This chapter discusses network architecture framework and design models. It covers the following topics:
This chapter introduces converged networks and the variety of traffic within them. To accommodate the requirements of such networks, Cisco has introduced the Intelligent Information Network (IIN) strategy along with the Service-Oriented Network Architecture (SONA) framework that guides the evolution of enterprise networks toward an IIN, both of which this chapter describes.
The components of the Cisco enterprise-wide systems architecture are introduced. Two network design models—the traditional hierarchical network model and the Enterprise Composite Network Model are described. The chapter concludes with a discussion of how routing protocols fit within the Enterprise Composite Network Model.
A converged network is one in which data, voice, and video traffic coexists on a single network. When voice and video are transported across a network, the voice and video are seen by the network as being just like any other application data.
Converged networks contain a variety of different types of traffic, including the following:
Voice and video traffic—. Examples include IP telephony, involving applications such as contact centers, and video broadcast and conferencing.
Mission-critical traffic—. This data is generated by applications critical to an organization (for example, information generated by a stock exchange application at a finance company, patient records at a hospital, and so forth).
Transactional traffic—. This information is generated by applications such as those for e-commerce.
Routing protocol traffic—. Data from whichever routing protocols are running in the network, such as the Routing Information Protocol (RIP), Open Shortest Path First Protocol (OSPF), Enhanced Interior Gateway Routing Protocol (EIGRP), Intermediate System-to-Intermediate System Protocol (IS-IS), and Border Gateway Protocol (BGP).
Network management traffic—. Including information about the status of the network and its devices.
The requirements on the network differ significantly depending on the mix of traffic types, especially in terms of security and performance.
For example, voice and video performance requirements include low delay and jitter (variation in delay), whereas transactional traffic requires high reliability and security with relatively low bandwidth. Voice applications, such as IP telephony, also require high reliability and availability because user expectations for “dial tone” in an IP network are exactly the same as in the traditional telephone network. Video traffic is frequently carried as IP multicast traffic, requiring multicast features to be enabled on the network. To meet these traffic requirements, converged networks use quality of service (QoS) mechanisms so that, for example, voice and video traffic are given priority over web-based traffic.
Several security strategies, such as device hardening with strict access control and authentication, intrusion protection, intrusion detection, and traffic protection with encryption, can minimize or possibly eliminate network security threats. Security is a key issue in all networks and becomes even more important in wireless networks where access is possible virtually anywhere.
To accommodate today’s and tomorrow’s network requirements, the Cisco vision of the future includes the IIN, a strategy that addresses how the network is integrated with businesses and business priorities. The IIN encompasses the following features:
Integration of networked resources and information assets that have been largely unlinked—. The modern converged networks with integrated voice, video, and data require that IT departments (and other departments that were traditionally responsible for other technologies) more closely link the IT infrastructure with the network.
Intelligence across multiple products and infrastructure layers—. The intelligence built in to each component of the network is extended network-wide and applies end to end.
Active participation of the network in the delivery of services and applications—. With added intelligence, the IIN makes it possible for the network to actively manage, monitor, and optimize service and application delivery across the entire IT environment.
The IIN offers much more than basic connectivity, bandwidth for users, and access to applications—it offers an end-to-end functionality and centralized, unified control that promotes true business transparency and agility.
With the IIN, Cisco is helping organizations to address new IT challenges, such as the deployment of service-oriented architectures, web services, and virtualization (as described in the upcoming “Phase 2” bullet). The IIN technology vision offers an evolutionary approach that consists of three phases in which functionality can be added to the infrastructure as required. The three phases are as follows:
Phase 1:Integrated transport—. Everything (data, voice, and video) consolidates onto an IP network for secure network convergence. By integrating data, voice, and video transport into a single, standards-based, modular network, organizations can simplify network management and generate enterprise-wide efficiencies. Network convergence also lays the foundation for a new class of IP-enabled applications, now known as Cisco Unified Communications solutions.
Note
Cisco Unified Communications is the name, launched in March 2006, for the entire range of what were previously known as Cisco IP communications products. These include all call control, conferencing, voicemail and messaging, customer contact, IP phone, video telephony, videoconferencing, rich media clients, and voice application products.
