Chapter 7
Admissibility of Digital Evidence
Learning Outcomes
After reading this chapter, you will be able to understand the following:
The structure of the legal system in the United States;
The role of constitutional law in computer forensics;
Principles of search and seizure of computers and other digital devices;
Rules for the admissibility of evidence at trial;
Case law concerning the use of digital surveillance devices by law enforcement;
Cases of computer forensics gone wrong;
Structure of the legal system in the European Union; and
Data privacy and computer forensics in the European Union.
The United States legal system is one of the most complicated in the world, primarily as a result of a dual legal system that is comprised of federal and state laws and their respective court systems. This complexity also makes for arguably one of the most exciting legal systems in the world.
Like other legal systems worldwide, U.S. legislation has been complicated further by the growing importance of digital evidence in criminal investigations and trial proceedings. U.S. legislation at all levels (federal, state, and local) has been impacted by computers and other digital devices. This chapter details how traditional laws have been applied to new technologies and how traditional laws have been amended to address the admissibility of digital evidence, and how new laws have been introduced to keep up with advances in technology.
History and Structure of the United States Legal System
First and foremost, a state-based legal system predates the federal legal system in the United States. Prior to the War of Independence, each of the 13 states operated with autonomy, with their own legal system, including their own official religion. For example, Maryland was originally established as a Catholic colony, whereas the Church of England was the state religion for New York, Virginia, Georgia, North Carolina, and South Carolina. These disparate entities, formerly known as colonies, were eventually united by a common outrage: taxation by Britain without representation. Although there was some notion of a confederation, this union did not have a tremendous amount of meaning until it became apparent that states needed to be united to fight the “oppression” of taxation by the British Crown and government. Furthermore, this confederation could be effective only if states were forced to fund a Congress that could then fund a Union Army. These states would also require this Congress to establish common laws for this federation—in other words, the institution and ratification of federal laws. Understandably, it took quite some time for each of these states, with a variety of denominations, ethnicities, and values, to come to an agreement on a new legal system that would coexist with their established state system. The relationship between a federal and state system was contentious during colonial times, and this relationship was severely tested during the American Civil War, which was not as much about the abolition of slavery as it was about the supremacy of the federal government on contentious issues such as the extension of slavery. The Civil War was also about the future of the U.S. economy: the rural, agrarian economy of the South, which was a vision of the future for founding father Benjamin Franklin, versus the urban capitalist society of the North, which was the way forward for Alexander Hamilton.
What does all of this have to do with computer forensics? The answer is that both federal and state laws impact criminal investigations and court trials. Moreover, investigations and court proceedings at the state and county levels are influenced by the Constitution, which is a federal document that protects the rights of the individual. Additionally, a computer forensics investigator must abide by federal and state laws, when conducting an investigation.
Interestingly, a case can be tried in a number of different ways. For example, in a criminal investigation, a jury might find the defendant not guilty. A jury is a group of people put under oath to hear arguments at trial and render a verdict of guilty or not guilty. But a civil lawsuit then can ensue, with a victim seeking monetary compensation against an offender or third party for physical damage or emotional distress. The plaintiff is the person who initiates the lawsuit and is responsible for the cost of litigation. The defendant is the person who defends him- or herself in a lawsuit. O. J. Simpson was acquitted of the murders of Nicole Brown Simpson and Ronald Goldman in a criminal trial, but the families successfully secured a $33.5 million settlement against him in civil court.
The Civil War ended more than a century and a half ago, but there is still a dichotomy of laws and authority between federal and state institutions in the United States. Problems still exist today, as evidenced by certain states with different immigration laws compared to the President of the United States, and other members of Congress. This tension is also clearly illustrated by California’s state law legalizing the use of marijuana for medicinal purposes, yet these distributors are operating illegally under federal law.
The United States Constitution was created on September 17, 1787, and then subsequently ratified by each state. With this ratification, the Constitution (and federal government) is supreme concerning the powers delegated to it, yet it still recognizes the sovereignty of the states and their supremacy over matters of state. The Constitution is a framework that defines the relationship between the federal government, its united states, and its citizens. The Constitution has been amended 27 times. The Bill of Rights refers to the first 10 amendments to the Constitution, which protects the rights of the individual.
The first three Articles of the Constitution establish the three branches of government: Article I, the Legislature (Congress), which is comprised of the House of Representatives and the Senate; Article II, the Executive (President); and Article III, the Judicial (Supreme Court and lower federal courts). In summary, Congress writes laws, the Supreme Court interprets those laws, and the President has the power to either sign into law or veto Congressional legislation.
Origins of the U.S. Legal System
The origins of the legal system in the United States are found in common law and English law. Common law is based on case law and precedent, with laws derived from court decisions. With precedent, court decisions are binding on future decisions in a particular jurisdiction. Therefore, these laws are derived not from legislation, but based on court decisions. The exception to this legal system is Louisiana, where the legal system was originally based on the Napoleonic Code. The Napoleonic Code has its origins in Roman law. Napoleon developed a written, uniform code of laws to assist in the administration of his vast empire.
The Napoleonic Code was based on civil law. Civil law is based on scholarly research, which, in turn, becomes a legal code, and is subsequently enacted by a legislature. There is no precedent. The Louisiana Civil Code Digest of 1808 has changed over time, and the current legal system in Louisiana is not that much different today from other states.
Three primary bodies of law exist in the United States: (a) constitutional law, (b) statutory law, and (c) regulatory law. Constitutional law outlines the relationships among the Legislative, Judiciary, and Executive branches, while protecting the rights of its citizens. It is also referred to as federal law. Statutory law is written law set forth by a legislature at the national, state, or local level. There are codified and uncodified laws in statutory law. Codified laws are statutes that are organized by subject matter. An example of this is the United States Code (U.S.C.). Regulatory law governs the activities of government administrative agencies. This body of law involves tribunals, commissions, and boards that are responsible for decision making. These decisions affect the environment, taxation, international trade, immigration, and so forth.
Overview of the U.S. Court System
It is important to explain the structure of the U.S. court system because you will then have a better understanding of the rationale for cases being tried in federal court versus those cases tried in state or county courts. A criminal prosecution might be tried in federal court because of the jurisdiction, meaning that crimes were committed across multiple states. Another reason for trying a case in federal court might be the nature of the crime. For example, the victim and perpetrator could both be located in California, but the defendant was accused of corporate espionage, which threatens national security and is therefore a federal case. Sometimes a case begins in a state court, but the case is then referred to a federal district court. This is common when the judge has determined that guilt or innocence depends on an interpretation of the Constitution; in other words, it is a constitutional matter.
In some cases, local law enforcement in multiple states collaborate. The criterion for determining where the case should be tried is often determined by deciding which of the states has tougher laws for a particular crime. Other times, one state might lack legislation for certain offenses. Figure 7.1 illustrates the basic structure of the court system.
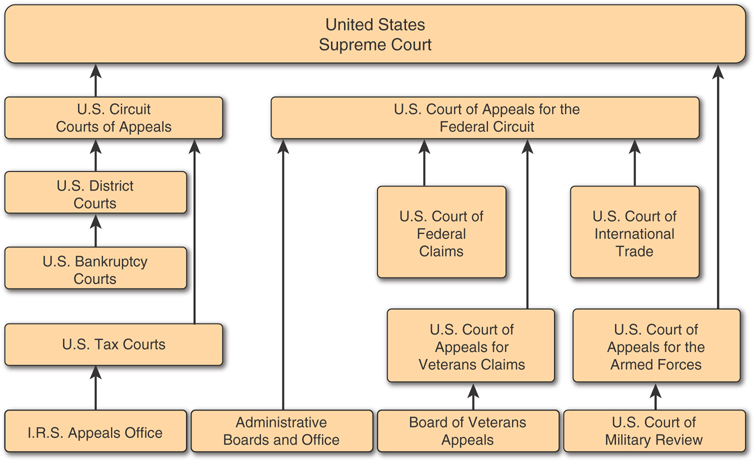
Figure 7.1 U.S. court system
The basic structure of federal, state, and local courts is the same. A defendant has the right to a fair trial, with the outcome determined by a jury of his or her peers. The role of the judge is to facilitate the trial process and ensure that the proceedings are in accordance with the law. The judge must also ensure that the proceedings are free of prejudice and that the innocence of the defendant is presumed until proven otherwise. The burden of proof is always on the prosecution. The role of the jury is to determine the facts of a case and render a verdict.
Appeals Courts
The U.S. court system enables its citizens to appeal a conviction. An appeals court decides whether to hear an appeal. Note that a court appeal is not a trial—there is no jury, so a panel of judges renders a decision about whether a mistake occurred in a lower court. One example might be that evidence was presented at trial that should have been deemed inadmissible. In that situation, the case is sent back to be retried, without the evidence deemed admissible. The prosecution may decide that the case is not worth retrying without a key piece of evidence deemed inadmissible or they may decide to retry the case in court. The panel of appeal judges consists of an odd number of judges and decides whether there has been a mistake of law in a previous trial.
Federal Courts
Two types of federal courts exist. The first type is derived from Article III of the Constitution. It consists of the U.S. District Courts, the U.S. Circuit Courts of Appeal, and the U.S. Supreme Court. There are two other types of Article III courts: the U.S. Court of Claims and the U.S. Court of International Trade. These special courts do not have general jurisdiction. Jurisdiction refers to the scope of legal authority granted to an entity.
The next category of federal court was not established by Article III but rather was created by Congress. These courts include magistrate courts, bankruptcy courts, the U.S. Court of Military Appeals, the U.S. Tax Court, and the U.S. Court of Veterans’ Appeals.
Supreme Court
Under Article III, the President of the United States is responsible for appointing federal judges, which includes Supreme Court justices. Their appointment is subject to the approval of the Senate. The appointment is for life unless removed through impeachment. The Supreme Court has one chief justice and eight associate justices. The role of the Supreme Court was largely decided with the case of Marbury v. Madison, in 1803, when the court demonstrated its right to interpret the Constitution and be the ultimate decision-maker in congressional issues. In other words, the judiciary branch is the ultimate arbiter of the law, not Congress or the President.
Article II of the Constitution outlines the jurisdiction of the Supreme Court and other federal courts:
The judicial Power shall extend to all Cases, in Law and Equity, arising under this Constitution, the Laws of the United States, and Treaties made, or which shall be made, under their Authority; to all Cases affecting Ambassadors, other public Ministers and Consuls; to all Cases of admiralty and maritime Jurisdiction; to Controversies to which the United States shall be a Party; to Controversies between two or more States; between a State and Citizens of another State; between Citizens of different States; between Citizens of the same State claiming Lands under Grants of different States, and between a State, or the Citizens thereof, and foreign States, Citizens or Subjects.
Federal Appellate Courts
There are 13 circuit courts of appeals, which were first established in the original 13 states of the United States. Today there are 12 regional circuit courts in several cities, as well as an additional Federal Circuit Court (13th Court) in Washington, D.C. Each of these circuits is assigned a circuit justice from the Supreme Court.
This chapter highlights many notable circuit court decisions with respect to the admissibility of digital evidence. One of the most noteworthy districts is the Ninth Circuit, which is by far the largest circuit and covers districts in Alaska, Arizona, California (Central, Eastern, Northern, Southern), Hawaii, Idaho, Montana, Nevada, Oregon, and Washington (Eastern and Western), with appellate jurisdiction over the territories of Guam and Northern Mariana Islands courts. These courts hear cases referred from lower federal district courts, known as U.S. District Courts.
Ultimately, the federal appellate courts can refer cases to the U.S. Supreme Court. Typically, three judges sit in these courts.
U.S. District Courts
There are 94 U.S. District Courts across the United States. Every state has at least one District Court, and larger states have more. For example, New York has a Southern District of New York (Bronx, Dutchess, New York, Orange, Putnam, Rockland, Sullivan, and Westchester counties), a Northern District of New York (from Ulster County and North), the Eastern District of New York (Kings, Nassau, Queens, Richmond, and Suffolk counties), and a Western District of New York. There can be multiple courthouses in each district. For example, in the Southern District of New York, there are courthouses in White Plains and New York City (Manhattan).
Most federal cases begin in a U.S. District Court. Cases in these courts can be civil or criminal. A kidnapping or intellectual property dispute case generally is the type of case tried in a U.S. District Court.
State Courts
The state court system varies from state to state. Nevertheless, there are some similarities. Local trial courts are located throughout the state and hear cases at the lower level. If the defendant is found guilty, the defendant can appeal a conviction in a state appellate court.
State Appellate Courts
Two types of state appellate courts exist. Often referred to as supreme courts or courts of appeal, these are the highest courts in the state judicial system. They have discretion over which cases they hear and are often referred cases where there could be an error in determining the law. They are confined to a particular jurisdiction and can be asked to preside over contentious decisions, like elections. Anywhere from three to nine judges can sit on a panel in a state appellate court.
Intermediate Appellate Courts
Intermediate appellate courts exist in 40 of the 50 states. The following states have no appellate courts: Delaware, Maine, Montana, Nevada, New Hampshire, Rhode Island, South Dakota, Vermont, West Virginia, and Wyoming. The number of these courts varies from state to state, as does the number of judges. Decisions from appellate courts can be appealed to the state’s highest court, which is referred to as the State Appellate Court.
Trial Courts of Limited Jurisdiction
Trial courts of limited jurisdiction are limited to hearing certain types of cases. These courts include the following:
Probate court: Sometimes referred to as a surrogate court, this court hears cases relating to the distribution of a deceased’s assets.
Family court: This court hears cases relating to family matters, including child custody, visitation, and support cases, as well as restraining orders.
Traffic court: This court hears cases relating to driving violations. An individual who is cited for a traffic violation can pay the fine (plead guilty) or can appeal in traffic court. With DUI (driving under the influence) citations, the individual may be required to appear in court before a judge. DUI and DWI (driving while intoxicated) are crimes, and these cases can be tried in criminal courts in many jurisdictions.
Juvenile court: In this court, minors are tried by a tribunal. The court generally hears cases against defendants who are under the age of 18. However, more serious crimes, like murder or rape crimes, that are committed by juveniles can be moved to a different court, where the defendant is prosecuted as an adult.
Small claims court: The function of these courts is to settle private disputes involving relatively small monetary amounts.
Municipal court: This court hears cases when a crime has occurred within their jurisdiction. These can include DUI, disorderly conduct, vandalism, trespassing, building code violations, and similar offenses.
Trial Courts of General Jurisdiction
A trial court of general jurisdiction can basically hear any kind of criminal or civil case that is not exclusive to another court.
New York Trial Courts
It is probably helpful to see an example of how the court system is set up in a particular state. For this example, let us consider New York State. In New York City, a trial by jury can be held in the following courts:
Supreme Court
New York City civil court
New York City criminal court
Outside of New York City, a jury trial can be held in the following courts:
Supreme Court
County court
District court
City court
Town and village court
A civil trial lasts for an average of 3 to 5 days; a criminal trial generally averages 5 to 10 days. The following people generally are present at trial:
Attorneys (or Counsel)
Court reporter
County clerk
Court officer
Defendant
Interpreter
Jury
Plaintiff
Prosecutor
Spectators
Witnesses
In the Courtroom
It is helpful for a computer forensics examiner to understand the pretrial and trial process because they might one day become part of that trial as an expert witness. The following is an outline of the steps taken during the pretrial and trial in a civil or criminal case:
Jury selection
Oath and preliminary instructions
Opening statement(s)
Testimony of witnesses and presentation of other evidence
Closing arguments
Jury instructions
Deliberations
Verdict
Sentencing
The Jury
The right to a trial by jury is clearly outlined in the Sixth Amendment to the U.S. Constitution:
In all criminal prosecutions, the accused shall enjoy the right to a speedy and public trial, by an impartial jury of the State and district wherein the crime shall have been committed, which district shall have been previously ascertained by law, and to be informed of the nature and cause of the accusation; to be confronted with the witnesses against him; to have compulsory process for obtaining witnesses in his favor, and to have the Assistance of Counsel for his defense.
Voir dire is the questioning process used in the jury selection process. During voir dire, lawyers and, in some cases, the judge ask potential jurors questions to determine any prior knowledge of the facts of the case or any biases that could influence their impartiality in the case. All defendants are presumed innocent until proven guilty beyond a reasonable doubt. Jurors may be required to fill out a survey prior to oral questioning. In a criminal case, voir dire is recorded by the court reporter and becomes part of the trial record. If used, the questionnaire and responses also become a part of the trial record. Generally, in civil trials, voir dire and any questionnaire would not become part of the court record.
