This chapter introduces the Intermediate System-Intermediate System (IS-IS) protocol and covers the following topics:
This chapter provides an overview of the Integrated Intermediate System-to-Intermediate System (IS-IS) protocol, including its operation and configuration. The IS-IS protocol is a part of the Open System Interconnection (OSI) suite of protocols. The OSI suite uses Connectionless Network Service (CLNS) to provide connectionless delivery of data, and the actual Layer 3 protocol is Connectionless Network Protocol (CLNP). CLNP is the solution for “unreliable” (connectionless) delivery of data, similar to IP. IS-IS uses CLNS addresses to identify the routers and build the link-state database (LSDB).
IS-IS operates in strictly CLNS terms; however, Integrated IS-IS supports IP routing and CLNS. CLNS addresses are required to configure and troubleshoot Integrated IS-IS, even when it is used only for IP. IS-IS supports different data-link environments, such as Ethernet and Frame Relay.
IS-IS supports the most important characteristics of the Open Shortest Path First (OSPF) and Enhanced Interior Gateway Routing Protocol (EIGRP) routing protocols, because it supports variable-length subnet masking (VLSM) and converges quickly. Each protocol has advantages and disadvantages, but this commonality makes any of the three scalable and appropriate for supporting today’s large-scale networks.
Integrated IS-IS is a proven and extensible IP routing protocol that converges quickly and supports VLSM. IS-IS is a public standard, originally published as ISO 9542 and republished as Requests For Comments (RFC) 995, End System to Intermediate System Routing Exchange Protocol. Integrated IS-IS (or dual IS-IS) is specified in RFC 1195, Use of OSI IS-IS for routing in TCP/IP and dual environments, and offers support for IP and OSI protocols. Although not as common, Integrated IS-IS is comparable to, and in some cases preferable to, OSPF. This section describes IS-IS and Integrated IS-IS routing and compares Integrated IS-IS with OSPF. It also explores some of the concepts necessary to develop an understanding of Integrated IS-IS.
IS-IS is a popular IP routing protocol in the Internet service provider (ISP) industry. The simplicity and stability of IS-IS make it robust in large internetworks. IS-IS is found in large ISPs and in some networks that support OSI protocols.
IS-IS development began before OSPF development. Large ISPs chose IS-IS because of their unique requirement for scalability, convergence, and stability. The U.S. government also required support for OSI protocols in the early Internet. Although this requirement was later dropped, IS-IS met both constraints.
Later, businesses typically chose OSPF because it was a more widely supported native IP protocol. Today it is harder to find information and expertise on IS-IS than it is for OSPF. However, some of the largest networks in the world still persist with IS-IS, which is a tribute to its capabilities.
ISO specifications call routers “intermediate systems” (ISs). Thus, IS-IS is a protocol that allows routers to communicate with other routers.
Key Point: OSI Suite Protocols
The OSI suite uses CLNS to provide connectionless delivery of data.
The actual Layer 3 protocol is CLNP, which provides connectionless delivery of data, similar to what IP does for the TCP/IP suite.
The IS-IS routing protocol uses CLNS addresses to identify the routers and to build the LSDB. IS-IS serves as an Interior Gateway Protocol (IGP) for the CLNS.
IS-IS is the dynamic link-state routing protocol for the OSI protocol stack. It distributes routing information for routing CLNP data for the ISO CLNS environment.
IS-IS operates similarly to OSPF. IS-IS allows the routing domain to be partitioned into areas. IS-IS routers establish adjacencies using a Hello protocol and exchange link-state information, using link-state packets (LSPs), throughout an area to build the LSDB. Each router then runs Dijkstra’s shortest path first (SPF) algorithm against its LSDB to pick the best paths. There is a minimal amount of information communicated between areas, which reduces the burden on routers supporting the protocol.
IS-IS routing takes place at two levels within an AS: Level 1 (L1) and Level 2 (L2).
L1 routing occurs within an IS-IS area and is responsible for routing to end systems (ESs) and ISs inside an area. All devices in an L1 routing area have the same area address. Routing within an area is accomplished by looking at the locally significant address portion, known as the system ID, and choosing the lowest-cost path.
L2 routing occurs between IS-IS areas. L2 routers learn the locations of L1 routing areas and build an interarea routing table. L2 routers use the destination area address to route traffic using the lowest-cost path.
Key Point: Two IS-IS Routing Levels
IS-IS supports two routing levels:
L1 builds a common topology of system IDs in the local area and routes traffic within the area using the lowest-cost path.
L2 exchanges prefix information (area addresses) between areas and routes traffic to an area using the lowest-cost path.
Key Point: Three Types of IS-IS Routers
To support the two routing levels, IS-IS defines three types of routers, as follows:
L1 routers use LSPs to learn about paths within the areas they connect to (intra-area).
L2 routers use LSPs to learn about paths among areas (interarea).
Level 1/Level 2 (L1/L2) routers learn about paths both within and between areas. L1/L2 routers are equivalent to area border routers (ABRs) in OSPF.
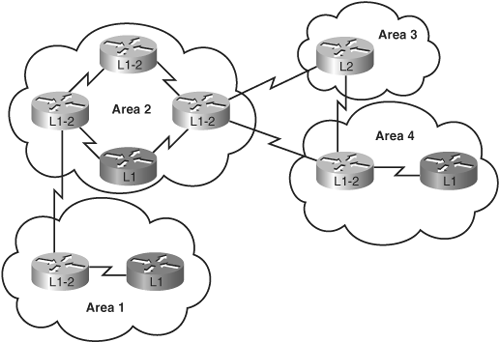
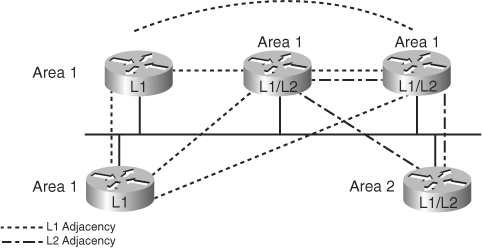
The three types of IS-IS routers are shown in Figure 6-1.
The path of connected L2 and L1/L2 routers is called the backbone. All areas and the backbone must be contiguous.
Integrated IS-IS or dual IS-IS is an implementation of the IS-IS protocol for routing multiple network protocols, IP and CLNS, and is specified in RFC 1195 and ISO 10589.
Integrated IS-IS tags CLNP routes with information about IP networks and subnets. Integrated IS-IS provides IP with an alternative to OSPF and combines ISO CLNS and IP routing in one protocol; it can be used for IP routing, CLNS routing, or for a combination of the two.
Integrated IS-IS uses its own protocol data units (PDUs) to transport information between routers, including IP reachability information. IS-IS information is not carried within a network layer protocol but is instead carried directly within data-link layer frames.
Note
This protocol-independence makes IS-IS easily extensible; there is also a version of Integrated IS-IS that supports IP version 6 (IPv6), as described in Chapter 10, “Implementing IPv6.”
Because IS-IS uses CLNS addresses to identify the routers and to build the LSDB, an understanding of CLNS addresses is required to configure and troubleshoot IS-IS, even when it is used only for routing IP.
Effective networks are well-planned. The first and most important step in building a scalable network is developing a good addressing plan that allows for route summarization. Route summarization is possible only when using a hierarchical addressing structure.
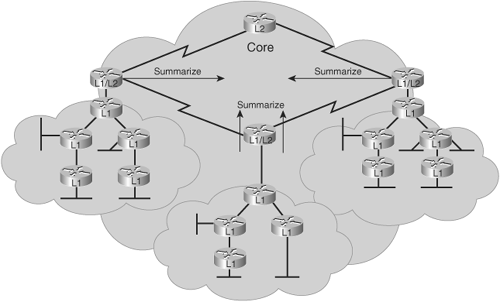
Effective address planning presents opportunities to group devices into areas. Using areas confines the scope of LSP propagation and saves bandwidth. L1/L2 routers, on the border between an L1 area and the L2 backbone, are logical places to implement route summarization, as shown in Figure 6-2.
Route summarization has many benefits. It saves memory because each IS (router) is no longer responsible for the LSPs of the entire routing domain. It also saves CPU usage, because a smaller routing table is easier to maintain. Route summarization also results in a more stable network, because topology changes can be isolated to a small portion of the network, and not propagate throughout; routers in other portions of the network therefore do not have to run the routing algorithm and update their routing tables as often.
One issue with IS-IS is that older implementations default to using narrow metrics, which limit the maximum interface metric to 63 (6 bits) and the maximum total path metric to 1023 (10 bits). This provides little room to distinguish between paths.
Cisco IOS Software, beginning in Release 12.0, supports wide metrics, which allow a 24-bit interface and a 32-bit path metric. The default, however, is still narrow metrics.
Note
Complications can occur if you use wide metrics along with narrow metrics (for example, on older routers or in a multivendor environment).
Another issue is that IS-IS as implemented on Cisco routers does not automatically scale the interface metric. Instead, all IS-IS interfaces have a default metric of 10, as shown in Figure 6-3; this can be changed manually. If the default metric is not adjusted on each interface, the IS-IS metric becomes similar to the hop count metric used by the Routing Information Protocol (RIP).
Hosts in OSI terminology are called end systems. The End System-to-Intermediate System (ES-IS) protocol permits ESs (hosts) and ISs (routers) to discover one another. ES-IS also allows ESs to learn their network layer addresses. ES-IS handles topology information discovery and exchange between ESs and ISs.
ES-IS performs the following tasks:
It identifies the area prefix to ESs.
It creates adjacencies between ESs and ISs.
It creates data link-to-network address mappings.
ESs send End System Hellos (ESHs) to well-known addresses that announce their presence to routers (ISs), as shown in Figure 6-4. Routers listen to ESHs to find the ESs on a segment. Routers include information on ESs in LSPs.
Routers transmit Intermediate System Hellos (ISHs) to well-known addresses, announcing their presence to ESs. ESs listen for these ISHs and randomly pick an IS to which they forward all their packets. When an ES needs to send a packet to another ES, it sends the packet to one of the ISs (routers) on its directly attached network.
Routers use IS-IS Hellos (IIHs) to establish and maintain adjacencies between ISs.
IP end host systems do not use ES-IS. IP has its own processes and applications to handle the same functions as ES-IS, such as Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP), and Dynamic Host Configuration Protocol (DHCP).
Although Integrated IS-IS can support IP exclusively, IS-IS still uses CLNS to transmit reachability information and still forms adjacencies using IIHs.
The OSI specifications discuss four unique types of routing operations, numbered 0 to 3, as shown in Figure 6-5. As discussed earlier, IS-IS is responsible for L1 and L2 OSI routing.
