Many people forge right into the application development process with little worry about the scalability of the application. Even a simple application that begins as a single-user application can develop into a multiuser application. It can even be used throughout the enterprise. Unfortunately, the techniques you can get away with in the single-user application can wreak havoc in a network or client/server environment. It is therefore necessary to think about the future when you design any application. Although the initial development process might be more complex, if written properly, the application will survive any growth that it experiences. This chapter focuses on writing applications that transition easily from the single-user environment through the enterprise client/server environment.
When you develop applications that will be accessed over the network by multiple users, you must make sure they effectively handle sharing data and other application objects. Many options are available for developers when they design multiuser applications, and this chapter covers the pros and cons of these options.
Multiuser issues revolve around locking data; they include deciding where to store database objects, when to lock data, and how much data to lock. In a multiuser environment, having several users simultaneously trying to modify the same data can cause conflicts. As a developer, you need to handle these conflicts. Otherwise, your users will experience unexplainable errors.
There are many methods for handling concurrent access to data and other application objects by multiple users; each one offers both solutions and limitations. It’s important to select the best solution for your particular environment.
There are two strategies for installing Access:
Run Access from a file server across a network
Run a separate copy of Access on each workstation
The advantages of running Access from a file server are that it
Note
The Access software takes up a significant amount of disk space. Although using the Access runtime engine can reduce disk space requirements, local hard-disk space can definitely be a problem. Installing Access on the file server at least partially eliminates this problem. It can totally eliminate the problem if dynamic link libraries (DLLs) are also installed on the file server.
File server installations also have serious drawbacks, including the following:
Every time the user launches an Access application, the Access EXE, DLLs, and any other files required to run Access are all sent over the network wire to the local machine. Obviously, this generates a significant volume of network traffic.
Performance is generally degraded to unacceptable levels.
Because the disadvantages of running Access from a file server are so pronounced, I strongly recommend that Access, or at least the runtime engine, be installed on each user’s machine.
Just as there are different strategies for installing Access, there are also various strategies for installing your application, such as the following:
Install both the application and data on a file server
Install the data on the file server and the application on each workstation
Install the application and the data on a machine running Windows 2000 Terminal Services
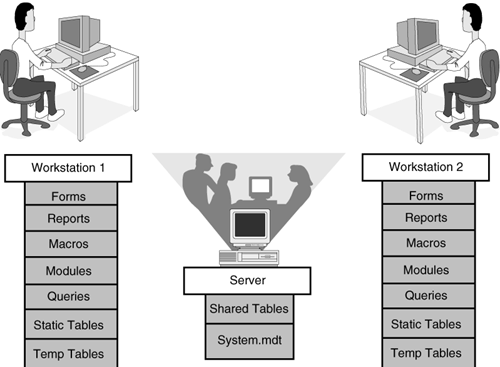
In other words, after you have created an application, you can place the entire application on the network, which means that all the tables, queries, forms, reports, macros, and modules that make up the system reside on the file server. Although this method of shared access keeps everything in the same place, you will see many advantages to placing only the database’s data tables on the file server. The remaining objects are placed in a database on each user’s machine, and each local application database is linked to the tables on the network. In this way, users share data but not the rest of the application objects.
The advantages of doing this are as follows:
Because each user has a copy of the local database objects, load time and network traffic are both reduced.
It’s very easy to back up data without having to back up the rest of the application objects.
When redistributing new versions of the application, you don’t need to worry about overwriting the application’s data.
Multiple applications can all be designed to use the same centrally located data.
Users can add their own objects (such as their own queries) to their local copies of the database.
In addition to storing the queries, forms, reports, macros, and modules that make up the application in a local database, I also recommend that you store the following objects in each local database:
Temporary tables
Static tables
Semistatic tables
Temporary tables should be stored in the database that’s on each workstation because, if two users are performing operations that build the same temporary tables, you don’t want one user’s process to interfere with the other user’s process. The potential conflict of one user’s temporary tables overwriting the other’s can be eliminated by storing all temporary tables in each user’s local copy of the database.
You should also place static lookup tables, such as state tables, on each workstation. Because the data doesn’t change, maintenance isn’t an issue. The benefit is that Access doesn’t need to pull that data over the network each time it’s needed.
Semistatic tables—tables that are rarely updated—can also be placed on the local machine. As with static tables, having these tables in a local database means reduced network traffic and better performance, not only for the user needing the data, but also for anyone sharing the same network wire. Changes made to the semistatic tables can be transported to each workstation by using replication (covered briefly in this chapter and in significant detail in Alison Balter’s Mastering Access 2002 Enterprise Development).
The configuration described throughout this section is illustrated in Figure 20.1.
The final option has recently emerged as a viable alternative for deployment of an Access application. It addresses both bandwidth and centralization issues. With this option, a Windows 2000 machine runs the Windows 2000 Terminal Services. Client machines then access the server machine using the Terminal Server Client Utility. In this scenario, Access, your application, and the data that it accesses, are all installed on the Windows 2000 Server machine. All other machines access the application via user sessions created on the server machine. Keystrokes and mouse events are sent from the client machines to the server machine. The resulting screen image is returned to the client machine. This configuration addresses many of the problems inherent in the two other solutions.
Linking to external data, including data not stored in another Access database, is covered extensively in Chapter 19, “Using External Data.” Three options are available to you:
Design the databases separately from the start.
