5
Cyber Standards for Modeling and Simulation
The emerging cyber threat presents defense with military command and control issues of a type, scale, and scope not seen before (Stella Croom‐Johnson 2016). Traditional processes have been stretched beyond their intended limits by the need to take into account not only the new factors and novel methods of attack introduced by the cyber threat but also the uncertainty regarding the efficiency of defensive countermeasures. In addition, on the INFOSEC “Hard Problems List” (Cyber Security and Information Assurance Interagency Working Group [CSIA IWG] 2006), under the heading “Information Provenance,” identifies assuring the quality of shared data by tracking its evolution, as one of the most fundamental problems in information security (Dandurand and Serrano 2013).
While cyber standards are developing to facilitate common terminology and the efficiency of work, they are used for an array of applications, often disjoint; some examples are shown in Table 5.1.
Table 5.1 Example cyber standards.
| Standard | Use | Author |
| Cyber Range Interoperability Standard (CRIS) | Connect cyber models on logical ranges for training exercises | Test Resource Management Center (TRMC) |
| Common Research Into Threats (CRITS) | Ability to communicate and share threats between organizations, government, and the public, opens up a more collaborative effort toward intelligence‐based active threat defense (MITRE 2014). | MITRE |
| Common Vulnerability Specification System (CVSS) | Open framework for communicating the characteristics and impacts of IT vulnerabilities. Its quantitative model ensures repeatable accurate measurement while enabling users to see the underlying vulnerability characteristics that were used to generate the scores (NIST). | NIST |
| OCTAVE | The OCTAVE method is an approach used to assess an organization's information security needs. OCTAVE Allegro is the most recently developed and actively supported method. This method is based on two older versions called OCTAVE Original and OCTAVE‐S (Carnegie Mellon University Software Engineering Institute [CMU SEI]). | CMU SEI |
| STIX/TAXII | Categorize cyber incidents using cyber information exchange standards | MITRE |
Table 5.1 provides a sampling of cyber standards currently available, mostly for information assurance use. Traditional Modeling and Simulation (M&S) tools, however, were developed to address the questions surrounding conventional warfare, but not those surrounding the confidentiality, integrity, and availability of essential mission networks, or their respective impact on a scenario. In cyber space, some of these questions can be addressed by the use of models. These range from those that categorize cyber incidents using cyber information exchange standards (such as TAXII and CybOX) to tools that provide a structured expression of threat and attack (such as STIX), and those that provide a visual analysis, and subsequent Situational Awareness (SA) of candidate threat scenarios.
Models of this type are capable of translating diverse and constantly changing information into actionable knowledge, giving cyber defenders flexibility in their available responses, helping to understand cyber observables and incidents, and giving managers outside the cyber domain an improved awareness of how a given situation might develop. This area is developing very quickly, and new tools have often been developed to address a specific need, but without interoperability with other such tools being a primary consideration. There is a very real need for standardization not only of the structures and formats used by these tools, but also for a common language across all areas to reduce misunderstandings and to facilitate the speedy processing and dissemination of information.
There are a number of areas where M&S tools can contribute to the cyber defense effort and has considered some of the potential benefits that could be derived from the application of standards. Building on this and other work, this section will identify some of the tools and standards currently in use in these areas, highlighting the benefits that could be derived from the consistent application of standards, potentially including the introduction of a common language.
5.1 Cyber Modeling and Simulation Standards Background
The emerging cyber threat presents defense with military command and control issues of a type, scale, and scope not seen before. Traditional processes have been stretched beyond their intended limits by the need to take into account new factors, and novel methods, of attack introduced by the cyber threat. Traditional M&S tools were developed to address questions surrounding conventional warfare. However, they were not designed to address the questions surrounding the confidentiality, integrity, and availability of essential cyber components, which are needed to support missions at the network and mission layers, nor do they address the question of how to represent the impact on a conventional training scenario of the loss of one or more of the supporting elements. The first line of cyber defense is provided by monitoring the cyber events and observables triggered by potential threats at the different layers and ensuring that robust security configurations, practices, and components provide the optimum balance between protection and usability. However, it may be assumed that at some point attack vectors will succeed in penetrating the operational network. This means that military personnel in non‐cyber roles need to be trained in how to recognize early indicators of potential cyberattacks and to understand the appropriate responses in such an eventuality.