OSI routing begins with ES-IS, when the ESs discover the nearest IS by listening to ISH packets.
When an ES needs to send a packet to another ES, it sends the packet to an IS on an attached network. This process is known as L0 routing.
Each ES and IS resides in a particular area. To pass traffic, the router looks up the destination address and forwards the packet along the best route. If the destination is on the same subnetwork, the IS knows the location (from listening to the ESH) and forwards the packet appropriately. The IS can also provide a redirect message back to the source that tells it that a more direct route is available. If the destination is on a different subnetwork but within the same area, the router identifies the best path, using the system ID, and forwards the traffic appropriately.
If a destination address is in another area, the L1 IS sends the packet to the nearest L1/L2 IS. Packet forwarding continues through L2 and L1/L2 ISs, using the area address, until the packet reaches an L1/L2 IS in the destination area. This process is called L2 routing. Within the destination area, ISs forward the packet along the best path, based on system ID, until the packet reaches the destination.
Routing between separate domains is called L3 routing. L3 routing is comparable to Border Gateway Protocol (BGP) interdomain routing in IP. L3 routing passes traffic between different autonomous systems; these autonomous systems might have different routing logic, so metrics cannot be directly compared. L3 OSI routing is not implemented on Cisco routers but is specified as being accomplished through the Interdomain Routing Protocol (IDRP).
Most of the development of the OSPF and IS-IS protocols was done concurrently. The cooperation and competition between the development groups produced two protocols that are very similar, and each is better because of the other. The practical differences between the two protocols deal with perceived issues of resource usage and customization.
Most debates of the merits of these protocols are colored by their mutual history; different groups with different cultures developed them.
Digital Equipment Corporation (DEC) originally developed IS-IS for DECnet Phase V. In 1987, the American National Standards Institute (ANSI) chose it to be the OSI IGP. At that time it could route only CLNP.
The ISO process is an international standards development process. According to an account given by Christian Huitema in his book Routing in the Internet, groups within ISO and outside the United States did not approve of TCP/IP because of its origin (it was also called the U.S. Department of Defense [DoD] protocol).
From the perspective of ISO, IP development was chaotic and imprecise, based on the famous maxim of “loose consensus and running code.” From the perspective of the early Internet engineers, the ISO process was slow, irritating, and disenfranchising.
In 1988, the U.S. National Science Foundation Network (NSFnet) was created. The IGP used was based on an early draft of IS-IS. The extensions to IS-IS for handling IP were developed in 1988. OSPF development began during this time; it was loosely based on IS-IS.
In 1989, OSPF Version 1 (OSPFv1) was published, and conflict ensued between the proponents of IS-IS and OSPF. The IETF eventually supported both, although it continued to favor OSPF. With the unofficial endorsement of the IETF, OSPF eventually became more popular.
By the mid-1990s, large ISPs in need of an IGP selected IS-IS for two reasons. IS-IS supported IP and CLNS (and therefore solved two problems at once), and OSPF was seen as immature at the time.
IS-IS and OSPF are more similar than dissimilar. Both routing protocols have the following characteristics:
They are open standard link-state routing protocols.
They use similar mechanisms (link-state advertisements [LSAs], link-state aging timers, and link-state database synchronization) to maintain the health of the LSDB.
They use the SPF algorithm, with similar update, decision, and flooding processes.
They are successful in the largest and most-demanding deployments (ISP networks).
They converge quickly after network changes.
The differences between OSPF and Integrate IS-IS are small, but they do exist; these differences are explored in this section.
With OSPF, network design is constrained because OSPF is based on a central backbone, area 0, with all other areas being physically attached to area 0, as shown in Figure 6-6.
The border between OSPF areas is inside the ABRs; each link is in only one area. When you use this type of hierarchical model, you need a consistent IP addressing structure to summarize addresses into the backbone. Summarization also reduces the amount of information carried in the backbone and advertised across the network.
In comparison, IS-IS has a hierarchy of L1, L2/L1, and L2 routers, and the area borders lie on links, as shown in Figure 6-7. IS-IS permits a more flexible approach to extending the backbone. The backbone can be extended by simply adding more L2/L1 or L2 routers, a less-complex process than with OSPF.
OSPF produces many small LSAs, whereas a router groups IS-IS updates and sends them as one LSP. Thus, as network complexity increases, the number of IS-IS updates is not an issue. Each packet must be routed though, and routing takes network resources, so more packets represent a larger impact on the network. Because IS-IS uses significantly fewer LSPs, more routers, at least 1,000, can reside in a single area, making IS-IS more scalable than OSPF.
IS-IS is also more efficient than OSPF in the use of CPU resources and in how it processes routing updates, as shown in Figure 6-8. For one thing, there are fewer LSPs to process (LSAs in OSPF terminology). Also, the mechanism by which IS-IS installs and withdraws prefixes is less resource intensive because it uses network entity title (NET) addresses, which are already summarized. Recall that OSPF runs on top of IP, whereas IS-IS runs through CLNS.
Both OSPF and IS-IS are link-state protocols and thus provide fast convergence. The convergence time depends on a number of factors, such as timers, number of nodes, and type of router. Based on the default timers, IS-IS detects a failure faster than OSPF; therefore, convergence occurs more rapidly. If there are many neighboring routers and adjacencies, the convergence time also might depend on the router’s processing power; IS-IS is less CPU intensive than OSPF.
New ideas are not easily expressed in OSPF packets; they require the creation of a new LSA. The OSPF description schema is difficult to extend, because of compatibility issues, and because it was developed exclusively for IPv4. IS-IS is easy to extend through the Type, Length, and Value (TLV) mechanism. TLV strings, called tuples, encode all IS-IS updates. IS-IS can easily grow to cover IPv6 or any other protocol because extending IS-IS consists of simply creating new type codes.
An organization might choose OSPF over IS-IS because OSPF is more optimized and was designed exclusively as an IP routing protocol. For example, OSPF defines different area types (standard, stub, and not-so-stubby [NSSA]). On Cisco routers the default OSPF metric is related to the interface bandwidth, whereas IS-IS defaults to a metric of 10 on all interfaces.
If an organization does choose OSPF, it will require networking equipment that supports OSPF, and network engineers that are familiar with OSPF theory and operation. It is relatively easy to find both equipment and personnel to support an OSPF infrastructure. Furthermore, OSPF documentation is much more readily available than documentation for IS-IS.
Table 6-1 summarizes the differences between OSPF and Integrated IS-IS.
Table 6-1. Summary of Differences Between OSPF and Integrated IS-IS
OSPF | Integrated IS-IS |
|---|---|
Area border inside routers (ABRs) | Area border on links |
Each link in only 1 area | Each router in only 1 area |
More complex to extend backbone | Simple extension of backbone |
Many small LSAs sent | Fewer LSPs sent |
Runs on top of IP | Runs on top of data-link layer |
Requires IP addresses | Requires IP and CLNS addresses |
Default metric is scaled by interface bandwidth | Default metric is 10 for all interfaces |
Not easy to extend | Easy to support new protocols with new TLV tuples |
Equipment, personnel, and information more readily available | Equipment, personnel, and information not as readily available |
Key Point: CLNS Addresses Required Even if Routing Only for IP
Unlike IP addresses, CLNS addresses apply to entire nodes and not to interfaces. Because IS-IS was originally designed for CLNS, IS-IS requires CLNS node addresses even if the router is used for routing only IP.
CLNS addresses that are used by routers are called network service access points (NSAPs). One part of an NSAP address is the NSAP selector (NSEL) byte. When an NSAP is specified with an NSEL of 0, the NSAP is called the network entity title (NET).
This section starts by describing NSAP and NET addresses for use with Integrated IS-IS. The section then describes how CLNS addressing affects IS-IS operation and how the IS-IS protocol learns the network topology, makes routing decisions, and handles different types of data links.
IS-IS LSPs use NSAP addresses to identify the router and build the topology table and the underlying IS-IS routing tree; therefore, IS-IS requires NSAP addresses to function properly, even if it is used only for routing IP.
NSAP addresses contain the following:
The device’s OSI address
A link to the higher-layer process
The NSAP address is equivalent to the combination of the IP address and upper-layer protocol in an IP header.
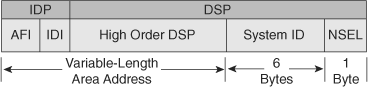
NSAP addresses have a maximum size of 20 bytes. Various uses require definition of different address structures; the high-order bits identify the interarea structure, and the low-order bits identify unique systems within an area (intra-area).
Key Point: NSAP Address Structure
The Cisco implementation of Integrated IS-IS divides the NSAP address into three fields: the area address, the system ID, and the NSEL.
The NSAP address structure is shown in Figure 6-9.
Cisco routers routing CLNS use addressing that conforms to the ISO 10589 standard. ISO NSAP addresses consist of the following:
The authority and format identifier (AFI) and the initial domain identifier (IDI) make up the initial domain part (IDP) of the NSAP address. The IDP corresponds roughly to an IP classful major network.
The AFI byte specifies the format of the address and the authority that assigned that address. Some valid values are shown in Table 6-2.
Addresses starting with the AFI value of 49 are private addresses, analogous to RFC 1918 for IP addresses. IS-IS routes these addresses; however, this group of addresses should not be advertised to other CLNS networks because they are ad hoc addresses. Other companies that use a value of 49 may have created different numbering schemes that, when used together, could create confusion.
The IDI identifies a subdomain under the AFI. For instance, 47.0005 is assigned to civilian departments of the U.S. Government and 47.0006 to the U.S. Department of Defense.
The domain-specific part (DSP) contributes to routing within an IS-IS routing domain. The DSP is comprised of the high-order domain-specific part (HODSP), the system ID, and the NSEL.
The HODSP subdivides the domain into areas. The HODSP is more or less the OSI equivalent of a subnet in IP.
The system ID identifies an individual OSI device. In OSI each device has an address, just as it does in DECnet, whereas in IP, each interface has an address.
The NSEL identifies a process on the device and corresponds roughly to a port or socket in IP. The NSEL is not used in routing decisions.
Key Point: NSAP Format
The simplest NSAP format, used by most companies running IS-IS as their IGP, comprises the following:
The area address, which must be at least 1 byte, separated into two parts:
The AFI set to 49, which signifies that the AFI is locally administered and thus individual addresses can be assigned by the company.
The area identifier (ID), the octets of the area address after the AFI.
A system ID. Cisco routers compliant with the U.S. Government OSI Profile (GOSIP) Version 2.0 standard require a 6-byte system ID.
The NSEL, which must always be set to 0 for a router.