Include all objects in one database; then split them manually when you’re ready to distribute your application.
Include all objects in one database; then split them by using the Database Splitter Wizard.
The first two options are covered in Chapter 19. The last option, the Database Splitter Wizard, is covered here. To split the objects in a database into two separate .MDB files, follow these steps:
Open the database whose objects you want to split.
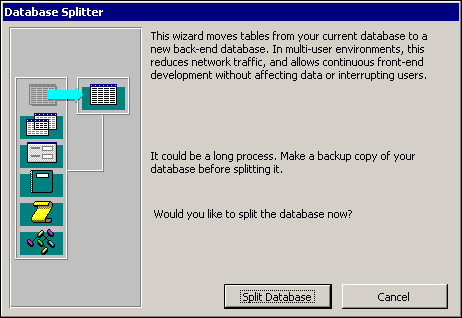
Choose Tools|Database Utilities|Database Splitter to open the Database Splitter dialog box, shown in Figure 20.2.
Click Split Database; this opens the Create Back-end Database dialog box. (See Figure 20.3.)
Enter the name for the database that will contain all the tables. Click Split. The Database Splitter Wizard creates a new database holding all the tables, and links are created between the current database and the database containing the tables. (See Figure 20.4.)
Caution
Be aware that, when you’re distributing an application using linked tables, you must write code to make sure the data tables can be located from each application database on the network. This is because Access hard-codes the location of linked tables into the application database. If each user has the same path to the file server, this isn’t a problem. However, if the path to the file server varies, you need to write a routine that makes sure the tables can be successfully relinked. If they can’t, the routine prompts the user for the data’s location. This routine is covered in Chapter 19.
Although the preceding tips for designing network applications reduce network traffic, they in no way reduce locking conflicts. To protect shared data, Access locks either a record or a page of data as the user edits a record. In this way, multiple users can read the data, but only one user can make changes to it. Data can be locked through a form or through a recordset that isn’t bound to a form.
Here are the methods of locking for an Access application:
Record locking
Page locking
Table and Recordset locking
Opening an entire database with Exclusive Access
With Record locking, only the record the user is editing is locked. With Page locking, the 4K page with the record being edited is locked. On the other hand, in Table and Recordset locking, the entire table or recordset with the record being edited is locked. With Database locking, the entire database is locked, unless the user opening the database has opened it for read-only access. In that case, other users can also open the database for read-only access. The ability to get exclusive use of a database can be restricted through security.
It’s important to note that the locking scheme you adhere to depends on the source providing the data. If you’re using client/server data, you inherit the locking scheme of the particular back end you’re using. If you’re manipulating ISAM data over a network, you get the type of data locking that the particular ISAM database supports. For example, if you’re working with a FoxPro database, you can use Record locking or any other locking scheme that FoxPro supports.
Now that you understand the basics of using Access in a multiuser environment, I am going to take things a step further by discussing client/server applications. One of the hot computing terms of the ‘90s, client/server refers to distributed processing of information. A client/server model involves the storage of data on database servers dedicated to the tasks of processing data and storing it.
The client/server model introduces a separation of functionalities. The client, or front end, is responsible for presenting the data and doing some processing. The server, or back end, is responsible for storing, protecting, and performing the bulk of the data processing.
With its tools that assist in the rapid development of queries, forms, and reports, Access provides an excellent front end for the presentation of back-end data.
For years, most information professionals have worked with traditional programming languages to process and maintain data integrity in the application. This means that data validation rules must be embedded in the programming code. Furthermore, these types of applications are record oriented—that is, all records are read into memory and processed. This scenario has several drawbacks:
If the underlying data structure changes, every application that uses the data structure must be changed.
Data validation rules must be placed in every application that accesses a data table.
Presentation, processing, and storage are handled by one program.
Record-oriented processing results in an extraordinary amount of unnecessary network traffic.
Client/server technology was not as necessary when there was a clear delineation between mainframe applications and personal computer applications. Today, the line of demarcation has blurred. Personal computer applications are beginning to take over many applications that had been relegated to mainframe computers in the past. The problem is that users still are very limited by the bandwidth of network communications. This is one place where client/server technology can really help.
However, many developers are confused about what client/server architecture really is. Some mistakenly believe that an Access MDB database file stored on a file server acts as a database server. This is not the case. (In fact, I have participated in many debates in which other developers have insisted that Access itself is a database server application. Well, it’s not.) Access is a front-end application that can process data stored on a back end. In this scenario, the Access application runs on the client machine accessing data stored on a database server running software such as Microsoft SQL Server. Access does an excellent job acting as the client-side, front-end software in this scenario. The confusion lies in Access’s capability to act as a database server.
Many people mistakenly believe that an Access MDB database file stored on a file server acts as a database server. This is not the case. The difference lies in the way that data is retrieved when Access is acting as the front end to a database server versus when the data is stored in an Access MDB file. Suppose that you have a table with 500,000 records. A user runs a query based on the 500,000-record table stored in an Access database on a file server. Suppose that the user wants to see a list of all the Californians who make more than $75,000 per year. With the data stored on the file server in the Access MDB file format, all records would be sent over the network to the workstation, and the query would be performed on the workstation. (See Figure 20.5.) This results in significant network traffic.
On the other hand, assume that these 500,000 records were stored on a database server such as Microsoft SQL Server. If user runs the same query, only the names of the Californians who make more than $75,000 per year would be sent over the network. In this scenario, only the specific fields requested would be retrieved. (See Figure 20.6.)
