in Russia or China. Amazon Web Services (AWS) has also been used by many hackers.
Exfiltration
Exfiltration involves the theft of data from a network. PFC Bradley Manning is a prime example of data exfiltration from a government network, and Edward Snowden is yet another obvious example. Exfiltration is the payoff for a government-sponsored attack and can provide key intellectual property, for example, from a missile defense system or cooling tiles on the NASA space shuttle.
Tactics, Techniques, and Procedures (TTP)
The terms tactics, techniques and procedures are used to describe ways to analyze an APT or a type of threat actor (hacker). Once you identify how malware was used to access a network or ways in which an adversary logged onto another computer on a network (e.g. using Remote Desktop Protocol (RDP)). The following sections will discuss the tools and methods used to achieve their goals and ways in which to identify TTPs and remediate these threats.
YARA
YARA is an open source tool that is used to classify and identify malware variants. An examiner can also copy the MD5 hash for a file and search on VirusTotal to see whether the file has been previously identified as malware (see Figure 8.8).

Figure 8.8 VirusTotal website
Persistence
Once a hacker has successfully infiltrated a network, the key to success is to remain on a compromised system using malware that is persistent. To maintain persistence, the malware installation will need to remain in a directory where it is activated every time that a host computer is powered on. Therefore, one of the first places that an investigator will examine is the start-up directory on a computer.
Dynamic-Link Library (DLL) Side-Loading
Microsoft, in an effort to make binary updates more convenient for developers, with the Windows side-by-side (WinSxS) feature, has inadvertently created a vulnerability used by APT attackers. Using this feature, hackers have successfully circumvented anti-virus tools and passed malware from computer to computer. The malicious payload actually runs in memory, rather than in the file system, where anti-virus scanners function.
Remediation
An investigator should remediate the risk once an intrusion has been identified. A computer can be easily replaced and preventing a threat and protecting the data are paramount. The investigation is secondary to nullifying the risk to a network, primarily because of the threat to intellectual property and other proprietary data. In terms of remediation, a company should follow some or all of the following steps:
Block malicious IP addresses;
Block malicious domain names;
Remove compromised systems from the network;
Generate a list of indicators of compromise (IOCs) and create a remediation and investigative process based on those IOCs;
Rebuild compromised systems;
Coordinate with cloud and service providers;
Enterprise password change;
Verify all remediation activities; and
Create a root cause analysis to prevent similar types of attacks in the future.
Indicators of Compromise (IOC)
The problem with APTs is that they are so advanced that many traditional security mechanisms, like firewalls, IDS, antivirus, etc., are ineffective. However, certain hallmarks of an APT attack, or indicators of compromise (IOCs), are known and can include the following:
Registry keys: Windows configuration files.
DLL files: Dynamic Link Library (DLL) files are Windows system files that contain procedures and drivers that are executed by a program. Multiple programs can access these shared system files. Changes might have occurred. If so, they can be identified by matching version numbers of the DLL files with the version of Windows.
ServiceDLL: If the service.dll file is found on a personal computer, the machine could be infected with the Trojan infostealer.msnbancos.
svchost.eve: This is a system process that hosts multiple Windows services. If the file
svchost.exeis located outside the System32 directory, there has been a compromise.Email: The email SMTP IP address does not match the domain name.
Ports: Regularly unused computer ports that are now used. Internet Relay Chat (IRC) is an Internet protocol for live chat. It utilizes port 6667. IRC is also used for command and control of compromised computers that are controlled by hackers.
$USN_Journal: This is the Update Sequence Number Journal, which is a feature of NTFS, and keeps track of changes on a volume. This is also referred to as the Change Journal. This file should be examined by an incident responder.
Prefetch files: New prefetch files might refer to new drivers or new downloaded files. Prefetch is a folder in the Windows system folder that contains files used in the boot process and regularly opened by other programs. The purpose of prefetch is to boot up a machine or start a program faster by keeping track of commonly used files.