The NSAP is called the NET when it has an NSEL of 0. Routers use the NET to identify themselves in the IS-IS PDUs.
For example, you might assign 49.0001.0000.0c12.3456.00, which represents the following:
AFI of 49
Area ID of 0001
System ID of 0000.0c12.3456, the Media Access Control (MAC) address of a LAN interface on the device
NSEL of 0
The first part of an NSAP is the area address and is associated with the IS-IS routing process. Unlike OSPF, an IS-IS router can be a member of only one area, as shown in Figure 6-10.
All routers in an area must use the same area address, which actually defines the area. The area address is used in L2 routing.
ESs recognize only ISs and other ESs on the same subnetwork that share the same area address.
The 6-byte NSAP system ID must be unique within an area. It is customary to use a MAC address from the router as the system ID, as shown in Figure 6-11, or, for Integrated IS-IS, to encode an IP address into the system ID.
All the system IDs in a domain must be of equal length. Cisco enforces this OSI directive by fixing the length of the system ID at 6 bytes in all cases.
Level 1 intra-area routing is based on system IDs; therefore, each ES and IS must have a unique system ID within the area.
All Level 2 ISs eventually recognize all other ISs in the Level 2 backbone; therefore, they must also have unique system IDs.
Thus, system IDs should remain unique across the domain. If the system IDs remain unique, there can never be a conflict at L1 or L2 if, for example, a device moves into a different area.
As discussed earlier, NSAP address have a one octet NSEL field that identifies a process on the device, corresponding roughly to a port number in IP. NET addresses are NSAP addresses with an NSEL value of 0. A NET address is used to uniquely identify an OSI host within an IS-IS routing domain. Because IS-IS originates from the OSI world, NET addresses are required even if the only routed protocol is IP.
The NET refers to the device itself; that is, it is the equivalent of that device’s Layer 3 OSI address.
Routers use the NET to identify themselves in the LSPs and, therefore, form the basis for the OSI routing calculation.
Three additional IS-IS terms related to NET addresses are introduced in Figure 6-12: subnetwork point of attachment (SNPA), circuit ID, and link.
The SNPA is the point that provides subnetwork services. SNPA is the equivalent of the Layer 2 address corresponding to the NET or NSAP address. The SNPA is assigned by using one of the following:
The MAC address on a LAN interface
The virtual circuit ID from X.25 or ATM connections, or the data-link connection identifier (DLCI) from Frame Relay connections
For High-Level Data Link Control (HDLC) interfaces, the SNPA is simply set to “HDLC”
A circuit is the IS-IS term for an interface. Because the NSAP and NET refer to the entire device, a circuit ID is used to distinguish a particular interface. A router assigns a circuit ID (1 octet) to each of its interfaces as follows:
In the case of point-to-point interfaces, the SNPA is the sole identifier for the circuit. For example, on an HDLC point-to-point link, the circuit ID is 0x00.
In the case of LAN interfaces, the circuit ID is tagged to the end of the system ID of the designated IS (DIS) to form a 7-byte LAN ID, for example, 1921.6800.0001.01. On Cisco routers, the router hostname is used instead of the system ID; therefore, the circuit ID of a LAN interface may look like R1.01. (The DIS is described in the “Implementing IS-IS in Broadcast Networks” section later in this chapter.)
A link is the path between two neighbor ISs and is defined as being up when communication is possible between the two neighbor SNPAs.
Recall that IS-IS defines three types of routers as follows:
Level 1—. L1 routers learn about paths within the areas they connect to (intra-area). L1 routers are similar to OSPF internal nonbackbone routers.
Level 2—. L2 routers learn about paths between areas (interarea). L2 routers are similar to OSPF backbone routers.
Level 1-2—. L1/L2 routers learn about paths both within and between areas. L1/L2 routers are equivalent to ABRs in OSPF.
Intra-area (L1) routing enables ESs to communicate. An L1 area is a collection of L1 and L1/L2 routers.
The path of connected L2 and L1/L2 routers is called the backbone. All areas and the backbone must be contiguous.
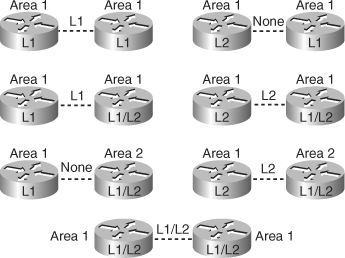
Area boundaries fall on the links. Each IS-IS router belongs to exactly one area. Neighboring routers learn whether they are in the same area or different areas and negotiate appropriate adjacencies, L1, L2, or both.
L1 ISs maintain a copy of the L1 area LSDB. L2 ISs maintain a copy of the L2 area LSDB. Each router keeps a copy of the LSDBs for the levels it is responsible for.
An L1/L2 router automatically advertises to all L1 routers (within its area) that it is a potential exit point of the area. L1 routers will default to the nearest attached L1/L2 router.
IS-IS routing flows naturally from the OSI address plan in which areas are identified and unique system IDs are given to each device.
The area address portion of the NSAP address can range from 1 to 13 bytes in length, as specified by the ISO standard. Therefore, an NSAP for an IS-IS network can be as little as 8 bytes in length; the NSAP is usually longer to permit some granularity in the allocation of areas. The area address is common to all devices in an area and is unique for each area. ISs and ESs are in the same area if they share the same area address.
Routing within an area involves collecting system IDs and adjacencies for all ISs and ESs in an area and using Dijkstra’s algorithm to compute best paths between devices. L1 routers are only aware of the local area topology. They pass the traffic destined outside the area to the closest L1/L2 router.
Routing between areas is based on area address. L2 (or L1/L2) routers in different areas exchange area address information and use Dijkstra’s algorithm to compute best paths between areas. They pass traffic destined to another area to the best L2 or L1/L2 router to reach that specific area.
Key Point: Addressing and Routing
The area address is used to route between areas; the system ID is not considered.
The system ID is used to route within an area; the area address is not considered.
When an ES is required to send a packet to another ES, the packet goes to one of the ISs on a network directly attached to the ES. The router then searches for the destination address and forwards the packet along the best route. If the destination ES is in the same area, the local IS recognizes the location by listening to ESH packets and forwards the packet appropriately; routing is by system ID within the area. If the destination address is an ES in another area, the L1 IS sends the packet to the nearest L1/L2 IS.
The L1/L2 IS routes by area address to other L1/L2 or L2 ISs. Forwarding through L1/L2 or L2 ISs, by area address, continues until the packet reaches an L1/L2 or L2 IS in the destination area. Within the destination area, ISs forward the packet along the best path, routing by system ID, until the destination ES is reached.
Because each router makes its own best-path decisions at every hop along the way, there is a significant chance that paths will not be reciprocal. That is, return traffic can take a different path than the outgoing traffic. For this reason, it is important to know the traffic patterns within your network and tune IS-IS for optimal path selection if necessary.
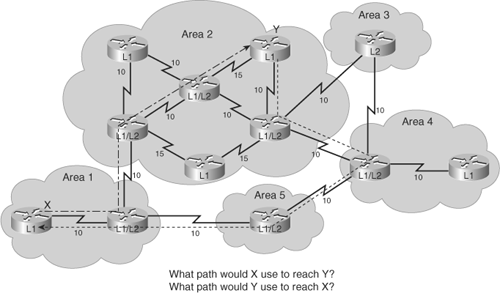
Using Figure 6-13, the following list analyzes traffic from Router 7 (R7) to Router 9 (R9):
R7 recognizes that R9’s prefix (49.00CC) is not the same as R7’s prefix (49.00BB). R7 therefore passes the traffic to the closest L1/L2 router, Router 5 (R5). R7 uses its L1 topology database to find the best path to R5.
R5 uses its L2 topology database to pick the best next hop to reach the prefix 49.00CC: R3. R5 does not use the destination system ID in this decision.
R3 uses its L2 topology database to pick the best next hop to reach the prefix 49.00CC: R1. R3 does not use the destination system ID in this decision.
R1 uses its L2 topology database to pick the best next hop to reach the prefix 49.00CC: R8. R1 does not use the destination system ID in this decision.
R8 recognizes that R9’s prefix (49.00CC) is the same as R8’s prefix (49.00CC). R8 therefore passes the traffic to R9 using its L1 topology database to find the best path.
Figure 6-14 illustrates another example, this time with asymmetric routing. Area 1 contains the following two routers:
One router borders area 2 and area 5; it is an L1/L2 IS.
The other router is contained within the area and is an L1 IS only.
Some of the routers are specified as L1. The routers route either internally to that area or to the exit points (the L1/L2 ISs).
L1/L2 routers form a chain across the area linking to the neighbor areas. Although the middle router of the three L1/L2 routers does not link directly to another area, the middle router must support L2 routing to ensure that the backbone is contiguous. If the middle router fails, the other L1-only routers cannot perform the L2 function (despite providing a physical path across the area), and the backbone is broken.
Note
The lower router in Area 2 in Figure 6-14 could be L1/L2, to provide redundancy.
Area 3 contains one router that borders areas 2 and 4, yet it has no intra-area neighbors and is currently performing L2 functions only. If you add another router to area 3, you should change it to be an L1/L2 IS.
Recall, as shown in Figure 6-14, the border between the areas in an IS-IS network is on the link between L2 routers. (This is in contrast to OSPF, where the border exists inside the ABR itself.)
Key Point: L1 and L2 Are Separate
In IS-IS, asymmetric routing (packets taking different paths in different directions) might occur because L1 and L2 computations are separate. The L2 details are hidden from the L1 routers.
In this example, symmetric routing does not occur because L2 details are hidden from L1 routers, which only recognize a default route to the nearest L1/L2 router. For example, traffic from Router X to Router Y flows from Router X to its closest L1/L2 router. The L1/L2 router then forwards the traffic along the shortest path to the destination area (area 2), where it is routed along the shortest intra-area path to Router Y.
Router Y routes return packets to Router X via its nearest L1/L2 router. The L1/L2 router recognizes the best route to area 1 via area 4 based on the lowest-cost L2 path. Because L1 and L2 computations are separate, the path taken from Router Y back to Router X is not necessarily the least-cost path from Router Y to Router X.
Asymmetric routing is not detrimental to the network. However, troubleshooting can be difficult, and this type of routing is sometimes a symptom of suboptimal design. Like EIGRP and OSPF, a good IS-IS design is generally hierarchical and symmetrical.
Route leaking is a feature available since Cisco IOS Software Release 12.0 that helps avoid asymmetric routing and reduce suboptimal routing by providing a mechanism for leaking, or redistributing, L2 routes into L1 routers in a controlled manner. By having more detail about interarea routes, an L1 router is able to make a better choice with regard to which L1/L2 router to forward the packet.