Civil trials typically have 6 jurors and up to 4 alternates. For criminal felony trials, there are 12 jurors and up to 6 alternatives. In lesser criminal trials there may be 6 jurors and up to 4 alternates. During the trial, jury members may not discuss the trial amongst themselves or with others and may not read about the case. This is because each juror must hear all facts of the case before making a decision. A juror can be held in contempt of court if he or she discusses the trial before deliberations occur. In certain trials, particularly highly publicized trials, the jury can be sequestered in local accommodations, instead of being allowed to go home each day. Jury sequestration refers to isolating the jury and preventing external influences on jury decisions. Contempt of court means violating the rules of court procedure. The foreperson is usually the first juror seated and is ultimately responsible for reporting the verdict to the judge.
Opening Statements
During a criminal trial, the prosecution makes an opening statement first because the burden of proof is on the prosecution. The burden of proof implies that a defendant is innocent until proven guilty, the prosecution must prove guilt, and the defense must not prove anything. Under the Fifth Amendment, the defendant need not speak ever during the trial. Of course, in practice, defense counsel makes opening and closing remarks and is involved in direct examination and in cross-examination. A direct examination is the questioning of counsel’s witness in a trial. A cross-examination is the questioning of the opposing side’s witness in a trial.
Verdicts
Deliberations are the process whereby the jury reviews the evidence from the trial and discusses opinions about the case. A hung jury occurs when the jury cannot come to a unanimous decision in a criminal trial and a retrial must occur. Unlike a criminal trial, in a civil trial, the decision by the jury does not need to be unanimous. The jury also decides compensatory issues in a civil trial.
After the jury has reached a verdict, it is the responsibility of the judge to determine the sentence. Following deliberations, the foreperson informs the court officer that the jury has reached a decision and will deliver a verdict.
Criminal Trial Versus Civil Trial
Criminal charges are initiated by government prosecutors on behalf of the people. As a result, the defendant is indicted to stand trial and answer questions relating to serious crimes or provide information. A felony is a serious crime and generally carries a penalty of a year or more in prison. A misdemeanor is a less serious crime, with a possible sentence of less than a year. In a civil trial, depositions may be taken whereas in a criminal trial, they are generally not taken. A deposition is sworn witness testimony taken, prior to a trial (discovery phase), which can be presented during a civil trial. Thus, witness testimony and cross-examination are largely based on their depositions recorded during discovery. In a criminal trial the government accuses an individual of breaking the law, a statute or a penal law that appears to have been violated. In a civil case, a case is brought by an individual or organization (including corporations and the government), referred to as the plaintiff, against an individual or organization.
Civil trials generally involve disputes over money. If successful, the plaintiff is awarded money by the jury. A civil trial identifies whether an entity failed to act reasonably and prudently under a certain set of circumstances. The standard that needs to be met to win a civil trial is referred to as preponderance of the evidence. This means that most of the evidence presented indicates which party was in the right and which party was in the wrong. In a criminal trial, the burden of proof is on the prosecution to prove that the defendant is guilty. In a civil trial, the burden of proof begins with the plaintiff. However, in civil trials, the burden of proof can move to the defense to prove that he or she was not at fault. In a criminal trial, the standard to prove guilt is “beyond a reasonable doubt”. This means that, regardless of the evidence, there must be no doubt in the minds of all jurors that the defendant is guilty. Of course, this is a different standard than preponderance of the evidence. Table 7.1 summarizes the differences between criminal and civil trials.
Table 7.1 Comparison of Criminal Versus Civil Trials
Description |
Criminal Trial |
Civil Trial |
Deposition |
No |
Yes |
Trial law |
Statutes, penal laws, and precedent |
Plaintiff claims defendant was negligent |
Charges |
Accused of felony or misdemeanor |
Lawsuit |
Voir dire |
Part of trial record |
Not recorded |
Litigant |
Government prosecutor |
Plaintiff (individual or organization) |
Jury members |
Up to 12 jurors + 6 alternates |
6 jurors + 4 alternates |
Verdict |
Must be unanimous |
Majority rule |
Sentence/Penalty |
Delivered by the judge |
Delivered by the jury |
Evidence Admissibility
The judge is responsible for deciding whether the evidence being submitted is legally admissible. Evidence can include witness testimony. The admissibility of digital evidence is problematic because judges were originally trained to be lawyers years earlier. The prosecution and investigators are often called upon to explain to a judge why certain types of digital evidence should be admitted in a case. A judge may know what an email is but may not know what a system log is and whether it is acceptable in court. These system logs could be critical in determining the fate of a defendant. Moreover, a jury is comprised of individuals with various backgrounds and occupations. For example, a juror could include a pastry chef, a shoe salesman, a geography teacher, or a stay-at-home mother. Imagine how difficult it can be for the prosecution to explain system logs, IP addresses, file registries, and so on.
Constitutional Law
George Mason, author of the Virginia Declaration of Rights, became an opponent of the Constitution because he stated, “It has no declaration of rights”. Mason’s views were strongly considered, and ultimately, James Madison drafted a series of amendments to the Constitution. These amendments were based on Mason’s Virginia Declaration of Rights and later became known as the Bill of Rights. The Founding Fathers originally intended for the Supreme Court to decide on the constitutionality of laws passed by Congress. However, in 1803, with the landmark case of Marbury v. Madison, the Supreme Court became recognized as a court for judicial review. As previously noted, cases that require an interpretation of the U.S. Constitution are handled by the federal court system, which includes the U.S. Supreme Court.
First Amendment
Surprisingly, many books and articles that detail the impact of constitutional law simply focus on the Fourth Amendment and fail to recognize the importance of other amendments, like the First Amendment. So many cases today involve digital evidence that relate to an individual’s First Amendment rights. The importance of this amendment is especially pertinent in cyberbullying cases. The First Amendment states the following:
Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the Government for a redress of grievances.
We know that this amendment was written long before the advent of digital communications. Nevertheless, we rely on the Supreme Court and lower federal courts to interpret what protections a person posting insulting comments about an individual on a blog has, in addition to the rights of the victim. Can any opinion, no matter how disturbing, be posted on a blog? The initial answer is no—you cannot post a message that could incite a disturbance or violence. In March 2011, the Supreme Court ruled that the First Amendment protected the Westboro Baptist Church from suits seeking emotional distress caused by picketing (see Snyder v. Phelps, 562 U.S. 443 (2011)). The church made headlines with its protests at military funerals and its condemnations of homosexuals, Catholics, and Jews. Others waved signs with captions like “THANK GOD FOR DEAD SOLDIERS”, The Supreme Court agreed to review the case following the conflicting decisions of two circuit courts in Ohio. Unfortunately, there is sometimes a difference between moral responsibility and constitutional law.
First Amendment and the Internet
The Internet is relatively new. Therefore, we rely on traditional laws and case law to guide us most of the time. One area of constitutional law that is still being explored and interpreted involves freedom of speech, the role of the school, and school control over student activities on the Internet.
It is important to begin this discussion with a landmark case that predates the Internet as we know it today. The case of Tinker v. Des Moines Independent Community School District, 393 U.S. 503 (1969), was a case heard by the Supreme Court over the rights of a student to protect school policy. Two siblings, John and Mary Beth Tinker, decided to protest the Vietnam War by wearing black armbands to school. The Des Moines School District adopted a policy banning students from wearing the armbands and stated that students who did not comply would be suspended and could return only when they agreed to comply. The Tinker siblings chose not to comply by wearing the black armbands and were also joined by Christopher Eckhardt. As expected, the students were summarily suspended. The Tinker parents filed suit in U.S. District Court (under 42 U.S.C. § 1983), claiming that their First Amendment right to freedom of speech had been violated. However, the court agreed with the school’s policy. When the case came to the Eighth Circuit U.S. Court of Appeals, a panel of judges was tied in its decision, which meant that the U.S. District Court decision stood. The Tinkers and Eckhardts then appealed to the Supreme Court. The Supreme Court ruled that the Tinkers’ and Christopher Eckhardt’s First Amendment rights had been violated and that the First Amendment does apply to public schools. The Court noted, “It can hardly be argued that either students or teachers shed their constitutional rights to freedom of speech or expression at the schoolhouse gate”.
According to the Supreme Court, student expression may not be suppressed unless it will “materially and substantially disrupt the work and discipline of the school”.
In the case of Layshock et al v. Hermitage School District et al, Justin Layshock’s parents argued that their son’s school violated Justin’s First Amendment right to freedom of speech. Justin created a fake MySpace profile of Eric Trosch, the school principal for Hickory High School, Pennsylvania. Justin posted the following comments online:
In the past month have you smoked? Big Blunt
Use of alcohol? Big keg behind my desk
Your birthday? Too drunk to remember
Big steroid fan
Big whore
Big hard ass
The school asserted that Justin had been disrespectful and disruptive with his comments. Word spread around the school about the profile page. Justin attempted to delete the profile page, and he apologized to the principal. Subsequently, the school contacted MySpace to have the page removed. Justin and his father were summoned to the local police station for questioning, but no charges were filed. Justin, a 17-year-old with a 3.3 GPA, seemed destined for college. However, the school placed Justin in an alternative program comprised of students with behavior and attendance problems. The class met only three hours a day and had no assignments from regular classes. Justin was also banned from extracurricular activities, including Advanced Placement (AP) classes and the graduation ceremony.
Justin’s parents filed suit in federal court, arguing that the school had overstepped its bounds with an off-campus ban. Furthermore, they argued that they were responsible for Justin outside of school. They argued that their son had created a non-threatening parody of the school’s principal. The school argued that Justin’s behavior was disruptive because the school’s computers had to be shut down after so many students visited the profile page, which then led to class cancellations. The IT staff also needed to install extra firewall protection. The court encouraged the school and the parents to reach a settlement, which they did. Justin could return to regular classes, was allowed to participate in extracurricular activities, and could attend graduation.
In February 2010, a three-judge panel of the Third Circuit of Appeal ruled that the school had violated Justin’s First Amendment rights. In its opinion:
…the reach of school authorities is not without limits.…It would be an unseemly and dangerous precedent to allow the state in the guise of school authorities to reach into a child’s home and control his/her actions there…we therefore conclude that the district court correctly ruled that the District’s response to Justin’s expressive conduct violated the First Amendment guarantee of free expression.
The school’s principal later filed a suit claiming that Justin’s actions had damaged his reputation, caused humiliation, and impaired his earnings capacity. The court ruled that Justin’s statements were not malicious, and the principal was ordered to pay punitive damages.
Federal court judges have not always found in favor of a student’s right to post derogatory comments online and not suffer repercussions. The case of Avery Doninger v. Lewis Mills High School is an interesting case related to the First Amendment rights of students in school (see Doninger v. Niehoff, 527 F.3d 41 (2d Cir. 2008)). Avery Doninger was a 16-year-old junior, who was class secretary and a member of the student council at Lewis Mills High School, Connecticut. In 2007, she had been planning “Jamfest” (Battle of the Bands). The event had been canceled three times and was likely to be canceled again because the school’s technician was unavailable. An upset Avery sent emails to get community support and encouraged people to antagonize the principal and superintendent. Avery posted the following message to her LiveJournal blog: “jamfest is canceled due to the douchebags in central office—here is a letter to get an idea of what to write if you want to write something or call her [school superintendent] to piss her off more”. When the school found out about Avery’s online comments, it prevented her from running for senior class secretary. Students wore T-shirts with “Team Avery” on them, which the school banned. Even though Avery’s name was not on the ballot, she still won the student election, although Avery was not permitted by the school to take office. Avery’s mother filed a lawsuit, arguing that it was unconstitutional for the school to prevent her daughter from running for office, and that the school had intentionally inflicted emotional distress. The case was then moved to federal court because it was deemed to be a constitutional matter related to the First Amendment.
The court ruled that, as a student leader, Avery should have exhibited qualities of good citizenship both on and off campus. Furthermore, her comments were intended to irritate the superintendent, which was in violation of school policy. Moreover, Avery had not been barred from school office based on skin color, religion, or politics. Avery had been prevented from running from office because of the language on her blog and the risk of disruption at school. Avery was free to express her opinion, but the First Amendment does not protect the right to run for a voluntary extracurricular position. Her request for a new election was denied. The Second Circuit Court of Appeal ruled that the school did not violate Avery’s constitutional rights in disciplining her because Avery’s blog “created a foreseeable risk of substantial disruption” at the school.
However, there are limits on certain types of speech. In the case of Miller v. California, 413 U.S. 15 (1973), the U.S. Supreme Court affirmed that obscenity is not protected by the First Amendment.
Fourth Amendment
The Fourth Amendment of the Constitution is a part of the Bill of Rights. The purpose of this constitutional amendment was not only to protect individuals against unlawful search and seizure, but also to provide a system of checks and balances in the judicial system. The amendment states the following:
The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
In the landmark case of Weeks v. United States, 232 U.S. 383 (1914), the Supreme Court stated that a warrantless search of a private residence is a violation of a person’s Fourth Amendment rights. This case was responsible for the introduction of the exclusionary rule. The exclusionary rule states that evidence seized and examined without a warrant or in violation of an individual’s constitutional rights will often be inadmissible as evidence in court in a criminal case. An extension of the exclusionary rule is called fruit of the poisonous tree. Fruit of the poisonous tree is a metaphorical expression to describe evidence that was initially acquired illegally, meaning that all evidence subsequently gathered at every point from that initial search is inadmissible in court.
A number of years later, the U.S. Supreme Court heard the case of Olmstead v. United States, 277 U.S. 438 (1928). Roy Olmstead was found guilty of charges relating to violating the National Prohibition Act. He challenged his conviction based on the premise that his Fourth and Fifth Constitutional Amendment rights had been violated because federal agents had tapped his private telephone calls without a court-issued warrant. The court upheld Olmstead’s conviction. This decision was later overturned by the Supreme Court’s decision in the Katz v. United States case.
It is clear that the Fourth Amendment protects people, not places. The case of Katz v. United States, 389 U.S. 347 (1967), clearly illustrates this assertion. Charles Katz was accused of using a public payphone to conduct his illegal gambling business. Katz later found out that the FBI had placed a wiretap on the payphone. They then used Katz’s recorded conversations as evidence at trial. Katz was found guilty and sentenced. Katz challenged his conviction and argued that his Fourth Amendment right had been violated based on unreasonable search and seizure and because he believed there was an expectation of privacy. Katz was unsuccessful in the Court of Appeals, but the Supreme Court granted certiorari. Certiorari is an order made by a higher court that directs a lower court or tribunal to send it court documents, related to a case, for further review. The Supreme Court ruled in favor of Katz. The Supreme Court opined: “One who occupies [a telephone booth], shuts the door behind him, and pays the toll that permits him to place a call is surely entitled to assume that the words he utters into the mouthpiece will not be broadcast to the world.” Wiretapping constitutes a search and, therefore, requires a warrant. One of the issues that arises with the Fourth Amendment is the expectation of privacy. A link clearly exists between unreasonable search and seizure and the expectation of privacy, but the Supreme Court has not always been clear about the linkage. This causes confusion, and case law is the best guide for litigators.
An expectation of privacy in the workplace is still a grey area. In the case of O’Connor v. Ortega, 480 U.S. 709 (1987), the Supreme Court heard the case of Magno Ortega, a California State Hospital doctor who argued that a search of his office violated his Fourth Amendment rights. Ortega’s supervisors found alleged inculpatory evidence in his office during investigations into employees violating hospital policies. The case was subsequently remanded to the district court, and 11 years later, the Ninth Circuit found in favor of Ortega. With this decision, employer monitoring of employees is reduced when there is a failure to notify employees.
Search Warrants
The Fourth Amendment is arguably the most important part of the Constitution in terms of computer forensics investigations and probably all investigations. Law enforcement must obtain a warrant, issued by a judge or magistrate, before a search or arrest can be carried out. A search warrant is a court order issued by judge or magistrate authorizing law enforcement to search a person or place, as well as seize items or information within the parameters of the warrant. Furthermore, an investigator must demonstrate probable cause. Probable cause refers to the conditions under which law enforcement may obtain a warrant for a search or arrest, when it is evident that a crime has been committed. Law enforcement must show that a crime was committed and that it is more probable than not to expect that evidence exists at the place to be searched.