System32: Contains Windows system files and other program files, which are critical to the Windows operating system. The directory can be found in C:WindowsSystem32 or C:Winntsystem32. The
System32folder may also contain malicious files installed by a hacker and be an indicator of compromise. DNS and DHCP logs can also be found in theSystem32directory.Master File Table (MFT): Contains an entry for every file that is stored on an NTFS volume and includes metadata about the file, including the size, date created, date modified, last accessed date and permissions. The MFT is a critical resource for incident responders as well as for traditional forensic examiners. This is because if anti-forensics techniques were attempted with a system, such as timestomping, or an attempt was made to delete files, then the MFT can be used to identify whether a hacker or a suspect did manipulate files. Most dates can be manipulated by an attacker except for the “FN Info Creation Date”.
The MFT can be parsed with most licensed forensics tools and there are free tools, such as Eric Zimmerman’s MFTECmd parser tool. The MFT is located here in Windows: %systemroot%$MFT.
The investigator should be very specific with search dates with an MFT parsing tool because the MFT contains a huge amount of entries. Figure 8.9 shows some sample MFT data.
Figure 8.9 Sample MFT data
Event Logs: were introduced in Chapter 2 as an important source of evidence for investigators. They are also important for IR. One example in incident response (IR) are Event IDs related to successful login attempts. Event ID 4624 indicates that a successful login occurred. However, this Event ID also provides a Logon Type. If the Event ID 4624 Logon Type is 2 (Interactive: logon at keyboard and screen of system), then we might not be concerned. However, a Logon Type of 10 (Terminal Services, Remote Desktop or Remote Assistance) could be an indicator of compromise, as sophisticated hackers will often use Remote Desktop to remotely connect to other hosts on a network, as they move laterally. This particular Event ID (4624) will also provide information about the host that successfully remotely logged onto another host. Important Event IDs, associated with Remote Desktop (RDP), are Event ID 21/22 (RDP/Citrix authentications), Event ID 23/24 (RDP/Citrix logoffs), Event ID 1158 (RDP from an IP address), and Event ID 1149 (successful RDP authentication). Other important Event IDs are 7045, 7036 and 4697 to identify installed services on an infected host machine.
At the time of writing, the website ultimatewindowssecurity.com provides a comprehensive list of Event IDs. Figure 8.10 shows a tremendous resource for searching for Event IDs of interest.

Figure 8.10 Ultimate IT Security website
MRU (most recently used) lists: are also a potential artifact of interest for an incident responder. These are a listing of applications and files recently used by a user. This file can be found in Windows Registry here: HKCUSoftwareMicrosoftWindows CurrentVersion ExplorerRunMRU.
PsExec: is a Windows command-line tool that allows a user to remotely execute processes on a computer without having to install client software. As you can imagine, it could be a tool of choice for an attacker. Ironically, PsExec is also used by Windows administrators and incident responders. Event ID 540 will show a PsExec login.
UserAssist: contains a list of programs that have been executed on a Windows computer, including the run count and last execution date and time. Didier Stevens has produced a tool to parse these entries. The file containing these entries is located here: HCUSoftwareMicrosoftWindowsCurrentVersion ExplorerUserAssist
An IR team will typically circulate a list of IOCs for team members to search for—some of which are out highlighted above. IOCs on that list may also include IP address(es) of interest, malware name(s) and MD5 hash(es) of known malware, and a list of keywords that can be used to search through an imaged drive. A keyword list may include names of malware, IP addresses, and other search terms of interest.
Investigating a Network Attack
Network attacks and breaches are not all APTs. Some attackers simply want to cause disruption and destruction, while others want to smash and grab your money or sensitive data. Identifying a compromise can be difficult, especially because an attacker may move from computer to computer in an organization and because an indicator of a compromise can be hard to find. With regards to the latter, finding small changes in a labyrinth of registry files can be like finding a needle in a haystack. Sometimes the most efficient way to identify a compromise is to compare a potentially infected system with an uninfected system. If an organization was recently attacked, and you can find the computer of an employee who is on disability leave or on vacation, that computer might not be infected and would make identifying the compromise a lot easier. Another method of identifying a compromise on a Windows machine is to look at restore points on a system. Since the introduction of Windows Vista, Microsoft has used a file backup system called Volume Shadow Copy (VSC). There are several tools used to examine VSCs, like BlackLight and ProDiscover, which can examine versions of a computer’s system at a particular point in time.