What does this mean to you? When should you become concerned with client/server technology and what it can offer you? The following sections present some guidelines as to why you might want to upsize from an Access back end to a SQL Server back end.
As the volume of data in your Access database increases, you probably will notice a degradation in performance. Many people say that 100MB is the magical number for the maximum size of an Access database, but many back-end database servers can handle databases containing multiple gigabytes of data. Although a maximum size of 100MB for an Access database is a good general guideline, it is not a hard-and-fast rule. You might find that the need to upsize occurs when your database is significantly larger or smaller than 100MB. The magic number for you depends on all the factors discussed in the following sections, as well as on how many tables are included in the database. Generally, Access performs better with large volumes of data stored in a single table rather than in multiple tables.
Just as a large volume of data can be a problem, so can a large number of concurrent users. In fact, more than 10 users concurrently accessing an Access database can degrade performance. As with the amount of data, this is not a magical number. I have seen applications with fewer than 10 users where performance is awful, and I have seen applications with significantly more than 10 users where performance is acceptable. It often depends on how the application is designed, as well as what tasks the users are performing.
Certain applications demand better performance than other applications. An Online Transaction Processing system (OLTP) generally requires significantly better performance than a Decision Support System (DSS), for example. Suppose that 100 users are simultaneously taking phone orders. It would not be appropriate for the users of the system to ask their customers to wait 15 seconds between entering each item that is ordered. On the other hand, asking users to wait 60 seconds to process a management report that users run once each month is not a lot to ask (although many still will complain about the minute).
Most back-end database servers can use multithreaded operating systems with multiple processors to handle large volumes of user demand; Access cannot.
As a file server in an organization experiences increasing demands, the Access application simply might exacerbate an already growing problem. By moving the application data to a database server, the overall reduced demands on the network might provide all users on the network with better performance regardless of whether they are using the Access application.
Probably one of the most exaggerated situations I have seen is one in which all the workstations were diskless. Windows and all application software were installed on a file server. All the users were concurrently loading Microsoft Word, Microsoft Excel, and Microsoft PowerPoint over the network. In addition, they had large Access applications with many database objects and large volumes of data. All this was stored on the file server as well. Needless to say, performance was abysmal. You can’t expect an already overloaded file server to handle sending large volumes of data over a small bandwidth. The benefits offered by client/server technology can help alleviate this problem.
The backup and recovery options offered with an Access MDB database stored on a file server simply do not rival the options for backup and recovery on a database server. Any database server worth its salt sports very powerful uninterruptible power sources (UPSs). Many have hot-swappable disk drives with disk mirroring, disk duplexing, or disk striping with parity (RAID Level 5). With disk mirroring and duplexing, data can be written to multiple drives at one time, providing instantaneous backups. Furthermore, some database server tape backup software enables backups to be completed while users are accessing the system. Many offer automatic transaction logging. All these options mean less chance of data loss or downtime. With certain applications, this type of backup and recovery is overkill. With other applications, it is imperative. Although some of what back ends have to offer in backup and recovery can be mimicked by using code and replication, it is nearly impossible to get the same level of protection from an Access database stored on a file server that you can get from a database stored on a database server.
Access offers what can be considered the best security for a desktop database. However, it cannot compare with the security provided by most database servers. Database server security often works in conjunction with the network operating system. This is the case, for example, with Microsoft SQL Server and Windows NT Server. The user is given no direct rights to the physical database file; it can be accessed only via an ODBC data source or an ADO connection. Remember that no matter how much security you place on an Access database, this does not prevent a user from seeing or even deleting the entire MDB file from the network disk.
It is very easy to offer protection from this potential problem, and others, on a database server. Furthermore, many back-end application database server products offer field-level security not offered within an Access MDB file. Finally, many back ends offer integrated security with one logon for both the network and the database.
The Access MDB file format is proprietary. Very few other products can read data stored in the Access database format. With a back-end database server that supports open database connectivity (ODBC), front-end applications can be written in a variety of front-end application software, all concurrently using the same back-end data.
You must evaluate the specific environment in which your application will run:
After you answer these and other questions, you can begin to decide whether the benefits of the client/server architecture outweigh the costs involved.
The good news is that it is not an all-or-none decision. Various options are available for client/server applications using Access as a front end. Furthermore, if you design your application with upsizing in mind, moving to client/server technology will not require you to throw out what you have done and start again. In fact, Microsoft provides an upsizing wizard that makes upsizing to a SQL Server database a relatively painless process. How painless depends on numerous factors, including how complex your queries are, whether your queries include VBA functions, and other factors that are covered later in this chapter, and in detail in Alison Balter’s Mastering Access 2002 Enterprise Development.
This section takes a look at the many different roles Access can take in an application design.
Earlier in this book, you learned about using Access as both the front end and the back end. The Access database is not acting as a true back end because it is not doing any processing. Figure 20.7 shows the architecture in this scenario. The Access application resides on the workstation. Access uses the Microsoft Jet Engine to communicate with data stored in an Access MDB database file stored on the file server.