Phase 2: Integrated services—. When the network infrastructure is converged, IT resources can be pooled and shared, or virtualized, to flexibly address the changing needs of the organization. By extending this virtualization concept to encompass server, storage, and network elements, an organization can transparently use all of its resources more efficiently. Business continuity is also enhanced because in the event of a local systems failure, shared resources across the IIN can provide needed services.
Phase 3: Integrated applications—. This phase focuses on making the network application aware so that it can optimize application performance and more efficiently deliver networked applications to users. With Application-Oriented Networking (AON) technology, Cisco has entered this third IIN phase. In addition to capabilities such as content caching, load balancing, and application-level security, the Cisco AON makes it possible for the network to simplify the application infrastructure by integrating intelligent application message handling, optimization, and security into the existing network.
Note
You can access the IIN home page at http://www.cisco.com/go/iin.
The Cisco SONA is an architectural framework that illustrates how to build integrated systems and guides the evolution of enterprise networks toward an IIN. Using the SONA framework, enterprises can improve flexibility and increase efficiency by optimizing applications, business processes, and resources to enable IT to have a greater impact on business.
The SONA framework leverages the extensive product-line services, proven architectures, and experience of Cisco and its partners to help enterprises achieve their business goals.
The SONA framework, shown in Figure 1-1, shows how integrated systems can allow a dynamic, flexible architecture and provide for operational efficiency through standardization and virtualization. In this framework, the network is the common element that connects and enables all components of the IT infrastructure.
The SONA framework outlines the following three layers:
Networked infrastructure layer—. Where all the IT resources are interconnected across a converged network foundation. The IT resources include servers, storage, and clients. The network infrastructure layer represents how these resources exist in different places in the network, including the campus, branch, data center, wide-area network (WAN), metropolitan-area network (MAN), and with the teleworker. The objective of this layer is to provide connectivity, anywhere and anytime.
Interactive services layer—. Enables efficient allocation of resources to applications and business processes delivered through the networked infrastructure. This layer comprises these services:
Application layer—. This layer includes business applications and collaboration applications. The objective of this layer is to meet business requirements and achieve efficiencies by leveraging the interactive services layer.
Note
You can access the SONA home page at http://www.cisco.com/go/sona.
Cisco provides an enterprise-wide systems architecture that helps companies to protect, optimize, and grow the infrastructure that supports their business processes. As illustrated in Figure 1-2, the architecture provides for integration of the entire network—campus, data center, branches, teleworkers, and WAN—offering staff secure access to the tools, processes, and services they require.
The Cisco Enterprise Campus Architecture combines a core infrastructure of intelligent switching and routing with tightly integrated productivity-enhancing technologies, including IP communications, mobility, and advanced security. The architecture provides the enterprise with high availability through a resilient multilayer design, redundant hardware and software features, and automatic procedures for reconfiguring network paths when failures occur. IP multicast capabilities provide optimized bandwidth consumption, and QoS features ensure that real-time traffic (such as voice, video, or critical data) is not dropped or delayed. Integrated security protects against and mitigates the impact of worms, viruses, and other attacks on the network, including at the switch port level. For example, the Cisco enterprise-wide architecture extends support for security standards, such as the Institute for Electrical and Electronic Engineers (IEEE) 802.1x port-based network access control standard and the Extensible Authentication Protocol (EAP). It also provides the flexibility to add IPsec and Multiprotocol Label Switching virtual private networks (MPLS VPNs), identity and access management, and virtual local-area networks (VLANs) to compartmentalize access. These features help improve performance and security while decreasing costs.
The Cisco Enterprise Data Center Architecture is a cohesive, adaptive network architecture that supports requirements for consolidation, business continuance, and security while enabling emerging service-oriented architectures, virtualization, and on-demand computing. Staff, suppliers, or customers can be provided with secure access to applications and resources, simplifying and streamlining management and significantly reducing overhead. Redundant data centers provide backup using synchronous and asynchronous data and application replication. The network and devices offer server and application load balancing to maximize performance. This architecture allows the enterprise to scale without major changes to the infrastructure.