Random Access Memory (RAM)
An important indicator of compromise (IOC) is RAM. Of course, a forensic analysis of RAM requires a system to be powered on and requires special RAM live forensics tools.
AmCache
As discussed in Chapter 2, an analysis of the AmCache.hve, introduced with Windows 8, can be used to determine what applications were run by a malicious actor. Eric Zimmerman’s AmcacheParser, which is a free open source tool, will parse out the contents of the AmCache.hve, which includes installation date and time, execution date and time, the Program ID (application), and the path from which the application was run. Figure 8.11 shows output from an Amcache.hve file.

Figure 8.11 Output from Amcache.hve
ShimCache
In Chapter 2, we spoke in depth about the importance of ShimCache in investigations. As previously noted, ShimCache can potentially provide information about applications that were executed by a hacker on a system. ShimCache Parser is one of a number of tools that can be used to parse Shim-Cache. AppCompatCacheParser is another tool that can be downloaded for free to analyze ShimCache.
ShellBags
As previously noted in Chapter 2, ShellBags are valuable in identifying folders that were accessed by hackers or other users. ShellBags are located in several locations, including the following:
HKEY_USERS<USERID>SoftwareMicrosoftWindowsShell HKEY_USERS<USERID>SoftwareMicrosoftWindowsShellNoRoam
Volume Shadow Copy
Volume Shadow Copy (VSC) Service was introduced in Chapter 2 and we discussed how a comparison of copies, between different dates, can provide investigators with an idea of what changed in the system. With an APT, the attacker may have replaced Windows DLL (service files) with malicious files, for example, and an examination of VSCs may provide some insight into small changes made by a sophisticated attacker to a system. Many tools, like BlackLight, natively support of comparison of VSCs. There are also some free, open source tools, like libvshadow 4; libvshadow was created by Joachim Metz and can perform VSC comparisons.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a tool for monitoring threats on network hosts and then automatically responding to certain types of attacks. The power of EDR lies in its tremendous logging capabilities, which certainly make the life of an incident responder much easier. Carbon Black is one of the most well-known EDR tools, with comprehensive logging capabilities. However, the cost of EDR can be prohibitively expensive for most companies.
Kibana
Kibana is a free, open source, data visualization tool, which can be used for log analysis and application monitoring. The tool integrates with Elasticsearch, which is a powerful analytical search engine. Kibana uses a variety of histograms, heat maps, line graphs, and other data visualization tools, to visually identify what occurred during a specific timeframe. This is easier than scanning through thousands of logs. When using Kibana, we can identify if there was a lot of activity during a time when an employee would not normally be at work. This could indicate that a hacker in Asia has been remotely active on a host computer at 2:00 am, local time, in New York, which is during daytime hours in Asia. Kibana can also display unusual connections to IP addresses in other countries that would not be expected. It should however be noted that with APT attacks, the hackers have used proxy computers in other countries to obfuscate their identities, i.e. their true Domain Name Server and IP address. An incident responder would also search for large amounts of data being transferred out of the targeted company – an indication of data exfiltration. Kibana also has the ability to quickly search for specific Event IDs for specific hosts on a network. For example, Event ID 4624 with a logon type of 10 would be of particular interest.