For a holistic cyber approach to be truly effective, a systems approach is needed that embraces network defense, physical security, intelligence gathering, cyber response, operational training, and mission rehearsal. The main challenge in developing this approach is how to best integrate cyber standards with existing simulation standards to create a seamless representation of the impact of a cyberattack in non‐cyber mission rehearsal and training exercises.
5.2 An Introduction to Cyber Standards for Modeling and Simulation
The breadth of the cyber domain makes a full survey of cyber tools and research an evolving pursuit; independent of M&S. MITRE, for example, has done extensive work on cyber description, providing tools for both cyber specialists and more traditional operators who rely on cyber systems. In addition, M&S‐based approaches, including Tolk’s hierarchy (Tolk and Muguira 2003), provide a level of abstraction that helps capture the sometimes opaque cyber system relations.
5.2.1 MITRE’s (MITRE) Cyber Threat Information Standards
CybOX™, STIX™, and TAXII™ were developed by the MITRE Corporation as part of an initiative by the US Department of Homeland Security (DHS) Office of Cybersecurity and Communications, National Cybersecurity and Communications Integration Center (NCCIC). The aim was to automate and structure operational cybersecurity information‐sharing techniques across the globe, but even from the brief summary of these standards given below, synergies with the SISO objectives and standards are clearly apparent. These standards have transitioned to OASIS (OASIS) and are now open standards (Table 5.2).
Table 5.2 Cyber description tools (MITRE).
| Title | Description |
| CybOX™ (Cyber Observable eXpression) (MITRE) | The MITRE website summarizes CybOX™ as “a standardized language for encoding and communicating high‐fidelity information about cyber observables.” It offers a common structure at the enterprise level that can be used to represent dynamic events and static attributes in the network of interest, together with the associated corrective actions taken. |
| STIX™ (Structured Threat Information eXpression) (MITRE) | The STIX™ framework uses an XML schema to express cyber threat information with a view to enabling the sharing of that information and generating a cyber threat analysis language. It tries to build up the language by using referential relations between tables and nodes, with the goal of creating a standardized way of representing the cyber threat. |
| TAXII™ (Trusted Automated eXchange of Indicator Information) (MITRE) | TAXII™ is a standardized way of defining a set of services and message exchanges for exchanging cyber threat information. It uses XML and is service‐oriented with four options (Inbox, Poll, Collection Management, and Discovery) and three sharing models (Hub and Spoke, Source/Subscriber, and Peer to Peer). |
CybOX™, TAXII™, and many other information assurance tools fall into the “cyber for cyber” category, and are primarily tools which allow cyber professionals to communicate with each other. STIX™ is also a “cyber for cyber” tool: part of its functionality is as a common language for information sharing, but it has additional relevance to this section as it also provides a model for simulations to represent the different types of attacks.
These standards are focused on enabling information sharing between cyber defense tools and leveraging them for simulation requires a differentiation to be made between the two different communities:
- Cyber for Cyber (C4C)
- Cyber for Others (C4O)
The differences between the two types of simulation could be summarized as simulations for C4C personnel being task oriented and covering the tools, techniques, and procedures used in cyber defense. Those for C4O personnel are impact oriented and facilitate consideration of the measures needed to minimize the effects of a cyberattack on a mission. In this context, C4C tools address capability training and C4O tools address awareness.
Figure 5.1 goes some way to illustrating this difference, while highlighting the overlap between items of interest to non‐cyber military personnel (C4O) and those of interest to cyber operators (C4C) within the military. However, even though M&S systems and operator training systems are composed of the same underlying technologies, the policy and training overlap between them is limited.