In the second scenario, back-end tables can be linked to the front-end application database (.MDB). The process of linking to back-end tables is almost identical to that of linking to tables in other Access databases or to external tables stored in FoxPro, Paradox, or dBASE. And, the linked tables can be treated like any other linked tables. Access uses ODBC to communicate with the back-end tables. (See Figure 20.8.) Your application sends an Access SQL statement to the Access Jet Engine, which translates the statement into ODBC SQL. This ODBC SQL statement is then sent to the ODBC Manager, which locates the correct ODBC driver and passes it the ODBC SQL statement. Supplied by the back-end vendor, the driver translates the statement into the back end’s specific dialect. The now back end–specific query is sent to the SQL server and to the appropriate database. As you might imagine, all this translation takes quite a bit of time. Furthermore, ODBC is becoming a technology of the past; it is quickly being replaced by the ADO/OLEDB technology. That is why one of the two alternatives that follow might be a better solution.
One of the bottlenecks of using linked tables is waiting for all the translation to happen. Because of this and for the following reasons, you want to bypass the translation process:
Access SQL might not support some operation that is supported by the native query language of the back end.
Either the Jet Engine or the ODBC driver produces a SQL statement that is not optimized for the back end.
You want a process performed in its entirety on the back end.
As an alternative, you can execute a pass-through query written in the syntax specific to the back-end database server. Although the query does pass through the Jet Engine, Jet does not perform any translation on the query. Neither does ODBC. The ODBC Manager sends the query to the ODBC driver, which passes the query to the back end without performing any translation. In other words, exactly what was sent from Access is what is received by the SQL database. Figure 20.9 illustrates this scenario. Notice that the Jet Engine, the ODBC Manager, and the ODBC driver are not eliminated entirely. They are still there, but they have much less impact on the process than they do with attached tables. Pass-through queries are covered in more detail in the “Using Pass-Through Queries” section of this chapter.
As you will see later in this chapter, pass-through queries are not a panacea, although they are very useful. The results of a pass-through query are not updateable, for example. Furthermore, because pass-through queries are written in the back end’s specific SQL dialect, you must rewrite them if you swap out your back end. For these reasons and others, pass-through queries generally are used with other solutions.
A stored procedure is compiled SQL code stored on a back end. It is generally executed using ADO or DAO code. You can also execute a stored procedure using a pass-through query. Regardless of what you call it, the code within the stored procedure is written in the SQL native to the back end on which it is stored, and the stored procedure is executed in entirety on the back end. Stored procedures can return results or can simply execute on the back end without returning any data.
An additional, very viable solution is available when working with a back-end database server. This involves using a Microsoft Access Data Project (.adp), which was introduced with Access 2000. By using a Microsoft Access Data Project (.adp), you bypass the Jet Engine entirely. An Access project contains only code-based objects such as forms, reports, data access pages, macros, and modules. All tables, views, database diagrams, functions, and stored procedures are stored in a SQL Server database. After you have connected with a SQL Server database, you can easily view, create, modify, and delete SQL Server objects. Figure 20.10 illustrates this scenario. Notice that neither the Jet Engine nor ODBC is involved in the scenario.
People who talk about client/server technology use many terms that are unfamiliar to the average database developer. To get a full appreciation of client/server technology and what it offers, you must have at least a general understanding of the terminology. Table 20.1 lists the most commonly used terms.
Table 20.1. Client/Server Terms
Term | Definition |
|---|---|
Column | A field. |
DDL | A data definition language used to define and describe the database structure. |
Foreign key | A value in one table that must be looked up in another table for validation. |
Jet | The native database engine used by Microsoft Access. |
ODBC (Open Database Connectivity) | A standard proposed by Microsoft that provides access to a variety of back-end databases through a common interface. In essence, ODBC is a translator. |
OLE DB | A new standard for connecting to relational and nonrelational data sources. |
DAO (Data Access Objects) | A method of manipulating data. It is being replaced by ADO and was optimized for accessing Jet databases. |
ADO (ActiveX Data Objects) | A COM-based object model that you to easily manipulate OLE DB data sources. It is the data access methodology that DAO. |
Primary key | A set of fields that uniquely identifies a row. |
Row | A record. |
Schema | A blueprint of the entire database. Includes table definitions, relationships, security, and other important information about the database. |
SQL (Structured Query Language) | A type of data manipulation language commonly used to talk to tables residing on a server. |
Stored procedures | Compiled SQL statements, such as queries, stored on the database server. Can be called by an application. |
Transaction | A set of actions that must be performed on a database. If any one action fails, all the actions are discarded. |
Triggers | Pieces of code that execute in response to an action occurring on a table (insert, edit, or delete). |
Many books are devoted solely to client/server technology; Alison Balter’s Mastering Access 2002 Enterprise Development focuses entirely on client/server and Web development using Access 2002. Most magazines targeted at developers contain numerous articles on client/server technology. Access/VB/SQL Advisor always offers excellent articles on client/server development. Many of the articles are specifically about client/server connectivity using Access as a front end. VB Programmer’s Journal often contains useful articles as well. Another excellent source of information is the Microsoft Developer Network CD. Offered by Microsoft as a subscription, it includes numerous articles and white papers on client/server technology, ODBC, and use of Access as a front end to a database server.
Suppose that your database is using Microsoft Access as both the front end and back end. Although an Access database on a file server might have been sufficient for a while, the need for better performance, enhanced security, or one of the other benefits that a back-end database provides compels your company (or your client’s company) to upsize to a client/server architecture. The Access tables already have been created and even contain volumes of data. In this scenario, it might make sense to upsize.