Log2Timeline/Plaso
Log2Timeline is an important tool for incident responders as it takes log files and parses different types of logs, from a variety of Registry files, and creates a timeline of system logs. The tool is typically used on an infected computer once the security team has narrowed down some potential dates of compromise for a host on a network. Given the thousands of system logs that can be generated by a host each day, it is important to narrow the scope of time when an attack occurred as quickly as possible. You may want to consider adding the following files to Log2Timeline for further analysis:
WindowsAppCompatProgramsAmcache.hve
Windowssystem32configSAM
Windowssystem32configSECURITY
Windowssystem32configSOFTWARE
Windowssystem32configwinevt
SANS SIFT Workstation
The SIFT is a free suite of forensics tools, which are available from SANS Institute (www.sans.org). The tool integrates with VMWare Player, which is also a free download. The SIFT can be used to mount images and then perform different types of analysis, using the many tools included, in a virtual box, i.e., each session of the SIFT will have no impact on your personal computer. Figure 8.12 shows the SANS SIFT user interface. Learning to use virtual machines is an important skill to obtain in digital forensics and cybersecurity positions, especially when working with a system potentially infected with malware.

Figure 8.12 SANS SIFT Workstation
The SIFT supports the following file systems:
NTFS (NTFS)
iso9660 (ISO9660 CD)
hfs (HFS+)
raw (raw data)
swap (swap space)
memory (RAM data)
fat12 (FAT12)
fat16 (FAT16)
fat32 (FAT32)
ext2 (EXT2)
ext3 (EXT3)
ext4 (EXT4)
ufs1 (UFS1)
ufs2 (UFS2)
vmdk
The SIFT Workstation includes the following open source tools:
Log2timeline (Timeline Generation Tool)
Rekall Framework (Memory Analysis)
Volatility Framework (Memory Analysis)
autopsy
dc3dd
libevt
libevtx
libvshadow
lightgrep
log2timeline
RegRipper and plug-ins
Sleuth Kit
A basic knowledge of Linux is required since the Workstation does use a line command interface.
Windows Registry
In Chapter 2, we introduced Windows Registry and learned that the registries contain changes to a computer’s configuration. Generally, all 32-bit and 64-bit Windows programs store configuration and preference data in the Registry. As discussed earlier, the Registry also stores information about Plug and Play hardware configuration. For example, information about USB devices that were connected to a system are stored in HKLMSYSTEMControlSet00xEnumUSBSTOR
The Registry can also provide us with detailed information about what a hacker was doing. This is different from other investigations where the user-created files, like photos or Office documents, are of importance. A sophisticated attacker may access a host on your network, copy data and then use anti-forensics techniques. Anti-forensics is a concerted effort to manipulate files on a system to cover up a hacker’s activity. For example, a hacker may try to change the system clock on a host or change a file extension or mimic the activity of a regular user. However, a seasoned network examiner can use Windows Registry and Windows Event Viewer to identify when an intrusion occurred and gain some insight into what the hacker sought to do. We could write an entire book on the registries but in this section, we will focus on some of the most important hives and files related to incident response. Figure 8.13 shows the Registry hives.

Figure 8.13 Registry hives in Registry Editor
RegRipper is a free, open source tool that can be used to parse different registry files for a personal computer. After the investigator/responder forensically images a computer, e.g. with FTK Imager, the SYSTEM, SOFTWARE, SAM and SECURITY hives (Registry) can be copied from the image copy, copied and pasted into the folder, where you installed RegRipper and then parsed out by the tool. RegRipper is a Windows, command-line tool. Knowledge of some basic Linux commands is required to process the Registry files. We shall now discuss some important hives in more detail.
HKEY_CLASSES_ROOT (HKCR)
This registry hive stores information about applications, including file name extension associations and COM class information. This hive also includes information about program shortcuts and the user interface.
HKEY_CURRENT_USER (HCR)
This registry contains information about the user that is currently logged in to the system, which includes their desktop settings and user folders.
HKEY_CURRENT_USERSoftwareMicrosoftActiveSetupInstalledComponents
HKEY_LOCAL MACHINE (HKLM)
HKEY_LOCAL_MACHINE stores settings that apply to all users on a system. HKEY_LOCAL_MACHINE/SOFTWARE stores information about Wi-Fi networks, including SSID and MAC address. You may also find malware, installed and uninstalled programs in this hive. You may also be able to retrieve saved passwords for a user here. ShellBag information is also found in this hive and indicates which folders a user accessed and when they were accessed. You will also find prefetch files here and these files will show you how many times an application has been executed. These files have a .pf extension. Prefetch is a feature that allows a system to run faster by preloading some code that is frequently used by a user.