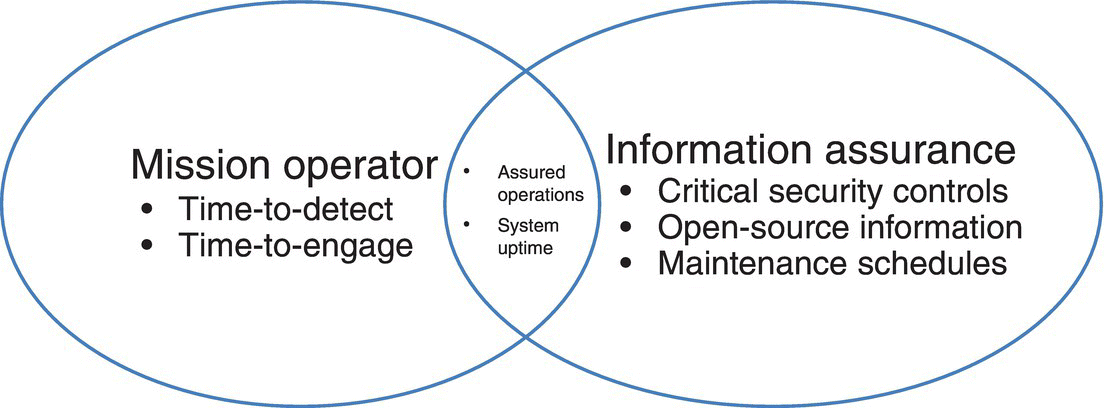
Figure 5.1 Military operator and cyber IA overlaps.
It is only recently that attempts have been made to integrate the cyber element with the mission rehearsal and training simulations for C4O personnel. Due to the way the term “cyber” has been overloaded, it is currently a challenge to differentiate between the training for the respective personnel shown in Figure 5.1. For example, CyberCiege (Thompson and Irvine 2011), a well‐known tool within the cyber community, is more likely to fit into the Cyber Information Assurance sphere in Figure 5.1, even though it is supplied by the US Naval Postgraduate School which would at first sight make it seem a fit for Military Operators. In addition, the Cyber Operational Architecture Training System (COATS) (Wells and Bryan 2015; Morse et al. 2014a, b) described below, although currently aspirational and described in terms of distributed simulation (i.e. information technology) terms, is intended as more of a training tool.
5.2.2 Cyber Operational Architecture Training System
The US COATS (Wells and Bryan 2015) project examined how a general‐purpose cyber effects data model might allow the outputs of a cyber range to be injected into a simulation similar to those used in mission rehearsal and training exercises for non‐cyber military personnel. This used the IEEE standard 1730‐2010™ (IEEE recommended Practice for Distributed Simulation Engineering and Execution Process [DSEEP]) (IEEE Std 1730‐2010) to support the integration of simulations for the two groups and to support the creation of linkages between them. A natural next stage is the integration of multiple cyber ranges and tools with multiple simulations (Damodaran and Couretas 2015), currently called a logical range. Implicit in this activity is the need for standardized formats, semantics, and architectures to enable interoperability between cyber ranges and tools, as well as between cyber ranges and tools and simulation tools. An additional issue is the need to reconcile the issues involved with porting data from the cyber tools and ranges into training simulations. The simulations and cyber tools will not necessarily operate at the same levels of abstraction, so this is not a trivial challenge.
5.2.3 Levels of Conceptual Interoperability
Tolk’s levels of Conceptual Interoperability Model (Tolk and Muguira 2003) outlines seven levels of interoperability with applications to cyber M&S (Figure 5.2).

Figure 5.2 Levels of Conceptual Interoperability Model.
Tolk’s levels span a range that goes from stand‐alone tools, with no interoperability, to tools with conceptual interoperability where all elements of a model are designed with interoperability being a key requirement taken into account from their design stage.
From the Tolk model, it can be inferred that cyber tools used by C4C personnel, especially ranges, have traditionally been designed at Level 0 (emulators, no interoperability) to ensure maximum security both from incoming cyberattacks and accidental (outgoing) data leakage. As cyber ranges mostly use emulators, they tend to be confined to using real (or virtualized) Computer Information Systems (CIS) components or protocols, and have relatively few constructive components. This is because constructive simulations are software and may be adapted easily to implement any interface for interoperability: cyber range components, as given above, are mostly CIS components (live or virtual), and it is more difficult to modify them to provide functional control interfaces. On the other hand, many C4C tools include scenarios requiring CIS components rather than software implementations.
While this is now starting to change, the standards for cyber tools are predominantly technical standards focused at Levels 0–3, whereas SISO standards are more focused at Levels 4 and 5. Simulations used by C4O personnel in training and mission rehearsal exercises for non‐cyber military personnel often include constructive elements (e.g. Computer Generated Forces [CGFs]) making it easier for them to reach these higher levels of interoperability.