Because all the tables have been designed as Access tables, they must be upsized to the back-end database server. Upsizing involves moving tables from a local Access database (or from any PC database) to a back-end database server that usually runs on Unix, Windows 2000, Windows NT Server, and OS/2 LAN Server or as a Novell NetWare NLM.
Another reason why tables are upsized from Access to a back-end server is that many developers prefer to design their tables from within the Access environment. Access offers a more user-friendly environment for table creation than most server applications.
Because of the many caveats involved when moving tables from Access to a back end, many people opt to design the tables directly on the back end. If you do design your tables in Access, you can export them to the back end and then link them to your local database, or you can use the Upsizing Wizard to greatly facilitate this process. Regardless of the method that you choose, as you export your tables to the database server, you need to be aware of the issues covered in the following sections.
Note
If you are updating to a SQL Server database, most of the concerns regarding upsizing are handled by the Upsizing Wizards included as part of Microsoft Access 2000 and Microsoft Access 2002.
When exporting a table to a server, no indexes are created. All indexes need to be re-created on the back-end database server. If your database server is running Microsoft SQL Server, you can use the Access Upsizing Wizard for Access 2000 or Access 2002. These wizards create indexes for server tables in the place where the indexes exist in your Access tables.
AutoNumber fields are exported as Long integers. Because some database servers do not support autonumbering, you have to create an insert trigger on the server that provides the next key value. You also can achieve autonumbering by using form-level events, but this is not desirable. The numbering will not be enforced if other applications access the data. If you are upsizing to Microsoft SQL Server, the Upsizing Wizard for Access 2000 and Access 2002 convert all AutoNumber fields to Identity fields.
Default values are not automatically moved to the server, even if the server supports them. You can set up default values directly on the server, but these values do not automatically appear when new records are added to the table unless the record is saved without data being added to the field containing the default value. As with autonumbering, default values can be implemented at the form level, with the same drawbacks. If the Upsizing Wizard for Access 2000 or Access 2002 is used to move the data to Microsoft SQL Server, default values are exported to your server database.
Validation rules are not exported to the server. They must be re-created using triggers on the server. No Access-defined error messages are displayed when a server validation rule is violated. Your application should be coded to provide the appropriate error messages. You also can perform validation rules at the form level, but they are not enforced if the data is accessed by other means. If the Upsizing Wizard for Access 2000 or Access 2002 is used to move the data to Microsoft SQL Server, validation rules are exported to the server database.
Relationships need to be enforced using server-based triggers. Access’s default error messages do not appear when referential integrity is violated. You need to respond to, and code for, these error messages in your application. You can enforce relationships at the form level, but as with other form-level validations, this method of validation does not adequately protect your data. If the Upsizing Wizard for Access 2000 or Access 2002 is used to move the data to Microsoft SQL Server, all relationships and referential integrity that you have set up in your Access database are set up within the server database.
Security features that you have set up in Access do not carry forward to the server. You need to re-establish table security on the server. After security is set up on the server, Access is unaware that the security exists until the Access application attempts to violate the server’s security. Then, error codes are returned to the application. You must handle these errors by using code and displaying the appropriate error message to users.
Servers often have much more stringent rules than Access does regarding the naming of fields. When you export a table, all characters that are not alphanumeric are converted to underscores. Most back ends do not allow spaces in field names. Furthermore, most back ends limit the length of object names to 30 characters or fewer. If you already have created queries, forms, reports, macros, and modules that use spaces and very long field and table names, these database objects might become unusable when you move your tables to a back-end database server.
Most back ends have many reserved words. It is important to be aware of the reserved words of your specific back end. It is quite shocking when you upsize a table and find that field names you have been using are reserved words on your database server. If this is the case, you need to rename all the fields in which a conflict occurs. Once again, this means modifying all the queries, forms, reports, macros, and modules that reference the original field names.
Many back-end databases are case sensitive. If this is the case with your back end, you might find that your queries and application code don’t process as expected. Queries or code that refer to the field or table name by using the wrong case are not recognized by the back-end database and do not process correctly.
Most properties cannot be modified on remote tables. Any properties that can be modified are lost upon export, so you need to set them up again when the table is exported.
If you set up your tables and code modules with upsizing in mind, you can eliminate many of the pitfalls discussed previously. Despite any of the problems that upsizing can bring, the scalability of Access is one of its stronger points. Sometimes resources are not available to implement client/server technology in the early stages of an application. If you think through the design of the project with the possibility of upsizing in mind, you will be pleased at how relatively easy it is to move to client/server technology when the time is right. With the Access 2000 and Access 2002 Upsizing Wizards, which are designed to take an Access application and upsize it to Microsoft SQL Server, the process is relatively simple. The upsizing tools for Access 2000 and Access 2002 perform a lot of the work involved in upsizing a database, with just the click of a few buttons.
Note
Client/server development and client/server issues are covered in extensive detail in Alison Balter’s Mastering Access 2002 Enterprise Development.
Caution
Although the upsizing tools for Access 2000 and Access 2002 are both excellent, they do have their drawbacks. For example, they do not always map the Access field type to the desired SQL Server field type. For this reason you can opt not to use the wizards. If, despite their shortcomings, you decide to use the upsizing wizards, make sure that you carefully review both the upsizing report and the structure of each table after it is upsized.