ImagePath is yet another potential IOC, and this is a back door found in the following registry key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftActiveSetupInstalledComponentsHKEY_USERS (HKU)
This registry contains information about all users, regardless of who is currently logged in. This information does not have to be accessed via the Registry but can be accessed here:
Documents and SettingsUser ProfileNTUSER.DAT
The NTUSER.DAT file is very important for incident response as it contains the profile of a specific user. You can identify which applications were executed on a particular computer for a specific user.
The file NTUSER.DATSoftwareMicrosoftWindowsCurrentVersion ExplorerRecentDocs Interpretation contains the last 150 files or folders opened by a specific user.
HKEY_CURRENT_CONFIG (HCU)
This registry contains configuration information for the user currently logged in to the system being examined.
Summary
Numerous network forensics tools exist, many of which are expensive, like EnCase Enterprise, but there are also numerous highly effective free, open source tools, like Wireshark and tcpdump. Networking devices, including intrusion detection systems, routers, and firewalls, can yield a tremendous amount of evidence about hosts on a network. Network forensics differs from traditional forensics because both client and internal server computers are examined. One of the most important types of server is a web server, which not only contains webpages but also contains logs relating to client computer requests. Therefore, an investigator does not have to simply rely on a suspect’s computer for Internet activity. The investigator can also subpoena a web server proprietor to obtain client requests for webpages. Internet Protocol version 4 (IPv4) is the most pervasive Internet addressing protocol today, but the inevitable exhaustion of IP addresses has necessitated the move to longer IPv6 addresses. Applications on the Internet use IP addresses to find a destination host on a network.
On a LAN, a MAC address is used to identify a host on a network and is used at the Data Link Layer of the OSI Model. The OSI Model is used to explain how data is routed from one host on the Internet to another host. Investigators must understand the different layers of the OSI so that they can explain how communications are transformed as they move from one layer to another, while also demonstrating that they can prove that a suspect was responsible for a particular communication. The Transport Layer of the OSI Model is arguably the most important because many of the tools that analyze TCP/IP traffic are invaluable to investigators, particularly when identifying network intrusions by hackers.
An investigator whose knowledge is limited to examining client computers, and who does not understand the network or networks that it is connected to, runs the risk of missing important evidence. This can actually lead to the arrest of the wrong individual, as noted in an earlier case study.
Advanced persistent threats (APTs) are a major concern for the United States and illustrate how important it is for organizations to hire network forensics investigators instead of relying on existing IT security personnel. These threats are so sophisticated that many traditional methods of security are unreliable. APTs are developed using months of planning. Many organizations do not realize that they publicly provide information that gives an attacker a wealth of information about their network infrastructure. This information can be gleaned from job postings, press releases, corporate websites, and a variety of other sources.
Incident Response (IR) requires a knowledge of both network and computer forensics. IR is very different from traditional forensics because (1) many more computers on a network must be examined, (2) the investigation is generally performed internally within an organization, (3) rates of prosecution are much lower since the actor is often remotely accessing a host and the chances of extraditing the perpetrator are extremely low, and (4) system logs are the focus of the investigation rather than user-created documents. There are numerous indicators of compromise, and an examination of Event IDs are critical to identify how an attacker logged onto a system and determine what services were installed. In terms of identifying which programs were executed, the examiner can review the following forensics artifacts: AmCache, Prefetch, ShimCache and RecentFileCache.bcf. Eric Zimmerman has developed numerous free, open source tools to assist incident responders with examining Windows operating system artifacts.
Key Terms
Address Resolution Protocol (ARP): A method by which the Network Layer (Layer 3) of the OSI is linked to the Data Link Layer (Layer 2).
advanced persistent threat (APT): A sophisticated, relentless, coordinated attack on a computer network, with the goal of stealing intellectual property.
anti-forensics: A concerted effort to manipulate files on a system to cover up a hacker’s activity.