The case of United States v. Leon, 468 U.S. 897 (1984), created a “good faith” exception to the exclusionary rule. A judge issued a search warrant to the police in Burbank, California. Later, the search warrant was found to be invalid because the police did not properly demonstrate probable cause. Nevertheless, the police were deemed to be acting in good faith when seizing the evidence initially because they believed the warrant to be valid at the time.
In the case of United States v. Warshak, 562 F. Supp. 2d 986 (S.D. Ohio 2008), the Sixth Circuit of the U.S. Court of Appeals held that the government’s seizure of 27,000 private emails from Steven Warshak’s Internet service provider (ISP) violated his Fourth Amendment rights because the emails were acquired without a warrant. The ruling demonstrates that a federal court has recognized an expectation of privacy with emails stored on third-party servers. Nevertheless, the evidence was admissible in court because the government had relied, in good faith, on the Stored Communications Act (SCA).
Email is probably the most important type of digital evidence, and it is continually addressed in many cases. In the case of United States v. Ziegler, William Wayne Ziegler was accused of viewing child pornography on a computer at work. The employer decided to make copies of the suspect’s hard drive and delivered them to the FBI. Ziegler filed a motion to suppress the evidence because his Fourth Amendment rights had been violated. A motion in limine is a request by a lawyer to hold a hearing before a trial, in an effort to suppress evidence. That evidence could include expert witness testimony. If this motion is successful, the jury will never see the evidence. The Ninth Circuit Court of Appeals agreed that the employee did have an expectation of privacy. However, warrants apply to government agents, and the employer was not acting as an agent of the government or in response to a request from a government agent.
It is important to understand that a warrant is specific to a particular crime and criminal investigation and is very specific to a geographic location. For example, if a house borders two counties, then two separate warrants are necessary to search the entire property. This specificity cannot be overemphasized. In one case, law enforcement was issued a warrant to search a house. When investigators arrived at the house, they realized that the suspect’s computer was located in a shed at the back of the house. Therefore, investigators were not permitted to search the location of the computer and could not seize the computer.
The Fourth Amendment states the following:
The right of the people to be secure in their persons, houses, papers, and effects,[a] against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
The scope of a warrant is narrow, which means that even with probable cause, a government is limited to a specific place, person, and thing(s) to be searched. A Ninth U.S. Circuit Court of Appeal’s decision in 2008, and other decisions, have made this fact clear. Federal investigators successfully obtained a search warrant from the Central District Court of California to investigate the records of 10 Major League Baseball (MLB) players suspected of taking steroids kept at Bay Area Laboratories Company (BALCO). Federal investigators subsequently searched records of steroid use involving many more MLB players. Even though investigators tried to argue that the records of other players not noted in the initial warrant were in plain view, the majority of Ninth Circuit judges ruled that the investigators went too far. The court’s majority noted the following:
We accept the reality that such over-seizing is an inherent part of the electronic search process and proceed on the assumption that, when it comes to the seizure of electronic records, this will be far more common than in the days of paper records. This calls for greater vigilance on the part of judicial officers in striking the right balance between the government’s interest in law enforcement and the right of individuals to be free from unreasonable searches and seizures.
The ruling will naturally have implications for computer investigations going forward.
Warrantless Searches
Not all searches require a search warrant, however. With the passing of the USA PATRIOT Act, law enforcement has been provided with greater powers, which extends to warrantless searches when a person’s life or safety may be in danger. Exigent circumstances allow agents to conduct a warrantless search in an emergency situation when there is risk of harm to an individual or when there is risk of possible destruction of evidence. The case of United States v. McConney, 728 F.2d 1195, 1199 (9th Cir.), clearly details what is meant by exigent circumstances:
Those circumstances that would cause a reasonable person to believe that entry (or other relevant prompt action) was necessary to prevent physical harm to the officers or other persons, the destruction of relevant evidence, the escape of a suspect, or some other consequence improperly frustrating legitimate law enforcement efforts.
The U.S. Department of Justice (DOJ) provides guidelines for warrantless searches and seizures of computers at https://www.justice.gov/criminal-ccips/ccips-documents-and-reports.
When appropriate consent is granted to a government agent, a warrant is not required. Consent can be granted when an individual waives his or her Fourth Amendment rights. However, the search is limited to the physical area of the individual’s authority and is limited to a specific criminal investigation. A warrantless search is also subject to the totality of circumstances. This means that the individual granting consent must be of sound mind, must be an adult, and must be educated with a certain degree of intelligence.
Sometimes law enforcement uses a tactic known as a “knock and talk”. Knock and talk is when law enforcement does not have sufficient evidence or cannot demonstrate probable cause to enter a residence and execute a search. Instead, law enforcement personnel go to the suspect’s home and try to obtain the consent of the individual to gain entry to the home and conduct a consensual search. Sometimes this includes a non-custodial interview. This is an example of a warrantless search.
Plain view doctrine allows a government agent to seize evidence without a warrant when the officer can clearly observe contraband. To comply with this doctrine, an officer must be lawfully present in an area protected by the Fourth Amendment, the evidence must be in plain view, and the officer must immediately identify the item as contraband without further intrusion. These conditions of the plain view doctrine were affirmed in the case of Horton v. California.
Extending the scope of a warrant to include digital evidence in plain view can be extraordinarily difficult, however, as illustrated in the case of United States v. Carey (see United States v. Carey, No. 14-50222 (9th Cir. 2016)). Patrick Carey was under investigation for suspected possession and sale of cocaine. After a series of controlled drug purchases at his residence, police obtained an arrest warrant. Police asked Carey for consent to search his apartment. Concerned that his apartment might be trashed during a search, he signed a formal written consent. During the search, police seized drugs and two computers. Police subsequently obtained a warrant to search the computers for “names, telephone numbers, ledger receipts, addresses, and other documentary evidence pertaining to the sale and distribution of controlled substances”. Detective Lewis went through the computers’ files and noticed directories and files with sexually suggestive names. The detective opened an image file that was deemed to be child pornography. The detective continued with the search and downloaded 244 image files and viewed some more images of child pornography. Carey moved to suppress the images. The Tenth Circuit U.S. Court of Appeals agreed with the defendant because, after viewing one image, the detective would have had an expectation of more child pornography on the computer and, therefore, required a new warrant to investigate a different crime. The warrant the detective had obtained was for a drug investigation, not for possession of child pornography.
In this case, the detective might have successfully argued his case that evidence of a crime was in plain view if the images had been displayed in the normal course of the investigation. In this case, the detective had been performing keyword searches to find evidence supporting his investigation of illegal possession and distribution of narcotics. You obviously would not be running keyword searches on images. A search warrant never allows investigators to conduct a general search.
The case of UNITED STATES of America, Plaintiff-Appellee, v. Russell Lane WALSER, Defendant-Appellant. No. 01-8019 is similar in nature. In June 2000, the manager of a hotel went to a guest room to check on a smoke alarm. While in the room, he noticed what he believed to be illegal drugs. He called the police, who then secured the room and obtained a search warrant for the hotel room. The warrant gave permission for the following search:
Controlled substances, evidence of the possession of controlled substances, which may include, but not be limited to, cash or proceeds from the sales of controlled substances, items, substances, and other paraphernalia designed or used in the weighing, cutting, and packaging of controlled substances, firearms, records, and/or receipts, written or electronically stored, income tax records, checking and savings records, records that show or tend to show ownership or control of the premises and other property used to facilitate the distribution and delivery [of] controlled substances.
The police searched the room, found illegal drugs and drug paraphernalia, and seized a computer in the room. Back at the forensic laboratory, during a search of the computer by Agent McFarland, the investigator stumbled upon what he believed to be child pornography. Agent McFarland ended his search and informed an investigator more familiar with child endangerment cases. The computer was shut down immediately, and another warrant was obtained. The defendant-appellant requested that the Tenth Circuit U.S. Court of Appeals approve his motion to suppress the evidence garnered from the two searches of his computer, arguing that they lacked probable cause to do so. The court examined the case for plain error. Plain error arises when an appeals court identifies a major mistake made in court proceedings, even though no objection was made during the initial trial in which judgment was passed and a new trial was ordered. Under Rule 52(b), in the Rules of Criminal Procedure, a plain error that affects substantial rights may be considered even though it was not brought to the court’s attention. Rules of Criminal Procedure are protocols for how criminal proceedings in a federal court should be conducted. The defendant argued that the investigator who opened the .avi file, a video file, exceeded the scope of the warrant. He argued that a video file could not possibly have contained evidence relating to an investigation of drug possession, so the investigator should not have opened the file under the conditions outlined in the warrant. Based on the fact that the agent showed restraint in continuing his search, the court opined that the search was lawful and that the evidence was admissible.
This decision was in contrast to the Tenth Circuit Court’s decision earlier, in the case of United States v. Carey, when a police search of the suspect’s computer was deemed to be overly broad. We can therefore conclude that warrants must be specific to a particular criminal investigation and if, in the normal course of an investigation, the investigator inadvertently finds contraband unrelated to the initial investigation, the investigator should immediately cease the search for new contraband and obtain a new search warrant.
Interestingly, in the case of United States v. Mann (No. 08-3041), the Seventh Circuit Court upheld an earlier conviction in the case of a lifeguard instructor named Matthew Mann. He was investigated after video cameras were found in a locker room where women were changing clothes. Police obtained a warrant to search for computers and storage media. During the investigation, police found child pornography on the suspect’s hard drive, and Mann was subsequently charged. Mann filed a motion to suppress this evidence, but the Seventh Circuit Court opined that the search was not overbroad, even though the images of children were specially flagged by investigators, who knew that they were now working on a different investigation. Nevertheless, given previous decisions, it does seem wise for law enforcement to err on the side of caution and obtain a warrant before continuing a search related to a different crime.
The case of People v. Diaz is an interesting case that deals with a warrantless search of a suspect’s cellphone. The Supreme Court of California upheld the Court of Appeals decision that a warrantless search of text messages is lawful after an arrest. Diaz was arrested after selling drugs to a police informant. Upon arrest, the suspect’s cellphone was seized, placed into evidence, and searched. The defense moved to suppress the cellphone evidence, but the court sided with law enforcement, citing that it was incident to arrest. A subsequent ruling, with Riley v. California, which was a landmark Supreme Court decision in 2014, held that a warrantless search of a cellphone, incident to arrest, is illegal. Search incident to a lawful arrest allows law enforcement to conduct a warrantless search after an arrest has been made. The search is limited to the individual and her surrounding area and may include a search of the suspect’s vehicle (see Arizona v. Gant, 2009).
Law enforcement may also be able to acquire evidence without a warrant via a third-party. For example, a service provider might offer evidence for a suspect, or text messages or email could be acquired from a victim. In these situations, the suspect has no standing. Standing refers to a suspect’s right to object to a Fourth Amendment search, as outlined by the Supreme Court.
When Does Digital Surveillance Become a Search?
Two recent court cases bring into question the rights of an individual and the expectations of government agents during an investigation. In all but one of the following cases, the convicted criminals were involved in some appalling criminal activities.
In the case of U.S. v. Daniel David Rigmaiden, 844 F.Supp.2d 982 (2012), the suspect was charged with financial fraud. Between January 2005 and April 2008, Rigmaiden allegedly acquired $4 million from fraudulently filing 1,900 tax returns. The case was tried in the U.S. District Court of Arizona. Law enforcement located the suspect using a “Stingray” device. Stingray is the generic name given to a device that acts like a cellphone tower to locate criminal suspects but can also be used to locate people in disaster areas, such as earthquakes. In the case of Rigmaiden, federal agents were able to locate him based on a Verizon broadband card, which operates on a cellphone network.
The defense argued that federal agents required a search warrant to use the device. In addition, they argued that they had a right to view the Stingray used to capture the suspect. The prosecution contended that the use of a pen register requires only a court order, not a warrant. A court order is issued by a court and details a set of steps to be carried out by law enforcement; it is easier to obtain than a warrant because probable cause need not be demonstrated. A pen register is an electronic device that captures telephone numbers. Pen register orders require law enforcement to show only that information retrieved is likely to assist in an ongoing investigation. Rules governing the use of a pen register can be found in 18 U.S.C., Chapter 206. A pen register is not a search, as opined by the Supreme Court in Smith v. Maryland, 442 U.S. 735 (1979). The defense counsel argued that the Stingray cannot be classified as a pen register device because the device also records the location of people. The defense counsel also argued the legality of the prosecution using the device, expunging the device of evidence, and not allowing the defense to view the device. The prosecution did not want to show the device because it is a “secret device” and the evidence was regularly scrubbed from the device because the device would also record the information of innocent cellphone users. The Department of Justice later admitted that it conducted a search but still contended that, when using a cellphone (or a broadband card), there is no expectation of privacy. The prosecution also stated that a court order did allow investigators to capture real-time data from Verizon. Nevertheless, the suspect was found in his apartment. A search warrant for the apartment was later obtained.
GPS Tracking
The use of GPS tracking devices is prevalent and widespread, but only recently has the legality of these devices come to the fore. Yasir Afifi, a 20-year-old Arab-American student, was the son of an Islamic-American community leader. Afifi was surfing the Internet when he noticed a piece about GPS tracking devices. On a whim, he checked his car and noticed a wire sticking out. Afifi found the device on the undercarriage of his car and had it removed. The device, known as the Orion Guardian ST820, is manufactured by Cobham PLC.
FBI agents showed up at the student’s house and demanded the expensive, secretive device back. Afifi complied with their demand. Interestingly, the Ninth Circuit Court opined that attaching the device was not illegal and did not require a warrant, even if the device was attached to the car while in a person’s driveway. Afifi’s driveway was not enclosed and did not pass the Dunn test for Curtilage. Curtilage refers to the property surrounding a house. In the case of U.S. v. Dunn, 480 U.S. 294 (1987), Drug Enforcement Agency (DEA) agents used electronic tracking devices in an electric hot plate stirrer, a drum of acetic anhydride, and a phenylacetic acid container. Agents noticed from aerial photographs that the suspect backed his truck up to a barn on his ranch. The entire ranch perimeter was enclosed by a fence and barbed wire. Agents crossed a perimeter fence and an interior fence, looked through the window of a barn, and spotted a methamphetamine laboratory in the barn with the use of a flashlight. They subsequently entered the barn to confirm the existence of the laboratory. They then obtained and executed a search warrant. The Fifth Circuit Court of Appeals reversed the Dunn conviction because agents had entered the ranch without a warrant, and the barn was within the protected curtilage. The U.S. Supreme Court reversed the decision and opined that the barn was not within curtilage because it was not used for intimate activities. They stated that the agents in “open fields” were no different than being in a public place.
In a similar case, U.S. v. Knotts 460 U.S. 276 (1983), Minnesota police placed a radio transmitter (beeper) inside a chloroform container. The suspect, Armstrong, was suspected of using chloroform to manufacture illicit drugs. The Federal District Court denied the defendant’s motion to suppress the evidence obtained from the beeper. Later the Court of Appeals reversed the decision of the Federal District Court. The case was subsequently heard by the Supreme Court, which reversed the Court of Appeals decision and upheld the original conviction. In the majority opinion:
Monitoring the beeper signals did not invade any legitimate expectation of privacy on respondent’s part, and thus there was neither a “search” nor a “seizure” within the contemplation of the Fourth Amendment. The beeper surveillance amounted principally to following an automobile on public streets and highways. A person traveling in an automobile on public thoroughfares has no reasonable expectation of privacy in his movements.
The use of GPS tracking devices has come up numerous times in case law. In U.S. v. McIver, law enforcement attached a tracking device to McIver’s car while it was parked in front of his garage. McIver was suspected of growing marijuana. The court deemed the car to be outside the curtilage of his home and was therefore not deemed a search. They also noted that “[t]he undercarriage is part of the car’s exterior, and as such, is not afforded a reasonable expectation of privacy.” The case of U.S. v. Pineda-Moreno was very similar, and the case was heard by the Ninth Circuit Court of Appeals. The DEA noticed the suspect purchasing large quantities of fertilizer from a Home Depot and suspected that he was using it for growing marijuana. On seven different occasions, a GPS tracking device was attached to the suspect’s Jeep, once when the car was parked in the owner’s driveway. Agents pulled the suspect’s car over, smelled the odor of marijuana, and asked the suspect for permission to search the vehicle. The suspect allowed the agents to search the car, and they found two large trash bags filled with marijuana. The suspect was then indicted by a grand jury. Defense counsel filed a motion to suppress the evidence on the basis of a Fourth Amendment violation and entered a conditional plea of guilty with the District Court. The Ninth Circuit ruled that the car was within the curtilage of the home, which “is only a semiprivate area” (see United States v. Magana, 512 F.2d 1169, 1171 [9th Cir. 1975]). The court also noted that the “undercarriage of a vehicle, as part of its exterior, is not entitled to a reasonable expectation of privacy.”