Transaction processing refers to the grouping of a series of changes into a single batch. The entire batch of changes is either accepted or rejected as a group. One of the most common implementations of transaction processing is a bank automated teller machine (ATM) transaction. Imagine that you go to the ATM to deposit your paycheck. In the middle of processing, a power outage occurs. Unfortunately, the bank recorded the incoming funds prior to the outage, but the funds had not yet been credited to your account when the power outage occurred. You would not be very pleased with the outcome of this situation. Transaction processing would prevent this scenario from occurring. With transaction processing, the whole process succeeds or fails as a unit.
A group of operations is considered a transaction if it meets the following criteria:
It is atomic.—. The group of operations should finish as a unit or not at all.
It is consistent.—. The group of operations, when completed as a unit, retains the consistency of the application.
It is isolated.—. The group of operations is independent of anything else going on in the system.
It is durable.—. After the group of operations is committed, the changes persist, even if the system crashes.
If your application contains a group of operations that are atomic and isolated, and if, in order to maintain the consistency of your application, all changes must persist even if the system crashes, you should place the group of operations in a transaction loop. With Access 2000 and Access 2002, the primary benefit of transaction processing is data integrity. As you will see in the next section, in versions prior to Access 95, transaction processing also provided performance benefits.
In Access 2.0, there were many marginal benefits of added transaction processing because Access 2.0 did no implicit transaction processing itself. Listing 20.1 shows code that, when run in Access 2.0, writes the data to disk each time the Update method occurs in the loop. These disk writes were costly in terms of performance, especially if the tables were not located on a local machine.
Example 20.1. Transaction Processing Using Access Basic as Seen in Access 2.0
Sub IncreaseQuantity()
On Error GoTo IncreaseQuantity_Err
Dim db As DATABASE
Dim rst As Recordset
Set db = CurrentDb
Set rst = db.OpenRecordset("Select OrderId, _
Quantity From tblOrderDetails", _
dbOpenDynaset)
'Loop through recordset increasing Quantity field by 1
Do Until rst.EOF
rst.Edit
rst!Quantity = rst!Quantity + 1
rst.UPDATE
rst.MoveNext
Loop
IncreaseQuantity_Exit:
Set db = Nothing
Set rst = Nothing
Exit Sub
IncreaseQuantity_Err:
MsgBox "Error # " & Err.Number & ": " & Error.Description
Resume IncreaseQuantity_Exit
End SubNote
This code, and all the code in this chapter, is located in the CHAP20EX.MDB database on the sample code CD-ROM in the basTrans module.
The same code found in Listing 20.1 performs much differently when run in Access 2000 or Access 2002. In addition to any explicit transaction processing you might implement for data-integrity reasons, Access 2000 and Access 2002 do their own behind-the-scenes transaction processing. This implicit transaction processing is done solely to improve the performance of your application. As the processing loop in the IncreaseQuantity routine executes, Access buffers and then periodically writes the data to disk. In a multiuser environment, Jet (implicitly) commits transactions every 50 milliseconds by default. This period of time is optimized for concurrency rather than performance. If you feel that it is necessary to sacrifice concurrency for performance, you can modify a few Windows registry settings to achieve the specific outcome you want. These settings are covered in the next section.
Although implicit transaction processing, along with the modifiable Windows registry settings, generally gives you better performance than explicit transaction processing, it is not a cut-and-dried situation. Many factors impact the performance benefits gained by both implicit and explicit transaction processing:
Amount of free memory
Number of columns and rows being updated
Size of the rows being updated
Network traffic
If you plan to implement explicit transaction processing solely to improve performance, you should make sure that you benchmark performance using both implicit and explicit transactions. It is critical that your application-testing environment be as similar as possible to the production environment in which the application will run.
Before you learn how to implement transaction processing, take a look at what you can do to modify the default behavior of the transaction processing built in to Access 2000 and Access 2002. Three registry settings affect implicit transactions in Access 2000 and Access 2002: ImplicitCommitSync, ExclusiveAsnycDelay, and SharedAsyncDelay. These keys are located in the HKEY_LOCAL_MACHINESOFTWAREMicrosoftJet4.0EnginesJet 4.0 registry folder.
Tip
You can access the Windows registry using the RegEdit utility. To utilize RegEdit, select the Run option from the Start menu. Then type RegEdit.
The ImplicitCommitSync setting determines whether the system waits for a commit to finish before proceeding with application processing. The default is No. This means that the system will proceed without waiting for the commit to finish. You generally won’t want to change this setting; using No dramatically improves performance. The danger of accepting the value of No is that you will increase the amount of time during which the data is vulnerable. Before the data is flushed to disk, the user might turn off the machine, compromising the integrity of the data.
The ExclusiveAsyncDelay setting specifies the maximum number of milliseconds that elapse before Jet commits an implicit transaction when a database is opened for exclusive use. The default value for this setting is 2000 milliseconds. This setting does not in any way affect databases that are open for shared use.
The SharedAsyncDelay setting is similar to the ExclusiveAsyncDelay setting. It determines the maximum number of milliseconds that elapse before Jet commits an implicit transaction when a database is opened for shared use. The default value for this setting is 50. The higher this value, the greater the performance benefits reaped from implicit transactions, but also the higher the chances that concurrency problems will result. These concurrency issues are discussed in detail in Alison Balter’s Mastering Access 2002 Enterprise Development.
In addition to the settings that affect implicit transaction processing in Access 2000 and Access 2002, an additional registry setting affects explicit transaction processing. The UserCommitSync setting controls whether explicit transactions are completed synchronously or asynchronously. With the default setting of Yes, control doesn’t return from a CommitTrans statement until the transactions actually are written to disk, resulting in synchronous transactions. When this value is changed to No, a series of changes is queued, and control returns before the changes are complete.