Route leaking is defined in RFC 2966, Domain-wide Prefix Distribution with Two-Level IS-IS, for use with the narrow metric TLV types 128 and 130. The IETF has also defined route leaking for use with the wide metric (using TLV type 135).
To implement route leaking, an up/down bit in the TLV is used to indicate whether or not the route identified in the TLV has been leaked. If the up/down bit is set to 0 the route was originated within that L1 area. If the up/down bit is set to 1 the route has been redistributed into the area from L2. The up/down bit is used to prevent routing loops: An L1/L2 router does not re-advertise into L2 any L1 routes that have the up/down bit set.
Route leaking should be planned and deployed carefully to avoid the situation where any topology change in one area results in having to recompute many routes in all other areas.
This section describes the OSI PDUs and four types of IS-IS PDUs.
The OSI stack defines a unit of data as a PDU. OSI recognizes a frame as a data-link PDU and a packet (or datagram, in the IP environment) as a network PDU.
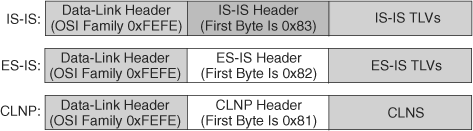
Figure 6-15 shows examples of three types of PDUs (all with IEEE 802.2 Logical Link Control [LLC] encapsulation). IS-IS and ES-IS PDUs are encapsulated directly in a data-link PDU (frame); there is no CLNP header and no IP header. (In other words, IS-IS and ES-IS do not put routing information in IP or CLNP packets; rather, they put routing information directly in a data-link layer frame.) True CLNP (data) packets contain a full CLNP header between the data-link header and any higher-layer CLNS information.
The IS-IS and ES-IS PDUs contain variable-length fields, depending on the function of the PDU. Each field contains a type code, a length, and the appropriate values; this information is known as the TLVs.
Key Point: IS-IS PDUs
As mentioned, IS-IS PDUs are encapsulated directly into an OSI data-link frame. There is no CLNP or IP header.
IS-IS defines the following four types of PDUs:
Hello PDU (ESH, ISH, IIH)—Used to establish and maintain adjacencies
LSP—Used to distribute link-state information
Partial sequence number PDU (PSNP)—Used to acknowledge and request missing pieces of link-state information
Complete sequence number PDU (CSNP)—Used to describe the complete list of LSPs in a router’s LSDB
The Hello PDUs were described earlier in section “The ES-IS Protocol”; IIHs use is further explored later in this chapter in the “Implementing IS-IS in Different Network Types” section. LSPs are described in the next section. PSNPs and CSNPs use is described in the later “Link-State Database Synchronization” section.
In IS-IS, router characteristics are defined by an LSP. A router’s LSP contains an LSP header followed by TLV fields, as shown in Figure 6-16.
An LSP header describes the following:
The PDU type and length
The LSP ID
The LSP sequence number, used to identify duplicate LSPs and to ensure that the latest LSP information is stored in the topology table
The LSP’s remaining lifetime, which is used to age out LSPs
The LSP sequence number allows receiving routers to do the following:
Ensure that they use the latest LSPs in their route calculations
Avoid entering duplicate LSPs in the topology tables
If a router reloads, the sequence number is set to 1. The router then receives its previous LSPs back from its neighbors. These LSPs have the last valid sequence number before the router reloaded. The router records this number and reissues its own LSPs with the next-highest sequence number.
Each LSP has a remaining lifetime that is used by the LSP aging process to ensure the removal of outdated and invalid LSPs from the topology table after a suitable time period. This process uses a decreasing timer and is known as the count-to-zero operation; 1200 seconds is the default start value.
Each LSP includes specific information about networks and stations attached to a router. This information is found in multiple TLV fields that follow the LSP’s common header. The TLV structure is a flexible way to add data to the LSP and an easy mechanism for adding new data fields that might be required in the future.
The TLV variable-length fields contain elements including the following:
The router’s neighbor ISs, which are used to build the map of the network
The router’s neighbor ESs
Authentication information, which is used to secure routing updates
Attached IP subnets (optional, for Integrated IS-IS)
Table 6-3 shows examples of TLVs.
Table 6-3. LSP TLV Examples
TLV | Type Code | Length Field | Value Variable Length |
|---|---|---|---|
Area address | 1 | Area address length + 1 | Area addresses |
Intermediate system neighbors | 2 | Neighbor count + 1 | IS neighbors |
IP internal reachability | 128 | Number of connected IP prefixes | Connected IP prefixes: 4 octet metric, 4 octet prefix, 4 octet mask |
IP external reachability | 130 | Number of redistributed IP prefixes | Redistributed IP prefixes: 4 octet metric, 4 octet prefix, 4 octet mask |
You can find documentation on important TLVs in ISO 10589 and RFC 1195.
Network topologies can be divided into the following two general types:
Point-to-point networks—. Point-to-point links that are either permanently established (leased line, permanent virtual circuit [PVC]) or dynamically established (ISDN, switched virtual circuit [SVC])
Broadcast networks—. Multipoint WAN links or LAN links such as Ethernet, Token Ring, or Fiber Distributed Data Interface (FDDI)
IS-IS supports only the following two media representations for its link states:
Broadcast—. For LANs and multipoint WAN links
Point to point—. For all other media
Key Point: IS-IS Does Not Know About NBMA
IS-IS has no concept of NBMA networks. It is recommended that you use point-to-point links, such as point-to-point subinterfaces, over NBMA networks, such as ATM, Frame Relay, or X.25.
Cisco IOS Software automatically uses broadcast mode for LAN links and multipoint WAN links. It uses point-to-point mode for point-to-point links, such as point-to-point subinterfaces and dialer interfaces.
IS-IS has no specific support for NBMA networks. When implemented in broadcast mode, Cisco IOS Software assumes that the NBMA environment features a full mesh of PVCs. When creating static maps to map the remote IP address to the local DLCI on a Frame Relay interface, you should use the broadcast keyword; this is because broadcast mode uses multicast updates, which will not be sent without this keyword set.
When you use multipoint WAN links such as multipoint Frame Relay interfaces, you must also allow CLNS broadcasts and multicasts. This can be done by using the frame-relay map clns dlci-number broadcast command (in addition to creating the IP maps).
In IS-IS, broadcast networks are LAN interfaces or multipoint WAN interfaces.
Key Point: Use Broadcast Mode Only for LANs
Broadcast mode is recommended for use only on LAN interfaces, although it is also the default for multipoint WANs.
Separate IS-IS adjacencies are established for L1 and L2 processes. If two neighboring routers in the same area run both L1 and L2, they establish two adjacencies, one for each level. The router stores the L1 and L2 adjacencies in separate L1 and L2 adjacency tables. On LANs, routers establish the two adjacencies with specific Layer 1 and Layer 2 IIH PDUs.
Key Point: Adjacencies on a LAN
Routers on a LAN establish adjacencies with all other routers on the LAN (unlike OSPF, where routers establish full adjacencies only with the Designated Router [DR] and Backup Designated Router [BDR]).
IIH PDUs announce the area address; separate IIH packets announce the L1 and L2 neighbors. Adjacencies form based on the area address communicated in the incoming IIH and the type of router (L1 or L2). L1 routers accept L1 IIH PDUs from their own area and establish adjacencies with other routers in their own area. L2 routers (or the L2 process within any L1/L2 router) accept only L2 IIH PDUs and establish only Level 2 adjacencies.
In IS-IS, a broadcast link itself is modeled as a pseudo-node that connects all attached routers to a star-shaped topology. The pseudo-node is represented by the DIS. Dijkstra’s algorithm requires this virtual router (pseudo-node) to build a directed graph for broadcast media.
Criteria for DIS selection are, first, highest priority and second, highest SNPA (recall that on LANs the SNPA is the MAC address). Cisco router interfaces have a default L1 and L2 priority of 64. You can configure the priority from 0 to 127 using the isis priority number-value[level-1 | level-2] interface configuration command. The L1 DIS and L2 DIS on a LAN may or may not be the same router, because an interface can have different L1 and L2 priorities.
In IS-IS, all routers on a LAN establish adjacencies with all other routers and with the DIS. Therefore, if the DIS fails, another router takes over immediately with little or no impact on the network’s topology. There is no backup DIS. Contrast this behavior with OSPF, where the DR and BDR are selected and the other routers on the LAN establish full adjacencies only with the DR and BDR. In case of DR failure, the BDR is promoted to DR, and a new BDR is elected.
A selected router is not guaranteed to remain the DIS. Any adjacent IS with a higher priority automatically takes over the DIS role; this is called preemptive behavior. Because the IS-IS LSDB is synchronized frequently on a LAN, giving priority to another IS over the DIS is not a significant issue.
Rather than having each router connected to the LAN advertise an adjacency with every other router on the LAN, each router (including the DIS) just advertises a single adjacency to the pseudo-node. Otherwise, each IS on a broadcast network with n connected ISs would require (n)(n – 1)/2 adjacency advertisements. Generating LSPs for each adjacency creates considerable overhead in terms of LSDB synchronization.
As shown in Figure 6-17, the DIS generates the pseudo-node LSPs. A pseudo-node LSP details only the adjacent ISs (for example, the ISs connected to that LAN). The pseudo-node LSP is used to build the map of the network and to calculate the SPF tree. The pseudo-node LSP is the equivalent of a network LSA in OSPF.
This section describes the LSPs and IIHs used by L1 and L2 routers.
The link-state information for the two levels is distributed separately, in L1 LSPs and L2 LSPs. Each IS originates its own LSPs (one for L1 and one for L2).
On a LAN, one router (the DIS, representing a pseudo-node) sends out LSP information on behalf of the LAN. The DIS sends out the separate L1 and L2 LSPs for the pseudo-node. Recall that the L1 DIS and the L2 DIS on a LAN may or may not be the same router, because an interface can have different L1 and L2 priorities.
LSPs on broadcast media (LANs) are sent as multicast, and LSPs on point-to-point links are sent as unicast.
IIHs are used to establish and maintain neighbor adjacency between ISs. The default hello interval is every 10 seconds; however, the hello interval timer is adjustable.
On a LAN, separate L1 and L2 IIHs are sent periodically as multicasts to a multicast MAC address. L1 announcements are sent to the AllL1IS multicast MAC address 0180.C200.0014, and L2 announcements are sent to the AllL2IS multicast MAC address 0180.C200.0015. The default hello interval for the DIS is 3 times faster (that is, it is 3 times smaller) than the interval for other routers, so that DIS failures can be detected quickly. Unlike DR/BDR in OSPF, there is no backup DIS in IS-IS.