The Cisco Enterprise Branch Architecture allows enterprises to extend head-office applications and services (such as security, IP communications, and advanced application performance) to thousands of remote locations and users or to a small group of branches. Cisco integrates security, switching, network analysis, caching, and converged voice and video services into a series of integrated services routers (ISRs) in the branch so that the enterprises can deploy new services without buying new routers. This architecture provides secure access to voice, mission-critical data, and video applications—anywhere, anytime. Advanced routing, VPNs, redundant WAN links, application content caching, and local IP telephony call processing features are available with high levels of resilience for all the branch offices. An optimized network leverages the WAN and LAN to reduce traffic and save bandwidth and operational expenses. The enterprise can easily support branch offices with the ability to centrally configure, monitor, and manage devices located at remote sites, including tools, such as AutoQoS, which configures devices to handle congestion and bandwidth issues before they affect network performance.
The Cisco Enterprise Teleworker Architecture allows enterprises to securely deliver voice and data services to remote small or home offices over a standard broadband access service, providing a business-resiliency solution for the enterprise and a flexible work environment for employees. Centralized management minimizes the IT support costs. Integrated security and identity-based networking services enable the enterprise to extend campus security policies to the teleworker. Staff can securely log in to the network over an always-on VPN and gain access to authorized applications and services from a single cost-effective platform. Productivity can further be enhanced by adding an IP phone, thereby providing cost-effective access to a centralized IP communications system with voice and unified messaging services.
The Cisco Enterprise WAN Architecture offers the convergence of voice, video, and data services over a single Cisco Unified Communications network, which enables the enterprise to cost-effectively span large geographic areas. QoS, granular service levels, and comprehensive encryption options help ensure the secure delivery of high-quality corporate voice, video, and data resources to all corporate sites, enabling staff to work productively and efficiently wherever they are located. Security is provided with multiservice VPNs (IPsec and MPLS) over Layer 2 or Layer 3 WANs, hub-and-spoke, or full-mesh topologies.
Traditionally, the three-layer hierarchical model has been used in network design, providing a modular framework that allows design flexibility and facilitates implementation and troubleshooting. The hierarchical model divides networks or modular blocks within a network into the access, distribution, and core layers, as illustrated in Figure 1-3. The features of the hierarchical layers are as follows:
Access layer—. This layer is used to grant users access to network devices. In a network campus, the access layer generally incorporates switched LAN devices with ports that provide connectivity to workstations and servers. In the WAN environment, the access layer at remote sites or at teleworkers’ homes provides access to the corporate network across various WAN technologies.
Distribution layer—. This layer aggregates the wiring closets and uses switches to segment workgroups and isolate network problems in a campus environment. Similarly, the distribution layer aggregates WAN connections at the edge of the campus and provides policy-based connectivity (in other words, it implements the organization’s policies).
Core layer (also referred to as the backbone)—. The core layer is a high-speed backbone and is designed to switch packets as fast as possible. Because the core is critical for connectivity, it must provide a high level of availability and adapt to changes quickly.
The hierarchical model can be applied to networks that include any type of connectivity, such as LANs, WANs, wireless LANs (WLANs), MANs, and VPNs. For example, Figure 1-4 demonstrates the hierarchical model applied to a WAN environment.
The hierarchical model is useful for smaller networks, but does not scale well to today’s larger, more complex networks. The Enterprise Composite Network Model, introduced in the following section, provides additional modularity and functionality.
Cisco has developed a set of best practices for security, comprising a blueprint for network designers and administrators for the proper deployment of security solutions to support network applications and the existing network infrastructure. This blueprint is called “SAFE.” SAFE includes the Enterprise Composite Network Model, which network professionals can use to describe and analyze any modern enterprise network. This model supports larger networks than those designed with only the hierarchical model and clarifies the functional boundaries within the network.
Note
You can access the SAFE blueprint home page at http://www.cisco.com/go/safe.
The Enterprise Composite Network Model first divides the network into three functional areas, as illustrated in Figure 1-5 and described as follows:
Enterprise Campus—. This functional area contains the modules required to build a hierarchical, highly robust campus network. Access, distribution, and core principles are applied to these modules appropriately.
Enterprise Edge—. This functional area aggregates connectivity from the various elements at the edge of the enterprise network, including to remote locations, the Internet, and remote users.
Service Provider Edge—. This area is not implemented by the organization; instead, it is included to represent connectivity to service providers such as Internet service providers (ISPs), WAN providers, and the public switched telephone network (PSTN).