Application Layer: The closest layer to the end user. Interacts with applications.
Browser Help Object (BHO): Adds functionality to a web browser. The object starts every time the user opens the browser.
default gateway: The node on a network that serves as the forwarding host (router) to other networks
Domain Name System (DNS): A naming system for computers and other devices connected to the Internet.
Dynamic Host Configuration Protocol (DHCP): A standard for allowing a server to dynamically assign IP addresses and configuration to hosts on a network.
Dynamic Link Library (DLL) files: Windows system files that contain procedures and drivers that are executed by a program.
firewall: Software or hardware mechanism used to inspect data packets on a network and determine, based on a set of rules, whether each packet should be allowed through.
hosts file: A text file found on Windows that maps hostnames to IP addresses.
Hub: A hardware networking device that broadcasts data packets to all devices on a network regardless of the MAC address.
HyperText Transfer Protocol (HTTP): A standard for requests and responses between a client and a server.
Internet Assigned Numbers Authority (IANA): Organization that is responsible for the allocation of IP addresses globally.
Internet Protocol version 4 (IPv4): The fourth version protocol for connectionless data transmission on packet-switched internetworks.
intrusion detection system (IDS): Hardware or software used to monitor network traffic for malicious activity.
managed service provider (MSP): A company that generally provides IT infrastructure services, like cloud storage, to an organization.
Multipurpose Internet Mail Extensions (MIME): An electronic email protocol that extends character sets beyond ASCII and supports email attachments.
Network Address Translation (NAT): A protocol that allows multiple network devices on a network to share a single IP address (see RFC 1631).
Network Layer: Defines communications between networks or operation of the subnet and makes decisions about the physical path through which transmission should occur.
Open Systems Interconnection (OSI) Model: A model used to define how data is transmitted across the Internet.
packet: A block of data transmitted across a network.
packet sniffers: Used to capture data packets on a wireless or wired network.
PBX (Private Branch Exchange): A telephone system, within an organization, that switches calls between users in that organization on local phone lines and enables users to share a limited number of external phone lines.
Physical Layer: Defines the hardware or medium through which data is transmitted and the power required for transmission.
port: Communication channel that is specific to a running process or application on a computer.
Prefetch: A folder in the Windows system folder that contains files used in the boot process and also files regularly opened by other programs.
Presentation Layer: Prepares data for the Application Layer and is responsible for data conversion, compression, and encryption.
promiscuous mode: Enables a NIC to listen to communications broadcast on a network, regardless of the intended recipient.
protocol analyzer: Used to analyze and interpret traffic over a network.
proxy server: A computer that relays a request for a client to a server computer.
router: Hardware that connects a network to one or more other networks and directs data packets from one node to another.
routing table: Contains information about the network and provides the most effective method of directing packets across that network.
Secure Data Transmission: The process of sending data over a secure channel, whereby the channel remains secure through the use of encryption.
Session Layer: Responsible for initiating, maintaining, and terminating processes on different systems.
Simple Mail Transport Protocol (SMTP) server: Used to send email, for a client, and the email is then routed to another SMTP server, or other email server.
subnet mask: Facilitates the communication between segregated networks.
switch: An intelligent hardware device that connects devices on a network.
Timestomping: An anti-forensics technique used to manipulate the timestamps of a file.
Traceroute: A tool used to track the path of IP packets from one system to another.
Transmission Control Protocol (TCP): A communication standard that is used in conjunction with the Internet.
Trojan: A legitimate-looking application used to disguise malware.
Uniform Resource Identifier (URI): Used to locate a resource on the Internet.
User Datagram Protocol (UDP): A connectionless communication protocol that has limited packet recovery functionality and operates at the Transport Layer.