A neighbor is declared dead if hellos are not received within the hold time. The hold time is calculated as the product of the hello multiplier and hello time. The default hello time is 10 seconds and the default multiplier is 3; therefore, the default hold time is 30 seconds.
Unlike LAN interfaces with separate L1 and L2 IIHs, point-to-point links have a common point-to-point IIH format that specifies whether the hello relates to L1 or L2 or both. Point-to-point hellos are sent to the unicast address of the connected router.
Table 6-4 summarizes the differences between broadcast and point-to-point links.
This section describes how IS-IS LSDBs are synchronized between routers.
An IS-IS update process is responsible for flooding the LSPs throughout the IS-IS domain. An LSP is typically flooded to all adjacent neighbors except the neighbor from which it was received. L1 LSPs are flooded within their local areas. L2 LSPs are flooded throughout the backbone.
Each IS originates its own LSPs (one for L1 and one for L2). These LSPs are identified by the originator’s system ID and an LSP fragment number starting at 0. If an LSP exceeds the maximum transmission unit (MTU), it is fragmented into several LSPs, numbered 1, 2, 3, and so on.
IS-IS maintains the L1 and L2 LSPs in separate LSDBs.
When an IS receives an LSP, it examines the checksum and discards any invalid LSPs, flooding them with an expired lifetime age. If the LSP is valid and newer than what is currently in the LSDB, it is retained, acknowledged, and given a lifetime of 1200 seconds. The age is decremented every second until it reaches 0, at which point the LSP is considered to have expired. If an LSP expires, it is kept for an additional 60 seconds before it is flooded as an expired LSP.
Sequence number PDUs (SNPs) are used to acknowledge the receipt of LSPs and to maintain LSDB synchronization. There are two types of SNPs: CSNP and PSNP. The use of SNPs differs between point-to-point and broadcast media.
Key Point: CSNPs and PSNPs
CSNPs and PSNPs share the same format; that is, each carries summarized LSP information.
The main difference is that CSNPs contain summaries of all LSPs in the LSDB, whereas PSNPs contain only a subset of LSP entries.
Separate CSNPs and PSNPs are used for L1 and L2 adjacencies.
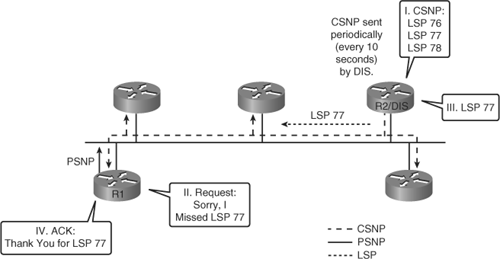
Adjacent IS-IS routers exchange CSNPs to compare their LSDB. In broadcast networks, only the DIS transmits CSNPs. All adjacent neighbors compare the LSP summaries received in the CSNP with the contents of their local LSDBs to determine whether their LSDBs are synchronized (in other words, whether they have the same copies of LSPs as other routers for the appropriate levels and area of routing). CSNPs are periodically multicast (every 10 seconds) by the DIS on a LAN to ensure LSDB accuracy.
If there are too many LSPs to include in one CSNP, they are sent in ranges. The CSNP header indicates the starting and ending LSP ID in the range. If all LSPs fit the CSNP, the range is set to default values.
Adjacent IS-IS routers use PSNPs to acknowledge the receipt of LSPs and to request transmission of missing or newer LSPs.
On point-to-point networks, CSNPs are sent when the link comes up to synchronize the LSDBs.
On a LAN the DIS periodically (every 10 seconds) sends CSNPs that list the LSPs it holds in its LSDB. This update is a multicast to all L1 or L2 IS-IS routers on the LAN.
Figure 6-18 illustrates an example. In this network, R1 compares the list of LSPs from the DIS with its topology table and realizes it is missing one LSP. Therefore, it sends a PSNP to the DIS (R2) to request the missing LSP.
The DIS reissues only that missing LSP (LSP 77), and R1 acknowledges it with a PSNP.
Unlike on broadcast links, such as LAN links, CSNPs are not periodically sent on point-to-point links. A CSNP is sent only once, when the point-to-point link first comes up. After that, LSPs are sent to describe topology changes, and they are acknowledged with a PSNP.
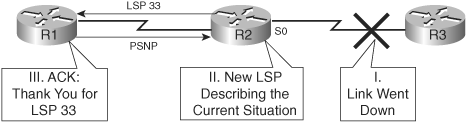
Figure 6-19 shows an example of what happens on a point-to-point link when a link failure is detected.
The steps shown in this example are as follows:
A link fails.
R2 notices this failure and issues a new LSP noting the change.
R1 receives the LSP, stores it in its topology table, and sends a PSNP back to R2 to acknowledge receipt of the LSP.
IIH PDUs announce the area address. On LANs, separate IIH packets announce the L1 and L2 neighbors.
For example, when a LAN has routers from two areas attached, as shown in Figure 6-20, the following process takes place:
The routers from one area accept L1 IIH PDUs only from their own area and therefore establish adjacencies only with their own area routers.
The routers from a second area similarly accept L1 IIH PDUs only from their own area.
The L2 routers (or the L2 process within any L1/L2 router) accept only L2 IIH PDUs and establish only L2 adjacencies.
On point-to-point WAN links, the IIH PDUs are a common format to both levels. The level type and the area address are announced in the hellos, as follows:
L1 routers in the same area (which includes links between L1 and L1/L2 routers) exchange IIH PDUs that specify L1 and establish an L1 adjacency.
L2 routers (in the same area or between areas, and including links between L2 only and L1/L2 routers) exchange IIH PDUs that specify L2 and establish an L2 adjacency.
Two L1/L2 routers in the same area establish both L1 and L2 adjacencies and maintain these with a common IIH PDU format that specifies the L1 and L2 information.
Two L1 routers that are physically connected but are not in the same area can exchange IIHs, but they do not establish an adjacency, because the area addresses do not match.
Figure 6-21 shows the different permutations for WAN adjacencies.
Even when IS-IS is used to support IP exclusively, network devices must also be configured to use the OSI CLNS protocol. Each IS-IS router requires a NET, and IS-IS packets are directly encapsulated onto the data link layer instead of traveling inside IP packets.
The commands to configure Integrated IS-IS are slightly different from those of the other IP routing protocols that you have studied earlier in this book, so it is important to understand how to enable IS-IS processes.
In addition, the default settings for IS-IS can result in the inefficient use of router and network resources and suboptimal routing; therefore, a network administrator also needs to know how to effectively tune IS-IS for optimum performance.
This section discusses the mechanics of Integrated IS-IS operation in an IP and CLNS environment and outlines specific commands necessary to implement Integrated IS-IS on a Cisco router.
A NET address identifies a device (an IS or ES), not an interface. This is a critical difference between a NET address and an IP address.
Even if you use Integrated IS-IS only for IP routing, each IS-IS router must have a NET address configured, because Integrated IS-IS depends on the support of CLNS routing. The OSI protocols (hello PDUs) are used to form the neighbor relationship between routers, and the SPF calculations rely on a configured NET address to identify the routers.
A device identifies other devices within its own area based on matching area addresses in their NET. It then knows that it can communicate with these other devices without using a default route. A default route is injected into the area by the L1/L2 router. If the area addresses do not match, the device knows that it must forward that traffic to its nearest L1/L2 router.
When you are using IS-IS to route IP traffic, IP subnets are treated as leaf objects associated with IS-IS areas. When routing IP traffic, the router looks up the destination network in its routing table. If the network belongs to a different area, then that traffic must also be forwarded to the nearest L1/L2 router.
Scalability is achieved by minimizing the size of the LSDB and routing tables, the amount of processing, and the number of network updates—in other words, using route summarization wherever possible. Route summarization can be accomplished only where the address planning permits grouping addresses by a common prefix. This condition is true for OSI and IP. Therefore, it is very important to carefully plan the IS-IS areas, NET addresses, and IP addresses.
IS-IS uses an OSI forwarding database (routing table) to select the best path to a destination.
When the LSDBs are synchronized, routers use the LSDBs to calculate the SPF tree to OSI destinations (NETs). The total of the link metrics along each path determines the shortest path to any given destination. L1 and L2 routes have separate LSDBs; therefore, routers may run the SPF algorithm twice, once for each level, and create separate SPF trees for each level. Routers insert the best paths into the CLNS routing table (also called the OSI forwarding database).
Routers calculate ES reachability with a partial route calculation (PRC), based on the L1 and L2 SPF trees.
Key Point: IP Routes Only Require PRC
While there are no OSI ESs in a pure IP Integrated IS-IS environment, Integrated IS-IS includes IP prefix reachability information in the LSPs, treating it as if it were ES information. In other words IP prefix information is treated as leaf connections to the SPF tree. Therefore, updating IP reachability requires only a PRC, similar to ES reachability in an OSI network.
The PRC generates best-path choices for IP routes and offers the routes to the IP routing table, where they are accepted based on normal IP routing table rules. For example, if more than one routing protocol is running, the router compares the administrative distances of routes to the same destination. When the IP IS-IS routes are entered into the routing table, they are shown as via L1 or L2, as appropriate.
The separation of IP reachability from the core IS-IS network architecture provides Integrated IS-IS better scalability than OSPF, as follows:
OSPF sends LSAs for individual IP subnets. If an IP subnet fails, the LSA floods through the network and all routers must run a full SPF calculation, which is extremely CPU intensive.
Integrated IS-IS builds the SPF tree from CLNS information. If an IP subnet fails, the LSP floods through the network, which is the same for OSPF. However, if this is a leaf (stub) IP subnet (that is, the loss of the subnet does not affect the underlying CLNS architecture), the SPF tree is unaffected; therefore, only a PRC occurs.
This section describes the configuration process for Integrated IS-IS in an IP environment.
The following four steps are required for the basic setup of Integrated IS-IS. Additional commands are available for fine-tuning the configuration.
Before you can configure Integrated IS-IS, you must plan the areas, prepare the addressing plan (NETs) for the routers, and determine which interfaces to enable Integrated IS-IS on.
Enable IS-IS on the router.
Configure the router’s NET.
Enable Integrated IS-IS on the proper interfaces. Do not forget interfaces to stub IP networks, such as loopbacks (although there are no CLNS neighbors there).
Table 6-5 describes the three basic commands used to enable Integrated IS-IS.