In the case of United States v. Jones, the D.C. Circuit Court was asked to hear the case of Antoine Jones, concerning a GPS tracking device that was used. Jones was suspected of distributing narcotics. Agents secured a Title III wiretap, which allows for electronic surveillance. A D.C. federal judge issued a warrant to covertly install a GPS tracking device on Jones’s Jeep Cherokee within 10 days of the warrant issue date. However, agents did not install the device until the 11th day. Agents later seized 97 kilograms of cocaine and $850,000 from the suspect’s home. The U.S. District Court (D.C.) found Jones guilty of conspiring to sell cocaine and he was sentenced to life in prison. However, a Court of Appeals later reversed the decision. The D.C. Circuit Court noted that the Knotts decision did not apply because Jones was under constant surveillance. The court opined:
The Court explicitly distinguished between the limited information discovered by use of the beeper—movements during a discrete journey—and more comprehensive or sustained monitoring of the sort at issue in this case.…Most important for the present case, the Court specifically reserved the question whether a warrant would be required in a case involving twenty-four hour surveillance, stating, “if such dragnet-type law enforcement practices as respondent envisions should eventually occur, there will be time enough then to determine whether different constitutional principles may be applicable.”
The case was then referred to the U.S. Supreme Court, and because the warrant had expired when the device was attached, the question became whether a warrant was necessary. During oral arguments, it was clear that this case is different from other cases involving the warrantless use of tracking devices. Justice Sonia Sotomayor stated the following:
What motivated the Fourth Amendment historically was the disapproval, the outrage, that our Founding Fathers experienced with general warrants that permitted police indiscriminately to investigate just on the basis of suspicion, not probable cause, and to invade every possession that the individual had in search of a crime.
Justice Samuel Alito took quite a different view of the use of tracking devices, in a digital age when so much of our personal information is freely available on social networking websites:
“With computers around, it’s now so simple to amass an enormous amount of information. How do we deal with this? Just say nothing has changed?”
Justice Elena Kagan noted that times have changed and that many cities have numerous speed and surveillance cameras.
The use of GPS surveillance devices has clearly become a contentious issue, and there is a distinct lack of clarity in case law. Under Knotts, law enforcement may be able to install GPS tracking devices even if the installation occurs on a driveway, generally deemed by the courts to be outside of the privacy of one’s home, in a semi-private area and not protected under the Fourth Amendment.
In January 2012, the Supreme Court unanimously decided that government agents violated Jones’s Fourth Amendment rights. However, the justices’ reasoning for doing so was split 5–4. The majority ruled that the search was illegal because they deemed that the agents had trespassed. Justice Alito, a conservative, and three other justices went as far as to say that Jones’s expectation of privacy was violated, although Justice Scalia and four others did not agree.
The U.S. v. Jones Supreme Court decision has had repercussions for the GPS surveillance of criminal suspects. GPS tracking constitutes a search and seizure. Justice Scalia noted the following in the decision:
We decide whether the attachment of a Global Positioning-System (GPS) tracking device to an individual’s vehicle, and subsequent use of that device to monitor the vehicle’s movements on public streets, constitutes a search or seizure within the meaning of the Fourth Amendment.
An interesting part of this case are the opinions of the Supreme Court justices, who appeared to be voicing the opinions of divided public opinion and considering whether it is right to sacrifice our expectation of privacy in a digital age.
GPS Tracking (State Law)
A number of states prohibit the use of GPS tracking devices without a warrant. In the case of Oregon v. Meredith, a transmitter was attached to a United States Forest Service (USFS) truck. The suspect was caught setting a fire and was charged with arson. In this case, the lower court agreed with the defense’s motion to suppress evidence derived from the transmitter. The Supreme Court of Oregon disagreed because the defendant did not have an expectation of privacy when using the vehicle in public. Moreover, the defendant was using the employer’s vehicle. The use of the monitor did not constitute a “search” under Article 1, Section 9, of the Oregon Constitution.
There was a slightly different opinion, however, in the case of Washington v. Jackson, 150 Wash.2d 251, 76 P.3d 217 (Wash. 2003). Under Article 1, Section 7, of the Washington Constitution, GPS tracking is unlawful without a warrant. GPS tracking is viewed as an intrusion into someone’s life. The court ruled that law enforcement did have a warrant to use GPS tracking and that it was the only reasonable way to track the two vehicles needed to track the suspect.
The New York Constitution prohibits the use of GPS tracking devices without a warrant. In the case of New York v. Weaver, a police officer attached a GPS device to a suspect’s van bumper in connection with a series of burglaries. The defendant and code-fendant were arrested and charged with burglary in the third degree and grand larceny in the second degree. The New York Court of Appeals opined:
Technological advances have produced many valuable tools for law enforcement and, as the years go by, the technology available to aid in the detection of criminal conduct will only become more and more sophisticated. Without judicial oversight, the use of these powerful devices presents a significant and, to our minds, unacceptable risk of abuse. Under our State Constitution, in the absence of exigent circumstances, the installation and use of a GPS device to monitor an individual’s whereabouts requires a warrant supported by probable cause.
The State of Ohio has upheld the warrantless use of GPS tracking devices. In Ohio v. Johnson, agents attached a tracking device to the undercarriage of a suspected drug dealer’s van. Police later stopped Johnson’s van, and the suspect admitted that he was on his way to sell cocaine. The court opined,
“Johnson did not produce any evidence that demonstrated his intention to guard the undercarriage of his van from inspection or manipulation by others.…Supreme Court precedent has established not only that a vehicle’s exterior lacks a reasonable expectation of privacy, but also that one’s travel on public roads does not implicate Fourth Amendment protection against searches and seizures.”
Traffic Stops
The acquisition of digital evidence during a traffic stop can appear somewhat confusing when perusing case law. Surprisingly, Michigan State Police occasionally performed warrantless searches of drivers’ cellphones during traffic stops, using the Cellebrite UFED, which has the ability to capture evidence from thousands of different cellphone models. You might expect that these types of searches required a warrant, but certain types of warrantless searches can be conducted incident to arrest.
In the case of California v. Nottoli, policed stopped the suspect, Reid Nottoli, after speeding on a highway in his silver Acura TL. Santa Cruz County Deputy Sheriff Steven Ryan suspected that Nottoli was driving under the influence of a drug but was not driving while impaired. Nottoli’s license was also expired. Ryan informed the driver that his car would be impounded. Nottoli was placed in handcuffs and then put in the patrol car. Ryan decided to take an inventory of the vehicle’s contents before having it towed. During the search of the vehicle, he found a Glock 20 handgun with a Guncrafter Industries conversion, which meant that it should have been secured in the trunk of the car. Deputy Gonzales, who had later arrived on the scene, noticed a BlackBerry Curve cellphone in a cup holder. He pressed a button on the BlackBerry to see if it was functional and noticed a wallpaper image of a man wearing a mask holding two AR-15 assault rifles in akimbo fashion. The officer suspected that the individual in the picture was Nottoli. These rifles had been legal in California before the weapons ban, but Ryan confiscated the cellphone as evidence of possible “gun-related” criminal activity. The officer viewed pictures, emails, and text messages for approximately 10 minutes, according to court documents.
Only after this initial search did Ryan secure a search warrant for the cellphone and a second search warrant for Nottoli’s residence. SWAT personnel were sent into the home based on suspected drug-related information retrieved from the cellphone. Law enforcement seized $15,000 and a large cache of weapons and discovered a marijuana-growing operation. Nottoli filed a motion to suppress the evidence based on a violation of the Fourth Amendment, a warrantless search of the cellphone. At the initial trial, the magistrate agreed that the officers did not have a right to search the cellphone without a warrant:
I think there was an expectation of privacy that the defendant had for his BlackBerry, that there were not sufficient grounds to authorize the deputy to open that BlackBerry up and, therefore, anything that was discovered as a result of that activity would be suppressed.…
In South Dakota v. Opperman (1976) 428 U.S. 364 [96 S.Ct. 3092], the Supreme Court held that “a routine inventory search of an automobile lawfully impounded by police for violations of municipal parking ordinances”, consistent with “standard police procedures”, was reasonable under the Fourth Amendment to the U.S. Constitution.
The Court of Appeals of the State of California ruled that the deputies were justified in searching the vehicle’s passenger compartment and, ‘any containers therein’, based upon the Supreme Court decision on Arizona v. Gant. The court continued, with Justice Franklin D. Elia writing for the three judge panel:
In sum, it is our conclusion that, after Reid [Nottoli] was arrested for being under the influence, it was reasonable to believe that evidence relevant to that offense might be found in his vehicle. Consequently, the deputies had unqualified authority under Gant to search the passenger compartment of the vehicle and any container found therein, including Reid’s cell phone. It is up to the US Supreme Court to impose any greater limits on officers’ authority to search incident to arrest.
Many lawmakers were incensed by this decision. The California State Senate and Assembly then passed a bill requiring that a warrant be required before carrying out a search of a cellphone. Surprisingly, California Gov. Jerry Brown then vetoed the bill. Brown wrote in his message to the Senate, “I am returning Senate Bill 914 without my signature” and stated that the “courts are better suited to resolve the complex and case-specific issues relating to constitutional search-and-seizures protections.”
The case of New York v. Perez (2011 NY Slip Op 07659), had a different outcome. The defendant was found guilty in Suffolk County Court, New York, of criminal possession of a controlled substance in the first degree, false personation, operating a motor vehicle while using a mobile telephone (under Vehicle and Traffic Law § 1225-c(2)(a)), operating a motor vehicle without using a safety belt (under Vehicle and Traffic Law § 1229-c(3)), and failing to stay in a designated lane (under Vehicle and Traffic Law § 1128(a)). Police stopped the defendant and impounded the vehicle. While the vehicle was impounded, an officer searched the vehicle and leafed through a notebook. The notebook indicated the possible presence of narcotics in the vehicle. Police returned with a canine to help locate the suspected drugs. Police then pried open a compartment and found bundles of secreted cash. The New York State Supreme Court overturned the lower court’s decision and found that the defendant’s Fourth Amendment rights had been violated with an illegal search. With the car impounded, there was “ample time for the law enforcement officials to secure a warrant in order to make this significant intrusion” (People v Spinelli, 35 NY2d 77, 81). The defendant’s statements were suppressed after the illegal search as fruit of the poisonous tree.
In the case of Riley v. California, 573 U.S. 373 (2014), the U.S. Supreme Court ruled in 2014 that police require a warrant to search the cellphone of someone who is arrested. This was a landmark decision for law enforcement and forensics investigators because a cellphone can no longer be searched incident to arrest.
Carpenter v. United States
In the case of Carpenter v. United States in 2018, a 5–4 Supreme Court decision, authored by Chief Justice Roberts, stated that when the government obtains historical cellphone records that contain cell site location information (CSLI), without a warrant, then they are violating the Fourth Amendment.
The case stemmed from armed robberies at a RadioShack and a T-Mobile store in Michigan. The four thieves were caught and arrested. The FBI obtained call logs from one of the robbers, which ultimately included call logs from Timothy Carpenter, the Petitioner in this case, who was not one of the robbers. Historical cell-site location information (CLSI) data tracked Carpenter for 127 days—an average of 101 data points per day. In the Supreme Court opinion for this case, Roberts cited the previous court decision in United States v. Jones, 565 U. S. 400, whereby concerns were raised with GPS tracking. Again, the data derived from cell-sites could be used to track Carpenter’s location over a 127-day period. The opinion stated:
Tracking a person’s past movements through CSLI partakes of many of the qualities of GPS monitoring considered in Jones. In fact, historical cell-site records present even greater privacy concerns than the GPS monitoring considered in Jones: They give the Government near perfect surveillance and allow it to travel back in time to retrace a person’s whereabouts, subject only to the five-year retention policies of most wireless carriers.
Furthermore, the opinion (18 U. S. C.§2703(d)) noted:
that the “Government did not obtain a warrant supported by probable cause before acquiring Carpenter’s cell-site records. It acquired those records pursuant to a court order under the Stored Communications Act, which required the Government to show “reasonable grounds” for believing that the records were “relevant and material to an ongoing investigation.” 18 U. S. C. § 2703(d). That showing falls well short of the probable cause required for a warrant. Consequently, an order issued under § 2703(d) is not a permissible mechanism for accessing historical cell-site records.
Carpenter’s case was heard once again by the Sixth Circuit and he was sentenced to 116 years in prison, even with the Supreme Court ruling about the government requiring a warrant for location data, associated with cell site records. The court ruled that the FBI acted lawfully in collecting this data and therefore was not subject to the exclusionary rule.
Fifth Amendment
The Fifth Amendment is also a part of the Bill of Rights. This amendment protects the individual from self-incrimination. A defendant is not compelled to testify at trial and may “plead the Fifth”. However, an indictment is a charge delivered by a grand jury stating that the accused must stand trial. A grand jury is a relatively large jury that determines whether conditions exist for criminal prosecution in a case. The wording of this amendment states that a defendant in a criminal investigation cannot be tried more than once for the same crime. Therefore, a computer forensics investigator must be sure to have gathered all the necessary evidence before the case goes to trial. This is no easy feat, considering that corroborating evidence can be gathered from a suspect’s computer and cellphone, the victim’s computer and cellphone, web servers, email servers, CCTV, and a multitude of other sources.
The text of the Fifth Amendment is as follows:
No person shall be held to answer for a capital, or otherwise infamous crime, unless on a presentment or indictment of a Grand Jury, except in cases arising in the land or naval forces, or in the Militia, when in actual service in time of War or public danger; nor shall any person be subject for the same offense to be twice put in jeopardy of life or limb; nor shall be compelled in any criminal case to be a witness against himself, nor be deprived of life, liberty, or property, without due process of law; nor shall private property be taken for public use, without just compensation.
In the case of Miranda v. Arizona, the Supreme Court ruled that an incriminating statement by a suspect is inadmissible in court if the suspect was not advised of the Fifth Amendment right to remain silent and not give self-incriminating evidence. In addition to this, a person who is detained by a government agent has the right to counsel, as outlined in the Sixth Amendment. The Supreme Court opined that Ernesto Arturo Miranda’s Constitutional rights had been violated when arrested for rape and kidnapping. Generally, the following Miranda Rights are read to a suspect upon arrest:
You have the right to remain silent. Anything you say or do can and will be held against you in a court of law. You have the right to speak to an attorney. If you cannot afford an attorney, one will be appointed for you. Do you understand these rights as they have been read to you?
The Fifth Amendment can influence the outcome of computer forensics investigations, but the connection is rarely discussed. In the federal criminal case of In re Boucher, No. 2:06-mj-91, 2009 WL 424718, a suspect was stopped at the border, crossing from Canada into Vermont, and his laptop was searched. Agents found what they believed to be sexually explicit images of children on the computer, arrested the suspect, and charged him with the transportation of child pornography. Investigators imaged the hard drive but later realized that files on the hard drive were encrypted and password protected. The government issued a subpoena directing the defendant to assist with decrypting the files. A subpoena is an order by a court demanding a person to testify or to bring evidence to court. The defendant sought to quash the subpoena, arguing that it would violate his Fifth Amendment by being self-incriminating. The court agreed with the defendant and quashed the subpoena. This is because forcing a defendant to supply a password is forcing the defendant to provide testimony because the defendant is conveying his knowledge (a known password) to access files with incriminating evidence. This scenario is similar with a PIN on a cellphone, whereby a suspect cannot be forced to provide the PIN to access his device. Conversely, a suspect can be forced to use his finger to unlock a laptop or smartphone. Biometric access is not protected by the Constitution.
Sixth Amendment
The Sixth Amendment states the following:
In all criminal prosecutions, the accused shall enjoy the right to a speedy and public trial, by an impartial jury of the State and district wherein the crime shall have been committed, which district shall have been previously ascertained by law, and to be informed of the nature and cause of the accusation; to be confronted with the witnesses against him; to have compulsory process for obtaining witnesses in his favor, and to have the Assistance of Counsel for his defense.