Voice over Internet Protocol (VoIP): A protocol that takes analog audio signals, e.g., voice, and converts those signals to digital data that can be transmitted across the Internet.
web browser: Used to (1) work with a DNS server to resolve DNS addresses, (2) make HTTP requests, (3) download resources, and (4) display the contents of the file with browser help Objects (BHO).
web server: Stores and serves up HTML documents and related media resources in response to client requests.
Assessment
Classroom Discussions
1. How is the job of a network forensics examiner different from that of a traditional computer forensics examiner?
2. What difficulties are associated with investigating APTs?
3. Discuss indicators of compromise (IOCs) that an investor should look for in a network intrusion investigation.
Multiple-Choice Questions
1. Which of the following best describes malware that is disguised as a legitimate application or program?
Worm
Virus
Trojan
Logic bomb
2. Which of the following has a primary function of serving up HTML documents?
Web server
Proxy server
SMTP server
Virtual server
3. What is the name of the folder in the Windows system folder that contains files used in the boot process and regularly opened by other programs?
User
Journal
svchost
Prefetch
4. Which layer of the OSI Model can be viewed as closest to the user view?
Session Layer
Application Layer
Presentation Layer
Transport Layer
5. Which layer of the OSI Model defines the wires that electrical impulses flow through that are involved in Internet communication?
Transport Layer
Session Layer
Data Link Layer
Physical Layer
6. Which of the following is a protocol for connectionless data transmission on packet-switched internetworks? Its header has 14 fields. This protocol uses 32-bit addresses, which are usually represented in four octets of dotted decimal notation.
IPv2
IPv4
IPv6
IPv8
7. Which of the following enables a NIC to listen to communications broadcast on a network, regardless of the intended recipient?
Proprietary mode
Passive mode
Promiscuous mode
Active mode
8. Which of the following defines the standard format for electronic mail?
IRC
ICMP
SMTP
HTTP
9. Within the OSI Model, this layer is responsible for initiating, maintaining, and terminating processes on different systems.
Transport Layer
Session Layer
Data Link Layer
Physical Layer
10. Which of the following organizations is responsible for the allocation of IP addresses globally?
ISO
IEEE
IANA
NIST
Fill in the Blanks
1. A(n) __________ is a block of data used in communications across the Internet.
2. Transmission __________ Protocol is a communication standard that is used in conjunction with the Internet.
3. A(n) __________ detection system is hardware or software used to monitor network traffic for malicious activity.
4. User __________ Protocol is a connectionless communication protocol that has limited packet recovery functionality and operates at the Transport Layer.
5. Address __________ Protocol is a method by which the Network Layer (Layer 3) of the OSI Model is linked to the Data Link Layer (Layer 2).
6. A(n) __________ Help Object is used to add functionality to a web browser. The object starts every time the user opens the browser.
7. Dynamic __________ Library files are Windows system files that contain procedures and drivers that are executed by a program.
8. An advanced __________ threat is a sophisticated, relentless, coordinated attack on a computer network, with the goal of stealing intellectual property.
9. Packet __________ are used to capture data packets on a wireless or wired network.
10. HyperText __________ Protocol is a standard for requests and responses between a client and a server.
Projects
Research Internet Crimes
Conduct a search for crimes on the Internet that you believe would require the skills of a network forensics investigator. Detail the nature of the network evidence that would have been helpful to the investigation.
Write a Report Detailing Evidence Types Found on a Computer
Write a report detailing the type of evidence that can be found on a client computer relating to a user’s network activity.
Create an Investigation Guide on Device Types
Create a guide for investigators that details the type of devices in a home or business network that may contain valuable evidence.
Log2Timeline/RegRipper
Create an E01 file image of a Windows personal computer, using FTK Imager. Download either Log2Timeline or RegRipper. Use the files from your image, to examine the registry files, and then report what you find. Include in your report data from the NTUSER.DAT file.
SANS SIFT Workstation (Advanced)
Create an E01 file image of a Windows personal computer, using FTK Imager. Register and then download a copy of the SANS SIFT Workstation from www.sans.org. Download VMWare Player (free version). With some direction from your teacher/professor, try some of the many tools from the suite of applications contained in the SIFT workstation.
