- Create a WEP access point exactly as in the Caffe Latte attack using the
airbase-ngtool. The only additional option is the-Noption instead of the-Loption to launch the Hirte attack:
- Start
airodump-ngin a separate window to capture packets for the Wireless Lab Honeypot:
Airodump-ngwill now start monitoring this network and storing the packets inHirte-01.capfile.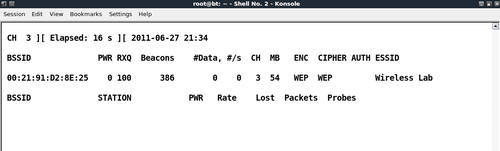
- Once the roaming client connects to out Honeypot AP, the Hirte attack is automatically launched by
airbase-ng:
- We start
aircrack-ngas in the case of the Caffe Latte attack and eventually the key would be cracked as shown next:

..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