The Sixth Amendment does not impact the work of computer forensics investigators in law enforcement very frequently, but it is important to acknowledge. In the case of Melendez-Diaz v. Massachusetts, the U.S. Supreme Court reversed the Massachusetts Appeals Court judgment, ruling that certificates of forensic findings should not have been admitted in court and violated the defendant’s Sixth Amendment right to confront witnesses against him. The Confrontation Clause is a Sixth Amendment clause that states: “in all criminal prosecutions, the accused shall enjoy the right…to be confronted with the witnesses against him.” Although this case did not involve digital evidence, there are obviously implications for computer forensics investigators, who previously submitted notarized testimony but are now being forced to appear in person.
Congressional Legislation
As previously mentioned, the role of Congress is to write laws, while the federal courts interpret congressional legislation and pass judgment over those who violate those laws. Changes in technology have brought about changes in legislation.
Federal Wiretap Act (18 U.S.C. § 2511)
The following is the preamble to the Federal Wiretap Act of 1968, which is often referred to as Title III:
Section 2511 of Title 18 prohibits the unauthorized interception, disclosure, and use of wire, oral, or electronic communications. The prohibitions are absolute, subject only to the specific exemptions in Title III. Consequently, unless an interception is specifically authorized, it is impermissible and, assuming existence of the requisite criminal intent, in violation of 18 U.S.C. § 2511.
The law is clear in detailing how law enforcement is prohibited from using a wiretap without permission from a judge. In fact, law enforcement can be penalized for any unauthorized use of a wiretap. A wiretap is authorized by the Justice Department, signed off by a U.S. District Court or Court of Appeals judge, and is valid for up to 30 days. Under 18 U.S.C. § 2511(2)(a)(i), service carriers may, on occasion, monitor and intercept communications to “combat fraud and theft of service”.
The Federal Wiretap Act has been amended several times to account for changes in technology. The Electronic Communications Privacy Act of 1986 (ECPA) was developed to extend the restrictions placed on law enforcement by the Federal Wiretap Act. Basically, the ECPA extended the Wiretap Act to include electronic data transmitted by a computer from merely including telephone intercepts. As part of the ECPA, Congress included the Stored Communications Act (SCA). When an individual uses an ISP or an electronic mail service provider, there are no protections under the Fourth Amendment. The Stored Communications Act was introduced to protect the rights of the individual and maintain their expectation of privacy.
“Stored communications” is defined at 18 U.S.C. § 2510(17):
(A) any temporary, intermediate storage of a wire or electronic communication incidental to the electronic transmission thereof; and
(B) any storage of such communication by an electronic communication service for purposes of backup protection of such communication.
The issue of applying SCA is somewhat problematic, however, considering that law enforcement operating in one jurisdiction is granted a search warrant but an ISP or electronic mail service provider may be headquartered in another jurisdiction, while the actual email server may be located in yet another jurisdiction. When Google introduced Gmail in 2004, it provided a tremendous amount of memory to its users and changed Internet email services forever. People now save thousands of emails for years, which is a tremendous benefit to law enforcement.
Recently, in the case of City of Ontario v. Quon, 560 U.S. (2010), two police officers were disciplined when their pager text messages were examined, and sexually explicit texts were found. Jeff Quon, a police sergeant from Ontario, California, and other officers sued the city, their superiors, and the service provider in federal court and argued that their Fourth Amendment rights and federal communications privacy laws had been violated. The Supreme Court ruled that the search was reasonable, thereby reversing the Ninth Circuit’s decision that a less intrusive search was warranted. This ruling means that there should be a diminished expectation of privacy, with electronic communications, in the workplace.
A similar case can be seen in Bohach v. City of Reno, where police officers faced an internal affairs investigation based upon stored pager messages. The officers in question tried to stop the investigation based on their rights under ECPA. The court disagreed that the search was illegal and stated that there could be no expectation of privacy because many people had access to the system where the messages were stored. Furthermore, there was no notion of an “intercept” of communications in this investigation.
In the case of Smyth v. The Pillsbury Company, Michael Smyth’s employment with the Pillsbury Company was terminated for inappropriate comments about management that he sent in an email. Smyth filed suit against the company for unfair dismissal because the company clearly stated in its policy that emails were confidential and would not be intercepted—and, furthermore, that emails could not be used as grounds for termination. Interestingly, the court found in favor of Pillsbury. Judge Charles R. Weiner granted Pillsbury’s motion to dismiss after examining common law exceptions to Pennsylvania’s denial of a cause of action for the termination of an at-will employee.
Foreign Intelligence Surveillance Act (FISA-1978)
The Foreign Intelligence Surveillance Act is a congressional act that was introduced during President Carter’s administration. The act outlines procedures by which electronic surveillance may be carried out to protect the United States against international espionage by foreign governments. The act was subsequently amended by the USA PATRIOT Act in 2001, which extended the scope to include terrorism, which may not be state-sponsored.
Certain portions of the act stand out when considering computer forensics investigations. One example is the use of pen registers and also trap-and-trace devices in foreign intelligence investigations (Title 50 U.S.C., Chapter 36, Subchapter III, § 1842).
The Protect America Act of 2007 amended FISA to allow for warrantless surveillance of foreign targets of intelligence gathering. This act was later repealed with the FISA Amendments Act of 2008 (Title VII of FISA).
Computer Fraud and Abuse Act (18 U.S.C. § 2511)
The Computer Fraud and Abuse Act is a part of Title 18 of the United States Code, which was passed by Congress in 1986. The early 1980s saw the growth of the personal computer, and with that growth came the emergence of the computer hacker. High-profile hackers targeted both corporate networks and government agency networks. The Computer Fraud and Abuse Act was introduced to invoke stiffer penalties for those found guilty of unauthorized access to a network. Section 814 of the USA PATRIOT Act made several amendments to the Computer Fraud and Abuse Act, including an increase in the maximum penalty for hackers, who damage protected computers, from 10 years to 20 years in prison. Moreover, the act changed to include intent to damage a computer rather than simply a type of damage. The USA PATRIOT Act also included a new offense for damaging computers used for national security or criminal justice. Some major provisions of the act are outlined shortly.
In the case of Andrew “weev” Auernheimer, the hacker was found guilty of violating the Computer Fraud and Abuse Act when he released hundreds of thousands of iPad email addresses. The Third Circuit Court of Appeals overturned his conviction after federal prosecutors wrongly filed the case against him in New Jersey, noting that none of the crimes had been perpetrated in that state.
Corporate Espionage (18 U.S.C. § 1030(a)(1))
Title 18 U.S.C. § 1030(a)(1) states:
having knowingly accessed a computer without authorization or exceeding authorized access, and by means of such conduct having obtained information that has been determined by the United States Government pursuant to an Executive order or statute to require protection against unauthorized disclosure for reasons of national defense or foreign relations, or any restricted data, as defined in paragraph y. of section 11 of the Atomic Energy Act of 1954, with reason to believe that such information so obtained could be used to the injury of the United States, or to the advantage of any foreign nation willfully communicates, delivers, transmits, or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it.…
Other provisions of the Computer Fraud and Abuse Act are important:
Computer Trespassing (18 U.S.C. § 1030(a)(2))
Committing Fraud with a Protected Computer (18 U.S.C. § 1030(a)(3))
Distributing Passwords of a Government/Commercial Computer (18 U.S.C. § 1030(a)(6))
Damage to a Protected Computer (18 U.S.C. § 1030(a)(7))
Communications Assistance for Law Enforcement Act (CALEA) (47 U.S.C. § 1002)
Advancements in telecommunications have often made it more difficult for law enforcement to carry out effective electronic surveillance of a criminal suspect. The Communications Assistance for Law Enforcement Act (CALEA) was introduced to facilitate law enforcement in their surveillance activities of telecom companies. In essence, telecommunications companies were forced to redesign much of their infrastructure to become compliant with CALEA and provide improved electronic surveillance for law enforcement. In other words, there is a legal obligation for telecommunication service providers to assist law enforcement with their investigations. Cisco has actually published a Lawful Intercept Configuration Guide, which outlines the schematics for communications interceptions by law enforcement agencies under CALEA. You can review the Cisco guide online (www.cisco.com).
What is important to note is that VoIP operators, like Vonage or Magic Jack, are not subject to CALEA and, therefore, might not be able to assist law enforcement with investigations, like a traditional telecom company, such as Verizon, can. Moreover, serious technological challenges are associated with using a Title III wiretap with VoIP because of the absence of switches on a VoIP network.
USA PATRIOT Act
The USA PATRIOT Act was introduced in the wake of the September 11, 2001, atrocity, to provide greater powers to law enforcement in an effort to prevent terrorist attacks from happening again. The act has caused such a stir because law enforcement now has the power to conduct surveillance without judicial approval in certain circumstances. Some view this legislative change as a reduction in our Fourth Amendment rights and introduces the potential for more “big brother” warrantless surveillance.
The USA PATRIOT Act has impacted investigations involving digital forensics. For example, if law enforcement received an email from someone who had been kidnapped, then under the USA PATRIOT Act, law enforcement could act without the use of a warrant because someone’s life was in danger. Before 9/11/2001, a warrant was needed to conduct a search, even when a person’s life was in danger.
Section 202 of the USA PATRIOT Act provides law enforcement with the authority to intercept voice communications in computer hacking investigations. Previously, law enforcement could not apply for a wiretap order or wire intercept for violations of the Computer Fraud and Abuse Act.
Section 209 of the USA PATRIOT Act impacts law enforcement’s access to electronically stored voice messages, like voicemail. Since the Electronic Communications Privacy Act, changes have been made to the electronic storage of communications. For example, with the introduction of Multipurpose Internet Mail Extensions (MIME), a government agent with a search warrant could not tell whether an unopened email contained a voice recording. Section 209 now allows law enforcement to access stored voice recordings without a Title III wiretap. In summary, recorded voice messages are no longer protected by the Fourth Amendment but have a lower standard under ECPA.
Section 210 of the USA PATRIOT Act broadens the amount of personal information that a government agent has access to with the use of a subpoena. Subsection 2703(c)(2) includes “records of session times and durations”, as well as “any temporarily assigned network address”. Section 210 also enables agents to obtain credit card and bank information for Internet users, which was previously unavailable without a subpoena. This is important because a user who used a false identity, but a real credit card, can now be found without the use of a warrant.
Section 210 of the USA PATRIOT Act was introduced to compel Internet Service Providers (ISPs) to assist law enforcement when there is the potential for loss of life. Section 210 also enables ISPs to voluntarily report non-content records, like a user’s login records, to law enforcement to protect themselves. If a computer hacker were to hack into an email server, the service provider is now legally able to hand over complete details about the incident to law enforcement. There has, however, been some pushback by ISPs about providing this information.
Section 213 of the USA PATRIOT Act is often referred to as the “sneak and peek” warrant provision. This provision enables law enforcement to search a home or business hastily without notifying the target in advance. The section was added to prevent a criminal suspect from tipping off other criminals about an imminent search.
Section 216 amends the Pen Register and Trap and Trace Statute to extend the law from just to telephone records to now include non-content information related to the Internet. Thus, pen register and trap-and-trace searches now can include IP addresses, MAC addresses, port numbers, and user account or email addresses.
Section 217 allows an individual, whose protected computer has suffered unauthorized access by a hacker, to allow law enforcement to intercept the communications of the trespasser. The user also has the right to intercept these communications. However, the victim must meet four conditions prior to monitoring:
Owner or user of a protected computer must authorize the interception of communications (Section 2511(2)(i)(I));
The person who intercepts the communication must be lawfully engaged in the ongoing investigation (Section 2511(2)(i)(II));
Reasonable grounds to believe that the interception of a communication will assist in an ongoing investigation (Section 2511(2)(i)(III)); and
Investigators must only intercept the communications of the trespasser (Section 2511(2)(i)(IV)).
Section 220 compels ISPs to hand over email records that are outside the jurisdiction of an investigation. On occasion, judges would not provide permission for law enforcement to access email located in another jurisdiction.
Finally, Section 816 requires the Attorney General to create regional computer forensics laboratories and to continue supporting existing laboratories.
PROTECT Act
The PROTECT Act of 2003 (PROTECT stands for Prosecutorial Remedies and Other Tools to end the Exploitation of Children Today) was codified as 18 U.S.C. § 2252(B)(b). The act was introduced to provide greater protection for children against abuse. The law eliminates waiting periods for law enforcement to begin investigating missing persons between the ages of 18 and 21. Another provision of the act is the elimination of statutes of limitations for child abuse or kidnapping. The act also prohibits computer-generated child pornography, although the First Amendment constitutionality of this provision has been questioned in case law.
Digital Millennium Copyright Act (DMCA) (17 U.S.C. § 1201)
The Digital Millennium Copyright Act (DMCA) was signed into law in 1998 by President Bill Clinton. DCMA is divided into four titles:
Title I: The “WIPO Copyright and Performances and Phonograms Treaties Implementation Act of 1998” implements the WIPO treaties.
Title II: The “Online Copyright Infringement Liability Limitation Act” creates limitations on the liability of online service providers for copyright infringement when engaging in certain types of activities.
Title III: The “Computer Maintenance Competition Assurance Act” creates an exemption for making a copy of a computer program by activating a computer for purposes of maintenance or repair.
Title IV: Contains six miscellaneous provisions, relating to the functions of the Copyright Office, distance education, the exceptions in the Copyright Act for libraries and for making ephemeral recordings, “webcasting” of sound recordings on the Internet, and the applicability of collective bargaining agreement obligations in the case of transfers of rights in motion pictures.
A copy of DCMA is available at www.copyright.gov/legislation/dmca.pdf.
The act is important because many people have been involved in litigation in civil cases that involve copyright infringement. These cases often involve subpoenas issued to online service providers and expert witness testimony from computer forensics investigators.
In the case of Sony Computer Entertainment America v. George Hotz, Sony filed a lawsuit against George Hotz, who was accused of violating the DCMA. Hotz provided users with a jailbreak for Sony PlayStation 3’s firmware that enabled users to play games on the PlayStation console that were unauthorized by Sony. Hotz posted the jailbreak solution on his blog and in a YouTube video; Hotz also had followers on Twitter. DCMA prohibits any device that circumvents intellectual property, and this was the focus of the violation from Sony’s perspective. Sony also believed that Hotz and others who used the firmware jailbreak had violated its terms of service.
Two issues stand out in this case. The first is that Sony managed to convince a magistrate to give the company permission to obtain the IP addresses and names of those who had visited Hotz’s blog, viewed the YouTube video, and followed him on Twitter. The Electronic Frontier Foundation (EFF) supported Hotz financially during the case and noted in a letter to the magistrate that allowing Sony to obtain the names of Hotz’s followers on the Internet was unlawful. Moreover, the foundation argued that this action would mean naming individuals who were not a part of the lawsuit and could not be present to object, in court, to their names being revealed.
It should be noted that there are some exemptions to being prosecuted under DMCA. For example, an entity seeking to find security flaws in a legitimate manner is exempt from prosecution.
The Supreme Court decision in the case of McIntyre v. Ohio Elections Comm’n, 514 U.S. 334, 357 (1995), clearly protects the right to anonymity:
Anonymity is a shield from the tyranny of the majority [that] exemplifies the purpose [of the First Amendment]: “to protect unpopular individuals from retaliation…at the hand of an intolerant society.”
The case of Sony Music Entertainment v. Does, 326 F.Supp.2d 556, 565 (S.D.N.Y. 2004), is more specific about protecting an individual’s right to speak anonymously on the Internet. Several other cases protect the identity of online service subscribers under the First Amendment. Some have even cited the Federalist Papers, authored by Alexander Hamilton, James Madison, and John Jay, promoting the U.S. Constitution. This series of 85 articles was published under the pseudonym of Publius. Therefore, our Founding Fathers believed that the Constitution should protect the right of anonymous speech and reading.
The second interesting fact about the case involving Sony v. Hotz is that the hacktivist group Anonymous hacked into Sony’s PlayStation network and compromised 24.6 million user accounts, along with credit card and bank information for many of those users. This was retribution for Sony’s lawsuit against Hotz. In the group’s eyes, Sony was challenging Hotz’s First Amendment right to free speech.
Ultimately, Sony and Hotz reached an out-of-court settlement, but serious questions were raised about the ability of Sony to obtain IP addresses and names of Internet users who were not part of the lawsuit.