You can modify the values of these registry settings and other Jet settings by using Regedit.exe (the Registry Editor) for Windows 95/98, Windows NT, and Windows 2000. Changes to this section of the registry affect all applications that use the Jet 4.0 Engine. If you want to affect only your application, you can export the Microsoft Jet portion of the registry tree and import it into your application’s registry tree. You then can customize the registry settings for your application. To force your application to load the appropriate registry tree, you must set the INIPath property of the DBEngine object.
A much simpler approach is to set properties of the ADO Connection object; you can specify new settings at runtime for all the previously mentioned registry entries as well as for additional entries. A further advantage of this approach is that it will modify (temporarily) registry entries for any machine under which your application runs. Any values you change at runtime temporarily override the registry values that are set, enabling you to easily control and maintain specific settings for each application. This code illustrates how you modify the ExclusiveAsyncDelay and SharedAsyncDelay settings using properties of the Connection object:
Sub ChangeOptions()
Dim cnn As ADODB.Connection
Set cnn = CurrentProject.Connection
cnn.Properties("JET OLEDB:Exclusive Async Delay") = 1000
cnn.Properties("JET OLEDB:Shared Async Delay") = 50
End SubNow that you are aware of the settings that affect transaction processing, you are ready to learn how to implement transaction processing. Three methods of the Connection object (covered in Chapter 14, “What Are ActiveX Data Objects and Data Access Objects, and Why Are They Important?”) control transaction processing:
BeginTransCommitTransRollbackTrans
The BeginTrans method of the Connection object begins the transaction loop. The moment BeginTrans is encountered, Access begins writing all changes to a log file in memory. Unless the CommitTrans method is issued on the Connection object, the changes are never actually written to the database file. After the CommitTrans method is issued, the updates are written permanently to the database object. If a RollbackTrans method of the Connection object is encountered, the log-in memory is released. Listing 20.2 shows an example of how transaction processing works under Access 2000 and Access 2002. Compare this to Listing 20.1.
Example 22.2. Transaction Processing in Access 2000 and Access 2002 Using BeginTrans, Logging, CommitTrans, and RollbackTrans
Sub IncreaseQuantityTrans()
On Error GoTo IncreaseQuantityTrans_Err
Dim cnn As ADODB.Connection
Dim rst As ADODB.Recordset
Dim boolInTrans As Boolean
boolInTrans = False
Set rst = New ADODB.Recordset
Set cnn = CurrentProject.Connection
rst.ActiveConnection = cnn
rst.CursorType = adOpenKeyset
rst.LockType = adLockOptimistic
rst.Open "Select OrderId, Quantity From tblOrderDetails"
'Begin the Transaction Loop
cnn.BeginTrans
boolInTrans = True
'Loop through recordset increasing Quantity field by 1
Do Until rst.EOF
rst!Quantity = rst!Quantity + 1
rst.UPDATE
rst.MoveNext
Loop
'Commit the Transaction; Everything went as Planned
cnn.CommitTrans
boolInTrans = False
IncreaseQuantityTrans_Exit:
Set cnn = Nothing
Set rst = Nothing
Exit Sub
IncreaseQuantityTrans_Err:
MsgBox "Error # " & Err.Number & ": " & Err.Description
'Rollback the Transaction; An Error Occurred
If boolInTrans Then
cnn.RollbackTrans
End If
Resume IncreaseQuantityTrans_Exit
End SubThis code uses a transaction loop to ensure that everything completes as planned or not at all. Notice that the loop that moves through the recordset, increasing the Quantity field in each record by 1, is placed in a transaction loop. If all processing in the loop completes successfully, the CommitTrans method executes. If the error-handling code is encountered, the RollbackTrans method is issued, ensuring that none of the changes are written to disk. The boolInTrans variable is used to determine whether the code is within the transaction loop. This ensures that the error handler only performs the rollback if an error occurs within the transaction loop. If the CommitTrans method or the RollBackTrans method is issued without an open transaction, an error occurs.
Access 95 was the first desktop database that included built-in replication capabilities. Replication has further matured with the introduction of Access 2000 and Access 2002; it’s a powerful feature that is becoming increasingly important in today’s world of mobile and distributed computing. This section teaches you about replication and how to implement it through both the user interface and code.
Data replication is the capability of a system to automatically make copies of its data and application objects in remote locations. Any changes to the original or data changes to the copies are propagated to all other copies. Data replication allows users to make changes to data offline at remote locations. Changes to either the original or the remote data are synchronized with other instances of the database.
The original database is referred to as the design master. Changes to definitions of tables or other application objects can be made only at the design master. The design master is used to make special copies called replicas. Although there is only one design master, replicas can be made from other replicas. The process of the design master and replicas sharing changes is referred to as synchronization. The design master and replicas that participate in the synchronization process are collectively referred to as a replica set.
To see an example of data replication at work, suppose that you have a team of salespeople who are out on the road all day. At the end of the day, each salesperson logs on to one of the company’s Windows NT servers through DUN (Dial-Up Networking) or RAS (Remote Access Services). Each salesperson’s transactions are sent to the server. If necessary, any changes to the server data are also sent to the salesperson. In addition to data being replicated, if the developers in the organization are busily adding forms, reports, and modules to the database’s master copy, any changes to the application components are also updated in the remote copies as users log on to the system.