Table 6-5. Commands Necessary to Configure Integrated IS-IS
Command | Description |
|---|---|
(config)#router isis [area-tag] | Enables IS-IS as an IP routing protocol and assigns a tag to the process (optional). |
(config-router)#net network-entity-title | Identifies the router for IS-IS by assigning a NET to the router. |
(config-if)#ip router isis [area-tag] | Enables an interface to use IS-IS to distribute its routing information. (This approach is slightly different from most other IP routing protocols, where the interfaces are defined by network commands; no network command exists under the IS-IS process.) |
The following sections detail these four steps.
Recall that all interarea traffic in IS-IS must traverse the L2 backbone area. Thus, CLNS addresses must be planned to execute a two-level hierarchy. You must decide which routers will be backbone (L2) routers, which routers will be L1/L2, and which will be internal area (L1) routers. If some routers must do both L1 and L2 routing, the specific interfaces that will participate in each type of routing should be identified.
Remember that a router’s CLNS address is called the NET, and it consists of three main parts:
The area address (prefix), which identifies the area that the router is a part of
The system ID, which uniquely identifies each device
The NSEL, which must be 0
It is not enough to plan the IS-IS area addressing. You must also plan IP addressing to allow for summarization of addresses so that the network is scalable. Route summarization is the key that enables all the benefits of hierarchical addressing design. Route summarization minimizes routing update traffic and resource utilization.
Be particularly careful when you configure the IP addressing on the router, because it is more difficult to troubleshoot IP address misconfigurations with IS-IS. The IS-IS neighbor relationships are established over OSI CLNS, not over IP. Because of this approach, two ends of a CLNS adjacency can have IP addresses on different subnets, with no impact on the operation of IS-IS.
The router isis [area-tag] global configuration command enables Integrated IS-IS on the router. You can use the optional tag to identify multiple IS-IS processes. (Just as multiple OSPF processes can be present on the same router, multiple IS-IS processes are possible.) The process name is significant only to the local router. If it is omitted, the Cisco IOS Software assumes a tag of 0. If more than one IS-IS process is used, the network plan should indicate which interfaces will participate in which IS-IS process.
IP routing is enabled by default; CLNS routing is disabled by default. To enable CLNS routing, use the clns routing global configuration command. In addition, you must enable CLNS routing at each interface.
After the IS-IS process is enabled, the router’s NET must be assigned, with the net network-entity-title router configuration command.
Even when you use IS-IS for IP routing only (with CLNS routing not enabled), you must still configure a NET. The NET is a combination of area number and a unique system identification number for each particular router, plus an NSEL of 00 at the end. The area number must be between 1 and 13 bytes in length. The system ID has a fixed length of 6 bytes in Cisco routers and must be unique throughout each area (L1) and throughout the backbone (L2).
The final step is to select which interfaces participate in IS-IS routing. Interfaces that use IS-IS to route IP (and thus must establish IS-IS adjacencies) must be configured using the ip router isis [area-tag] interface configuration command. Enable Integrated IS-IS on the appropriate interfaces—do not forget interfaces to stub IP networks, such as loopback interfaces (even though there are no CLNS neighbors on those interfaces).
If there is more than one IS-IS process, the IS-IS process to which the interface belongs must be specified using the appropriate process name in the optional area-tag field. If no area-tag is listed, the Cisco IOS Software assumes a tag value of 0. If only one IS-IS process is active on the router, no area-tag value is needed.
Use the clns router isis [area-tag] interface configuration command to enable the IS-IS routing process on an interface to support CLNS routing.
Example 6-1 shows a simple Integrated IS-IS configuration for IP routing only; CLNS routing is not enabled. This configuration specifies only one IS-IS process, so the optional area-tag is not used. The net command configures the router to be in area 49.0001 and assigns a system ID of 0000.0000.0002. IS-IS is enabled on the Fast Ethernet 0/0 and serial 0/0/1 interfaces. This router acts as an L1/L2 router by default.
Optimizing IS-IS facilitates its proper functioning and maximizes its efficiency. Three commands that help optimize IS-IS operation are discussed in this section.
The default configuration of IS-IS leaves the router with an IS type of L1/L2. Although this configuration has the advantage of allowing all routers to learn of each other and pass routes without too much administrative oversight, it is not the most efficient way to build an IS-IS network. Routers with the default configuration send out both L1 and L2 hellos and maintain both L1 and L2 LSDBs.
Each router should be configured to support the minimum level of routing required, which does the following:
Saves memory—. If a router does not need the LSDB for one of the levels, it does not maintain one.
Saves bandwidth—. Hellos and LSPs are sent only for the necessary level.
If a router is to operate only as an internal area router or a backbone router, specify this configuration by entering the is-type {level-1 | level-1-2 | level-2-only} router configuration command. To specify that the router act only as an internal area (L1) router, use is-type level-1. To specify that the router act only as a backbone (L2) router, use is-type level-2-only. If the level type has been changed from the default, you can return to the default with the is-type level-1-2 command.
Although a router can be an L1/L2 router, it might not be required to establish both types of adjacencies over all interfaces.
If a particular interface only has L1 routers connected to it, there is no need for the router to send L2 hellos out that interface. Similarly, if an interface only has L2 routers connected to it, there is no need for the router to send L1 hellos out that interface. Extraneous hellos would waste bandwidth and router resources trying to establish adjacencies that do not exist.
To make IS-IS more efficient in these types of situations, configure the interface to send only the needed type of hellos by using the isis circuit-type {level-1 | level-1-2 | level-2-only} interface configuration command. The default is level-1-2; the router will attempt to establish both types of adjacencies over the interface.
Unlike most other IP protocols, IS-IS on a Cisco router does not take into account line speed or bandwidth when it sets its link metrics; all interfaces are assigned a metric value of 10 by default. In a network with links of varying types and speeds, this assignment can result in suboptimal routing.
To change the metric value, use the isis metric metric [delay-metric [expense-metric [error-metric]]] {level-1 | level-2} interface configuration command. The metric can have different values for L1 and L2 over the same interface. The metric value is from 1 to 63.
Note
The IS-IS specification defines four different types of metrics. Cost, being the default metric, is supported by all routers. Delay, expense, and error are optional metrics. The delay metric measures transit delay, the expense metric measures the monetary cost of link utilization, and the error metric measures the residual error probability associated with a link. The default Cisco implementation uses cost only. However, the Cisco IOS does now allow all four metrics to be set with the optional parameters in the isis metric command.
If the metric value for all interfaces needs to be changed from the default value of 10, then the change needs to be performed one by one on all IS-IS interfaces, which can be time-consuming and error-prone, especially for routers with many IS-IS interfaces. Alternately, the metric default-value {level-1 | level-2} router configuration command can be used to change the metric value for all IS-IS interfaces. If the keyword level-1 or level-2 is not entered, the metric will be applied to both L1 and L2 IS-IS interfaces. This command is available only in Cisco IOS Software Release 12.3(4)T and later; it only supports the cost metric.
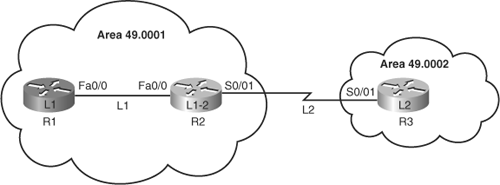
Figure 6-22 shows two different areas. The configurations of the routers are provided in Example 6-2.
Example 6-2. Configurations for Routers in Figure 6-22
R1(config)#router isis R1(config-router)#net 49.0001.0000.0000.0001.00 R1(config-router)#is-type level-1 R1(config)#interface FastEthernet0/0 R1(config-if)#ip router isis R1(config-if)#isis circuit-type level-1 R2(config)#router isis R2(config-router)#net 49.0001.0000.0000.0002.00 R2(config)#interface FastEthernet0/0 R2(config-if)#ip router isis R2(config-if)#isis circuit-type level-1 R2(config)#interface serial 0/0/1 R2(config-if)#ip router isis R2(config-if)#isis circuit-type level-2-only R2(config-if)#isis metric 35 level-2 R3(config)#router isis R3(config-router)#net 49.0002.0000.0000.0003.00 R3(config-router)#is-type level-2-only R3(config)#interface Serial0/0/1 R3(config-if)#ip router isis R3(config-if)#isis circuit-type level-2-only R3(config-if)#isis metric 35 level-2
In this example, area 49.0002 contains only one router (R3) and needs to do only L2 routing. Therefore, it is appropriate to change R3’s IS type to level-2-only.
Area 49.0001 has two routers. R1 is strictly an internal area router; it does not connect to routers in any other area. It is appropriate to configure this router as IS type level-1.
R2 connects to the internal area router R1 and also to R3, in a different area. Therefore, R2 must do both L1 and L2 routing, so it is left at the default IS L1/L2 type setting. However, there is no need for R2 to send L2 hellos out the interface connected to R1, so it is appropriate to set the IS-IS circuit type of R2’s FastEthernet 0/0 to L1. Similarly, because R2’s Serial 0/0/1 interface connects only to an L2 router, the IS-IS circuit type should be set to level-2-only.
Remember that the default IS-IS metric for all interfaces is 10. In this topology, the serial link is slower than the Fast Ethernet link. Using the default metric does not give the routers a true picture of the value of each link, so the routers cannot make truly informed routing decisions. Therefore, the IS-IS metric on each serial interface should be changed to reflect the link preference; in Example 6-2, the metric is set to 35.
Routing protocol scalability is a function of the appropriate use of route summarization.
An IS-IS router can be configured to aggregate a range of IP addresses into a summary address, using the summary-address address mask [level-1 | level-2 | level-1-2] [tag tag-number] [metric metric-value] router configuration command.
This command can be used on any router in an IS-IS network. The router summarizes IP routes into L1, L2, or both; the default is into L2 (level-2). The optional tag-number is used to tag the summary route. The optional metric-value is applied to the summary route.
As discussed earlier, the benefits of summarization include the following:
Reduced routing table size
Reduced LSP traffic and protection from flapping routes
Reduced memory requirements
Reduced CPU usage
A more stable network because topology changes can be isolated
The following is an example of the use of this command, summarizing 10.3.2.0/23 into L1/L2:
R1(config-router)#summary-address 10.3.2.0 255.255.254.0 level-1-2Route summarization is removed with the no form of the command.
Note
The summary-address command works on all IS-IS routers (L1 and L2), but it will only summarize the external IS-IS L1 routes (routes that were redistributed into IS-IS L1). The description of the level-1 parameter in the command documentation is consistent with this: “Only routes redistributed into Level 1 are summarized with the configured address and mask value.” To test this functionality, three loopback interfaces were created, two of them running IS-IS and one redistributed into IS-IS. Only the redistributed route was summarized using the summary-address command on the L1 router.