CLOUD (Clarifying Lawful Overseas Use of Data) Act
Enacted in 2018, this federal legislation obliges USA-based technology corporations to allow federal law enforcement to obtain data stored on servers domestically and internationally, with a subpoena or a warrant. This act has largely been in response to pushback by companies, including Microsoft, with servers in countries, like Ireland, which believed that servers located outside of the USA fall under the jurisdiction of other nations. This act has been viewed by some as being controversial since data stored on a server in an EU country should comply with both sovereign law (country law) and EU legislation, which is the case for other types of evidence. Conversely, it is important for law enforcement to have access to critical evidence on foreign servers, where the suspect or victim is based in the USA.
At time of writing, this law needs to also be ratified reciprocally by other countries—more specifically, in the European Union.
Rules for Evidence Admissibility
The admissibility of digital evidence will continue to be challenged. The primary issue is that the traditional science of forensics has been applied to computers and technology. In theory, evidence is gathered from a crime scene or suspect and remains unchanged when admitted to court. When a blood sample has been gathered and has undergone DNA analysis, there is still blood that remains unchanged in its chemical composition. In digital forensics, systems are often in a state of flux. For example, if a system is running, then the contents of RAM are particularly important in potentially finding a suspect’s password, websites visited, processes running, and so forth. Nevertheless, while gathering the contents of RAM, the computer’s memory is continually changing. The same is true when a cellular telephone has been seized. Typically, the cellphone will be powered on and system changes will occur while in custody. These continual changes make the evidence easier to challenge in court. Additionally, with rapid changes in technology, new decisions are being made in court cases. No longer do we simply rely on files retrieved from a hard disk drive, but we also need to consider evidence from social networking websites, mobile devices, and cloud computing. With the diversification of digital evidence, finding experts with strengths in numerous areas of this discipline becomes problematic.
Ultimately, when dealing with the issue of admissibility in court, we rely on case law, especially as it relates to acceptable scientific practice, and what are known as Federal Rules of Evidence. Of course, the manner by which the evidence was seized, handled, and documented in accordance with the law is critical to its acceptance by a judge.
Frye Test for Evidence Admissibility
The case of Frye v. United States dealt with the admissibility of evidence in a case in which James Alphonzo Frye was tried for second-degree murder. The focus of evidence credibility was a systolic blood pressure test that was a precursor to the polygraph test. This blood pressure test was not widely accepted by scientists, so it was ruled inadmissible. The case is a landmark case because the decision has subsequently influenced the admissibility of scientific evidence, particularly in reference to expert witness testimony. In 1923, the D.C. Court of Appeals opined:
Just when a scientific principal or discovery crosses the line between the experimental and demonstrable stages is difficult to define. Somewhere in this twilight zone the evidential force of the principle must be recognized, and while courts will go a long way in admitting expert testimony deduced from a well-recognized scientific principle or discovery, the thing from which the deduction is made must be sufficiently established to have gained general acceptance in the particular field in which it belongs. (emphasis added).
In summary, the decision states that expert opinion must be derived from a thing and must be based on science that is demonstrable and not experimental.
Daubert Test for Evidence Admissibility
In some jurisdictions, the Frye test (or standard) has been supplanted by the Daubert test. In the case of Daubert v. Merrell Dow Pharmaceuticals in 1993, the parents of Jason Daubert and Eric Schuller sued Merrell Dow Pharmaceuticals over birth defects suffered by their children after the use of the drug Bendectin. Both parties used expert witness testimony, but the plaintiffs referenced the impact of the drug testing on animal—testing that was not yet generally accepted in the scientific community. Under the Frye standard, this evidence would be inadmissible. The U.S. District Court found in favor, and the Ninth Circuit agreed when appealed by Daubert and Schuller. The plaintiffs submitted a request for review by the Supreme Court, which they agreed to do. The plaintiffs argued that after Congress passed the Federal Rules of Evidence (FRE) in 1975, the Frye standard no longer applied. The Supreme Court agreed and opined that the Frye standard no longer applies.
The case of Kumho Tire Co. v. Carmichael extended the importance of the Federal Rules of Evidence over the Frye standard by giving equal weight to the testimony of a technician with that of a scientist. Rule 702 of FRE applies to “scientific, technical, or other specialized knowledge”.
Ultimately, the impact of Frye and Daubert on investigations involving digital evidence is that computer forensics investigators must perform benchmark testing on their hardware and software tools. This testing will enable the investigator to explain known error rates.
Federal Rules of Evidence
The Federal Rules of Evidence (FRE) are a set of rules that determine the admissibility of evidence in both civil and criminal cases in federal court. Nevertheless, many states have adopted similar guidelines for evidence admissibility. These rules became law when Congress enacted FRE under the Act to Establish Rules of Evidence for Certain Courts and Proceedings.
Several FRE directly impact the admissibility of digital evidence and expert testimony. As noted earlier, Rule 702 deals with expert testimony:
If scientific, technical, or other specialized knowledge will assist the trier of fact to understand the evidence or to determine a fact in issue, a witness qualified as an expert by knowledge, skill, experience, training, or education, may testify thereto in the form of an opinion or otherwise, if (1) the testimony is based upon sufficient facts or data, (2) the testimony is the product of reliable principles and methods, and (3) the witness has applied the principles and methods reliably to the facts of the case.
However, the rule noted above does not outline how to determine what “knowledge” is. When determining knowledge, we need to qualify the expertise of an expert witness.
Expert Witnesses
In general, testimony that is not firsthand is referred to as hearsay and is therefore inadmissible in court. An exception exists, however, for digital evidence under the Federal Rules of Evidence. Therefore, an expert witness can provide her opinion in court, and that opinion can be used as evidence. Expert testimony can be provided during a trial or in a deposition. A deposition is pretrial testimony given under oath, with both defense and prosecution attorneys present.
Both the defense and the prosecution can use their own expert witness and have the right to cross-examine the opponent’s expert. An expert witness might also be appointed by the court. The goals of the defense are to discredit the expert, the testimony, the evidence, the tools, and the scientific methodology used, to ultimately gain concessions.
Under FRE 702, 703, and 704, all parties in a trial must disclose the witnesses that they will use at trial, which includes expert witnesses. The role of the expert witness is to educate the jury. Unlike a lay witness, an expert witness can express opinion according to FRE 704. An expert can speculate on a theory based on a theory rooted in facts. Opinion will guide the questions posed by the counsel the expert is representing. An expert may bring his own exhibits to the trial.
When seeking guidelines on the use of an expert witness at trial, we not only observe FRE guidelines, but we must also note the Federal Rules of Civil Procedure. The Federal Rules of Civil Procedure (FRCP) apply to civil cases in federal district courts, and these rules are promulgated by the U.S. Supreme Court. Many state courts also have adopted these rules. Under Rule 26(2) of FRCP, an expert witness who will be used at trial generally needs to provide a written report. Disclosure of an expert witness is an important part of discovery. Discovery is a pre-trial phase in which both parties in a civil lawsuit must share evidence when requested, by means of interrogations, depositions, documents, and subpoenas from parties not part of the lawsuit. Under Rule 26(2)(B), the expert witness’s written report must contain the following:
A complete statement of all opinions the witness will express and the basis and reasons for them;
The facts or data considered by the witness in forming them;
Any exhibits that will be used to summarize or support them;
The witness’s qualifications, including a list of all publications authored in the previous 10 years;
A list of all other cases in which, during the previous 4 years, the witness testified as an expert at trial or by deposition; and
A statement of the compensation to be paid for the study and testimony in the case.
As part of the pretrial disclosures, under Rule 26(3)(A), a party must provide the other party with the following information:
The name and, if not previously provided, the address and telephone number of each witness—separately identifying those the party expects to present and those it may call if the need arises;
The designation of those witnesses whose testimony the party expects to present by deposition and, if not taken stenographically, a transcript of the pertinent parts of the deposition; and
An identification of each document or other exhibit, including summaries of other evidence—separately identifying those items the party expects to offer and those it may offer if the need arises.
Of course, as with any evidence (or witness testimony), there can be objections to the testimony of an expert witness both at pretrial and during the trial.
Federal Rules of Evidence (FRE) and Hearsay
Another important rule that impacts digital evidence is FRE, Rule 803(6), which states the following:
Records of regularly conducted activity. A memorandum, report, record, or data compilation, in any form, of acts, events, conditions, opinions, or diagnoses, made at or near the time by, or from information transmitted by, a person with knowledge, if kept in the course of a regularly conducted business activity, and if it was the regular practice of that business activity to make the memorandum, report, record or data compilation, all as shown by the testimony of the custodian or other qualified witness, or by certification that complies with Rule 902(11), Rule 902(12), or a statute permitting certification, unless the source of information or the method or circumstances of preparation indicate lack of trustworthiness. The term “business” as used in this paragraph includes business, institution, association, profession, occupation, and calling of every kind, whether or not conducted for profit.
We can determine from this rule that emails, spreadsheets, systems logs, and so forth are records created in the normal course of business and are therefore admissible in federal court.
According to the Federal Rules of Evidence, hearsay is a statement other than one made by the declarant while testifying at the trial or hearing offered in evidence to prove the truth of the matter asserted. Digital evidence can be categorized as hearsay, but this is not always the case. In State v. Armstead, digital evidence is not hearsay when it is “the by-product of a machine operation which uses for its input ‘statements’ entered into the machine” and was “was generated solely by the electrical and mechanical operations of the computer and telephone equipment.” Therefore, under Rule 803(6) of FRE, digital evidence that is conducted in the “regular practice of that business activity” is not hearsay. Nevertheless, there is a distinction between digital evidence of a conversation in an email versus digital evidence in the form of a system log that simply notes when an individual logged onto a computer. In other words, the hearsay rule is applied differently to content created by a person versus content created by a machine. Evidence on a computer can however be created by both the human and the computer. For example, the user may enter information into a Quicken application, but the application has a computational component built in.
Rule 901, Requirement of Authentication or Identification, states the following:
The requirement of authentication or identification as a condition precedent to admissibility is satisfied by evidence sufficient to support a finding that the matter in question is what its proponent claims.
In the case of United States v. Tank, the defendant appealed his conviction of conspiring to receive and distribute child pornography. The appeal focused on the admissibility of chat logs saved on a computer. Tank argued that the chat logs were incomplete and that the logs from a co-conspirator could have been altered before the government seized the computer. The court stated that the issue of the completeness of the chat logs was influenced by the weight of the evidence rather than its admissibility. Riva, the co-conspirator, explained how the logs were created and stated that the printouts were an accurate representation of the chat logs. Even though the screen name on the printouts displayed “Cessna” and not “Tank”, several co-conspirators stated that Tank used the name Cessna. The court accepted printouts of chat logs as authentic and admissible under Rule 903(a).
Best Evidence Rule
The best evidence rule states that secondary evidence, or a copy, is inadmissible in court when the original exists. Nevertheless, an exception is often made for digital evidence. When you think about it, all files physically stored on a hard disk drive are just variations in the magnetism of a metal disk. These magnetically charged areas are represented by 1s and 0s that make sense only when translated to text or some type of interpretation. Common sense shows that you cannot submit the original media and have the judge and jury look at metal platters. Therefore, printouts of information are necessary. Moreover, an investigator might need to change something or use an application to view the content of a file. As noted in Chapter 3, “Handling Computer Hardware”, in the case of State of Connecticut v. John Kaminski, police needed to modify the media to view the contents of a compact disc. Criminals will often try to tamper with evidence or hide files and therefore investigators are forced to modify files—and sometimes even storage media—to recover incriminating evidence. Additionally, a cellphone conversation travels through many different channels, and the communication changes formation as conversations become digital data packets. Therefore, evidence will change from its original form from sender to recipient.
Criminal Defense
On March 5, 1770, five colonists were dead—shot by British regulars in an event that was to go down in history as the Boston Massacre. Their deaths were the culmination of bitterness toward the tremendous burden of taxation imposed by the British. The soldiers were brought up on criminal charges, and given the overwhelming hatred cast upon these “murderers”, it was certainly not strange that the culprits of this great tragedy could not find a lawyer to defend them in court. One man reluctantly stepped forward, and to everyone’s surprise, six of the soldiers were acquitted and the two soldiers, who had fired directly at the protestors, were convicted on only manslaughter charges, even though they had initially been charged with murder. That man was John Adams, who went on to persuade many colonial leaders to support and sign the Declaration of Independence. Adams later served as the second President of the United States (1797–1801). He was famously quoted: “Facts are stubborn things; and whatever may be our wishes, our inclinations, or the dictates of our passion, they cannot alter the state of facts and evidence.”
It is important to note that we should respect the vital work of law enforcement and prosecutors in bringing criminals to justice. Nevertheless, we must acknowledge the vital role of defense attorneys in the judicial system. It must be remembered that, under the Sixth Amendment, all defendants must be given the right to defense counsel. At the end of the day, if expert investigators lawfully and scientifically acquired incriminating evidence and the findings are presented appropriately, the prosecution should be successful if the defendant is guilty.
A defense attorney is an advocate and representative for a defendant in a court case. Defense attorneys use a number of strategies to defend their clients. One important tactic is to find reasons why each evidence exhibit should not be admitted into trial. Another tactic is to question the way in which the evidence was acquired and handled. Moreover, the defense attorney will question the legality of the steps carried out by investigators during the investigation, procedural issues relating to the pretrial discovery, and also the prosecution’s actions during the trial itself.
As we can see from the earlier section on the Fourth Amendment, defense attorneys first focus on whether the investigators’ search and seizure of evidence was legal. For example, did law enforcement personnel need a warrant to conduct the search? If so, did they do so in accordance with the provisions of the warrant?
After the suspect is arrested, the defense attorney determines whether there was sufficient evidence to make the arrest and then ascertains whether the suspect was properly informed of his rights. In terms of rights, a suspect has the right to remain silent (Fifth Amendment) and the right to an attorney “for his defence” (Sixth Amendment). Pending the trial, bail can be granted (Eighth Amendment).
During the pretrial phase, the defense attorney has the right to examine the evidence being used by the prosecution in its case. Therefore, if a computer and USB drive of a suspect were seized, defense counsel has the right to obtain copies of the computer’s hard drive and a copy of files retrieved from the USB device. Defense counsel must also be afforded ample time to review these copies by one of its computer forensics experts.
During the trial, defense counsel will raise questions about how the evidence was acquired and whether it was obtained in a forensically sound manner. Under cross-examination, a defense attorney might question the credentials of the investigator, the methods used, and knowledge about the forensic tools used, as well as ask general questions about the investigation. The search warrant is not the only legal document that the defense will scrutinize; the defense will also examine the investigators’ notes and, more importantly, the chain of custody form. Any gaps of time or inconsistencies on this form will render the evidence inadmissible.
California Consumer Privacy Act (CCPA)
Signed into law in 2018, the CCPA came into effect in 2020. The law impacts for-profit businesses with exposure to the personal data of California (CA) residents. More specifically, the act impacts businesses with revenues in excess of $25 million, who handle records for 50,000 or more CA residents or businesses that derive at least 50% of revenue by selling personal information for CA residents. This act stipulates that a business must inform customers about what personal information is being collected and shared with third parties. The act also forces businesses to allow consumers to easily opt-out of the collection of personal information. Consumers under the age of 16 must not be opted-in by default. Furthermore, consent from a parent/guardian must be obtained by the business for consumers aged 13 and under.
California residents, under CCPA, will have the right to request the removal of personal information, prevent the sale of personal information, and have the right to access their personal information from businesses. Data theft or a security breach may result in a fine of $100 to $750 per CA resident or the actual cost of damages. There may also be an additional fine of $7,500 for each intentional violation or $2,500 for each unintentional violation.
CCPA and other similar privacy legislation is important for a forensics investigator to know so that she can understand required local/state/federal/regional notifications and determine what forensics data may be available and how it can be lawfully accessed.
NYS DFS Rule 23 NYCRR 500
The New York State (NYS) Department of Financial Services (DFS) Section 500 was announced in 2017, in an effort to ensure that the financial services industry create an effective cybersecurity plan to protect their networks and their customers. With fines of up to $250,000 or 1% of banking assets, banks and other financial institutions in the financial capital of the world have taken notice, and taken action, to ensure compliance. For a financial institution to comply, it needs to ensure that it has developed effective planning and policies that address the following domains:
Maintain a cybersecurity program
Cybersecurity policy
Role of the CISO
Pen testing & vulnerability assessment
Audit trail
Access privileges
Application security
Risk assessment
Qualified personnel & intelligence
Third party service provider
Multi-factor authentication
Limitations on data retention
Training & Monitoring
Encryption of non-public information
Incident response plan
Notices to superintendent
Canada Personal Information Protection and Electronic Documents Act (PIPEDA)
Introduced in April 2000, this act impacts private sector companies across Canada that collect, use, or disclose personal information. These federally regulated organizations include the following:
Airports, aircraft and airlines;
Banks and authorized foreign banks;
Inter-provincial or international transportation companies;
Telecommunications companies;
Offshore drilling operations; and
Radio and television broadcasters.