This example illustrates just one of the several valuable uses of replication. In a nutshell, data replication is used to improve the availability and integrity of data throughout an organization or enterprise. The practical uses of data replication are many; they can be categorized into five general areas, explained in the following sections.
In today’s global economy, it’s the norm for companies to have many offices distributed throughout the country, or even the world. Before Access 95, it was difficult to implement an Access application that would support sharing data among several offices. However, with replication, each office can have a replica of the database. Periodically throughout the day, each office can synchronize its changes into data at corporate headquarters. How often the synchronization happens depends on the frequency required for data at each location to be current at any given moment.
Sharing data among dispersed users is illustrated by the salespersons example used earlier. This implementation of replication generally involves mobile users who connect to the network after modifying data out on the road. Because only incremental changes are transferred from the design master (the original) to the replicas (the copies), and from the replicas to the design master, this form of replication makes the mobile computing scenario economically feasible.
Replication can be very effective in reducing network traffic loads. The design master can be replicated onto one or more additional servers. Distributed users can then make changes to one of the additional servers, which significantly improves performance by distributing the processing load throughout the network. Changes made to the data on the additional servers can be synchronized with the main server periodically during the day.
Replication is an excellent vehicle for distributing application updates. Design changes can be made only to the design master; therefore, as users throughout the organization log on to synchronize with the design master, any structural changes to the application are sent to the user. This is much more efficient and effective than giving every user an entirely new copy of the application database each time a minor change is made to the application’s schema.
Many people don’t think of replication as a means of backing up application data, but replication is extremely well suited for this task. Ordinarily, to back up an Access database, everyone must log off the system, but that’s not necessary with replication. The synchronization process can occur periodically during the day while users are still logged on to the system, and all changes are replicated. Not only is this more efficient than backing up the entire database, it also ensures that you can quickly be up and running on a backup server if there’s a problem on a main server.
Despite the many positive aspects of replication, it is not appropriate in a few situations, such as when data consistency is critical. If an application requires that data be current at every given moment, it isn’t a good candidate for replication. Replication is also not effective when many different users modify a large number of existing records throughout the day. In a situation like this, resolving conflicts that happen when multiple users update the same record wouldn’t be practical. Furthermore, you cannot use replication if you are using Visual SourceSafe to manage the development process. Finally, you cannot rename or move design masters, and a design master that becomes corrupted can be difficult to recover.
The following steps compose the replication process:
Making a database replicable
Creating and distributing replicas
Synchronizing replicas with the design master
Resolving conflicts
These steps can be completed in the following ways:
Through the Access user interface
By using the Windows Briefcase
By using the Replication Manager
By using ADO code
The steps needed for the replication process, and the alternatives for performing each step, are covered in this chapter. An overview of each alternative is outlined in the following sections.
The Access user interface gives you a series of menu items that allow you to perform all the steps of the replication process. The Tools|Replication menu has the following options: Create Replica, Synchronize Now, Partial Replica Wizard, Resolve Conflict, and Recover Design Master. These menu options are covered throughout this chapter.
The Windows Briefcase supplies the foundation Access needs for the replication process. Users can simply drag a database file to the Briefcase to replicate it, make changes to the file while on the road, and synchronize the replica with the design master when they reconnect to the network. This is done because, when Access is installed, it registers a special class ID with the Windows Briefcase. When a database is dragged to the Briefcase, the Briefcase’s Reconciler code is called. When the user selects Update Selection or Update All from the Briefcase menu, the Merge Reconciler is called. Briefcase replication is available as an installation option through Windows 95, its successors, and Windows NT 4.0 and later.
The Replication Manager is a sophisticated tool that’s part of Microsoft Office 2000 and Office 2002 Developer. It’s a mandatory player in the replication process when you’re managing many replicas. Besides providing basic replication functionality, the Replication Manager lets you schedule the synchronization of replicas. In fact, the Replication Manager allows you to manage and intricately control all aspects of the replication process. The Replication Manager is covered in detail in Alison Balter’s Mastering Access 2002 Enterprise Development.
Most aspects of the replication process can also be done by using ADO code, which can be used to make a database replicable, create and synchronize replicas, and get and set properties of a replicable database. ADO can easily be integrated with the other methods of replication. Although it requires the most time and effort on your part, ADO code lets you base replication on events rather than time and give your users a custom user interface for the replication process.
Visual Basic 4.0 and later, Excel for Windows 95 and later, and Visual C++ all support replication using Data Access. You can’t perform replication with these products by using either the Briefcase or Microsoft Office Developer, however, so it’s easier to manage the replication process on a machine that has Access installed.
Many people think that the transition of a simple Access application to a multiuser or client/server environment is a simple one. I strongly disagree. There are several things to think about when moving an application from a single-user environment to a multiuser environment and even more things to think about when moving to a client/server environment. The more you think about these potential evolutions when you first design and build your application, the less problems you’ll have if your application data has to be upsized.
This chapter exposed you to multiuser techniques. It explained client/server technology and when you need it. It also talked about the various roles that Access plays in the application design model. Finally, you learned about two techniques that are important within an enterprise application: transaction processing and replication.
The chapter is intended to be an introduction to these important topics. All the topics in this chapter are covered in detail in Alison Balter’s Mastering Access 2002 Enterprise Development.