At this stage it should be highlighted that an emerging finding from the COATS work was the importance of ensuring a common understanding of the vocabulary used. When working across boundaries between federated training simulations and tools in the cyber domain, each community has its own vocabulary and the meaning of a given word can differ substantially according to context. Many words are common between the cyber and simulation communities, but this can give rise to confusion when working with members of both communities. For instance, a representative from the simulation world (C4O) might draw their interpretation from the mission perspective and understand “synthetic environment” to mean terrain or CGFs. A representative from the cyber world (C4C) is more likely to draw their interpretation from a technical perspective and, in the same conversation, understand “synthetic environment” to mean a cyber range. It is important for all users to have the same understanding of what is meant in the given context and these two perspectives will need to be reconciled and aligned before work can start to create a common vocabulary.
5.3 Standards Overview – Cyber vs. Simulation
This section will take a brief look at the standards used in both the cyber domain and the simulation domain. It will show how standards are a key element in each domain, and how they are aimed at different levels of Tolk’s Conceptual Interoperability model.
From even a brief comparison it becomes apparent that most standards used in the cyber community operate at Levels 0–3 of the Tolk model. These are focused on ensuring the confidentiality, integrity, and availability of data and assume a relatively low level of trust between organizations and nations. SISO standards typically address the physical layer, and operate at Levels 4 and 5 of the Tolk model. They are aimed at sharing data between federations of simulations.
Cyber‐specific training is currently intended to assure that operators can recover from a cyberattack. The models used are often attack models, with the systems holding no representation of the associated defense models. As a consequence, although cyber ranges use metrics to measure defensive capabilities, these only reflect how successfully a network is defended. They do not reflect whether the relevant countermeasures were successful in preventing attackers from attaining their objectives. Part of this will depend on whether the affected non‐cyber personnel were aware of the appropriate and proportionate reactions – and behaved accordingly.
5.3.1 Simulation Interoperability Standards Organization (SISO) Standards
This section is not a comprehensive review of SISO standards but gives a brief overview of those deemed to be of most interest in the cyber context.
5.3.1.1 C2SIM: Command and Control Systems – Simulation Systems Interoperation
The C2SIM Product Development Group (PDG) and Product Support Group (PSG) are an evolution of SISO groups that developed the Standard for Military Scenario Definition Language SISO‐STD‐007‐2008 (MSDL) (SISO‐STD‐007‐2008) and SISO‐STD‐011‐2014 Standard for Coalition Battle Management Language (C‐BML) Phase 1 (SISO‐STD‐011‐2014). MSDL is a standardized XML‐based language that enables the sharing of scenario data between synthetic environments and the C4I elements of a simulation. C‐BML is an XML‐based language to express commanders’ intent, and is structured in such a way that it can send commands and receive reports across a combination of command and control (C2) systems, live virtual and constructive (LVC) M&S systems, and autonomous systems. It is primarily focused on simulations running at Levels 4 and5 of the Tolk model.
The C2 element of C2SIM gives it the potential to support the representation of a cyberattack. Not only could it highlight when a degradation of communication might be an indicator of possible cyberattack but could also facilitate the representation of the impact of packets failing to arrive, or packet interception with dissemination of false information and spurious commands arising from their subsequent onward transmission. Current standards are challenged to make specific provision for such a representation of the impact of a cyberattack. The implementation of this is likely to be a complex task, probably needing cyber components to be mapped to missions, and will need to be addressed from the dual perspective of both of mission SA, and of Course of Action analysis.
5.3.1.2 DSEEP: IEEE Standard 1730‐210™ (IEEE Recommended Practice for Distributed Simulation Engineering and Execution Process) (IEEE Std 1730‐2010)
The DSEEP process was developed and is maintained by SISO. It defines a seven‐step process that can be deconstructed into component tasks and activities that set out best practice for the design, development, integration, and testing of simulation environments. The normal diagrammatic representation shows seven sequential steps running from the definition of objectives through to the final stage of after‐action review and analysis of results. In practice, the development sequence follows an iterative spiral model rather than a waterfall model, with any given stage in the process having the potential to generate a need to revisit and adjust the outputs of earlier stages.
In traditional exercises, the level of abstraction at which many simulations operate means that the impact (rather than the reality) of a cyberattack needs to be represented. These impacts, such as loss of power, are often no different to the effects experienced from a traditional, kinetic attack. Therefore, many of these effects can already be represented in simulations and the use of DSEEP would help to integrate a representation of cyber into the more traditional scenarios.