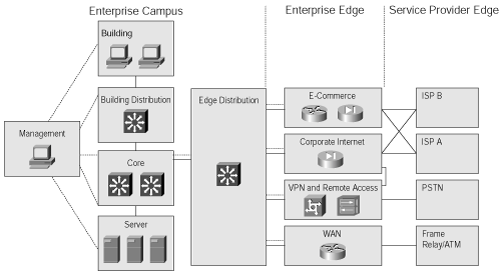
As illustrated in Figure 1-6, each of these functional areas contains various network modules. These modules can in turn include hierarchical core, distribution, and access layer functionality.
The Enterprise Campus functional area comprises the following modules:
Building—. Containing access switches and end-user devices (including PCs and IP phones).
Building Distribution—. Includes distribution multilayer switches to provide access between workgroups and to the Core.
Core—. Also called the backbone, provides a high-speed connection between buildings themselves, and between buildings and the Server and Edge Distribution modules.
Edge Distribution—. The interface between the Enterprise Campus and the Enterprise Edge functional areas. This module concentrates connectivity to and from all branches and teleworkers accessing the campus via a WAN or the Internet.
Server—. Represents the campus’s data center.
Management—. Represents the network management functionality, including monitoring, logging, security, and other management features within an enterprise.
Figure 1-7 illustrates how the Building, Building Distribution, and Core modules map directly onto the hierarchical model’s access, distribution, and core layers. The figure also shows how multiple buildings can be represented by multiple sets of a Building and a Building Distribution module, with each connected to the Core.
The Enterprise Edge functional area is the interface between the Enterprise Campus functional area (through the Edge Distribution module) and the Service Provider Edge functional area. It is composed of the following four modules:
E-commerce—. Includes the servers, network devices, and so forth necessary for an organization to provide e-commerce functionality, such as online ordering
Corporate Internet—. Provides Internet access for the organization, and passes VPN traffic from external users to the VPN and Remote Access module
VPN and Remote Access—. Terminates VPN traffic and dial-in connections from external users
WAN—. Provides connectivity from remote sites using various WAN technologies
The three modules within the Service Provider Edge functional area are as follows:
ISP—. Represents Internet connections
PSTN—. Represents all nonpermanent connections, including via analog phone, cellular phone, and Integrated Services Digital Network (ISDN)
Frame Relay/Asynchronous Transfer Mode (ATM)—. Represents all permanent connections to remote locations, including via Frame Relay, ATM, leased lines, cable, digital subscriber line (DSL), and wireless
Routing protocols are an integral part of any network. When designing a network using the architectures and models introduced in this chapter, routing protocol selection and planning are among the design decisions to be made. Although the best practice is to use one IP routing protocol throughout the enterprise if possible, in many cases multiple routing protocols might be required, as illustrated in Figure 1-8. For example, BGP might be used in the Corporate Internet module, whereas static routes are often used for remote-access and VPN users. Therefore, enterprises might have to deal with multiple routing protocols.
The Enterprise Composite Network Model can assist in determining where each routing protocol is implemented, where the boundaries between protocols are, and how traffic flows between them will be managed.
Each routing protocol has its own unique characteristics, some of which Table 1-1 identifies. The next part of this book, Part II, focuses on the characteristics, operation, and configuration of IP routing protocols.
Table 1-1. Routing Protocol Comparison
Parameters | EIGRP | OSPF | IS-IS |
|---|---|---|---|
Size of network (small-medium-large-very large) | Large | Large | Very large |
Speed of convergence (very high-high-medium-low) | Very high | High | High |
Use of VLSM (yes-no) | Yes | Yes | Yes |
Support for mixed-vendor devices (yes-no) | No | Yes | Yes |
Network support staff knowledge (good, fair, poor) | Good | Good | Fair |
In this chapter, you learned about converged networks and network architecture frameworks and design models. The IIN strategy and the SONA framework that guides enterprises toward an IIN were described. The components of the Cisco enterprise-wide systems architecture were explored, and the traditional hierarchical network model was introduced. The Enterprise Composite Network Model was described, along with how routing protocols fit within this model.
Answer the following questions, and then refer to Appendix A, “Answers to Review Questions,” for the answers.