The act states that an organization must obtain an individual’s consent when they collect or share personal information. An individual also has the right to access that information and challenge its accuracy. PIPEDA also includes mandatory breach notifications.
Private sector privacy laws, which are substantially similar to PIPEDA, also exist in Quebec (An Act Respecting the Protection of Personal Information in the Private Sector), Alberta (Personal Information Protection Act) and British Columbia (Personal Information Protection Act).
When Computer Forensics Goes Wrong
Law enforcement generally gets it right when it comes to investigations involving digital evidence. There are, however, occasions when things do not go according to plan.
Pornography in the Classroom
Julie Amero was a 40-year-old substitute teacher at Kelly Middle School in Connecticut. On October 19, 2004, Amero was teaching a seventh-grade language class when her Internet browser inexplicably began displaying pornographic images. Instead of shutting down the computer, she immediately sought help from the school’s administration, which she later explained was protocol. A letter was sent to the pupils’ parents explaining that Amero would never teach in the school district again. Shortly afterward, Amero was arrested and charged with multiple felonies.
At the trial, a computer crimes investigator from Norwich Police Department, Det. Mark Lounsbury, testified that Amero had been intentionally viewing pornography on the Internet during her class. The detective stated that Amero would have had to click on links to display the pornographic images. In 2007, Norwich Superior Court found Amero guilty on four counts of risk of injury to a minor or impairing the morals of a child.
The conviction followed controversy as many experts, including 28 professors, disagreed with the detective’s findings. They believed that his assertions were flawed because he did not check the computer for malware, which could have enabled the pornographic pop-ups. It was later discovered that a DNS hijacking program, called NewDotNet, had been installed on the computer before the alleged crime.
On June 6, 2007, the conviction was thrown out in a New London court, and a new trial was granted. On November 21, 2008, Amero pled guilty to a charge of disorderly conduct and was fined $100. She also lost her ability to teach again, although this was a small price to pay, considering that the original charges in this case could have led to Amero facing up to 40 years in prison.
The moral of the story is that computer forensics experts need to be thorough and make no initial assumptions. An investigator should also never just rely on one forensics tool, where possible. Moreover, an investigator should exhaust all possibilities in a case and be open to getting advice from other experts.
Structure of the Legal System in the European Union (E.U.)
In this digital age, the use of digital evidence in investigations has grown exponentially. We have already discussed how the Internet necessitates more cross-border collaboration. This collaboration refers not just to interstate investigations, but also to international collaboration. The growth of cloud computing has exacerbated this phenomenon. It is important to also think about how U.S. corporations often maintain their servers, and the records of U.S. citizens, on servers located in other countries. These records then become subject to privacy and search and seizure laws in the country where the servers reside.
Increasingly, we read about INTERPOL’s involvement in international investigations, especially those involving crimes against children, human trafficking, financial fraud, and drug trafficking. In addition, we are hearing about the concept of cyberwarfare as the possible precursor to an actual war.
Origins of European Law
Apart from Ireland and the United Kingdom, the legal systems of most European countries are based on Roman law. Roman law consists of three books of law: (a) people, (b) property, and (c) acquiring property. The first category refers to issues such as marriage. Property issues relate to ownership, which, in Roman times, included slaves. Acquiring property included wills and laws of succession. Under Roman law, the plaintiff was required to call the defendant, or sometimes force the defendant, to come to court. The magistrate then decided whether the case should go before the Judex, a group of prominent laymen, who in Roman times heard arguments, questioned witnesses, and then rendered a decision. The concept of the summons originated in Roman times, as did the role of the court in enforcing court sentences.
Structure of European Union Law
The European Union (E.U.) consists of 27 countries, each with its own sovereign laws. These countries are as follows: Austria, Belgium, Bulgaria, Croatia, Cyprus, the Czech Republic, Denmark, Estonia, Finland, France, Germany, Greece, Hungary, Ireland, Italy, Latvia, Lithuania, Luxembourg, Malta, the Netherlands, Poland, Portugal, Romania, Slovakia, Slovenia, Spain, and Sweden.
The European Union is similar to the United States because it has a dual legal system in place: each country has (1) its own laws and (2) E.U. law. However, there some notable differences in the composition of both entities. The European Union is a treaty with member states. Any state can leave this union at any time without consequence, which is certainly not the case in the United States, as demonstrated when states in the South tried to secede from the Union in 1861.
E.U. Legislature
The E.U. legislature is comprised of the European Parliament and the Council of the European Union. These institutions have the power to write, amend, and repeal laws. The European Commission is similar to the Office of the President of the United States, in that it is the executive body of the E.U. However, the European Commission has the power to propose legislation and initiate legal proceedings against member states. The Court of Justice of the European Union interprets European law, related to its treaties, and is the highest court in the European Union. This court is the equivalent of the U.S. Supreme Court and is made up of the Court of Justice, the General Court, and a number of specialized courts.
Data Privacy
E.U. law clearly protects the rights of an individual in terms of personal data sharing more than the U.S. legal system does. In the United States, very few laws protect an individual’s personal information, especially at the federal level. The Health Insurance Portability and Accountability Act (HIPAA) gives control of personal healthcare data to the individual. The Gramm–Leach–Bliley Act is also concerned with privacy, in that financial institutions must provide consumers with a copy of their privacy policy and any amendments. Nevertheless, consumers have no right to prevent the financial institution from sharing their personal data. That is not the case in Europe, where the individual is afforded control over personal data. This presents tremendous challenges to computer forensics investigators and their access to digital evidence in the E.U.
A U.S. investigator traveling to the E.U. will notice some significant differences. For example, in some jurisdictions, employees need to be notified when an investigation of their computer will take place, which is not the case in the United States. Additionally, an investigator cannot acquire evidence from a computer in some European countries and simply bring it back to the United States for analysis. Online privacy is an individual right in the E.U., whereas this is not the case in the United States. For example, cookies have become standardized. As stipulated by the E.U., a user must choose to opt in to accept cookies on a website. Conversely, in the United States, the user generally is opted in by default. Therefore, the Internet evidence for a user differs in the E.U. from the United States. In May 2014, the European Union Court of Justice (ECJ) ruled that people on the Internet have the right to be forgotten, and therefore people can force Google to remove sensitive data about themselves. In fact, the user now has more control over searches performed, so Google and others have been gradually removing websites from searches performed by users. This may be good news for the users and their privacy, but online searches of suspects and subpoenas sent to Internet companies, like Google, will often yield fewer results for investigators, and the environment should prove even more problematic in the future. Directive 95/46/EC outlines the processing, handling, and sharing of personal data:
(2) Whereas data-processing systems are designed to serve man; whereas they must, whatever the nationality or residence of natural persons, respect their fundamental rights and freedoms, notably the right to privacy, and contribute to economic and social progress, trade expansion and the well-being of individuals
In January 2012, the European Commission voted to overhaul the 1995 Data Protection Directive, thereby enabling Internet users to have more control over their personal information. The provisions of the new law allow people to ask firms to delete their data and notify customers when their information has been compromised.
Directive 97/66/EC protects the processing of personal data and the protection of privacy in the telecommunications sector.
General Data Protection Regulation (GDPR)
Instituted in the EU on May 25, 2018, GDPR has had a profound impact on incident response and criminal investigations involving digital data. This regulation stipulates how companies, or entities, must handle the records of European Union citizens. Thus, a U.S. company that maintains personal information for EU citizens on its servers must comply. The law does not apply to small and mid-sized companies where personal data is not core to its business and personal data is not at risk.
The reason why this law has caused fear for so many companies is the fact that (i) a fine could be as high as €20 million or 4% of global annual turnover and (ii) the law limits the amount of data that a company can collect about a consumer. The latter has huge implications for companies, like Facebook and Google, which collect vast amounts of personal data about consumers, which goes beyond the initial transactional level. For example, under GDPR, a company can only collect personal data that is necessary to complete a transaction. Therefore, a shop selling shoes can only request an email address from a customer with their explicit consent and by explaining how they intend to use that information after the purchase has been made. Personal data may not be used for another purpose later and cannot be sold to a third party.
The focus of GDPR is protection of the individual and ensuring that the individual is in control of his or her own personal data rather than corporations. These rights include:
The right to be forgotten
The right to access their personal data
The right to amend incorrect personal data
The right to transfer data from one provider to another
A company must clearly state its privacy policy and data sharing agreements in full and not links i.e. providing web links to its policies are inappropriate. A consumer must be provided with details that include the name of the Data Protection Officer (DPO) of the company, reasons why their data is being collected, categories of personal data, legal justification, and data retention policy.
What Type of Data Can Be Collected under GDPR?
A company or entity must have a specific purpose for collecting personal data (“purpose limitation”). Furthermore, you must inform the E.U. citizen as to the purpose of the data collection. Only data necessary to complete a transaction can be collected (“data minimization”). A company must ensure that the personal data collected is correct (“accuracy”). Personal data can only be used for the original purpose and not used for any additional activities. A company cannot store data longer than necessary (“storage limitation”). The company must also ensure data security (“integrity and confidentiality”).
Personal Data versus Sensitive Data
GDPR makes a distinction between personal data and sensitive data. Personal data can include a consumer’s name, address, email address or IP address. Sensitive data can include race or ethnicity, political opinions, religious/philosophical beliefs, trade union membership, genetics/biometrics, health records and sexual orientation. This information becomes important in terms of how a data breach is reported. Under GDPR, a data breach must be reported within 72 hours to the Data Protection Authority (DPA). The DPA has the authority to issue warnings, reprimand, place a temporary ban on processing or a definitive ban on processing and issue a fine up to €20 million or 4% of global annual turnover. An individual may also claim compensation if his personal information has been compromised. More information about incident response and reporting requirements will be covered in Chapter 8, “Network Forensics and Incident Response”.
GDPR also makes a distinction between a data controller and a data processor, which makes a difference in terms of reporting after a data breach. A data processor is an entity that processes data for a data controller, based on specific guidelines provided by the controller. The controller essentially maintains the personal information. For example, Cisco is a data controller for its employees, while a third-party payroll company would be a data processor for Cisco’s employees. Hypothetically, if ADP was the payroll company for Cisco, then it would take direction from Cisco about how Cisco’s employee information should be handled or processed.
Impact of GDPR on Digital Forensics Investigations
One cannot underestimate the impact of GDPR on investigations. With limitations on data collection and retention, a criminal investigator may have more limited access to personal information from corporations. The biggest impact of GDPR is on incident response (IR). For example, if a U.S. company had an employee located in Spain whose laptop was stolen, it could be problematic to check if that laptop was compliant, i.e., was encrypted. Additionally, if that same company needed to image a computer in an E.U. country, then both GDPR and local legislation impact whether that investigation must take place in-country, whether the data can be transferred back to investigators in the USA, and permission may need to be sought from the employee to investigate a laptop owned by the company.
One major shift with IR, under GDPR, is that investigations have become attorney directed, i.e., the incident responder may have to seek advice from a cyber legal attorney, country legal, and the company’s data protection officer (also an attorney) during an investigation because of the potential reporting requirements. If a data breach has a reporting requirement, under GDPR, then the Data Protection Authority may ask the following questions:
What happened?
When did it happen?
What data was involved?
What data protections were in place?
How have you mitigated the threat?
How will you mitigate future threats?
With regards to the inadvertent disclosure, did the employee have access to the data in the normal course of business?
Was the data encrypted?
Was the device encrypted?
What type of device was the data stored on?
Has the client been informed?
When was the client informed?
Has the employee been referred for consequences?
What type of training do you provide your employees?
There are some challenges, however, associated with reporting a data breach. For example, it can be difficult for a company to pinpoint when a breach occurred. If there has been data exfiltration, and the hacker(s) encrypted the data, then the company may not be able to determine if personal data has been compromised or not.
Human Trafficking Legislation
The U.K. Modern Slavery Act is an extremely important piece of legislation. It is important because it confirms that slavery still exists in the Western World as well as in other regions of the globe. Men, women and children are being manipulated by criminals with the prospect of job opportunities in other countries and then forced into the sex industry (primarily women and children) or other forced labor, including agriculture, fishing and factories (primarily men). For example, women and children from high unemployment regions of Eastern Europe and Africa are being sold into slavery in Western countries, including Germany and France. Women and children from South American countries, like Honduras, are being enslaved in the USA – especially in lucrative cities like Las Vegas. Modern slavery is a multi-billion dollar industry. Of course, there are other countries, like India and North Korea, where slavery and human trafficking is a huge problem. Human trafficking has been rising significantly in recent years, and figures from the White House estimate that more than 25 million people are enslaved worldwide.
The criminals involved in modern slavery are investigated by agencies, including the National Crime Agency (NCA), Federal Bureau of Investigation, Homeland Security Investigations and Europol, to name but a few. One cannot underestimate the seriousness of this criminal activity and the time afforded by agencies worldwide to combat the abuse of women and children. Recently, the laws have changed in places, like New York State, where the focus of prosecution has moved to combat sex trafficking and support the victims. Some agencies have been progressive and changed laws to recognize the victims of the sex trade. Manhattan District Attorney is one organization that has recognized victims of trauma and expunged the records of many victims of the sex trade. Agencies, like Homeland Security Investigations, actively support the victims of human trafficking and raise charitable donations through the Homeland Security Philanthropy Council.
Investigatory Powers Act 2016
The Investigatory Powers Act, passed by both Houses of Parliament in 2016, details what digital data law enforcement and intelligence agencies, in the United Kingdom (U.K.), may access and what they cannot access. The goal of the Act is to improve national security (intelligence) and the capabilities of law enforcement (criminal investigations), by providing greater access to more electronic data. In particular, the act provides greater guidance about the lawful inception of communications data. The Investigatory Powers Commissioner’s Office (IPCO) oversees the use of investigatory powers by law enforcement, intelligence agencies and other public authorities. IPCO’s staff includes 15 Judicial Commissioners (current and retired judges) and a Technical Advisory Panel of scientific experts.
The location of the data is always key in terms of jurisdiction. In 2011, Facebook agreed to overhaul its privacy settings for more than half a billion users following a probe by the Irish Data Protection Commissioner (DPC). Facebook Ireland handles all of Facebook’s users who reside outside the United States and Canada. WhatsApp, which is owned by Facebook, maintains message servers in Ireland.
Intellectual Property
The recording industry has experienced tremendous challenges to the protection of intellectual property in the European Union. In a recent dispute between Scarlet Extended SA, an ISP owned by Belgacom, and Belgian management company SABAM (Case C-70/10), Europe’s highest court, the European Court of Justice, ruled that Internet access is a human right and that the music industry could not force ISPs to block access to users illegally sharing music and videos. In a similar decision, Eircom had been questioned by the Data Protection Commission about its “three strikes” policy against users illegally downloading copyrighted files. E.U. law prevents injunctions, decided by national courts, from being imposed when requiring the ISP to install filtering systems to prevent users from illegally downloading files.
Amendment 138/46 has been highly controversial. France and the U.K. had sought to scrap the amendment as part of the Telecoms Package, which states that the Internet is a basic human right. However, a compromise was found so that countries could impose their own laws on denying Internet service to copyright violators but allow the E.U. Parliament to review such cases.
E.U. Directives on Child Pornography
The European Union has been very tough on criminals who view, possess, and distribute child pornography. Recent directives now require member states to remove child pornography websites and enact national laws prohibiting child pornography. The European Parliament has fought for tougher penalties against these criminals and has outlined penalties for approximately 20 criminal offenses. For example, those producing this type of content will face a minimum of three years, while criminals viewing this content online will face at least one year in prison.
In summary, each member state of the European Union has its own laws concerning the use of digital evidence in cases. However, the E.U. allows individuals to appeal judgments, which is similar to the U.S. Supreme Court.