The partial configuration of R3, an L1 router, is as follows:
!partial config of R3, an L1 router ! interface Loopback111 ip address 3.3.3.3 255.255.255.255 ip router isis ! interface Loopback112 ip address 3.3.3.4 255.255.255.255 ip router isis ! interface Loopback222 ip address 122.122.122.122 255.255.255.255 ! router isis net 49.0011.3333.3333.3333.00 summary-address 122.122.122.0 255.255.255.0 level-1 summary-address 3.3.3.0 255.255.255.0 level-1 redistribute connected level-1 is-type level-1 !
The partial routing table on the R3 L1 router is as follows:
R3#show ip route
<output omitted>
3.0.0.0/32 is subnetted, 2 subnets
C 3.3.3.3 is directly connected, Loopback111
C 3.3.3.4 is directly connected, Loopback112
<output omitted>
122.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 122.122.122.122/32 is directly connected, Loopback222
i su 122.122.122.0/24 [115/0] via 0.0.0.0, Null0The partial routing table on R1, an L1/L2 upstream router, is as follows:
R1#show ip route <output omitted> 3.0.0.0/32 is subnetted, 2 subnets i L1 3.3.3.3 [115/20] via 10.1.1.3, Ethernet0/0 i L1 3.3.3.4 [115/20] via 10.1.1.3, Ethernet0/0 <output omitted> 122.0.0.0/24 is subnetted, 1 subnets i L1 122.122.122.0 [115/10] via 10.1.1.3, Ethernet0/0
Only the redistributed route, 122.122.122.122/32, was summarized, to 122.122.122.0/24. The other two routes were not summarized.
This section describes some commands that can be used to verify IS-IS configuration and CLNS IS-IS structures.
To verify the IS-IS configuration and IP functionality of an Integrated IS-IS network, use the following commands; these commands can also be useful for troubleshooting problems with the IS-IS network:
show ip protocols—. Displays the active IP routing protocols, the interfaces on which they are active, and the networks for which they are routing.
show ip route [address [mask]] | [protocol [process-id]]—. Displays the IP routing table. You can specify the details for a particular route or a list of all routes in the routing table from a particular routing protocol process.
Example 6-3 is sample output from the show ip protocols command that displays information about IP routing being done by Integrated IS-IS. IS-IS is running, it is not redistributing any other protocols, and address summarization has not been configured. Example 6-3 also shows that interfaces FastEthernet 0/0, Loopback 0, and Serial 0/0/1 are taking part in Integrated IS-IS, that there are two sources of routing information (the neighboring routers), and that the administrative distance of Integrated IS-IS is 115.
Example 6-3. show ip protocols Command to Examine IS-IS
R2#show ip protocols
Routing Protocol is "isis"
Invalid after 0 seconds, hold down 0, flushed after 0
Outgoing update filter list for all interfaces is not set
Incoming update filter list for all interfaces is not set
Redistributing: isis
Address Summarization:
None
Maximum path: 4
Routing for Networks:
FastEthernet0/0
Loopback0
Serial0/0/1
Routing Information Sources:
Gateway Distance Last Update
10.10.10.10 115 00:00:02
10.30.30.30 115 00:00:03
Distance: (default is 115)
R2#Sample output from the show ip route isis command in Example 6-4 displays only the IS-IS routes in the IP routing table. One route is from L1, as indicated by the i L1 tag, and the other is from L2, as indicated by the i L2 tag.
Integrated IS-IS uses, by default, an administrative distance of 115. The metric shown for each route is the IS-IS cost to the destination. In Example 6-4, in the value [115/20], 115 is the Integrated IS-IS administrative distance, and 20 is the IS-IS metric.
Many show commands are helpful when troubleshooting CLNS and IS-IS structures, as covered in this section.
You can use the following show clns commands to verify the router configuration and to troubleshoot the CLNS portion of an Integrated IS-IS network:
show clns—. This command displays general information about the CLNS network.
show clns [area-tag] protocol—. This command displays information for the specific IS-IS processes in the router.
show clns interface [type number]—. This command displays information about the interfaces that currently run CLNS.
show clns [area-tag] neighbors [type number] [detail]—. This command displays IS and ES neighbors, if there are any. The neighbor routers are the routers with which this router has IS-IS adjacencies. The optional keyword detail displays the area addresses advertised by the neighbor in the hello messages. You can reduce the list to those neighbors across a particular interface if you specify the interface in the command.
You can use the following show commands to verify the router configuration and to troubleshoot the CLNS and IS-IS portions of the Integrated IS-IS network:
show isis [area-tag] route—. This command displays the IS-IS L1 routing table, which includes all other system IDs in the area. This command is available only if CLNS routing is enabled both globally and at the interface level.
show clns route [nsap]—. This command displays the IS-IS L2 routing table, which includes the areas known to this router and the routes to them. Specify a specific address with the optional nsap parameter.
show isis [area-tag] database—. This command displays the contents of the IS-IS LSDB. To force IS-IS to refresh its LSDB and recalculate all routes, issue the clear isis command; an asterisk (*) can be used to clear all IS-IS processes.
show isis [area-tag] topology—. This command displays the L1 and L2 topology tables, which show the least-cost IS-IS paths to the ISs.
Figure 6-23 is a copy of Figure 6-22, repeated here for your convenience. The figure shows three routers in two areas; routers R1 and R2 belong to area 49.0001 and router R3 belongs to area 49.0002. R1 is an L1 router doing only L1 routing. R2 is an L1/L2 router doing both L1 and L2 routing. R3 is an L2 router doing only L2 routing. The configuration of the three routers is shown earlier, in Example 6-2.
Figure 6-23 forms the basis of the following show command output examples.
The show isis topology command, as shown in Example 6-5, displays the topology databases with the least-cost paths to destination ISs.
Example 6-5. show isis topology Command Output
R1#show isis topology IS-IS paths to level-1 routers System Id Metric Next-Hop Interface SNPA R1 — R2 10 R2 Fa0/0 0016.4650.c470 R2#show isis topology IS-IS paths to level-1 routers System Id Metric Next-Hop Interface SNPA R1 10 R1 Fa0/0 0016.4610.fdb0 R2 — IS-IS paths to level-2 routers System Id Metric Next-Hop Interface SNPA R1 ** R2 — R3 35 R3 Se0/0/1 *HDLC*
Notice in Example 6-5 that the output for Router R1 (an L1 router) shows the topology database for L1 only and the output for Router R2 (an L1/L2 router) shows that separate topology databases exist for L1 and L2.
The fields in the topology database are common for both levels of routing. They are as follows:
The System ID column shows the NET of the destination IS. Cisco IOS Software uses dynamic hostname mapping (per RFC 2763, Dynamic Hostname Exchange Mechanism for IS-IS) to map the system ID to a hostname that is available to the router.
The Metric column displays the sum of the metrics on the least-cost path to the destination.
The Next-Hop column displays the next IS along the path to a destination.
The Interface column shows the output interface that leads to the IS listed in Next-Hop.
The SNPA column contains the OSI Layer 2 address of the next hop. HDLC is shown as the SNPA across an HDLC serial interface. The SNPA across the FastEthernet interface is the MAC address. For a Frame Relay interface, the SNPA would be the DLCI.
The topology database on R1 (an L1 router) in Example 6-5 shows only routers within the local area. R1 is doing only L1 routing, so it does not know of any routers outside its area. Traffic bound for other areas is forwarded to the nearest router doing L2 routing—in this case, R2.
R2 is doing both levels of routing. It thus maintains two topology databases. The L1 database looks very much like the R1 database; only routers within the local area are listed. The L2 database is where the external area router, R3, finally shows up.
In Example 6-6, the example output from the show clns protocol command displays the following information:
The Integrated IS-IS process is running; its tag, if present, is also displayed.
The system ID and area address for this router.
The IS level types for the router.
The interfaces using Integrated IS-IS for routing, including whether they are routing for IP, CLNS, or both.
Any redistribution of other route sources.
Information about the administrative distance for Level 2 CLNS routes and the acceptance and generation of metrics.
Example 6-6. show clns protocol Command as a Troubleshooting Tool
R2#show clns protocol
IS-IS Router: <Null Tag>
System Id: 0000.0000.0002.00 IS-Type: level-1-2
Manual area address(es):
49.0001
Routing for area address(es):
49.0001
Interfaces supported by IS-IS:
Loopback0 - IP
Serial0/0/1 - IP
FastEthernet0/0 - IP
Redistribute:
static (on by default)
Distance for L2 CLNS routes: 110
RRR level: none
Generate narrow metrics: level-1-2
Accept narrow metrics: level-1-2
Generate wide metrics: none
Accept wide metrics: noneIn the example output in Example 6-7, the show clns neighbors command displays the following information:
In Example 6-8, the output from the show clns interface command displays the following information:
The interface runs IS-IS and attempts to establish L2 adjacencies.
The interface numbers and circuit ID for IS-IS purposes.
The ID of the neighbor.
The metric or metrics for the interface.
The priority for DIS negotiation. Priority is not relevant in this case because it is a serial HDLC interface.
Information about hello timers and the number of established adjacencies.
The state of the interface.
Example 6-8. show clns interface Command Output
R2#show clns interface s0/0/1
Serial0/0/1 is up, line protocol is up
Checksums enabled, MTU 1500, Encapsulation HDLC
ERPDUs enabled, min. interval 10 msec.
CLNS fast switching enabled
CLNS SSE switching disabled
DEC compatibility mode OFF for this interface
Next ESH/ISH in 45 seconds
Routing Protocol: IS-IS
Circuit Type: level-2
Interface number 0x1, local circuit ID 0x100
Neighbor System-ID: R3
Level-2 Metric: 35, Priority: 64, Circuit ID: R2.00
Level-2 IPv6 Metric: 10
Number of active level-2 adjacencies: 1
Next IS-IS Hello in 5 seconds
if state UPIn this chapter, you learned about IS-IS, a proven IP routing protocol; the following topics were covered:
History of IS-IS, as the routing protocol for the OSI protocol suite, and its use of CLNS addresses to identify routers and to build the LSDBs.
The two IS-IS routing levels: L1 within areas and L2 between areas.
The three types of IS-IS routers: L1, L2, and L1/L2.
The IS-IS backbone, the path of connected L2 and L1/L2 routers.
Integrated IS-IS, the implementation of the IS-IS protocol for routing multiple network protocols, including IP and CLNS.
Various related protocols and hello messages, including ES-IS, ESHs, ISHs, and IIHs.
The similarities and differences between IS-IS and OSPF.
IS-IS routing operation, including NSAP and NET addresses, how CLNS addressing affects IS-IS operation, and how the IS-IS protocol learns the topology, makes routing decisions, and handles different types of data links.