A number of overlays exist to tailor DSEEP for specific circumstances, but the process currently makes no specific provision for cyber. The DSEEP documentation sets out a detailed product flow for each of the seven steps, breaking them down into component activities. Subsequent sections provide more detail about each activity, suggesting inputs, recommended tasks, and outcomes. Existing overlays outline where their activities are identical with the baseline DSEEP and offer guidance about how to manage differences between the overlay and the generic DSEEP activity descriptions. An overlay for cyber that did this would facilitate the integration of the representation of a cyberattack into mission rehearsal and training exercises for non‐cyber military personnel.
5.3.1.3 DIS: IEEE Standard 1278™ Series, “IEEE Standard for Distributed Interactive Simulation” (DIS) (IEEE Std 1278 Series)
The NATO Allied Modeling & Simulation Standards Profile (AMSP) (NATO 2015) states that “DIS is a protocol for linking simulations of various types at multiple locations to create realistic, complex, virtual worlds for the simulation of highly interactive activities.” An important attribute of this standard is that it facilitates interoperability between systems designed to achieve different objectives, with structures, format, and language suited to their own objectives. Exercises using DIS are intended to support a mixture of virtual entities with computer‐controlled behavior (CGFs), virtual entities with live operators (human‐in‐the‐loop simulators), live entities (operational platforms and test and evaluation systems), and constructive entities (war games and other automated simulations).
Federations using DIS are relatively simple to establish, but a number of factors make it unlikely to be the best base architecture for the large mission rehearsal and training simulations used in training C4O personnel. However, many legacy systems, and some systems from other nations – including many cyber tools and ranges – have been designed to operate using DIS. This should not be seen as an insuperable barrier to their inclusion in the larger exercises, as a suitable gateway can be used to connect them with one or more cyber effects models similar to those suggested by the COATS project.
5.3.1.4 HLA‐E: IEEE Std 1516™, High‐Level Architecture for M&S (HLA) (IEEE Std 1516)
The AMSP (NATO 2015) states that HLA‐E “was developed to provide a common technical architecture that facilitates the reuse and interoperation of simulation systems and assets. It provides a general framework within which developers can structure and describe their simulation systems and/or assets and interoperate with other simulation systems and assets.” Each federation agreement uses a Federation Object Model (FOM) to specify the information to be exchanged by federates at run time. This defines the couplings that will take place between federates allowing participants to know what data they can expect to receive, and the format of the data. For a federation to include a specific representation of cyber, a FOM would need to include descriptions of the disruption a cyberattack would cause to the interactions within the simulation.
One well‐known example of a FOM is the NATO NETN (NATO Education and Training Network) FOM. This takes a modular approach to defining the interactions, one module dealing with those between the C2 and the simulation. This could potentially be extended to facilitate a representation of the impact of a cyberattack in C4O simulations. At this stage it is not possible to ascertain whether there is a need for a separate cyber‐specific FOM.
5.3.2 Cyber Standards
In contrast to the SISO standards, cyber standards (Levels 1–3 of the Tolk model) are aimed at ensuring the secure transmission of data packets between network nodes, and the protection of a network from unauthorized activity, including the introduction of threat vectors. Figure 5.3 illustrates how different controls and countermeasures are appropriate to the different points along the attack path, and – should these not be addressed – the potential consequences, with the effects of those consequences.

Figure 5.3 Cyber “Bow‐Tie” – Prevention, Attack, and Remediation
Although Figure 5.3’s ‘Bow‐Tie’ is a cyber construct, it has a wider application within the context of this section, as it shows how differing but equally valid interpretations are possible at both the cyber and simulation levels. A seamless progression in the representation of cyber as we move through the levels of the Tolk model may well be possible, provided there is a clear understanding of the context and objectives of what needs to be represented for events at each level. At the cyber level, the event represents an attack entering a network, with the effects and consequences being those manifested at the network level. In the context of simulations used for mission rehearsal and training, the event would be the compromise of a network (irrespective of the cause) with the effects and consequences highlighted being those on the mission rather than on the network. This would make the Bow‐Tie a powerful enabler for a dialogue about cyber tools and their possible contribution to situational awareness.