Europol
Europol is the European Union law enforcement agency. It investigates more than 12,000 cases annually, from human trafficking, to drug trafficking, to cybercrime, to currency counterfeiting. In March 2012, Europol announced the establishment of the European Cybercrime Centre (EC3) at The Hague, Belgium. The new center became operational in 2013 and is supported by a team of digital forensics investigators. The focus of the center is on investigating cybercrime and online child abuse cases. In May 2017, Europol officially became the European Union Agency for Law Enforcement Cooperation. This change means that Europol has more power when it comes to counter-terrorism and cybercrime investigations.
OLAF (European Anti-fraud Office)
In January 2014, OLAF released its standard operating procedures for digital forensics investigations conducted by its agencies. These guidelines outline good practices for the identification, acquisition, imaging, collection, analysis, and preservation of digital evidence. This guide is available at https://ec.europa.eu/anti-fraud/sites/antifraud/files/guidelines_en.pdf.
ACPO Guidelines
The Association of Chief Police Officers (ACPO) in the United Kingdom has created a set of guidelines for computer forensics investigations in a report called Good Practice Guide for Computer-Based Electronic Evidence. The document is important because many other European law enforcement agencies have based their standard operating procedures on these guidelines.
The guidelines lay out a number of important principles of good practice. Law enforcement should maintain the digital evidence in its original format. However, in certain circumstances, when the original evidence must be accessed, it must be accessed by an expert who can clearly explain the need for his activities and be able to detail the implications of his actions on the evidence. Furthermore, all steps performed by the investigator must be meticulously documented so that a third-party could follow the same documented steps to achieve the same results. Finally, the lead investigator is responsible for ensuring that accepted scientific methods of investigation and the law are adhered to at all times.
Privacy Legislation in Asia
Internet and privacy legislation is still being developed in Asia and varies greatly from country to country.
China
China has arguably the greatest restrictions on Internet content, and the government closely monitors content that its citizens view. Censorship has become so contentious that Internet users in mainland China cannot use Google’s search engine. Google moved its operations to Hong Kong in favor of reduced governmental scrutiny. Therefore, U.S. companies operating online services in China might have less information about Internet users. Conversely, India has less censorship but has instituted important privacy legislation.
India
In April 2011, India introduced new privacy legislation known as Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules 2011. The legislation was introduced to protect the privacy of online consumers, and it is important to know that this legislation impacts U.S. companies that outsource services to India. This legislation contains five primary tenets:
Privacy policy: All organizations must maintain a privacy policy of how they process and use personal data. This policy must be posted on their website. This information can be helpful for investigators who need to find out how much information may be available about a customer that they are investigating.
Consent: An individual needs to provide an organization with consent before their information is shared with a third party.
Consumer access and editing: An individual has the right to access personal information being collected about them and can dispute any erroneous data.
Transfer of personal data: Consent from the customer must be obtained before sensitive information is transferred to another party, and the organization must ensure that the recipient has similar standards for data privacy.
Security: An organization must maintain best practices in terms of security. However, the guidelines on what exemplifies best practices are not clearly outlined.
Summary
The original legal system in the United States was primarily state based, but the move toward independence solidified the federal legal system. The U.S. Constitution was created on September 17, 1787, and was subsequently ratified by each of the colonies. The first three articles of the Constitution establish the three branches of government: (1) the legislature (Congress), which writes laws; (2) the executive (president), which approves congressional laws; and (3) the judicial branch (the Supreme Court and lower federal court), which interprets and enforces the law.
Ten amendments were added to the U.S. Constitution, which later became known as the Bill of Rights. These amendments affect individual rights and can have a tremendous impact on investigations involving computer forensics. Of particular note is the Fourth Amendment, which protects an individual from illegal searches and requires that government agents demonstrate probable cause before obtaining a warrant to conduct a lawful search. Cases that require an interpretation of the U.S. Constitution are referred to federal court.
The U.S. legal system is based on common law, also known as case law, and English law. Case decisions create a precedent and are therefore binding on future decisions in that jurisdiction. The exception to this is Louisiana, whose legal system is based upon the Napoleonic Code, which has its roots in Roman law.
A state legal system, with its own courts, co-exists with the federal legal system. State courts can provide citizens greater protections than the federal system. For example, the Supreme Court has historically ruled in favor of warrantless usage of GPS tracking devices on vehicles, whereas some states have ruled that law enforcement requires a court-issued warrant. Evidence illegally attained without a warrant is subject to the exclusionary rule, which means that it is inadmissible in court, unless the court rules that law enforcement acted in good faith.
Many criminal suspects are investigated and charged under congressional law. In terms of electronic surveillance, the Federal Wiretap Act has been amended several times to incorporate changes in technology. The Electronic Communications Privacy Act (ECPA), which includes the Stored Communications Act (SCA), was introduced to protect the rights of the individual to unlawful searches, including email searches. The Foreign Intelligence Surveillance Act (FISA) was introduced to allow for surveillance of foreign entities and has been amended several times to include electronic surveillance. Some of those changes were instituted with the introduction of the USA PATRIOT Act, which broadens the warrantless electronic surveillance powers of law enforcement.
Congressional laws have been enacted to specifically deal with computer-related crimes. Of note is the Computer Fraud and Abuse Act, which includes a provision for corporate espionage.
In terms of evidence admissibility, digital evidence needs to pass the Daubert test. Evidence is also subject to the guidelines found in the Federal Rules of Evidence (FRE). Civil cases in federal court use the Federal Rules of Civil Procedure (FRCP), which are also often used by state courts, to determine evidence admissibility. Digital evidence is not helpful to a jury in its original format, so a representation of the data is appropriate, as outlined under the Best Evidence Rule.
Over the past few years, important privacy legislation has been introduced by New York State and California, which greatly impacts digital forensics investigations. Canada and many of its territories have also implemented important privacy legislation, with important reporting requirements when it comes to data breaches. The most significant privacy legislation to impact investigations is GDPR because it limits the amount of personal information and data retention, in addition to the potential for millions in fines for violating this regulation.
Investigations involving digital forensics are different in the European Union (E.U.) because of strict E.U. privacy laws. Generally, less personal information is captured and saved electronically, so employees typically must be informed before a search of their computers can be conducted at the workplace. The E.U. has enacted tough laws with stiff penalties for anyone found possessing or distributing child pornography or endangering the safety of a minor. The Association of Chief Police Officers (ACPO) was one of the first law enforcement agencies to establish guidelines for computer forensics investigations. Many other agencies across Europe have adopted the investigative principles.
Apart from Ireland and the United Kingdom, most countries in the European Union have a legal system that has origins in Roman (civil) law.
Key Terms
Best Evidence Rule: This rule states that secondary evidence, or a copy, is inadmissible in court when the original exists.
Bill of Rights: The first 10 amendments to the Constitution that protect the rights of the individual.
burden of proof: A legal principle that implies that a defendant is innocent until proven guilty. The prosecution must prove guilt, and the defense does not have to prove anything.
certiorari: An order made by a higher court that directs a lower court or tribunal to send it court documents related to a case, for further review.
civil law: Law that is based on scholarly research, which, in turn, becomes a legal code, which is subsequently enacted by a legislature.
codified laws: Statutes that are organized by subject matter.
common law: Law based on case law and precedent, where laws are derived from court decisions.
Confrontation Clause: A Sixth Amendment clause stating that “in all criminal prosecutions, the accused shall enjoy the right…to be confronted with the witnesses against him.”
constitutional law: Laws that outline the relationship among the legislative, judicial, and executive branches and also protect the rights of its citizens.
contempt of court: To violate the rules of court procedure.
Court of Justice of the European Union: Interprets European law and is the highest court in the European Union.
court order: Issued by a court and details a set of steps to be carried out by law enforcement. It is easier to obtain than a warrant because probable cause need not be demonstrated.
cross-examination: Questioning of the opposing side’s witness in a trial.
curtilage: Refers to the property surrounding a house.
defendant: The person who defends himself in a lawsuit.
defense attorney: An advocate and representative for a defendant in a court case.
deliberations: The process by which the jury reviews the evidence from the trial and discusses opinions about the case.
deposition: Pretrial testimony given under oath, with both defense and prosecution attorneys present.
direct examination: Questioning of counsel’s witness in a trial.
discovery: A pretrial phase in which both parties in a civil lawsuit share evidence when requested, by means of interrogations, depositions, documents, and subpoenas from parties not part of the lawsuit.
European Commission: The body that has the power to propose legislation and initiate legal proceedings against member states.
E.U. Legislature: A body comprised of the European Parliament and the Council of the European Union.
exclusionary rule: States that evidence seized and examined without a warrant or in violation of an individual’s constitutional rights will often be inadmissible as evidence in court in a criminal case.
exigent circumstances: A set of conditions that allow agents to conduct a warrantless search in an emergency situation when there is risk of harm to an individual or risk of the possible destruction of evidence.
family court: Hears cases relating to family matters, including child custody, visitation, and support cases, as well as restraining orders.
Federal Rules of Civil Procedure (FRCP): A set of rules that apply to civil cases in federal district courts. These rules are promulgated by the U.S. Supreme Court.
Federal Rules of Evidence (FRE): A set of rules that determine the admissibility of evidence in both civil and criminal cases in federal court.
felony: A serious crime that generally carries a penalty of a year or more in prison.
foreperson: Usually the first juror seated and the person ultimately responsible for reporting the verdict to the judge.
fruit of the poisonous tree: A metaphorical expression to describe evidence that was initially acquired illegally, meaning that all evidence subsequently gathered at every point from that initial search is inadmissible in court.
grand jury: A relatively large jury that determines whether the conditions exist for criminal prosecution in a case.
hearsay: A statement other than one made by the declarant while testifying at the trial or hearing, offered in evidence to prove the truth of the matter asserted.
hung jury: A jury that cannot come to a unanimous decision in a criminal trial, forcing a retrial.
indictment: A charge delivered by a grand jury stating that the accused must stand trial.
Judex: A group of prominent laymen who, in Roman times, heard arguments, questioned witnesses, and then subsequently rendered a decision.
judge: A person who facilitates the trial process and ensures that the proceedings are fair and in accordance with the law.
jurisdiction: Refers to the scope of legal authority granted to an entity.
jury: A group of people put under oath to hear arguments at trial and render a verdict of guilty or not guilty.
jury sequestration: Isolating the jury and preventing external influences on their decisions.
juvenile court: A court where minors are tried by a tribunal.
knock and talk: When law enforcement does not have sufficient evidence or cannot demonstrate probable cause to enter a residence and execute a search, so they go to the suspect’s home and try to get the consent of the individual to gain entry to the home and conduct a search.
misdemeanor: A less serious crime, with a possible conviction of less than a year.
motion in limine: A request by a lawyer to hold a hearing before a trial, in an effort to suppress evidence.
municipal court: Court that hears cases when a crime has occurred within its jurisdiction. Charges can include DUI, disorderly conduct, vandalism, trespassing, building code violations, and similar offenses.
pen register: An electronic device that captures telephone numbers.
plain error: When an appeals court identifies a major mistake that was made in court proceedings, even though no objection was made during the initial trial where judgment was passed. A new trial then is ordered.
plain view doctrine: Allows a government agent to seize evidence without a warrant when the officer can clearly observe contraband.
plaintiff: Person who initiates the lawsuit and is responsible for the cost of litigation.
precedent: Court decisions are binding on future decisions in a particular jurisdiction.
probable cause: The conditions under which law enforcement may obtain a warrant for a search or arrest, when it is evident that a crime has been committed.
probate court: Sometimes referred to as a surrogate court; this court hears cases relating to the distribution of a deceased’s assets.
regulatory law: Governs the activities of government administrative agencies.
Rules of Criminal Procedure: Protocols for how criminal proceedings in a federal court should be conducted.
search incident to a lawful arrest: Allows law enforcement to conduct a warrantless search after an arrest has been made.
search warrant: Court order issued by a judge or magistrate authorizing law enforcement to search a person or place, as well as seize items or information within the parameters of the warrant.
small claims court: Courts that settle private disputes involving relatively small monetary amounts.
standing: Refers to a suspect’s right to object to a Fourth Amendment search as outlined by the Supreme Court.
statutory law: Written law set forth by a legislature at the national, state, or local level.
Stingray: The generic name given to a device that acts like a cellphone tower to locate criminal suspects, but can also be used to locate people in disaster areas such as earthquake zones.
subpoena: A court order demanding a person to testify or to bring evidence to court.
traffic court: Court that hears cases relating to driving violations. An individual who is cited for a traffic violation can pay the fine (plead guilty) or can appeal in traffic court.
voir dire: The questioning process used in jury selection.
Assessment
Classroom Discussions
1. In this new digital age, can we assume that we have fewer protections under the Fourth Amendment?
2. What was the motivation for the Founding Fathers’ creation of the Bill of Rights?
3. How could an investigation involving digital evidence be different in the European Union than in the United States?
4. Under what circumstances can a case move from a state court to federal court?
5. Under what circumstances is a warrant not required by law enforcement to conduct a search?
6. Why is the USA PATRIOT Act so contentious with the American public?
7. What is GDPR and what is its impact on investigations involving digital data?
Multiple-Choice Questions
1. The person who initiates the lawsuit and is responsible for the cost of litigation is referred to as which of the following?
Counsel
Plaintiff
Defendant
Suspect
2. Which of the following courts hears cases relating to the distribution of a deceased individual’s assets?
Small claims court
Municipal court
Family court
Probate court
3. Which of the following amendments allows an individual to freely post opinions online, as long as those opinions do not incite violence?
First Amendment
Second Amendment
Third Amendment
Fourth Amendment
4. Which of the following amendments protects the individual from government agents performing an illegal search?
First Amendment
Fourth Amendment
Fifth Amendment
Sixth Amendment
5. Which of the following best describes a court order that requires an individual to testify or make evidence available?
Indictment
Warrant
Writ
Subpoena
6. Which of the following is a set of rules that determine the admissibility of evidence in both civil and criminal cases in federal court?
Federal Rules of Discovery
Federal Rules of Civil Procedure
Federal Rules of Evidence
Federal Rules of Hearsay
7. Which of the following states that secondary evidence, or a copy, is inadmissible in court when the original exists?
Exclusionary Rule
Federal Rules of Evidence
Hearsay Rule
Best Evidence Rule
8. Which of the following entities has the power to propose legislation and initiate legal proceedings against member states?
European Legislature
European Commission
Court of Justice of the European Union
European Parliament
9. What is the name of the court that interprets European law and is the highest court in the European Union?
Court of Justice of the European Union
E.U. Supreme Court
European State Court
Council of the European Union
10. Which of the following best describes pretrial testimony given under oath, with both defense and prosecution attorneys present?
Deposition
Discovery
Subpoena
Indictment
Fill in the Blanks
1. A group of people put under oath to hear arguments at trial and render a verdict of guilty or not guilty is referred to as a(n) __________.
2. The Bill of __________ refers to the first 10 amendments to the U.S. Constitution.
3. The __________ Amendment states that a defendant is not required to take the witness stand.
4. Fruit of the __________ is a metaphorical expression for evidence acquired from an illegal search.
5. __________ refers to the conditions under which law enforcement may obtain a warrant for a search or arrest when it is evident that a crime has been committed.
6. A statement other than one made by the declarant while testifying at the trial or hearing, offered in evidence to prove the truth of the matter asserted, is called __________.
7. The __________ test means that evidence does not necessarily need to have general acceptance by the scientific community but does need to meet the requirements of FRE 702.
8. __________ is the pretrial phase in which both parties in a civil lawsuit must share evidence when requested, by means of interrogations, depositions, documents, and subpoenas from parties not part of the lawsuit.
9. __________ is the name given to the property surrounding a house.
10. __________ is the generic name given to a device that acts like a cellphone tower to locate criminal suspects, but can also be used to locate people in disaster areas, such as earthquake zones.
Projects
Review Court Cases of Email Evidence
Find some court cases in which email was used as evidence at trial to help convict a suspect of criminal activity.
Write an Essay about the Use of Digital Evidence
Write an essay describing how the use of digital evidence in investigations has impacted criminal cases. Include in your answer case law.
Write an Essay Detailing the Impact of Changes in Legislation
Write an essay detailing how both congressional and state legislation have changed to deal with changes in technology and the way criminal activity has changed.
Create a Chart Comparing U.S. Investigations to E.U. Investigations
Create a chart or matrix comparing how conducting an investigation is different in the U.S. from the E.U. Be as specific as possible—for example—“Cookies” would be one category.