The OSI PDUs, including the IS-IS and ES-IS PDUs, and the four types of IS-IS PDUs: Hello PDUs, LSPs, PSNPs, and CSNPs.
IS-IS configuration, including enabling the IS-IS protocol, configuring a NET, and enabling IS-IS on the appropriate interfaces.
Optimizing IS-IS configuration, including changing the IS-IS router level and interface level, changing the IS-IS interface metric, and configuring IP route summarization.
Verifying IS-IS configuration and CLNS IS-IS structures.
In this exercise, you configure the routers in your pod for IS-IS routing in multiple areas.
Note
Throughout this exercise, the pod number is referred to as x, and the router number is referred to as y. Substitute the appropriate numbers as needed.
Figure 6-24 illustrates the topology used and what you will accomplish in this exercise.
In this exercise, you use the commands in Table 6-6, listed in logical order. Refer to this list if you need configuration command assistance during the exercise.
Table 6-6. Configuration Exercise Commands
Command | Description |
|---|---|
(config)#router isis | Enables IS-IS on the router. |
(config-router)#net 49.00x1.yyyy.yyyy.yyyy.00 | Identifies the NET to be used for this device. CLNS addresses identify a device, not an interface. |
(config-if)#ip router isis | Enables IS-IS routing on an interface. |
(config-router)#is-type level-1 | Sets this router to participate in only L1 routing (used on internal routers only). |
#show isis topology | Display the IS-IS topology table. |
(config-if)#isis circuit-type level-2-only | Sets this interface to participate in only L2 routing. |
(config-if)#isis circuit-type level-1 | Sets this interface to participate in only L1 routing. |
(config-router)#summary-address 10.x.0.0 255.255.254.0 | Creates a summary route 10.x.0.0/23 (into L2 by default). |
Caution
Although the command syntax is shown in Table 6-6, the addresses shown are typically for the PxR1 and PxR3 routers. Be careful when addressing your routers! Refer to the exercise instructions and the appropriate visual objective diagram for addressing details.
Before starting to investigate IS-IS, you need to remove the OSPF configuration and shut down interfaces to the core.
Remove all OSPF configuration from the internal routers (PxR3 and PxR4).
Solution:
The following shows how to do the required step on the P1R3 router:
P1R3(config)#no router ospf 1Remove all OSPF configuration from the edge routers. Remember to remove the ip ospf network point-to-multipoint command on the S0/0/0.1 subinterface.
Shut down the serial 0/0/0 interface on the edge routers (PxR1 and PxR2) to isolate your pod from the core for this exercise.
Solution:
The following shows how to do the required steps on the P1R1 router:
P1R1(config)#no router ospf 1 P1R1(config)#int s0/0/0 P1R1(config-if)#shutdown P1R1(config-if)#int s0/0/0.1 P1R1(config-subif)#no ip ospf network point-to-multipoint
In this task, you configure IS-IS in multiple areas.
Configure IS-IS on the pod routers and assign a NET address to each router, as shown in Table 6-7. PxR1 and PxR3 should be in area 49.00x1. PxR2 and PxR4 should be in area 49.00x2.
Solution:
The following shows how to do the required steps on the P1R1 and P1R3 routers:
P1R1(config)#router isis P1R1(config-router)#net 49.0011.1111.1111.1111.00 P1R3(config)#router isis P1R3(config-router)#net 49.0011.3333.3333.3333.00
Enable IS-IS on the active serial, loopback, and FastEthernet interfaces of all the routers within your pod. (Recall that only your PxR3 and PxR4 routers have loopback addresses at this point.)
Solution:
The following shows how to do the required steps on the P1R1 and P1R3 routers:
P1R1(config)#int fa0/0 P1R1(config-if)#ip router isis P1R1(config-if)#int s0/0/1 P1R1(config-if)#ip router isis P1R3(config)#int fa0/0 P1R3(config-if)#ip router isis P1R3(config-if)#int s0/0/0 P1R3(config-if)#ip router isis P1R3(config-if)#int loop 0 P1R3(config-if)#ip router isis
Leave the edge routers as the default IS type of L1/L2; however, set up internal routers to participate only in L1 routing using the proper IS-IS router configuration command. When the setup is complete, all communication between the areas will go through the edge routers.
Solution:
The following shows how to do the required steps on the P1R3 router:
P1R3(config)#router isis P1R3(config-router)#is-type level-1
L1 communication takes place only if the areas match. Therefore, PxR3 and PxR4 will not form an L1 adjacency with each other, because they are in different areas. They form an adjacency only with their directly connected edge router. PxR1 and PxR2 form an L2 adjacency.
Look at the IS-IS topology on an internal router; the internal router should have an L1 adjacency with the edge router. Trace the path from one internal router to the loopback address of the opposite internal router. The trace should show that the path to reach the opposite internal router’s loopback address goes through the edge router.
Solution:
The following shows the output on the P1R3 router. P1R3 has an L1 adjacency with the edge router P1R1. The trace shows that the path to reach the opposite internal router’s (P1R4) loopback address goes through the edge router (P1R1, which has address 10.1.1.1).
P1R3#show isis topology IS-IS paths to level-1 routers System Id Metric Next-Hop Interface SNPA P1R1 10 P1R1 Fa0/0 0016.4650.c470 P1R3 — P1R3#trace 10.200.200.14 Type escape sequence to abort. Tracing the route to 10.200.200.14 1 10.1.1.1 0 msec 0 msec 4 msec 2 10.1.0.2 12 msec 16 msec 12 msec 3 10.1.2.4 16 msec * 12 msec P1R3#
Look at the routing table on the internal routers. Notice that IS-IS L1 routing tables resemble OSPF totally stubby areas. For instance, where is the route to the loopback address you just traced to?
Solution:
The following shows the output on the P1R3 router:
P1R3#show ip route <output omitted> Gateway of last resort is 10.1.1.1 to network 0.0.0.0 10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks C 10.200.200.13/32 is directly connected, Loopback0 C 10.1.3.0/24 is directly connected, Serial0/0/0 C 10.1.1.0/24 is directly connected, FastEthernet0/0 i L1 10.1.0.0/24 [115/20] via 10.1.1.1, FastEthernet0/0 i*L1 0.0.0.0/0 [115/10] via 10.1.1.1, FastEthernet0/0 P1R3#
The route to 10.200.200.14 is not shown in the routing table, so the router would use the default route 0.0.0.0, through 10.1.1.1 (P1R1).
Notice the 10.x.0.0/24 route in the routing table. Why is it there?
Solution:
The 10.x.0.0/24 route is the subnet between the edge routers. By default all interfaces on the edge routers are participating in L1 and L2 routing. Therefore, the edge routers are advertising this 10.x.0.0/24 route to the internal routers, as an IS-IS L1 route (displayed as i L1 in the routing table).
Look at the IS-IS topology table on the edge routers. Although these routers participate in L1 and L2 routing, they use only L1 on the FastEthernet interface and only L2 on the serial interface.
Solution:
The following shows the output on the P1R1 router:
P1R1#show isis topology IS-IS paths to level-1 routers System Id Metric Next-Hop Interface SNPA P1R1 — P1R3 10 P1R3 Fa0/0 0016.4610.fdb0 IS-IS paths to level-2 routers System Id Metric Next-Hop Interface SNPA P1R1 — P1R2 10 P1R2 Se0/0/1 *HDLC* P1R3 ** P1R4 ** P1R1#Use the proper IS-IS interface configuration command to remove the redundant (and unused) hellos by forcing PxR1 and PxR2 to participate in a single routing level on each interface (L1 only on the FastEthernet interfaces and L2 only on the serial interfaces). Redundancy—forming both L1 and L2 adjacencies—wastes bandwidth and router resources to form both L1 and L2 adjacencies.
Solution:
The following shows how to do the required steps on the P1R1 router:
P1R1(config)#int s0/0/1 P1R1(config-if)#isis circuit level-2-only P1R1(config-if)#int fa0/0 P1R1(config-if)#isis circuit level-1
Look at the routing table on the internal routers; notice that the 10.x.0.0/24 route is no longer there.
Solution:
The following shows the output on the P1R3 router; the 10.x.0.0/24 route is no longer there:
P1R3#show ip route <output omitted> Gateway of last resort is 10.1.1.1 to network 0.0.0.0 10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks C 10.200.200.13/32 is directly connected, Loopback0 C 10.1.3.0/24 is directly connected, Serial0/0/0 C 10.1.1.0/24 is directly connected, FastEthernet0/0 i*L1 0.0.0.0/0 [115/10] via 10.1.1.1, FastEthernet0/0 P1R3#
On PxR1, summarize the 10.x.0.0 and 10.x.1.0 networks to 10.x.0.0/23. On PxR2, summarize the 10.x.2.0/24 and 10.x.3.0/24 networks to 10.x.2.0/23.
Solution:
The following shows how to do the required steps on the P1R1 and P1R2 routers:
P1R1(config)#router isis P1R1(config-router)#summary-address 10.1.0.0 255.255.254.0 P1R2(config)#router isis P1R2(config-router)#summary-address 10.1.2.0 255.255.254.0
Examine the routing tables on PxR1 and PxR2 to verify that the summary route appears.
Solution:
The following shows the output on the P1R1 router:
P1R1#show ip route <output omitted> Gateway of last resort is not set 10.0.0.0/8 is variably subnetted, 7 subnets, 3 masks i L2 10.200.200.14/32 [115/30] via 10.1.0.2, Serial0/0/1 i L1 10.200.200.13/32 [115/20] via 10.1.1.3, FastEthernet0/0 i L1 10.1.3.0/24 [115/20] via 10.1.1.3, FastEthernet0/0 i L2 10.1.2.0/23 [115/20] via 10.1.0.2, Serial0/0/1 C 10.1.1.0/24 is directly connected, FastEthernet0/0 C 10.1.0.0/24 is directly connected, Serial0/0/1 i su 10.1.0.0/23 [115/10] via 0.0.0.0, Null0 P1R1#
The summary route to 10.1.2.0/23, from P1R2, appears in P1R1’s routing table. Note that the 10.1.3.0/24 route still appears in P1R1’s routing table, but via its FastEthernet 0/0 interface. P1R1 is learning the /24 route from P1R3, and the /23 route from P1R2; it keeps both because they are different routes.
Save your configurations to NVRAM.
Solution:
The following shows how to perform the required step on the P1R1 router:
P1R1#copy run start Destination filename [startup-config]? Building configuration... [OK]
Answer the following questions, and then refer to Appendix A, “Answers to Review Questions,” for the answers.