In addition to leveraging threat information standards, the cyber domain uses them to help manage both pre‐event sanitization and post‐event remediation. For example, each of the SANS 20 Controls is designed to provide automatic, machine programmable approaches to respond to cyber threats. Their stated goal is to “protect critical assets, infrastructure, and information by strengthening your organization's defensive posture through continuous, automated protection and monitoring of your sensitive information technology infrastructure to reduce compromises, minimize the need for recovery efforts, and lower associated costs.” These are paralleled in Australia by the Australian Signal Directorate’s “Top 4” preventive techniques, said to prevent 85% of attacks. In addition, the Security Content Automation Protocol (SCAP) includes specifications for organizing and expressing security‐related information in standardized ways, as well as related reference data such as unique identifiers for vulnerabilities:
- Languages:
- Asset Reporting Format (ARF)
- Open Checklist Interactive Language (OCIL)
- Open Checklist Reporting language (OCRL)
- Measures:
- Common Configuration Scoring System (CCSS)
- Common Misuse Scoring System (CMSS)
SCAP affiliations include:
- Languages: XSCCDF, OVAL
- Enumerations:
- Common Configuration Enumeration (CCE)
- Common Platform Enumeration (CPE)
- Common Vulnerabilities and Exposures (CVE)
- Common Attack Pattern Enumerations and Classifications (CAPEC)
- Measures: (CVSS)
In addition, standards currently used to facilitate cyber simulation include:
- RFC 5070
- STIX™
- 8500.01
- NIST SCAP
- NATO NISP
- STANAG 4631, 5067
- IO PDU from the IEEE Std 1278™ series, “IEEE Standard for Distributed Interactive Simulation” (DIS)
The heavy reliance on standards of cyber ranges makes them a natural fit for cyber modeling and simulation. Also, while Logical Ranges (Damodaran and Couretas 2015) (multiple federated ranges) show promise for Levels 2 through 6 of Tolk’s model, the continued development of formal standards will help the training community to adopt this concept in a coherent and coordinated way.
Within the cyber community, standards that result in ranges and other cyber tools sharing data are emerging, but are not yet in general use. The NATO Allied Modeling & Simulation Standards Profile (AMSP) makes no reference to the network level standards most commonly used by cyber tools. The OASIS standards (OASIS) show that the cyber community is starting to consider interoperability issues, although this is still in the early stages. However, these standards appear to have evolved without the objective of integration with SISO standards and make no reference to them. In turn, the SISO standards currently have no specific provision for the inclusion of a cyber element in a simulation.
5.4 Conclusions
In order to achieve true all‐round cyber SA, the information from cyber tools and ranges needs to be exploitable by other cyber tools and ranges, as well as by the simulations used in mission rehearsal and training exercises for C4O (non‐cyber specialists). The previous sections have shown how, although tools in each category might comply with the standards used with in its own area, it is unusual for their design to include provision for interoperability outside their own domain.
Benefits that could be derived from the consistent introduction (and use) of standards to achieve interoperability between the two sides of the equation include:
- Improved general cyber awareness across cyber and non‐cyber military personnel alike.
- Improved awareness among non‐cyber military personnel of how to recognize a potential cyberattack, and of how to respond to such an event appropriately and proportionately.
- Improved awareness of the potential impact of a cyberattack on an operational mission – for cyber and non‐cyber personnel alike.
- An improved ability to conduct “What If” and Course of Action analyses on scenarios that include a cyber element.
- Improved awareness among cyber personnel of the potential for their activities to enhance non‐cyber mission rehearsal and training exercises.
The interoperability question is not confined to technology tools, but extends to the vocabulary used by C4O and C4C personnel. Different interpretation of words that are at first sight common between the communities can have an unexpected on situational awareness. A common, standardized language would help to reduce misunderstandings, and lead to an improved common understanding and situational awareness. Enhanced mutual awareness of these respective standards increases the likelihood that tools in both areas would be designed and used bearing in mind interoperability with the others.
5.5 Questions
- 1 What advantages will standards for cyber M&S provide?
- 2 Why is the C4C/C4O differentiation important for cyber M&S?
- 3 What cyber information types is Tolk’s Hierarchy best suited for?
- 4 How do attack models translate between the training and testing domains?
